ae816710724e631b10ada4383a45ba6c.ppt
- Количество слайдов: 28

Foundations of Network and Computer Security John Black Lecture #17 Oct 8 th 2007 CSCI 6268/TLEN 5831, Fall 2007
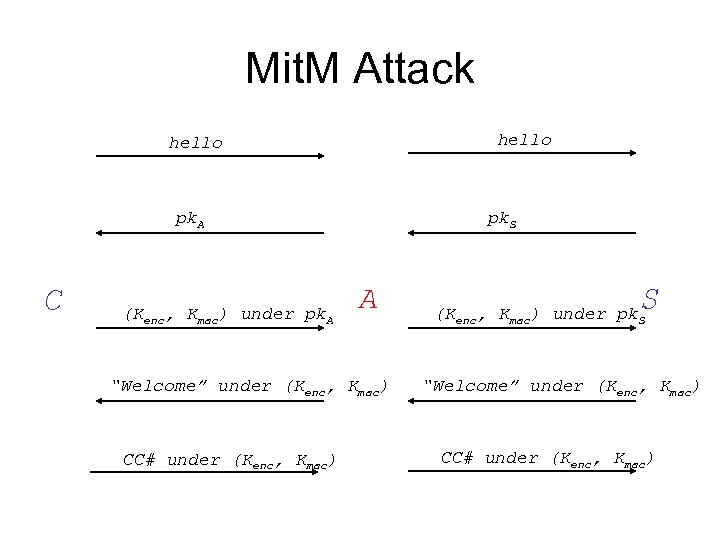
Mit. M Attack hello pk. A C (Kenc, Kmac) under pk. A pk. S A “Welcome” under (Kenc, Kmac) CC# under (Kenc, Kmac) S (Kenc, Kmac) under pk. S “Welcome” under (Kenc, Kmac) CC# under (Kenc, Kmac)

How do we Stop This? • Idea: – Embed pk. S in the browser • A cannot impersonate S if the public key of S is already held by C • Problems: – Scalability (100, 000 public keys in your browser? ) – Key freshening (if a key got compromised and it were already embedding in your browser, how would S update? ) – New keys (how do you get new keys? A new browser? ) – Your crypto is only as reliable as the state of your browser (what if someone gets you to install a bogus browser? ) • (Partial) Solution: Certificates

Certificates: Basic Idea • Enter the “Certification Authority” (CA) – Some trusted entity who signs S’s public key • • • Well-known ones are Verisign, RSA Let’s assume the entity is called “CA” CA generates keys vk. CA and sk. CA CA signs pk. S using sk. CA CA’s vk. S is embedded in all browsers – Same problem with corrupted browsers as before, but the scaling problem is gone

New Protocol • C sends Hello • S sends pk. S and the signature of CA on pk. S – These two objects together are called a “certificate” • C verifies signature using vk. CA which is built in to his browser • C generates (Kenc, Kmac), encrypts with pk. S and sends to S • S decrypts (Kenc, Kmac) with sk. S • Session proceeds with symmetric cryptography

SSH (A Different Model) • SSH (Secure SHell) – Replacement for telnet – Allows secure remote logins • Different model – – – Too many hosts and too many clients How to distribute pk of host? Can be done physically Can pay a CA to sign your keys (not likely) Can run your own CA • More reasonable, but still we have a bootstrapping problem

SSH: Typical Solution • The most common “solution” is to accept initial exposure – When you connect to a host for the first time you get a warning: • “Warning: host key xxxxxx with fingerprint xx: xx is not in the. ssh_hosts file; do you wish to continue? Saying yes may allow a man-in-the-middle attack. ” (Or something like that) • You take a risk by saying “yes” • If the host key changes on your host and you didn’t expect that to happen, you will get a similar warning – And you should be suspicious

Key Fingerprints • The key fingerprint we just saw was a hash of the public key – Can use this when you’re on the road to verify that it’s the key you expect • Write down the fingerprint on a small card and check it • When you log in from a foreign computer, verify the fingerprint – Always a risk to log in from foreign computers!

X. 509 Certificates • X. 509 is a format for a certificate – It contains a public key (for us, at least), email address, and other information – In order to be valid, it must be signed by the CA – In this class, our grader Martin, will be the CA

Project #1 • The next phase of the project – Won’t be assigned for a while, but here is a heads-up – You will generate an RSA pk, sk pair using Open. SSL (genrsa command) • Your private key should be password protected • PEM stands for “Privacy Enhanced Mail” and is the default format used by Open. SSL % openssl genrsa –out john-priv. pem 1024 Generating RSA private key, 1024 bit long modulus. . ++++++ e is 65537 (0 x 10001)
What does secret key look like? -----BEGIN RSA PRIVATE KEY----f. Fbk. Gj. Yxpp 9 d. Epiq 5 p 61 Q/Dm/Vz 5 X 2 Kpp 2+11 q. FCKXLzxc 8 Z 8 z. L 7 Xgi 3 o. V 5 RUt. Sl w. Fjki. Ja. PP 7 fyo/X/Swz 0 LO 1 QKVQ 7 RDUe 9 Npnw. TUBV 44 rt. QVs. SWfbgzd. A 9 MAQT 945 w. BI 27 OAJWYQTAp. Ee. M 2 Jhgvq. CSPtd. In 9 pa. C 9 ye. Iz. XLxwqrnl. LCsc. GKnc. X 53 y 3 J 3 QG KP 1 Uqujpd. TY 9 FRMvb. L 6 b. M 5 cn 1 b. Q 16 p. Sbjntg. Fi 5 q 4 sdcw. BNi. Wve. Fy 5 BNf 4 Fn. Wtk 6 Kd. AQ 4 j. Fe. Zqnw. R 3 e. AP 0 kdleosuc. PNZMxo. QKafsi 19 b. Gi 9 BDd. R 4 Fo. Bd. Hy+K 1 sb. XEm 0 Z 5+mc. VPIITm. B 9 Mg. UQLZ/AFgu. XHsx. GDi. H 74 es 2 Ahe 6 OACx. Wlqe 4 nf. Fxik. XJf. Jw 8 EY 9 nzw 8 x. SZV 5 ov 66 Bu. T 6 e/K 5 cyrd 2 r 0 ml. Ub 9 goo. Yo. VZ 9 Uo. Cf. O/C 6 m. Jcs 7 i 7 MWRNakv t. C 1 Ukt 9 Fq. VF 14 Bcr 1 o. B 4 QEe. K 1 o. WW 3 QU 2 TAr. CWQKc 67 s. Vc. SBuv. MJj. Bd 18 Q+8 AZ 7 GY Jtt 4 rc. OEb 0/EUJu. Mauv 4 Xl. AQki. Jc. Q 46 q. Qjtk. Uo 346+XMe. Rj. Wu. Uy. Q/e 5 A/3 Fhprat 7 C 10 rel. DQon. Vi 5 Wo. Xr. EUTKeoa. Jggg. Zae. Fhdpoee 6 DQe. PSWf. LKB 06 u 7 qp. J 6 Gr 5 XAd Nn. Bo. HEWBYH 4 C 0 Yc. Gm 77 Om. X 7 Cb. Pa. Zi. Irha/WU 7 m. HUBXPUHDCOhy. YQK 8 uis. ADKfm. EV XEzyl 3 i. K 6 h. F 3 c. JFDZJ 5 BBm. I 774 Ao. Bs. B/vah. Lqu. BUj. SPt. Druic 24 h 6 n 2 ZXc. GCLiyc redr 8 Oi. GRJ 0 r 6 XF 85 GYKUO 82 v. Q 6 Tb. SXq. Bg. M 5 Llotf 53 g. DZj. Md. T 71 e. Mx. I 4 Fj 3 PH 91 -----END RSA PRIVATE KEY----(Not very useful, is it? )

Open. SSL RSA Private Key % openssl rsa -in john-priv. pem -text -noout Private-Key: (1024 bit) modulus: 00: a 3: 8 d: 60: 56: df: 75: 52: 50: 62: fb: 6 b: 09: 3 a: 2 e: e 4: 46: 4 e: e 3: e 2: d 2: fe: c 5: 43: 52: 71: 5 a: 47: ed: 26: . . . 63: 29: 27: 38: bf: df: cc: cd: 0 b public. Exponent: 65537 (0 x 10001) private. Exponent: 7 f: 09: 7 c: 50: 5 e: 27: c 9: f 5: 28: bd: 33: 29: aa: a 8: eb: a 4: f 8: 2 b: a 2: 4 a: 44: 3 d: 03: 97: 8 a: 51: 9 e: 12: 29: . . . 19: 7 f: 28: b 4: ff: 70: f 8: 99 prime 1: 00: d 9: 12: 85: e 4: c 5: 6 f: 23: 7 a: 19: 7 c: 34: 81: 1 a: 20: ac: 80: ae: 9 a: 0 d: 24: a 8: ca: 9 d: 43: 06: 7 a: 26: a 1: 02: . . . 0 c: 8 f: a 5: 8 d: 9 f prime 2: … exponent 1: … exponent 2: … coefficient: …

But Notice no Password! • Shouldn’t leave your private key lying around without password protection; let’s fix this % openssl genrsa -aes 128 -out john-priv. pem 1024 Generating RSA private key, 1024 bit long modulus. . . ++++++. . . ++++++ e is 65537 (0 x 10001) Enter pass phrase for john-priv. pem: Verifying - Enter pass phrase for john-priv. pem: % openssl rsa -in john-priv. pem -text -noout Enter pass phrase for john-priv. pem: Private-Key: (1024 bit) modulus: 00: ca: 40: b 9: ef: 31: c 2: 84: 73: ab: ef: e 2: 6 d: 07: 17. . .
What does key look like now? This private key file is encrypted -----BEGIN RSA PRIVATE KEY----Proc-Type: 4, ENCRYPTED DEK-Info: AES-128 -CBC, 1210 A 20 F 8 F 950 B 78 E 710 B 75 AC 837599 B f. Fbk. Gj. Yxpp 9 d. Epiq 5 p 61 Q/Dm/Vz 5 X 2 Kpp 2+11 q. FCKXLzxc 8 Z 8 z. L 7 Xgi 3 o. V 5 RUt. Sl w. Fjki. Ja. PP 7 fyo/X/Swz 0 LO 1 QKVQ 7 RDUe 9 Npnw. TUBV 44 rt. QVs. SWfbgzd. A 9 MAQT 945 w. BI 27 OAJWYQTAp. Ee. M 2 Jhgvq. CSPtd. In 9 pa. C 9 ye. Iz. XLxwqrnl. LCsc. GKnc. X 53 y 3 J 3 QG KP 1 Uqujpd. TY 9 FRMvb. L 6 b. M 5 cn 1 b. Q 16 p. Sbjntg. Fi 5 q 4 sdcw. BNi. Wve. Fy 5 BNf 4 Fn. Wtk 6 Kd. AQ 4 j. Fe. Zqnw. R 3 e. AP 0 kdleosuc. PNZMxo. QKafsi 19 b. Gi 9 BDd. R 4 Fo. Bd. Hy+K 1 sb. XEm 0 Z 5+mc. VPIITm. B 9 Mg. UQLZ/AFgu. XHsx. GDi. H 74 es 2 Ahe 6 OACx. Wlqe 4 nf. Fxik. XJf. Jw 8 EY 9 nzw 8 x. SZV 5 ov 66 Bu. T 6 e/K 5 cyrd 2 r 0 ml. Ub 9 goo. Yo. VZ 9 Uo. Cf. O/C 6 m. Jcs 7 i 7 MWRNakv t. C 1 Ukt 9 Fq. VF 14 Bcr 1 o. B 4 QEe. K 1 o. WW 3 QU 2 TAr. CWQKc 67 s. Vc. SBuv. MJj. Bd 18 Q+8 AZ 7 GY Jtt 4 rc. OEb 0/EUJu. Mauv 4 Xl. AQki. Jc. Q 46 q. Qjtk. Uo 346+XMe. Rj. Wu. Uy. Q/e 5 A/3 Fhprat 7 C 10 rel. DQon. Vi 5 Wo. Xr. EUTKeoa. Jggg. Zae. Fhdpoee 6 DQe. PSWf. LKB 06 u 7 qp. J 6 Gr 5 XAd Nn. Bo. HEWBYH 4 C 0 Yc. Gm 77 Om. X 7 Cb. Pa. Zi. Irha/WU 7 m. HUBXPUHDCOhy. YQK 8 uis. ADKfm. EV XEzyl 3 i. K 6 h. F 3 c. JFDZJ 5 BBm. I 774 Ao. Bs. B/vah. Lqu. BUj. SPt. Druic 24 h 6 n 2 ZXc. GCLiyc redr 8 Oi. GRJ 0 r 6 XF 85 GYKUO 82 v. Q 6 Tb. SXq. Bg. M 5 Llotf 53 g. DZj. Md. T 71 e. Mx. I 4 Fj 3 PH 91 -----END RSA PRIVATE KEY-----

CSR: Certificate Request • You will generate a CSR – Certificate Request • Has your name, email, other info, your public key, and you sign it • Send your CSR to the CA – CA will sign it if it is properly formatted – His signature overwrites your signature on the CSR • Once CA signs your CSR it becomes a certificate

Creating a CSR % openssl req -key john-priv. pem -new -out john-req. pem Enter pass phrase for john-priv. pem: You are about to be asked to enter information that will be incorporated into your certificate request. Country Name (2 letter code) [AU]: US State or Province Name (full name) [Some-State]: Colorado Locality Name (eg, city) []: Boulder Organization Name (eg, company) [Internet Widgits Pty Ltd]: University of Colorado Organizational Unit Name (eg, section) []: Computer Science Common Name (eg, YOUR name) []: John Black Email Address []: jrblack@cs. colorado. edu (Leave the rest blank) This outputs the file john-req. pem which is a cert request

Viewing a CSR % openssl req -in john-req. pem -text -noout Note: not password protected Certificate Request: Data: Version: 0 (0 x 0) Subject: C=US, ST=Colorado, L=Boulder, O=University of Colorado, OU=Computer Science, CN=John Black/email. Address=jrblack@cs. colorado. edu Subject Public Key Info: Public Key Algorithm: rsa. Encryption RSA Public Key: (1024 bit) Modulus (1024 bit): 00: ca: 40: b 9: ef: 31: c 2: 84: 73: ab: ef: e 2: 6 d: 07: 17: 83: 5 e: 96: 46: 24: 25: 38: ed: 7 a: 60: 54: 58: e 6: f 4: 7 b: . . . 27: de: 00: 09: 40: 0 c: 5 e: 80: 17 Exponent: 65537 (0 x 10001) Attributes: a 0: 00 Signature Algorithm: md 5 With. RSAEncryption 32: e 1: 3 f: e 2: 12: 47: 74: 88: a 3: f 9: f 4: 44: 8 a: f 3: b 7: 4 e: d 1: 14: 1 f: 0 b: be: b 8: 19: be: 45: 40: ed: 5 b: fb: ab: 9 b: 01: e 8: 9 a: 26: 0 c: . . . 9 c: e 0 CSR is signed by you

CSRs • Why is your CSR signed by you? – Ensures that the CSR author (you) have the private key corresponding to the public key in the CSR • If we didn’t do this, I could get the CA to sign anyone’s public key as my own – Not that big a deal since I can’t decrypt things without the corresponding private key, but still we disallow this • Why does the CA sign your public key – Well, because that’s his reason for existence, as discussed previously – Ok, let’s say I email my CSR to Martin and he signs it… then what?

Sample Certificate -----BEGIN CERTIFICATE----MIIDk. DCCAnig. Aw. IBAg. IBCz. ANBgkqhki. G 9 w 0 BAQQFADCBg. TEQMA 4 GA 1 UEAx. MHSm 9 o bi. BDQTERMA 8 GA 1 UECBMIQ 29 sb 3 Jh. ZG 8 x. Cz. AJBg. NVBAYTAl. VTMSYw. JAYJKo. ZIhvc. N AQk. BFhdqcm. Js. YWNr. QGNz. Lm. Nvb. G 9 y. YWRv. Lm. Vkd. TEl. MCMGA 1 UECh. Mc. Um 9 vd. CBDZXJ 0 a. WZp. Y 2 F 0 a. W 9 u. IEF 1 d. Ghvcml 0 e. TAe. Fw 0 w. Mz. Ex. MTMy. MDQ 1 Mj. Fa. Fw 0 w. NDEx. MTIy. MDQ 1 Mj. Fa. MIGFMRIw. EAYDVQQDEwl. UZXN 0 IFVz. ZXIx. ETAPBg. NVBAg. TCENvb. G 9 y. YWRv. MQsw CQYDVQQGEw. JVUz. Ej. MCEGCSq. GSIb 3 DQEJARYUd. GVzd. EBjcy 5 jb 2 xvcm. Fkby 5 l. ZHUx Fj. AUBg. NVBAo. TDVVua. XYg. Q 29 sb 3 Jh. ZG 8 x. Ej. AQBg. NVBAs. TCUNTQ 0 kg. NDgz. MDCCASIw DQYJKo. ZIhvc. NAQEBBQADgg. EPADCCAQo. Cgg. EBAL 1 k 6 h. J 9 gw. Xl. UYHi. FOm 6 OHOf+8 Y 0 o 1 b 7 WOex. Yf. NDWm 9 H 0 I 79 o 0 w. Vg. Dj 7 wa. Ogt 4 hz 2 FE 2 h+g. Arf. GY 5 Vsa. Szm. CH 0 EA 4 k. DS m/s. Pob 3 HTVpb. IFwlb. XTV 7 h. C 0 Ox. Oz. Rs 8 lph. Ddj 1 va. NDSn. Owq. OS 1 ADCf. Ida. GEh 9 WKi r. Ed. Fdriiu 7 v 1 bw+c 1 By. M 57 v 9 a. HO 7 Rslsw. R 9 En. RFZPWYa 8 Gp. K+St 0 s 8 b. ZVf 98 IOOk H 8 Hiliy. VSt 5 l. AXRMn. Ixh. YMG 89 tkku. CAwxg. DD+7 Wqy. ETYx. Y 0 UCg/jo. FV 4 IKc. C 7 W 1 b Cmvxs. Y 6/H 35 Up. Ggv 0 an. Ckjy. P 0 m. KY/YWB 9 KXwr. R 8 NHC 7/hacij 0 YNi. V 77 EIMCAw. EA Aa. MNMAsw. CQYDVR 0 TBAIw. ADANBgkqhki. G 9 w 0 BAQQFAAOCAQEAZr 4 hd. QPc. Gn. AYmk++ 0 b. Q 4 UKILXj 9 wr 7 UZdgz 3 DKJNp. MPk. Fjz. U 6 wv. Jrd 1 C 8 KIKf. JC 63 TKHJ 7 svmd. Zw. TCB 2 h. NUFy 8 kbe 2 Kv. NWQi. Go. X 3 Pa. Y 1 eo 3 au. Lz. Ii 8 Ix. Pq. N+W/p 1 z 3 Mhtp. Qq. Nllqz. G 8 G 1 o 50 QP 2 y. Ayj 2 V 0 rnwl. RL 3 k. Z 7 ibv. XRn. SB 1 Bz+6 z. JJLAQr 4 k. TQD 2 Efx. Lhpks+i. SE+m 58 PV tfck 25 o 2 IMJYYLAdto. NGjc. FG 9/a. Dk+GHbsx 8 LP/va 6 B 6 BIz. B 3 vrefu. Qv. Bu+7 j/mz a. XP 7 Qku. GYf 1 r 4 yy. Oiu. MYnw 0 kwp 5 xnd. DKTz. ORsxks. HQk 5 AWf. BXr. Dd. GPZrb 6 i 1 Ul. Oq U/P 3+A== -----END CERTIFICATE----- Ooh…how useful!
Viewing a Certificate % openssl x 509 -in john-cert. pem -text –noout Certificate: Again, no encryption Data: Version: 3 (0 x 2) Serial Number: 1 (0 x 1) Signature Algorithm: sha 1 With. RSAEncryption Issuer: CN=Martin Cochran, ST=Colorado, C=US/ email. Address=Martin. Cochran @colorado. edu, O=University of Colorado Validity Not Before: Oct 7 19: 52: 43 2007 GMT Not After : Oct 7 19: 52: 43 2008 GMT Subject: C=US, ST=Colorado, L=Boulder, O=University of Colorado, OU=Computer Science, CN=John Black/email. Address=jrblack@cs. colorado. edu Subject Public Key Info: Public Key Algorithm: rsa. Encryption RSA Public Key: (1024 bit) Modulus (1024 bit): 00: ca: 40: b 9: ef: 31: c 2: 84: 73: ab: ef: e 2: 6 d: 07: 17: 83: 5 e: 96: 46: 24: 25: 38: ed: 7 a: 60: 54: 58: e 6: f 4: 7 b: . . . 27: de: 00: 09: 40: 0 c: 5 e: 80: 17 Exponent: 65537 (0 x 10001) Signature Algorithm: sha 1 With. RSAEncryption 97: 4 a: 20: ea: a 7: 5 a: 4 d: 4 c: 77: b 9: 3 e: c 0: 49: 9 b: ab: 8 f: 6 f: 02: 53: 24: a 9: 71: 97: 2 c: 1 f: e 8: e 4: eb: d 0: f 6: 6 a: 7 c: 74: 30: 1 d: 9 e: . . . 3 a: 59 Now it’s the CA’s signature

What have we Accomplished? • We have an X. 509 cert – It contains our public key, name, email, and other stuff – It is signed by the CA • You have a private key in a password-protected file – Don’t lose this file or forget the password! • What else do we need? – We need to be able to verify the CA’s signature on a public key! – We therefore need the CA’s verification key

CA’s Verification Key is a Cert! • The CA generates a self-signed “root certificate” – This is his verification key (aka public key) which he signs – This certificate is what is embedded in your browser – This certificate is used to validate public keys sent from other sources – Martin’s root certificate will be used to validate all public keys for our class

Martin’s Root Cert -----BEGIN CERTIFICATE----MIIDo. TCCAomg. Aw. IBAg. IJALqp. KIgpak. S 2 MA 0 GCSq. GSIb 3 DQEBBQUAMIGGMRcw. FQYD VQQDEw 5 NYXJ 0 a. W 4 g. Q 29 ja. HJhbj. ERMA 8 GA 1 UECBMIQ 29 sb 3 Jh. ZG 8 x. Cz. AJBg. NVBAYT Al. VTMSow. KAYJKo. ZIhvc. NAQk. BFht. NYXJ 0 a. W 4 u. Q 29 ja. HJhbk. Bjb 2 xvcm. Fkby 5 l. ZHUx Hz. Ad. Bg. NVBAo. TFl. Vua. XZlcn. Npd. Hkgb 2 Yg. Q 29 sb 3 Jh. ZG 8 w. Hhc. NMDUx. MDE 3 MTk 1 Mj. Qz Whc. NMDYx. MDE 3 MTk 1 Mj. Qz. Wj. CBhj. EXMBUGA 1 UEAx. MOTWFyd. Glu. IENv. Y 2 hy. YW 4 x. ETAP Bg. NVBAg. TCENvb. G 9 y. YWRv. MQsw. CQYDVQQGEw. JVUz. Eq. MCg. GCSq. GSIb 3 DQEJARYb. TWFy d. Glu. Lk. Nv. Y 2 hy. YW 5 AY 29 sb 3 Jh. ZG 8 u. ZWR 1 MR 8 w. HQYDVQQKEx. ZVbml 2 ZXJza. XR 5 IG 9 m IENvb. G 9 y. YWRv. MIIBIj. ANBgkqhki. G 9 w 0 BAQEFAAOCAQ 8 AMIIBCg. KCAQEAx. R 40 jv 85 z 6 Ackjv. P 9 yu. TDYS 7 tb. Ciai 738 a. Hp. GVGXvi. Ufd. PR 2 TS 3 la. Rx. Xnh 8 Nd 8 i 4 LT 8+X/BB WJk 9 le. Bs 82 Vfu. EEO 2 m 7 ksri. Hu+Z 1 v. ADJ 0 q 9 L 6 cmx. HQk. PA 32 okx. OPlx 33 F 6 u. U+E 7+ qfv. O 1 Uimf/QAb. Wv. XTHlnv/Bt. Ivz 2 h. RHi. Uguu. Nx. Iq. Vq. Fpejeb. L 7 qerzq. IBei 6 o. BTo OMkj 7 sjx. XM 6/ag. U 7 p 1 x. Axlnxusl. PKw 9 ff 8 QR 7 N 4 Ai. Fr. Gm. Qka. Fpjd. ZGTd. Fyofm. XRB MBahb 4 Zn 1/Dv. WA 1 t. HFJGAv 2 EEEMd 5 ey. URzbt+kd 2 Xjt. Hdy. Hd 62 Rf 8 b. Z 6 Yz. Pin. I 3 o 72+go. Fp. WW 97 YEw. IDAQABox. Aw. Dj. AMBg. NVHRMEBTADAQH/MA 0 GCSq. GSIb 3 DQEBBQUA A 4 IBAQAk 15 usr 3 Y 9 f. WKdm. Fz. Rjyl 7 ICv. XLb 3 b. Ap. BEA 4 RFIHv 6 i. MAPt. L 58 Xg. Yo 48 ke Eh. Cxt 4 YJU 2 ed. Oql 2 Ko+l. Gq 9 Dn. DM 12 a. Lfp. GTx. F 6+Qzg. BC 0 c. A 3 Bewxvue. WTWQF 23 V 6 bn. Ve. Qq. Zm. K 3 m+bv 4 rvj 0 x 1 HMKSVqf. S 83 UDJxv 8 k. Fq 1 EQj 2 ja. WOVuu. IDLGNBr 75 x. Tk /Lbz. Dy. Y/BLmr. Btsd. G 1 VCAm 6 ONLRf. SEum. Q 2 B 3 f. Wpa 8 Elcv. KNTR 6 WJOe. HIh. K 0 VUHRW 14 bxv. MNWSg. QEPSqbe. SUr. HM 7 ar. ZMbv. E 7/CFPxn/Sjvgz 9 Pkjm 0 f. Jh 4 AIKz. Tq/7 K 2 Z x. ZK 7 ZGq 0 UP 6 n. MS 75 a 7 Hy/q. OC 1 YQe -----END CERTIFICATE-----

How to Distribute the Root Cert? • It’s ridiculous for me to ask you to write this down, right? – If I email it to you, it might get altered by an adversary – If I put it on the web page, it might get altered by an adversary – Ok, this is probably not a REAL concern for us, but we’re practicing being paranoid – What can we do?

Distributing the Root Cert • Fingerprint the root certificate! – We’ll just distribute the fingerprint as a verification check – The cert itself will be distributed via some insecure means – The fingerprint will use a collision-resistant hash function, so it cannot be altered – But now we have to distribute the fingerprint • This you can write down, or I can hand you a hardcopy on a business card, etc • People used to have a fingerprint of their PGP public key on their business cards at conferences… haven’t seen this in a while though
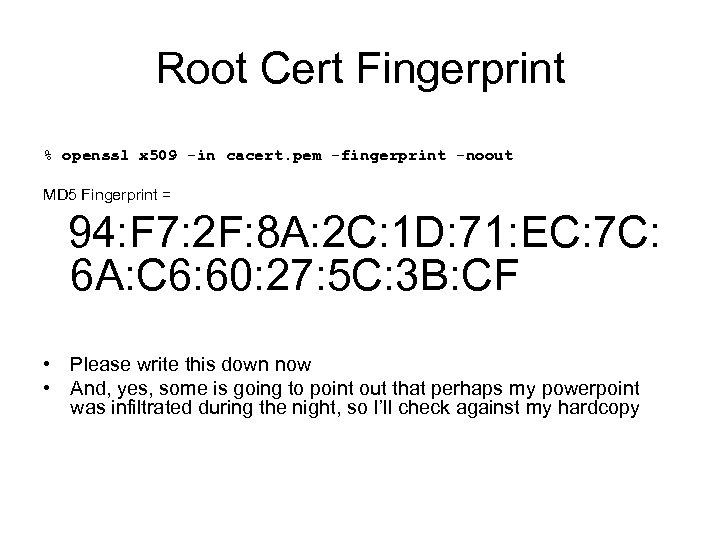
Root Cert Fingerprint % openssl x 509 -in cacert. pem -fingerprint -noout MD 5 Fingerprint = 94: F 7: 2 F: 8 A: 2 C: 1 D: 71: EC: 7 C: 6 A: C 6: 60: 27: 5 C: 3 B: CF • Please write this down now • And, yes, some is going to point out that perhaps my powerpoint was infiltrated during the night, so I’ll check against my hardcopy

Overall Idea of the Project • Each student has a cert containing a public key corresponding to his private key • Each student knows the verification key of the CA • Student A wants to send secure mail message M to student B – A obtains B’s cert and verifies it is correctly signed by the CA – A chooses a random session key K and RSA encrypts using B’s public key (from B’s cert) – A writes out the encrypted K followed by M encrypted symmetrically, then signs each of these with her private key and sends to B • B receives all of this and… – – Obtains A’s cert and verifies it is signed by CA B verifies A’s signature on the message B uses his private key to decrypt K (session key used by A) B uses K to decrypt M

Sample Message from A to B RSA Encrypted Session Key K -----BEGIN CSCI 6268 MESSAGE----hjh 2 vke. SGp. Weh. Awg. MOEb. Koms. W 3 l. Td 8 BBBr. Ef. Fchb. AZpnbc+O 7 wc. I 8 OT 0 g 9 WP 9 i. PV K 92 xbz. Ai. Vl. AN 7 ZFOWlx/i. X 2 XQIb. UQBU 6 kl 7 NOy. PTt. SZ/5+9 JHVDY 1 TFZG 3 c. Gt. Vj 5 Se. J 97+kvu. Wk. Zv. Nc. Kj. Aec 1 Yb. RYp. XRGw. Rmq. Ptz+o 5 WYWq. Wmq. PV 6 l. QWjb. N 4 Jc+w 2 Gcl FKR 7 t 0 Zsi 5 Rcn. Ew. In+c. Ztu. Te 3 QWW 4/in. MGMBFgb. Xj. A 2 E 6 VU 7 zn 62 Bd. BHh 7 S 1/o. BR tt 84 Rr 4/o. XXJhr. EASd. ZJEd. Gw 8 trh 0 FPd 48 io. HEl. T 7 TNGMx 4 YJKHBV 1+EMj. Tc. Hwd. N DCr 29 AZ 2 Qy. Dh/p. HYqv. Jm. Vg== AES-128 -CBC encrypted message M U 2 Fsd. GVk. X 1/QUjgfw 4 j. EV 34 P/Efn 8 Ub 7 NDz. V 5 QL+u. Woe. Dblsp. Qiz 2 Bi. Pq. QEa 1 acb CD 2+Xg. D 36 Fmmc. P 9 Wx. DOd. Q 63 Al. X 2 K 4 t 4 Sd. Sy. TT 8 uk 9 Ypd. UC 0 thq. CXFk. DGM 6 P 0 u 7 Xx g. Bx. P 0 s 0 mtc. NFKbcpwmi. Ep 5 K 8 ay. GHs. YW 5 l. M 2 ve. Fcl. VL 75 x. Re. QGA 8 fkj. Z 3 OQQe. R+nz n. QTg 2 Hniyaniwbb 11 Yg. Bmy. WQ 4 bs. VK 5 UDG 0 i. Yab 100 cv. PUl. FZXr. Mm. K 4 aum. MNt. C+0 Z +Syj 4 Fa. Pz. Uphhebhuhs. U 29 tahd 8 h. L 9 DZQ 5 Zuz. Zi 5 hy 0 n. G 5 z 45 FHktap/bww. OGC Iu 3 m. RM 6 Zqo. TVVan. Tqf 0 c. Ba. RA 5 c+XJbhu. XLxj. S 44 vi. FKSKENm. Z 7 p. EPZtdisvd/aq 2 we. Zb 1 am. Cy 2 jn. P 0 x. Qio. I 8 Lc/zkno 5 XRW 21 b. GH 3 k. We. G 8 k. Mu. Or. BKVyms 2 FOEps. I 0 TH 0 UIzck 095 R 4 jn. PUI+e 7 S 85 z 1 Wx 1 Toy. MI 3 Ub/Mee 3 My. It 60 H 2 r 2 LC 4 sp 9 CO 1 Yn 4 t. YN p. A 4 ULy 3 Dh. Fy 4 z 9 x 4 b. X+a. U+b. Symiqf 5 Jv. Sj. MXS/z. QYERW+1 fh. OKn. U 3 f. I 518 m. E 9 Gbx t. JBJJmjn. Px. Wh. Wp. SJjv. G 7 q. EAdy/Pibc. D 8 YPXn 3 NZ 7 j 1 m. U 8 Sg. Yog 9 vw. Jwz 3 fs. Ka. CS 6 AP 4 LTLN 9 ef 5 Hb/STtv. A+ow== -----END CSCI 6268 MESSAGE----- RSA signature on first two chunks
ae816710724e631b10ada4383a45ba6c.ppt