731af5afb5d61f8983379844847c6679.ppt
- Количество слайдов: 28
 FIDES CA DG MARE’s X. 509 Certification Authority for use in FLUX TL, VMS, ERS and CREWS systems
FIDES CA DG MARE’s X. 509 Certification Authority for use in FLUX TL, VMS, ERS and CREWS systems
 Context • • For years, coastal FMC’s and European Commission have been exchanging VMS data over X. 25 ( Example: Reg. (EC) 2244/2003 ) 2000 -2006: X. 25 progressively phasing out by Telecom operators 2005: Trackwell proposed a new VMS protocol using the Internet: X. 25 → easy RESTful-like HTTP Web Service over 2 -way SSL/TLS Problem: – – – Each VMS client/server requires a X. 509 Digital Certificate (Cert) Without a Certification Authority (CA), one must use a self-signed Cert CA’s are either expensive or not trustworthy! Many will use self-signed Certs Everyone must trust many other unrelated party’s Certs, all Certs need to be replaced regularly and then tested against every other party’s server Infrastructure becomes unmanageable! • 05/2006: Meeting on VMS with NEAFC at Gdynia, Poland European Commission proposes to run a dedicated central CA for “supplying X. 509 v 3 Digital Certificates to any Party who depends on cryptographic services to fulfill some requirements deriving from a Community Regulation in the field of fisheries. ” 3/18/2018 FIDES CA 2
Context • • For years, coastal FMC’s and European Commission have been exchanging VMS data over X. 25 ( Example: Reg. (EC) 2244/2003 ) 2000 -2006: X. 25 progressively phasing out by Telecom operators 2005: Trackwell proposed a new VMS protocol using the Internet: X. 25 → easy RESTful-like HTTP Web Service over 2 -way SSL/TLS Problem: – – – Each VMS client/server requires a X. 509 Digital Certificate (Cert) Without a Certification Authority (CA), one must use a self-signed Cert CA’s are either expensive or not trustworthy! Many will use self-signed Certs Everyone must trust many other unrelated party’s Certs, all Certs need to be replaced regularly and then tested against every other party’s server Infrastructure becomes unmanageable! • 05/2006: Meeting on VMS with NEAFC at Gdynia, Poland European Commission proposes to run a dedicated central CA for “supplying X. 509 v 3 Digital Certificates to any Party who depends on cryptographic services to fulfill some requirements deriving from a Community Regulation in the field of fisheries. ” 3/18/2018 FIDES CA 2
 Concepts (PKI, X. 509 & CA) • Public Key Infrastructure: http: //en. wikipedia. org/wiki/Public_key_infrastructure – each party has: RSA (or DSA) Public Key (copy to all parties) + Private Key (kept secret!) – identified Key Pairs + well known hash (MD 5, SHA-1. . . ) & encryption (RSA, 3 DES. . . ) algorithms identified → confidentiality (encrypt/decrypt) + data integrity and non-repudiation (sign/verify) – Private Key can be guessed over time Must expire after some time (longer keys are safer) – Private Key can leak out Must be revoked and replaced immediately! • X. 509 version 3 Digital Cert: http: //en. wikipedia. org/wiki/X. 509 – a standard way of binding: Public Key + Owner ID + attributes (e. g. Exp. Date, client/server roles, etc) – Owner ID: Subject Distinguished Name (DN) must uniquely identify a person/machine! – signed by some Trusted Party (either the owner itself or a CA) a Cert identifies its Owner • CA: http: //en. wikipedia. org/wiki/Certificate_authority – is a Trusted Third Party using its Key pairs to sign and issue Certs: Ø for itself: CA Root Cert (self-signed), Subordinate CA Certs Ø for others: Delegated Subordinate CA, End Entities (client/server) Certs – must first verify Cert Owner ID to some extent limitation of Liability ~ Cert cost – manages optional services: Cert revocation (CRL, OSCP), may offer Private Key recovery. . . – publishes: Certificate Practice Statements (CPS), directories of issued Certs, CRLs, . . . • TLS 1. 0: http: //en. wikipedia. org/wiki/Transport_Layer_Security – secures channel to a server identified by a client-trusted server-owned [client/]server Cert server identified – optionally requires client identify with a server-trusted client-owned client[/server] Cert client to identify – part of server’s Cert Subject DN must match full DNS server name built-in server authorization server – client authorization is not automatic: server needs some kind of extra Access Control system, authorization unless everyone having a Cert from a server-trusted CA can do everything in the system! 3/18/2018 FIDES CA 3
Concepts (PKI, X. 509 & CA) • Public Key Infrastructure: http: //en. wikipedia. org/wiki/Public_key_infrastructure – each party has: RSA (or DSA) Public Key (copy to all parties) + Private Key (kept secret!) – identified Key Pairs + well known hash (MD 5, SHA-1. . . ) & encryption (RSA, 3 DES. . . ) algorithms identified → confidentiality (encrypt/decrypt) + data integrity and non-repudiation (sign/verify) – Private Key can be guessed over time Must expire after some time (longer keys are safer) – Private Key can leak out Must be revoked and replaced immediately! • X. 509 version 3 Digital Cert: http: //en. wikipedia. org/wiki/X. 509 – a standard way of binding: Public Key + Owner ID + attributes (e. g. Exp. Date, client/server roles, etc) – Owner ID: Subject Distinguished Name (DN) must uniquely identify a person/machine! – signed by some Trusted Party (either the owner itself or a CA) a Cert identifies its Owner • CA: http: //en. wikipedia. org/wiki/Certificate_authority – is a Trusted Third Party using its Key pairs to sign and issue Certs: Ø for itself: CA Root Cert (self-signed), Subordinate CA Certs Ø for others: Delegated Subordinate CA, End Entities (client/server) Certs – must first verify Cert Owner ID to some extent limitation of Liability ~ Cert cost – manages optional services: Cert revocation (CRL, OSCP), may offer Private Key recovery. . . – publishes: Certificate Practice Statements (CPS), directories of issued Certs, CRLs, . . . • TLS 1. 0: http: //en. wikipedia. org/wiki/Transport_Layer_Security – secures channel to a server identified by a client-trusted server-owned [client/]server Cert server identified – optionally requires client identify with a server-trusted client-owned client[/server] Cert client to identify – part of server’s Cert Subject DN must match full DNS server name built-in server authorization server – client authorization is not automatic: server needs some kind of extra Access Control system, authorization unless everyone having a Cert from a server-trusted CA can do everything in the system! 3/18/2018 FIDES CA 3
 Concepts (2 -way SSL) 3/18/2018 FIDES CA 4
Concepts (2 -way SSL) 3/18/2018 FIDES CA 4
 Common X. 509 File Types • • • 3/18/2018 X. 509 Cert, Cert Signing Request and Private Key file formats: –. DER: Cert in binary files (DER binary format) –. PEM: text files (Base-64 encoded) Cert files sometimes. CER (binary) or. CRT (text) Cert Signing Request files (PKCS#10) usually. CSR/. REQ (text) Private Key files sometimes. KEY, sometimes encrypted with a password Cert file + Trust chain (“Trustees”) can be: – separate. DER/. PEM/. CER/. CRT text or binary files –. PEM Cert files concatenated together in a bigger. PEM file –. P 7 B binary PKCS#7 file “Certificate Bag” Private Key + Cert file [+ Trust chain] can be: – separate. DER/. PEM/. CER/. CRT/. KEY text or binary files –. PEM Cert and Key files concatenated together in a bigger private. PEM file –. PFX/. P 12 binary PKCS#12 file “Personal Information Exchange Syntax Standard” To examine a file: . PEM/. CRT/. CSR/. REQ → open in text editor, split before “-----BEGIN” lines, use openssl [x 509|req] –noout –text –in
Common X. 509 File Types • • • 3/18/2018 X. 509 Cert, Cert Signing Request and Private Key file formats: –. DER: Cert in binary files (DER binary format) –. PEM: text files (Base-64 encoded) Cert files sometimes. CER (binary) or. CRT (text) Cert Signing Request files (PKCS#10) usually. CSR/. REQ (text) Private Key files sometimes. KEY, sometimes encrypted with a password Cert file + Trust chain (“Trustees”) can be: – separate. DER/. PEM/. CER/. CRT text or binary files –. PEM Cert files concatenated together in a bigger. PEM file –. P 7 B binary PKCS#7 file “Certificate Bag” Private Key + Cert file [+ Trust chain] can be: – separate. DER/. PEM/. CER/. CRT/. KEY text or binary files –. PEM Cert and Key files concatenated together in a bigger private. PEM file –. PFX/. P 12 binary PKCS#12 file “Personal Information Exchange Syntax Standard” To examine a file: . PEM/. CRT/. CSR/. REQ → open in text editor, split before “-----BEGIN” lines, use openssl [x 509|req] –noout –text –in
 FIDES CA (1 / 2) • • • Hosted and operated at DG MARE using freeware Open. SSL tools (http: //www. openssl. org/) Single Contact point to apply / report a technical problem: fish-fidesinfo@ec. europa. eu 2 FIDES CA (*): Symmetric distinct Production & Test CA’s using ≠ Root CA Private Key Well separated Production & Test CA Domains: – – • • • Test CA domain: whoever, identity of applicant is not verified Never trust Fides Test CA on a production box! Prod CA domain: • for public sector authorities in Member States, Third Countries and International Organizations → DG MARE verifies identity of applicant by: Ø Looking up the applicant’s server DNS name in RIPE (Easy) Ø Contacting the National Administration by email or fax (Easy) • for actors in the private sector → identity of applicant must be guaranteed by a National Administration (Official Letter) Certificate Lists in Open. SSL CA format: https: //webgate. ec. europa. eu/fides/ca[/test]/ca[deh|fides|vms]. txt Version 1 CRL’s for CA + End Entity Certs available over 1 -way SSL HTTPS (No OCSP) Never issues Certs with identical Subject DN to different entities: ≠ Entity ≠ Subject DN Hint: it is recommended that renewed Certs keep the same Subject DN Offers reasonably high level of security (Root Private Keys stored offline in a safe deposit) FIDES CA operations during European Commission's business hours only. FIDES CA Web site offered on a "best effort availability" outside of these hours. FIDES CA liability limitation statement: FIDES CA expressly disclaims any liability in case damages are incurred as a result of failure, delay, or masquerading or any kind of fraud or abuse in the operation of the FIDES CA infrastructure or theft of its Private Keys. (*) In fact 3: existed an “old” FIDES Test CA now Read-Only; since 25/6/2010 a “new” FIDES Test CA takes over. 3/18/2018 FIDES CA 6
FIDES CA (1 / 2) • • • Hosted and operated at DG MARE using freeware Open. SSL tools (http: //www. openssl. org/) Single Contact point to apply / report a technical problem: fish-fidesinfo@ec. europa. eu 2 FIDES CA (*): Symmetric distinct Production & Test CA’s using ≠ Root CA Private Key Well separated Production & Test CA Domains: – – • • • Test CA domain: whoever, identity of applicant is not verified Never trust Fides Test CA on a production box! Prod CA domain: • for public sector authorities in Member States, Third Countries and International Organizations → DG MARE verifies identity of applicant by: Ø Looking up the applicant’s server DNS name in RIPE (Easy) Ø Contacting the National Administration by email or fax (Easy) • for actors in the private sector → identity of applicant must be guaranteed by a National Administration (Official Letter) Certificate Lists in Open. SSL CA format: https: //webgate. ec. europa. eu/fides/ca[/test]/ca[deh|fides|vms]. txt Version 1 CRL’s for CA + End Entity Certs available over 1 -way SSL HTTPS (No OCSP) Never issues Certs with identical Subject DN to different entities: ≠ Entity ≠ Subject DN Hint: it is recommended that renewed Certs keep the same Subject DN Offers reasonably high level of security (Root Private Keys stored offline in a safe deposit) FIDES CA operations during European Commission's business hours only. FIDES CA Web site offered on a "best effort availability" outside of these hours. FIDES CA liability limitation statement: FIDES CA expressly disclaims any liability in case damages are incurred as a result of failure, delay, or masquerading or any kind of fraud or abuse in the operation of the FIDES CA infrastructure or theft of its Private Keys. (*) In fact 3: existed an “old” FIDES Test CA now Read-Only; since 25/6/2010 a “new” FIDES Test CA takes over. 3/18/2018 FIDES CA 6
 FIDES CA (2 / 2) Your duties: ü ü ü ü Trust FIDES CA Primary CA Cert. Hint: avoid dealing with End Entities Certs others than your own! To obtain a Cert, you: 1. Compute a new Key Pair on your server yourself Hint: use Portecle (see demo on page 15) 2. Derive a Certificate Signing Request (. CSR, PKCS#10) file Hint: supply the correct CN value! 3. Email that. CSR file in clear to fish-fidesinfo@ec. europa. eu Hints: Ø Specify whether you want a PRODUCTION or a TEST Cert! Ø Your Private Key should never leave your server! 4. Import back the signed Cert over the Key Pair Hint: . PEM, . DER and. P 7 B files are supplied. Use the. P 7 B if possible. When your Cert expires, you must send in a new Certificate Signing Request to FIDES CA to obtain a new one Hint: make a new Key Pair but reuse the same Subject DN When your Private Key gets compromised, you must inform FIDES CA immediately! When you lose your Private Key, your Cert must be renewed (No Key Recovery service) Keep your SSL software/libraries up to date (fixes known SSL vulnerabilities) Keep your client list up to date in your Access Control system 3/18/2018 FIDES CA 7
FIDES CA (2 / 2) Your duties: ü ü ü ü Trust FIDES CA Primary CA Cert. Hint: avoid dealing with End Entities Certs others than your own! To obtain a Cert, you: 1. Compute a new Key Pair on your server yourself Hint: use Portecle (see demo on page 15) 2. Derive a Certificate Signing Request (. CSR, PKCS#10) file Hint: supply the correct CN value! 3. Email that. CSR file in clear to fish-fidesinfo@ec. europa. eu Hints: Ø Specify whether you want a PRODUCTION or a TEST Cert! Ø Your Private Key should never leave your server! 4. Import back the signed Cert over the Key Pair Hint: . PEM, . DER and. P 7 B files are supplied. Use the. P 7 B if possible. When your Cert expires, you must send in a new Certificate Signing Request to FIDES CA to obtain a new one Hint: make a new Key Pair but reuse the same Subject DN When your Private Key gets compromised, you must inform FIDES CA immediately! When you lose your Private Key, your Cert must be renewed (No Key Recovery service) Keep your SSL software/libraries up to date (fixes known SSL vulnerabilities) Keep your client list up to date in your Access Control system 3/18/2018 FIDES CA 7
 FIDES CA Certs • • • Prod. Subject: CN=FIDES SSL Primary CA, OU=DG FISH, O=European Commission, L=Brussels B-1049, C=BE/mail=fish-fidesinfo@ec. europa. eu SHA-1 hash: BF: 3 E: 47: 5 E: 0 B: AB: 41: E 2: FD: 3 A: D 8: 3 F: B 8: 6 B: 36: 2 C: F 2: DB: AE: 91 Test Subject: C=BE, L=Brussels B-1049, O=European Commission, OU=DG FISH, CN=FIDES SSL Primary CA - test/email. Address=fish-fidesinfo@ec. europa. eu SHA-1 hash: F 9: 2 A: A 1: B 1: E 1: 9 A: 89: E 2: D 4: 12: A 4: 43: 66: E 3: BC: 19: 18: 40: AC: 72 FIDES Test CA Cert “ – test” suffix in Subject Common Name (CN) CA Certs use 2048 -bit RSA Key Pairs valid for 15 years (End Entity: you choose, max 5 years) End Entity Certs issued by a Subordinate CA: – – • • DG MARE [test] Certs issued by: C=. . . , CN=FIDES SSL CA [- test]/. . . M. S. [test] Certs issued by: C=. . . , CN=VMS SSL CA [- test]/. . . X 509 v 3 Authority Key Identifier & Subject Key Identifier in all Certs easy Cert Chain construction Few X 509 v 3 Extensions and only 1 is Critical: X 509 v 3 Basic Constraints: CA: [TRUE|FALSE] Best software compatibility + No one can operate as a Delegated CA Extended Key Usage (End entity Cert default: SSL_client + SSL_server + S-MIME) Authority Information Access (CA Web Site URL + email) & CRL Distribution Points (URL) 3/18/2018 FIDES CA 8
FIDES CA Certs • • • Prod. Subject: CN=FIDES SSL Primary CA, OU=DG FISH, O=European Commission, L=Brussels B-1049, C=BE/mail=fish-fidesinfo@ec. europa. eu SHA-1 hash: BF: 3 E: 47: 5 E: 0 B: AB: 41: E 2: FD: 3 A: D 8: 3 F: B 8: 6 B: 36: 2 C: F 2: DB: AE: 91 Test Subject: C=BE, L=Brussels B-1049, O=European Commission, OU=DG FISH, CN=FIDES SSL Primary CA - test/email. Address=fish-fidesinfo@ec. europa. eu SHA-1 hash: F 9: 2 A: A 1: B 1: E 1: 9 A: 89: E 2: D 4: 12: A 4: 43: 66: E 3: BC: 19: 18: 40: AC: 72 FIDES Test CA Cert “ – test” suffix in Subject Common Name (CN) CA Certs use 2048 -bit RSA Key Pairs valid for 15 years (End Entity: you choose, max 5 years) End Entity Certs issued by a Subordinate CA: – – • • DG MARE [test] Certs issued by: C=. . . , CN=FIDES SSL CA [- test]/. . . M. S. [test] Certs issued by: C=. . . , CN=VMS SSL CA [- test]/. . . X 509 v 3 Authority Key Identifier & Subject Key Identifier in all Certs easy Cert Chain construction Few X 509 v 3 Extensions and only 1 is Critical: X 509 v 3 Basic Constraints: CA: [TRUE|FALSE] Best software compatibility + No one can operate as a Delegated CA Extended Key Usage (End entity Cert default: SSL_client + SSL_server + S-MIME) Authority Information Access (CA Web Site URL + email) & CRL Distribution Points (URL) 3/18/2018 FIDES CA 8
 Certs used in Production (1/2) • EEC: https: //fides. ec. europa. eu/wsnorers/v 1. . . • Trusts: – – FIDES Prod CA (has copies of all Subordinates) /C=ZA/ST=Western Cape/L=Cape Town/O=Thawte Consulting cc/OU=Certification Services Division/CN=Thawte Server CA/email. Address=server-certs@thawte. com – /C=ca/ST=Nova Scotia/L=Dartmouth/O=NAFO/OU=NAFO Secretariat/CN=NAFO FMC CA/email. Address=vms@nafo. int – /C=DK/L=Copenhagen/O=Sirius IT A/S/OU=CT 2/CN=Sirius IT CA/email. Address=vtrack_support@siriusit. com – /C=DK/L=Copenhagen/O=Tieto. Enator A/S/OU=Public, Fishery/CN=TE PUBFIS DK/email. Address=vtrack@tietoenator. com –. . . Tip 1 : self-signed Entities will not be accepted here Tip 2 : more “well known” commercial CA’s can be added upon request • Client Certificate is used is different from the Server Certificate 3/18/2018 FIDES CA 9
Certs used in Production (1/2) • EEC: https: //fides. ec. europa. eu/wsnorers/v 1. . . • Trusts: – – FIDES Prod CA (has copies of all Subordinates) /C=ZA/ST=Western Cape/L=Cape Town/O=Thawte Consulting cc/OU=Certification Services Division/CN=Thawte Server CA/email. Address=server-certs@thawte. com – /C=ca/ST=Nova Scotia/L=Dartmouth/O=NAFO/OU=NAFO Secretariat/CN=NAFO FMC CA/email. Address=vms@nafo. int – /C=DK/L=Copenhagen/O=Sirius IT A/S/OU=CT 2/CN=Sirius IT CA/email. Address=vtrack_support@siriusit. com – /C=DK/L=Copenhagen/O=Tieto. Enator A/S/OU=Public, Fishery/CN=TE PUBFIS DK/email. Address=vtrack@tietoenator. com –. . . Tip 1 : self-signed Entities will not be accepted here Tip 2 : more “well known” commercial CA’s can be added upon request • Client Certificate is used is different from the Server Certificate 3/18/2018 FIDES CA 9
 Certs used in Production (2/2) • Problems: – Subordinates /CN=FIDES SSL CA/ and /CN=VMS SSL CA/ sometimes causes problems in some SSL implementations doing online Revocation checking with CRL’s – Server EEC Certificate expires already (5 -year old) • Solution: – a new subordinate /CN=DEH SSL CA/ is created signed by same Primary CA (=> trusted automatically by everyone) – a new Server EEC Certificate will be issued by it 3/18/2018 FIDES CA 10
Certs used in Production (2/2) • Problems: – Subordinates /CN=FIDES SSL CA/ and /CN=VMS SSL CA/ sometimes causes problems in some SSL implementations doing online Revocation checking with CRL’s – Server EEC Certificate expires already (5 -year old) • Solution: – a new subordinate /CN=DEH SSL CA/ is created signed by same Primary CA (=> trusted automatically by everyone) – a new Server EEC Certificate will be issued by it 3/18/2018 FIDES CA 10
 Certs used in Test/Acceptance • EEC: https: //fides. acceptance. ec. europa. eu/. . . Tip : supports TLS v 1. x only. SSL v 3 no longer supported. • Trusts: – FIDES Test CA both old (<25/6/2010) and new (>=25/6/2010), has copies of all Subordinates – /C=ZA/ST=Western Cape/L=Cape Town/O=Thawte Consulting cc/OU=Certification Services Division/CN=Thawte Server CA/email. Address=servercerts@thawte. com – /C=ca/ST=Nova Scotia/L=Dartmouth/O=NAFO/OU=NAFO Secretariat/CN=NAFO FMC CA/email. Address=vms@nafo. int Tip 1 : self-signed Entities will not be accepted here Tip 2 : more “well known” commercial CA’s can be added upon request • When a Client Certificate is used, it’s different from the Server Certificate. 3/18/2018 FIDES CA 11
Certs used in Test/Acceptance • EEC: https: //fides. acceptance. ec. europa. eu/. . . Tip : supports TLS v 1. x only. SSL v 3 no longer supported. • Trusts: – FIDES Test CA both old (<25/6/2010) and new (>=25/6/2010), has copies of all Subordinates – /C=ZA/ST=Western Cape/L=Cape Town/O=Thawte Consulting cc/OU=Certification Services Division/CN=Thawte Server CA/email. Address=servercerts@thawte. com – /C=ca/ST=Nova Scotia/L=Dartmouth/O=NAFO/OU=NAFO Secretariat/CN=NAFO FMC CA/email. Address=vms@nafo. int Tip 1 : self-signed Entities will not be accepted here Tip 2 : more “well known” commercial CA’s can be added upon request • When a Client Certificate is used, it’s different from the Server Certificate. 3/18/2018 FIDES CA 11
 EEC FMC Server is unlike a typical VMS, ERS or CREWS server: ü Front-end server = Blue. Coat Reverse Proxy gives HTTP error response with HTML payload when request fails in certain ways: • • • ü ü back-end server timeout Network Error (tcp_error) wrong/bad client Cert Network Error (ssl_failed) wrong HTTP/1. 1 request (e. g. bad URL or HTTP/1. 0 with no “Host: ” header) Access Denied (policy_denied) Server Cert (on Bluecoat) ≠ Client Cert (on back-end Server) Both Certs signed by an unusual Subordinate CA (CN=FIDES SSL CA) 3/18/2018 FIDES CA 12
EEC FMC Server is unlike a typical VMS, ERS or CREWS server: ü Front-end server = Blue. Coat Reverse Proxy gives HTTP error response with HTML payload when request fails in certain ways: • • • ü ü back-end server timeout Network Error (tcp_error) wrong/bad client Cert Network Error (ssl_failed) wrong HTTP/1. 1 request (e. g. bad URL or HTTP/1. 0 with no “Host: ” header) Access Denied (policy_denied) Server Cert (on Bluecoat) ≠ Client Cert (on back-end Server) Both Certs signed by an unusual Subordinate CA (CN=FIDES SSL CA) 3/18/2018 FIDES CA 12
 Setting up your Server 1. 2. 3. 4. 3/18/2018 Obtain combined client/server (preferred) or separate client & server Certs from either: – FIDES Test or Prod CA (free, recommended) – A well known Commercial CA (suggestions at http: //www. mozilla. org/projects/security/certs/included/) Subject CN in Cert for your server must match the public full DNS name (preferred) or public IP address (avoid!) as in the public URL used by all its clients. Install FIDES Test or Prod CA Root Cert (ca. der) as a Trusted Certificate object in your test/prod server Keystore (preferred) or Truststore Hint: it’s suggested to also install FIDES CA’s Subordinate VMS SSL CA (cavms. der) as another Trusted Certificate object On a production system, install only production FIDES CA Certs. On a test system, install either only the FIDES Test CA Certs or both. Install your client/server Cert(s) and Private Key(s) as Key Pair object(s) in your server’s Keystore Set up your server’s Access Control system to recognize all its VMS, ERS or CREWS clients, e. g. using data from FIDES CA Certificate Lists (see page 5) FIDES CA 13
Setting up your Server 1. 2. 3. 4. 3/18/2018 Obtain combined client/server (preferred) or separate client & server Certs from either: – FIDES Test or Prod CA (free, recommended) – A well known Commercial CA (suggestions at http: //www. mozilla. org/projects/security/certs/included/) Subject CN in Cert for your server must match the public full DNS name (preferred) or public IP address (avoid!) as in the public URL used by all its clients. Install FIDES Test or Prod CA Root Cert (ca. der) as a Trusted Certificate object in your test/prod server Keystore (preferred) or Truststore Hint: it’s suggested to also install FIDES CA’s Subordinate VMS SSL CA (cavms. der) as another Trusted Certificate object On a production system, install only production FIDES CA Certs. On a test system, install either only the FIDES Test CA Certs or both. Install your client/server Cert(s) and Private Key(s) as Key Pair object(s) in your server’s Keystore Set up your server’s Access Control system to recognize all its VMS, ERS or CREWS clients, e. g. using data from FIDES CA Certificate Lists (see page 5) FIDES CA 13
 Suggestions and problems • If your server is Java: – – • • 3/18/2018 forget Keytool cmd-line, use Portecle freeware GUI (http: //portecle. sourceforge. net/) Tip: even if it’s not Java, you can still generate a dummy Keystore, a Key Pair and CSR, then import P 7 B back and export PEM and PFX using Portecle and then trash the Keystore! Easy! Get SSL debug info on stdout by adding -Djavax. net. debug=ssl to Java command-line. See http: //java. sun. com/j 2 ee/1. 4/docs/tutorial/doc/Security 6. html When installing your new Cert, make sure to import it into the matching Key Pair object in the Keystore. (Otherwise you get it configured as a simple Trusted Certificate and it won’t work. ) Import from the P 7 B if supported by your software so import the full Trust Chain with it. If using PEM files, import all CA files as Trusted Certificates first. (If your software can’t figure out its certificate Trust Chain, connection will only succeed with other systems which do have a copy of these CA Certs, and it will fail with all other systems). When upgrading Weblogic to version 10, watch out for certificate order in concatenated. PEM files! (Bad order causes the SSL client authentication to always fail. Was not a problem in previous Weblogic versions. ) If replacing your old client/server by a new one, make sure to remove the old one from the Keystore. (If you don’t, you don’t know which one will be used and it can fail randomly. ) If needed to use a client Cert that supports online Revocation checking with CRL’s: If you got a Cert from FIDES Test CA before 28/6/2010, apply for a new one! If you got a Cert from FIDES CA before 1/9/2011, apply for a new one! EEC FMC server can get to your servers using multiple IP addresses in Brussels or Luxembourg (158. 169. 9. 14, 158. 169. 131. 14). If you run your server behind a firewall, make sure to allow both IPs. FIDES CA 14
Suggestions and problems • If your server is Java: – – • • 3/18/2018 forget Keytool cmd-line, use Portecle freeware GUI (http: //portecle. sourceforge. net/) Tip: even if it’s not Java, you can still generate a dummy Keystore, a Key Pair and CSR, then import P 7 B back and export PEM and PFX using Portecle and then trash the Keystore! Easy! Get SSL debug info on stdout by adding -Djavax. net. debug=ssl to Java command-line. See http: //java. sun. com/j 2 ee/1. 4/docs/tutorial/doc/Security 6. html When installing your new Cert, make sure to import it into the matching Key Pair object in the Keystore. (Otherwise you get it configured as a simple Trusted Certificate and it won’t work. ) Import from the P 7 B if supported by your software so import the full Trust Chain with it. If using PEM files, import all CA files as Trusted Certificates first. (If your software can’t figure out its certificate Trust Chain, connection will only succeed with other systems which do have a copy of these CA Certs, and it will fail with all other systems). When upgrading Weblogic to version 10, watch out for certificate order in concatenated. PEM files! (Bad order causes the SSL client authentication to always fail. Was not a problem in previous Weblogic versions. ) If replacing your old client/server by a new one, make sure to remove the old one from the Keystore. (If you don’t, you don’t know which one will be used and it can fail randomly. ) If needed to use a client Cert that supports online Revocation checking with CRL’s: If you got a Cert from FIDES Test CA before 28/6/2010, apply for a new one! If you got a Cert from FIDES CA before 1/9/2011, apply for a new one! EEC FMC server can get to your servers using multiple IP addresses in Brussels or Luxembourg (158. 169. 9. 14, 158. 169. 131. 14). If you run your server behind a firewall, make sure to allow both IPs. FIDES CA 14
 Wrapping Up Demo: – Obtain and configure your certificate using Portecle (http: //portecle. sourceforge. net/) References: – “Track. Well VMS - Secure Internet Specifications and API”, Appendix A – – “NEAFC HTTPS Gateway - Testing Connection”, both © Trackwell Software, 2003 http: //circa. europa. eu/Public/irc/ida/fides/library? l=/message_specifications “PKI tutorial”, anonymous http: //pdfdatabase. com/download/pki-tutorial-pdf-581024 -html “Everything you Never Wanted to Know about PKI but were Forced to Find Out”, Peter Gutmann, University of Auckland http: //www. cs. auckland. ac. nz/~pgut 001/pubs/pkitutorial. pdf Contact: – 3/18/2018 MARE Helpdesk (fish-fidesinfo@ec. europa. eu) FIDES CA 15
Wrapping Up Demo: – Obtain and configure your certificate using Portecle (http: //portecle. sourceforge. net/) References: – “Track. Well VMS - Secure Internet Specifications and API”, Appendix A – – “NEAFC HTTPS Gateway - Testing Connection”, both © Trackwell Software, 2003 http: //circa. europa. eu/Public/irc/ida/fides/library? l=/message_specifications “PKI tutorial”, anonymous http: //pdfdatabase. com/download/pki-tutorial-pdf-581024 -html “Everything you Never Wanted to Know about PKI but were Forced to Find Out”, Peter Gutmann, University of Auckland http: //www. cs. auckland. ac. nz/~pgut 001/pubs/pkitutorial. pdf Contact: – 3/18/2018 MARE Helpdesk (fish-fidesinfo@ec. europa. eu) FIDES CA 15
 Demo 1/13 Open you server’s Key. Store (JKS file) in Portecle or create a new one. Create a new RSA Key Pair and an interim Self-Signed Certificate for your server. 3/18/2018 FIDES CA 16
Demo 1/13 Open you server’s Key. Store (JKS file) in Portecle or create a new one. Create a new RSA Key Pair and an interim Self-Signed Certificate for your server. 3/18/2018 FIDES CA 16
 Demo 2/13 Populate the Self-Signed Certificate values. CN must match the server public DNS name. 3/18/2018 FIDES CA 17
Demo 2/13 Populate the Self-Signed Certificate values. CN must match the server public DNS name. 3/18/2018 FIDES CA 17
 Demo 3/13 Right-click your new Key Pair and select Generate Certification Request (CSR file). 3/18/2018 FIDES CA 18
Demo 3/13 Right-click your new Key Pair and select Generate Certification Request (CSR file). 3/18/2018 FIDES CA 18
 Demo 4/13 Save the JKS file (you will need it later). Supply a Password that you will remember. 3/18/2018 FIDES CA 19
Demo 4/13 Save the JKS file (you will need it later). Supply a Password that you will remember. 3/18/2018 FIDES CA 19
 Demo 5/13 Submit the CSR file from step 3 to FIDES Helpdesk. Specify if for Production or Test use! 3/18/2018 FIDES CA 20
Demo 5/13 Submit the CSR file from step 3 to FIDES Helpdesk. Specify if for Production or Test use! 3/18/2018 FIDES CA 20
 Demo 6/13 Zip file sent back by FIDES Helpdesk contains CA root (1) and Signed Certificate (2). Unzip everything. 3/18/2018 FIDES CA 21
Demo 6/13 Zip file sent back by FIDES Helpdesk contains CA root (1) and Signed Certificate (2). Unzip everything. 3/18/2018 FIDES CA 21
 Demo 7/13 Open the JKS file used before. Supply the same password as in step 4. (1) Import CA root Certificate (ca. der) as a Trusted Certificate. 3/18/2018 FIDES CA 22
Demo 7/13 Open the JKS file used before. Supply the same password as in step 4. (1) Import CA root Certificate (ca. der) as a Trusted Certificate. 3/18/2018 FIDES CA 22
 Demo 8/13 (1) Check the Fingerprint value and confirm you trust it. 3/18/2018 FIDES CA 23
Demo 8/13 (1) Check the Fingerprint value and confirm you trust it. 3/18/2018 FIDES CA 23
 Demo 9/13 (2) Right-click your Key Pair generated at step 2 and select Import CA Reply. This is NOT the same procedure as you did in step 7! 3/18/2018 FIDES CA 24
Demo 9/13 (2) Right-click your Key Pair generated at step 2 and select Import CA Reply. This is NOT the same procedure as you did in step 7! 3/18/2018 FIDES CA 24
 Demo 10/13 (2) Select the P 7 B file and confirm. There should be no errors. 3/18/2018 FIDES CA 25
Demo 10/13 (2) Select the P 7 B file and confirm. There should be no errors. 3/18/2018 FIDES CA 25
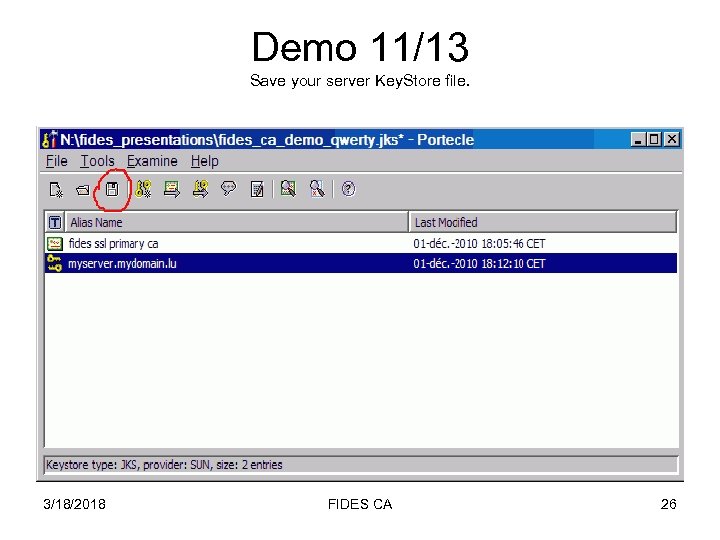 Demo 11/13 Save your server Key. Store file. 3/18/2018 FIDES CA 26
Demo 11/13 Save your server Key. Store file. 3/18/2018 FIDES CA 26
 Demo 12/13 (optional) If server software is not Java, export Private Key and signed Certificate into files. Right-click your Key Pair modified at step 10 and select Export. 3/18/2018 FIDES CA 27
Demo 12/13 (optional) If server software is not Java, export Private Key and signed Certificate into files. Right-click your Key Pair modified at step 10 and select Export. 3/18/2018 FIDES CA 27
 Demo 13/13 (optional) Choose Private Key and Certificates. For use in Apache, also choose PEM Encoded. Click OK. Then, supply the password from step 4 as Key Pair Entry Password. For use in Apache, leave Private Key Export Password blank to have it unencrypted. 3/18/2018 FIDES CA 28
Demo 13/13 (optional) Choose Private Key and Certificates. For use in Apache, also choose PEM Encoded. Click OK. Then, supply the password from step 4 as Key Pair Entry Password. For use in Apache, leave Private Key Export Password blank to have it unencrypted. 3/18/2018 FIDES CA 28


