44d0198c73c1739ca0d42eb674b31d20.ppt
- Количество слайдов: 19
 Firewalls Network Security Marshall Leitem 11/30/04
Firewalls Network Security Marshall Leitem 11/30/04
 Overview § § § What is a firewall? What does it protect us from? What does it consist of? Hardware/software Questions?
Overview § § § What is a firewall? What does it protect us from? What does it consist of? Hardware/software Questions?
 What is a Firewall? § fire·wall Any of a number of security schemes that prevent unauthorized users from gaining access to a computer network or that monitor transfers of information to and from the network.
What is a Firewall? § fire·wall Any of a number of security schemes that prevent unauthorized users from gaining access to a computer network or that monitor transfers of information to and from the network.
 Securities Employed § Packet Filtering Checks incoming packets to see they meet set requirements, if not the packets are discarded. § Proxy Service Information from the Internet is retrieved by the firewall and then sent to the requesting system and vice versa. § Stateful inspection - doesn't examine the contents of each packet, compares certain key parts of the packet to a database of trusted information. Information traveling from inside the firewall to the outside is monitored for specific defining characteristics, then incoming information is compared to these characteristics. If the comparison yields a reasonable match, the information is allowed through. Otherwise it is discarded
Securities Employed § Packet Filtering Checks incoming packets to see they meet set requirements, if not the packets are discarded. § Proxy Service Information from the Internet is retrieved by the firewall and then sent to the requesting system and vice versa. § Stateful inspection - doesn't examine the contents of each packet, compares certain key parts of the packet to a database of trusted information. Information traveling from inside the firewall to the outside is monitored for specific defining characteristics, then incoming information is compared to these characteristics. If the comparison yields a reasonable match, the information is allowed through. Otherwise it is discarded
 What does it consist of? § Software Implementations § Zone Alarm § Omniquad Personal Firewall § Norton Personal Firewall § Hardware Implementations § Linksys Etherfast Cable/DSL Firewall Router § CISCO PIX 500 Firewall
What does it consist of? § Software Implementations § Zone Alarm § Omniquad Personal Firewall § Norton Personal Firewall § Hardware Implementations § Linksys Etherfast Cable/DSL Firewall Router § CISCO PIX 500 Firewall
 Pictures
Pictures
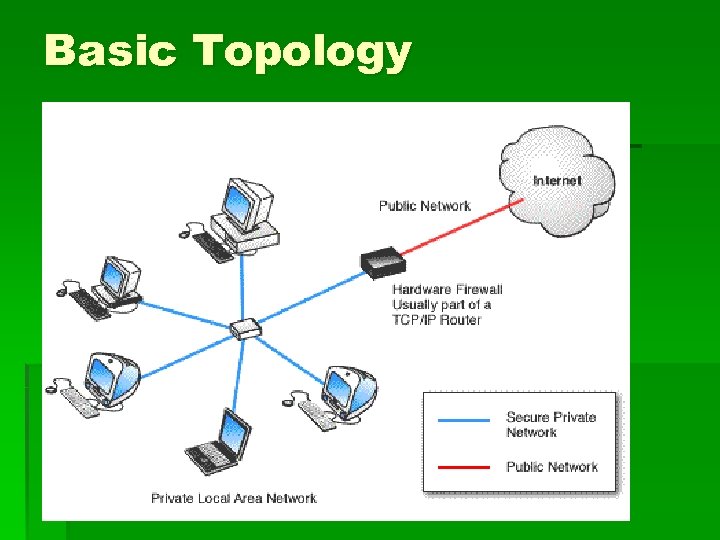 Basic Topology
Basic Topology
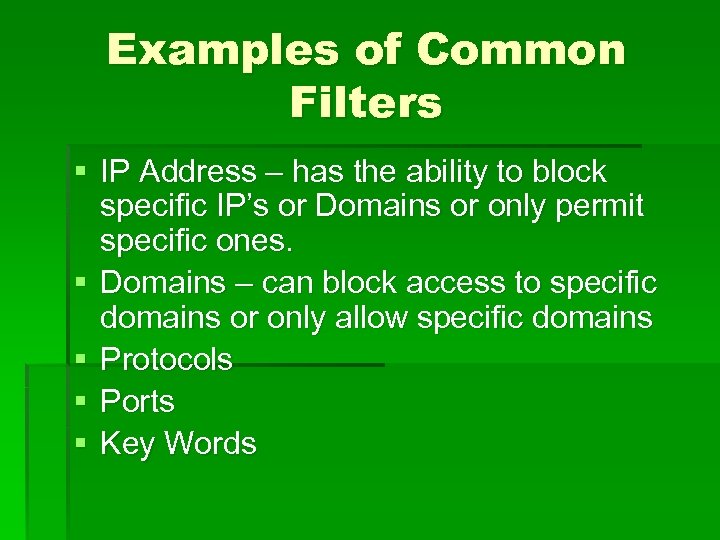 Examples of Common Filters § IP Address – has the ability to block specific IP’s or Domains or only permit specific ones. § Domains – can block access to specific domains or only allow specific domains § Protocols § Ports § Key Words
Examples of Common Filters § IP Address – has the ability to block specific IP’s or Domains or only permit specific ones. § Domains – can block access to specific domains or only allow specific domains § Protocols § Ports § Key Words
 What it Prevents § § § Remote Login Application Backdoors SMTP session Jacking Denial of Service Attacks Spam Source Routing
What it Prevents § § § Remote Login Application Backdoors SMTP session Jacking Denial of Service Attacks Spam Source Routing
 Demilitarized Zone § You want the un-trusted or un-known networks to have access to some of your resources § You still want to maintain a secure private network § A Firewall is used to create this area
Demilitarized Zone § You want the un-trusted or un-known networks to have access to some of your resources § You still want to maintain a secure private network § A Firewall is used to create this area
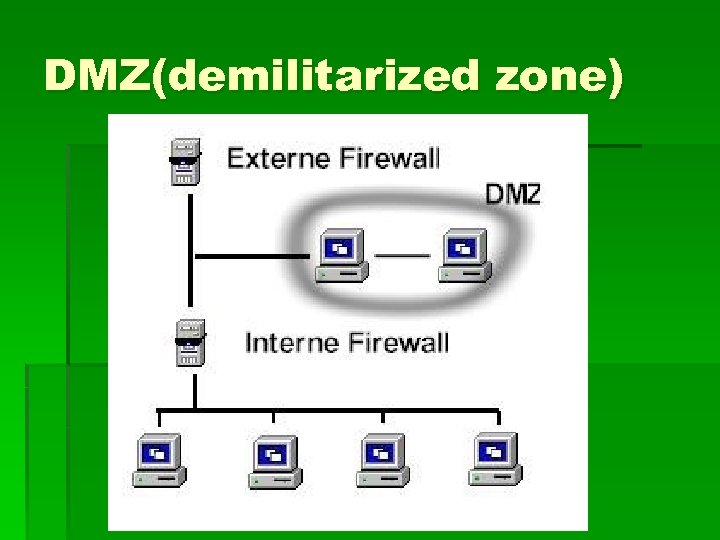 DMZ(demilitarized zone)
DMZ(demilitarized zone)
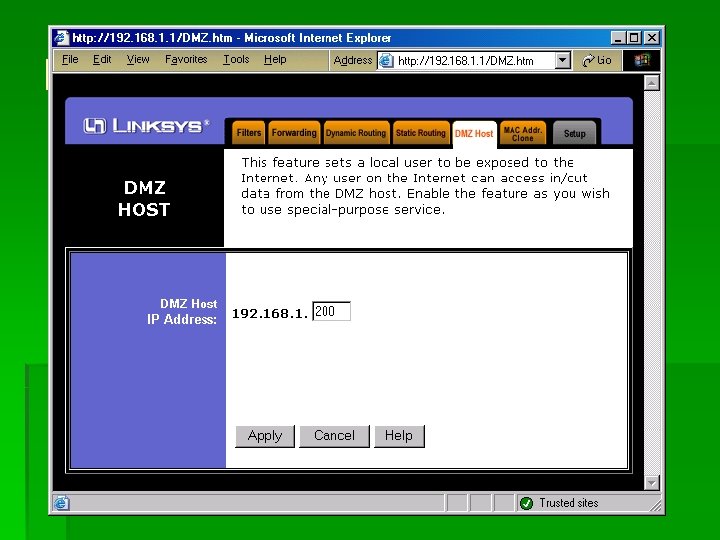 DMZ
DMZ
 Downside of Firewalls § § § Performance Degradation Can be difficult to configure Can be susceptible to IP-Spoofing Can Interfere with some software Extra Costs
Downside of Firewalls § § § Performance Degradation Can be difficult to configure Can be susceptible to IP-Spoofing Can Interfere with some software Extra Costs
 Benefits of Firewalls § Provides a “choke point” in which traffic can be evaluated to see it meets specifications. § Prevents Remote Login § Allows rules on users and data traveling through to be imposed.
Benefits of Firewalls § Provides a “choke point” in which traffic can be evaluated to see it meets specifications. § Prevents Remote Login § Allows rules on users and data traveling through to be imposed.
 What can’t Firewalls Protect Against? (Steel door on a Wooden House) § Attacks that don’t go through firewall § Traitors § Manually Moving of Data (tape storage, etc) § Tunneling § Trojans & Viruses
What can’t Firewalls Protect Against? (Steel door on a Wooden House) § Attacks that don’t go through firewall § Traitors § Manually Moving of Data (tape storage, etc) § Tunneling § Trojans & Viruses
 Cost Options? § Free – software based firewalls can be found § Exspensive up to $100, 000+ hardware solutions that require much time and effort to install
Cost Options? § Free – software based firewalls can be found § Exspensive up to $100, 000+ hardware solutions that require much time and effort to install
 Hardware Vs. Software § Hardware § in most cases, they can be effective with little or no configuration § can protect every machine on a local network § Can be susceptible to attacks from inside the private network due to trojans § Often packet filtering is set up too trusting of outgoing packets § Group wide Policy
Hardware Vs. Software § Hardware § in most cases, they can be effective with little or no configuration § can protect every machine on a local network § Can be susceptible to attacks from inside the private network due to trojans § Often packet filtering is set up too trusting of outgoing packets § Group wide Policy
 Hardware Vs. Software § you can specify which applications are allowed to communicate over the Internet from that PC (ex: only outlook express can use Port 25) § can only protect the machine they're installed on § Better protection against trojans and worms than hardware but must be configured on each machine
Hardware Vs. Software § you can specify which applications are allowed to communicate over the Internet from that PC (ex: only outlook express can use Port 25) § can only protect the machine they're installed on § Better protection against trojans and worms than hardware but must be configured on each machine
 Questions?
Questions?


