55a055460cedb0bcbeec129b1986cd76.ppt
- Количество слайдов: 58

Fish. Net Security E-Discovery Benjamin Stephan CISSP CISA En. CE PA-QSA PFI Benjamin. Stephan@Fish. Net. Security. com

Fish. Net Security Overview Committed to security excellence, Fish. Net Security is the #1 provider of information security solutions that combine technology, services, support, and training. Fish. Net Security solutions have enabled over 3, 000 clients to better manage risk, meet compliance requirements, and reduce costs while maximizing security effectiveness and operational efficiency. § Over 12 years of experience delivering enterprise solutions and comprehensive service offerings § Established relationships with “best-of-breed” information security partners and vendors § A full-suite of information security services provided § Respected national presence Focused local support

About Fish. Net Security Office Locations Atlanta, GA Boston, MA Charlotte, NC Chicago, IL Columbus, OH Dallas, TX Denver, CO Detroit, MI Ft. Wayne, IN Houston, TX Indianapolis, IN Kansas City, MO Newport Beach, CA New York City, NY Omaha, NE Phoenix, AZ San Francisco, CA Seattle, WA St. Louis, MO St. Paul, MN Tallahassee, FL Tampa, FL Washington, D. C. West Palm Beach, FL Cambridge, UK
Overview § § § § Introduction Computer Forensics vs. e-Discovery Federal Rules of Civil Procedures E-Discovery Reference Model Early Case Assessment Products & Services Sample Cases Disclaimer: -Speakers opinions are just that – opinions -Not offering legal advice, just discussing principals
Introduction § Technology Age § Rapid Communication § E-mail § Cell Phones § Instant Messaging § Digital Information § Electronic Media § Documents, Spreadsheets, Power. Point, Databases § CD, DVD, Blu-Ray § Data Capacity § § 90’s – Megabytes 00’s – Gigabytes 10’s – Petabytes 20’s – Zettabytes
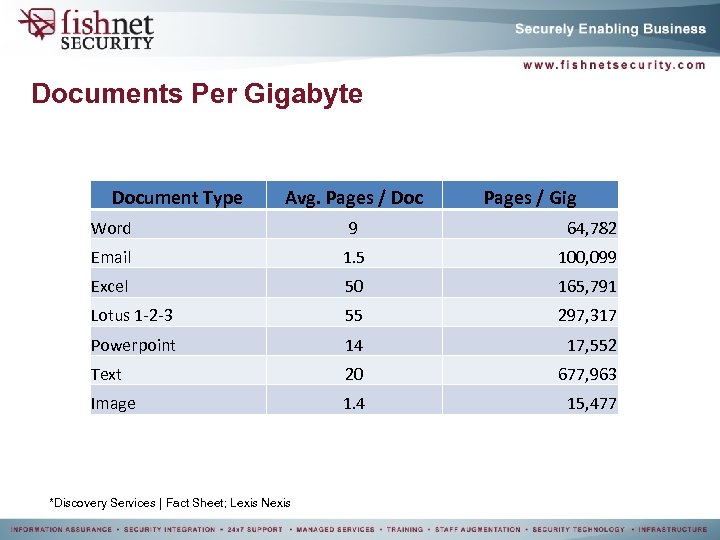
Documents Per Gigabyte Document Type Avg. Pages / Doc Pages / Gig Word 9 64, 782 Email 1. 5 100, 099 Excel 50 165, 791 Lotus 1 -2 -3 55 297, 317 Powerpoint 14 17, 552 Text 20 677, 963 Image 1. 4 15, 477 *Discovery Services | Fact Sheet; Lexis Nexis
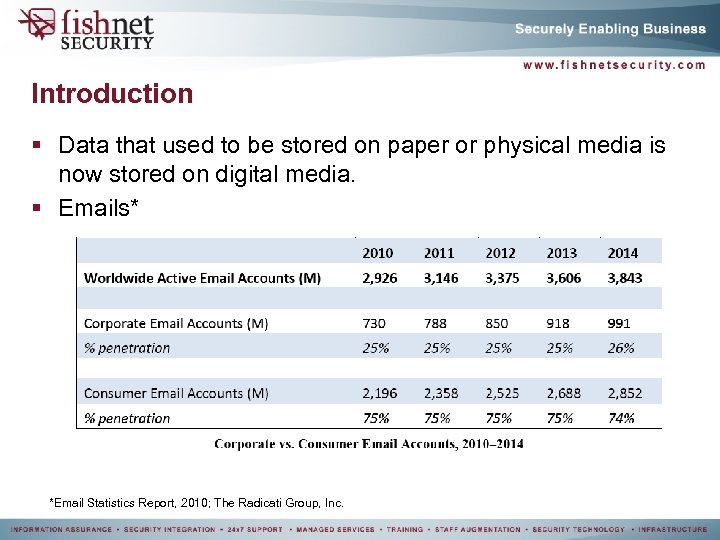
Introduction § Data that used to be stored on paper or physical media is now stored on digital media. § Emails* *Email Statistics Report, 2010; The Radicati Group, Inc.

Computer Forensics vs. e-Discovery

Computer Forensics vs. e-Discovery § Computer Forensics: The acquisition, preservation and analysis of digital information that meets the requirements of evidence for court presentation. § e-Discovery: refers to any process in which electronic data is sought, located, secured, and searched with the intent of using it as evidence in a civil or criminal legal case.

Computer Forensics vs. e-Discovery § Forensics vs. e-Discovery: E-discovery is the process of analyzing data that is accessible without the need for additional tools or applications. Whereas, Computer Forensics is the process of analyzing data that can only be accessed with proper training and tools.

Federal Rules of Civil Procedures (FRCP)

Federal Rules of Civil Procedures § Key Date: December 1, 2006 § The FRCP is amended to more accurately address digital information. § Amended Rules: 16, 26, 33, 34, 37, 35 § Electronically Stored Information (ESI; Rule 26. a): § ESI is all information stored on electronic media. § Examples: § § § § § Email Voicemail CD DVD Hard Drive Thumb Drive Computer in your car Fragmented files PS 3 / WII / Xbox 360 Mobile Devices
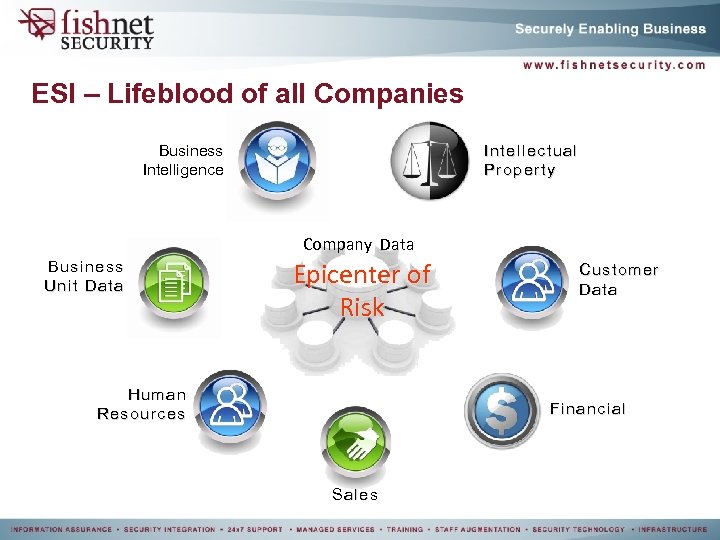
ESI – Lifeblood of all Companies Business Intelligence Intellectual Property Company Data Business Unit Data Epicenter of Risk Human Resources Customer Data Financial Sales

FRCP Rule 26 § Requesting party must submit: § Information on people § Information on the ESI § Only information requested is allowed (26. s). § Meet and confer “gottchas” (26. f): § Must occur 120 days from request § Most attorneys want 30 days to review § Most attorneys wait 30 days to provide § Litigation Holds § “Clawback” (26. b) § Inadvertent disclosure of ESI § Privileged information

FRCP Rule 26 § Identify sources of ESI § Sample information § Validation of sources § Exclusion of sources § Reasons for exclusion: § Not relevant § Excessive burden § Both parties should agree on ESI § Court makes final decision § Determine who is responsible for payment

FRCP Rule 34 & 37 § Establish protocols of production § Requesting party can set format § “Safe Harbor” § Minimize the potential of loss data § Data deleted as part of everyday processes is acceptable § Must have defined data retention policies
E-Discovery Reference Model (EDRM)
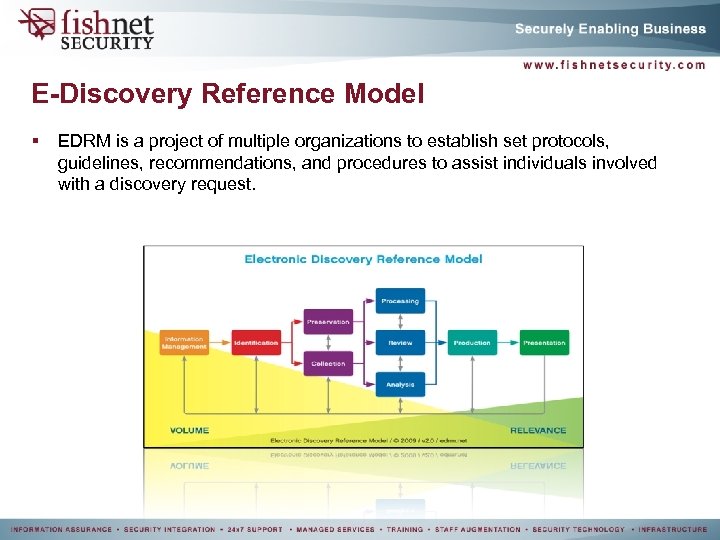
E-Discovery Reference Model § EDRM is a project of multiple organizations to establish set protocols, guidelines, recommendations, and procedures to assist individuals involved with a discovery request.
E-Discovery Reference Model § Information Management: The process of maintaining structure and organization around ESI. § Some organizations implement products to allow for pre-capture of potentially critical ESI. § Such as collection of all email both ingress and egress. The email is then indexed and archived. When a request for discovery is initiated then the emails can be processed easily. § Pre-collection of critical data allows for ESI to be archived and indexed prior to a discovery request. § Pros: § Data is pre-indexed § Minimal interruption § Cons: § Substantial storage space requirements § Can be expensive § Some solutions provide online hosting which would require additional bandwidth
E-Discovery Reference Model § Identification: The process by which ESI is categorized and marked for potential necessity in a discovery request. § ESI profiling § Custodians are correlated with ESI based on the level of access to data. § A primary matrix is kept to easily correlate the potential ESI sources based on the discovery request. § Data classification § Data is classified according to sensitivity and access controls. § By creating a data classification structure ESI is more easily segmented and controlled.

What’s My Data? § Develop a data classification plan. § Develop a data retention policy. § Assure data is appropriately marked. Where’s My Data? § ESI may be stored in many places: § § File servers Laptops Blackberries Thumbdrives

Who Has The Data? § Custodian to information matrix § Also know as an ACL matrix § Custodian to system matrix § § How many systems does your Administrator access? Data access history Physical Access controls Access and Audit logs
Data Classification § Mapping of sensitive data classification § Determination of risk of data compromise § Citation of evidence of exfiltration § Interpretation of exfiltration potential § Assist in determination of notification potential § Identification of sensitive data storage § § § PCI HIPAA PII SOX Financial records
Sensitive Data Flow
E-Discovery Reference Model § Preservation § Data must be preserves in its native format. § Alterations to the data can lead to spoliation, contamination, and potential sanctions § Collection § Data must be collected by trained professionals § Failure to collect the data in the correct manner can lead to dismissal of the evidence § “The most expensive piece of evidence is the one you can’t use. ”
Preservation & Collection § Collect & Secure any data in a forensically sound way § Targeted collection vs. forensic image § Tools used to carry out the collection exercise • • • Encase FTK Write blocker § Time for initial culling? • • De-Nist Hash sets System files Filter in/out § Analyze the data § Produce culled data set for the processing phase

Evidence Collection § Both computer forensics and e-discovery require professional expertise in collecting the data. § Computer Forensic Collection & Investigation • Imaging § PCs/laptops, USB devices & mobile phones • Investigations § § § Corporate theft/leakage HR issues Data deletion & concealment Breach analysis Incident response • Experienced practitioners • Expert witness for civil and criminal matter

Evidence Collection § Evidence Handling & Chain of Custody • Chain of Custody “Chain of custody refers to the chronological documentation, and/or paper trail, showing the seizure, custody, control, transfer, analysis, and disposition of evidence, physical or electronic”. http: //en. wikipedia. org • Secure storage • Evidential integrity and continuity
E-Discovery Reference Model § Processing § E-Discovery processing uses sophisticated mapping, indexing, and heuristical software to create a relationship structure from all the ESI collected. § Often keywords, document types, conversational topics, and other criterion are used to filter the ESI into a smaller dataset. § Filter can happen on multiple levels to help reduce the amount of data to be reviewed.
E-Discovery Reference Model § Taking the collected data from different sources • • • Digital Hard copy Audio § Entering the data into one controllable database § Whittle down the size of the data by: • • • Keywords Date ranges Custodians De duplication File types § Produce a responsive data subset to go to review phase.
E-Discovery Reference Model § Review § Document review is often a critical portion of the litigation process. The efficiency of the review can be maximized by decrease the review set to allow more time for accurate analysis. § Tools § The efficiency of ESI review can also be improved by leveraging advance tools. § Query tools can leverage multiple methodology to review the ESI such as: § § Conversational de-duplication Content pivoting Boolean logic dt. Search
E-Discovery Reference Model § Review § Following a reduction of data via the processing phase the review phase prepares the data for a legal review. § Many utilities allow for reviews to view, tag, mark up any documents, emails, attachments or any data found to be relevant.
E-Discovery Reference Model § Review § One key step in the review process is redaction. § Redaction: The process of reviewing multiple documents and extracting key pieces of data from the original content. § In litigation cases the redaction process is applied to remove client attorney privileged information from ESI prior to provision of evidence to opposing counsel. § Redacted information must be logged and explained such that if any discrepancies arise then the reason for the redaction can be supported.
E-Discovery Reference Model § Analysis § Throughout the e-discovery process ESI is analyzed using multiple criterion. § While analysis falls after review in the EDRM the analysis actually occurs throughout the discovery. Analysis help to: § § Minimize the ESI data set Determine relativity of data Identify potential ESI sources Create ESI sets for manual review

E-Discovery Reference Model § Production: The process of organizing ESI into a format that can be delivered to legal counsel. § After the ESI has been reviewed by legal counsel and is ready for delivery to opposing counsel, the ESI must be “produced”. § Production of ESI in a litigation case can be a crucial step. The FRCP mandates that the means of production be fully delineated by both parties. § Failure to produce ESI according to the agreed upon means can lead to fines and sanctions. § ESI must be produced in its “native format”. § Rule 34(b) allows that the requesting party may specify the format for production.

Production § Finding the responsive and reviewed data set then converting into a production set ready for disclosure. § Options to consider when doing a batch print: • • • Endorse (i. e. bates number), Annotations & Coding Document redaction Watermark Export Convert documents to PDF, TIFF or both

E-Discovery Reference Model § Presentation: The results of the discovery process must be presented in such a format that all parties involved are able to understand the results. § ESI is often presented in “image” format. The image format allows for easy view of the ESI and corresponding data. § Images are often in TIFF or PDF format § Expert witnesses can be critical to the presentation of the ESI. The expert witness interprets, explains, and details the results of the discovery process.

Early Case Assessment

Early Case Assessment § Strategic Scoping § “Meet and Confer”: Leverage the meet and confer meetings to establish an exact means of scoping. Ensure discovery requests address specific custodians, data flows, data classifications, and technical architecture. § Targeted Collection § Live collection § Logical Evidence File (LEF) § Keyword Triage § Keyword crawlers § GREP § 7 phrase

Early Case Assessment § ESI Profiling § Custodian to ESI Matrix § Legal Hold § Ambiguous § Too comprehensive § Overly Burdensome § Pre-process Data Culling § Keyword filtering § Boolean expressions § Data Pivoting § Visualizing data statistics § Graphical analysis of trending and anomalies
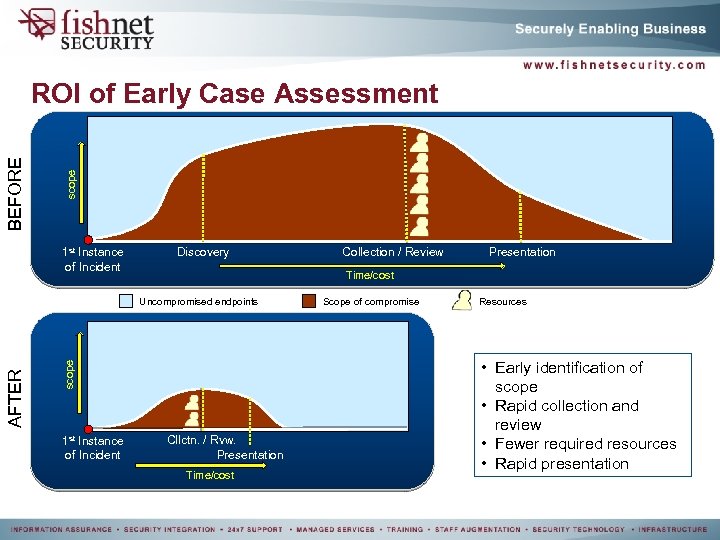
scope BEFORE ROI of Early Case Assessment 1 st Instance of Incident Discovery scope AFTER Presentation Time/cost Uncompromised endpoints 1 st Instance of Incident Collection / Review Cllctn. / Rvw. Presentation Time/cost Scope of compromise Resources • Early identification of scope • Rapid collection and review • Fewer required resources • Rapid presentation

Products and Services

§ Flexible • • • Custom workflow Multiple parties or multi-stage review Tracking, e. g. timelines or chain of custody § Secure • • Role based Folder-level Document –level Field-level § Scalable • • • Millions of documents Hundreds of concurrent users Multiple delivery options
§ Foreign Language Support • Fully Unicode compliant. • Language identification § Relativity Analytics • Cluster similar documents § Relativity Pivot • Data analysis functionality § Hosted • Via Legal Gateway

e-Discovery Services § Enterprise e-Discovery § Native file review § Online tiff conversion for redaction § Local file review § Concept Searching § Review and search documents based on “concepts” or subject matter terms. § dt. Searches § Relativity Pivot § Graphical analysis of search statistics and metadata § Online review § Provide access to opposing counsel
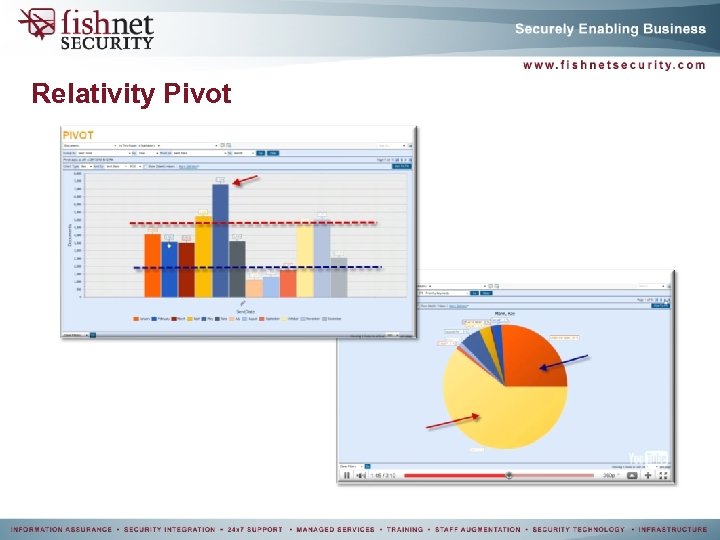
Relativity Pivot
Mobile Review § New e-Discovery services support virtually any mobile device § Secured review § Power of e-Discovery anywhere § Redaction at your fingertips… literally
Nexidia § Audio e. Discovery • Nexidia • Speed of search • Reduces cost of review • Accuracy
En. Case e-Discovery § In house e-Discovery § Collection § Pre-collection Analytics § Preservation § Early Case Assessment & Review § Legal Hold Automation § Web based § Validation § Email delivery § User Friendly § User defined tagging § Email & conversational searches
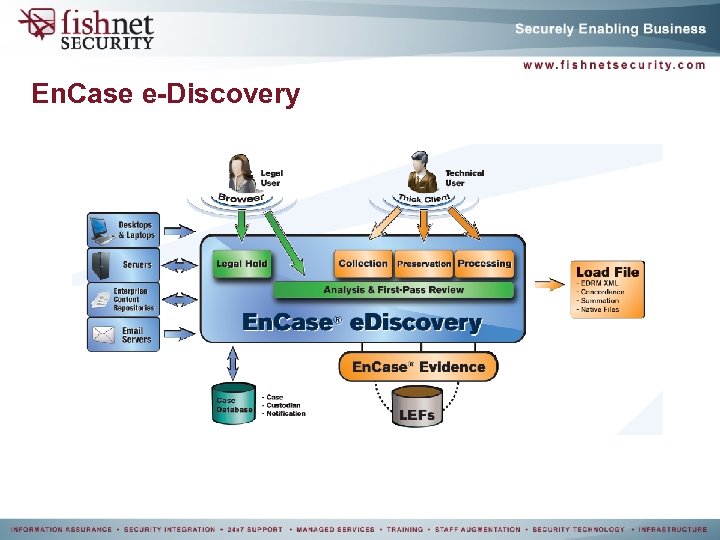
En. Case e-Discovery
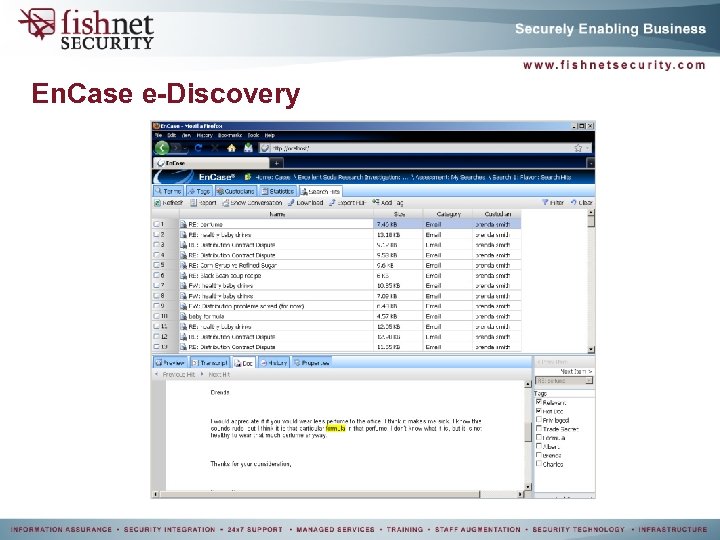
En. Case e-Discovery
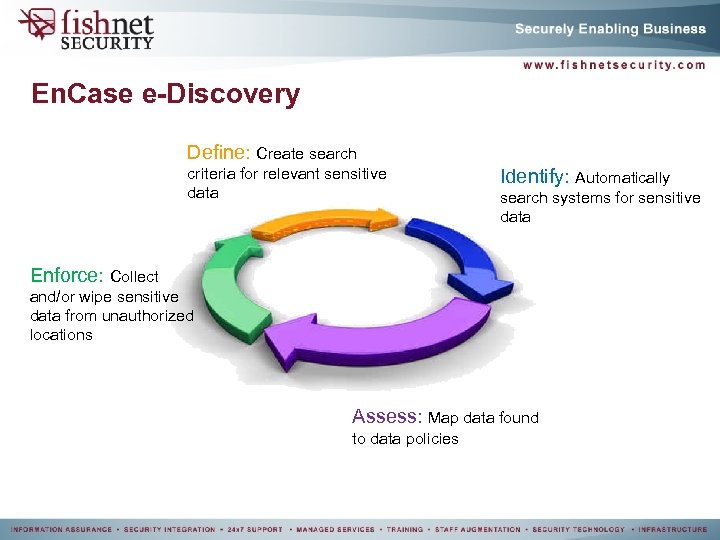
En. Case e-Discovery Define: Create search criteria for relevant sensitive data Identify: Automatically search systems for sensitive data Enforce: Collect and/or wipe sensitive data from unauthorized locations Assess: Map data found to data policies

Sample Cases
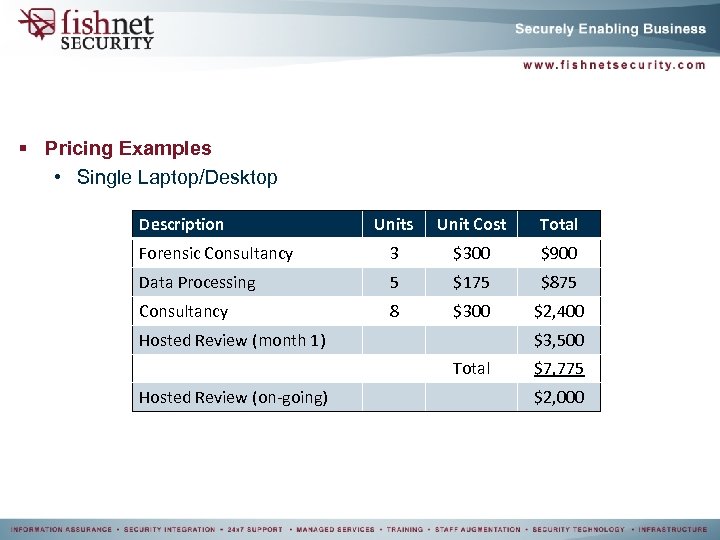
§ Pricing Examples • Single Laptop/Desktop Description Units Unit Cost Total Forensic Consultancy 3 $300 $900 Data Processing 5 $175 $875 Consultancy 8 $300 $2, 400 Hosted Review (month 1) $3, 500 Total Hosted Review (on-going) $7, 775 $2, 000
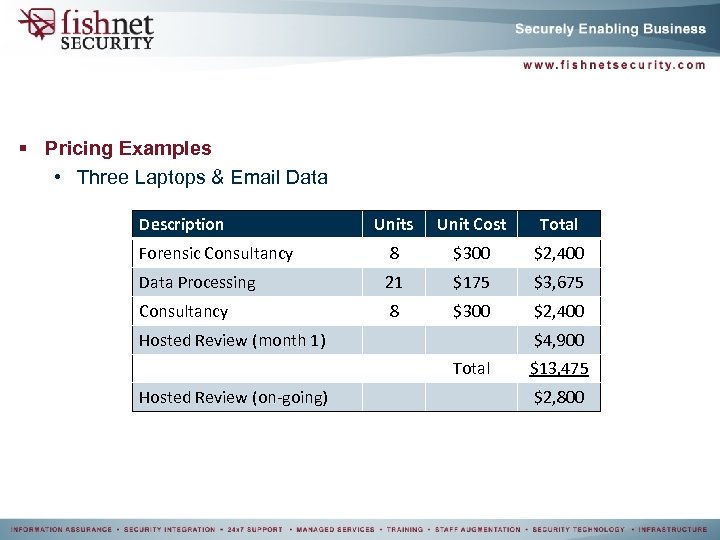
§ Pricing Examples • Three Laptops & Email Data Description Units Unit Cost Total Forensic Consultancy 8 $300 $2, 400 Data Processing 21 $175 $3, 675 Consultancy 8 $300 $2, 400 Hosted Review (month 1) $4, 900 Total Hosted Review (on-going) $13, 475 $2, 800
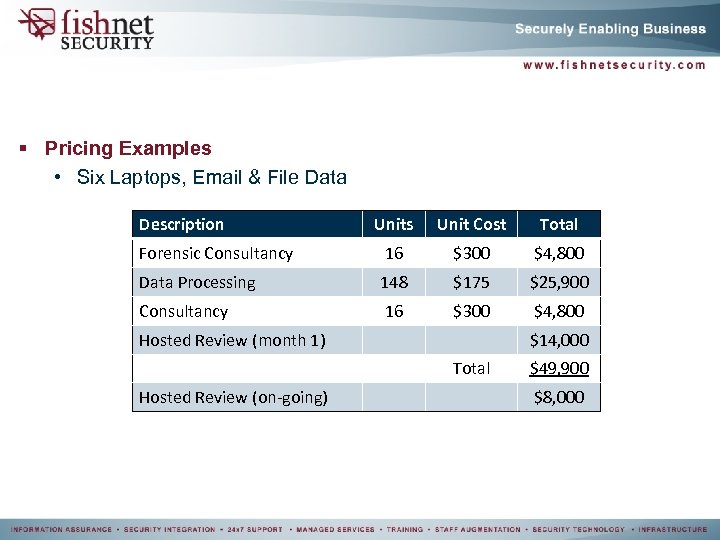
§ Pricing Examples • Six Laptops, Email & File Data Description Units Unit Cost Total Forensic Consultancy 16 $300 $4, 800 Data Processing 148 $175 $25, 900 Consultancy 16 $300 $4, 800 Hosted Review (month 1) $14, 000 Total Hosted Review (on-going) $49, 900 $8, 000

Questions? Benjamin. Stephan@Fish. Net. Security. com

Benjamin Stephan: Benjamin Stephan has over 10 years of experience in software development, computer forensics, digital investigations, regulatory compliance, security assessments, computer programming, and risk management. Benjamin has been with Fish. Net Security for over 2 years and during that time has dedicated himself to PCI compliance, breach investigations, and computer forensics. At Fish. Net Security, Benjamin helped develop and implement the methodology for both Fish. Net Security’s Incident Management and PA -DSS practices. Benjamin also helped lead efforts enabling the company to become a Visa Qualified Incident Response Assessor (QIRA) and Master. Card Qualified Forensic Investigator (QFI). Prior to his employment at Fish. Net Security, Benjamin helped develop, implement, and maintain the computer forensics division for a leading security company in Arizona. Benjamin’s current efforts include oversight of high profile QIRA investigations, quality assurance review of QIRA investigation, and management of the Incident Response practice. Benjamin received his Bachelor’s of Science degree in Electrical Engineering from Arizona State University. Benjamin has also achieved the following certifications: En. Case Certified Examiner (En. CE), Certified Information Systems Security Professional (CISSP), Certified Information Systems Auditor (CISA), PCI DSS Qualified Security Assessor, and PA DSS Qualified Security Assessor. *All logos, images, trademarks, are owned by their associated reference. Images provide by public websites and documentation.
55a055460cedb0bcbeec129b1986cd76.ppt