3a0329429cd33d42e5521a3daf6cadaa.ppt
- Количество слайдов: 40
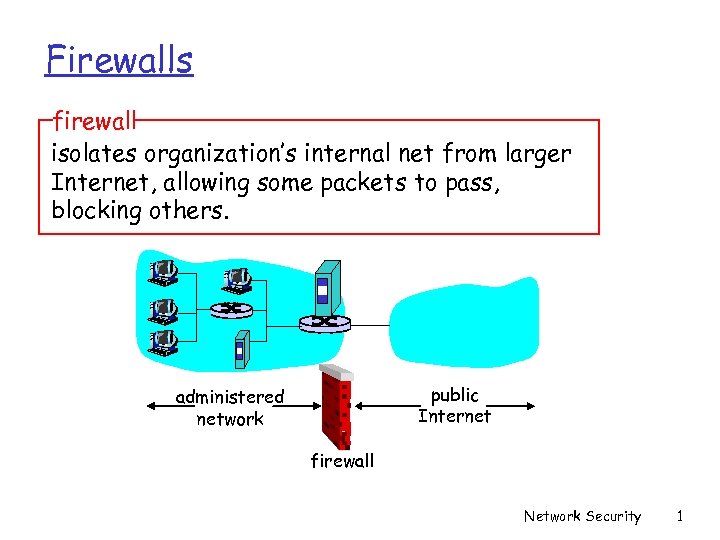 Firewalls firewall isolates organization’s internal net from larger Internet, allowing some packets to pass, blocking others. public Internet administered network firewall Network Security 1
Firewalls firewall isolates organization’s internal net from larger Internet, allowing some packets to pass, blocking others. public Internet administered network firewall Network Security 1
 Firewalls: Why Prevent denial of service attacks: m Denial-of-Service (Do. S) attack: • Send many fake requests to congest link or consume server resource (CPU, memory) m SYN flooding: • attacker sends many SYNs to victim; victim has to allocate connection resource; victim has no resource left for real connection requests any more. • Usually with spoofed source IP address Prevent illegal modification/access of internal data. m e. g. , attacker replaces CIA’s homepage with something else Network Security 2
Firewalls: Why Prevent denial of service attacks: m Denial-of-Service (Do. S) attack: • Send many fake requests to congest link or consume server resource (CPU, memory) m SYN flooding: • attacker sends many SYNs to victim; victim has to allocate connection resource; victim has no resource left for real connection requests any more. • Usually with spoofed source IP address Prevent illegal modification/access of internal data. m e. g. , attacker replaces CIA’s homepage with something else Network Security 2
 Firewalls: Why Allow only authorized access to inside network m m Set of authenticated users Set of authorized IP addresses Two types of firewalls: m application-level • Checking application level data m packet-filtering • Checking TCP or IP packets only Network Security 3
Firewalls: Why Allow only authorized access to inside network m m Set of authenticated users Set of authorized IP addresses Two types of firewalls: m application-level • Checking application level data m packet-filtering • Checking TCP or IP packets only Network Security 3
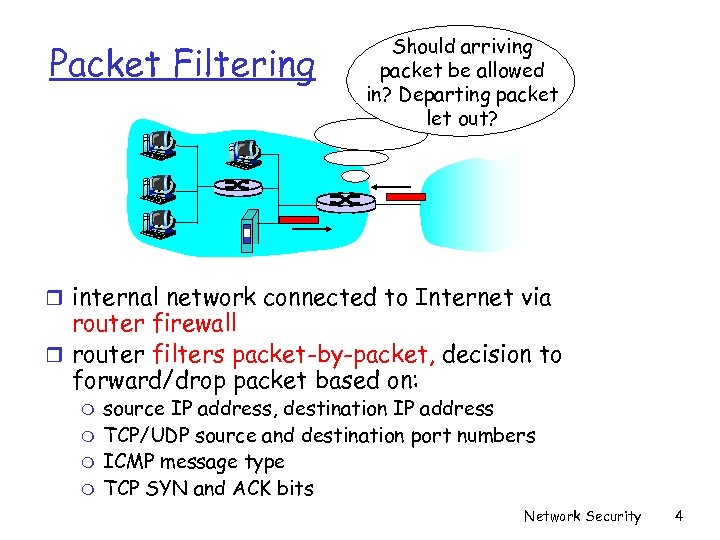 Packet Filtering Should arriving packet be allowed in? Departing packet let out? r internal network connected to Internet via router firewall r router filters packet-by-packet, decision to forward/drop packet based on: m m source IP address, destination IP address TCP/UDP source and destination port numbers ICMP message type TCP SYN and ACK bits Network Security 4
Packet Filtering Should arriving packet be allowed in? Departing packet let out? r internal network connected to Internet via router firewall r router filters packet-by-packet, decision to forward/drop packet based on: m m source IP address, destination IP address TCP/UDP source and destination port numbers ICMP message type TCP SYN and ACK bits Network Security 4
 Packet Filtering r Example 1: block incoming and outgoing datagrams with IP protocol field = 17 and with either source or dest port = 23. m All incoming and outgoing UDP flows and telnet connections are blocked. r Example 2: Block inbound TCP segments with SYN=1. m Prevents external clients from making TCP connections with internal clients, but allows internal clients to connect to outside. Example of Windows XP service pack 2 firewall (control panel security center windows firewall) Network Security 5
Packet Filtering r Example 1: block incoming and outgoing datagrams with IP protocol field = 17 and with either source or dest port = 23. m All incoming and outgoing UDP flows and telnet connections are blocked. r Example 2: Block inbound TCP segments with SYN=1. m Prevents external clients from making TCP connections with internal clients, but allows internal clients to connect to outside. Example of Windows XP service pack 2 firewall (control panel security center windows firewall) Network Security 5
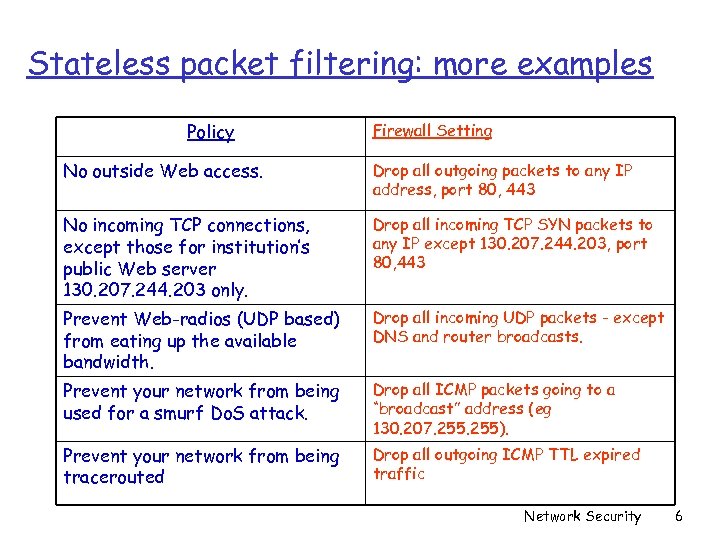 Stateless packet filtering: more examples Policy Firewall Setting No outside Web access. Drop all outgoing packets to any IP address, port 80, 443 No incoming TCP connections, except those for institution’s public Web server 130. 207. 244. 203 only. Drop all incoming TCP SYN packets to any IP except 130. 207. 244. 203, port 80, 443 Prevent Web-radios (UDP based) from eating up the available bandwidth. Drop all incoming UDP packets - except DNS and router broadcasts. Prevent your network from being used for a smurf Do. S attack. Drop all ICMP packets going to a “broadcast” address (eg 130. 207. 255). Prevent your network from being tracerouted Drop all outgoing ICMP TTL expired traffic Network Security 6
Stateless packet filtering: more examples Policy Firewall Setting No outside Web access. Drop all outgoing packets to any IP address, port 80, 443 No incoming TCP connections, except those for institution’s public Web server 130. 207. 244. 203 only. Drop all incoming TCP SYN packets to any IP except 130. 207. 244. 203, port 80, 443 Prevent Web-radios (UDP based) from eating up the available bandwidth. Drop all incoming UDP packets - except DNS and router broadcasts. Prevent your network from being used for a smurf Do. S attack. Drop all ICMP packets going to a “broadcast” address (eg 130. 207. 255). Prevent your network from being tracerouted Drop all outgoing ICMP TTL expired traffic Network Security 6
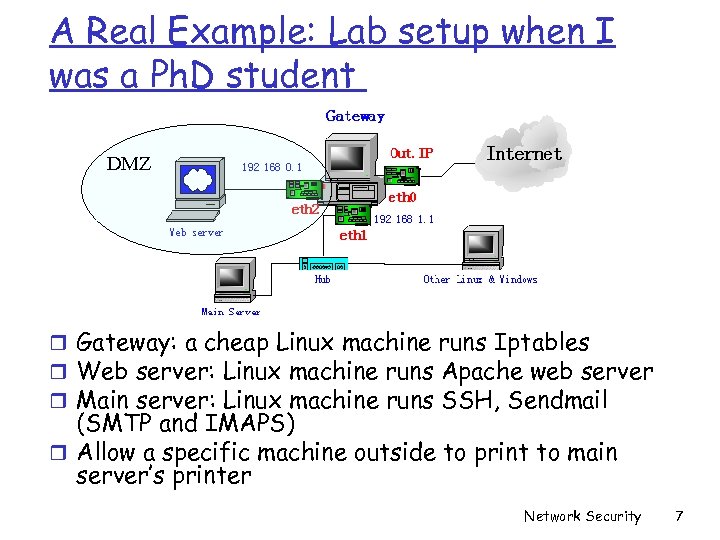 A Real Example: Lab setup when I was a Ph. D student DMZ r Gateway: a cheap Linux machine runs Iptables r Web server: Linux machine runs Apache web server r Main server: Linux machine runs SSH, Sendmail (SMTP and IMAPS) r Allow a specific machine outside to print to main server’s printer Network Security 7
A Real Example: Lab setup when I was a Ph. D student DMZ r Gateway: a cheap Linux machine runs Iptables r Web server: Linux machine runs Apache web server r Main server: Linux machine runs SSH, Sendmail (SMTP and IMAPS) r Allow a specific machine outside to print to main server’s printer Network Security 7
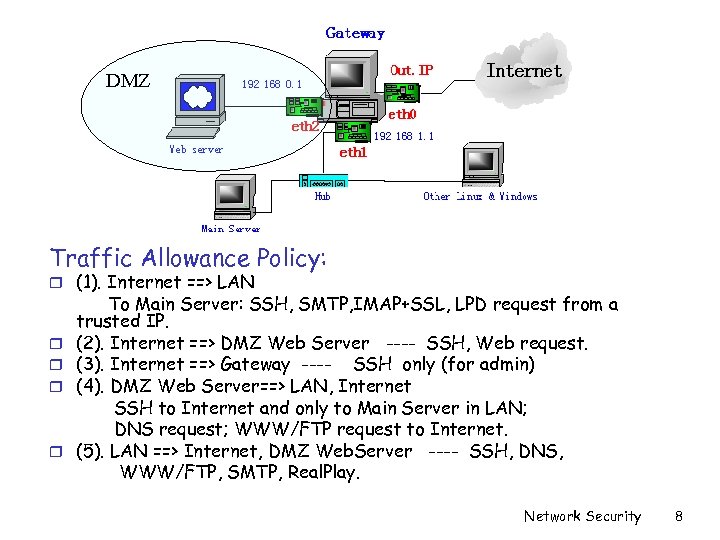 DMZ Traffic Allowance Policy: r (1). Internet ==> LAN r r To Main Server: SSH, SMTP, IMAP+SSL, LPD request from a trusted IP. (2). Internet ==> DMZ Web Server ---- SSH, Web request. (3). Internet ==> Gateway ---- SSH only (for admin) (4). DMZ Web Server==> LAN, Internet SSH to Internet and only to Main Server in LAN; DNS request; WWW/FTP request to Internet. (5). LAN ==> Internet, DMZ Web. Server ---- SSH, DNS, WWW/FTP, SMTP, Real. Play. Network Security 8
DMZ Traffic Allowance Policy: r (1). Internet ==> LAN r r To Main Server: SSH, SMTP, IMAP+SSL, LPD request from a trusted IP. (2). Internet ==> DMZ Web Server ---- SSH, Web request. (3). Internet ==> Gateway ---- SSH only (for admin) (4). DMZ Web Server==> LAN, Internet SSH to Internet and only to Main Server in LAN; DNS request; WWW/FTP request to Internet. (5). LAN ==> Internet, DMZ Web. Server ---- SSH, DNS, WWW/FTP, SMTP, Real. Play. Network Security 8
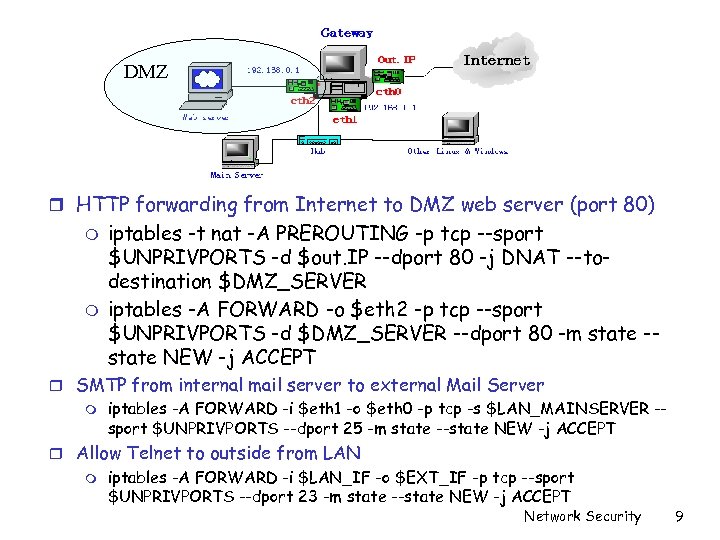 DMZ r HTTP forwarding from Internet to DMZ web server (port 80) m m iptables -t nat -A PREROUTING -p tcp --sport $UNPRIVPORTS -d $out. IP --dport 80 -j DNAT --todestination $DMZ_SERVER iptables -A FORWARD -o $eth 2 -p tcp --sport $UNPRIVPORTS -d $DMZ_SERVER --dport 80 -m state -state NEW -j ACCEPT r SMTP from internal mail server to external Mail Server m iptables -A FORWARD -i $eth 1 -o $eth 0 -p tcp -s $LAN_MAINSERVER -sport $UNPRIVPORTS --dport 25 -m state --state NEW -j ACCEPT r Allow Telnet to outside from LAN m iptables -A FORWARD -i $LAN_IF -o $EXT_IF -p tcp --sport $UNPRIVPORTS --dport 23 -m state --state NEW -j ACCEPT Network Security 9
DMZ r HTTP forwarding from Internet to DMZ web server (port 80) m m iptables -t nat -A PREROUTING -p tcp --sport $UNPRIVPORTS -d $out. IP --dport 80 -j DNAT --todestination $DMZ_SERVER iptables -A FORWARD -o $eth 2 -p tcp --sport $UNPRIVPORTS -d $DMZ_SERVER --dport 80 -m state -state NEW -j ACCEPT r SMTP from internal mail server to external Mail Server m iptables -A FORWARD -i $eth 1 -o $eth 0 -p tcp -s $LAN_MAINSERVER -sport $UNPRIVPORTS --dport 25 -m state --state NEW -j ACCEPT r Allow Telnet to outside from LAN m iptables -A FORWARD -i $LAN_IF -o $EXT_IF -p tcp --sport $UNPRIVPORTS --dport 23 -m state --state NEW -j ACCEPT Network Security 9
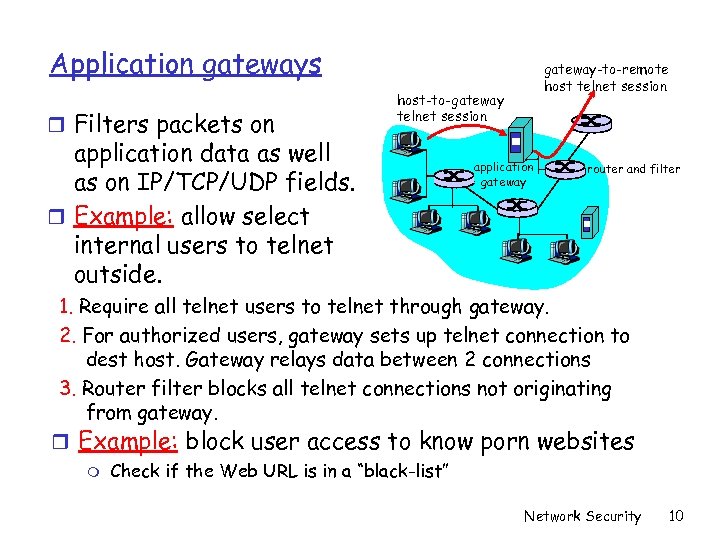 Application gateways r Filters packets on gateway-to-remote host telnet session host-to-gateway telnet session application data as well as on IP/TCP/UDP fields. r Example: allow select internal users to telnet outside. application gateway router and filter 1. Require all telnet users to telnet through gateway. 2. For authorized users, gateway sets up telnet connection to dest host. Gateway relays data between 2 connections 3. Router filter blocks all telnet connections not originating from gateway. r Example: block user access to know porn websites m Check if the Web URL is in a “black-list” Network Security 10
Application gateways r Filters packets on gateway-to-remote host telnet session host-to-gateway telnet session application data as well as on IP/TCP/UDP fields. r Example: allow select internal users to telnet outside. application gateway router and filter 1. Require all telnet users to telnet through gateway. 2. For authorized users, gateway sets up telnet connection to dest host. Gateway relays data between 2 connections 3. Router filter blocks all telnet connections not originating from gateway. r Example: block user access to know porn websites m Check if the Web URL is in a “black-list” Network Security 10
 r. Let me demonstrate how a real wireless router provides: m. NAT m. Access Control, security m. Firewall Network Security 11
r. Let me demonstrate how a real wireless router provides: m. NAT m. Access Control, security m. Firewall Network Security 11
 Limitations of firewalls and gateways r IP spoofing: router can’t know if data “really” comes from claimed source m m SYN flood attack UDP traffic r client software must know how to contact application gateway. m e. g. , must set IP address of proxy in Web browser r Speed constraint on high -bandwidth link m Application-level firewall is time consuming r filters often use all or nothing policy for UDP m m Usually most incoming UDP ports are blocked The trouble caused to realtime Internet video Network Security 12
Limitations of firewalls and gateways r IP spoofing: router can’t know if data “really” comes from claimed source m m SYN flood attack UDP traffic r client software must know how to contact application gateway. m e. g. , must set IP address of proxy in Web browser r Speed constraint on high -bandwidth link m Application-level firewall is time consuming r filters often use all or nothing policy for UDP m m Usually most incoming UDP ports are blocked The trouble caused to realtime Internet video Network Security 12
 Limitations of firewalls and gateways r tradeoff: degree of communication with outside world, level of security r Trend --- remote office m Blurred boundary between inside <-> outside m Employee laptop threat r many highly protected sites still suffer from attacks Network Security 13
Limitations of firewalls and gateways r tradeoff: degree of communication with outside world, level of security r Trend --- remote office m Blurred boundary between inside <-> outside m Employee laptop threat r many highly protected sites still suffer from attacks Network Security 13
 Internet security threats Mapping: m before attacking: “case the joint” – find out what services are implemented on network m Use ping to determine what hosts have addresses on network m Port-scanning: try to establish TCP connection to each port in sequence (see what happens) m nmap (http: //www. insecure. org/nmap/) mapper: “network exploration and security auditing” Countermeasures? Network Security 14
Internet security threats Mapping: m before attacking: “case the joint” – find out what services are implemented on network m Use ping to determine what hosts have addresses on network m Port-scanning: try to establish TCP connection to each port in sequence (see what happens) m nmap (http: //www. insecure. org/nmap/) mapper: “network exploration and security auditing” Countermeasures? Network Security 14
 Internet security threats Mapping: countermeasures m record traffic entering network m look for suspicious activity (IP addresses, pots being scanned sequentially) m Firewall to block incoming TCP/SYN to ports or computers not providing the services m Block ping traffic Network Security 15
Internet security threats Mapping: countermeasures m record traffic entering network m look for suspicious activity (IP addresses, pots being scanned sequentially) m Firewall to block incoming TCP/SYN to ports or computers not providing the services m Block ping traffic Network Security 15
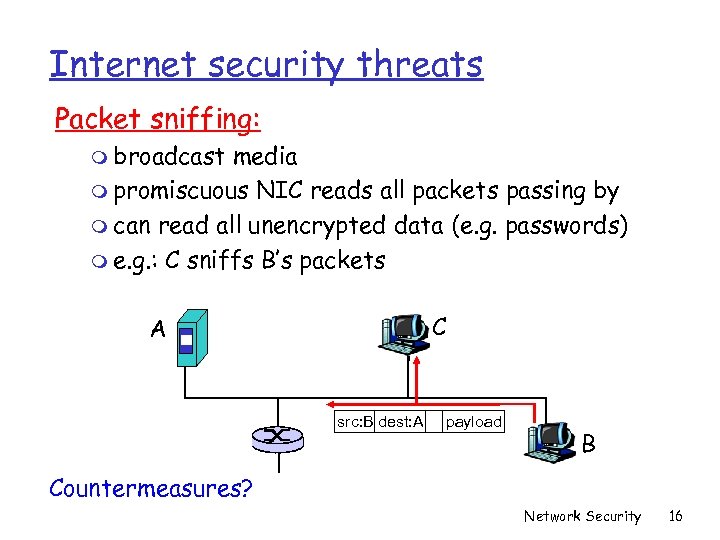 Internet security threats Packet sniffing: m broadcast media m promiscuous NIC reads all packets passing by m can read all unencrypted data (e. g. passwords) m e. g. : C sniffs B’s packets C A src: B dest: A payload B Countermeasures? Network Security 16
Internet security threats Packet sniffing: m broadcast media m promiscuous NIC reads all packets passing by m can read all unencrypted data (e. g. passwords) m e. g. : C sniffs B’s packets C A src: B dest: A payload B Countermeasures? Network Security 16
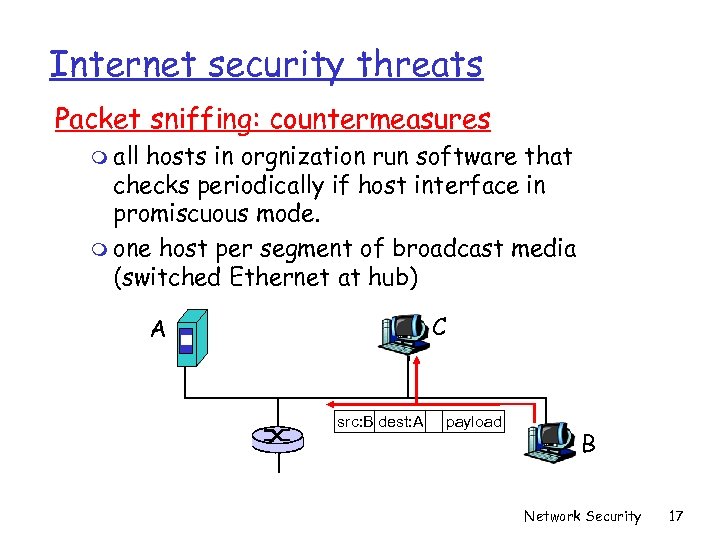 Internet security threats Packet sniffing: countermeasures m all hosts in orgnization run software that checks periodically if host interface in promiscuous mode. m one host per segment of broadcast media (switched Ethernet at hub) C A src: B dest: A payload B Network Security 17
Internet security threats Packet sniffing: countermeasures m all hosts in orgnization run software that checks periodically if host interface in promiscuous mode. m one host per segment of broadcast media (switched Ethernet at hub) C A src: B dest: A payload B Network Security 17
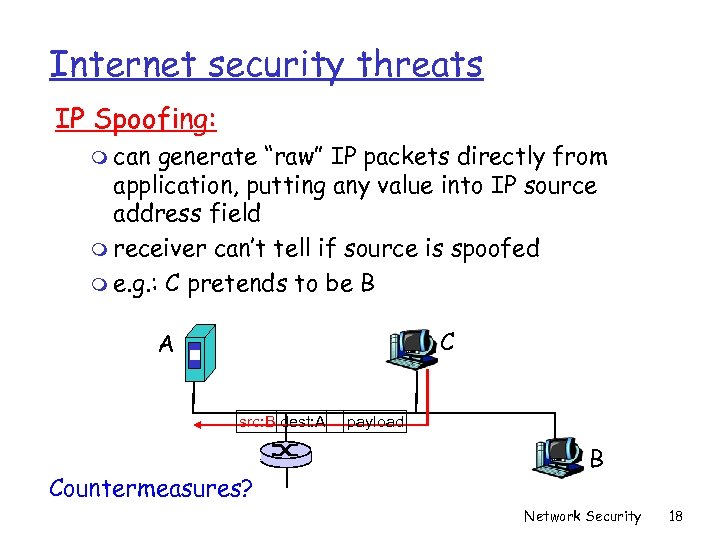 Internet security threats IP Spoofing: m can generate “raw” IP packets directly from application, putting any value into IP source address field m receiver can’t tell if source is spoofed m e. g. : C pretends to be B C A src: B dest: A Countermeasures? payload B Network Security 18
Internet security threats IP Spoofing: m can generate “raw” IP packets directly from application, putting any value into IP source address field m receiver can’t tell if source is spoofed m e. g. : C pretends to be B C A src: B dest: A Countermeasures? payload B Network Security 18
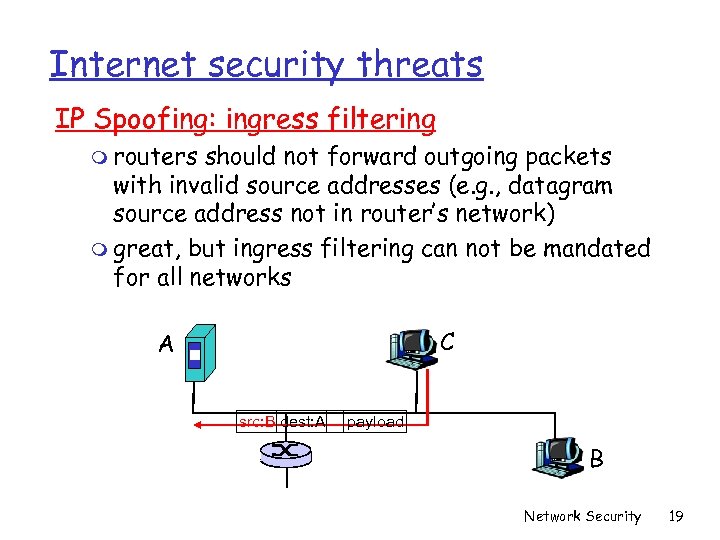 Internet security threats IP Spoofing: ingress filtering m routers should not forward outgoing packets with invalid source addresses (e. g. , datagram source address not in router’s network) m great, but ingress filtering can not be mandated for all networks C A src: B dest: A payload B Network Security 19
Internet security threats IP Spoofing: ingress filtering m routers should not forward outgoing packets with invalid source addresses (e. g. , datagram source address not in router’s network) m great, but ingress filtering can not be mandated for all networks C A src: B dest: A payload B Network Security 19
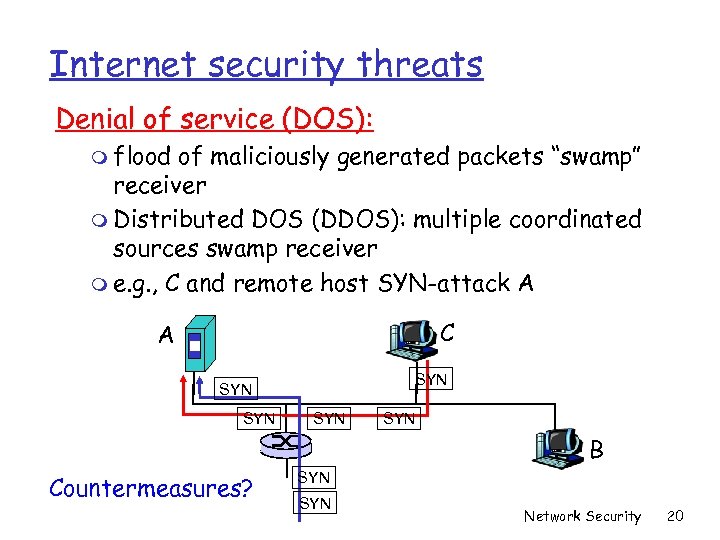 Internet security threats Denial of service (DOS): m flood of maliciously generated packets “swamp” receiver m Distributed DOS (DDOS): multiple coordinated sources swamp receiver m e. g. , C and remote host SYN-attack A C A SYN SYN SYN B Countermeasures? SYN Network Security 20
Internet security threats Denial of service (DOS): m flood of maliciously generated packets “swamp” receiver m Distributed DOS (DDOS): multiple coordinated sources swamp receiver m e. g. , C and remote host SYN-attack A C A SYN SYN SYN B Countermeasures? SYN Network Security 20
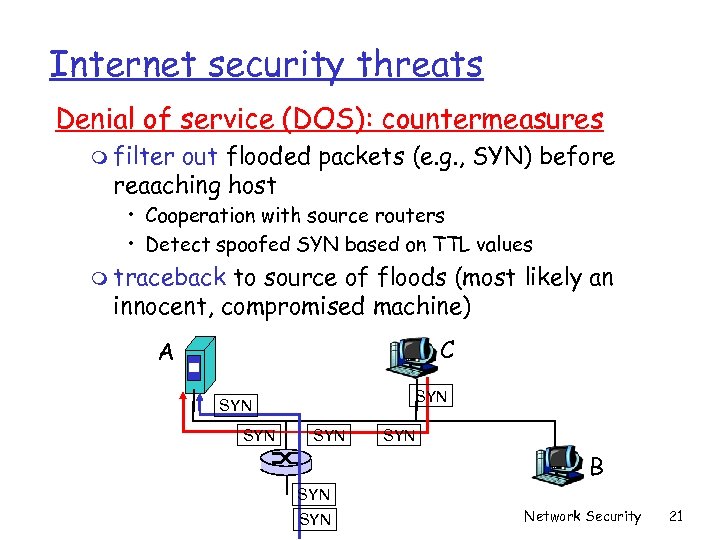 Internet security threats Denial of service (DOS): countermeasures m filter out flooded packets (e. g. , SYN) before reaaching host • Cooperation with source routers • Detect spoofed SYN based on TTL values m traceback to source of floods (most likely an innocent, compromised machine) C A SYN SYN SYN B SYN Network Security 21
Internet security threats Denial of service (DOS): countermeasures m filter out flooded packets (e. g. , SYN) before reaaching host • Cooperation with source routers • Detect spoofed SYN based on TTL values m traceback to source of floods (most likely an innocent, compromised machine) C A SYN SYN SYN B SYN Network Security 21
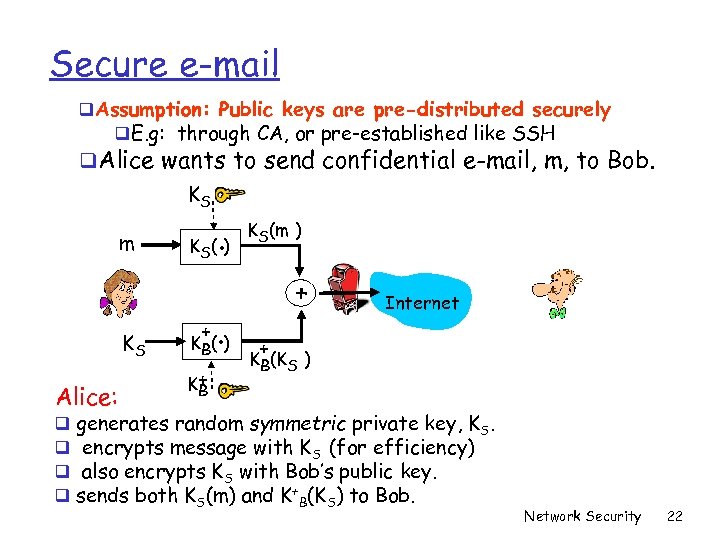 Secure e-mail q. Assumption: Public keys are pre-distributed securely q. E. g: through CA, or pre-established like SSH q. Alice wants to send confidential e-mail, m, to Bob. KS m KS Alice: q q . K S( ) + . K B( ) K+ B KS(m ) + Internet + KB(KS ) generates random symmetric private key, KS. encrypts message with KS (for efficiency) also encrypts KS with Bob’s public key. sends both KS(m) and K+B(KS) to Bob. Network Security 22
Secure e-mail q. Assumption: Public keys are pre-distributed securely q. E. g: through CA, or pre-established like SSH q. Alice wants to send confidential e-mail, m, to Bob. KS m KS Alice: q q . K S( ) + . K B( ) K+ B KS(m ) + Internet + KB(KS ) generates random symmetric private key, KS. encrypts message with KS (for efficiency) also encrypts KS with Bob’s public key. sends both KS(m) and K+B(KS) to Bob. Network Security 22
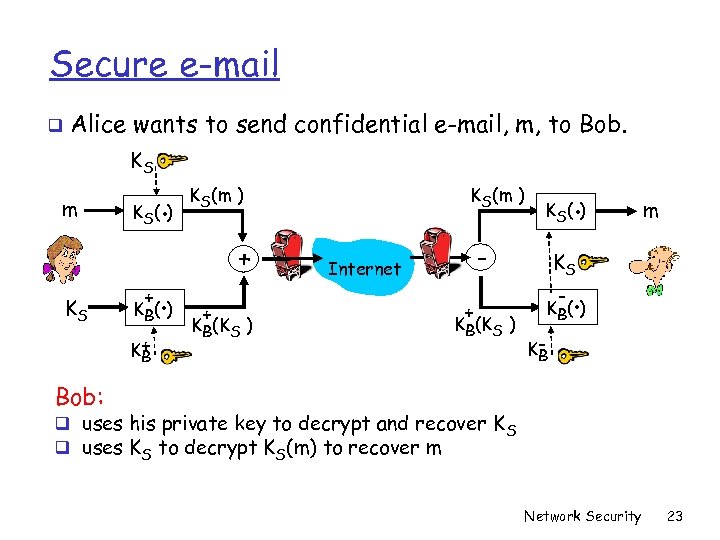 Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + . K B( ) K+ B KS(m ) + + KB(KS ) . K S( ) - Internet + KB(KS ) m KS - . K B( ) KB Bob: q uses his private key to decrypt and recover K S q uses KS to decrypt KS(m) to recover m Network Security 23
Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + . K B( ) K+ B KS(m ) + + KB(KS ) . K S( ) - Internet + KB(KS ) m KS - . K B( ) KB Bob: q uses his private key to decrypt and recover K S q uses KS to decrypt KS(m) to recover m Network Security 23
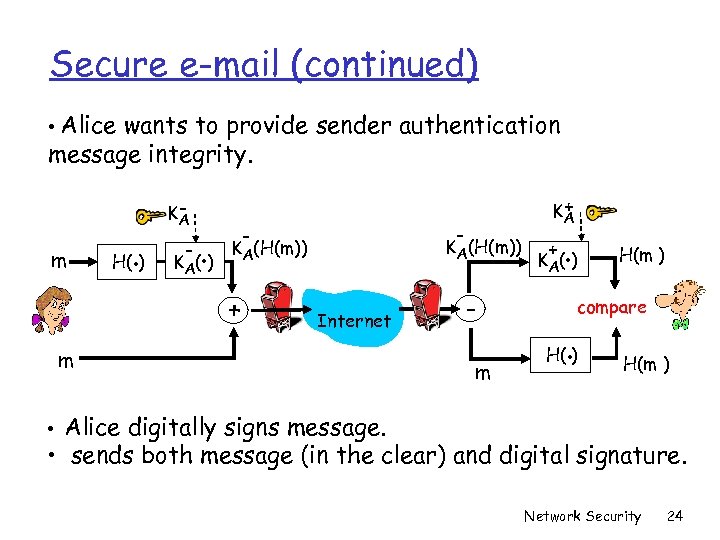 Secure e-mail (continued) • Alice wants to provide sender authentication message integrity. m H(. ) KA - . K A( ) - - KA(H(m)) + + KA Internet m m + . K A( ) H(m ) compare . H( ) H(m ) • Alice digitally signs message. • sends both message (in the clear) and digital signature. Network Security 24
Secure e-mail (continued) • Alice wants to provide sender authentication message integrity. m H(. ) KA - . K A( ) - - KA(H(m)) + + KA Internet m m + . K A( ) H(m ) compare . H( ) H(m ) • Alice digitally signs message. • sends both message (in the clear) and digital signature. Network Security 24
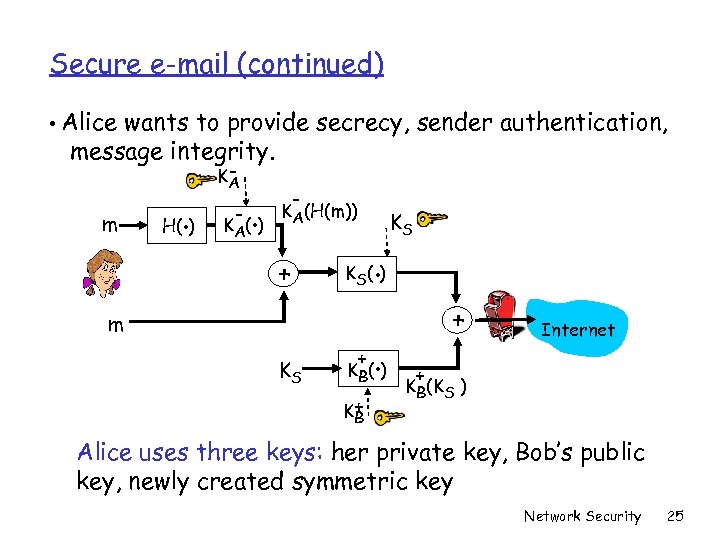 Secure e-mail (continued) • Alice wants to provide secrecy, sender authentication, message integrity. m . H( ) KA - . K A( ) - KA(H(m)) + . K S( ) m KS KS + . K B( ) K+ B + Internet + KB(KS ) Alice uses three keys: her private key, Bob’s public key, newly created symmetric key Network Security 25
Secure e-mail (continued) • Alice wants to provide secrecy, sender authentication, message integrity. m . H( ) KA - . K A( ) - KA(H(m)) + . K S( ) m KS KS + . K B( ) K+ B + Internet + KB(KS ) Alice uses three keys: her private key, Bob’s public key, newly created symmetric key Network Security 25
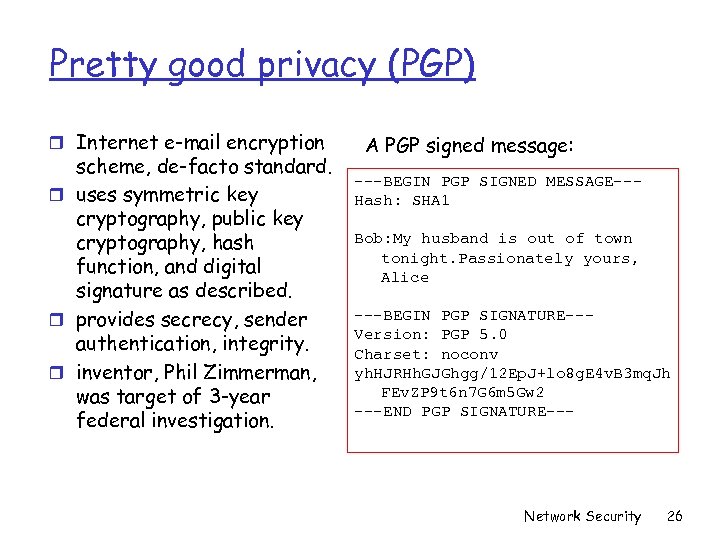 Pretty good privacy (PGP) r Internet e-mail encryption scheme, de-facto standard. r uses symmetric key cryptography, public key cryptography, hash function, and digital signature as described. r provides secrecy, sender authentication, integrity. r inventor, Phil Zimmerman, was target of 3 -year federal investigation. A PGP signed message: ---BEGIN PGP SIGNED MESSAGE--Hash: SHA 1 Bob: My husband is out of town tonight. Passionately yours, Alice ---BEGIN PGP SIGNATURE--Version: PGP 5. 0 Charset: noconv yh. HJRHh. GJGhgg/12 Ep. J+lo 8 g. E 4 v. B 3 mq. Jh FEv. ZP 9 t 6 n 7 G 6 m 5 Gw 2 ---END PGP SIGNATURE--- Network Security 26
Pretty good privacy (PGP) r Internet e-mail encryption scheme, de-facto standard. r uses symmetric key cryptography, public key cryptography, hash function, and digital signature as described. r provides secrecy, sender authentication, integrity. r inventor, Phil Zimmerman, was target of 3 -year federal investigation. A PGP signed message: ---BEGIN PGP SIGNED MESSAGE--Hash: SHA 1 Bob: My husband is out of town tonight. Passionately yours, Alice ---BEGIN PGP SIGNATURE--Version: PGP 5. 0 Charset: noconv yh. HJRHh. GJGhgg/12 Ep. J+lo 8 g. E 4 v. B 3 mq. Jh FEv. ZP 9 t 6 n 7 G 6 m 5 Gw 2 ---END PGP SIGNATURE--- Network Security 26
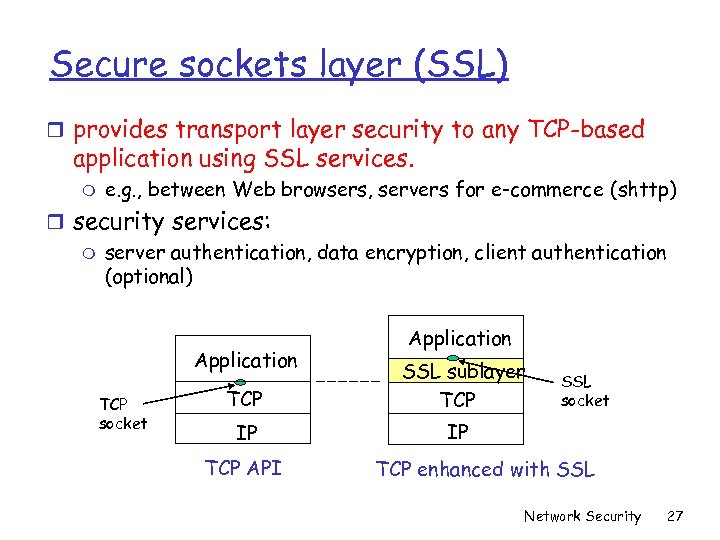 Secure sockets layer (SSL) r provides transport layer security to any TCP-based application using SSL services. m e. g. , between Web browsers, servers for e-commerce (shttp) r security services: m server authentication, data encryption, client authentication (optional) Application TCP socket Application TCP SSL sublayer TCP IP IP TCP API SSL socket TCP enhanced with SSL Network Security 27
Secure sockets layer (SSL) r provides transport layer security to any TCP-based application using SSL services. m e. g. , between Web browsers, servers for e-commerce (shttp) r security services: m server authentication, data encryption, client authentication (optional) Application TCP socket Application TCP SSL sublayer TCP IP IP TCP API SSL socket TCP enhanced with SSL Network Security 27
 Secure sockets layer (SSL) r transport layer security to any TCPbased app using SSL services. r used between Web browsers, servers for e-commerce (shttp). r security services: m m m server authentication data encryption client authentication (optional) r server authentication: m SSL-enabled browser includes public keys for trusted CAs. m Browser requests server certificate, issued by trusted CA. m Browser uses CA’s public key to extract server’s public key from certificate. r check your browser’s security menu to see its trusted CAs. Network Security 28
Secure sockets layer (SSL) r transport layer security to any TCPbased app using SSL services. r used between Web browsers, servers for e-commerce (shttp). r security services: m m m server authentication data encryption client authentication (optional) r server authentication: m SSL-enabled browser includes public keys for trusted CAs. m Browser requests server certificate, issued by trusted CA. m Browser uses CA’s public key to extract server’s public key from certificate. r check your browser’s security menu to see its trusted CAs. Network Security 28
 SSL (continued) Encrypted SSL session: r Browser generates symmetric session key, encrypts it with server’s public key, sends encrypted key to server. r Using private key, server decrypts session key. r Browser, server know session key m All data sent into TCP socket (by client or server) encrypted with session key. r SSL: basis of IETF Transport Layer Security (TLS). r SSL can be used for non-Web applications, e. g. , IMAP. r Client authentication can be done with client certificates. m Not widely used since too many clients Network Security 29
SSL (continued) Encrypted SSL session: r Browser generates symmetric session key, encrypts it with server’s public key, sends encrypted key to server. r Using private key, server decrypts session key. r Browser, server know session key m All data sent into TCP socket (by client or server) encrypted with session key. r SSL: basis of IETF Transport Layer Security (TLS). r SSL can be used for non-Web applications, e. g. , IMAP. r Client authentication can be done with client certificates. m Not widely used since too many clients Network Security 29
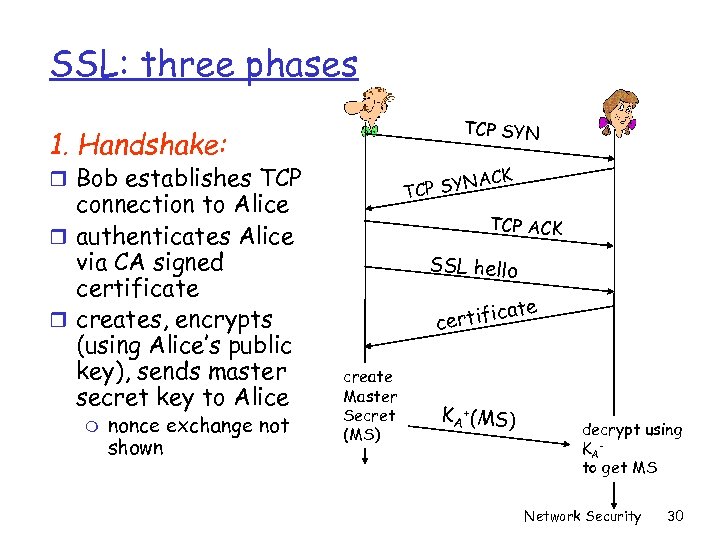 SSL: three phases TCP SYN 1. Handshake: r Bob establishes TCP connection to Alice r authenticates Alice via CA signed certificate r creates, encrypts (using Alice’s public key), sends master secret key to Alice m nonce exchange not shown ACK P SYN TC TCP ACK SSL hello te ca certifi create Master Secret (MS) KA +(MS) decrypt using KA to get MS Network Security 30
SSL: three phases TCP SYN 1. Handshake: r Bob establishes TCP connection to Alice r authenticates Alice via CA signed certificate r creates, encrypts (using Alice’s public key), sends master secret key to Alice m nonce exchange not shown ACK P SYN TC TCP ACK SSL hello te ca certifi create Master Secret (MS) KA +(MS) decrypt using KA to get MS Network Security 30
 SSL: three phases 2. Key Derivation: r Alice, Bob use shared secret (MS) to generate 4 keys: m m EB: Bob->Alice data encryption key EA: Alice->Bob data encryption key MB: Bob->Alice MAC key MA: Alice->Bob MAC key r encryption and MAC algorithms negotiable between Bob, Alice r why 4 keys? m m Different keys by each person Different keys for encryption and integrity checking Network Security 31
SSL: three phases 2. Key Derivation: r Alice, Bob use shared secret (MS) to generate 4 keys: m m EB: Bob->Alice data encryption key EA: Alice->Bob data encryption key MB: Bob->Alice MAC key MA: Alice->Bob MAC key r encryption and MAC algorithms negotiable between Bob, Alice r why 4 keys? m m Different keys by each person Different keys for encryption and integrity checking Network Security 31
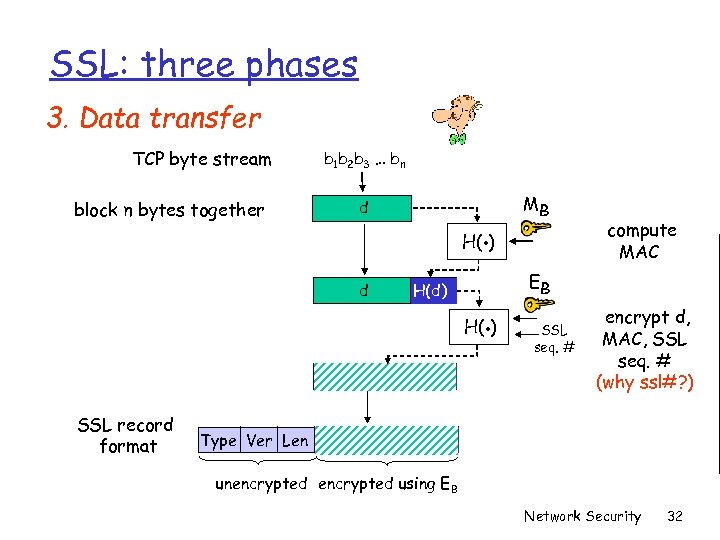 SSL: three phases 3. Data transfer TCP byte stream block n bytes together b 1 b 2 b 3 … bn d . MB H( ) d H(d) . H( ) d SSL record format Type Ver Len H(d) d compute MAC EB SSL seq. # encrypt d, MAC, SSL seq. # (why ssl#? ) H(d) unencrypted using EB Network Security 32
SSL: three phases 3. Data transfer TCP byte stream block n bytes together b 1 b 2 b 3 … bn d . MB H( ) d H(d) . H( ) d SSL record format Type Ver Len H(d) d compute MAC EB SSL seq. # encrypt d, MAC, SSL seq. # (why ssl#? ) H(d) unencrypted using EB Network Security 32
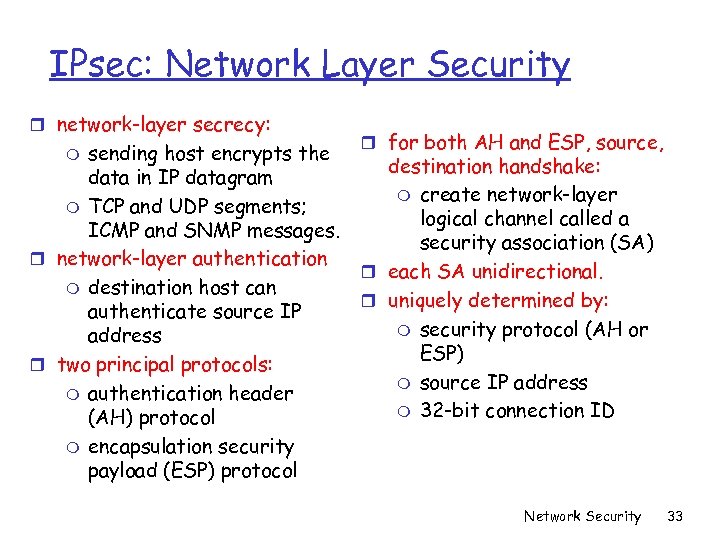 IPsec: Network Layer Security r network-layer secrecy: sending host encrypts the data in IP datagram m TCP and UDP segments; ICMP and SNMP messages. r network-layer authentication m destination host can authenticate source IP address r two principal protocols: m authentication header (AH) protocol m encapsulation security payload (ESP) protocol m r for both AH and ESP, source, destination handshake: m create network-layer logical channel called a security association (SA) r each SA unidirectional. r uniquely determined by: m security protocol (AH or ESP) m source IP address m 32 -bit connection ID Network Security 33
IPsec: Network Layer Security r network-layer secrecy: sending host encrypts the data in IP datagram m TCP and UDP segments; ICMP and SNMP messages. r network-layer authentication m destination host can authenticate source IP address r two principal protocols: m authentication header (AH) protocol m encapsulation security payload (ESP) protocol m r for both AH and ESP, source, destination handshake: m create network-layer logical channel called a security association (SA) r each SA unidirectional. r uniquely determined by: m security protocol (AH or ESP) m source IP address m 32 -bit connection ID Network Security 33
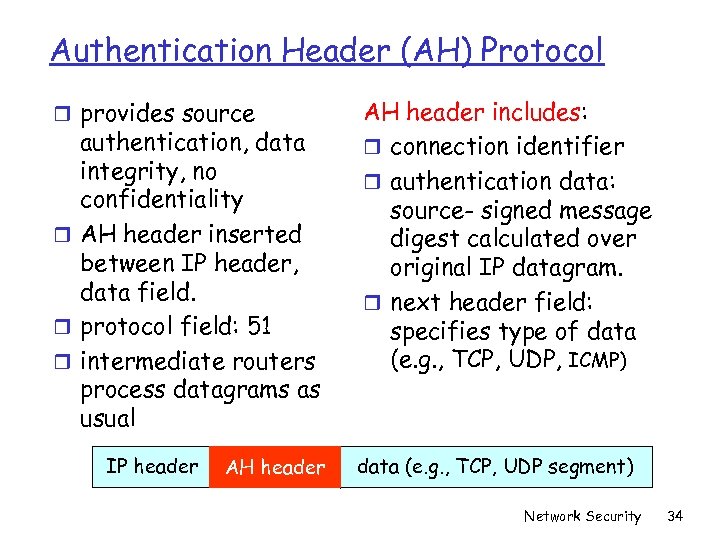 Authentication Header (AH) Protocol r provides source authentication, data integrity, no confidentiality r AH header inserted between IP header, data field. r protocol field: 51 r intermediate routers process datagrams as usual IP header AH header includes: r connection identifier r authentication data: source- signed message digest calculated over original IP datagram. r next header field: specifies type of data (e. g. , TCP, UDP, ICMP) data (e. g. , TCP, UDP segment) Network Security 34
Authentication Header (AH) Protocol r provides source authentication, data integrity, no confidentiality r AH header inserted between IP header, data field. r protocol field: 51 r intermediate routers process datagrams as usual IP header AH header includes: r connection identifier r authentication data: source- signed message digest calculated over original IP datagram. r next header field: specifies type of data (e. g. , TCP, UDP, ICMP) data (e. g. , TCP, UDP segment) Network Security 34
 IEEE 802. 11 security r Packet sniffing is unavoidable r War-driving: drive around Bay area, see what 802. 11 networks available? m More than 9000 accessible from public roadways m 85% use no encryption/authentication m packet-sniffing and various attacks easy! r Wired Equivalent Privacy (WEP): authentication as in protocol ap 4. 0 (require shared symmetric key) m host requests authentication from access point sends 128 bit nonce m host encrypts nonce using shared symmetric key m access point decrypts nonce, authenticates host Network Security 35
IEEE 802. 11 security r Packet sniffing is unavoidable r War-driving: drive around Bay area, see what 802. 11 networks available? m More than 9000 accessible from public roadways m 85% use no encryption/authentication m packet-sniffing and various attacks easy! r Wired Equivalent Privacy (WEP): authentication as in protocol ap 4. 0 (require shared symmetric key) m host requests authentication from access point sends 128 bit nonce m host encrypts nonce using shared symmetric key m access point decrypts nonce, authenticates host Network Security 35
 IEEE 802. 11 security r Wired Equivalent Privacy (WEP): data encryption m Host/AP share 40 bit symmetric key (semipermanent) m Host appends 24 -bit initialization vector (IV) to create 64 -bit key • IV is equivalent to a “nonce” bit key used to generate stream of keys, ki. IV (using RC 4 stream cipher) IV m ki used to encrypt i-th byte, di, in frame: ci = di XOR ki. IV m IV and encrypted bytes, ci sent in frame m 64 Network Security 36
IEEE 802. 11 security r Wired Equivalent Privacy (WEP): data encryption m Host/AP share 40 bit symmetric key (semipermanent) m Host appends 24 -bit initialization vector (IV) to create 64 -bit key • IV is equivalent to a “nonce” bit key used to generate stream of keys, ki. IV (using RC 4 stream cipher) IV m ki used to encrypt i-th byte, di, in frame: ci = di XOR ki. IV m IV and encrypted bytes, ci sent in frame m 64 Network Security 36
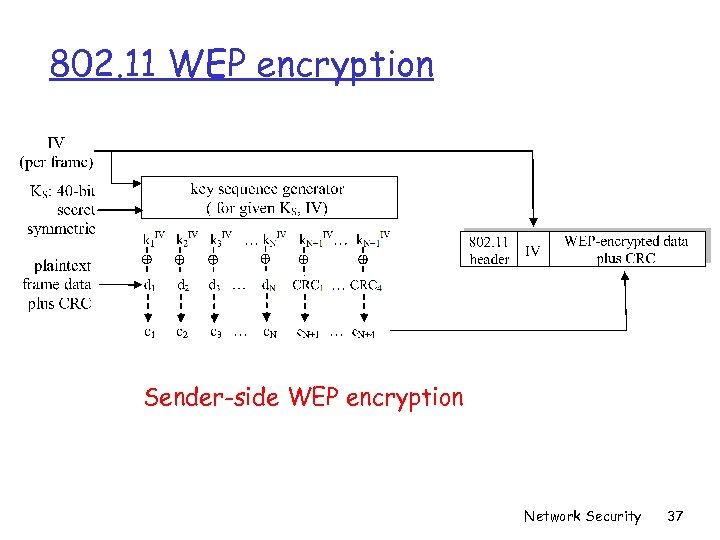 802. 11 WEP encryption Sender-side WEP encryption Network Security 37
802. 11 WEP encryption Sender-side WEP encryption Network Security 37
 802. 11 WEP Security Concern r 40 bits in encryption is too short r RC 4 is not properly used in 802. 11 r A more secure protocol is just standardized, 802. 11 i Network Security 38
802. 11 WEP Security Concern r 40 bits in encryption is too short r RC 4 is not properly used in 802. 11 r A more secure protocol is just standardized, 802. 11 i Network Security 38
 Breaking 802. 11 WEP encryption security hole: r 24 -bit IV, one IV per frame, -> IV’s eventually reused r IV transmitted in plaintext -> IV reuse detected r attack: m Trudy causes Alice to encrypt known plaintext d 1 d 2 d 3 d 4 … IV m Trudy sees: ci = di XOR ki knows ci di, so can compute ki. IV IV m Trudy knows encrypting key sequence k 1 k 2 k 3 … m Next time IV is used, Trudy can decrypt! m Trudy Network Security 39
Breaking 802. 11 WEP encryption security hole: r 24 -bit IV, one IV per frame, -> IV’s eventually reused r IV transmitted in plaintext -> IV reuse detected r attack: m Trudy causes Alice to encrypt known plaintext d 1 d 2 d 3 d 4 … IV m Trudy sees: ci = di XOR ki knows ci di, so can compute ki. IV IV m Trudy knows encrypting key sequence k 1 k 2 k 3 … m Next time IV is used, Trudy can decrypt! m Trudy Network Security 39
 Network Security (summary) Basic techniques…. . . m cryptography (symmetric and public) m authentication m message integrity m key distribution …. used in many different security scenarios m secure email m secure transport (SSL) m IP sec m 802. 11 security Network Security 40
Network Security (summary) Basic techniques…. . . m cryptography (symmetric and public) m authentication m message integrity m key distribution …. used in many different security scenarios m secure email m secure transport (SSL) m IP sec m 802. 11 security Network Security 40


