a66479945ef90f1150344deda6a83249.ppt
- Количество слайдов: 28

Focusing on the Fool: Building an Awareness and Training Program Bill Gardner (oncee) Branden Miller (f 0 zzie)
Agenda Other than the hidden one Intro What How Conclusion M

whoami Bill Gardner oncee Bill Gardner is an information security educator, co-founder and vice president of 304 Geeks, and chairman of the information security section and vice president of the Appalachian Institute of Digital Evidence. Gardner is also the co-founder and an organizer of Hack 3 r. Con, an annual information security conference in Charleston, WV.

Hack 3 r. Con. org


whoami Branden Miller f 0 zzee Branden Miller is responsible for the Awareness and Training program for a health care entity that has over 10, 000 employees. He retired from the US Navy in 2011 after 20 years of service. He has held many positions such as system administrator, network engineer, digital network exploitation analyst, and finally, adjunct faculty for the National Cryptologic School.
Why do we do it? Because, dumbass…it is a good idea, it is cheaper than responding all the time, and it may be the law. M
• Bad guys/hackers/degenerates B

• Laws, regulations, standards B

• Employees When employees do “stupid” stuff, it is our fault, not theirs! B

• Ponemon Institute • • An average web-based attack costs $143, 209; malicious code, $124, 083; and malicious insiders, $100, 300. (“Cost of Cyber Crime Study”) On average, data breaches cost [healthcare] organizations $2, 243, 700. This is an increase of $183, 526 from the 2010 study despite healthcare organizations’ increased compliance with federal regulations. (“ 2 nd Annual Benchmark Study on Patient Privacy and Data Security) M

Threats: Why the bad guys want your stuff • • Money – Identity Theft, Credit Card Theft Industrial Espionage - Trade Secrets Hacktivism Bragging Rights B
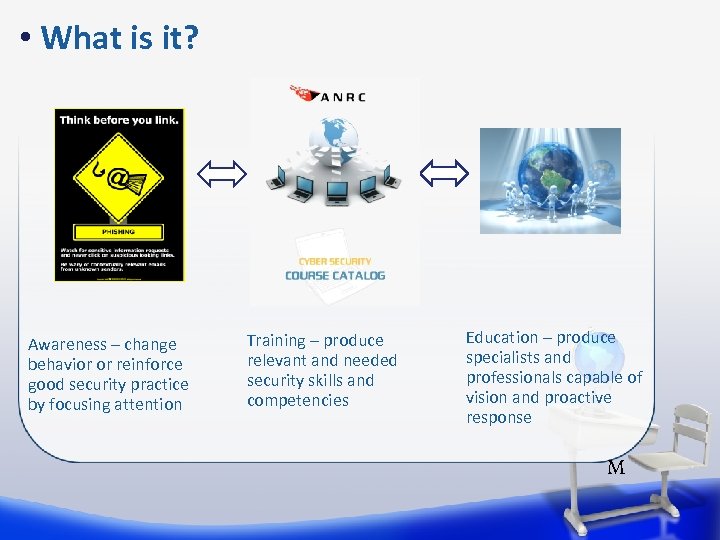
• What is it? Awareness – change behavior or reinforce good security practice by focusing attention Training – produce relevant and needed security skills and competencies Education – produce specialists and professionals capable of vision and proactive response M

• Professional Development A continuous “cradle-to-grave” learning process which has the purpose of ensuring a user possesses the required level of knowledge and competence necessary for their roles. Professional development “validates” skills through certification. M
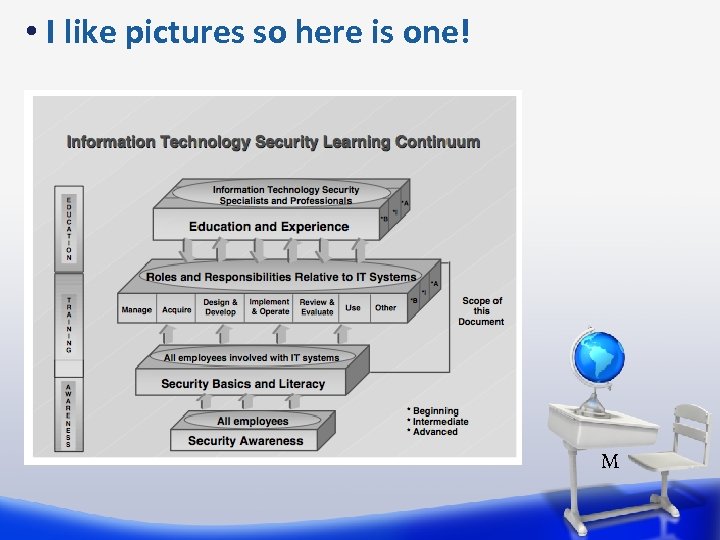
• I like pictures so here is one! M

• Get buy in! 3 approaches • Top down approach • • Bottom up approach • • Shows leadership supports New employees as “banner carriers” Blended • A little bit of both M
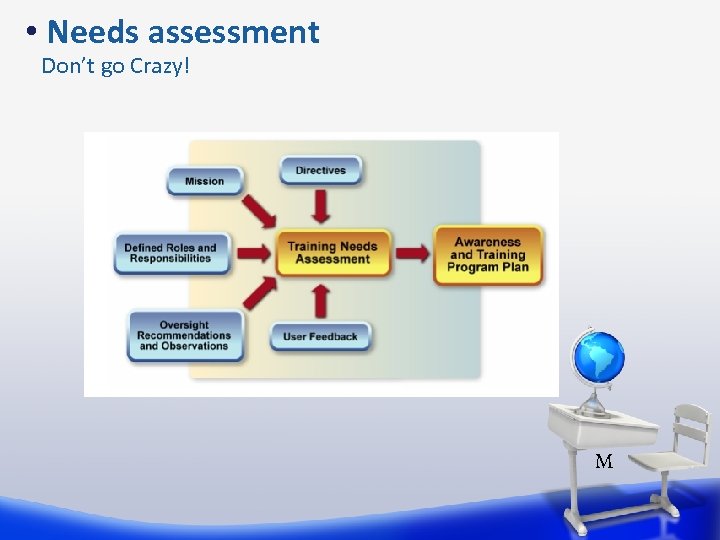
• Needs assessment Don’t go Crazy! M

• Gap Analysis Don’t over think it! M

• Develop a plan 1. 2. 3. 4. Scope/funding Goals/outcomes Mandatory/optional Topics • • Passwords Locking computers Attachments Phishing Social engineering No-tech hacking Data leakage “Hacking in the News” BM
• Develop materials Beg, borrow, leverage Buy Track Make changes Think of new and innovative ways to reach the users! B

• Reporting and metrics 1. Monitoring using: • • • 2. End of course feedback forms (lvl 1) 3 -6 month feedback forms (lvl 2) Supervisor feedback forms (lvl 3) Metrics • • Don’t track # of people trained unless it is regulatory! Do track the effectiveness of training on the environment. M
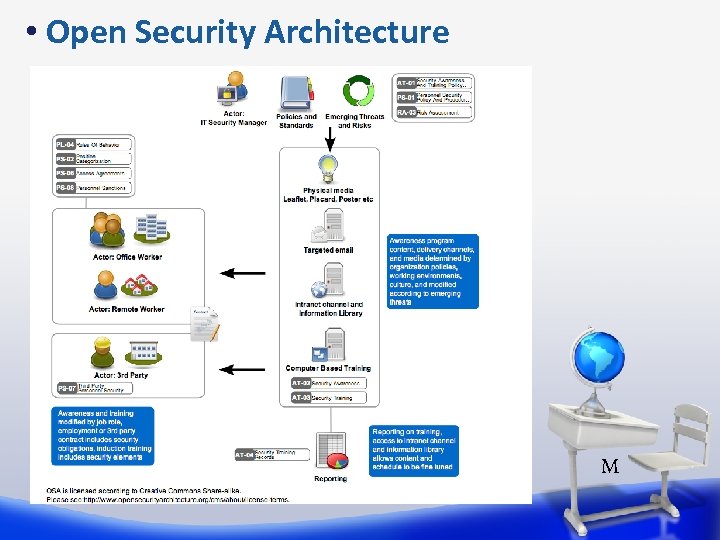
• Open Security Architecture M

• Conclusion • • • Each organization must develop a T-n-A program that fits their needs You can do it on a tight budget Focus on results. If something doesn’t work or the customer is not happy, change it. M

• Resources NIST SP 800 -50 Building an IT Security and Awareness Program NIST SP 800 -16 IT Security Training Requirements: A Role- and Performance-Based Approach Employee Training and Development by Raymond A. Noe M

• Resources continued The new user’s guide: How to raise information security awareness by The European Network and Information Security Agency Native Intelligence, Inc. @ www. nativeintelligence. com Noticebored by Isec. T, Ltd. @ www. noticebored. com Microsoft download center and toolkit

Questions? ? ?
a66479945ef90f1150344deda6a83249.ppt