3f251b15424afe3f436745fc49309573.ppt
- Количество слайдов: 21
G-SWFIT A Technique for Fault Injection in Executable Code SAS’ 07, Morgantown Sept. 25 th-27 th Nuno Silva Ricardo Barbosa VV&RAMS Engineering Unit Copyright Critical Software S. A. 1998 -2007 All Rights Reserved.

Presentation Overview n Last Year’s Presentation n Current R&D at CSW n n G-SWFIT Technique and Xception Plugin n n Space. AQua Project Other Research Initiatives Future Work © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 2

Last Year Presentation n COTS vs. Custom Made “Evaluation of COTS through Fault Injection? ” Three techniques for assessing COTS components n n Robustness and Stress Testing Double phased technique using API fault injection and SWIFI Fault Injection for Risk Assessment of real time (COTS) kernels through fault injection n Presentation of the case studies and results © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 3
Current R&D at CSW n Main stream R&D is divided into two different (but related) trends n n n Further development (improvement and optimization) of current Xception plugins n n Space. AQua Project G-SWFIT Technique Mainly based on industrial usage feedback Other Research Initiatives n n Xpy – Non intrusive monitoring tool for space applications Test. OO – Static assessment of object oriented real time applications © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 4
Space. AQua Project n Automated Qualification Framework n n Space. AQua will integrate several techniques and tools for assessing COTS used in space Qualify each assessed product according to a predefined qualification scheme n n Generic Test Plan for Reuse Automate qualification steps (including the definition, generation and execution of test cases) © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 5
G-SWFIT Technique n G-SWFIT n n Assessment and research of the technique Applicability analysis of technique in space systems evaluation, namely COTS Implementation of plug-in for Xception toolset (for Intel IA 32 architecture) Experimentation and validation of toolset © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 6

G-SWFIT Technique n Ph. D work of João Durães n n n Fault injection technique n n Durães, J. , Madeira, H. , “Definition of Software Fault Emulation Operators: a Field Data Study”, DSN 2003 Durães, J. , Madeira, H. , “Generic Faultloads Based on Software Faults for Dependability Benchmarking” Durães, J. , Madeira, H. , “Multidimensional Characterization of the Impact of Faulty Drivers on the Operating Systems Behavior”, IEICE 2003 Durães, J. , Madeira, H. , “Emulation of Software Faults by Educated Mutations at Machine-Code Level”, ISSRE 2002 Used on binary code No source code needed No recompilation or development environment required Applicable virtually to any software n n Need to investigate legal aspects for COTS software Check impacts on SW with Checksums © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 7
G-SWFIT Technique – Fault Types n n Analyses of opensource projects bug lists Classification of faults using: n ODC n n Extra variable ‘nature’ n n associated to the type of correction needed defines if there is something ‘missing’, ‘wrong’ or ‘extraneous’ Selection of the most representative faults © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 8
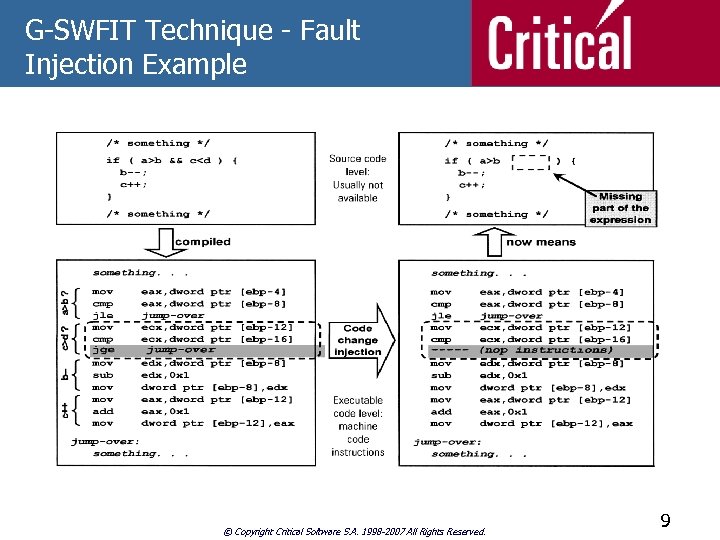
G-SWFIT Technique - Fault Injection Example © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 9
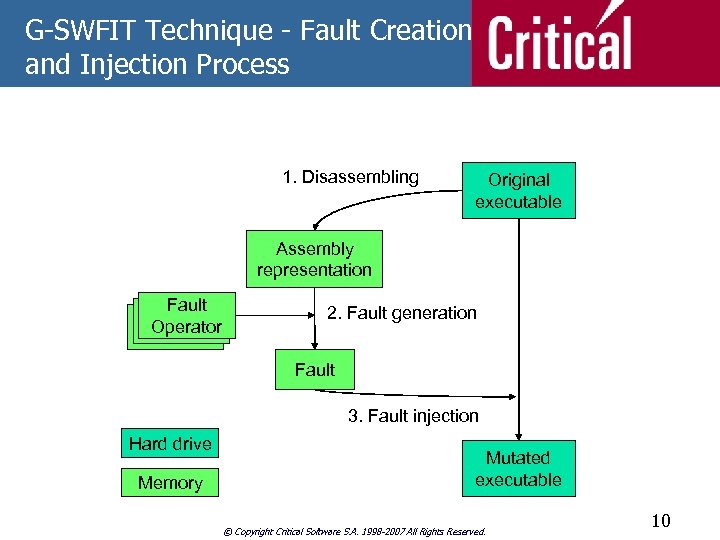
G-SWFIT Technique - Fault Creation and Injection Process 1. Disassembling Original executable Assembly representation Fault Operator 2. Fault generation Fault 3. Fault injection Hard drive Memory Mutated executable © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 10

G-SWFIT Technique - Operator example n Fault Operator for Missing Function Call 1. 2. 3. 4. Locates function calls Function call not alone in block Function Returned value (if any) not used Removes function call Example Search pattern function(. . . ); CALL target-address Pattern Constraint Injection Code change remove ‘CALL’ instruction CALL removal is made by replacing the CALL instruction by NOP instructions © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 11
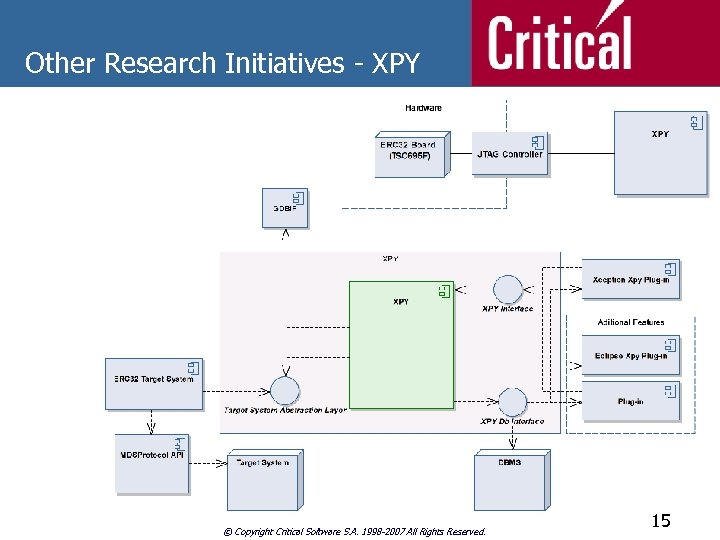
Other Research Initiatives - XPY n XPY - Monitoring and Profiling Tool for Space Software n n XPY provides the end user (VV Engineers) with a automated code coverage analysis of the user software in a non-intrusive way through boundary scan. XPY calculates coverage metrics over the original non -instrumented code, based on the low level monitoring of the target system. n SC (Statement Coverage), EEC (Entry and Exit Point Coverage), DC (Decision Coverage), BCC (Branch Condition Coverage), MC/DC (Modified Condition/Decision Coverage) © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 12
Other Research Initiatives - XPY n XPY - Monitoring and Profiling Tool for Space Software n n Modular architecture design allows to be integrated in different development environments (e. g. Eclipse) and target processors (e. g. LEON – Sparc V 8). The XPY components are: n n XPY Core – metrics calculation, timing statistics, execution control; XPY DB Interface – interface with the pre-defined Database, XPY Interface – integration with application specific plug-ins, Target System Abstraction Layer – interface layer to other processor specific boundary scan libraries. © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 13
Other Research Initiatives - XPY n XPY - Monitoring and Profiling Tool for Space Software n The XPY external components are described hereafter: n n n GDBIF – access to GDB functionalities in the application environment. MDSProtocol API – MDS JTAG API to the ERC 32 Xception. TM XPY Plug-In – XPY GUI as a new Xception. TM Plug-In © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 14
Other Research Initiatives - XPY © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 15

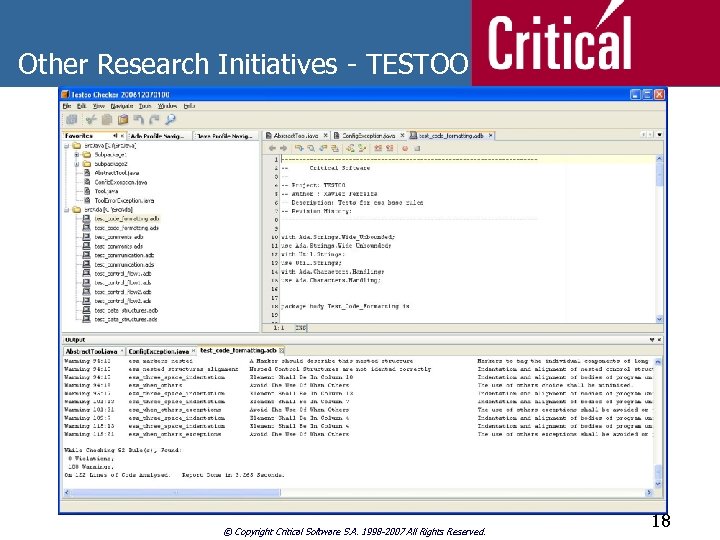
Other Research Initiatives - TESTOO n Testing Object Orientation (Test. OO) n n n Can we relay on Object Oriented Software in Critical Systems? Development a Coding Rules Checker Tool to support a set of coding rules enhancing the testability and verifiability of Object Oriented Software for Critical Systems; Checking Ada and JAVA source code for the right use of: General Best Coding Practices, ESA Standard Coding Rules, BSSC(98)3 Issue 1 Ada 95 Coding Standards, BSSC 2005(2) Issue 1 Java Coding Standards, Object Oriented guidelines provided within the scope of the project. © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 16

Other Research Initiatives - TESTOO n Testing Object Orientation (Test. OO) n Test. OO Checker Architecture n n Modular Architecture Design, Windows XP and Linux OS Portability, Integrates Open Source Tools and Rules DB (Data. Base) Test. OO Checker Features n Generic IDE Layout (GUI) n n n Explorer n File System Browser; Profile Manager (Ada and JAVA Profiles / Rules Navigators) Text Editor Output Console Reporting Facilities Command Line Interface (CLI) © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 17
Other Research Initiatives - TESTOO © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 18
Future Work n Evaluation of Xception G-SWFIT n n n Further validation of toolset Development of other fault operators Optimization of pattern search Assessment of disassembling capabilities Assessment of processor architecture and compiler dependencies OK for OSS, needs to be carefully thought for “other” COTS © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 19
Future Work n Space. AQua Project n n Kick Off of Space. AQua Project (late ’ 07) Cooperation between n n CSW, NASA IVV, WVU and CISUC © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 20

Questions? Thank You! VV&RAMS Engineering Unit Engineering Manager Nuno Silva nsilva@criticalsoftware. com Project Manager Ricardo Barbosa rbarbosa@criticalsoftware. com www. criticalsoftware. com Critical Software SA Critical Software, Limited Critical Software Technologies Ltd Parque Industrial de Taveiro, Lote 48 3045 -504 Coimbra, PORTUGAL Tel: +351 239 989 100 Fax: +351 239 989 119 Pólo Tecnológico de Lisboa, Lote 1, Estrada do Paço do Lumiar 1600 -546 Lisboa, PORTUGAL Tel: +351 21 7101192 Fax: +351 21 7101103 Tecmaia - Rua Eng. º Frederico Ulrich, nº 2650 4470 -605 Moreira da Maia, Porto, PORTUGAL Tel. : +351 229446927 Fax: +351 229446929 111 North Market Street, Suite 670 San Jose, California, USA, 95113 Tel: +1(408) 9711231 Fax: +1(408) 3513330 Suite 19 -21 - 2 Venture Road Southampton Science Park Chilworth - Southampton SO 16 7 NP - United Kingdom Tel: +44 (0)23 8076 3853 © Copyright Critical Software S. A. 1998 -2007 All Rights Reserved. 21
3f251b15424afe3f436745fc49309573.ppt