4d308e7e86f0e23b7e5a8c10758fd530.ppt
- Количество слайдов: 18
 Formalizing Security Requirements for Grids Syed Naqvi 1, 2, Philippe Massonet 1, Alvaro Arenas 2 1 Centre of Excellence in Information and Communication Technologies (CETIC) {syed. naqvi, philippe. massonet}@cetic. be 2 CCLRC Rutherford Appleton Laboratory {s. naqvi, a. e. arenas}@rl. ac. uk
Formalizing Security Requirements for Grids Syed Naqvi 1, 2, Philippe Massonet 1, Alvaro Arenas 2 1 Centre of Excellence in Information and Communication Technologies (CETIC) {syed. naqvi, philippe. massonet}@cetic. be 2 CCLRC Rutherford Appleton Laboratory {s. naqvi, a. e. arenas}@rl. ac. uk
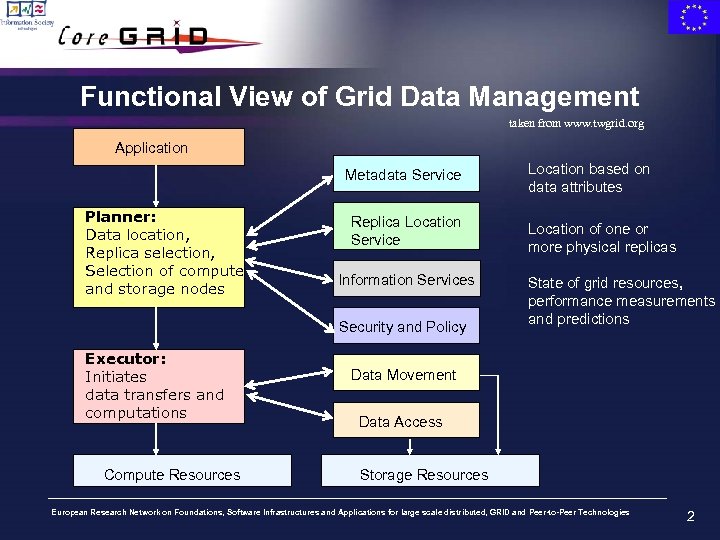 Functional View of Grid Data Management taken from www. twgrid. org Application Metadata Service Planner: Data location, Replica selection, Selection of compute and storage nodes Replica Location Service Information Services Security and Policy Executor: Initiates data transfers and computations Compute Resources Location based on data attributes Location of one or more physical replicas State of grid resources, performance measurements and predictions Data Movement Data Access Storage Resources European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 2
Functional View of Grid Data Management taken from www. twgrid. org Application Metadata Service Planner: Data location, Replica selection, Selection of compute and storage nodes Replica Location Service Information Services Security and Policy Executor: Initiates data transfers and computations Compute Resources Location based on data attributes Location of one or more physical replicas State of grid resources, performance measurements and predictions Data Movement Data Access Storage Resources European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 2
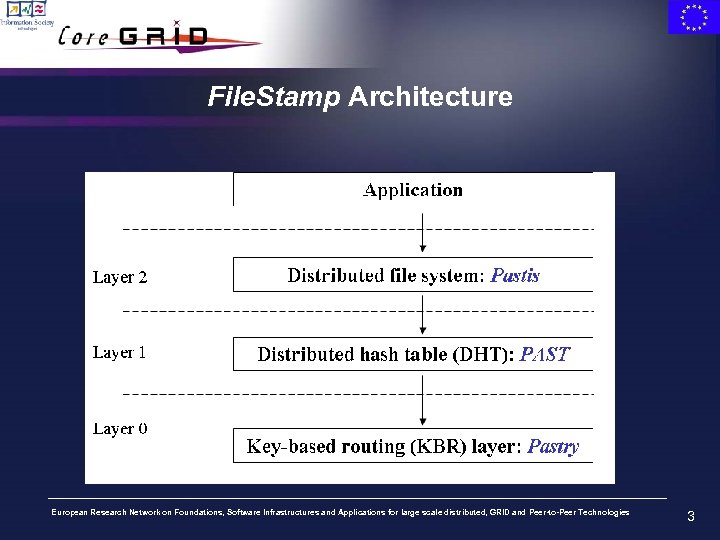 File. Stamp Architecture European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 3
File. Stamp Architecture European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 3
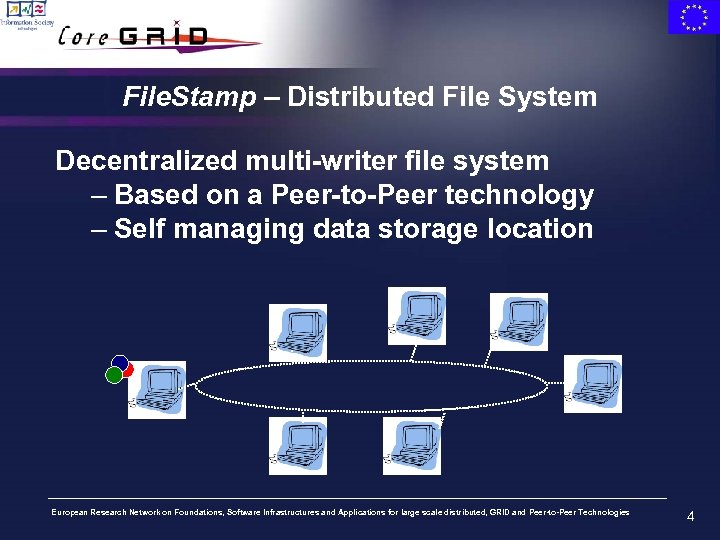 File. Stamp – Distributed File System Decentralized multi-writer file system – Based on a Peer-to-Peer technology – Self managing data storage location European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 4
File. Stamp – Distributed File System Decentralized multi-writer file system – Based on a Peer-to-Peer technology – Self managing data storage location European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 4
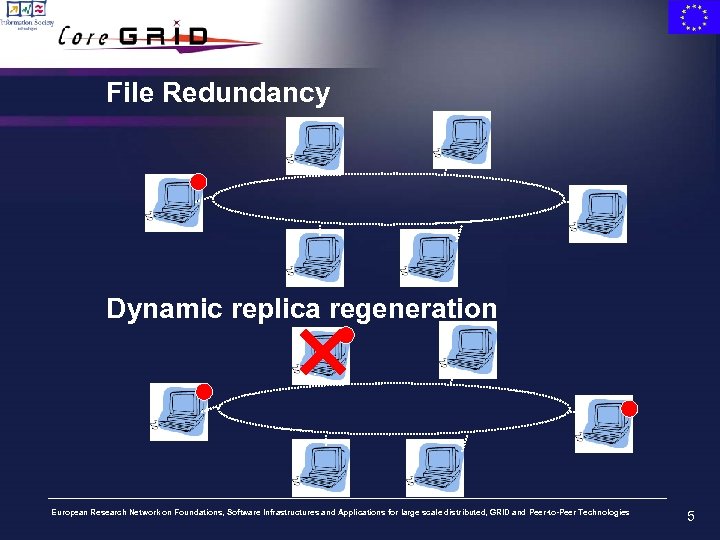 File Redundancy Dynamic replica regeneration European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 5
File Redundancy Dynamic replica regeneration European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 5
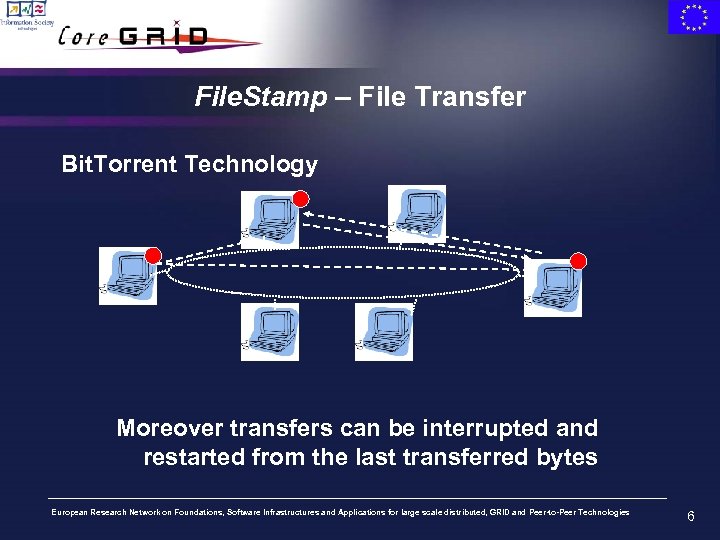 File. Stamp – File Transfer Bit. Torrent Technology Moreover transfers can be interrupted and restarted from the last transferred bytes European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 6
File. Stamp – File Transfer Bit. Torrent Technology Moreover transfers can be interrupted and restarted from the last transferred bytes European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 6
 How to Express Requirements ? Specification language understandable by all the actors European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 7
How to Express Requirements ? Specification language understandable by all the actors European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 7
 KAOS : Knowledge Acquisition in aut. Omated Specification Anti-Goal (Threats) Model Goal Model Responsibility Model Operations Model http: //www. objectiver. com Constraints Model http: //faust. cetic. be Dardenne A. , Lamsweerde A. and Fickas S. , Goal-Directed Requirements Acquisition, Science of Computer Programming Vol. 20, North Holland, 1993, pp. 3 -50. http: //www. info. ucl. ac. be/Research/Publication/1993/SCP. ps. gz Lamsweerde A. , Elaborating Security Requirements by Construction of Intentional Anti-Models, Proceedings of ICSE’ 04, 26 th International Conference on Software Engineering, Edinburgh, May. 2004, ACM-IEEE , pp 148 -157. http: //www. info. ucl. ac. be/Research/Publication/2004/avl-Icse 04 -Anti. Goals. pdf European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 8
KAOS : Knowledge Acquisition in aut. Omated Specification Anti-Goal (Threats) Model Goal Model Responsibility Model Operations Model http: //www. objectiver. com Constraints Model http: //faust. cetic. be Dardenne A. , Lamsweerde A. and Fickas S. , Goal-Directed Requirements Acquisition, Science of Computer Programming Vol. 20, North Holland, 1993, pp. 3 -50. http: //www. info. ucl. ac. be/Research/Publication/1993/SCP. ps. gz Lamsweerde A. , Elaborating Security Requirements by Construction of Intentional Anti-Models, Proceedings of ICSE’ 04, 26 th International Conference on Software Engineering, Edinburgh, May. 2004, ACM-IEEE , pp 148 -157. http: //www. info. ucl. ac. be/Research/Publication/2004/avl-Icse 04 -Anti. Goals. pdf European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 8
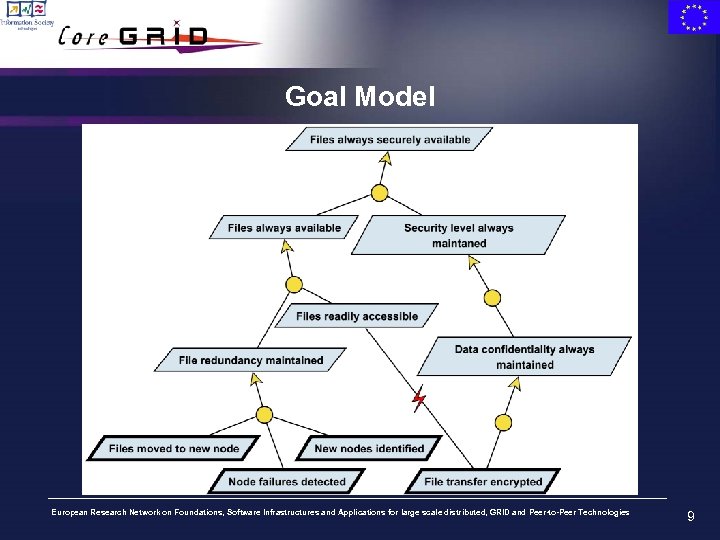 Goal Model European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 9
Goal Model European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 9
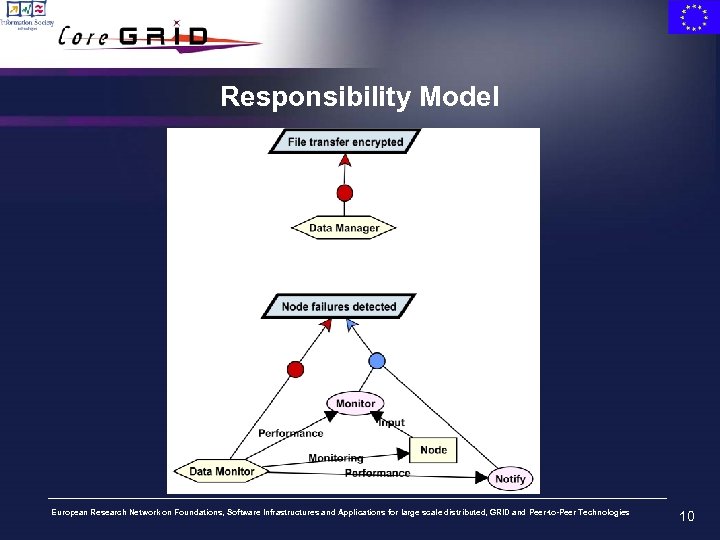 Responsibility Model European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 10
Responsibility Model European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 10
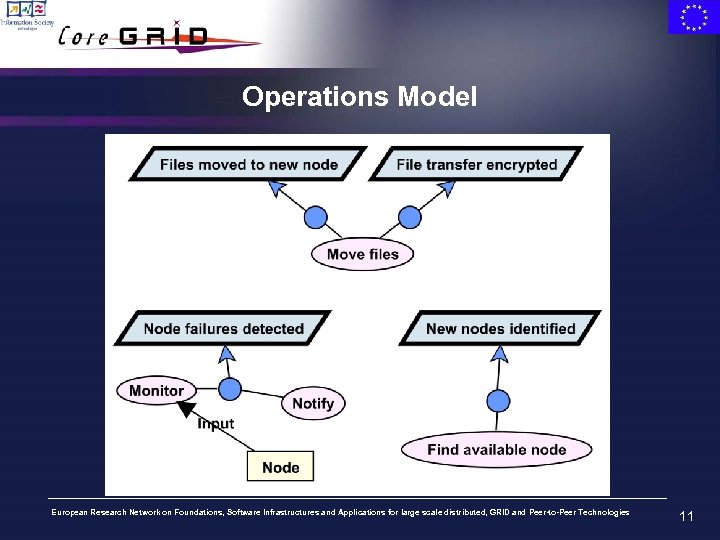 Operations Model European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 11
Operations Model European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 11
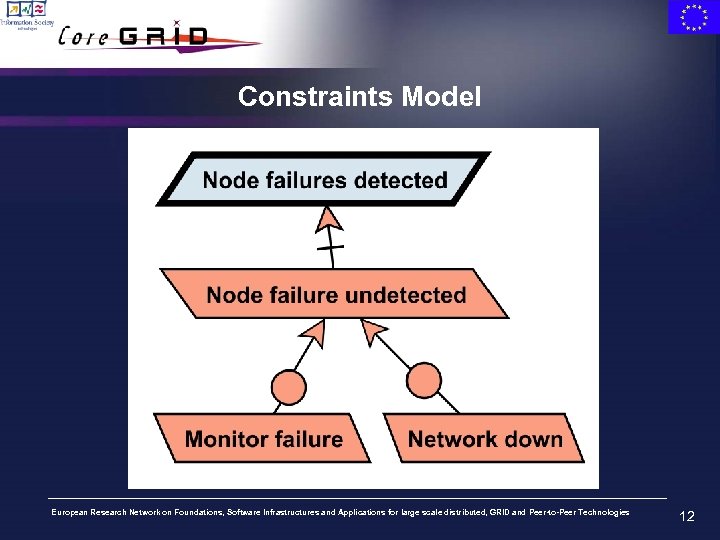 Constraints Model European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 12
Constraints Model European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 12
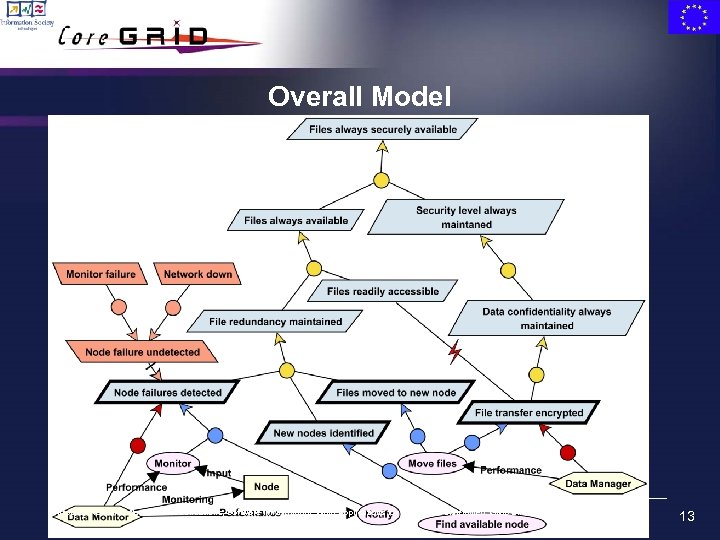 Overall Model European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 13
Overall Model European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 13
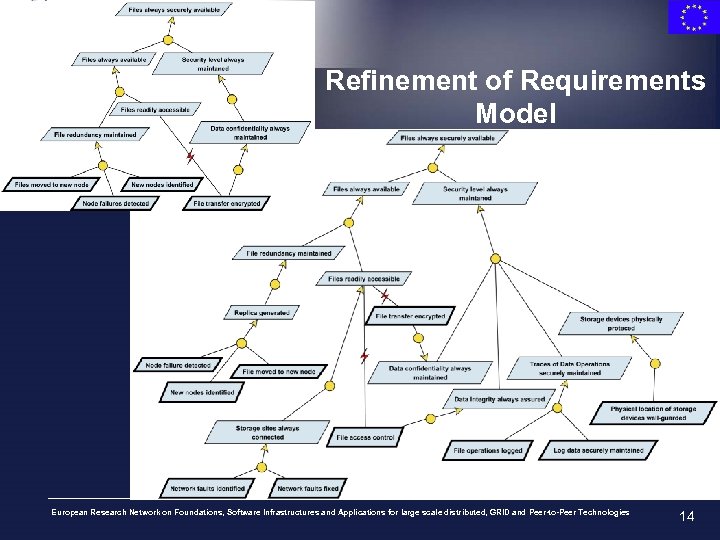 Refinement of Requirements Model European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 14
Refinement of Requirements Model European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 14
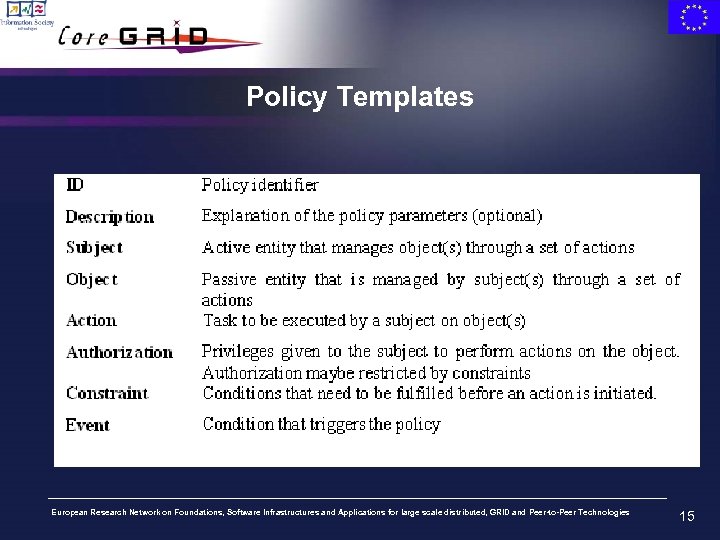 Policy Templates European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 15
Policy Templates European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 15
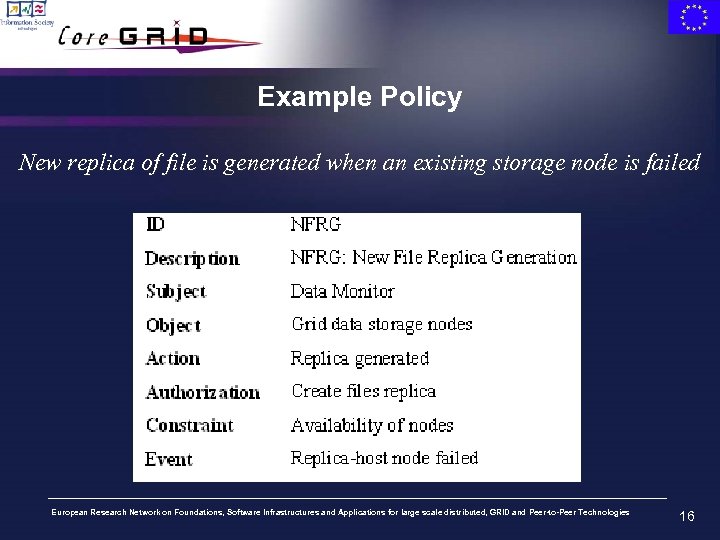 Example Policy New replica of file is generated when an existing storage node is failed European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 16
Example Policy New replica of file is generated when an existing storage node is failed European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 16
 Further Treatment of the Derived Policies • Refinement of High level Policies into Operational Policies – Determination of the resources that are needed to satisfy the requirements of the policy. – Translation of the high-level policies into operational policies that the system can enforce. – Verification that the lower level policies actually meet the requirements specified by the high level policies. • Implementation of Policies – Requires specific details of a particular system. – Formal representation techniques are employed. – Implemented in a specification language. European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 17
Further Treatment of the Derived Policies • Refinement of High level Policies into Operational Policies – Determination of the resources that are needed to satisfy the requirements of the policy. – Translation of the high-level policies into operational policies that the system can enforce. – Verification that the lower level policies actually meet the requirements specified by the high level policies. • Implementation of Policies – Requires specific details of a particular system. – Formal representation techniques are employed. – Implemented in a specification language. European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 17
 Conclusions • This work addresses issues related to formalizing Grid security requirements at the application level. • Our proposed technique is illustrated with the help of a case study of a data management system. • Results shows that formal security requirement models are not only helpful to derive security policies but also they can be employed for security rationale. • Our future directions include: – Refinement of security policies derived from the requirements model. – Work on negotiation protocols to assure service level security agreements. European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 18
Conclusions • This work addresses issues related to formalizing Grid security requirements at the application level. • Our proposed technique is illustrated with the help of a case study of a data management system. • Results shows that formal security requirement models are not only helpful to derive security policies but also they can be employed for security rationale. • Our future directions include: – Refinement of security policies derived from the requirements model. – Work on negotiation protocols to assure service level security agreements. European Research Network on Foundations, Software Infrastructures and Applications for large scale distributed, GRID and Peer-to-Peer Technologies 18


