52ec8cc91a9332030e2d7466e585ecd4.ppt
- Количество слайдов: 19
 Firewalls and Firewall Testing Techniques Sonia Fahmy Department of Computer Sciences Purdue University fahmy@cs. purdue. edu http: //www. cs. purdue. edu/homes/fahmy/ Purdue University Sonia Fahmy 1
Firewalls and Firewall Testing Techniques Sonia Fahmy Department of Computer Sciences Purdue University fahmy@cs. purdue. edu http: //www. cs. purdue. edu/homes/fahmy/ Purdue University Sonia Fahmy 1
 Overview q What is a firewall? q Firewall types and architectures q Firewall operations q Firewall testing Purdue University Sonia Fahmy 2
Overview q What is a firewall? q Firewall types and architectures q Firewall operations q Firewall testing Purdue University Sonia Fahmy 2
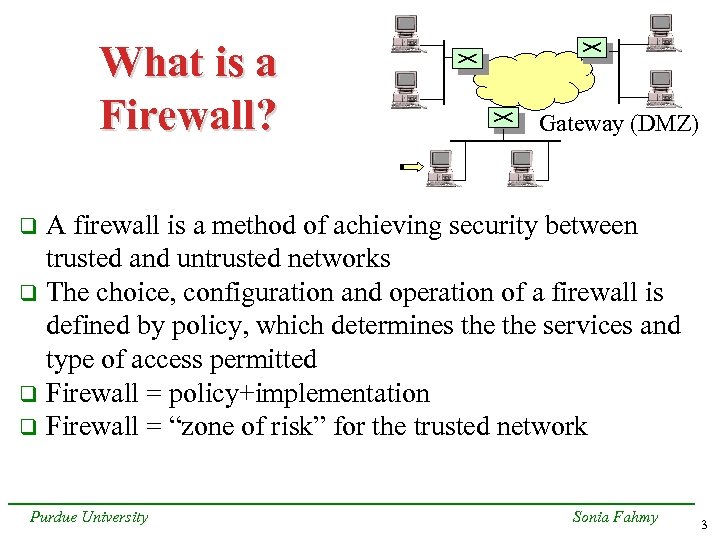 What is a Firewall? Gateway (DMZ) A firewall is a method of achieving security between trusted and untrusted networks q The choice, configuration and operation of a firewall is defined by policy, which determines the services and type of access permitted q Firewall = policy+implementation q Firewall = “zone of risk” for the trusted network q Purdue University Sonia Fahmy 3
What is a Firewall? Gateway (DMZ) A firewall is a method of achieving security between trusted and untrusted networks q The choice, configuration and operation of a firewall is defined by policy, which determines the services and type of access permitted q Firewall = policy+implementation q Firewall = “zone of risk” for the trusted network q Purdue University Sonia Fahmy 3
 Firewalls Should… Support and not impose a security policy q Use a “deny all services except those specifically permitted” policy q Accommodate new facilities and services q Contain advanced authentication measures q Employ filtering techniques to permit or deny services to specific hosts and use flexible and user-friendly filtering q Use proxy services for applications q Handle dial-in q Log suspicious activity q Purdue University Sonia Fahmy 4
Firewalls Should… Support and not impose a security policy q Use a “deny all services except those specifically permitted” policy q Accommodate new facilities and services q Contain advanced authentication measures q Employ filtering techniques to permit or deny services to specific hosts and use flexible and user-friendly filtering q Use proxy services for applications q Handle dial-in q Log suspicious activity q Purdue University Sonia Fahmy 4
 Firewalls Cannot… Protect against malicious insiders q Protect against connections that do not go through them (e. g. , dial-up) q Protect against new threats or new viruses q Purdue University Sonia Fahmy 5
Firewalls Cannot… Protect against malicious insiders q Protect against connections that do not go through them (e. g. , dial-up) q Protect against new threats or new viruses q Purdue University Sonia Fahmy 5
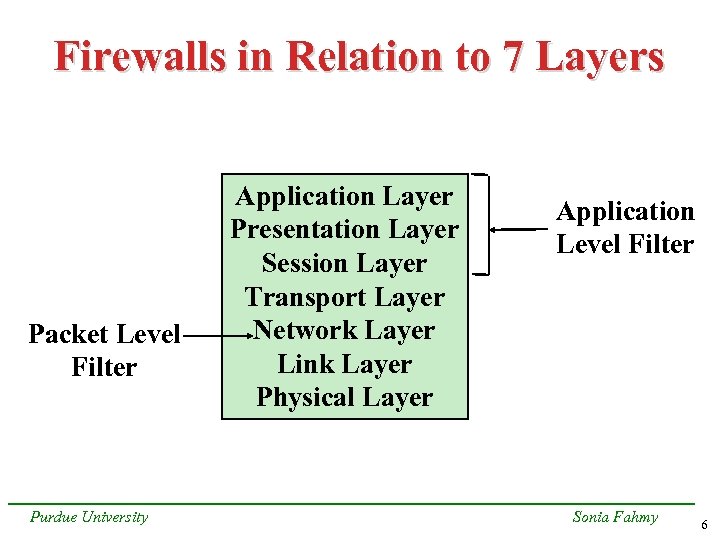 Firewalls in Relation to 7 Layers Packet Level Filter Purdue University Application Layer Presentation Layer Session Layer Transport Layer Network Layer Link Layer Physical Layer Application Level Filter Sonia Fahmy 6
Firewalls in Relation to 7 Layers Packet Level Filter Purdue University Application Layer Presentation Layer Session Layer Transport Layer Network Layer Link Layer Physical Layer Application Level Filter Sonia Fahmy 6
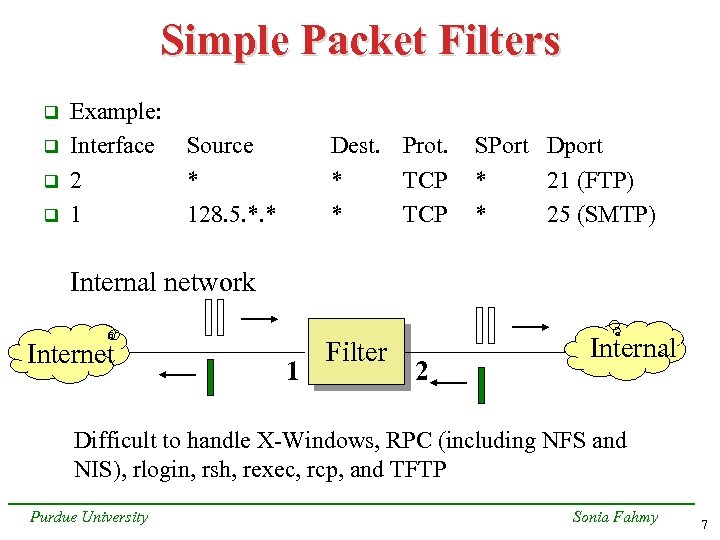 Simple Packet Filters q q Example: Interface 2 1 Source * 128. 5. *. * Dest. Prot. * TCP SPort Dport * 21 (FTP) * 25 (SMTP) Internal network Internet 1 Filter 2 Internal Difficult to handle X-Windows, RPC (including NFS and NIS), rlogin, rsh, rexec, rcp, and TFTP Purdue University Sonia Fahmy 7
Simple Packet Filters q q Example: Interface 2 1 Source * 128. 5. *. * Dest. Prot. * TCP SPort Dport * 21 (FTP) * 25 (SMTP) Internal network Internet 1 Filter 2 Internal Difficult to handle X-Windows, RPC (including NFS and NIS), rlogin, rsh, rexec, rcp, and TFTP Purdue University Sonia Fahmy 7
 Stateful Inspection q q Also known as dynamic packet filtering (dynamic rule set) Requires storing state for each stream, assuming: q If there is one packet, there will be more q If there is one packet, responses will be returned Prime candidate for resource starvation attacks What should be done when table is full? q Least recently used q Random early drop q Time out entries q Wait for FIN messages, etc. Purdue University Sonia Fahmy 8
Stateful Inspection q q Also known as dynamic packet filtering (dynamic rule set) Requires storing state for each stream, assuming: q If there is one packet, there will be more q If there is one packet, responses will be returned Prime candidate for resource starvation attacks What should be done when table is full? q Least recently used q Random early drop q Time out entries q Wait for FIN messages, etc. Purdue University Sonia Fahmy 8
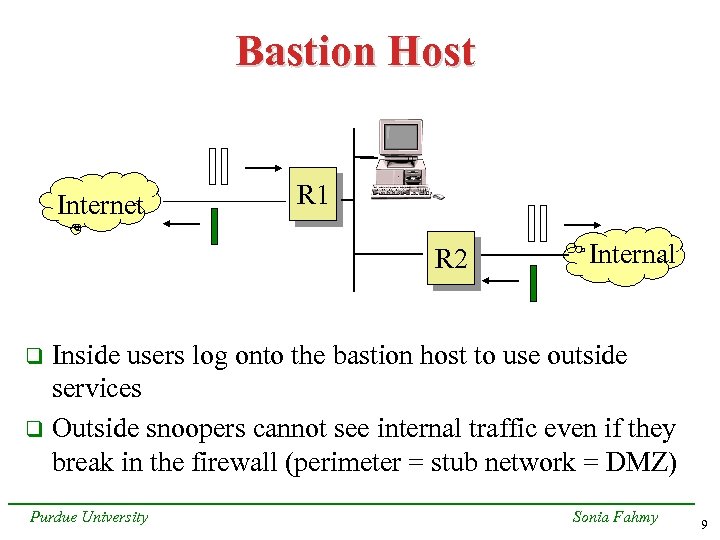 Bastion Host Internet R 1 R 2 Internal Inside users log onto the bastion host to use outside services q Outside snoopers cannot see internal traffic even if they break in the firewall (perimeter = stub network = DMZ) q Purdue University Sonia Fahmy 9
Bastion Host Internet R 1 R 2 Internal Inside users log onto the bastion host to use outside services q Outside snoopers cannot see internal traffic even if they break in the firewall (perimeter = stub network = DMZ) q Purdue University Sonia Fahmy 9
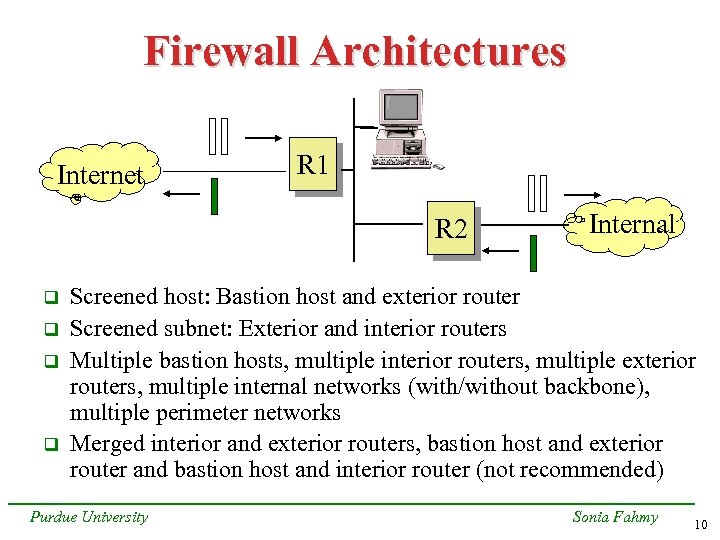 Firewall Architectures Internet R 1 R 2 q q Internal Screened host: Bastion host and exterior router Screened subnet: Exterior and interior routers Multiple bastion hosts, multiple interior routers, multiple exterior routers, multiple internal networks (with/without backbone), multiple perimeter networks Merged interior and exterior routers, bastion host and exterior router and bastion host and interior router (not recommended) Purdue University Sonia Fahmy 10
Firewall Architectures Internet R 1 R 2 q q Internal Screened host: Bastion host and exterior router Screened subnet: Exterior and interior routers Multiple bastion hosts, multiple interior routers, multiple exterior routers, multiple internal networks (with/without backbone), multiple perimeter networks Merged interior and exterior routers, bastion host and exterior router and bastion host and interior router (not recommended) Purdue University Sonia Fahmy 10
 Dual-homed Host Internet q Internal The dual-homed host is the firewall in this case Purdue University Sonia Fahmy 11
Dual-homed Host Internet q Internal The dual-homed host is the firewall in this case Purdue University Sonia Fahmy 11
 Application-Level Gateways Internet Server q q Dual-homed Host and Proxy Server Client Specialized programs on bastion host relay requests and responses, enforcing site policies (refusing some requests) Sometimes referred to as “proxy servers” Transparent with special “proxy client” programs Full protocol decomposition, e. g, Raptor, or “plug mode” e. g. , Firewall-1 and PIX Purdue University Sonia Fahmy 12
Application-Level Gateways Internet Server q q Dual-homed Host and Proxy Server Client Specialized programs on bastion host relay requests and responses, enforcing site policies (refusing some requests) Sometimes referred to as “proxy servers” Transparent with special “proxy client” programs Full protocol decomposition, e. g, Raptor, or “plug mode” e. g. , Firewall-1 and PIX Purdue University Sonia Fahmy 12
 Policies Network service access policy q Defines which services are to be explicitly allowed or denied+ways in which these services are to be used q Firewall design policy q Defines how the firewall implements restricted access and service filtering specified by the NSAP q FDP must be continuously updated with new vulnerabilities q Purdue University Sonia Fahmy 13
Policies Network service access policy q Defines which services are to be explicitly allowed or denied+ways in which these services are to be used q Firewall design policy q Defines how the firewall implements restricted access and service filtering specified by the NSAP q FDP must be continuously updated with new vulnerabilities q Purdue University Sonia Fahmy 13
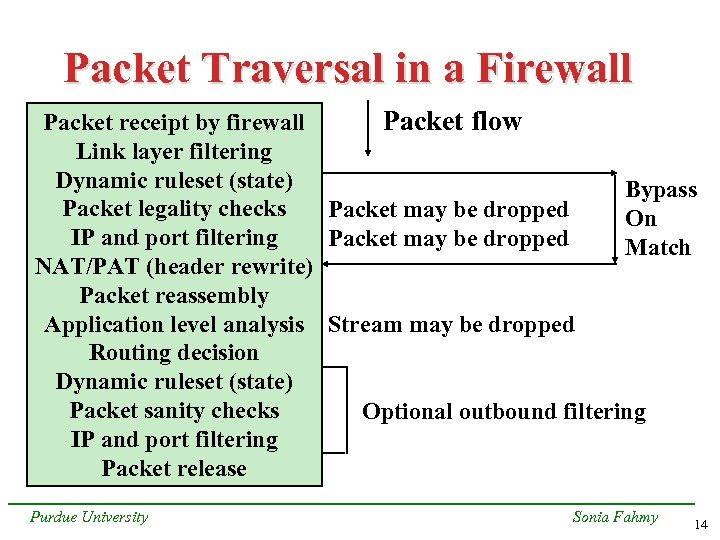 Packet Traversal in a Firewall Packet flow Packet receipt by firewall Link layer filtering Dynamic ruleset (state) Bypass Packet legality checks Packet may be dropped On IP and port filtering Packet may be dropped Match NAT/PAT (header rewrite) Packet reassembly Application level analysis Stream may be dropped Routing decision Dynamic ruleset (state) Packet sanity checks Optional outbound filtering IP and port filtering Packet release Purdue University Sonia Fahmy 14
Packet Traversal in a Firewall Packet flow Packet receipt by firewall Link layer filtering Dynamic ruleset (state) Bypass Packet legality checks Packet may be dropped On IP and port filtering Packet may be dropped Match NAT/PAT (header rewrite) Packet reassembly Application level analysis Stream may be dropped Routing decision Dynamic ruleset (state) Packet sanity checks Optional outbound filtering IP and port filtering Packet release Purdue University Sonia Fahmy 14
 Firewall Testing q q q Vulnerabilities = design or coding flaws = invalid assumptions, e. g. , insufficient verification, memory available, user data, trusted network object, predictable sequence, etc. Develop a vulnerability-operation matrix Place Common Vulnerabilities Exposure (CVE), and its candidates (CAN), and other known and new firewall problems in appropriate matrix cell Find clusters in matrix Predict problems Automate firewall testing through focusing on common problems Purdue University Sonia Fahmy 15
Firewall Testing q q q Vulnerabilities = design or coding flaws = invalid assumptions, e. g. , insufficient verification, memory available, user data, trusted network object, predictable sequence, etc. Develop a vulnerability-operation matrix Place Common Vulnerabilities Exposure (CVE), and its candidates (CAN), and other known and new firewall problems in appropriate matrix cell Find clusters in matrix Predict problems Automate firewall testing through focusing on common problems Purdue University Sonia Fahmy 15
 Example CVE-1999 -0158 q Cisco PIX firewall manager (PFM) allows retrieval of any file whose name and location is known q PIX proxy’s verification failure q Application level q Insufficient verification q Purdue University Sonia Fahmy 16
Example CVE-1999 -0158 q Cisco PIX firewall manager (PFM) allows retrieval of any file whose name and location is known q PIX proxy’s verification failure q Application level q Insufficient verification q Purdue University Sonia Fahmy 16
 Key Points Firewalls can employ: q Packet filters q Stateful inspection q Application-level gateways (many types) q Also circuit-level q Large variations, e. g. , Raptor, PIX, Firewall-1, Gauntlet q Several architectures to prevent all-or-nothing effect q Importance of policy q Firewall testing automation underway q Purdue University Sonia Fahmy 17
Key Points Firewalls can employ: q Packet filters q Stateful inspection q Application-level gateways (many types) q Also circuit-level q Large variations, e. g. , Raptor, PIX, Firewall-1, Gauntlet q Several architectures to prevent all-or-nothing effect q Importance of policy q Firewall testing automation underway q Purdue University Sonia Fahmy 17
 References q q q q RFC 2647, “Benchmarking” + drafts Simonds, “Network Security”, 1996 Hunt, “Internet/Intranet firewall security”, Computer Communications, 1998 Frantzen et al, “A framework for understanding vulnerabilties in firewalls using a dataflow model of firewall internals”, in preparation Kamara et al, “Testing firewalls”, in preparation Chapman, “Network (In)Security through IP packet filtering” http: //cve. mitre. org/, www. sans. org, www. cert. org Web pages and mailing lists Purdue University Sonia Fahmy 18
References q q q q RFC 2647, “Benchmarking” + drafts Simonds, “Network Security”, 1996 Hunt, “Internet/Intranet firewall security”, Computer Communications, 1998 Frantzen et al, “A framework for understanding vulnerabilties in firewalls using a dataflow model of firewall internals”, in preparation Kamara et al, “Testing firewalls”, in preparation Chapman, “Network (In)Security through IP packet filtering” http: //cve. mitre. org/, www. sans. org, www. cert. org Web pages and mailing lists Purdue University Sonia Fahmy 18
 Thank You! Questions? Purdue University Sonia Fahmy 19
Thank You! Questions? Purdue University Sonia Fahmy 19


