fc4c9769f105318398e6dc4afafa2773.ppt
- Количество слайдов: 31
 Foiling JD: Top 10 Ways to Stop Hackers David Le. Blanc Eric Schultze Microsoft Corporation
Foiling JD: Top 10 Ways to Stop Hackers David Le. Blanc Eric Schultze Microsoft Corporation
 Introduction n Practice Defense in Depth A well-configured server will often resist even newly found vulnerabilities Example – the NT 4. 0 system set up for Eweek’s first Open. Hack contest would have remained secure against most new attacks found over the next year
Introduction n Practice Defense in Depth A well-configured server will often resist even newly found vulnerabilities Example – the NT 4. 0 system set up for Eweek’s first Open. Hack contest would have remained secure against most new attacks found over the next year
 10. Secure Your Email client n Outlook n n Outlook Express n n n Apply the Outlook Security Update Move OE to Restricted Sites Zone Disable Active Scripting and Java Don’t read e-mail on a web server!
10. Secure Your Email client n Outlook n n Outlook Express n n n Apply the Outlook Security Update Move OE to Restricted Sites Zone Disable Active Scripting and Java Don’t read e-mail on a web server!
 9. Restrict Anonymous n Set Restrict. Anonymous=2 n n n This blocks detailed enumeration of users and groups over a variety of protocols (setting included in Hi. Sec* templates) Do not allow system with RA=2 to become master browser
9. Restrict Anonymous n Set Restrict. Anonymous=2 n n n This blocks detailed enumeration of users and groups over a variety of protocols (setting included in Hi. Sec* templates) Do not allow system with RA=2 to become master browser
 8. ACL System Executables n Remove ability for users to execute system commands (cmd. exe, tftp. exe, etc. ) n C: winnt (and subdirectories) n n Dir *. exe /s /b > outfile. txt Cacl *. exe files as such: n n Admins: Full System: Full
8. ACL System Executables n Remove ability for users to execute system commands (cmd. exe, tftp. exe, etc. ) n C: winnt (and subdirectories) n n Dir *. exe /s /b > outfile. txt Cacl *. exe files as such: n n Admins: Full System: Full
 7. ACL Directories n Remove permissions for IUSR, IWAM, and Everyone to Write and Execute files in all directories n n n Dump directory list to file Run cacls against each directory Identify each entry with Everyone perms n n n Read/Execute Write Reset perms as follows:
7. ACL Directories n Remove permissions for IUSR, IWAM, and Everyone to Write and Execute files in all directories n n n Dump directory list to file Run cacls against each directory Identify each entry with Everyone perms n n n Read/Execute Write Reset perms as follows:
 7. ACL Directories Inetpub Everyone: (OI)(CI)F Set to admins: F, everyone: R ---------------------------------------Documents and SettingsAll UsersDRM Everyone: (OI)(CI)F Set to everyone: R ---------------------------------------Documents and SettingsAll UsersApplication DataMicrosoftHTML Help Everyone: F Documents and SettingsAll UsersApplication DataMicrosoftHTML Help Everyone: (OI)(CI)(IO)F Set to everyone: R ---------------------------------------Documents and SettingsAll UsersApplication DataMicrosoftCryptoRSAMachine. Keys Everyone: (special access: ) READ_CONTROL SYNCHRONIZE FILE_GENERIC_READ FILE_GENERIC_WRITE FILE_READ_DATA FILE_WRITE_DATA FILE_APPEND_DATA FILE_READ_EA FILE_WRITE_EA FILE_READ_ATTRIBUTES FILE_WRITE_ATTRIBUTES Remove FILE_GENERIC_WRITE FILE_WRITE_DATA ---------------------------------------
7. ACL Directories Inetpub Everyone: (OI)(CI)F Set to admins: F, everyone: R ---------------------------------------Documents and SettingsAll UsersDRM Everyone: (OI)(CI)F Set to everyone: R ---------------------------------------Documents and SettingsAll UsersApplication DataMicrosoftHTML Help Everyone: F Documents and SettingsAll UsersApplication DataMicrosoftHTML Help Everyone: (OI)(CI)(IO)F Set to everyone: R ---------------------------------------Documents and SettingsAll UsersApplication DataMicrosoftCryptoRSAMachine. Keys Everyone: (special access: ) READ_CONTROL SYNCHRONIZE FILE_GENERIC_READ FILE_GENERIC_WRITE FILE_READ_DATA FILE_WRITE_DATA FILE_APPEND_DATA FILE_READ_EA FILE_WRITE_EA FILE_READ_ATTRIBUTES FILE_WRITE_ATTRIBUTES Remove FILE_GENERIC_WRITE FILE_WRITE_DATA ---------------------------------------
 7. ACL Directories InetpubAdmin. Scripts Everyone: (OI)(CI)F Inherited permissions from Inetpub ---------------------------------------Inetpubmailroot Everyone: (OI)(CI)F InetpubmailrootBadmail Everyone: (OI)(CI)F InetpubmailrootDrop Everyone: (OI)(CI)F InetpubmailrootMailbox Everyone: (OI)(CI)F InetpubmailrootPickup Everyone: (OI)(CI)F InetpubmailrootQueue Everyone: (OI)(CI)F InetpubmailrootRoute Everyone: (OI)(CI)F InetpubmailrootSort. Temp Everyone: (OI)(CI)F Inherited permissions from Inetpub ---------------------------------------
7. ACL Directories InetpubAdmin. Scripts Everyone: (OI)(CI)F Inherited permissions from Inetpub ---------------------------------------Inetpubmailroot Everyone: (OI)(CI)F InetpubmailrootBadmail Everyone: (OI)(CI)F InetpubmailrootDrop Everyone: (OI)(CI)F InetpubmailrootMailbox Everyone: (OI)(CI)F InetpubmailrootPickup Everyone: (OI)(CI)F InetpubmailrootQueue Everyone: (OI)(CI)F InetpubmailrootRoute Everyone: (OI)(CI)F InetpubmailrootSort. Temp Everyone: (OI)(CI)F Inherited permissions from Inetpub ---------------------------------------
 7. ACL Directories WINNTTasks Everyone: (OI)(CI)(special access: ) READ_CONTROL SYNCHRONIZE FILE_GENERIC_READ FILE_GENERIC_WRITE FILE_GENERIC_EXECUTE FILE_READ_DATA FILE_WRITE_DATA FILE_APPEND_DATA FILE_READ_EA FILE_WRITE_EA FILE_EXECUTE FILE_READ_ATTRIBUTES FILE_WRITE_ATTRIBUTES WINNTsystem 32Setup Everyone: (OI)(CI)F Set to admins: F, everyone: R ---------------------------------------WINNTsystem 32inetsrvData Everyone: F Set to everyone: R ---------------------------------------WINNTsystem 32MicrosoftCryptoRSAMachine. Keys Everyone: (special access: ) Set to everyone: R
7. ACL Directories WINNTTasks Everyone: (OI)(CI)(special access: ) READ_CONTROL SYNCHRONIZE FILE_GENERIC_READ FILE_GENERIC_WRITE FILE_GENERIC_EXECUTE FILE_READ_DATA FILE_WRITE_DATA FILE_APPEND_DATA FILE_READ_EA FILE_WRITE_EA FILE_EXECUTE FILE_READ_ATTRIBUTES FILE_WRITE_ATTRIBUTES WINNTsystem 32Setup Everyone: (OI)(CI)F Set to admins: F, everyone: R ---------------------------------------WINNTsystem 32inetsrvData Everyone: F Set to everyone: R ---------------------------------------WINNTsystem 32MicrosoftCryptoRSAMachine. Keys Everyone: (special access: ) Set to everyone: R
 6. Disable Services n n n Alerter Computer Browser Indexing Service Messenger Print spooler Remote Registry Distributed File System Workstation Server Telnet Smtp
6. Disable Services n n n Alerter Computer Browser Indexing Service Messenger Print spooler Remote Registry Distributed File System Workstation Server Telnet Smtp
 5. Filter Ports 42 80 88 135 139 389 443 445 464 593 636 3268 3269 3372 3389 xxxx WINS Host Name Server HTTP Kerberos MS RPC Net. BIOS Session Service LDAP SSL CIFS-SMB kpasswd HTTP endpoint mapper SSL-ldap MS Global Catalog (Local-host only connection) MS Terminal Server IIS 5. 0 HTML Mgmt
5. Filter Ports 42 80 88 135 139 389 443 445 464 593 636 3268 3269 3372 3389 xxxx WINS Host Name Server HTTP Kerberos MS RPC Net. BIOS Session Service LDAP SSL CIFS-SMB kpasswd HTTP endpoint mapper SSL-ldap MS Global Catalog (Local-host only connection) MS Terminal Server IIS 5. 0 HTML Mgmt
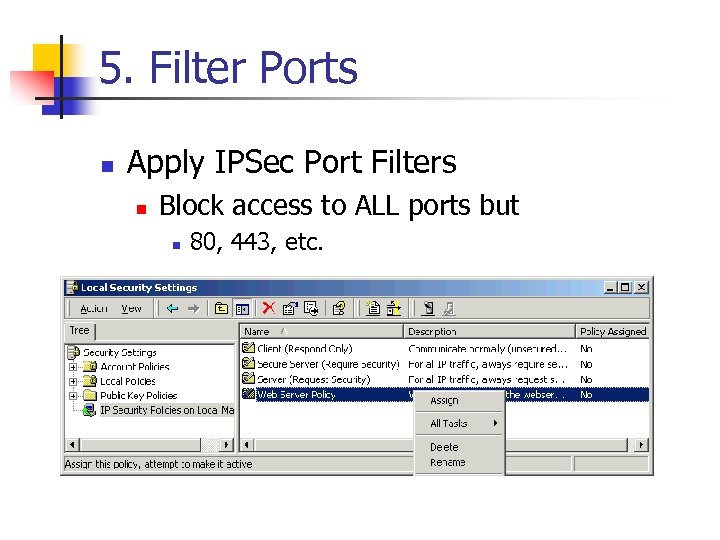 5. Filter Ports n Apply IPSec Port Filters n Block access to ALL ports but n 80, 443, etc.
5. Filter Ports n Apply IPSec Port Filters n Block access to ALL ports but n 80, 443, etc.
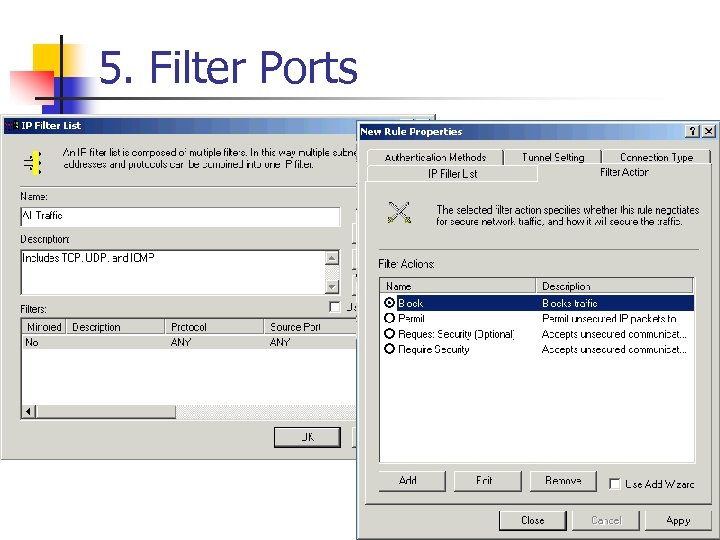 5. Filter Ports
5. Filter Ports
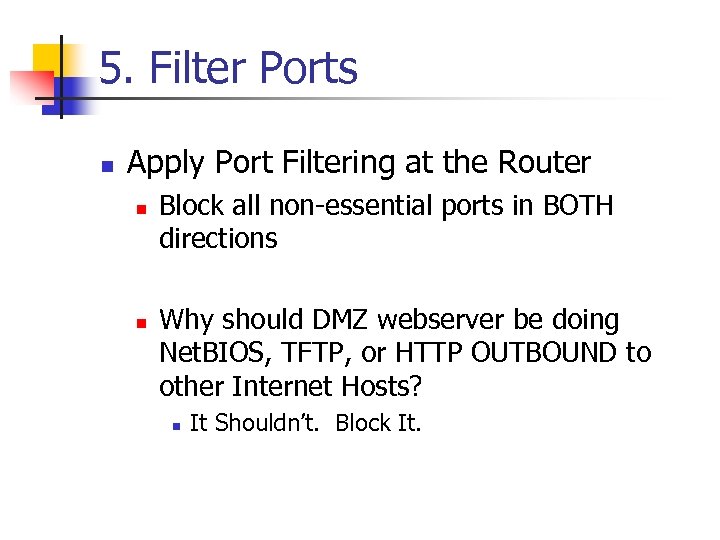 5. Filter Ports n Apply Port Filtering at the Router n n Block all non-essential ports in BOTH directions Why should DMZ webserver be doing Net. BIOS, TFTP, or HTTP OUTBOUND to other Internet Hosts? n It Shouldn’t. Block It.
5. Filter Ports n Apply Port Filtering at the Router n n Block all non-essential ports in BOTH directions Why should DMZ webserver be doing Net. BIOS, TFTP, or HTTP OUTBOUND to other Internet Hosts? n It Shouldn’t. Block It.
 4. Disable Net. BIOS n Foil Feinman n n Don’t allow malicious users to access tcp 139 and tcp/udp 445 Without this access – it will be much tougher for hacker to enumerate details about users and groups
4. Disable Net. BIOS n Foil Feinman n n Don’t allow malicious users to access tcp 139 and tcp/udp 445 Without this access – it will be much tougher for hacker to enumerate details about users and groups
 4. Disable Net. BIOS n IPSec n n Unbind File and Printer Sharing for Microsoft Networks n n Will stop 139 from responding to requests Advanced IP filtering n n Create Blocker rules for tcp 139 and tcp/udp 445 Only allow required ports Unbind Net. BIOS from WINS
4. Disable Net. BIOS n IPSec n n Unbind File and Printer Sharing for Microsoft Networks n n Will stop 139 from responding to requests Advanced IP filtering n n Create Blocker rules for tcp 139 and tcp/udp 445 Only allow required ports Unbind Net. BIOS from WINS
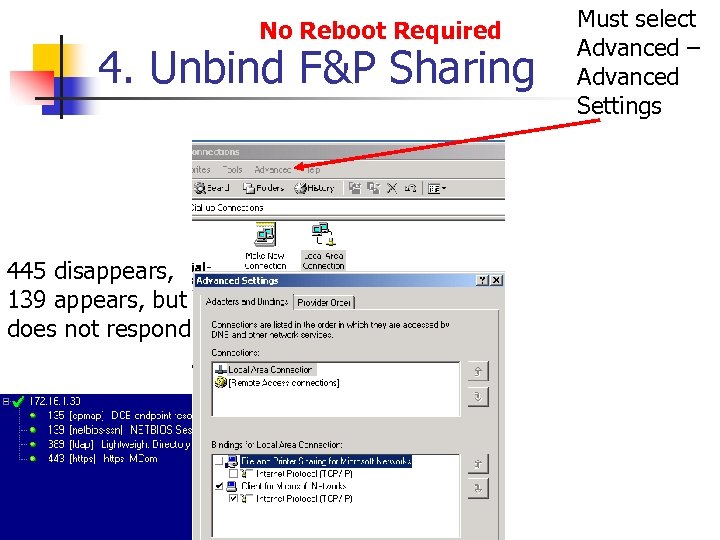 No Reboot Required 4. Unbind F&P Sharing 445 disappears, 139 appears, but does not respond Must select Advanced – Advanced Settings
No Reboot Required 4. Unbind F&P Sharing 445 disappears, 139 appears, but does not respond Must select Advanced – Advanced Settings
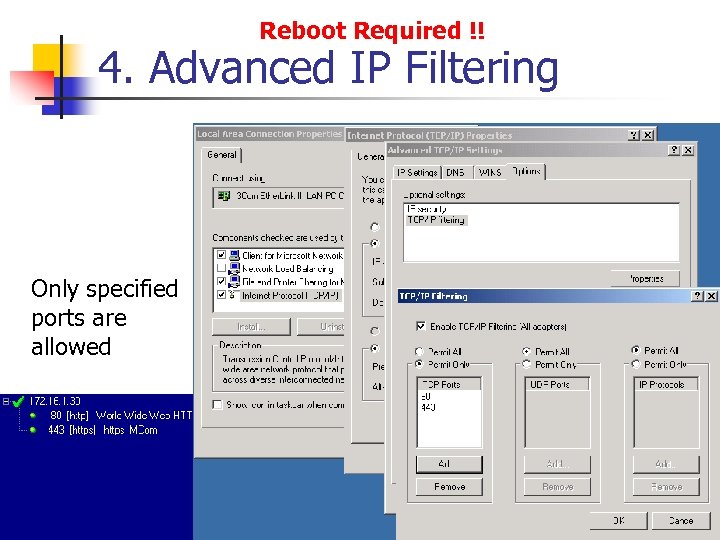 Reboot Required !! 4. Advanced IP Filtering Only specified ports are allowed
Reboot Required !! 4. Advanced IP Filtering Only specified ports are allowed
 Reboot Required !! 4. Advanced IP Filtering WARNING Selecting IP Protocols – Permit Only ‘ 6’ (tcp) will ALSO allow ICMP ‘ 1’ – even though this is not explicitely defined
Reboot Required !! 4. Advanced IP Filtering WARNING Selecting IP Protocols – Permit Only ‘ 6’ (tcp) will ALSO allow ICMP ‘ 1’ – even though this is not explicitely defined
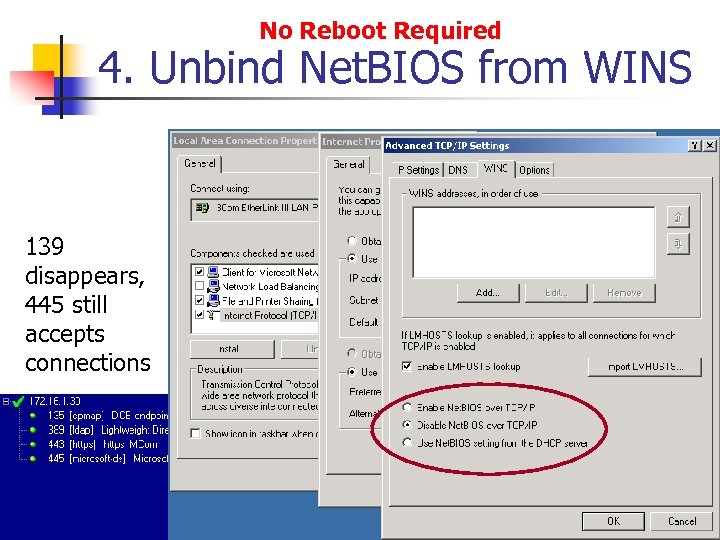 No Reboot Required 4. Unbind Net. BIOS from WINS 139 disappears, 445 still accepts connections
No Reboot Required 4. Unbind Net. BIOS from WINS 139 disappears, 445 still accepts connections
 4. Disable Net. BIOS n Most Secure Option Is to Unbind File and Printer Sharing from the specified adapter n Both 139 and 445 will be prohibited
4. Disable Net. BIOS n Most Secure Option Is to Unbind File and Printer Sharing from the specified adapter n Both 139 and 445 will be prohibited
 4. Foiling Feinman n Aside from Blocking User Enumeration via Net. BIOS n n n You must secure enumeration via SNMP and LDAP Block tcp 389 and udp 161 DO NOT weaken perms on AD during AD setup n Or, remove EVERYONE group from Pre. Windows 2000 Compatability group
4. Foiling Feinman n Aside from Blocking User Enumeration via Net. BIOS n n n You must secure enumeration via SNMP and LDAP Block tcp 389 and udp 161 DO NOT weaken perms on AD during AD setup n Or, remove EVERYONE group from Pre. Windows 2000 Compatability group
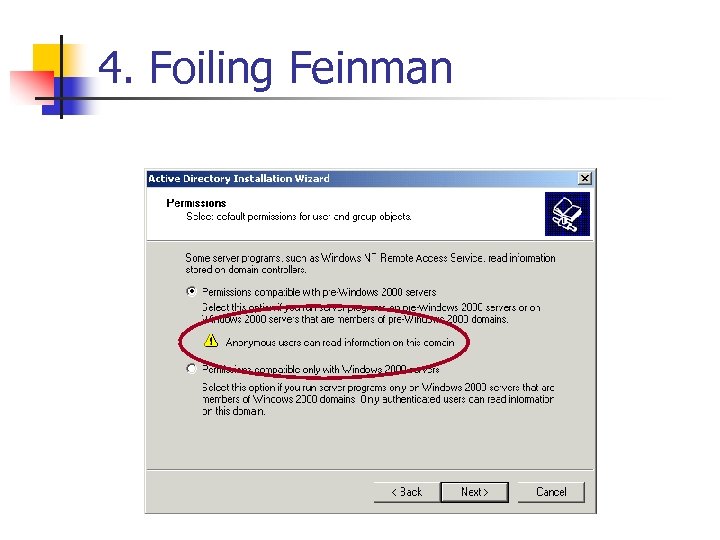 4. Foiling Feinman
4. Foiling Feinman
 3. Apply Security Templates n Templates located in: n Winntsecuritytemplates n n n Basicdc Basicsv Basicws Compatws Hisecdc Hisecws Ocfilesw Securedc Securews HISECWEB – download from microsoft. com/security
3. Apply Security Templates n Templates located in: n Winntsecuritytemplates n n n Basicdc Basicsv Basicws Compatws Hisecdc Hisecws Ocfilesw Securedc Securews HISECWEB – download from microsoft. com/security
 2. Follow IIS 5 Checklist n Summary: n Remove sample apps n n ACL IIS log file n n inetpubsamples winnthelpiishelp Program filescommon filessystemmsadc Admin and system Full Everyone RWC Enable IIS Logging Review all code on server for Revert. To. Self calls
2. Follow IIS 5 Checklist n Summary: n Remove sample apps n n ACL IIS log file n n inetpubsamples winnthelpiishelp Program filescommon filessystemmsadc Admin and system Full Everyone RWC Enable IIS Logging Review all code on server for Revert. To. Self calls
 2. Follow IIS 5 Checklist (cont) n Disable File System Object n n Remove IISADMPWD directory (if exists) n n Only exists if upgraded from IIS 4 Remove script mappings n n Regsrv 32 scrrun. dll /u htr, idc, stm, shtml Disable Parent Paths n Scripts, msadc, etc.
2. Follow IIS 5 Checklist (cont) n Disable File System Object n n Remove IISADMPWD directory (if exists) n n Only exists if upgraded from IIS 4 Remove script mappings n n Regsrv 32 scrrun. dll /u htr, idc, stm, shtml Disable Parent Paths n Scripts, msadc, etc.
 Additional IIS Security Steps n n Remove or disable Admin web sites Remove Server extensions if you aren’t using them (remove files, too) Run Permissions Wizard on all web directories Disable Windows Auth on directories that don’t need it
Additional IIS Security Steps n n Remove or disable Admin web sites Remove Server extensions if you aren’t using them (remove files, too) Run Permissions Wizard on all web directories Disable Windows Auth on directories that don’t need it
 1. Apply Hotfixes n Apply the Patches n MS 00 -086 n n n MS 01 -007 n n Solves Directory Traversal Vulnerability Supersedes 00 -057 and 00 -078 Solves Win 2 K Privilege Escalation Vulnerability Visit microsoft. com/security for others…
1. Apply Hotfixes n Apply the Patches n MS 00 -086 n n n MS 01 -007 n n Solves Directory Traversal Vulnerability Supersedes 00 -057 and 00 -078 Solves Win 2 K Privilege Escalation Vulnerability Visit microsoft. com/security for others…
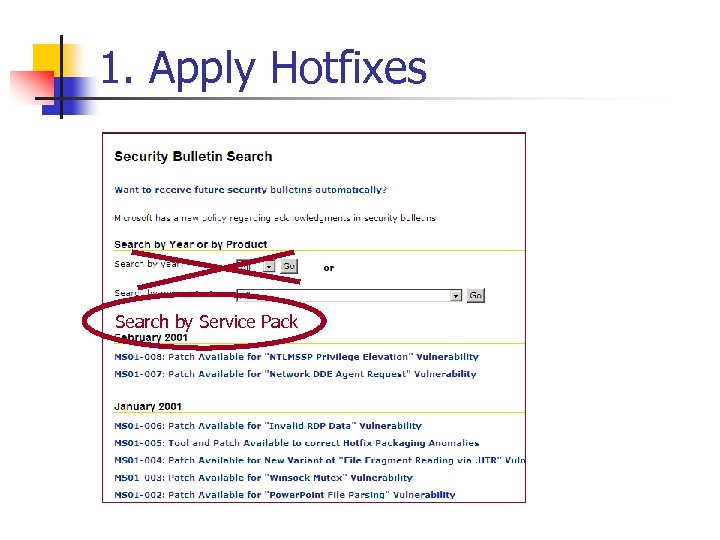 1. Apply Hotfixes Search by Service Pack
1. Apply Hotfixes Search by Service Pack
 1. Apply Hotfixes DRAFT
1. Apply Hotfixes DRAFT
 Resources n www. microsoft. com/security n n n secure@microsoft. com n n Bulletins and patches IIS 5 Security Checklist Hi. Sec. Web Template HFCheck (IIS 5 hotfix checker) Reports of security vulnerabilities in MS products secfdbck@microsoft. com n Feedback on website, tools, checklists, etc.
Resources n www. microsoft. com/security n n n secure@microsoft. com n n Bulletins and patches IIS 5 Security Checklist Hi. Sec. Web Template HFCheck (IIS 5 hotfix checker) Reports of security vulnerabilities in MS products secfdbck@microsoft. com n Feedback on website, tools, checklists, etc.


