01bf38678a874a2ffe2f1e2019b01396.ppt
- Количество слайдов: 89
 Forensic Engineering Chapter 18
Forensic Engineering Chapter 18
 Engineering Takes fundamental scientific, economic and practical knowledge and applies this understanding to the design and construction of structures, devices, materials, and processes that directly impact human lives. CHE 113 2
Engineering Takes fundamental scientific, economic and practical knowledge and applies this understanding to the design and construction of structures, devices, materials, and processes that directly impact human lives. CHE 113 2
 Forensic Engineering • In the 19 th century, forensic engineering began to inform courts regarding negligent or intentionally fraudulent building and design practices. • failure analysis • crime scene analysis and reconstruction.
Forensic Engineering • In the 19 th century, forensic engineering began to inform courts regarding negligent or intentionally fraudulent building and design practices. • failure analysis • crime scene analysis and reconstruction.
 Failure Analysis Goals • Determine who was responsible for the failure in order to bring either criminal charges or levy financial damages against them. • Modify specific designs or practices in order to prevent similar failures from happening in the future
Failure Analysis Goals • Determine who was responsible for the failure in order to bring either criminal charges or levy financial damages against them. • Modify specific designs or practices in order to prevent similar failures from happening in the future
 Tacoma Narrows Bridge • Bridge Collapse
Tacoma Narrows Bridge • Bridge Collapse
 Failure Analysis • Sometimes the catastrophic failure of an engineered system is brought about by the failure of just one or several smaller components that make up the entire system.
Failure Analysis • Sometimes the catastrophic failure of an engineered system is brought about by the failure of just one or several smaller components that make up the entire system.
 Space Shuttle Challenger
Space Shuttle Challenger
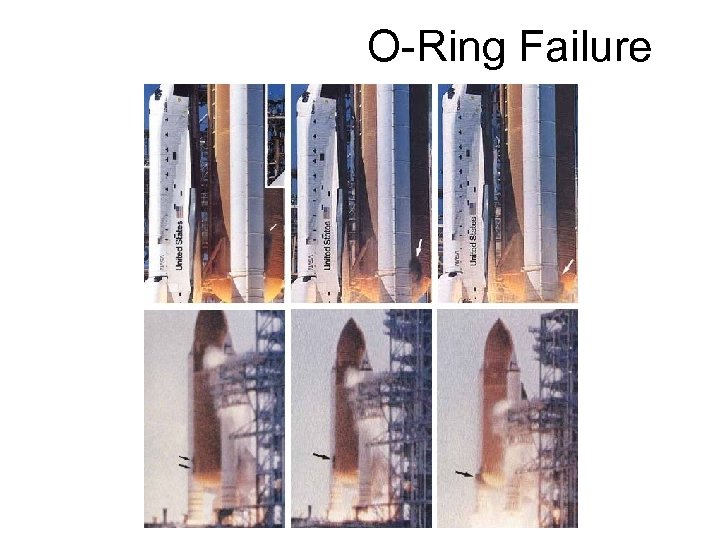 O-Ring Failure
O-Ring Failure

 Failure Analysis Protocol • Get background information (e. g. , blueprints, maintenance logs, legal requirements and standards, etc. ), • Carrying out detailed site investigations, completing computer modeling simulations, • run multidisciplinary laboratory analyses before a reasonable answer is reached
Failure Analysis Protocol • Get background information (e. g. , blueprints, maintenance logs, legal requirements and standards, etc. ), • Carrying out detailed site investigations, completing computer modeling simulations, • run multidisciplinary laboratory analyses before a reasonable answer is reached
 Tree eats car…
Tree eats car…
 Car in the bush…
Car in the bush…
 Truck in house…
Truck in house…
 Vehicle Accidents • Possible cause for single vehicle accidents
Vehicle Accidents • Possible cause for single vehicle accidents
 Possible Reasons 1. 2. 3. 4. 5. 6. 7. 8. *Distraction (Phone, Radio, Bugs…) Drunk Excessive speed with loss of control Slick road surface (unsafe speed, unsafe distance, bald tires) Avoidance of animal, person or other vehicle Brake/Accelerator Confusion Equipment malfunction Asleep
Possible Reasons 1. 2. 3. 4. 5. 6. 7. 8. *Distraction (Phone, Radio, Bugs…) Drunk Excessive speed with loss of control Slick road surface (unsafe speed, unsafe distance, bald tires) Avoidance of animal, person or other vehicle Brake/Accelerator Confusion Equipment malfunction Asleep
 Process Scene • • • Photograph Draw Measure Interview Witnesses Look at vehicle documents Document weather/road conditions
Process Scene • • • Photograph Draw Measure Interview Witnesses Look at vehicle documents Document weather/road conditions
 Skid Marks • Evidence of braking before crash • Friction between road and tire causes burning • Can determine Minimum Traveling Speed preceding accident, site of incident, evidence of avoidance or lack of avoidance
Skid Marks • Evidence of braking before crash • Friction between road and tire causes burning • Can determine Minimum Traveling Speed preceding accident, site of incident, evidence of avoidance or lack of avoidance
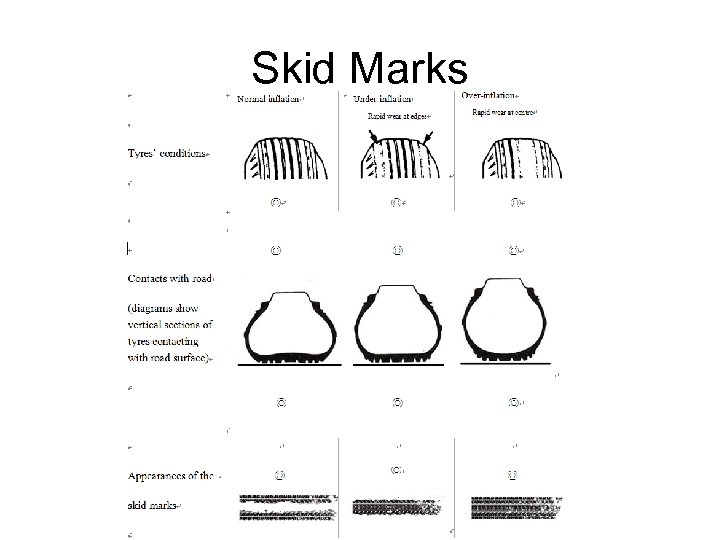 Skid Marks
Skid Marks
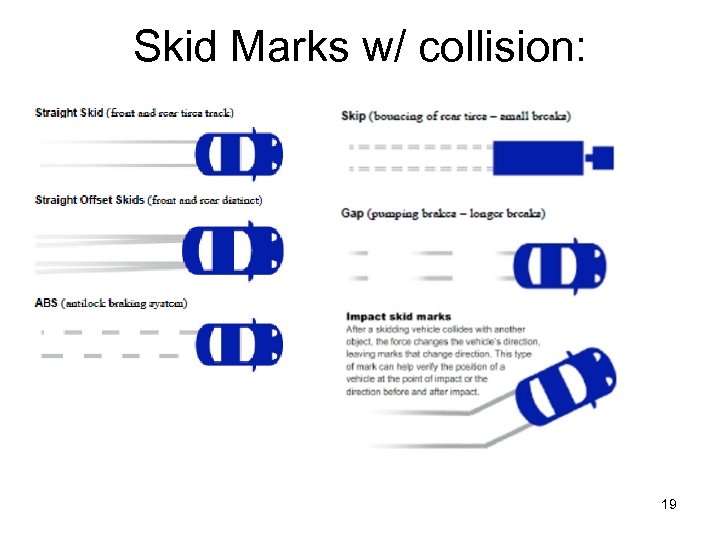 Skid Marks w/ collision: 19
Skid Marks w/ collision: 19
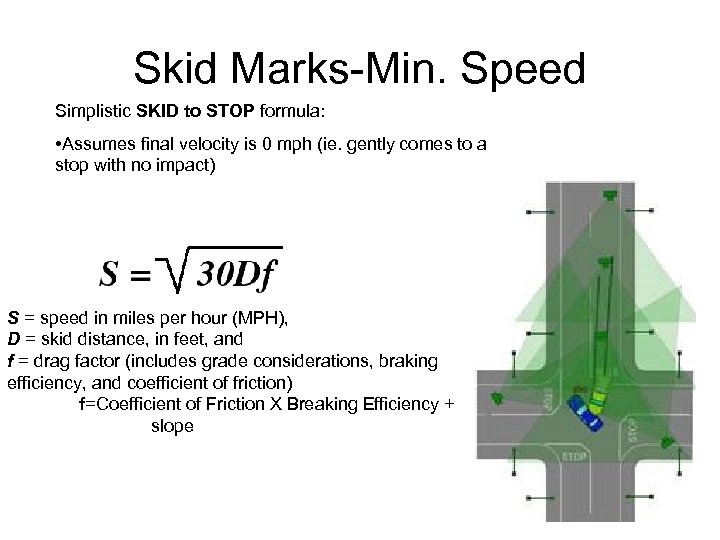 Skid Marks-Min. Speed Simplistic SKID to STOP formula: • Assumes final velocity is 0 mph (ie. gently comes to a stop with no impact) S = speed in miles per hour (MPH), D = skid distance, in feet, and f = drag factor (includes grade considerations, braking efficiency, and coefficient of friction) f=Coefficient of Friction X Breaking Efficiency + slope
Skid Marks-Min. Speed Simplistic SKID to STOP formula: • Assumes final velocity is 0 mph (ie. gently comes to a stop with no impact) S = speed in miles per hour (MPH), D = skid distance, in feet, and f = drag factor (includes grade considerations, braking efficiency, and coefficient of friction) f=Coefficient of Friction X Breaking Efficiency + slope
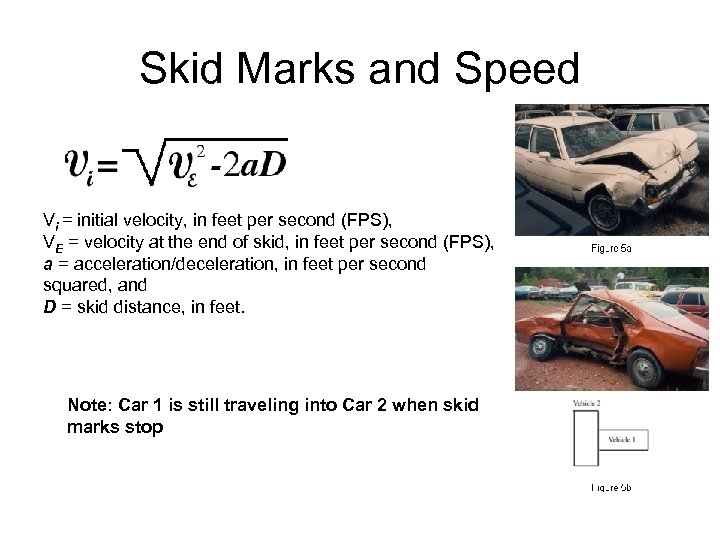 Skid Marks and Speed Vi = initial velocity, in feet per second (FPS), VE = velocity at the end of skid, in feet per second (FPS), a = acceleration/deceleration, in feet per second squared, and D = skid distance, in feet. Note: Car 1 is still traveling into Car 2 when skid marks stop
Skid Marks and Speed Vi = initial velocity, in feet per second (FPS), VE = velocity at the end of skid, in feet per second (FPS), a = acceleration/deceleration, in feet per second squared, and D = skid distance, in feet. Note: Car 1 is still traveling into Car 2 when skid marks stop
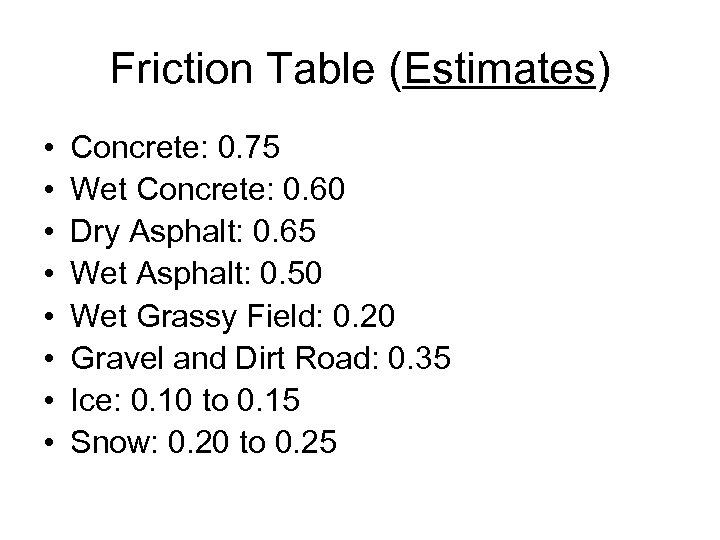 Friction Table (Estimates) • • Concrete: 0. 75 Wet Concrete: 0. 60 Dry Asphalt: 0. 65 Wet Asphalt: 0. 50 Wet Grassy Field: 0. 20 Gravel and Dirt Road: 0. 35 Ice: 0. 10 to 0. 15 Snow: 0. 20 to 0. 25
Friction Table (Estimates) • • Concrete: 0. 75 Wet Concrete: 0. 60 Dry Asphalt: 0. 65 Wet Asphalt: 0. 50 Wet Grassy Field: 0. 20 Gravel and Dirt Road: 0. 35 Ice: 0. 10 to 0. 15 Snow: 0. 20 to 0. 25
 Flaws with Friction Table • Road varies in age, exact construction material, and condition • Subject’s car tire condition important
Flaws with Friction Table • Road varies in age, exact construction material, and condition • Subject’s car tire condition important
 Best ways to determine real coefficient of friction • Optimal use subject car and run at known speed • Create skid marks • Calculate coefficient of friction • Or use a Drag Box
Best ways to determine real coefficient of friction • Optimal use subject car and run at known speed • Create skid marks • Calculate coefficient of friction • Or use a Drag Box
 Determining a surface’s coefficient of friction • Drag Box – Box has weight – Box has tire surface on bottom of box – Measure force to pull box and maintain speed – Coefficient of friction=Avg. pull force/box weight
Determining a surface’s coefficient of friction • Drag Box – Box has weight – Box has tire surface on bottom of box – Measure force to pull box and maintain speed – Coefficient of friction=Avg. pull force/box weight
 What if no skid marks? Explanations….
What if no skid marks? Explanations….
 • Brake malfunction – How do disk brakes work? • • Not watching road Couldn’t see out window Drunk Unconscious
• Brake malfunction – How do disk brakes work? • • Not watching road Couldn’t see out window Drunk Unconscious
 No Skid Marking • Event Data Recorder – Logs pre-crash speed – Logs brake use
No Skid Marking • Event Data Recorder – Logs pre-crash speed – Logs brake use
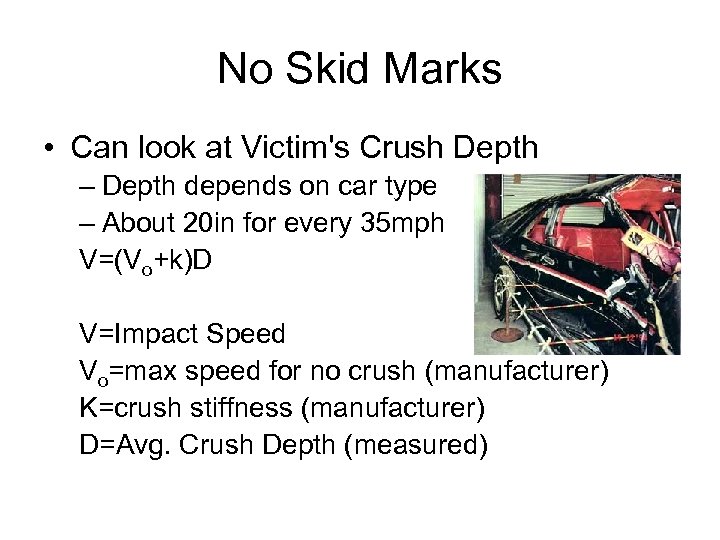 No Skid Marks • Can look at Victim's Crush Depth – Depth depends on car type – About 20 in for every 35 mph V=(Vo+k)D V=Impact Speed Vo=max speed for no crush (manufacturer) K=crush stiffness (manufacturer) D=Avg. Crush Depth (measured)
No Skid Marks • Can look at Victim's Crush Depth – Depth depends on car type – About 20 in for every 35 mph V=(Vo+k)D V=Impact Speed Vo=max speed for no crush (manufacturer) K=crush stiffness (manufacturer) D=Avg. Crush Depth (measured)
 Did Driver signal lane change or have headlights on?
Did Driver signal lane change or have headlights on?
 Brake Lights
Brake Lights
 Lights • • Brake Lights have filament bowed upward This means lights were on at crash Heat and impact causes deformed shape Means that driver braked before crash
Lights • • Brake Lights have filament bowed upward This means lights were on at crash Heat and impact causes deformed shape Means that driver braked before crash
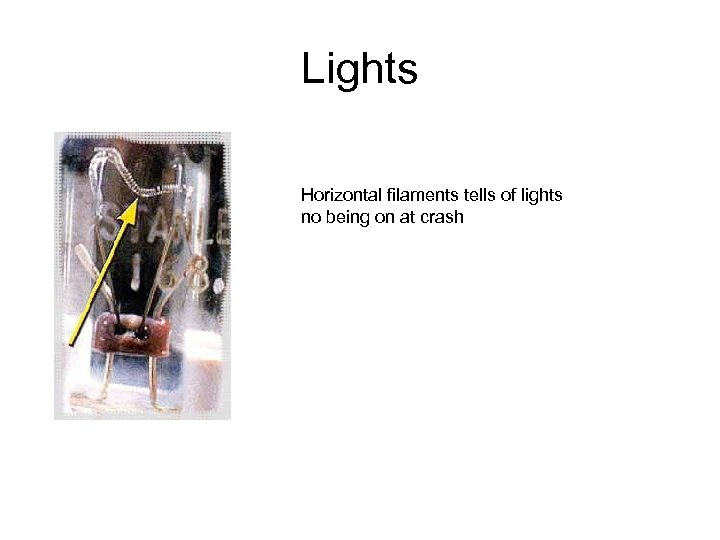 Lights Horizontal filaments tells of lights no being on at crash
Lights Horizontal filaments tells of lights no being on at crash
 Cyber Crime
Cyber Crime
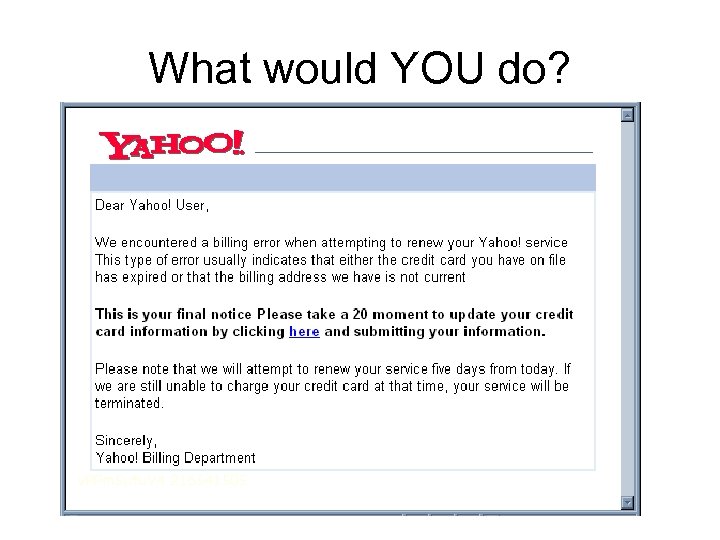 What would YOU do?
What would YOU do?
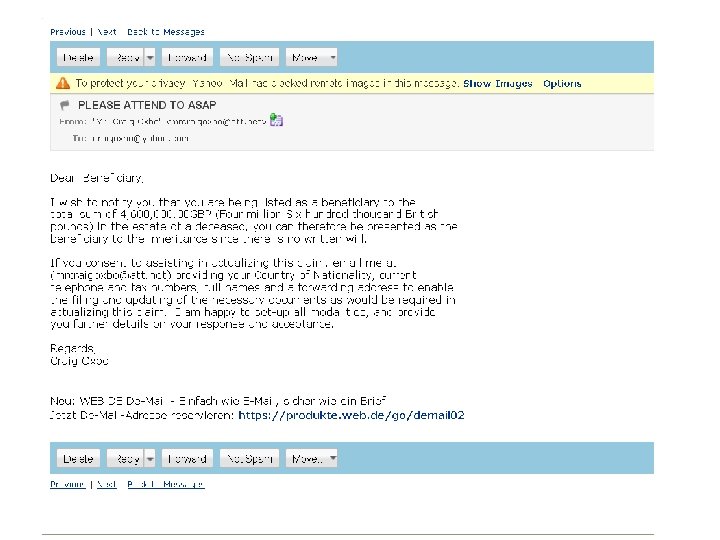
 Dear Customers, Employees, and Friends, During the past week, several of you have relayed to us that you experienced fraudulent activity on your credit cards. Security is paramount to us, and although we NEVER store any credit card data, we launched a vigorous investigation as soon as we were first notified. We have been working around the clock ever since…
Dear Customers, Employees, and Friends, During the past week, several of you have relayed to us that you experienced fraudulent activity on your credit cards. Security is paramount to us, and although we NEVER store any credit card data, we launched a vigorous investigation as soon as we were first notified. We have been working around the clock ever since…

 Computer Forensics • Deals with the identification, preservation, analysis and documentation of digital information derived primarily from computers and their storage media devices
Computer Forensics • Deals with the identification, preservation, analysis and documentation of digital information derived primarily from computers and their storage media devices
 Cyber Crimes • Cyber stalking, bullying, and harassment • Child and other illegal forms of pornography and sexual solicitation • Assault and attack (e. g. , denial of service, destruction of data, computer virus release
Cyber Crimes • Cyber stalking, bullying, and harassment • Child and other illegal forms of pornography and sexual solicitation • Assault and attack (e. g. , denial of service, destruction of data, computer virus release
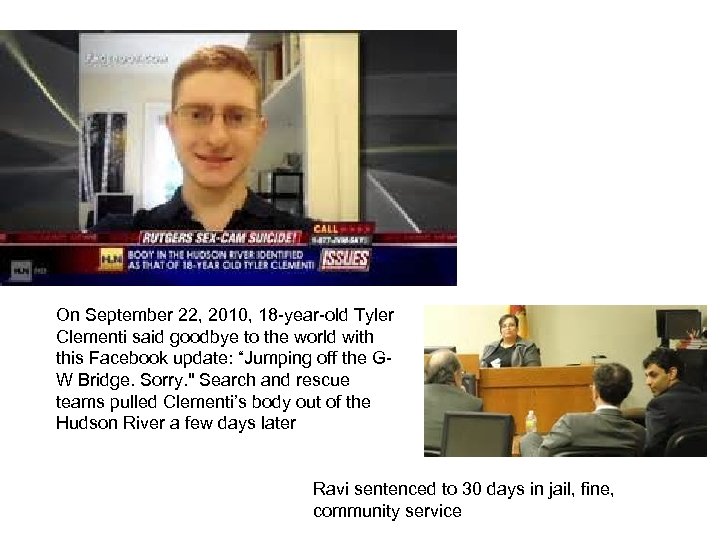 On September 22, 2010, 18 -year-old Tyler Clementi said goodbye to the world with this Facebook update: “Jumping off the GW Bridge. Sorry. " Search and rescue teams pulled Clementi’s body out of the Hudson River a few days later Ravi sentenced to 30 days in jail, fine, community service
On September 22, 2010, 18 -year-old Tyler Clementi said goodbye to the world with this Facebook update: “Jumping off the GW Bridge. Sorry. " Search and rescue teams pulled Clementi’s body out of the Hudson River a few days later Ravi sentenced to 30 days in jail, fine, community service
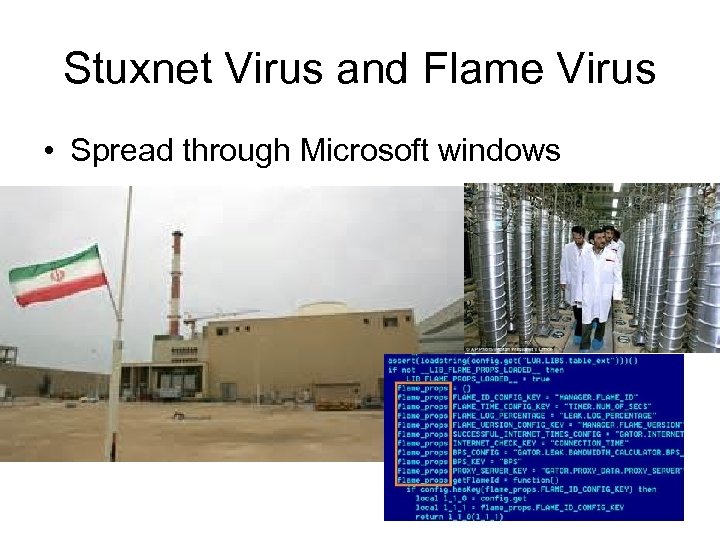 Stuxnet Virus and Flame Virus • Spread through Microsoft windows
Stuxnet Virus and Flame Virus • Spread through Microsoft windows
 Cyber Evidence • Employee internet abuse • Industrial/international espionage • Traditional crime information sources e. g. , drug deal records, money laundering, embezzlement, fraud
Cyber Evidence • Employee internet abuse • Industrial/international espionage • Traditional crime information sources e. g. , drug deal records, money laundering, embezzlement, fraud
 Cyber Tools • Disk imaging software –record both the structure and the contents of a hard drive without changing the hard drive itself. • Hashing tools –compare original hard drives with any copies made – allowing a determination of the copy as an identical match with the original. • File recovery programs –search for particular files and types digital data.
Cyber Tools • Disk imaging software –record both the structure and the contents of a hard drive without changing the hard drive itself. • Hashing tools –compare original hard drives with any copies made – allowing a determination of the copy as an identical match with the original. • File recovery programs –search for particular files and types digital data.
 Cyber Tools • Encryption decoding software – restoring encrypted or password protected data
Cyber Tools • Encryption decoding software – restoring encrypted or password protected data
 CSI for Geeks The wonderful world of digital forensics Mark M. Pollitt, Ph. D. Adjunct Faculty © 2105 Digital Evidence Professional Services, Inc.
CSI for Geeks The wonderful world of digital forensics Mark M. Pollitt, Ph. D. Adjunct Faculty © 2105 Digital Evidence Professional Services, Inc.
 What is Digital Forensics? “The application of science and engineering to the legal problem of digital evidence. ” FBI Definition
What is Digital Forensics? “The application of science and engineering to the legal problem of digital evidence. ” FBI Definition
 Digital Forensics is • Part information technology • Part anthropology – artifacts tell a story • Part literary criticism – what are they saying • Part puzzle – putting disparate pieces together • Part Forensic Science
Digital Forensics is • Part information technology • Part anthropology – artifacts tell a story • Part literary criticism – what are they saying • Part puzzle – putting disparate pieces together • Part Forensic Science
 It isn’t like TV! • • It isn’t quick It isn’t easy Nobody does it all We can’t do all the things you see on TV • We can’t always do it every time • Most of the time the answer is “maybe”
It isn’t like TV! • • It isn’t quick It isn’t easy Nobody does it all We can’t do all the things you see on TV • We can’t always do it every time • Most of the time the answer is “maybe”
 What is digital evidence? Information of probative value (to prove), stored or transmitted in binary form SWGDE Definition
What is digital evidence? Information of probative value (to prove), stored or transmitted in binary form SWGDE Definition
 Sources of Digital Evidence • • • Storage media Computing devices Communications devices Network communications Applications Cloud
Sources of Digital Evidence • • • Storage media Computing devices Communications devices Network communications Applications Cloud
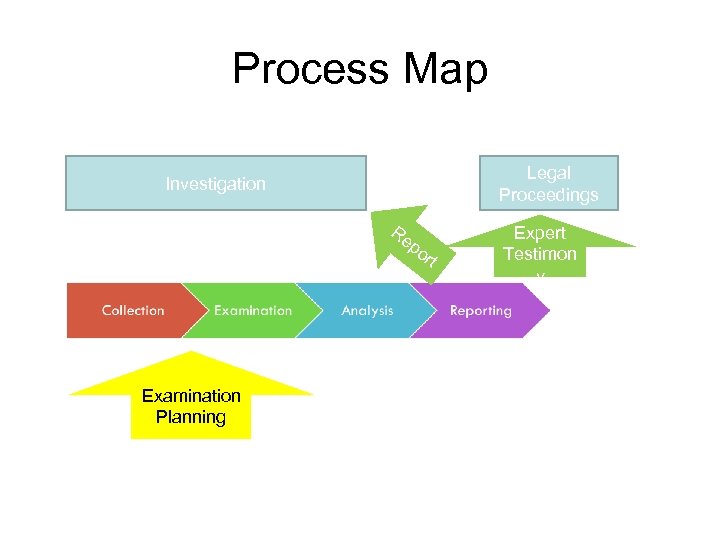 Process Map Legal Proceedings Investigation Taskin g Examination Planning Re po rt Expert Testimon y
Process Map Legal Proceedings Investigation Taskin g Examination Planning Re po rt Expert Testimon y
 Inherent Problems with Data • Size/volume – Terabytes of data (~10 -20 TB = Y 2 K Lib. Of Congress – Computers store 100’s of thousands of files in thousands of file types – Data is simultaneously in multiple contexts • Volatility • Reliability/authentication • Content
Inherent Problems with Data • Size/volume – Terabytes of data (~10 -20 TB = Y 2 K Lib. Of Congress – Computers store 100’s of thousands of files in thousands of file types – Data is simultaneously in multiple contexts • Volatility • Reliability/authentication • Content
 Contexts Information Systems Context • User • Computer • Application • Operating System • File • Storage Media • Network (inc. NAS) • Physical Media Investigative Context Who What When Where Why How
Contexts Information Systems Context • User • Computer • Application • Operating System • File • Storage Media • Network (inc. NAS) • Physical Media Investigative Context Who What When Where Why How
 The Problem is… • The questions are not data-centric • The data is not organized in a thematic, chronological, or topical way • In short, we are not asking numeric questions of a Grisham novel or medieval manuscript.
The Problem is… • The questions are not data-centric • The data is not organized in a thematic, chronological, or topical way • In short, we are not asking numeric questions of a Grisham novel or medieval manuscript.
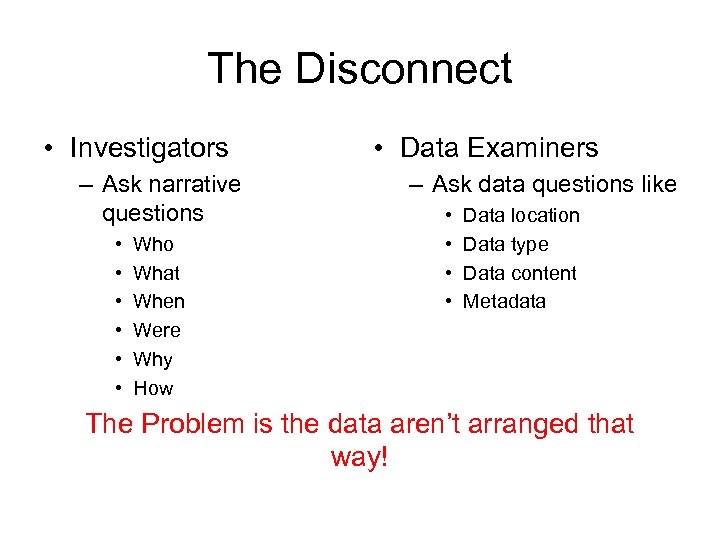 The Disconnect • Investigators – Ask narrative questions • • • Who What When Were Why How • Data Examiners – Ask data questions like • • Data location Data type Data content Metadata The Problem is the data aren’t arranged that way!
The Disconnect • Investigators – Ask narrative questions • • • Who What When Were Why How • Data Examiners – Ask data questions like • • Data location Data type Data content Metadata The Problem is the data aren’t arranged that way!
 Hard drives are huge anthologies Containing millions of “short Stories” The problem is parsing them!
Hard drives are huge anthologies Containing millions of “short Stories” The problem is parsing them!
 Stories, aka Narratives • Are found in: – – – Email Documents Photos Videos Web connections Web 2. 0 artifacts • Narratives can be: – – – Descriptive Persuasive Disorganized Unedited Directive graphic
Stories, aka Narratives • Are found in: – – – Email Documents Photos Videos Web connections Web 2. 0 artifacts • Narratives can be: – – – Descriptive Persuasive Disorganized Unedited Directive graphic
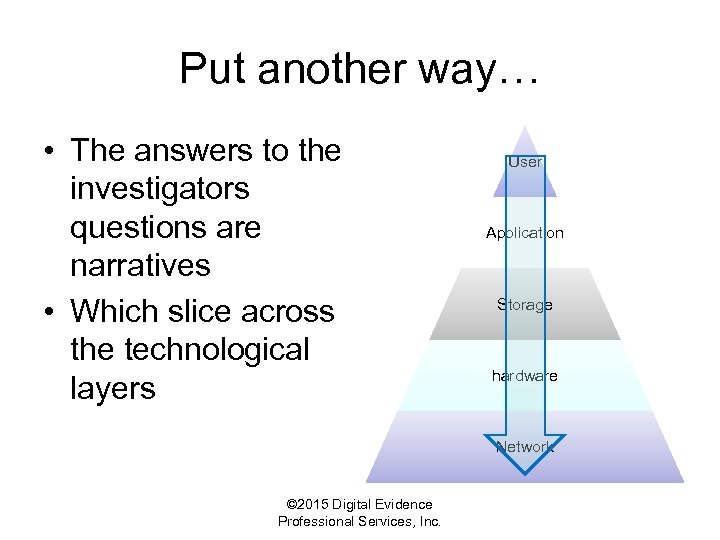 Put another way… • The answers to the investigators questions are narratives • Which slice across the technological layers User Application Storage hardware Network © 2015 Digital Evidence Professional Services, Inc.
Put another way… • The answers to the investigators questions are narratives • Which slice across the technological layers User Application Storage hardware Network © 2015 Digital Evidence Professional Services, Inc.
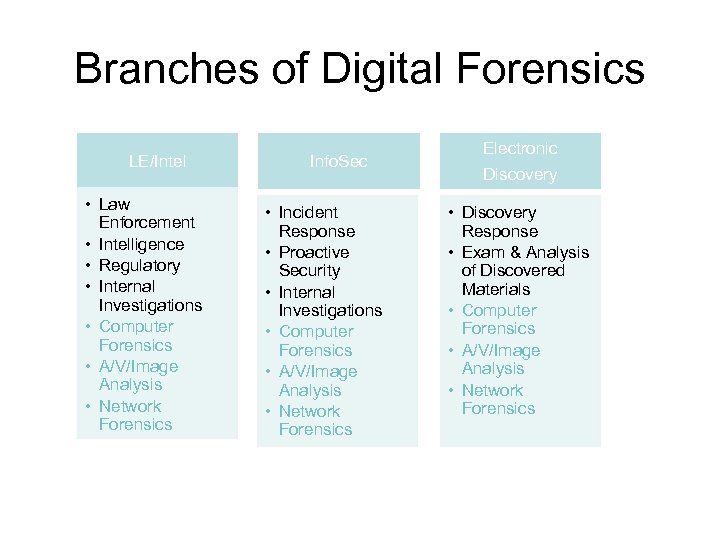 Branches of Digital Forensics LE/Intel • Law Enforcement • Intelligence • Regulatory • Internal Investigations • Computer Forensics • A/V/Image Analysis • Network Forensics Info. Sec • Incident Response • Proactive Security • Internal Investigations • Computer Forensics • A/V/Image Analysis • Network Forensics Electronic Discovery • Discovery Response • Exam & Analysis of Discovered Materials • Computer Forensics • A/V/Image Analysis • Network Forensics
Branches of Digital Forensics LE/Intel • Law Enforcement • Intelligence • Regulatory • Internal Investigations • Computer Forensics • A/V/Image Analysis • Network Forensics Info. Sec • Incident Response • Proactive Security • Internal Investigations • Computer Forensics • A/V/Image Analysis • Network Forensics Electronic Discovery • Discovery Response • Exam & Analysis of Discovered Materials • Computer Forensics • A/V/Image Analysis • Network Forensics
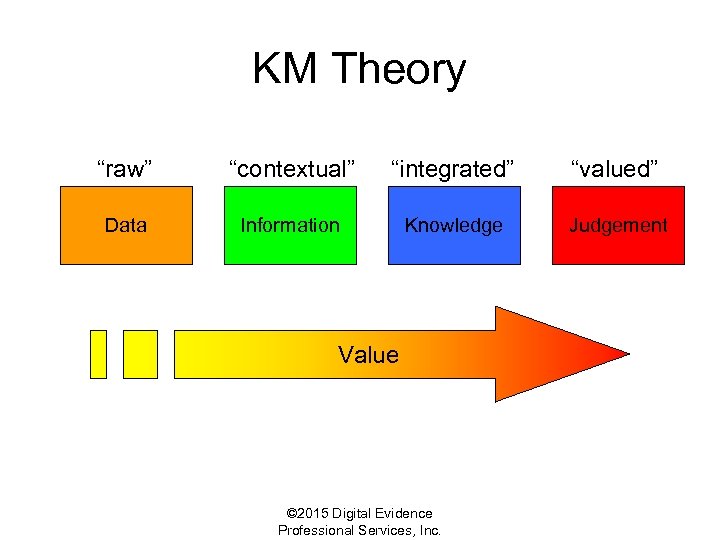 KM Theory “raw” “contextual” “integrated” “valued” Data Information Knowledge Judgement Value © 2015 Digital Evidence Professional Services, Inc.
KM Theory “raw” “contextual” “integrated” “valued” Data Information Knowledge Judgement Value © 2015 Digital Evidence Professional Services, Inc.
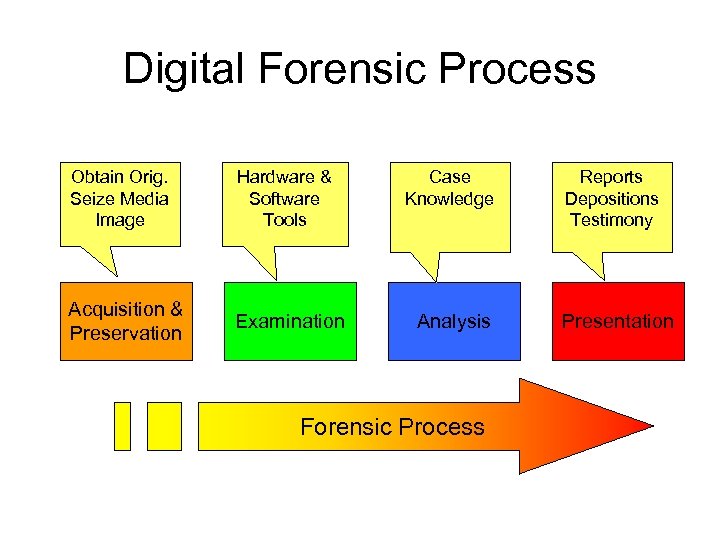 Digital Forensic Process Obtain Orig. Seize Media Image Hardware & Software Tools Case Knowledge Acquisition & Preservation Examination Analysis Forensic Process Reports Depositions Testimony Presentation
Digital Forensic Process Obtain Orig. Seize Media Image Hardware & Software Tools Case Knowledge Acquisition & Preservation Examination Analysis Forensic Process Reports Depositions Testimony Presentation
 It starts with the legal right to collect information • In a governmental (LE & Intel), it requires a form of legal authority (search warrant, court order, consent, etc. • In the private sector it is part law and part ethics. • In Electronic Discovery, it is procedural law. • No data should be collected without clear authority.
It starts with the legal right to collect information • In a governmental (LE & Intel), it requires a form of legal authority (search warrant, court order, consent, etc. • In the private sector it is part law and part ethics. • In Electronic Discovery, it is procedural law. • No data should be collected without clear authority.
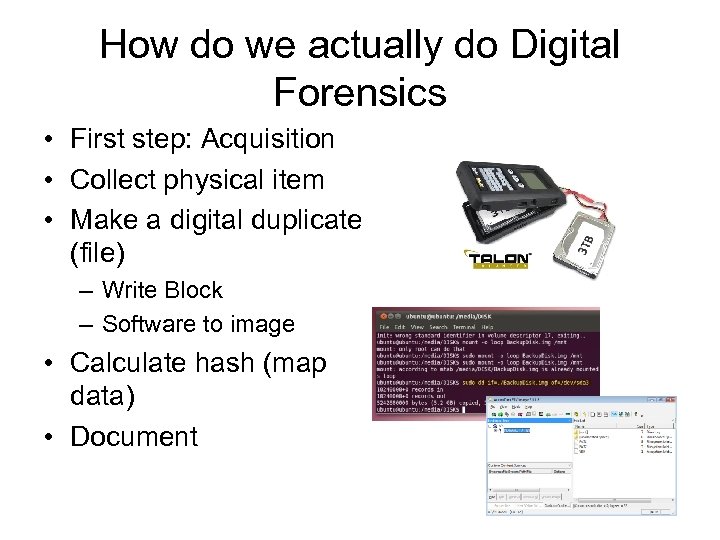 How do we actually do Digital Forensics • First step: Acquisition • Collect physical item • Make a digital duplicate (file) – Write Block – Software to image • Calculate hash (map data) • Document
How do we actually do Digital Forensics • First step: Acquisition • Collect physical item • Make a digital duplicate (file) – Write Block – Software to image • Calculate hash (map data) • Document
 Hashing – for authentication and reliability • Suite Tools (En. Case, FTK, Pro. Discover, etc. ) have hashing built in • Command line Tools
Hashing – for authentication and reliability • Suite Tools (En. Case, FTK, Pro. Discover, etc. ) have hashing built in • Command line Tools
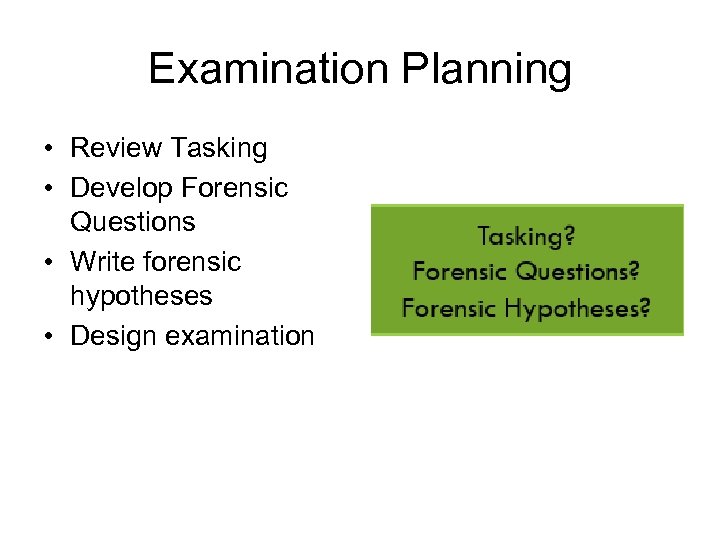 Examination Planning • Review Tasking • Develop Forensic Questions • Write forensic hypotheses • Design examination
Examination Planning • Review Tasking • Develop Forensic Questions • Write forensic hypotheses • Design examination
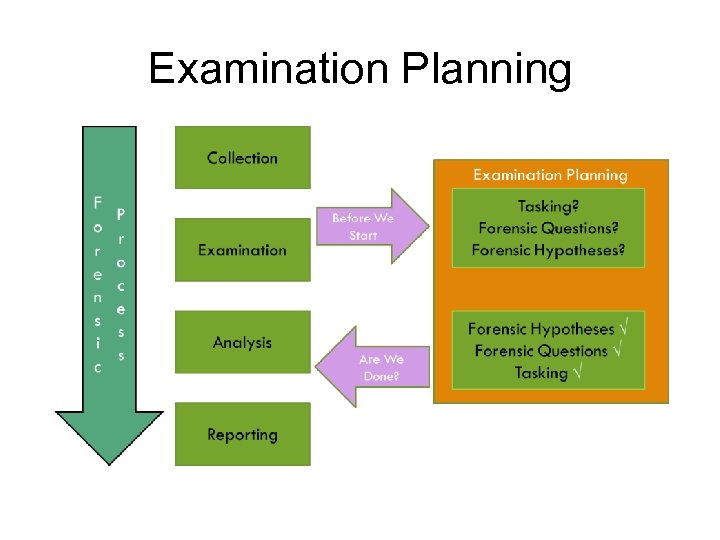 Examination Planning
Examination Planning
 Examination • Mount evidence • Document evidence • Recover data – Deleted – Unallocated – File fragments – carving • Search & extract • Command line or GUI
Examination • Mount evidence • Document evidence • Recover data – Deleted – Unallocated – File fragments – carving • Search & extract • Command line or GUI
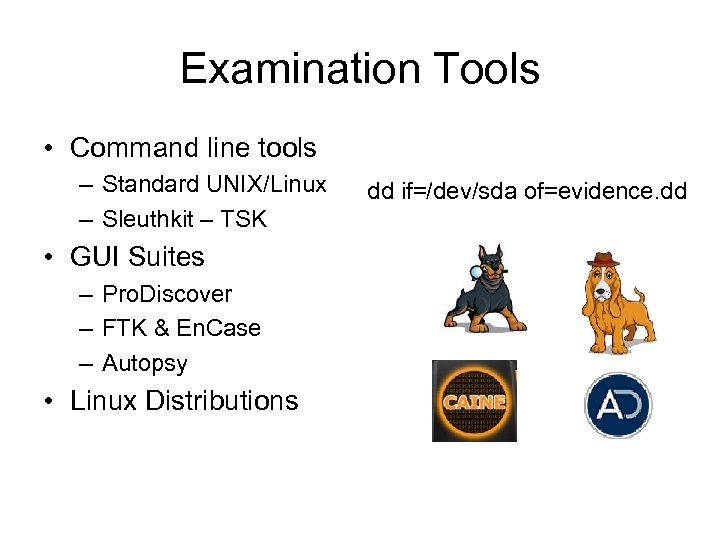 Examination Tools • Command line tools – Standard UNIX/Linux – Sleuthkit – TSK • GUI Suites – Pro. Discover – FTK & En. Case – Autopsy • Linux Distributions dd if=/dev/sda of=evidence. dd
Examination Tools • Command line tools – Standard UNIX/Linux – Sleuthkit – TSK • GUI Suites – Pro. Discover – FTK & En. Case – Autopsy • Linux Distributions dd if=/dev/sda of=evidence. dd
 Analysis • Analysis is taking the data recovered in the examination phase and answering questions: – Forensic Questions • • Identification Classification/individualization Association Reconstruction – Investigative Questions • Who, What, When, Where, Why, and How?
Analysis • Analysis is taking the data recovered in the examination phase and answering questions: – Forensic Questions • • Identification Classification/individualization Association Reconstruction – Investigative Questions • Who, What, When, Where, Why, and How?
 Analysis Continued • The analysis process is all about critical thinking • Selecting pertinent information – Classifying, refining, evaluating • Organizing information – Timelines, narratives, visualization, simulating • There aren’t really tools for this!
Analysis Continued • The analysis process is all about critical thinking • Selecting pertinent information – Classifying, refining, evaluating • Organizing information – Timelines, narratives, visualization, simulating • There aren’t really tools for this!
 Reporting & Testimony • Examiners write – A LOT! – Extensive, contemporaneous Notes – Reports – vary by organization – Provide oral briefings – Testify as expert witnesses • Teaching on the stand • Offer opinion and conclusion testimony
Reporting & Testimony • Examiners write – A LOT! – Extensive, contemporaneous Notes – Reports – vary by organization – Provide oral briefings – Testify as expert witnesses • Teaching on the stand • Offer opinion and conclusion testimony
 And if that wasn’t enough… • Everything is done under a quality management system – Standard Operating Procedures – Peer Reviews – Audits – Proficiency tests – Certification – Accreditation
And if that wasn’t enough… • Everything is done under a quality management system – Standard Operating Procedures – Peer Reviews – Audits – Proficiency tests – Certification – Accreditation
 Acquisition Teaching Modalities • Usually scenario based – Artificial or reality based • Evidence can: – Support scenario or refute it – Simple or complex (caution: it is always more complex than you think) • Think, Plan, Do – In that order!
Acquisition Teaching Modalities • Usually scenario based – Artificial or reality based • Evidence can: – Support scenario or refute it – Simple or complex (caution: it is always more complex than you think) • Think, Plan, Do – In that order!
 Virtualization • Dedicated hardware is nice, but not practical • Using virtual machines are the best and easiest way to ensure that the environment is controlled • Vmware and Virtual Box are the two main packages. • Vmware Player and Virtual Box are free http: //www. vmware. com https: //www. virtualbox. org/
Virtualization • Dedicated hardware is nice, but not practical • Using virtual machines are the best and easiest way to ensure that the environment is controlled • Vmware and Virtual Box are the two main packages. • Vmware Player and Virtual Box are free http: //www. vmware. com https: //www. virtualbox. org/
 Creating Evidence for Acquisition • Small, simple media e. g. : SD cards, USB drives – Start collecting a “stash” of old, small devices • ALWAYS wipe the media before “planting” the evidence • Plant using a clean, recently booted computer • Create an image and a hash • Test, test
Creating Evidence for Acquisition • Small, simple media e. g. : SD cards, USB drives – Start collecting a “stash” of old, small devices • ALWAYS wipe the media before “planting” the evidence • Plant using a clean, recently booted computer • Create an image and a hash • Test, test
 Imaging • Can use various tools – DD, DCFLDD – FTK Imager/Lite – Bootable CD/USB • Verify hash of original matches image file evidence. dd
Imaging • Can use various tools – DD, DCFLDD – FTK Imager/Lite – Bootable CD/USB • Verify hash of original matches image file evidence. dd
 Examination • Command line tools – Mostly Linux-based • Hex Editor – Win. Hex • Semi-suite – The Sleuthkit • Suites – Autopsy – FTK – Pro Discover • Bootable Linux distros – – – Caine Deft/Deft Zero Santoku Sift Kali – pen testing focus
Examination • Command line tools – Mostly Linux-based • Hex Editor – Win. Hex • Semi-suite – The Sleuthkit • Suites – Autopsy – FTK – Pro Discover • Bootable Linux distros – – – Caine Deft/Deft Zero Santoku Sift Kali – pen testing focus
 Network & Mobile Devices • Network Forensics is very “techy” • You MUST use a dedicated, isolated network – NEVER do this on a live network • Tools like Wire Shark are useful • Mobile devices, such as smartphones and tablets are the latest challenge • Very technical, tricky to set up and potential for “bricking” the device • Only for advanced instructors/students
Network & Mobile Devices • Network Forensics is very “techy” • You MUST use a dedicated, isolated network – NEVER do this on a live network • Tools like Wire Shark are useful • Mobile devices, such as smartphones and tablets are the latest challenge • Very technical, tricky to set up and potential for “bricking” the device • Only for advanced instructors/students
 Analysis • While suites typically allow “bookmarking”, it is often better to export data to analyze with other programs • Excel is a very powerful tool for this. • TSK and Autopsy offer timeline analysis • Good analysis is intellectually challenging • It’s about Knowledge Management
Analysis • While suites typically allow “bookmarking”, it is often better to export data to analyze with other programs • Excel is a very powerful tool for this. • TSK and Autopsy offer timeline analysis • Good analysis is intellectually challenging • It’s about Knowledge Management
 Reporting • Writing can serve several purposes – Notes are contemporaneous and can be used both for resource material for report writing, but can also be “learning by writing” – sort of journaling – Reports can be used both for presentation and for pedagogy • By defining a structure that forces a logical approach and completeness, students can become better thinkers and writers
Reporting • Writing can serve several purposes – Notes are contemporaneous and can be used both for resource material for report writing, but can also be “learning by writing” – sort of journaling – Reports can be used both for presentation and for pedagogy • By defining a structure that forces a logical approach and completeness, students can become better thinkers and writers
 Example Report Format • Tasking • Forensic Questions – – • • Identification Classification/individualization Association Reconstruction Steps Taken Results Conclusions Opinions
Example Report Format • Tasking • Forensic Questions – – • • Identification Classification/individualization Association Reconstruction Steps Taken Results Conclusions Opinions
 Books • Nelson – Guide to Computer Forensics & Investigations • Altheide – Digital Forensics with Open Source Tools • Carrier - File System Forensic Analysis
Books • Nelson – Guide to Computer Forensics & Investigations • Altheide – Digital Forensics with Open Source Tools • Carrier - File System Forensic Analysis
 Advanced Cyberforensics Education Consortium - ACE http: //www. cyberace. org
Advanced Cyberforensics Education Consortium - ACE http: //www. cyberace. org
 U. S. Digital Forensics Challenge http: //www. usdfc. org/
U. S. Digital Forensics Challenge http: //www. usdfc. org/
 Cyberpatriot
Cyberpatriot
 Software Links • Forensic Linux Distros – https: //www. kali. org/ – http: //www. deftlinux. net/ – http: //www. caine-live. net/ – https: //santoku-linux. com/ • Sleuthkit & Autopsyhttp: //www. sleuthkit. org/
Software Links • Forensic Linux Distros – https: //www. kali. org/ – http: //www. deftlinux. net/ – http: //www. caine-live. net/ – https: //santoku-linux. com/ • Sleuthkit & Autopsyhttp: //www. sleuthkit. org/
 Additional Resource links • • Forensic Wiki http: //forensicswiki. org Virtual Box https: //www. virtualbox. org/ Microsoft Sysinternals Pro. Discover Access Data FTK, Registry Viewer, Imager Guidance Software Fire. Eye - Mandiant https: //www. fireeye. com/services/freeware. ht ml
Additional Resource links • • Forensic Wiki http: //forensicswiki. org Virtual Box https: //www. virtualbox. org/ Microsoft Sysinternals Pro. Discover Access Data FTK, Registry Viewer, Imager Guidance Software Fire. Eye - Mandiant https: //www. fireeye. com/services/freeware. ht ml
 Thanks for all you do as teachers! Mark M. Pollitt, Ph. D. Adjunct Faculty i. School, Syracuse University mmpollit@syr. edu
Thanks for all you do as teachers! Mark M. Pollitt, Ph. D. Adjunct Faculty i. School, Syracuse University mmpollit@syr. edu


