f41fe9e0c41297d9108ed35e651d66d1.ppt
- Количество слайдов: 28
 » Foundstone Enterprise 4. 0 Detailed Product Presentation Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved
» Foundstone Enterprise 4. 0 Detailed Product Presentation Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved
 Agenda » » » » » Foundstone Solutions Truly Enterprise-Class Asset-based Vulnerability Management Unmatched Assessment Horsepower Life-cycle Threat Management Stream-lined Remediation Measurement & Benchmarking Interoperability: Foundstone Link Total Cost of Ownership Competitive Comparison Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 2
Agenda » » » » » Foundstone Solutions Truly Enterprise-Class Asset-based Vulnerability Management Unmatched Assessment Horsepower Life-cycle Threat Management Stream-lined Remediation Measurement & Benchmarking Interoperability: Foundstone Link Total Cost of Ownership Competitive Comparison Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 2
 Foundstone Product Family » Foundstone Enterprise v 4. 0 – Enterprise-class, award-winning vulnerability management system – Options include: – Remediation Module – Threat Correlation Module – Appliance-based – Feature-rich and the most scalable risk management system available – Low cost of ownership: automated download and installation – All updates Foundstone tested & approved » Foundstone On-Demand Service – Hosted system engineered to manage and mitigate risk – Integrated threat intelligence alerts and correlation – Zero-deployment; no administration or maintenance » Foundstone Professional TL – Designed for consultants and auditors – Enterprise-class functionality and scalability Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 3
Foundstone Product Family » Foundstone Enterprise v 4. 0 – Enterprise-class, award-winning vulnerability management system – Options include: – Remediation Module – Threat Correlation Module – Appliance-based – Feature-rich and the most scalable risk management system available – Low cost of ownership: automated download and installation – All updates Foundstone tested & approved » Foundstone On-Demand Service – Hosted system engineered to manage and mitigate risk – Integrated threat intelligence alerts and correlation – Zero-deployment; no administration or maintenance » Foundstone Professional TL – Designed for consultants and auditors – Enterprise-class functionality and scalability Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 3
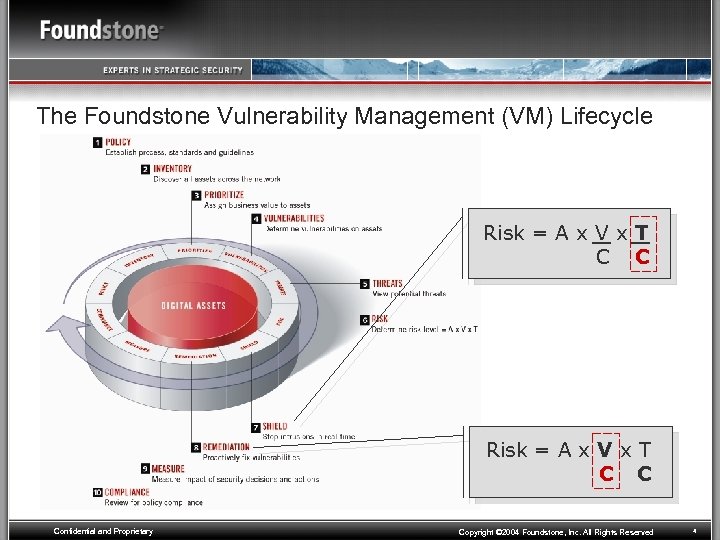 The Foundstone Vulnerability Management (VM) Lifecycle Risk = A x V x T C C Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 4
The Foundstone Vulnerability Management (VM) Lifecycle Risk = A x V x T C C Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 4
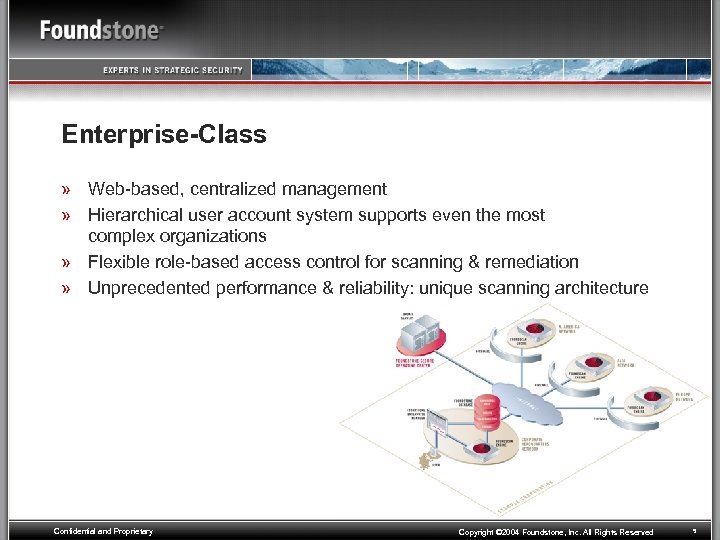 Enterprise-Class » Web-based, centralized management » Hierarchical user account system supports even the most complex organizations » Flexible role-based access control for scanning & remediation » Unprecedented performance & reliability: unique scanning architecture Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 5
Enterprise-Class » Web-based, centralized management » Hierarchical user account system supports even the most complex organizations » Flexible role-based access control for scanning & remediation » Unprecedented performance & reliability: unique scanning architecture Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 5
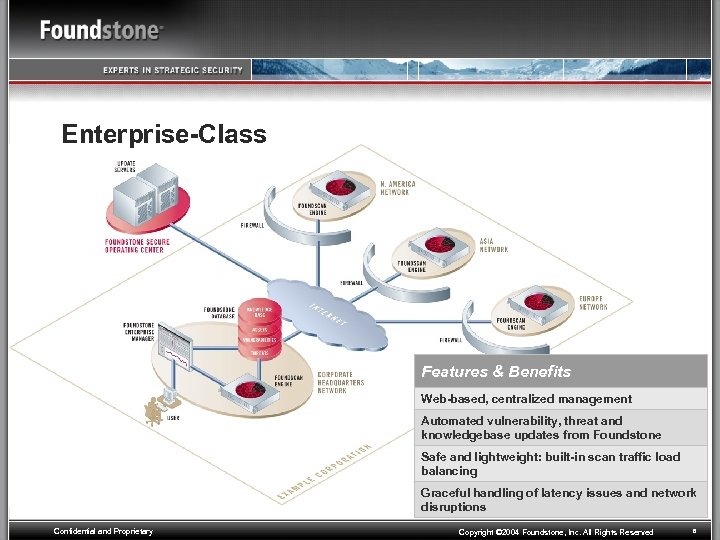 Enterprise-Class Features & Benefits Web-based, centralized management Automated vulnerability, threat and knowledgebase updates from Foundstone Safe and lightweight: built-in scan traffic load balancing Graceful handling of latency issues and network disruptions Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 6
Enterprise-Class Features & Benefits Web-based, centralized management Automated vulnerability, threat and knowledgebase updates from Foundstone Safe and lightweight: built-in scan traffic load balancing Graceful handling of latency issues and network disruptions Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 6
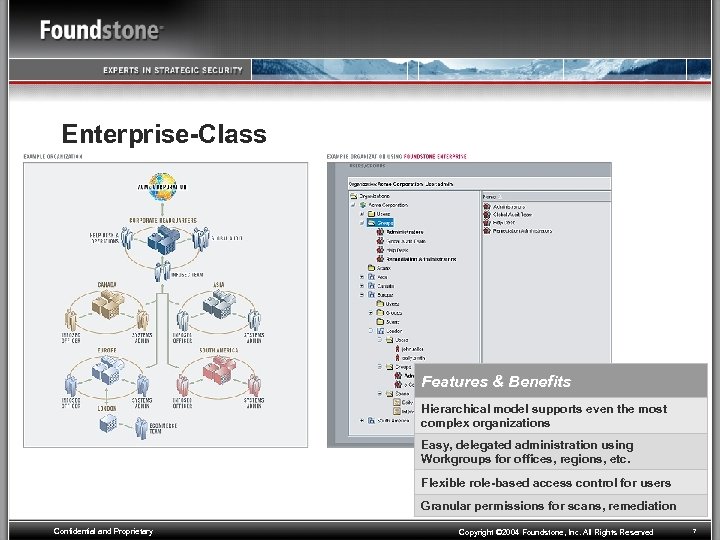 Enterprise-Class Features & Benefits Hierarchical model supports even the most complex organizations Easy, delegated administration using Workgroups for offices, regions, etc. Flexible role-based access control for users Granular permissions for scans, remediation Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 7
Enterprise-Class Features & Benefits Hierarchical model supports even the most complex organizations Easy, delegated administration using Workgroups for offices, regions, etc. Flexible role-based access control for users Granular permissions for scans, remediation Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 7
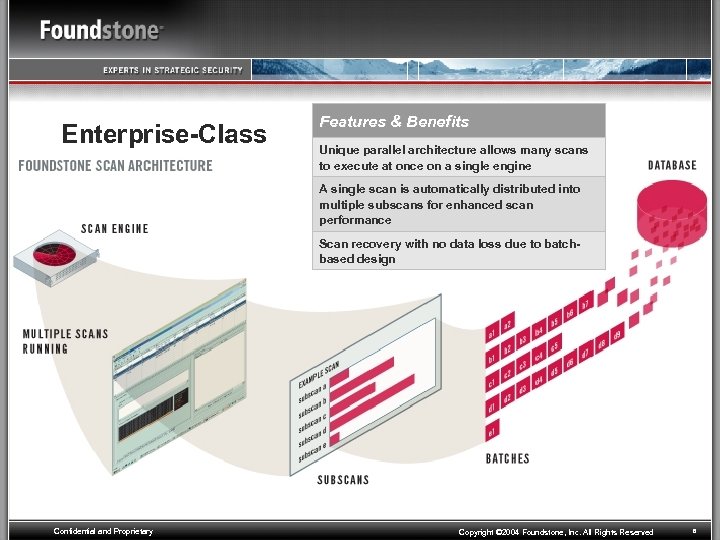 Enterprise-Class Features & Benefits Unique parallel architecture allows many scans to execute at once on a single engine A single scan is automatically distributed into multiple subscans for enhanced scan performance Scan recovery with no data loss due to batchbased design Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 8
Enterprise-Class Features & Benefits Unique parallel architecture allows many scans to execute at once on a single engine A single scan is automatically distributed into multiple subscans for enhanced scan performance Scan recovery with no data loss due to batchbased design Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 8
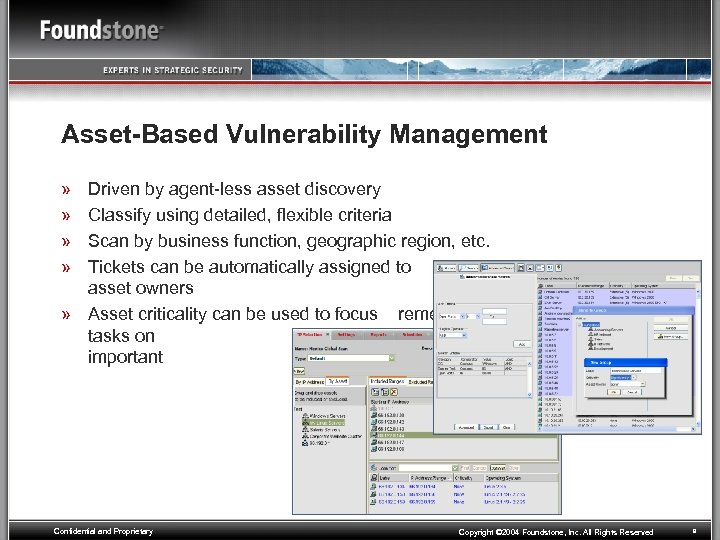 Asset-Based Vulnerability Management » » Driven by agent-less asset discovery Classify using detailed, flexible criteria Scan by business function, geographic region, etc. Tickets can be automatically assigned to group asset owners » Asset criticality can be used to focus remediation tasks on the most important systems Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 9
Asset-Based Vulnerability Management » » Driven by agent-less asset discovery Classify using detailed, flexible criteria Scan by business function, geographic region, etc. Tickets can be automatically assigned to group asset owners » Asset criticality can be used to focus remediation tasks on the most important systems Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 9
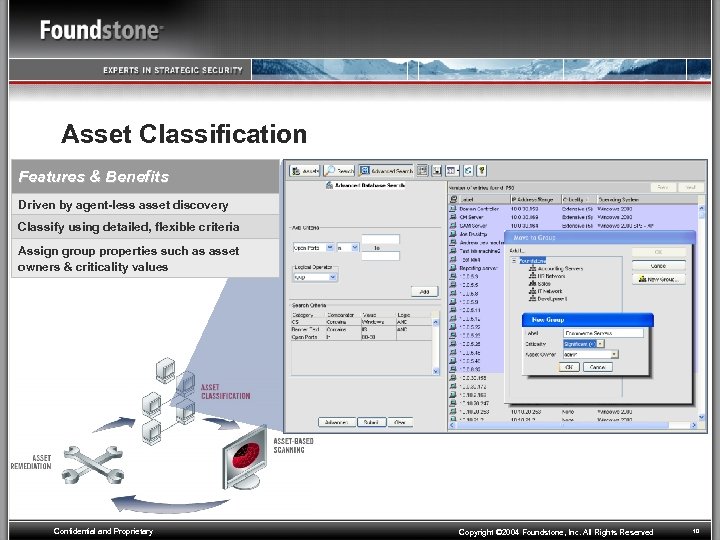 Asset Classification Features & Benefits Driven by agent-less asset discovery Classify using detailed, flexible criteria Assign group properties such as asset owners & criticality values Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 10
Asset Classification Features & Benefits Driven by agent-less asset discovery Classify using detailed, flexible criteria Assign group properties such as asset owners & criticality values Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 10
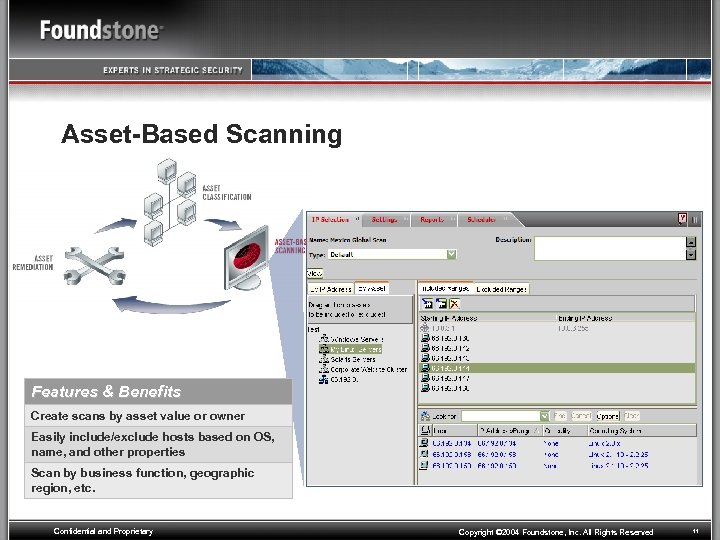 Asset-Based Scanning Features & Benefits Create scans by asset value or owner Easily include/exclude hosts based on OS, name, and other properties Scan by business function, geographic region, etc. Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 11
Asset-Based Scanning Features & Benefits Create scans by asset value or owner Easily include/exclude hosts based on OS, name, and other properties Scan by business function, geographic region, etc. Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 11
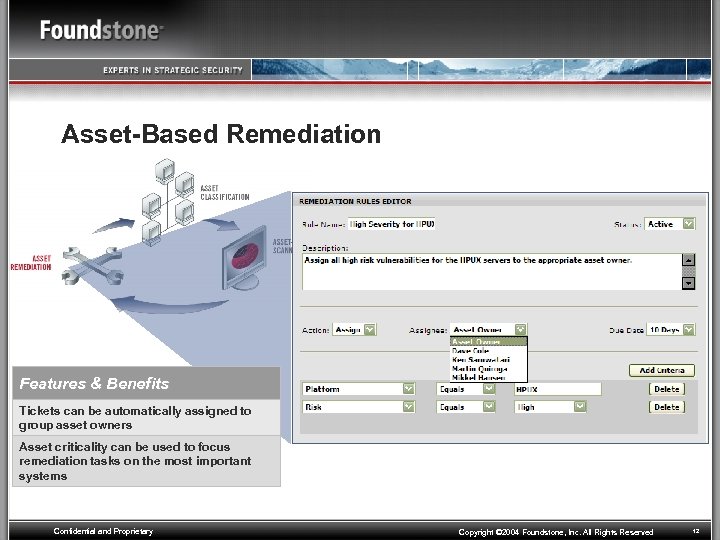 Asset-Based Remediation Features & Benefits Tickets can be automatically assigned to group asset owners Asset criticality can be used to focus remediation tasks on the most important systems Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 12
Asset-Based Remediation Features & Benefits Tickets can be automatically assigned to group asset owners Asset criticality can be used to focus remediation tasks on the most important systems Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 12
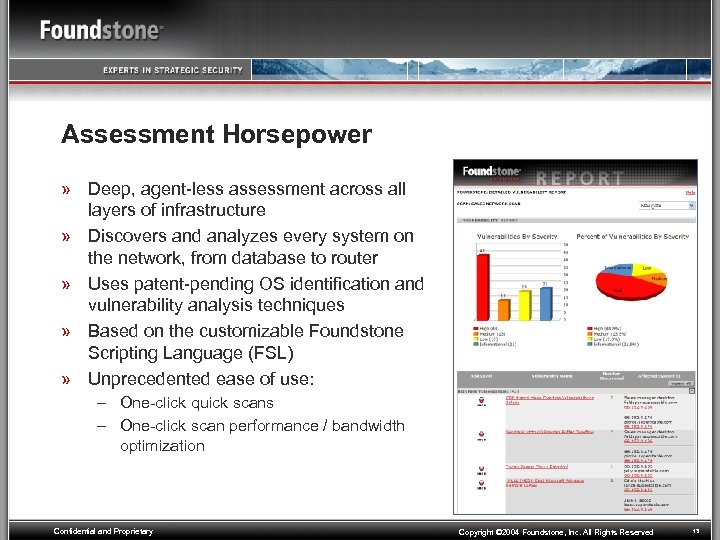 Assessment Horsepower » Deep, agent-less assessment across all layers of infrastructure » Discovers and analyzes every system on the network, from database to router » Uses patent-pending OS identification and vulnerability analysis techniques » Based on the customizable Foundstone Scripting Language (FSL) » Unprecedented ease of use: – One-click quick scans – One-click scan performance / bandwidth optimization Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 13
Assessment Horsepower » Deep, agent-less assessment across all layers of infrastructure » Discovers and analyzes every system on the network, from database to router » Uses patent-pending OS identification and vulnerability analysis techniques » Based on the customizable Foundstone Scripting Language (FSL) » Unprecedented ease of use: – One-click quick scans – One-click scan performance / bandwidth optimization Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 13
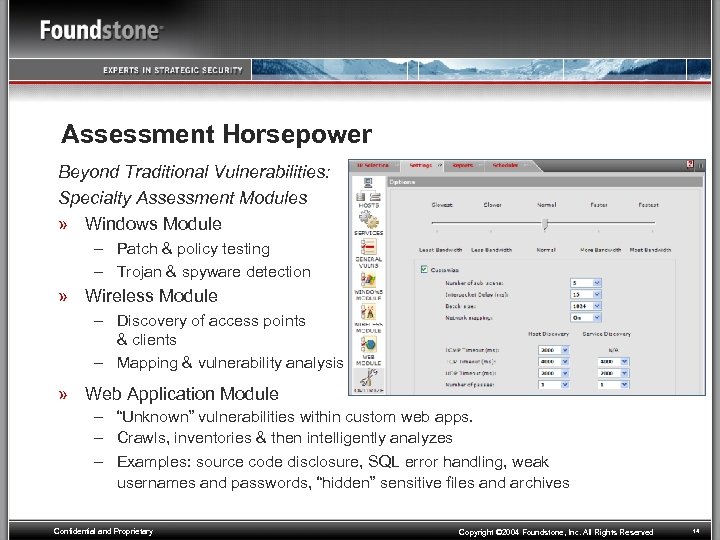 Assessment Horsepower Beyond Traditional Vulnerabilities: Specialty Assessment Modules » Windows Module – Patch & policy testing – Trojan & spyware detection » Wireless Module – Discovery of access points & clients – Mapping & vulnerability analysis » Web Application Module – “Unknown” vulnerabilities within custom web apps. – Crawls, inventories & then intelligently analyzes – Examples: source code disclosure, SQL error handling, weak usernames and passwords, “hidden” sensitive files and archives Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 14
Assessment Horsepower Beyond Traditional Vulnerabilities: Specialty Assessment Modules » Windows Module – Patch & policy testing – Trojan & spyware detection » Wireless Module – Discovery of access points & clients – Mapping & vulnerability analysis » Web Application Module – “Unknown” vulnerabilities within custom web apps. – Crawls, inventories & then intelligently analyzes – Examples: source code disclosure, SQL error handling, weak usernames and passwords, “hidden” sensitive files and archives Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 14
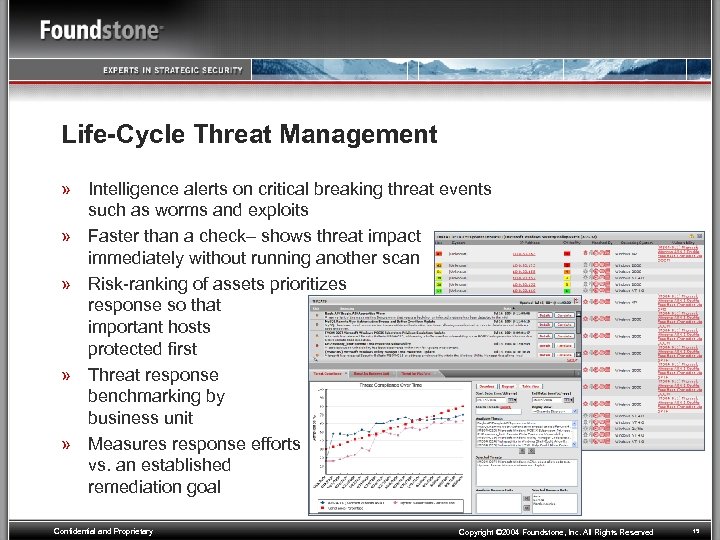 Life-Cycle Threat Management » Intelligence alerts on critical breaking threat events such as worms and exploits » Faster than a check– shows threat impact immediately without running another scan » Risk-ranking of assets prioritizes threat response so that the most important hosts are protected first » Threat response benchmarking by business unit » Measures response efforts vs. an established remediation goal Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 15
Life-Cycle Threat Management » Intelligence alerts on critical breaking threat events such as worms and exploits » Faster than a check– shows threat impact immediately without running another scan » Risk-ranking of assets prioritizes threat response so that the most important hosts are protected first » Threat response benchmarking by business unit » Measures response efforts vs. an established remediation goal Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 15
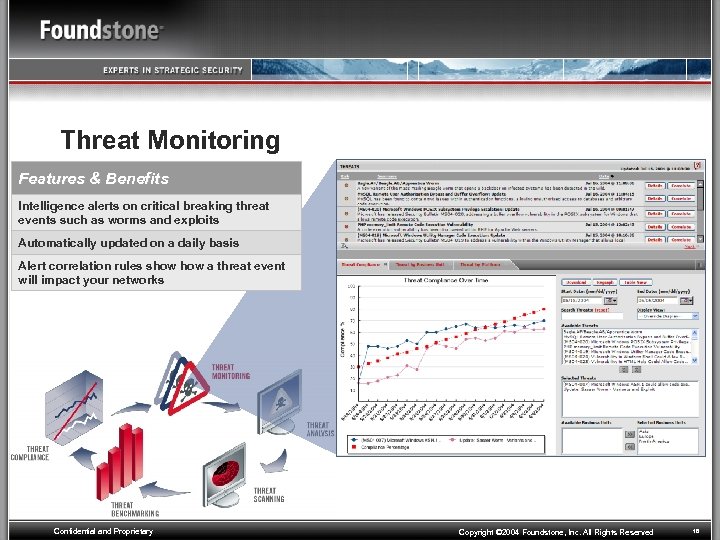 Threat Monitoring Features & Benefits Intelligence alerts on critical breaking threat events such as worms and exploits Automatically updated on a daily basis Alert correlation rules show a threat event will impact your networks Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 16
Threat Monitoring Features & Benefits Intelligence alerts on critical breaking threat events such as worms and exploits Automatically updated on a daily basis Alert correlation rules show a threat event will impact your networks Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 16
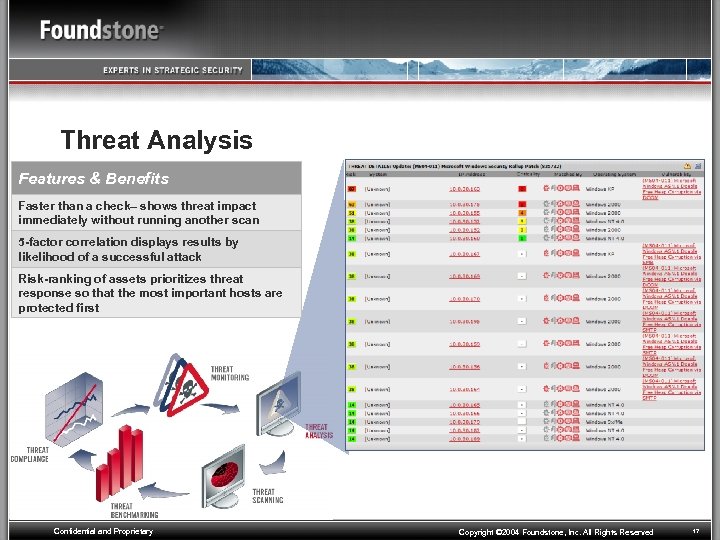 Threat Analysis Features & Benefits Faster than a check– shows threat impact immediately without running another scan 5 -factor correlation displays results by likelihood of a successful attack Risk-ranking of assets prioritizes threat response so that the most important hosts are protected first Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 17
Threat Analysis Features & Benefits Faster than a check– shows threat impact immediately without running another scan 5 -factor correlation displays results by likelihood of a successful attack Risk-ranking of assets prioritizes threat response so that the most important hosts are protected first Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 17
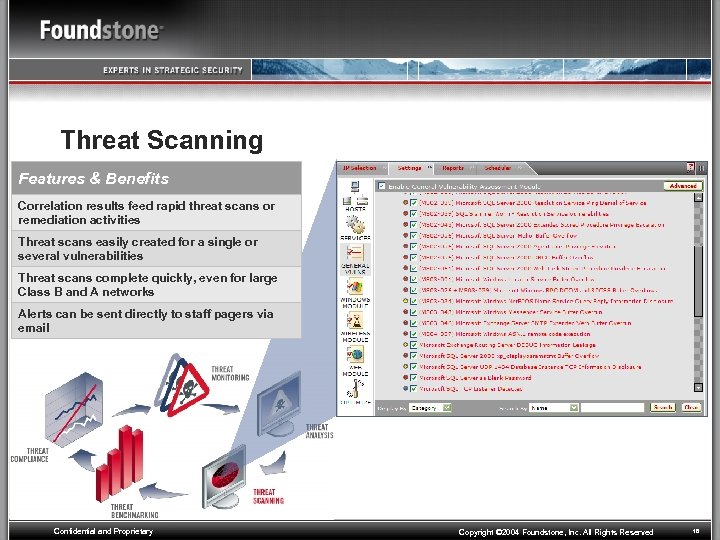 Threat Scanning Features & Benefits Correlation results feed rapid threat scans or remediation activities Threat scans easily created for a single or several vulnerabilities Threat scans complete quickly, even for large Class B and A networks Alerts can be sent directly to staff pagers via email Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 18
Threat Scanning Features & Benefits Correlation results feed rapid threat scans or remediation activities Threat scans easily created for a single or several vulnerabilities Threat scans complete quickly, even for large Class B and A networks Alerts can be sent directly to staff pagers via email Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 18
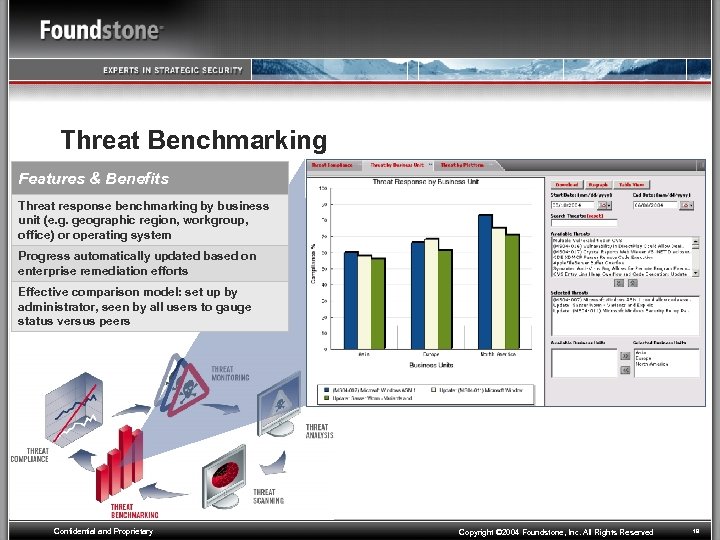 Threat Benchmarking Features & Benefits Threat response benchmarking by business unit (e. g. geographic region, workgroup, office) or operating system Progress automatically updated based on enterprise remediation efforts Effective comparison model: set up by administrator, seen by all users to gauge status versus peers Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 19
Threat Benchmarking Features & Benefits Threat response benchmarking by business unit (e. g. geographic region, workgroup, office) or operating system Progress automatically updated based on enterprise remediation efforts Effective comparison model: set up by administrator, seen by all users to gauge status versus peers Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 19
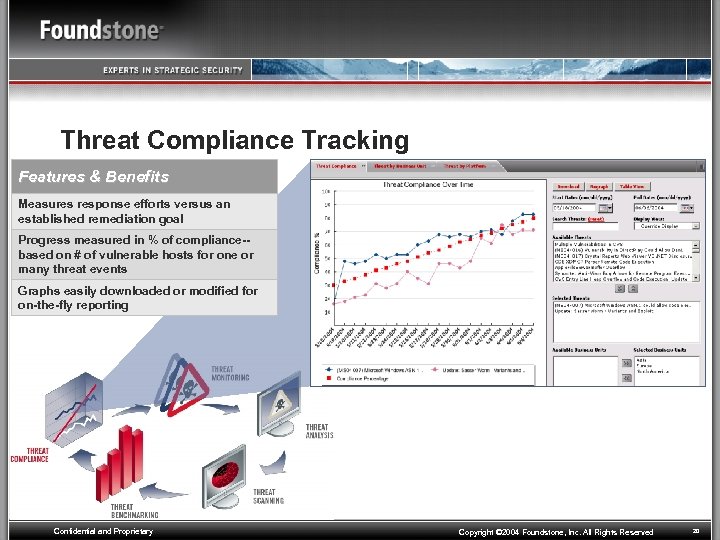 Threat Compliance Tracking Features & Benefits Measures response efforts versus an established remediation goal Progress measured in % of compliance-based on # of vulnerable hosts for one or many threat events Graphs easily downloaded or modified for on-the-fly reporting Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 20
Threat Compliance Tracking Features & Benefits Measures response efforts versus an established remediation goal Progress measured in % of compliance-based on # of vulnerable hosts for one or many threat events Graphs easily downloaded or modified for on-the-fly reporting Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 20
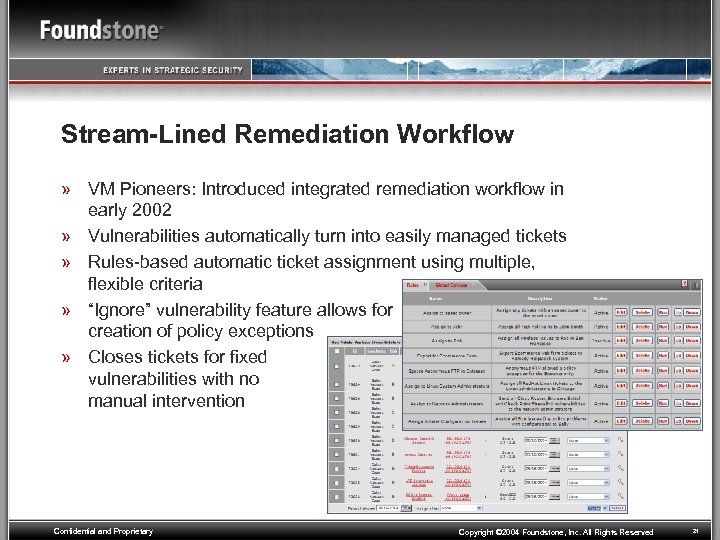 Stream-Lined Remediation Workflow » VM Pioneers: Introduced integrated remediation workflow in early 2002 » Vulnerabilities automatically turn into easily managed tickets » Rules-based automatic ticket assignment using multiple, flexible criteria » “Ignore” vulnerability feature allows for creation of policy exceptions » Closes tickets for fixed vulnerabilities with no manual intervention Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 21
Stream-Lined Remediation Workflow » VM Pioneers: Introduced integrated remediation workflow in early 2002 » Vulnerabilities automatically turn into easily managed tickets » Rules-based automatic ticket assignment using multiple, flexible criteria » “Ignore” vulnerability feature allows for creation of policy exceptions » Closes tickets for fixed vulnerabilities with no manual intervention Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 21
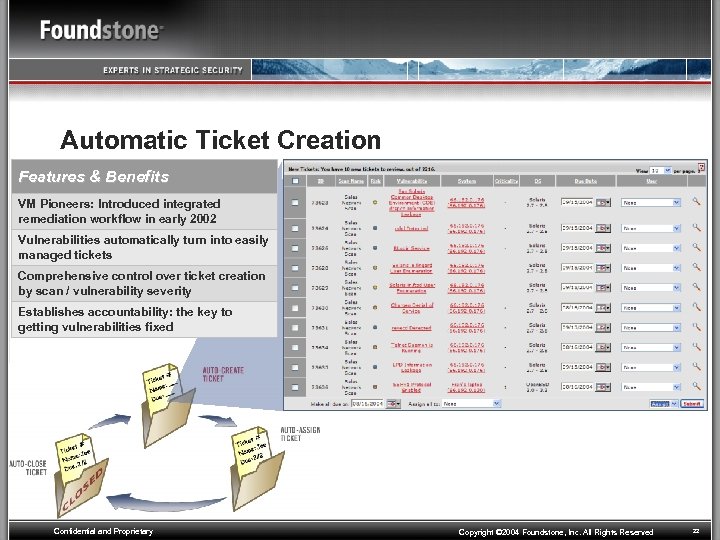 Automatic Ticket Creation Features & Benefits VM Pioneers: Introduced integrated remediation workflow in early 2002 Vulnerabilities automatically turn into easily managed tickets Comprehensive control over ticket creation by scan / vulnerability severity Establishes accountability: the key to getting vulnerabilities fixed Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 22
Automatic Ticket Creation Features & Benefits VM Pioneers: Introduced integrated remediation workflow in early 2002 Vulnerabilities automatically turn into easily managed tickets Comprehensive control over ticket creation by scan / vulnerability severity Establishes accountability: the key to getting vulnerabilities fixed Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 22
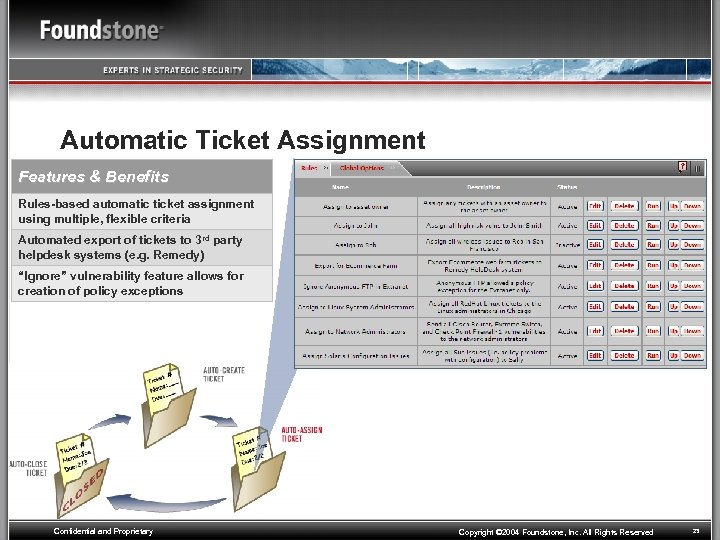 Automatic Ticket Assignment Features & Benefits Rules-based automatic ticket assignment using multiple, flexible criteria Automated export of tickets to 3 rd party helpdesk systems (e. g. Remedy) “Ignore” vulnerability feature allows for creation of policy exceptions Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 23
Automatic Ticket Assignment Features & Benefits Rules-based automatic ticket assignment using multiple, flexible criteria Automated export of tickets to 3 rd party helpdesk systems (e. g. Remedy) “Ignore” vulnerability feature allows for creation of policy exceptions Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 23
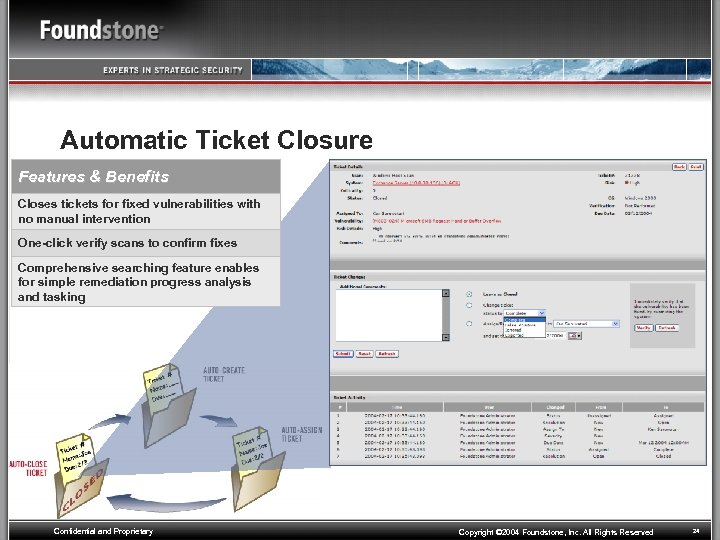 Automatic Ticket Closure Features & Benefits Closes tickets for fixed vulnerabilities with no manual intervention One-click verify scans to confirm fixes Comprehensive searching feature enables for simple remediation progress analysis and tasking Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 24
Automatic Ticket Closure Features & Benefits Closes tickets for fixed vulnerabilities with no manual intervention One-click verify scans to confirm fixes Comprehensive searching feature enables for simple remediation progress analysis and tasking Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 24
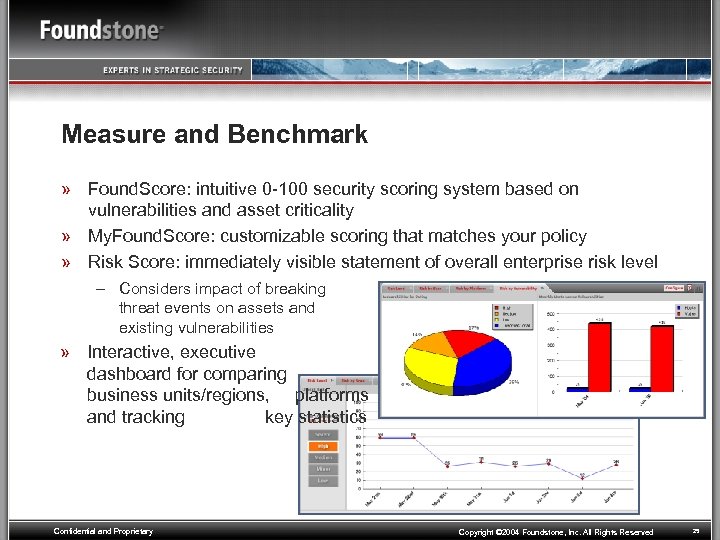 Measure and Benchmark » Found. Score: intuitive 0 -100 security scoring system based on vulnerabilities and asset criticality » My. Found. Score: customizable scoring that matches your policy » Risk Score: immediately visible statement of overall enterprise risk level – Considers impact of breaking threat events on assets and existing vulnerabilities » Interactive, executive dashboard for comparing business units/regions, platforms and tracking key statistics Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 25
Measure and Benchmark » Found. Score: intuitive 0 -100 security scoring system based on vulnerabilities and asset criticality » My. Found. Score: customizable scoring that matches your policy » Risk Score: immediately visible statement of overall enterprise risk level – Considers impact of breaking threat events on assets and existing vulnerabilities » Interactive, executive dashboard for comparing business units/regions, platforms and tracking key statistics Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 25
 Interoperability: Foundstone Link » Open architecture leverages current technology investments – Seamlessly integrates with existing database, network & management solutions – Open database design works with 3 rd party reporting tools & custom SQL queries – Web services-based system » API set to allow external applications to leverage the power of Found. Scan engines – Scan creation, scan management, scan results access » Authentication API for use with Netegrity Siteminder, RSA Secur. ID, LDAP and other technologies » Support for standards such as CVE, IAVA, & SANS/FBI Top 20 Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 26
Interoperability: Foundstone Link » Open architecture leverages current technology investments – Seamlessly integrates with existing database, network & management solutions – Open database design works with 3 rd party reporting tools & custom SQL queries – Web services-based system » API set to allow external applications to leverage the power of Found. Scan engines – Scan creation, scan management, scan results access » Authentication API for use with Netegrity Siteminder, RSA Secur. ID, LDAP and other technologies » Support for standards such as CVE, IAVA, & SANS/FBI Top 20 Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 26
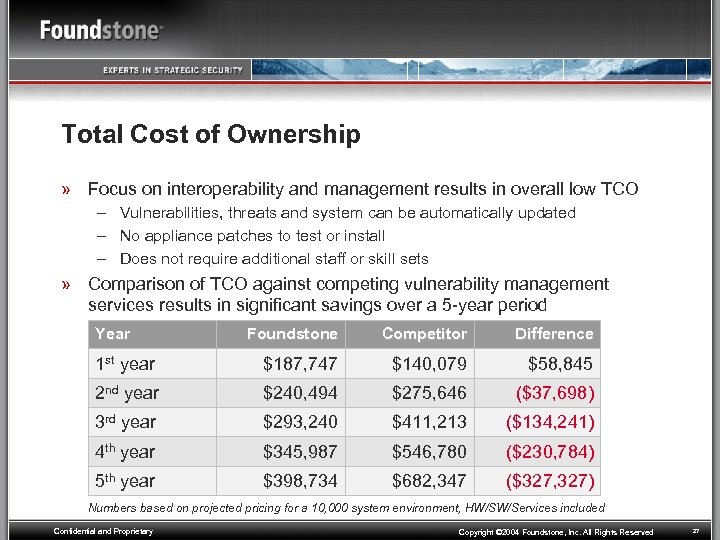 Total Cost of Ownership » Focus on interoperability and management results in overall low TCO – Vulnerabilities, threats and system can be automatically updated – No appliance patches to test or install – Does not require additional staff or skill sets » Comparison of TCO against competing vulnerability management services results in significant savings over a 5 -year period Year Foundstone Competitor Difference 1 st year $187, 747 $140, 079 $58, 845 2 nd year $240, 494 $275, 646 ($37, 698) 3 rd year $293, 240 $411, 213 ($134, 241) 4 th year $345, 987 $546, 780 ($230, 784) 5 th year $398, 734 $682, 347 ($327, 327) Numbers based on projected pricing for a 10, 000 system environment, HW/SW/Services included Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 27
Total Cost of Ownership » Focus on interoperability and management results in overall low TCO – Vulnerabilities, threats and system can be automatically updated – No appliance patches to test or install – Does not require additional staff or skill sets » Comparison of TCO against competing vulnerability management services results in significant savings over a 5 -year period Year Foundstone Competitor Difference 1 st year $187, 747 $140, 079 $58, 845 2 nd year $240, 494 $275, 646 ($37, 698) 3 rd year $293, 240 $411, 213 ($134, 241) 4 th year $345, 987 $546, 780 ($230, 784) 5 th year $398, 734 $682, 347 ($327, 327) Numbers based on projected pricing for a 10, 000 system environment, HW/SW/Services included Confidential and Proprietary Copyright © 2004 Foundstone, Inc. All Rights Reserved 27
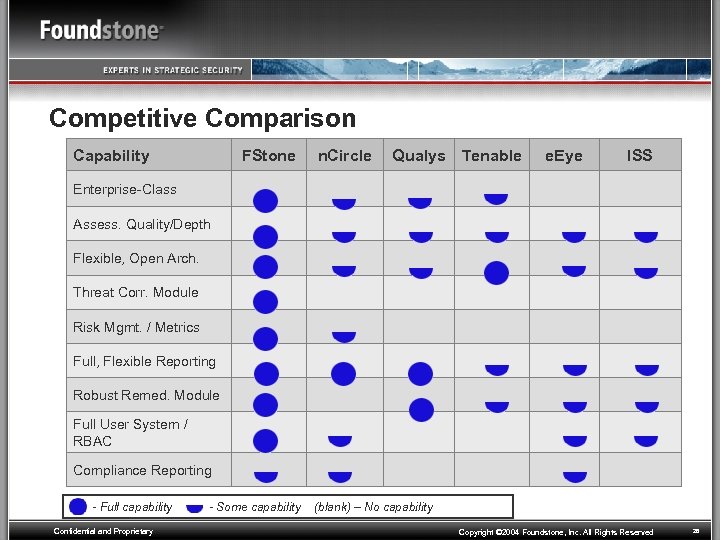 Competitive Comparison Capability FStone n. Circle Qualys Tenable e. Eye ISS Enterprise-Class Assess. Quality/Depth Flexible, Open Arch. Threat Corr. Module Risk Mgmt. / Metrics Full, Flexible Reporting Robust Remed. Module Full User System / RBAC Compliance Reporting - Full capability Confidential and Proprietary - Some capability (blank) – No capability Copyright © 2004 Foundstone, Inc. All Rights Reserved 28
Competitive Comparison Capability FStone n. Circle Qualys Tenable e. Eye ISS Enterprise-Class Assess. Quality/Depth Flexible, Open Arch. Threat Corr. Module Risk Mgmt. / Metrics Full, Flexible Reporting Robust Remed. Module Full User System / RBAC Compliance Reporting - Full capability Confidential and Proprietary - Some capability (blank) – No capability Copyright © 2004 Foundstone, Inc. All Rights Reserved 28


