134c547629b752357519f3c5de8dd61d.ppt
- Количество слайдов: 38
 FELK 19: Security of Wireless Networks* Mario Čagalj University of Split 2013/2014.
FELK 19: Security of Wireless Networks* Mario Čagalj University of Split 2013/2014.
 Wi. Fi (In)Security – 2 st part Assembled from different sources: Walker, Lehembre Buttyan, . . . Produced by Mario Čagalj
Wi. Fi (In)Security – 2 st part Assembled from different sources: Walker, Lehembre Buttyan, . . . Produced by Mario Čagalj
 Introduction: IEEE 802. 11 i We have seen that WEP is critically flawed IEEE 802. 11 i defined to properly secure wireless LANs (2004) Specifies robust security mechanisms for WLANs Defines Transition Security Network (TSN) Called Wi. Fi-Protected Access (WPA) by Wi. Fi-Alliance Based on “new” TKIP (that uses “old” RC 4 like WEP) Backward compatibility (with old RC 4 -only hardware) IEEE 802. 1 X authentication framework More importantly defines a Robust Security Network (RSN) Called Wi. Fi-Protected Access 2 (WPA 2) by Wi. Fi-Alliance Based on AES and optionally TKIP Also uses IEEE 802. 1 X authentication framework 3
Introduction: IEEE 802. 11 i We have seen that WEP is critically flawed IEEE 802. 11 i defined to properly secure wireless LANs (2004) Specifies robust security mechanisms for WLANs Defines Transition Security Network (TSN) Called Wi. Fi-Protected Access (WPA) by Wi. Fi-Alliance Based on “new” TKIP (that uses “old” RC 4 like WEP) Backward compatibility (with old RC 4 -only hardware) IEEE 802. 1 X authentication framework More importantly defines a Robust Security Network (RSN) Called Wi. Fi-Protected Access 2 (WPA 2) by Wi. Fi-Alliance Based on AES and optionally TKIP Also uses IEEE 802. 1 X authentication framework 3
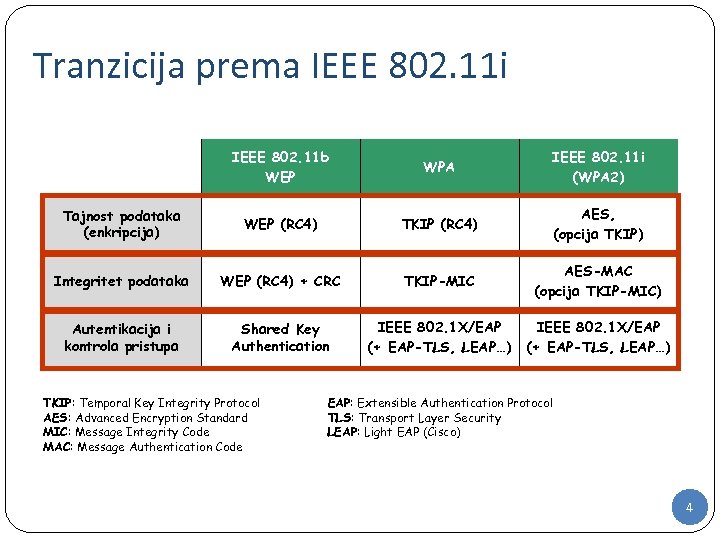 Tranzicija prema IEEE 802. 11 i IEEE 802. 11 b WEP WPA IEEE 802. 11 i (WPA 2) Tajnost podataka (enkripcija) WEP (RC 4) TKIP (RC 4) AES, (opcija TKIP) Integritet podataka WEP (RC 4) + CRC TKIP-MIC AES-MAC (opcija TKIP-MIC) Autentikacija i kontrola pristupa Shared Key Authentication IEEE 802. 1 X/EAP (+ EAP-TLS, LEAP…) TKIP: Temporal Key Integrity Protocol AES: Advanced Encryption Standard MIC: Message Integrity Code MAC: Message Authentication Code EAP: Extensible Authentication Protocol TLS: Transport Layer Security LEAP: Light EAP (Cisco) 4
Tranzicija prema IEEE 802. 11 i IEEE 802. 11 b WEP WPA IEEE 802. 11 i (WPA 2) Tajnost podataka (enkripcija) WEP (RC 4) TKIP (RC 4) AES, (opcija TKIP) Integritet podataka WEP (RC 4) + CRC TKIP-MIC AES-MAC (opcija TKIP-MIC) Autentikacija i kontrola pristupa Shared Key Authentication IEEE 802. 1 X/EAP (+ EAP-TLS, LEAP…) TKIP: Temporal Key Integrity Protocol AES: Advanced Encryption Standard MIC: Message Integrity Code MAC: Message Authentication Code EAP: Extensible Authentication Protocol TLS: Transport Layer Security LEAP: Light EAP (Cisco) 4
 Značajke IEEE 802. 11 i standarda Novine u IEEE 802. 11 i u usporedbi sa WEP-om Autentifikacija i kontrola pristupa zasnovana na IEEE 802. 1 X modelu Fleksibilan autentifikacijski okvir EAP (Extensible Authentication Protocol) Mogu se koristiti “dokazani” protokoli (npr. , TLS) Autentifikacijski proces rezultira sesijskim tajnim ključem Različite funkcije koriste različite ključeve koji se izvode iz sesijskog ključa Enkripcijska funkcija značajno poboljšana (AES, TKIP) Zaštita integriteta poruka značajno poboljšana AES-MAC i TKIP-MIC 5
Značajke IEEE 802. 11 i standarda Novine u IEEE 802. 11 i u usporedbi sa WEP-om Autentifikacija i kontrola pristupa zasnovana na IEEE 802. 1 X modelu Fleksibilan autentifikacijski okvir EAP (Extensible Authentication Protocol) Mogu se koristiti “dokazani” protokoli (npr. , TLS) Autentifikacijski proces rezultira sesijskim tajnim ključem Različite funkcije koriste različite ključeve koji se izvode iz sesijskog ključa Enkripcijska funkcija značajno poboljšana (AES, TKIP) Zaštita integriteta poruka značajno poboljšana AES-MAC i TKIP-MIC 5
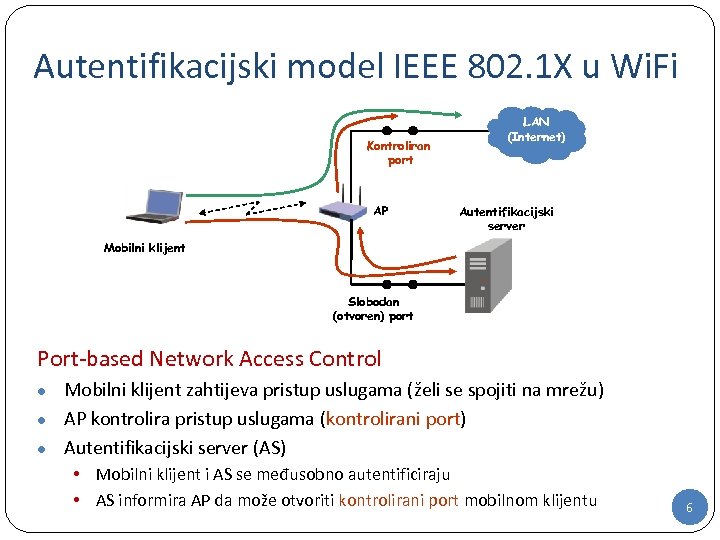 Autentifikacijski model IEEE 802. 1 X u Wi. Fi Kontroliran port AP LAN (Internet) Autentifikacijski server Mobilni klijent Slobodan (otvoren) port Port-based Network Access Control Mobilni klijent zahtijeva pristup uslugama (želi se spojiti na mrežu) ● AP kontrolira pristup uslugama (kontrolirani port) ● Autentifikacijski server (AS) ● • Mobilni klijent i AS se međusobno autentificiraju • AS informira AP da može otvoriti kontrolirani port mobilnom klijentu 6
Autentifikacijski model IEEE 802. 1 X u Wi. Fi Kontroliran port AP LAN (Internet) Autentifikacijski server Mobilni klijent Slobodan (otvoren) port Port-based Network Access Control Mobilni klijent zahtijeva pristup uslugama (želi se spojiti na mrežu) ● AP kontrolira pristup uslugama (kontrolirani port) ● Autentifikacijski server (AS) ● • Mobilni klijent i AS se međusobno autentificiraju • AS informira AP da može otvoriti kontrolirani port mobilnom klijentu 6
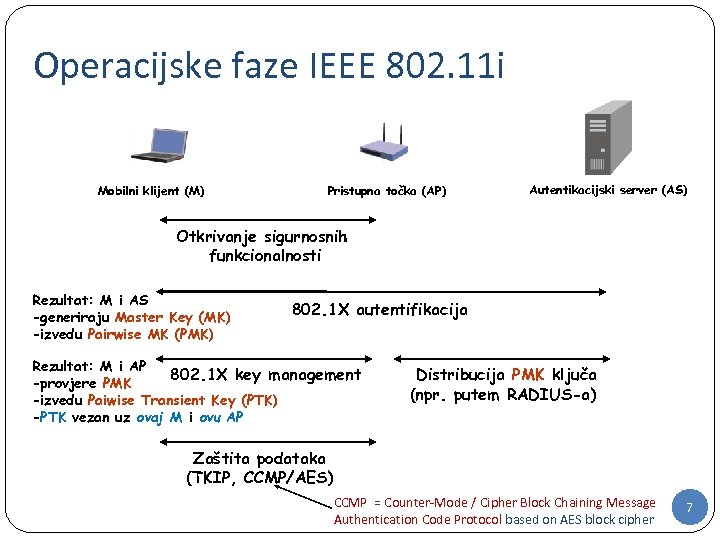 Operacijske faze IEEE 802. 11 i Mobilni klijent (M) Pristupna točka (AP) Autentikacijski server (AS) Otkrivanje sigurnosnih funkcionalnosti Rezultat: M i AS -generiraju Master Key (MK) -izvedu Pairwise MK (PMK) 802. 1 X autentifikacija Rezultat: M i AP 802. 1 X key management -provjere PMK -izvedu Paiwise Transient Key (PTK) -PTK vezan uz ovaj M i ovu AP Distribucija PMK ključa (npr. putem RADIUS-a) Zaštita podataka (TKIP, CCMP/AES) CCMP = Counter-Mode / Cipher Block Chaining Message Authentication Code Protocol based on AES block cipher 7
Operacijske faze IEEE 802. 11 i Mobilni klijent (M) Pristupna točka (AP) Autentikacijski server (AS) Otkrivanje sigurnosnih funkcionalnosti Rezultat: M i AS -generiraju Master Key (MK) -izvedu Pairwise MK (PMK) 802. 1 X autentifikacija Rezultat: M i AP 802. 1 X key management -provjere PMK -izvedu Paiwise Transient Key (PTK) -PTK vezan uz ovaj M i ovu AP Distribucija PMK ključa (npr. putem RADIUS-a) Zaštita podataka (TKIP, CCMP/AES) CCMP = Counter-Mode / Cipher Block Chaining Message Authentication Code Protocol based on AES block cipher 7
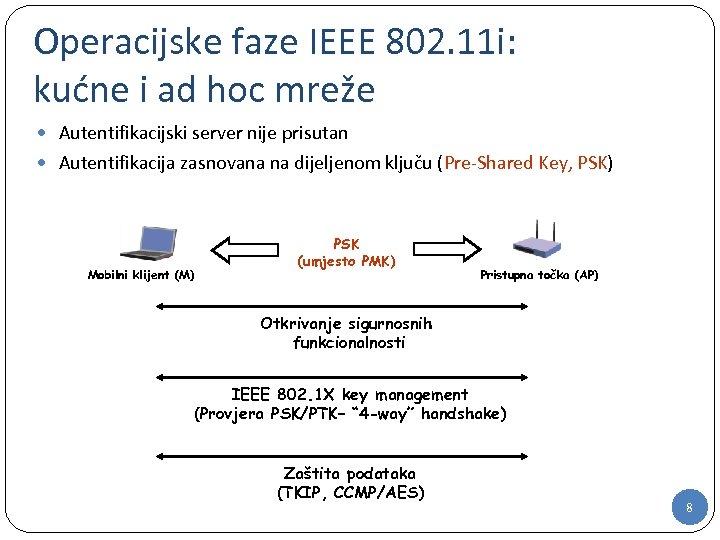 Operacijske faze IEEE 802. 11 i: kućne i ad hoc mreže Autentifikacijski server nije prisutan Autentifikacija zasnovana na dijeljenom ključu (Pre-Shared Key, PSK) Mobilni klijent (M) PSK (umjesto PMK) Pristupna točka (AP) Otkrivanje sigurnosnih funkcionalnosti IEEE 802. 1 X key management (Provjera PSK/PTK– “ 4 -way” handshake) Zaštita podataka (TKIP, CCMP/AES) 8
Operacijske faze IEEE 802. 11 i: kućne i ad hoc mreže Autentifikacijski server nije prisutan Autentifikacija zasnovana na dijeljenom ključu (Pre-Shared Key, PSK) Mobilni klijent (M) PSK (umjesto PMK) Pristupna točka (AP) Otkrivanje sigurnosnih funkcionalnosti IEEE 802. 1 X key management (Provjera PSK/PTK– “ 4 -way” handshake) Zaštita podataka (TKIP, CCMP/AES) 8
 Operational phases in IEEE 802. 11 i 1. 2. 3. 4. Agreeing on the security policy IEEE 802. 1 X authentication (absent in home nets) Key derivation and distribution Protecting data confidentiality and integrity 9
Operational phases in IEEE 802. 11 i 1. 2. 3. 4. Agreeing on the security policy IEEE 802. 1 X authentication (absent in home nets) Key derivation and distribution Protecting data confidentiality and integrity 9
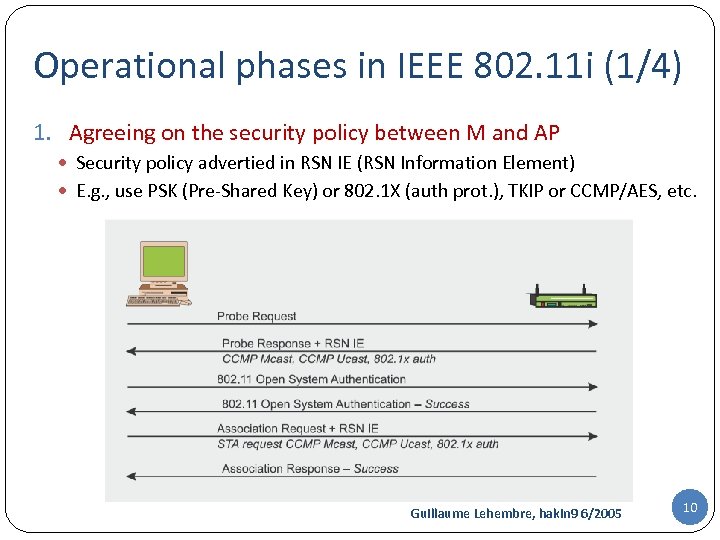 Operational phases in IEEE 802. 11 i (1/4) 1. Agreeing on the security policy between M and AP Security policy advertied in RSN IE (RSN Information Element) E. g. , use PSK (Pre-Shared Key) or 802. 1 X (auth prot. ), TKIP or CCMP/AES, etc. Guillaume Lehembre, hakin 9 6/2005 10
Operational phases in IEEE 802. 11 i (1/4) 1. Agreeing on the security policy between M and AP Security policy advertied in RSN IE (RSN Information Element) E. g. , use PSK (Pre-Shared Key) or 802. 1 X (auth prot. ), TKIP or CCMP/AES, etc. Guillaume Lehembre, hakin 9 6/2005 10
 Operational phases in IEEE 802. 11 i 1. 2. 3. 4. Agreeing on the security policy IEEE 802. 1 X authentication (absent in home nets) Key derivation and distribution Protecting data confidentiality and integrity 11
Operational phases in IEEE 802. 11 i 1. 2. 3. 4. Agreeing on the security policy IEEE 802. 1 X authentication (absent in home nets) Key derivation and distribution Protecting data confidentiality and integrity 11
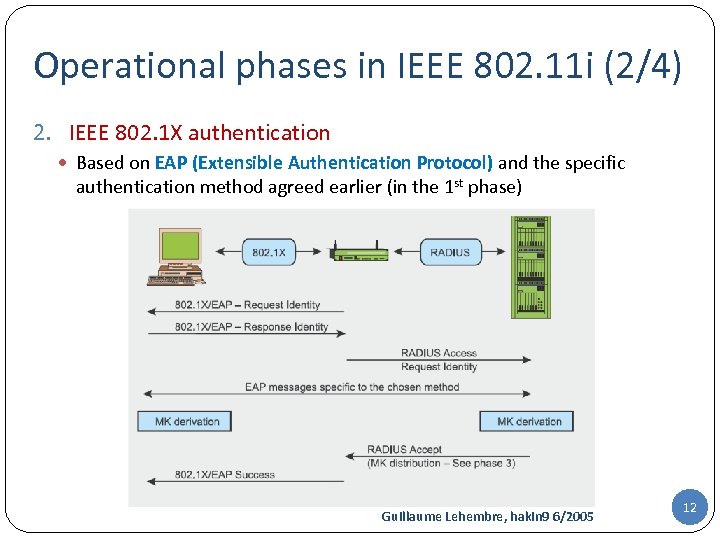 Operational phases in IEEE 802. 11 i (2/4) 2. IEEE 802. 1 X authentication Based on EAP (Extensible Authentication Protocol) and the specific authentication method agreed earlier (in the 1 st phase) Guillaume Lehembre, hakin 9 6/2005 12
Operational phases in IEEE 802. 11 i (2/4) 2. IEEE 802. 1 X authentication Based on EAP (Extensible Authentication Protocol) and the specific authentication method agreed earlier (in the 1 st phase) Guillaume Lehembre, hakin 9 6/2005 12
![IEEE 802. 1 X authentication (2 nd phase) EAP (Extensible Authentication Protocol) [RFC 3748] IEEE 802. 1 X authentication (2 nd phase) EAP (Extensible Authentication Protocol) [RFC 3748]](https://present5.com/presentation/134c547629b752357519f3c5de8dd61d/image-13.jpg) IEEE 802. 1 X authentication (2 nd phase) EAP (Extensible Authentication Protocol) [RFC 3748] carrier protocol designed to transport the messages of “real” authentication protocols (e. g. , TLS) very simple, four types of messages: EAP request – carries messages from AS to M EAP response – carries messages from M to the AS EAP success – signals successful authentication EAP failure – signals authentication failure authenticator (AP) doesn’t understand what is inside the EAP messages, it recognizes only EAP success and failure EAP is not an authentication method itself 13
IEEE 802. 1 X authentication (2 nd phase) EAP (Extensible Authentication Protocol) [RFC 3748] carrier protocol designed to transport the messages of “real” authentication protocols (e. g. , TLS) very simple, four types of messages: EAP request – carries messages from AS to M EAP response – carries messages from M to the AS EAP success – signals successful authentication EAP failure – signals authentication failure authenticator (AP) doesn’t understand what is inside the EAP messages, it recognizes only EAP success and failure EAP is not an authentication method itself 13
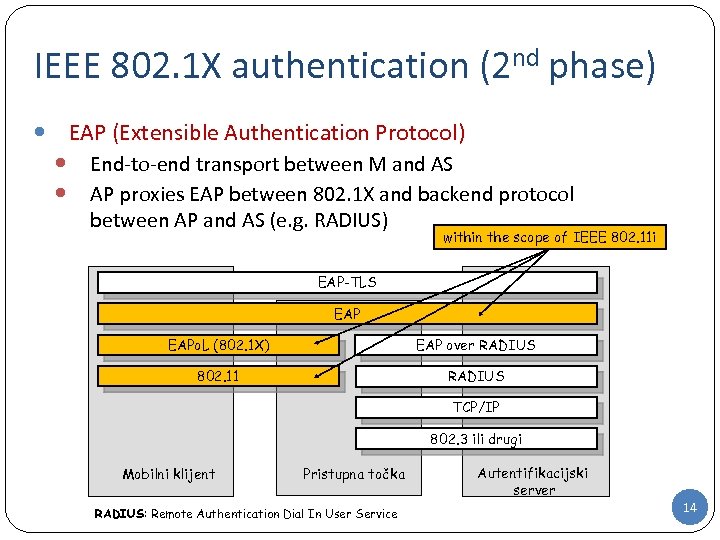 IEEE 802. 1 X authentication (2 nd phase) EAP (Extensible Authentication Protocol) End-to-end transport between M and AS AP proxies EAP between 802. 1 X and backend protocol between AP and AS (e. g. RADIUS) within the scope of IEEE 802. 11 i EAP-TLS EAPo. L (802. 1 X) EAP over RADIUS 802. 11 RADIUS TCP/IP 802. 3 ili drugi Mobilni klijent Pristupna točka RADIUS: Remote Authentication Dial In User Service Autentifikacijski server 14
IEEE 802. 1 X authentication (2 nd phase) EAP (Extensible Authentication Protocol) End-to-end transport between M and AS AP proxies EAP between 802. 1 X and backend protocol between AP and AS (e. g. RADIUS) within the scope of IEEE 802. 11 i EAP-TLS EAPo. L (802. 1 X) EAP over RADIUS 802. 11 RADIUS TCP/IP 802. 3 ili drugi Mobilni klijent Pristupna točka RADIUS: Remote Authentication Dial In User Service Autentifikacijski server 14
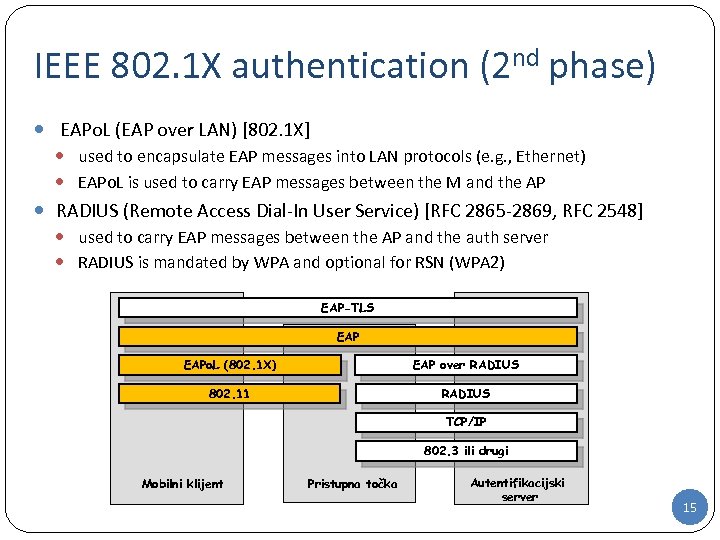 IEEE 802. 1 X authentication (2 nd phase) EAPo. L (EAP over LAN) [802. 1 X] used to encapsulate EAP messages into LAN protocols (e. g. , Ethernet) EAPo. L is used to carry EAP messages between the M and the AP RADIUS (Remote Access Dial-In User Service) [RFC 2865 -2869, RFC 2548] used to carry EAP messages between the AP and the auth server RADIUS is mandated by WPA and optional for RSN (WPA 2) EAP-TLS EAPo. L (802. 1 X) EAP over RADIUS 802. 11 RADIUS TCP/IP 802. 3 ili drugi Mobilni klijent Pristupna točka Autentifikacijski server 15
IEEE 802. 1 X authentication (2 nd phase) EAPo. L (EAP over LAN) [802. 1 X] used to encapsulate EAP messages into LAN protocols (e. g. , Ethernet) EAPo. L is used to carry EAP messages between the M and the AP RADIUS (Remote Access Dial-In User Service) [RFC 2865 -2869, RFC 2548] used to carry EAP messages between the AP and the auth server RADIUS is mandated by WPA and optional for RSN (WPA 2) EAP-TLS EAPo. L (802. 1 X) EAP over RADIUS 802. 11 RADIUS TCP/IP 802. 3 ili drugi Mobilni klijent Pristupna točka Autentifikacijski server 15
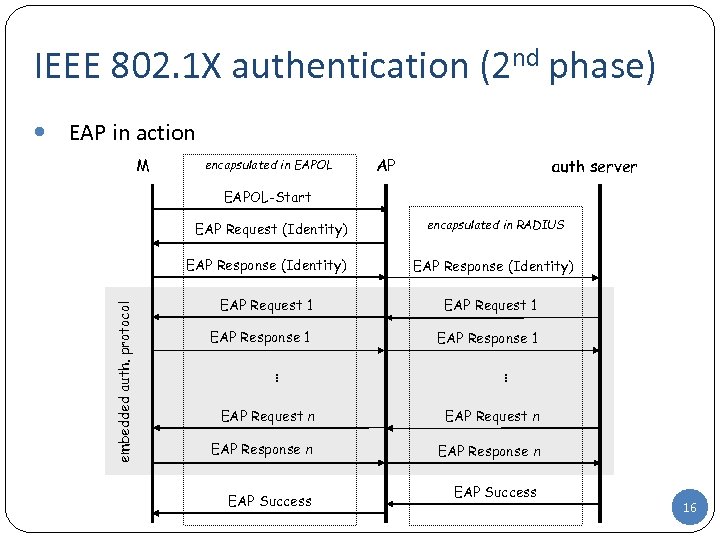 IEEE 802. 1 X authentication (2 nd phase) EAP in action M encapsulated in EAPOL AP auth server EAPOL-Start EAP Request (Identity) encapsulated in RADIUS EAP Response (Identity) EAP Request 1 EAP Response 1. . . embedded auth. protocol EAP Response (Identity) EAP Request n EAP Response n EAP Success 16
IEEE 802. 1 X authentication (2 nd phase) EAP in action M encapsulated in EAPOL AP auth server EAPOL-Start EAP Request (Identity) encapsulated in RADIUS EAP Response (Identity) EAP Request 1 EAP Response 1. . . embedded auth. protocol EAP Response (Identity) EAP Request n EAP Response n EAP Success 16
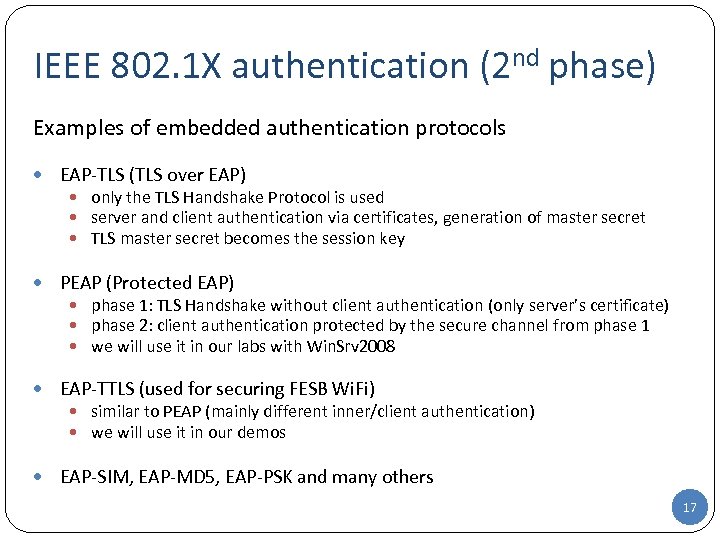 IEEE 802. 1 X authentication (2 nd phase) Examples of embedded authentication protocols EAP-TLS (TLS over EAP) only the TLS Handshake Protocol is used server and client authentication via certificates, generation of master secret TLS master secret becomes the session key PEAP (Protected EAP) phase 1: TLS Handshake without client authentication (only server’s certificate) phase 2: client authentication protected by the secure channel from phase 1 we will use it in our labs with Win. Srv 2008 EAP-TTLS (used for securing FESB Wi. Fi) similar to PEAP (mainly different inner/client authentication) we will use it in our demos EAP-SIM, EAP-MD 5, EAP-PSK and many others 17
IEEE 802. 1 X authentication (2 nd phase) Examples of embedded authentication protocols EAP-TLS (TLS over EAP) only the TLS Handshake Protocol is used server and client authentication via certificates, generation of master secret TLS master secret becomes the session key PEAP (Protected EAP) phase 1: TLS Handshake without client authentication (only server’s certificate) phase 2: client authentication protected by the secure channel from phase 1 we will use it in our labs with Win. Srv 2008 EAP-TTLS (used for securing FESB Wi. Fi) similar to PEAP (mainly different inner/client authentication) we will use it in our demos EAP-SIM, EAP-MD 5, EAP-PSK and many others 17
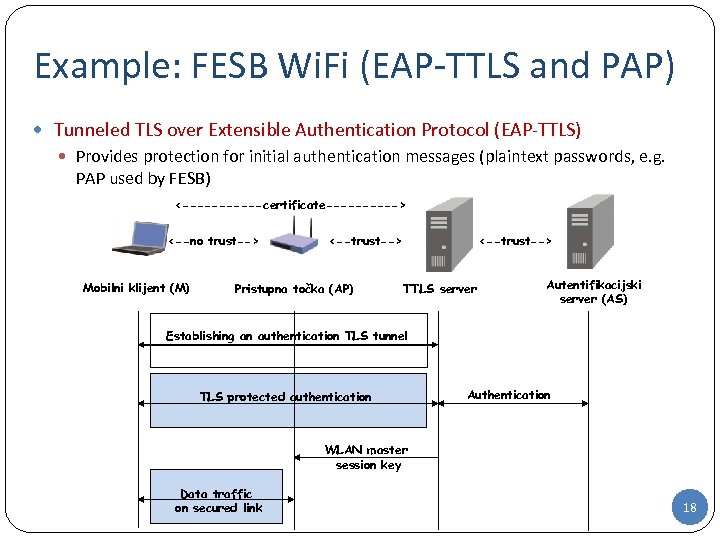 Example: FESB Wi. Fi (EAP-TTLS and PAP) Tunneled TLS over Extensible Authentication Protocol (EAP-TTLS) Provides protection for initial authentication messages (plaintext passwords, e. g. PAP used by FESB) <------certificate-----> <--no trust--> Mobilni klijent (M) <--trust--> Pristupna točka (AP) <--trust--> TTLS server Autentifikacijski server (AS) Establishing an authentication TLS tunnel TLS protected authentication Authentication WLAN master session key Data traffic on secured link 18
Example: FESB Wi. Fi (EAP-TTLS and PAP) Tunneled TLS over Extensible Authentication Protocol (EAP-TTLS) Provides protection for initial authentication messages (plaintext passwords, e. g. PAP used by FESB) <------certificate-----> <--no trust--> Mobilni klijent (M) <--trust--> Pristupna točka (AP) <--trust--> TTLS server Autentifikacijski server (AS) Establishing an authentication TLS tunnel TLS protected authentication Authentication WLAN master session key Data traffic on secured link 18
 IEEE 802. 1 X authentication summary At the end of authentication: The AS and M have established a session The AS and M possess a mutually authenticated Master Key (derived from the concrete EAP method) Master Key represents decision to grant access based on authentication M and AS have derived PMK (Pairwise Master Key) PMK is an authorization token to enforce access control decision at AP AS has distributed PMK to an AP (hopefully, to the M’s AP) 19
IEEE 802. 1 X authentication summary At the end of authentication: The AS and M have established a session The AS and M possess a mutually authenticated Master Key (derived from the concrete EAP method) Master Key represents decision to grant access based on authentication M and AS have derived PMK (Pairwise Master Key) PMK is an authorization token to enforce access control decision at AP AS has distributed PMK to an AP (hopefully, to the M’s AP) 19
 Operational phases in IEEE 802. 11 i 1. 2. 3. 4. Agreeing on the security policy IEEE 802. 1 X authentication (absent in home nets) Key derivation and distribution Protecting data confidentiality and integrity 20
Operational phases in IEEE 802. 11 i 1. 2. 3. 4. Agreeing on the security policy IEEE 802. 1 X authentication (absent in home nets) Key derivation and distribution Protecting data confidentiality and integrity 20
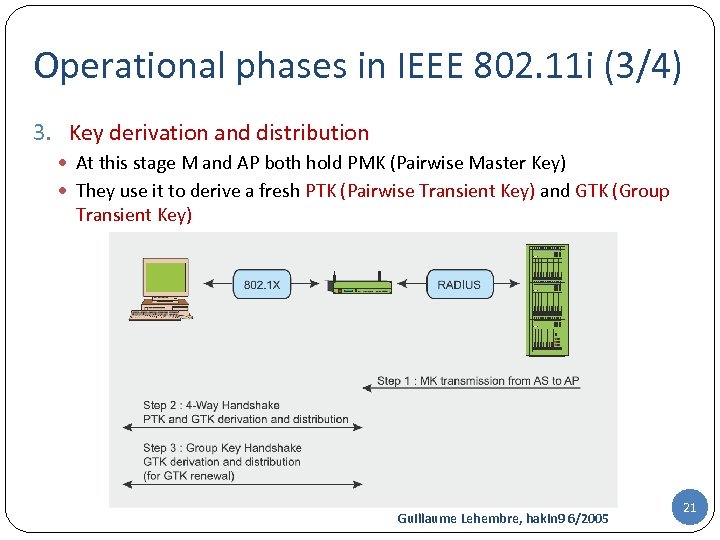 Operational phases in IEEE 802. 11 i (3/4) 3. Key derivation and distribution At this stage M and AP both hold PMK (Pairwise Master Key) They use it to derive a fresh PTK (Pairwise Transient Key) and GTK (Group Transient Key) Guillaume Lehembre, hakin 9 6/2005 21
Operational phases in IEEE 802. 11 i (3/4) 3. Key derivation and distribution At this stage M and AP both hold PMK (Pairwise Master Key) They use it to derive a fresh PTK (Pairwise Transient Key) and GTK (Group Transient Key) Guillaume Lehembre, hakin 9 6/2005 21
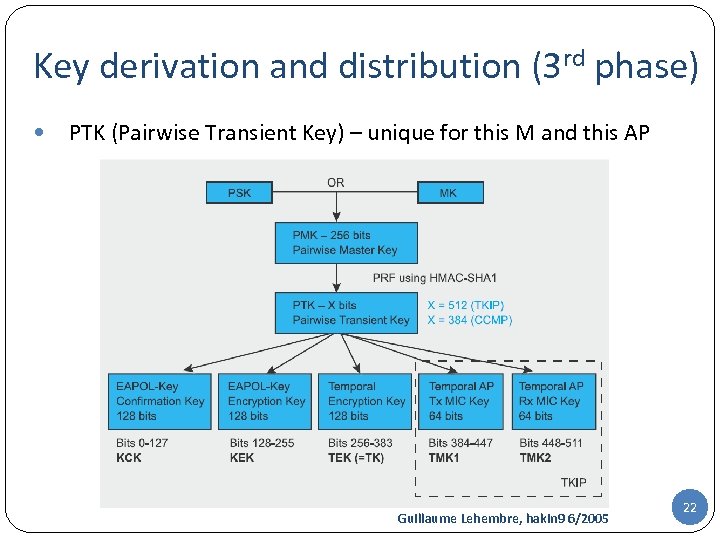 Key derivation and distribution (3 rd phase) PTK (Pairwise Transient Key) – unique for this M and this AP Guillaume Lehembre, hakin 9 6/2005 22
Key derivation and distribution (3 rd phase) PTK (Pairwise Transient Key) – unique for this M and this AP Guillaume Lehembre, hakin 9 6/2005 22
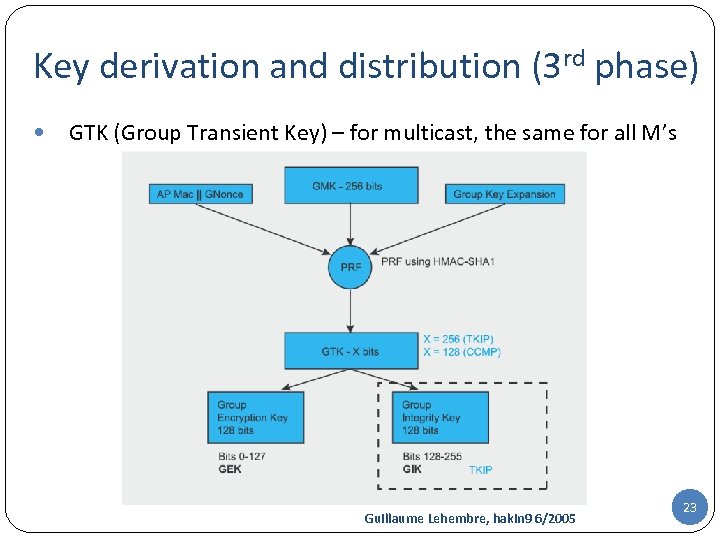 Key derivation and distribution (3 rd phase) GTK (Group Transient Key) – for multicast, the same for all M’s Guillaume Lehembre, hakin 9 6/2005 23
Key derivation and distribution (3 rd phase) GTK (Group Transient Key) – for multicast, the same for all M’s Guillaume Lehembre, hakin 9 6/2005 23
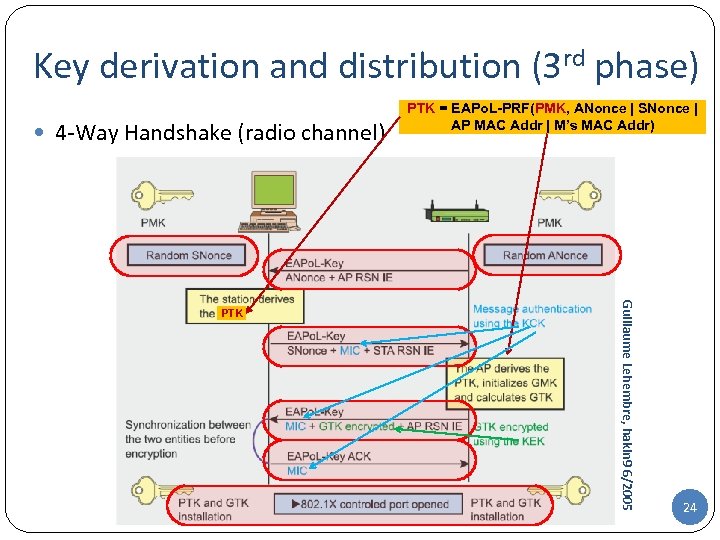 Key derivation and distribution (3 rd phase) 4 -Way Handshake (radio channel) Guillaume Lehembre, hakin 9 6/2005 PTK = EAPo. L-PRF(PMK, ANonce | SNonce | AP MAC Addr | M’s MAC Addr) 24
Key derivation and distribution (3 rd phase) 4 -Way Handshake (radio channel) Guillaume Lehembre, hakin 9 6/2005 PTK = EAPo. L-PRF(PMK, ANonce | SNonce | AP MAC Addr | M’s MAC Addr) 24
 Key derivation and distribution (3 rd phase) Key Management Summary 4 -Way Handshake Establishes a fresh pairwise key bound to M and AP for this session Proves liveness of peers Demonstrates there is no man-in-the-middle between PTK holders if there was no man-in-the-middle between PMK holders Synchronizes pairwise key use Provisions fresh group key GTK to all mobile stations (for multicast traffic) 25
Key derivation and distribution (3 rd phase) Key Management Summary 4 -Way Handshake Establishes a fresh pairwise key bound to M and AP for this session Proves liveness of peers Demonstrates there is no man-in-the-middle between PTK holders if there was no man-in-the-middle between PMK holders Synchronizes pairwise key use Provisions fresh group key GTK to all mobile stations (for multicast traffic) 25
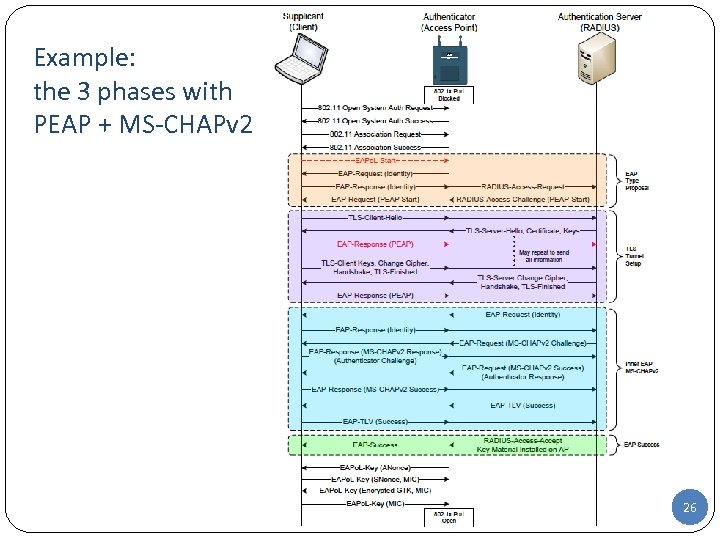 Example: the 3 phases with PEAP + MS-CHAPv 2 26
Example: the 3 phases with PEAP + MS-CHAPv 2 26
 Operational phases in IEEE 802. 11 i 1. 2. 3. 4. Agreeing on the security policy IEEE 802. 1 X authentication (absent in home nets) Key derivation and distribution Protecting data confidentiality and integrity 27
Operational phases in IEEE 802. 11 i 1. 2. 3. 4. Agreeing on the security policy IEEE 802. 1 X authentication (absent in home nets) Key derivation and distribution Protecting data confidentiality and integrity 27
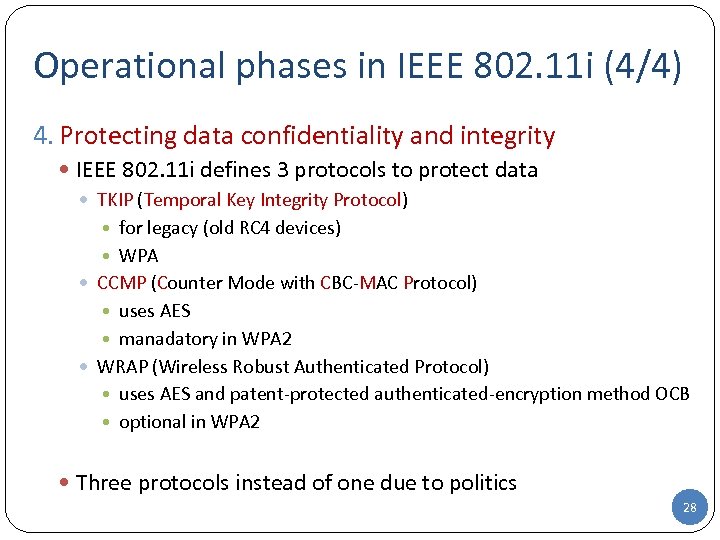 Operational phases in IEEE 802. 11 i (4/4) 4. Protecting data confidentiality and integrity IEEE 802. 11 i defines 3 protocols to protect data TKIP (Temporal Key Integrity Protocol) for legacy (old RC 4 devices) WPA CCMP (Counter Mode with CBC-MAC Protocol) uses AES manadatory in WPA 2 WRAP (Wireless Robust Authenticated Protocol) uses AES and patent-protected authenticated-encryption method OCB optional in WPA 2 Three protocols instead of one due to politics 28
Operational phases in IEEE 802. 11 i (4/4) 4. Protecting data confidentiality and integrity IEEE 802. 11 i defines 3 protocols to protect data TKIP (Temporal Key Integrity Protocol) for legacy (old RC 4 devices) WPA CCMP (Counter Mode with CBC-MAC Protocol) uses AES manadatory in WPA 2 WRAP (Wireless Robust Authenticated Protocol) uses AES and patent-protected authenticated-encryption method OCB optional in WPA 2 Three protocols instead of one due to politics 28
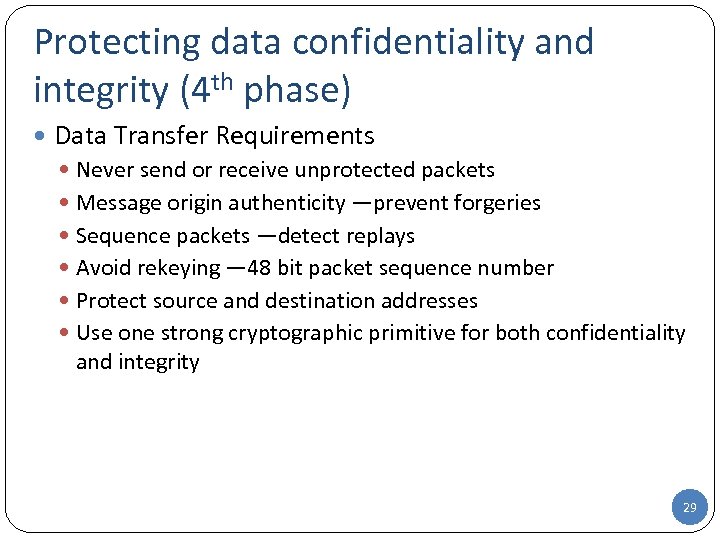 Protecting data confidentiality and integrity (4 th phase) Data Transfer Requirements Never send or receive unprotected packets Message origin authenticity —prevent forgeries Sequence packets —detect replays Avoid rekeying — 48 bit packet sequence number Protect source and destination addresses Use one strong cryptographic primitive for both confidentiality and integrity 29
Protecting data confidentiality and integrity (4 th phase) Data Transfer Requirements Never send or receive unprotected packets Message origin authenticity —prevent forgeries Sequence packets —detect replays Avoid rekeying — 48 bit packet sequence number Protect source and destination addresses Use one strong cryptographic primitive for both confidentiality and integrity 29
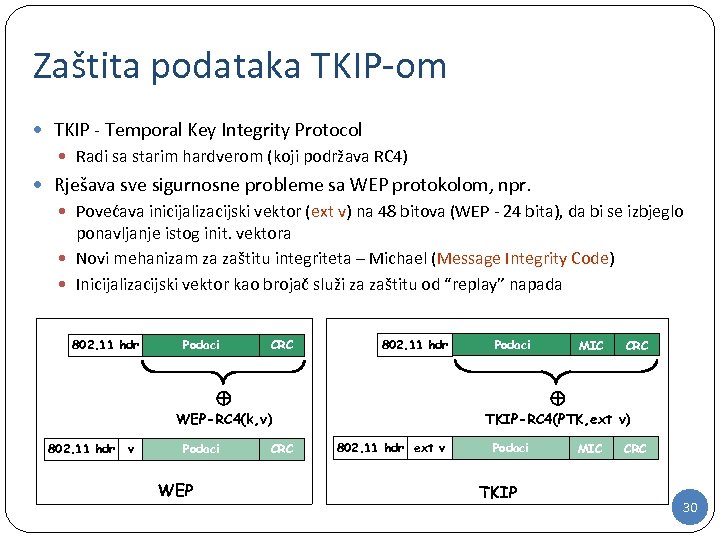 Zaštita podataka TKIP-om TKIP - Temporal Key Integrity Protocol Radi sa starim hardverom (koji podržava RC 4) Rješava sve sigurnosne probleme sa WEP protokolom, npr. Povećava inicijalizacijski vektor (ext v) na 48 bitova (WEP - 24 bita), da bi se izbjeglo ponavljanje istog init. vektora Novi mehanizam za zaštitu integriteta – Michael (Message Integrity Code) Inicijalizacijski vektor kao brojač služi za zaštitu od “replay” napada 802. 11 hdr Podaci CRC 802. 11 hdr Podaci WEP CRC TKIP-RC 4(PTK, ext v) WEP-RC 4(k, v) v MIC 802. 11 hdr Podaci 802. 11 hdr ext v Podaci TKIP MIC CRC 30
Zaštita podataka TKIP-om TKIP - Temporal Key Integrity Protocol Radi sa starim hardverom (koji podržava RC 4) Rješava sve sigurnosne probleme sa WEP protokolom, npr. Povećava inicijalizacijski vektor (ext v) na 48 bitova (WEP - 24 bita), da bi se izbjeglo ponavljanje istog init. vektora Novi mehanizam za zaštitu integriteta – Michael (Message Integrity Code) Inicijalizacijski vektor kao brojač služi za zaštitu od “replay” napada 802. 11 hdr Podaci CRC 802. 11 hdr Podaci WEP CRC TKIP-RC 4(PTK, ext v) WEP-RC 4(k, v) v MIC 802. 11 hdr Podaci 802. 11 hdr ext v Podaci TKIP MIC CRC 30
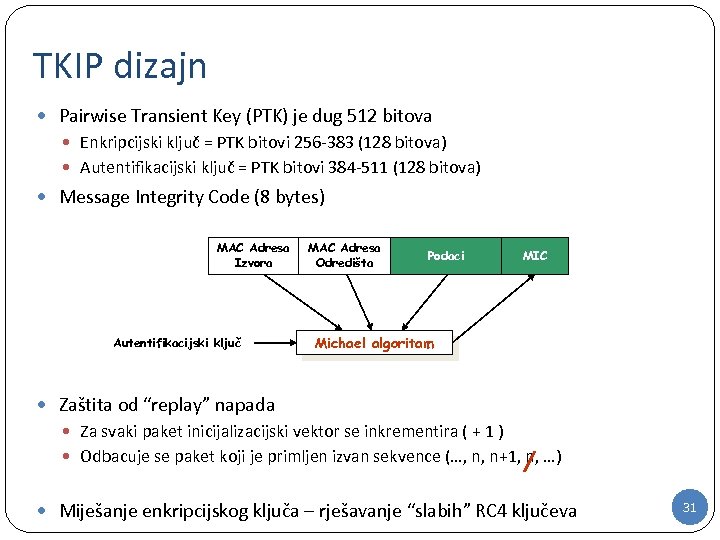 TKIP dizajn Pairwise Transient Key (PTK) je dug 512 bitova Enkripcijski ključ = PTK bitovi 256 -383 (128 bitova) Autentifikacijski ključ = PTK bitovi 384 -511 (128 bitova) Message Integrity Code (8 bytes) MAC Adresa Izvora Autentifikacijski ključ MAC Adresa Odredišta Podaci MIC Michael algoritam Zaštita od “replay” napada Za svaki paket inicijalizacijski vektor se inkrementira ( + 1 ) Odbacuje se paket koji je primljen izvan sekvence (…, n, n+1, n, …) Miješanje enkripcijskog ključa – rješavanje “slabih” RC 4 ključeva 31
TKIP dizajn Pairwise Transient Key (PTK) je dug 512 bitova Enkripcijski ključ = PTK bitovi 256 -383 (128 bitova) Autentifikacijski ključ = PTK bitovi 384 -511 (128 bitova) Message Integrity Code (8 bytes) MAC Adresa Izvora Autentifikacijski ključ MAC Adresa Odredišta Podaci MIC Michael algoritam Zaštita od “replay” napada Za svaki paket inicijalizacijski vektor se inkrementira ( + 1 ) Odbacuje se paket koji je primljen izvan sekvence (…, n, n+1, n, …) Miješanje enkripcijskog ključa – rješavanje “slabih” RC 4 ključeva 31
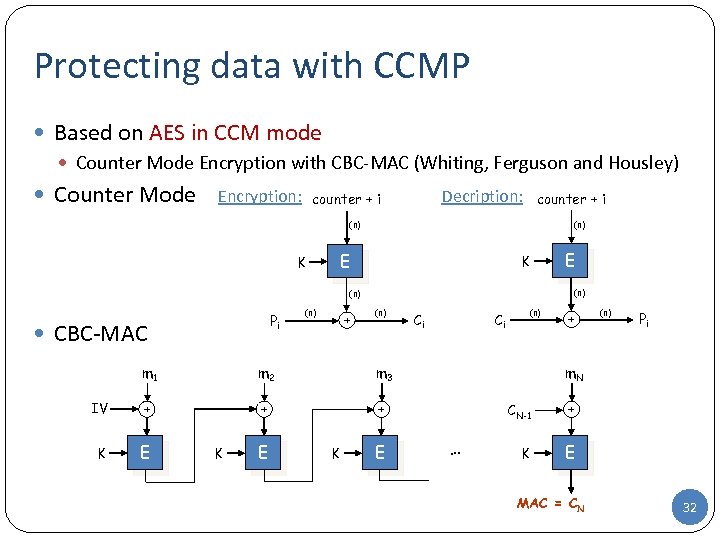 Protecting data with CCMP Based on AES in CCM mode Counter Mode Encryption with CBC-MAC (Whiting, Ferguson and Housley) Counter Mode Encryption: Decription: counter + i (n) E K K (n) Pi CBC-MAC (n) + (n) m 1 m 2 IV + + E Ci + K Ci (n) m 3 K E E + (n) Pi m. N CN-1 … + K E MAC = CN 32
Protecting data with CCMP Based on AES in CCM mode Counter Mode Encryption with CBC-MAC (Whiting, Ferguson and Housley) Counter Mode Encryption: Decription: counter + i (n) E K K (n) Pi CBC-MAC (n) + (n) m 1 m 2 IV + + E Ci + K Ci (n) m 3 K E E + (n) Pi m. N CN-1 … + K E MAC = CN 32
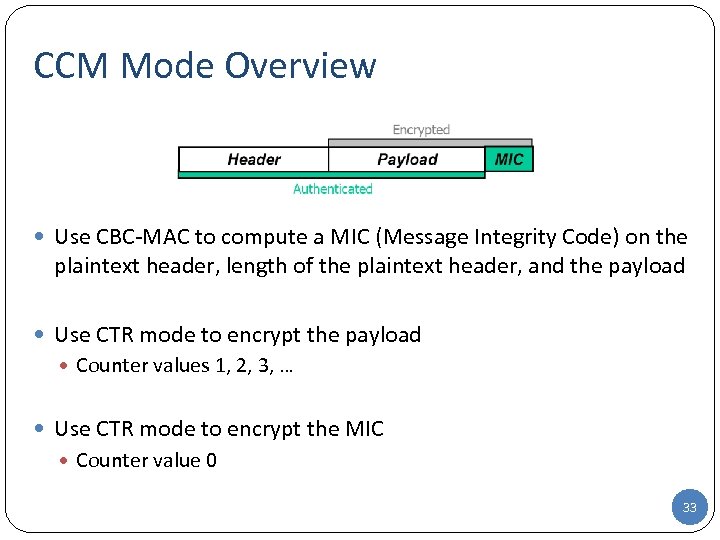 CCM Mode Overview Use CBC-MAC to compute a MIC (Message Integrity Code) on the plaintext header, length of the plaintext header, and the payload Use CTR mode to encrypt the payload Counter values 1, 2, 3, … Use CTR mode to encrypt the MIC Counter value 0 33
CCM Mode Overview Use CBC-MAC to compute a MIC (Message Integrity Code) on the plaintext header, length of the plaintext header, and the payload Use CTR mode to encrypt the payload Counter values 1, 2, 3, … Use CTR mode to encrypt the MIC Counter value 0 33
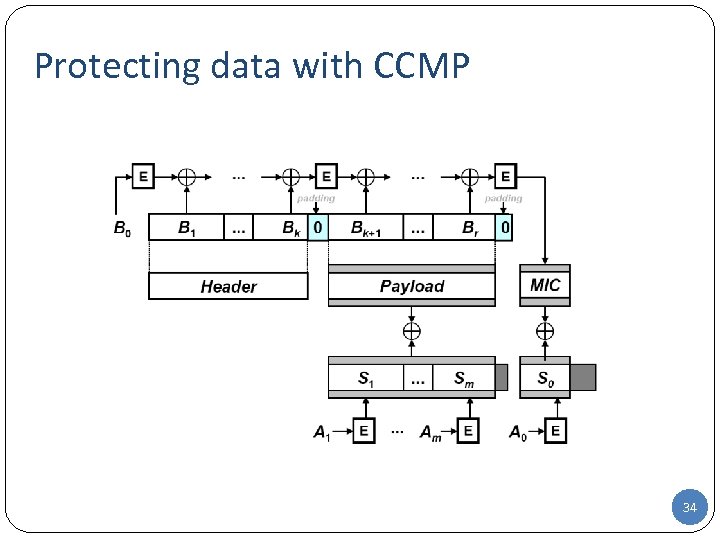 Protecting data with CCMP 34
Protecting data with CCMP 34
 Protecting data with CCMP CCM provides authenticity and privacy A CBC-MAC of the plaintext is appended to the plaintext to form an encoded plaintext The encoded plaintext is encrypted in CTR mode CCM is packet oriented CCM can leave any number of initial blocks of the plaintext unencrypted CCM has a high security level It is provably secure 35
Protecting data with CCMP CCM provides authenticity and privacy A CBC-MAC of the plaintext is appended to the plaintext to form an encoded plaintext The encoded plaintext is encrypted in CTR mode CCM is packet oriented CCM can leave any number of initial blocks of the plaintext unencrypted CCM has a high security level It is provably secure 35
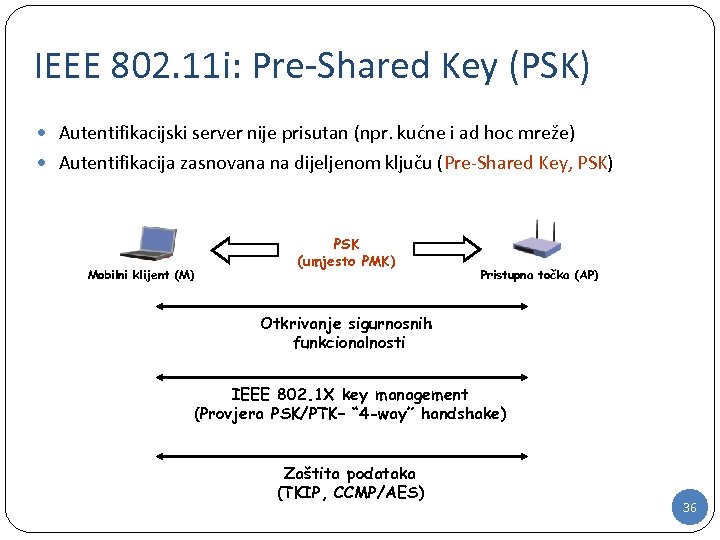 IEEE 802. 11 i: Pre-Shared Key (PSK) Autentifikacijski server nije prisutan (npr. kućne i ad hoc mreže) Autentifikacija zasnovana na dijeljenom ključu (Pre-Shared Key, PSK) Mobilni klijent (M) PSK (umjesto PMK) Pristupna točka (AP) Otkrivanje sigurnosnih funkcionalnosti IEEE 802. 1 X key management (Provjera PSK/PTK– “ 4 -way” handshake) Zaštita podataka (TKIP, CCMP/AES) 36
IEEE 802. 11 i: Pre-Shared Key (PSK) Autentifikacijski server nije prisutan (npr. kućne i ad hoc mreže) Autentifikacija zasnovana na dijeljenom ključu (Pre-Shared Key, PSK) Mobilni klijent (M) PSK (umjesto PMK) Pristupna točka (AP) Otkrivanje sigurnosnih funkcionalnosti IEEE 802. 1 X key management (Provjera PSK/PTK– “ 4 -way” handshake) Zaštita podataka (TKIP, CCMP/AES) 36
 IEEE 802. 11 i: Pre-Shared Key (PSK) No explicit authentication! The IEEE 802. 1 X authentication exchange absent Can have a single pre-shared key for entire network (insecure)… …or one per STA pair (secure) Password-to-Key Mapping Uses PKCS #5 v 2. 0 PBKDF 2 to generate a 256 -bit PSK from an ASCII password PMK=PSK = PBKDF 2 (Password, SSIDlength, 4096, 256) Salt = SSID, so PSK different for different SSIDs 4096 is the number of hashes used in this process 37
IEEE 802. 11 i: Pre-Shared Key (PSK) No explicit authentication! The IEEE 802. 1 X authentication exchange absent Can have a single pre-shared key for entire network (insecure)… …or one per STA pair (secure) Password-to-Key Mapping Uses PKCS #5 v 2. 0 PBKDF 2 to generate a 256 -bit PSK from an ASCII password PMK=PSK = PBKDF 2 (Password, SSIDlength, 4096, 256) Salt = SSID, so PSK different for different SSIDs 4096 is the number of hashes used in this process 37
 Next time Vulnerabilities of WPA, WPA 2, IEEE 802. 1 X 38
Next time Vulnerabilities of WPA, WPA 2, IEEE 802. 1 X 38


