f37542a1e93847ae45b0225c2a3f86e1.ppt
- Количество слайдов: 67
 FELK 19: Security of Wireless Networks Mario Čagalj University of Split 2013/2014.
FELK 19: Security of Wireless Networks Mario Čagalj University of Split 2013/2014.
 Administrativne informacije O predavaču Dr. sc. Mario Čagalj, izv. prof. http: //www. fesb. hr/~mcagalj Assistent Dr. sc. Toni Perković Web stranica predmeta http: //www. fesb. hr/~mcagalj/Wi. Sec Prezentacije s predavanja Razna literatura i reference Obavijesti (+ e. Learning) Konzultacije Email: {mario. cagalj, toperkov}@fesb. hr 2
Administrativne informacije O predavaču Dr. sc. Mario Čagalj, izv. prof. http: //www. fesb. hr/~mcagalj Assistent Dr. sc. Toni Perković Web stranica predmeta http: //www. fesb. hr/~mcagalj/Wi. Sec Prezentacije s predavanja Razna literatura i reference Obavijesti (+ e. Learning) Konzultacije Email: {mario. cagalj, toperkov}@fesb. hr 2
 Način provjere znanja Dva kolokvija Nakon 7. odnosno 13. tjedna nastave Laboratorijske vježbe Predana izvješća preduvjet za upis ocjene Ocjenjivanje A - Prisustvo (predavanja i lab) B - Izvješća s laboratorijskih vježbi C - 1. kolokvij D - 2. kolokvij (cijelo gradivo) Ocjena = Zaokruži (0. 05*A + 0. 2*B + 0. 30*C + 0. 45*D) 3
Način provjere znanja Dva kolokvija Nakon 7. odnosno 13. tjedna nastave Laboratorijske vježbe Predana izvješća preduvjet za upis ocjene Ocjenjivanje A - Prisustvo (predavanja i lab) B - Izvješća s laboratorijskih vježbi C - 1. kolokvij D - 2. kolokvij (cijelo gradivo) Ocjena = Zaokruži (0. 05*A + 0. 2*B + 0. 30*C + 0. 45*D) 3
 Literatura Prezentacije s predavanja Dio tema pokrivaju sljedeće knjige Buttyan L. and Hubaux J. -P. , “Security and Cooperation in Wireless Networks”, Cambridge University Press, 2008. (dostupna online http: //secowinet. epfl. ch) Menezes J. , van Oorschot P. C. and Vanstone S. A. , “Handbook of Applied Cryptography”, CRC Press, 1996. (dostupna online http: //www. cacr. math. uwaterloo. ca/hac) Adamy D. , “A First Course on Electronic Warfare”, Artech House, 2001. Dio tema baziran je na znanstvenim člancima (vidi web) 4
Literatura Prezentacije s predavanja Dio tema pokrivaju sljedeće knjige Buttyan L. and Hubaux J. -P. , “Security and Cooperation in Wireless Networks”, Cambridge University Press, 2008. (dostupna online http: //secowinet. epfl. ch) Menezes J. , van Oorschot P. C. and Vanstone S. A. , “Handbook of Applied Cryptography”, CRC Press, 1996. (dostupna online http: //www. cacr. math. uwaterloo. ca/hac) Adamy D. , “A First Course on Electronic Warfare”, Artech House, 2001. Dio tema baziran je na znanstvenim člancima (vidi web) 4
 Tentativni pregled nastavnih jedinica Uvod Radio komunikacijski kanal Napadi ometanjem signala (radio jamming) Prisluškivanje i napadi prijenosom komunikacije (relay attacks) Zaštita od ometanja signala: tehnike raspršenog spektra (FHSS i DSSS) Pregled osnovnih kriptografskih primitiva Sigurnost Wi. Fi mreža (IEEE 802. 11 arhitekture, WEP, WPA 2, 802. 11 i, anomalije) 1. kolokvij Sigurnost cellularnih mreža (GSM, UMTS, man-in-the-middle) Ranjivost bežičnih navigacijskih sustava (GPS, Gallileo) Sigurnost bežičnih senzorskih mreža (inicijalizacija, uspostava enkripcijskih ključeva) User-friendly autentifikacija poruka preko radio kanala (I-codes, uparivanje uređaja) Lokacijska privatnost u bežičnim mrežama 2. kolokvij 5
Tentativni pregled nastavnih jedinica Uvod Radio komunikacijski kanal Napadi ometanjem signala (radio jamming) Prisluškivanje i napadi prijenosom komunikacije (relay attacks) Zaštita od ometanja signala: tehnike raspršenog spektra (FHSS i DSSS) Pregled osnovnih kriptografskih primitiva Sigurnost Wi. Fi mreža (IEEE 802. 11 arhitekture, WEP, WPA 2, 802. 11 i, anomalije) 1. kolokvij Sigurnost cellularnih mreža (GSM, UMTS, man-in-the-middle) Ranjivost bežičnih navigacijskih sustava (GPS, Gallileo) Sigurnost bežičnih senzorskih mreža (inicijalizacija, uspostava enkripcijskih ključeva) User-friendly autentifikacija poruka preko radio kanala (I-codes, uparivanje uređaja) Lokacijska privatnost u bežičnim mrežama 2. kolokvij 5
 Laboratorijske vježbe (hands-on/demo) Ranjivost radio kanala Denial-of-service ometanjem signala, Mit. M putem ARP spoofing napada, prisluškivanje i analiza podataka Osnovni kriptografski primitivi (Cryptool 2) Sigurnost Wi. Fi mreža Probijanje WEP i WPA/WPA 2, lažne pristupne točke SSL stripping napad, propusti u konfiguraciji EAP-TTLS metode (FESB) Konfiguracija naprednih autentifikacijskim metoda: Win. Srv 2008 i kontroler pristupnih točaka Anomalija u performansama IEEE 802. 11 standarda Reduction/denial-of-service napadi Sigurnost u celularnim 2 G/3 G mrežama Mit. M i Do. S napadi Softverski radio 6
Laboratorijske vježbe (hands-on/demo) Ranjivost radio kanala Denial-of-service ometanjem signala, Mit. M putem ARP spoofing napada, prisluškivanje i analiza podataka Osnovni kriptografski primitivi (Cryptool 2) Sigurnost Wi. Fi mreža Probijanje WEP i WPA/WPA 2, lažne pristupne točke SSL stripping napad, propusti u konfiguraciji EAP-TTLS metode (FESB) Konfiguracija naprednih autentifikacijskim metoda: Win. Srv 2008 i kontroler pristupnih točaka Anomalija u performansama IEEE 802. 11 standarda Reduction/denial-of-service napadi Sigurnost u celularnim 2 G/3 G mrežama Mit. M i Do. S napadi Softverski radio 6
 Moto ovog kolegija Think outside the box http: //www. rojish. com/how-to-think-out-of-the-box-to-succeed-with-blogging/ 7
Moto ovog kolegija Think outside the box http: //www. rojish. com/how-to-think-out-of-the-box-to-succeed-with-blogging/ 7
 Introduction: Wireless Networks
Introduction: Wireless Networks
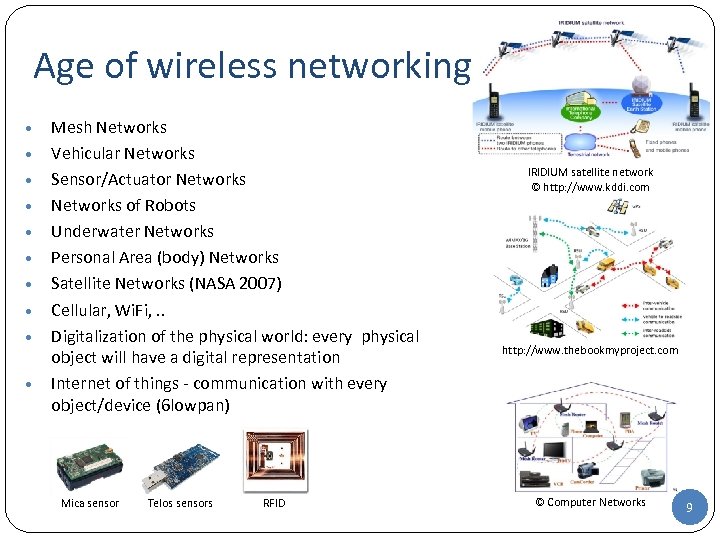 Age of wireless networking • • • Mesh Networks Vehicular Networks Sensor/Actuator Networks of Robots Underwater Networks Personal Area (body) Networks Satellite Networks (NASA 2007) Cellular, Wi. Fi, . . Digitalization of the physical world: every physical object will have a digital representation Internet of things - communication with every object/device (6 lowpan) Mica sensor Telos sensors RFID IRIDIUM satellite network © http: //www. kddi. com http: //www. thebookmyproject. com © Computer Networks 9
Age of wireless networking • • • Mesh Networks Vehicular Networks Sensor/Actuator Networks of Robots Underwater Networks Personal Area (body) Networks Satellite Networks (NASA 2007) Cellular, Wi. Fi, . . Digitalization of the physical world: every physical object will have a digital representation Internet of things - communication with every object/device (6 lowpan) Mica sensor Telos sensors RFID IRIDIUM satellite network © http: //www. kddi. com http: //www. thebookmyproject. com © Computer Networks 9
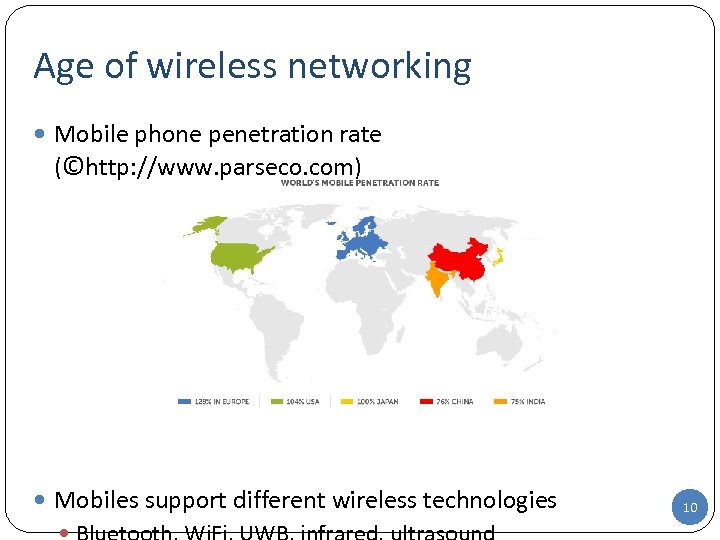 Age of wireless networking Mobile phone penetration rate (©http: //www. parseco. com) Mobiles support different wireless technologies 10
Age of wireless networking Mobile phone penetration rate (©http: //www. parseco. com) Mobiles support different wireless technologies 10
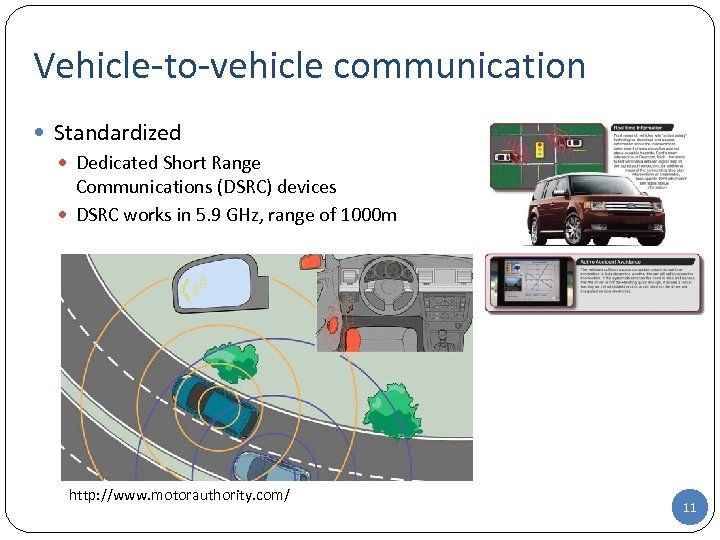 Vehicle-to-vehicle communication Standardized Dedicated Short Range Communications (DSRC) devices DSRC works in 5. 9 GHz, range of 1000 m http: //www. motorauthority. com/ 11
Vehicle-to-vehicle communication Standardized Dedicated Short Range Communications (DSRC) devices DSRC works in 5. 9 GHz, range of 1000 m http: //www. motorauthority. com/ 11
 Wireless/mobile healthcare Wireless pacemakers Daily monitoring and alerting No wires, less intrusive and less infections Wireless brain sensors/implants Developed at Brown University Wireless bionic eye A camera, attached to a pair of glasses, transmits high-frequency radio signals to a microchip implanted in the retina or directly into the brain 12
Wireless/mobile healthcare Wireless pacemakers Daily monitoring and alerting No wires, less intrusive and less infections Wireless brain sensors/implants Developed at Brown University Wireless bionic eye A camera, attached to a pair of glasses, transmits high-frequency radio signals to a microchip implanted in the retina or directly into the brain 12
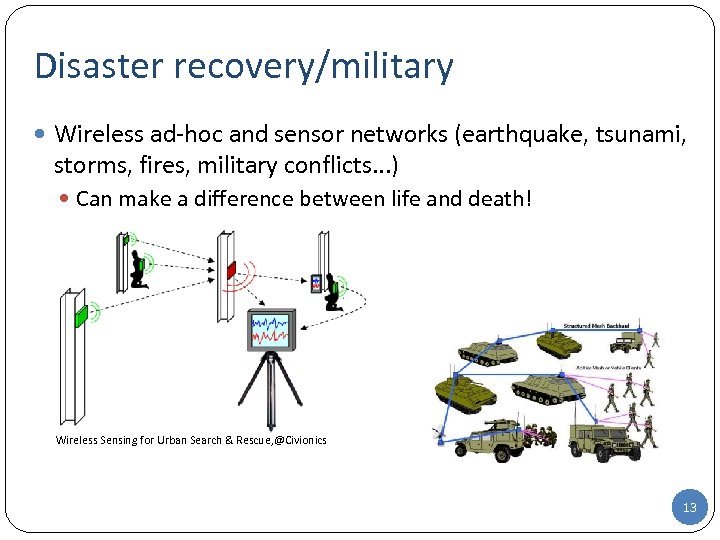 Disaster recovery/military Wireless ad-hoc and sensor networks (earthquake, tsunami, storms, fires, military conflicts. . . ) Can make a difference between life and death! Wireless Sensing for Urban Search & Rescue, @Civionics 13
Disaster recovery/military Wireless ad-hoc and sensor networks (earthquake, tsunami, storms, fires, military conflicts. . . ) Can make a difference between life and death! Wireless Sensing for Urban Search & Rescue, @Civionics 13
 Machine-2 -machine (m 2 m) systems Telemetry systems Enable remote communication between machines and other machines and people Smart meetering, smart grid, smart parking, smart home http: //www. libelium. com 14
Machine-2 -machine (m 2 m) systems Telemetry systems Enable remote communication between machines and other machines and people Smart meetering, smart grid, smart parking, smart home http: //www. libelium. com 14
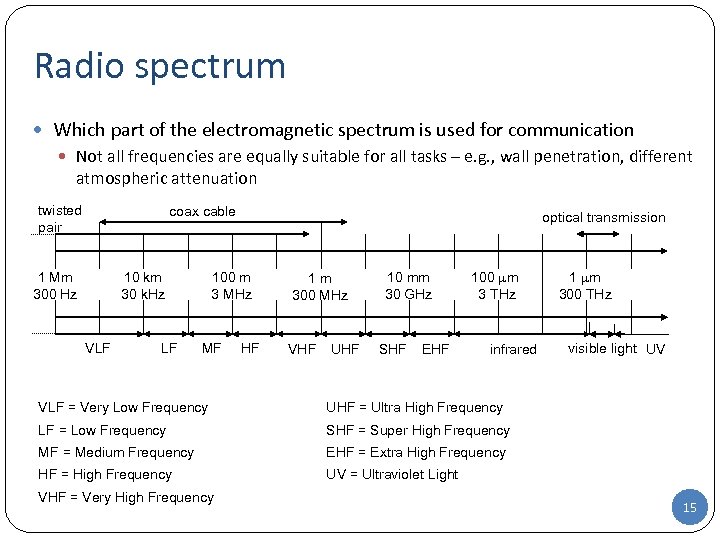 Radio spectrum Which part of the electromagnetic spectrum is used for communication Not all frequencies are equally suitable for all tasks – e. g. , wall penetration, different atmospheric attenuation twisted pair coax cable 1 Mm 300 Hz 10 km 30 k. Hz VLF LF optical transmission 100 m 3 MHz MF HF 1 m 300 MHz VHF UHF 10 mm 30 GHz SHF EHF 100 m 3 THz infrared VLF = Very Low Frequency SHF = Super High Frequency MF = Medium Frequency EHF = Extra High Frequency HF = High Frequency visible light UV UHF = Ultra High Frequency LF = Low Frequency 1 m 300 THz UV = Ultraviolet Light VHF = Very High Frequency 15
Radio spectrum Which part of the electromagnetic spectrum is used for communication Not all frequencies are equally suitable for all tasks – e. g. , wall penetration, different atmospheric attenuation twisted pair coax cable 1 Mm 300 Hz 10 km 30 k. Hz VLF LF optical transmission 100 m 3 MHz MF HF 1 m 300 MHz VHF UHF 10 mm 30 GHz SHF EHF 100 m 3 THz infrared VLF = Very Low Frequency SHF = Super High Frequency MF = Medium Frequency EHF = Extra High Frequency HF = High Frequency visible light UV UHF = Ultra High Frequency LF = Low Frequency 1 m 300 THz UV = Ultraviolet Light VHF = Very High Frequency 15
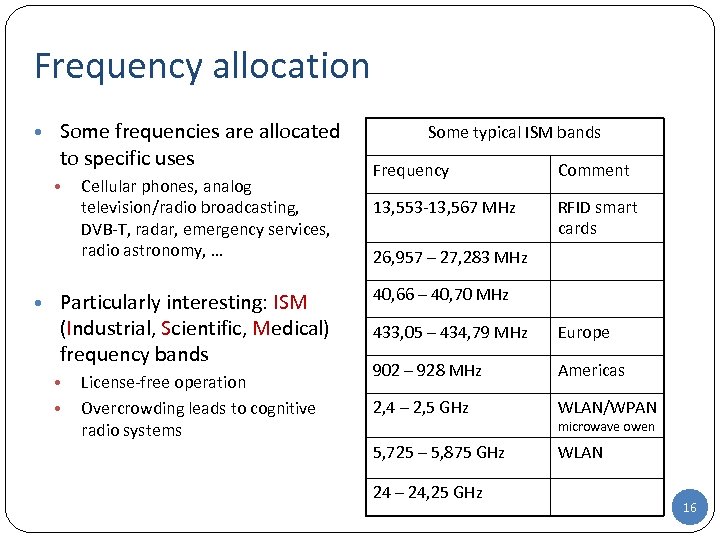 Frequency allocation • Some frequencies are allocated to specific uses • Cellular phones, analog television/radio broadcasting, DVB-T, radar, emergency services, radio astronomy, … • Particularly interesting: ISM (Industrial, Scientific, Medical) frequency bands • • License-free operation Overcrowding leads to cognitive radio systems Some typical ISM bands Frequency Comment 13, 553 -13, 567 MHz RFID smart cards 26, 957 – 27, 283 MHz 40, 66 – 40, 70 MHz 433, 05 – 434, 79 MHz Europe 902 – 928 MHz Americas 2, 4 – 2, 5 GHz WLAN/WPAN 5, 725 – 5, 875 GHz WLAN 24 – 24, 25 GHz microwave owen 16
Frequency allocation • Some frequencies are allocated to specific uses • Cellular phones, analog television/radio broadcasting, DVB-T, radar, emergency services, radio astronomy, … • Particularly interesting: ISM (Industrial, Scientific, Medical) frequency bands • • License-free operation Overcrowding leads to cognitive radio systems Some typical ISM bands Frequency Comment 13, 553 -13, 567 MHz RFID smart cards 26, 957 – 27, 283 MHz 40, 66 – 40, 70 MHz 433, 05 – 434, 79 MHz Europe 902 – 928 MHz Americas 2, 4 – 2, 5 GHz WLAN/WPAN 5, 725 – 5, 875 GHz WLAN 24 – 24, 25 GHz microwave owen 16
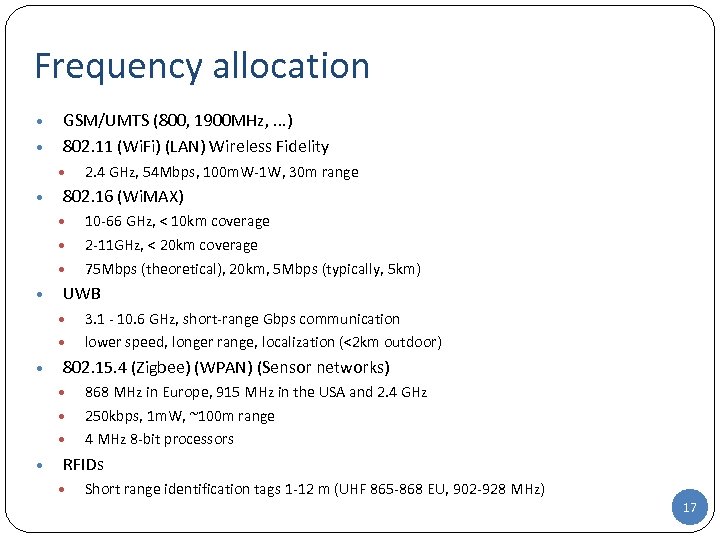 Frequency allocation • • GSM/UMTS (800, 1900 MHz, . . . ) 802. 11 (Wi. Fi) (LAN) Wireless Fidelity • • 802. 16 (Wi. MAX) • • • 3. 1 - 10. 6 GHz, short-range Gbps communication lower speed, longer range, localization (<2 km outdoor) 802. 15. 4 (Zigbee) (WPAN) (Sensor networks) • • 10 -66 GHz, < 10 km coverage 2 -11 GHz, < 20 km coverage 75 Mbps (theoretical), 20 km, 5 Mbps (typically, 5 km) UWB • • 2. 4 GHz, 54 Mbps, 100 m. W-1 W, 30 m range 868 MHz in Europe, 915 MHz in the USA and 2. 4 GHz 250 kbps, 1 m. W, ~100 m range 4 MHz 8 -bit processors RFIDs • Short range identification tags 1 -12 m (UHF 865 -868 EU, 902 -928 MHz) 17
Frequency allocation • • GSM/UMTS (800, 1900 MHz, . . . ) 802. 11 (Wi. Fi) (LAN) Wireless Fidelity • • 802. 16 (Wi. MAX) • • • 3. 1 - 10. 6 GHz, short-range Gbps communication lower speed, longer range, localization (<2 km outdoor) 802. 15. 4 (Zigbee) (WPAN) (Sensor networks) • • 10 -66 GHz, < 10 km coverage 2 -11 GHz, < 20 km coverage 75 Mbps (theoretical), 20 km, 5 Mbps (typically, 5 km) UWB • • 2. 4 GHz, 54 Mbps, 100 m. W-1 W, 30 m range 868 MHz in Europe, 915 MHz in the USA and 2. 4 GHz 250 kbps, 1 m. W, ~100 m range 4 MHz 8 -bit processors RFIDs • Short range identification tags 1 -12 m (UHF 865 -868 EU, 902 -928 MHz) 17
 Applications of wireless networks • Infrastructure-based • • Cellular – any data Wi. Fi access – any data GPS – location, time Local Area (Indoor) Navigation – location, time • Infrastructure-less (multi-hop) • • • Sensor networks – environmental (sensed) values Ad hoc (e. g. vehicular network) – any data Mesh networks (e. g. , home networks) – any data • RFID (Radio Frequency Identification) tags – identity 18
Applications of wireless networks • Infrastructure-based • • Cellular – any data Wi. Fi access – any data GPS – location, time Local Area (Indoor) Navigation – location, time • Infrastructure-less (multi-hop) • • • Sensor networks – environmental (sensed) values Ad hoc (e. g. vehicular network) – any data Mesh networks (e. g. , home networks) – any data • RFID (Radio Frequency Identification) tags – identity 18
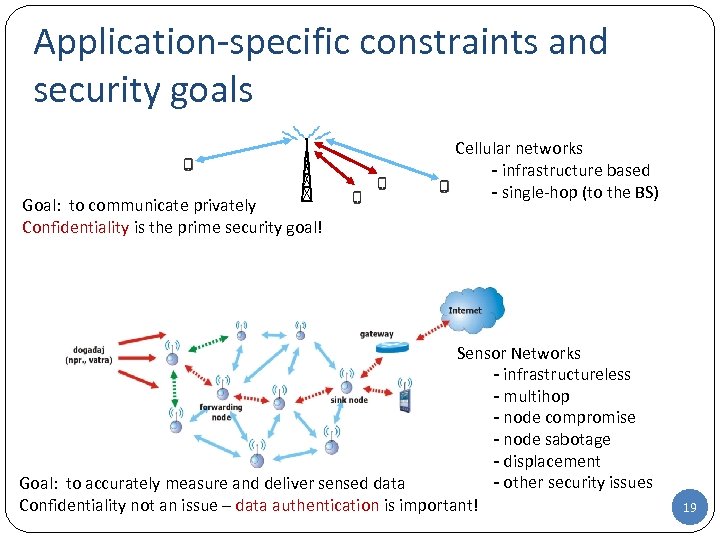 Application-specific constraints and security goals Goal: to communicate privately Confidentiality is the prime security goal! Cellular networks - infrastructure based - single-hop (to the BS) Sensor Networks - infrastructureless - multihop - node compromise - node sabotage - displacement - other security issues Goal: to accurately measure and deliver sensed data Confidentiality not an issue – data authentication is important! 19
Application-specific constraints and security goals Goal: to communicate privately Confidentiality is the prime security goal! Cellular networks - infrastructure based - single-hop (to the BS) Sensor Networks - infrastructureless - multihop - node compromise - node sabotage - displacement - other security issues Goal: to accurately measure and deliver sensed data Confidentiality not an issue – data authentication is important! 19
 This lecture • Wireless/radio communication • Message relay attacks • Eavesdropping • Message insertion • Relay attacks in practice 20
This lecture • Wireless/radio communication • Message relay attacks • Eavesdropping • Message insertion • Relay attacks in practice 20
 Wireless Communication
Wireless Communication
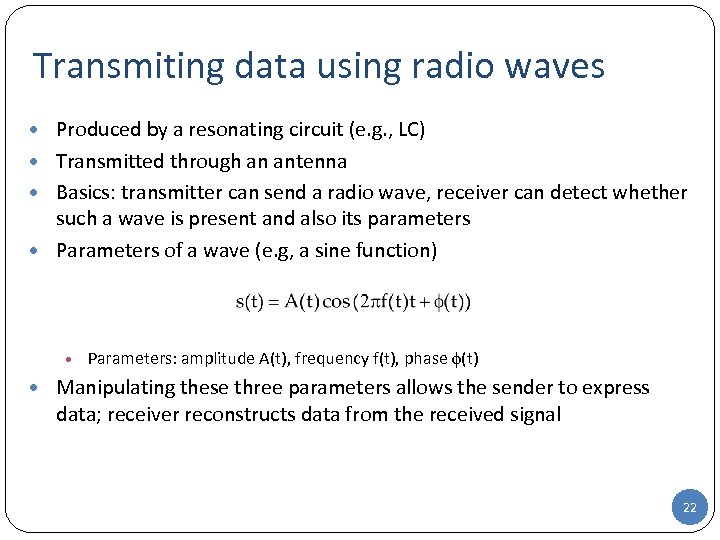 Transmiting data using radio waves • Produced by a resonating circuit (e. g. , LC) • Transmitted through an antenna • Basics: transmitter can send a radio wave, receiver can detect whether such a wave is present and also its parameters • Parameters of a wave (e. g, a sine function) • Parameters: amplitude A(t), frequency f(t), phase (t) • Manipulating these three parameters allows the sender to express data; receiver reconstructs data from the received signal 22
Transmiting data using radio waves • Produced by a resonating circuit (e. g. , LC) • Transmitted through an antenna • Basics: transmitter can send a radio wave, receiver can detect whether such a wave is present and also its parameters • Parameters of a wave (e. g, a sine function) • Parameters: amplitude A(t), frequency f(t), phase (t) • Manipulating these three parameters allows the sender to express data; receiver reconstructs data from the received signal 22
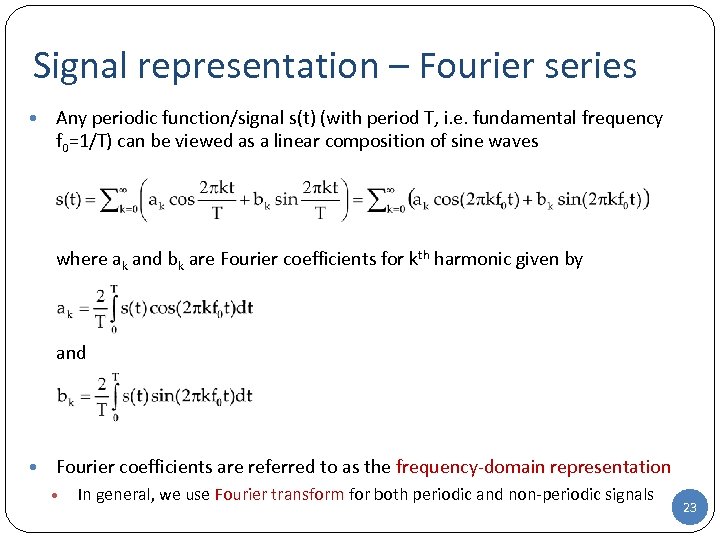 Signal representation – Fourier series • Any periodic function/signal s(t) (with period T, i. e. fundamental frequency f 0=1/T) can be viewed as a linear composition of sine waves where ak and bk are Fourier coefficients for kth harmonic given by and • Fourier coefficients are referred to as the frequency-domain representation • In general, we use Fourier transform for both periodic and non-periodic signals 23
Signal representation – Fourier series • Any periodic function/signal s(t) (with period T, i. e. fundamental frequency f 0=1/T) can be viewed as a linear composition of sine waves where ak and bk are Fourier coefficients for kth harmonic given by and • Fourier coefficients are referred to as the frequency-domain representation • In general, we use Fourier transform for both periodic and non-periodic signals 23
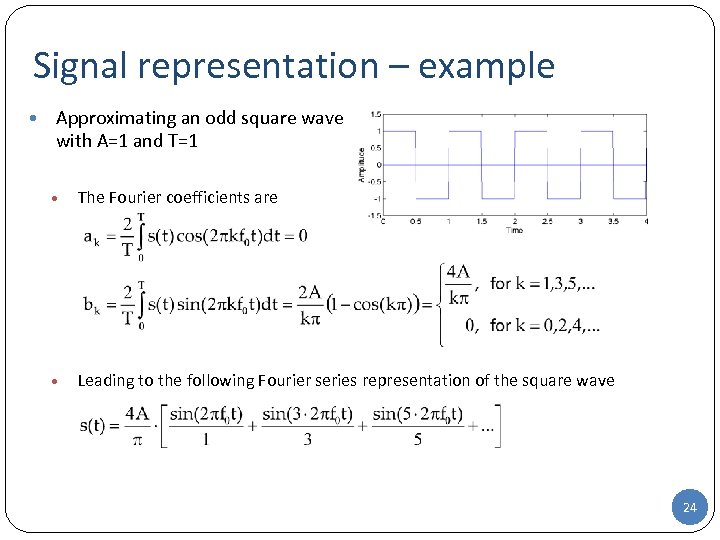 Signal representation – example • Approximating an odd square wave with A=1 and T=1 • The Fourier coefficients are • Leading to the following Fourier series representation of the square wave 24
Signal representation – example • Approximating an odd square wave with A=1 and T=1 • The Fourier coefficients are • Leading to the following Fourier series representation of the square wave 24
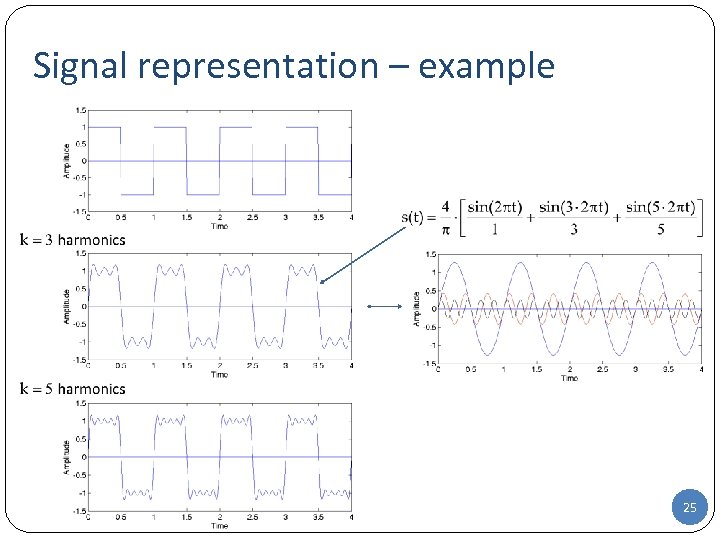 Signal representation – example 25
Signal representation – example 25
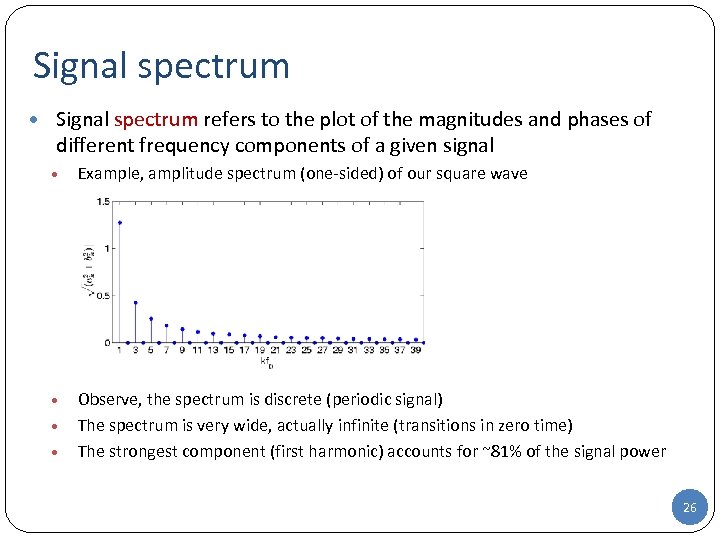 Signal spectrum • Signal spectrum refers to the plot of the magnitudes and phases of different frequency components of a given signal • Example, amplitude spectrum (one-sided) of our square wave • Observe, the spectrum is discrete (periodic signal) The spectrum is very wide, actually infinite (transitions in zero time) The strongest component (first harmonic) accounts for ~81% of the signal power • • 26
Signal spectrum • Signal spectrum refers to the plot of the magnitudes and phases of different frequency components of a given signal • Example, amplitude spectrum (one-sided) of our square wave • Observe, the spectrum is discrete (periodic signal) The spectrum is very wide, actually infinite (transitions in zero time) The strongest component (first harmonic) accounts for ~81% of the signal power • • 26
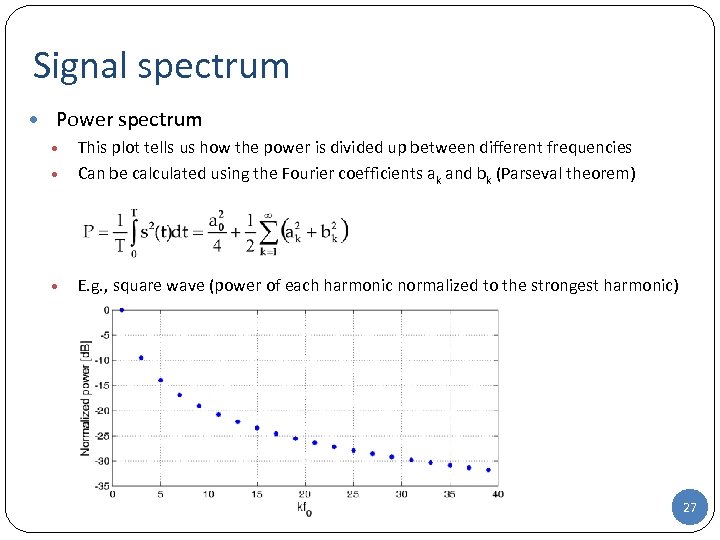 Signal spectrum • Power spectrum • This plot tells us how the power is divided up between different frequencies Can be calculated using the Fourier coefficients ak and bk (Parseval theorem) • E. g. , square wave (power of each harmonic normalized to the strongest harmonic) • 27
Signal spectrum • Power spectrum • This plot tells us how the power is divided up between different frequencies Can be calculated using the Fourier coefficients ak and bk (Parseval theorem) • E. g. , square wave (power of each harmonic normalized to the strongest harmonic) • 27
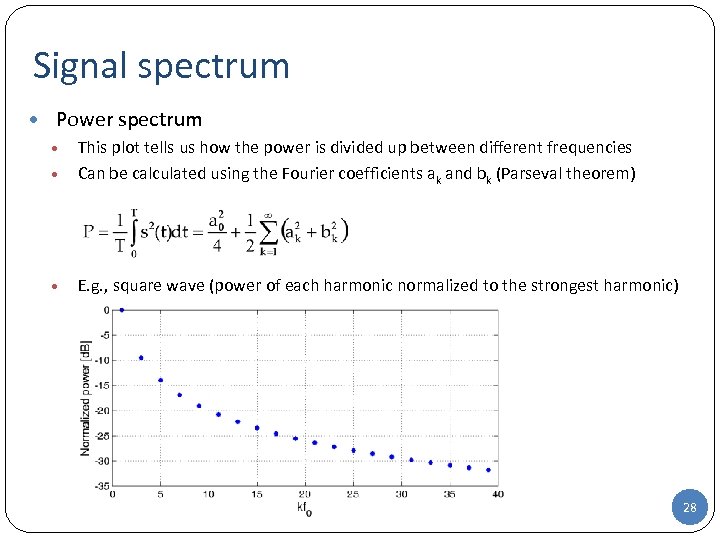 Signal spectrum • Power spectrum • This plot tells us how the power is divided up between different frequencies Can be calculated using the Fourier coefficients ak and bk (Parseval theorem) • E. g. , square wave (power of each harmonic normalized to the strongest harmonic) • 28
Signal spectrum • Power spectrum • This plot tells us how the power is divided up between different frequencies Can be calculated using the Fourier coefficients ak and bk (Parseval theorem) • E. g. , square wave (power of each harmonic normalized to the strongest harmonic) • 28
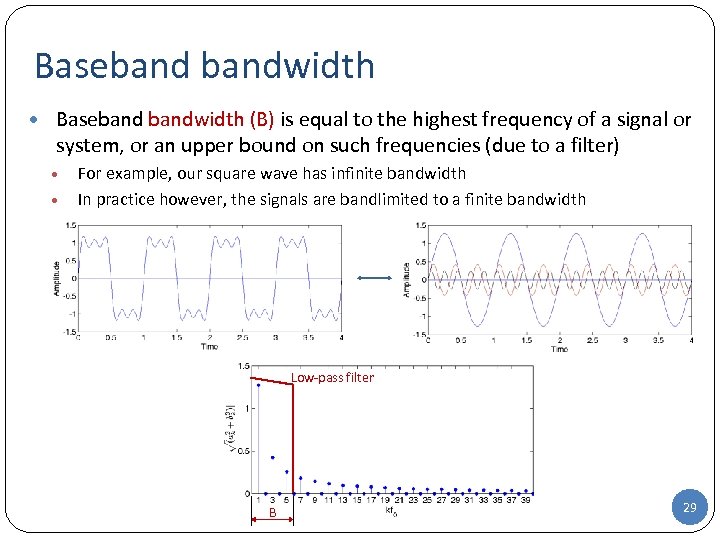 Basebandwidth • Basebandwidth (B) is equal to the highest frequency of a signal or system, or an upper bound on such frequencies (due to a filter) • • For example, our square wave has infinite bandwidth In practice however, the signals are bandlimited to a finite bandwidth Low-pass filter B 29
Basebandwidth • Basebandwidth (B) is equal to the highest frequency of a signal or system, or an upper bound on such frequencies (due to a filter) • • For example, our square wave has infinite bandwidth In practice however, the signals are bandlimited to a finite bandwidth Low-pass filter B 29
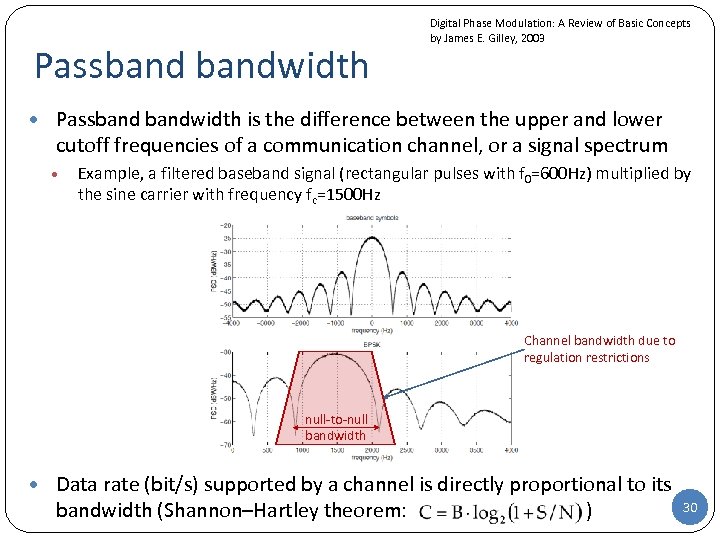 Passbandwidth Digital Phase Modulation: A Review of Basic Concepts by James E. Gilley, 2003 • Passbandwidth is the difference between the upper and lower cutoff frequencies of a communication channel, or a signal spectrum • Example, a filtered baseband signal (rectangular pulses with f 0=600 Hz) multiplied by the sine carrier with frequency fc=1500 Hz Channel bandwidth due to regulation restrictions null-to-null bandwidth • Data rate (bit/s) supported by a channel is directly proportional to its bandwidth (Shannon–Hartley theorem: ) 30
Passbandwidth Digital Phase Modulation: A Review of Basic Concepts by James E. Gilley, 2003 • Passbandwidth is the difference between the upper and lower cutoff frequencies of a communication channel, or a signal spectrum • Example, a filtered baseband signal (rectangular pulses with f 0=600 Hz) multiplied by the sine carrier with frequency fc=1500 Hz Channel bandwidth due to regulation restrictions null-to-null bandwidth • Data rate (bit/s) supported by a channel is directly proportional to its bandwidth (Shannon–Hartley theorem: ) 30
 Signal modulation • How to manipulate a given signal parameter? Set the parameter to an arbitrary value: analog modulation Choose parameter values from a finite set of legal values: digital keying • Modulation? Data to be transmitted is used to select transmission parameters as a function of time These parameters modify a basic sine wave, which serves as a starting point for modulating the signal onto it This basic sine wave has a center frequency fc The resulting signal requires a certain bandwidth to be transmitted (centered around the center frequency) 31
Signal modulation • How to manipulate a given signal parameter? Set the parameter to an arbitrary value: analog modulation Choose parameter values from a finite set of legal values: digital keying • Modulation? Data to be transmitted is used to select transmission parameters as a function of time These parameters modify a basic sine wave, which serves as a starting point for modulating the signal onto it This basic sine wave has a center frequency fc The resulting signal requires a certain bandwidth to be transmitted (centered around the center frequency) 31
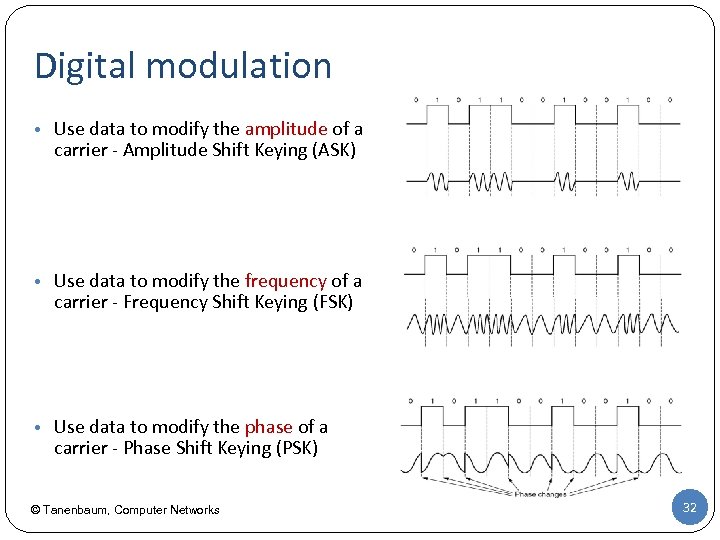 Digital modulation • Use data to modify the amplitude of a carrier - Amplitude Shift Keying (ASK) • Use data to modify the frequency of a carrier - Frequency Shift Keying (FSK) • Use data to modify the phase of a carrier - Phase Shift Keying (PSK) © Tanenbaum, Computer Networks 32
Digital modulation • Use data to modify the amplitude of a carrier - Amplitude Shift Keying (ASK) • Use data to modify the frequency of a carrier - Frequency Shift Keying (FSK) • Use data to modify the phase of a carrier - Phase Shift Keying (PSK) © Tanenbaum, Computer Networks 32
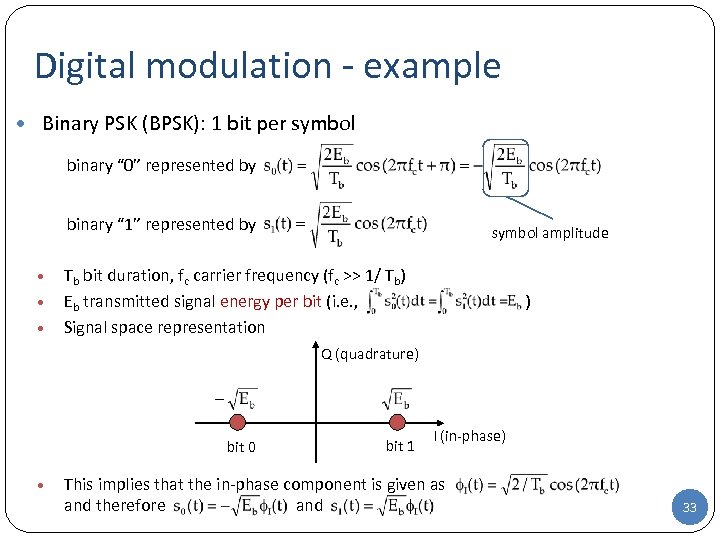 Digital modulation - example • Binary PSK (BPSK): 1 bit per symbol binary “ 0” represented by binary “ 1” represented by • • • symbol amplitude Tb bit duration, fc carrier frequency (fc >> 1/ Tb) Eb transmitted signal energy per bit (i. e. , ) Signal space representation Q (quadrature) bit 0 • bit 1 I (in-phase) This implies that the in-phase component is given as and therefore and 33
Digital modulation - example • Binary PSK (BPSK): 1 bit per symbol binary “ 0” represented by binary “ 1” represented by • • • symbol amplitude Tb bit duration, fc carrier frequency (fc >> 1/ Tb) Eb transmitted signal energy per bit (i. e. , ) Signal space representation Q (quadrature) bit 0 • bit 1 I (in-phase) This implies that the in-phase component is given as and therefore and 33
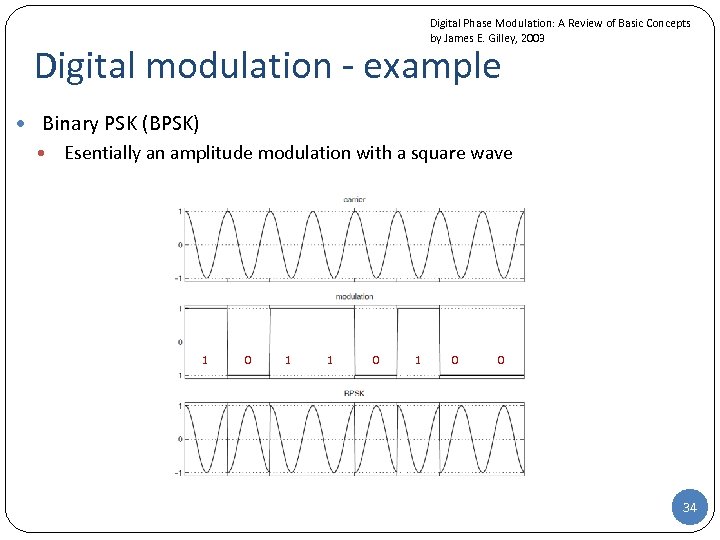 Digital Phase Modulation: A Review of Basic Concepts by James E. Gilley, 2003 Digital modulation - example • Binary PSK (BPSK) • Esentially an amplitude modulation with a square wave 1 0 1 0 0 34
Digital Phase Modulation: A Review of Basic Concepts by James E. Gilley, 2003 Digital modulation - example • Binary PSK (BPSK) • Esentially an amplitude modulation with a square wave 1 0 1 0 0 34
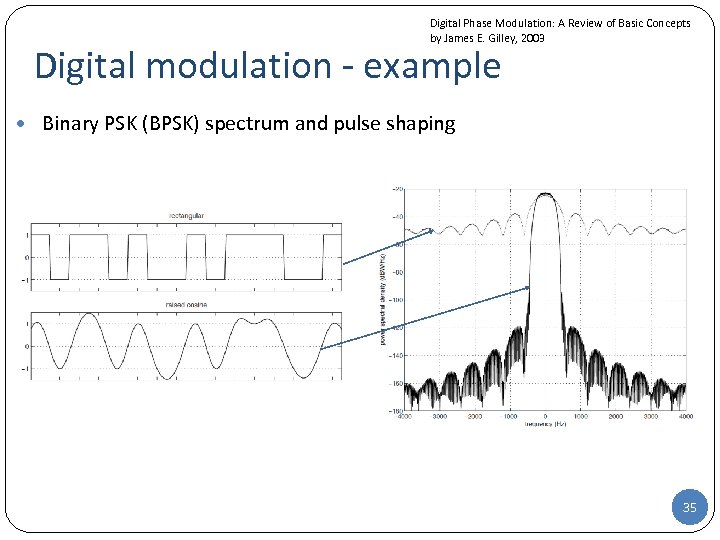 Digital Phase Modulation: A Review of Basic Concepts by James E. Gilley, 2003 Digital modulation - example • Binary PSK (BPSK) spectrum and pulse shaping 35
Digital Phase Modulation: A Review of Basic Concepts by James E. Gilley, 2003 Digital modulation - example • Binary PSK (BPSK) spectrum and pulse shaping 35
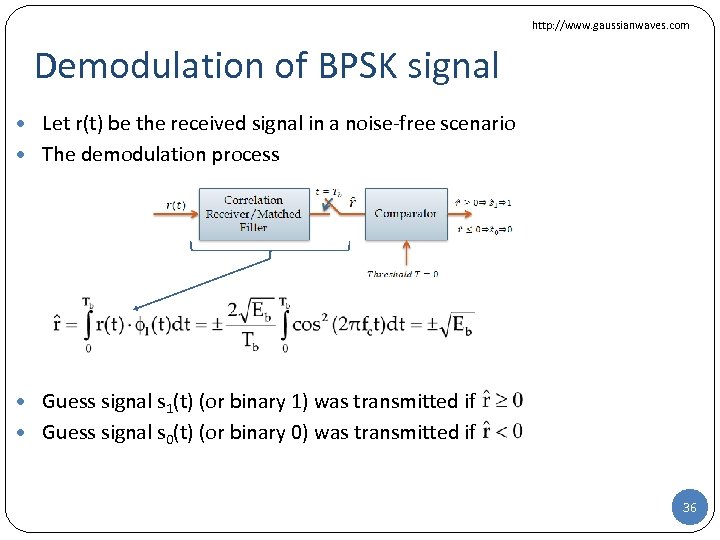 http: //www. gaussianwaves. com Demodulation of BPSK signal • Let r(t) be the received signal in a noise-free scenario • The demodulation process • Guess signal s 1(t) (or binary 1) was transmitted if • Guess signal s 0(t) (or binary 0) was transmitted if 36
http: //www. gaussianwaves. com Demodulation of BPSK signal • Let r(t) be the received signal in a noise-free scenario • The demodulation process • Guess signal s 1(t) (or binary 1) was transmitted if • Guess signal s 0(t) (or binary 0) was transmitted if 36
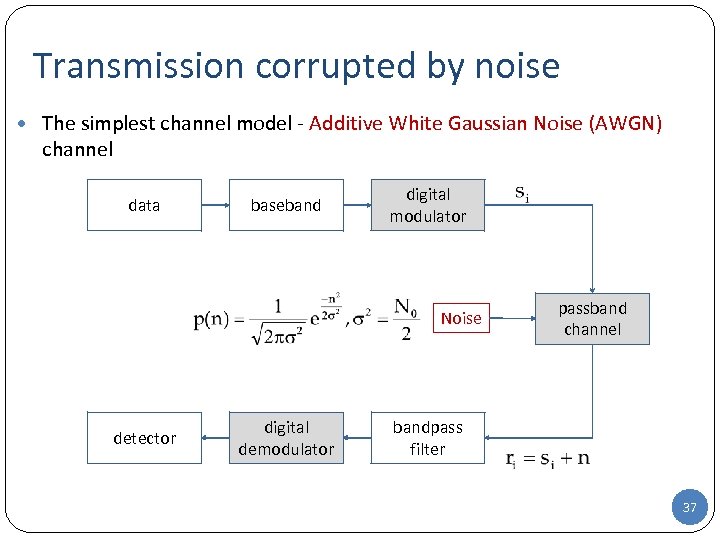 Transmission corrupted by noise The simplest channel model - Additive White Gaussian Noise (AWGN) channel data baseband digital modulator Noise detector digital demodulator passband channel bandpass filter 37
Transmission corrupted by noise The simplest channel model - Additive White Gaussian Noise (AWGN) channel data baseband digital modulator Noise detector digital demodulator passband channel bandpass filter 37
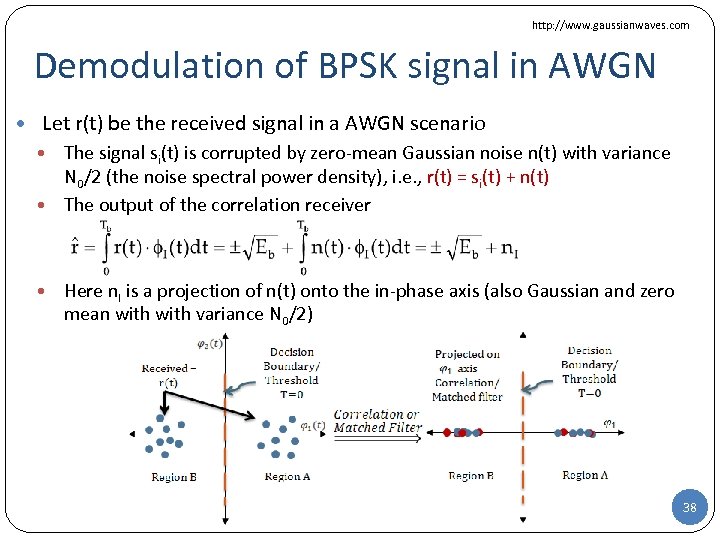 http: //www. gaussianwaves. com Demodulation of BPSK signal in AWGN • Let r(t) be the received signal in a AWGN scenario The signal si(t) is corrupted by zero-mean Gaussian noise n(t) with variance N 0/2 (the noise spectral power density), i. e. , r(t) = si(t) + n(t) • The output of the correlation receiver • • Here n. I is a projection of n(t) onto the in-phase axis (also Gaussian and zero mean with variance N 0/2) 38
http: //www. gaussianwaves. com Demodulation of BPSK signal in AWGN • Let r(t) be the received signal in a AWGN scenario The signal si(t) is corrupted by zero-mean Gaussian noise n(t) with variance N 0/2 (the noise spectral power density), i. e. , r(t) = si(t) + n(t) • The output of the correlation receiver • • Here n. I is a projection of n(t) onto the in-phase axis (also Gaussian and zero mean with variance N 0/2) 38
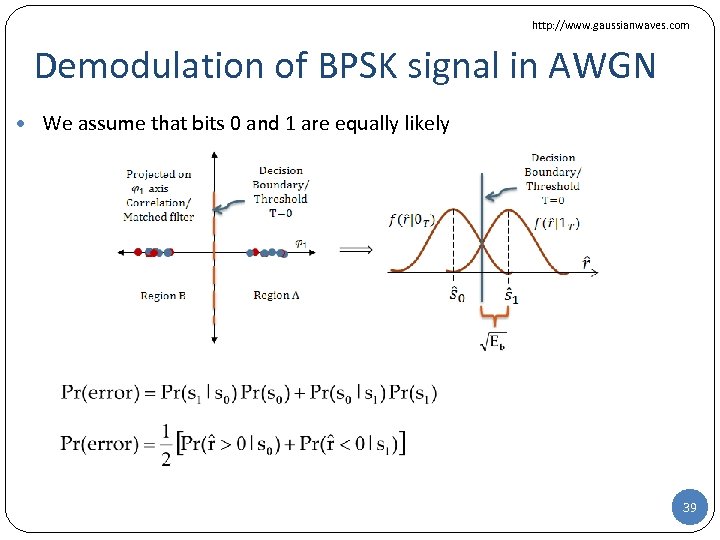 http: //www. gaussianwaves. com Demodulation of BPSK signal in AWGN • We assume that bits 0 and 1 are equally likely 39
http: //www. gaussianwaves. com Demodulation of BPSK signal in AWGN • We assume that bits 0 and 1 are equally likely 39
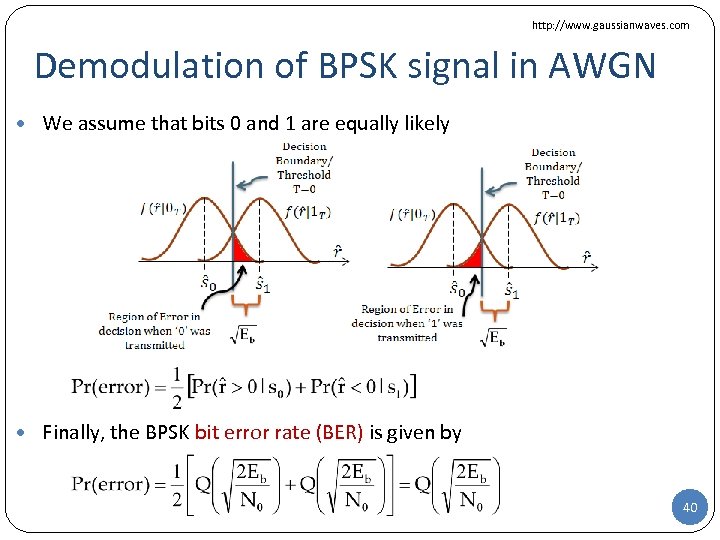 http: //www. gaussianwaves. com Demodulation of BPSK signal in AWGN • We assume that bits 0 and 1 are equally likely • Finally, the BPSK bit error rate (BER) is given by 40
http: //www. gaussianwaves. com Demodulation of BPSK signal in AWGN • We assume that bits 0 and 1 are equally likely • Finally, the BPSK bit error rate (BER) is given by 40
![Bit error rate (BER) BER (bit-error rate) Eb/N 0 [d. B] bit energy to Bit error rate (BER) BER (bit-error rate) Eb/N 0 [d. B] bit energy to](https://present5.com/presentation/f37542a1e93847ae45b0225c2a3f86e1/image-41.jpg) Bit error rate (BER) BER (bit-error rate) Eb/N 0 [d. B] bit energy to noise density ratio 41 [SNR/bit]
Bit error rate (BER) BER (bit-error rate) Eb/N 0 [d. B] bit energy to noise density ratio 41 [SNR/bit]
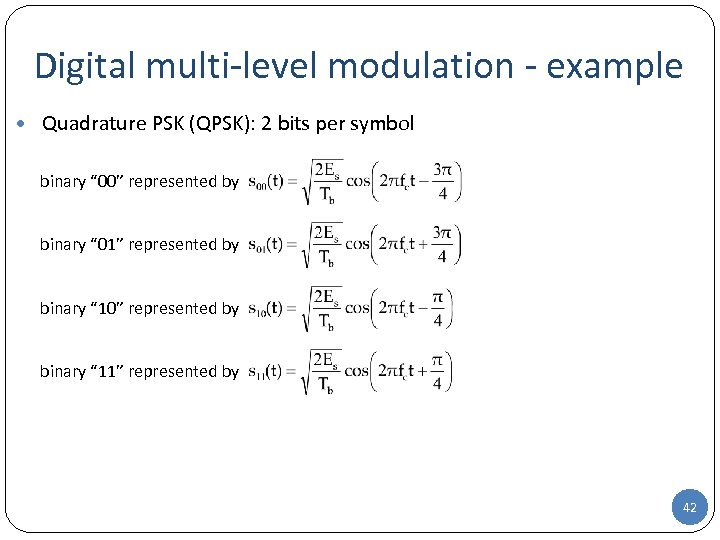 Digital multi-level modulation - example • Quadrature PSK (QPSK): 2 bits per symbol binary “ 00” represented by binary “ 01” represented by binary “ 10” represented by binary “ 11” represented by 42
Digital multi-level modulation - example • Quadrature PSK (QPSK): 2 bits per symbol binary “ 00” represented by binary “ 01” represented by binary “ 10” represented by binary “ 11” represented by 42
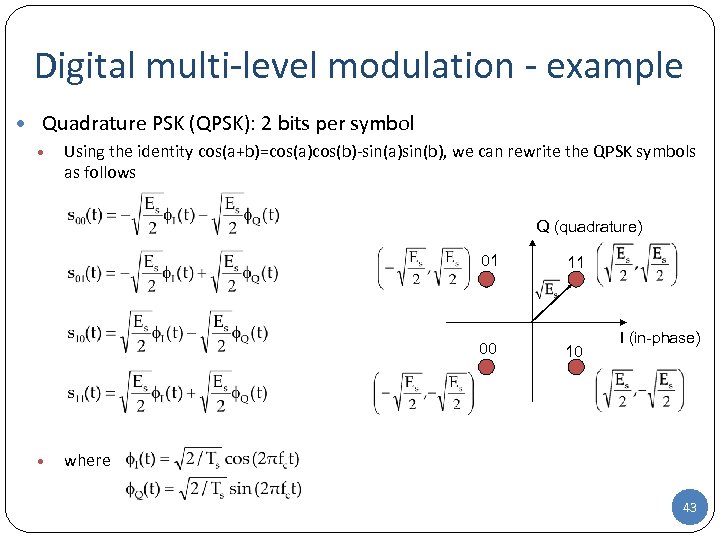 Digital multi-level modulation - example • Quadrature PSK (QPSK): 2 bits per symbol • Using the identity cos(a+b)=cos(a)cos(b)-sin(a)sin(b), we can rewrite the QPSK symbols as follows Q (quadrature) 01 00 • 11 10 I (in-phase) where 43
Digital multi-level modulation - example • Quadrature PSK (QPSK): 2 bits per symbol • Using the identity cos(a+b)=cos(a)cos(b)-sin(a)sin(b), we can rewrite the QPSK symbols as follows Q (quadrature) 01 00 • 11 10 I (in-phase) where 43
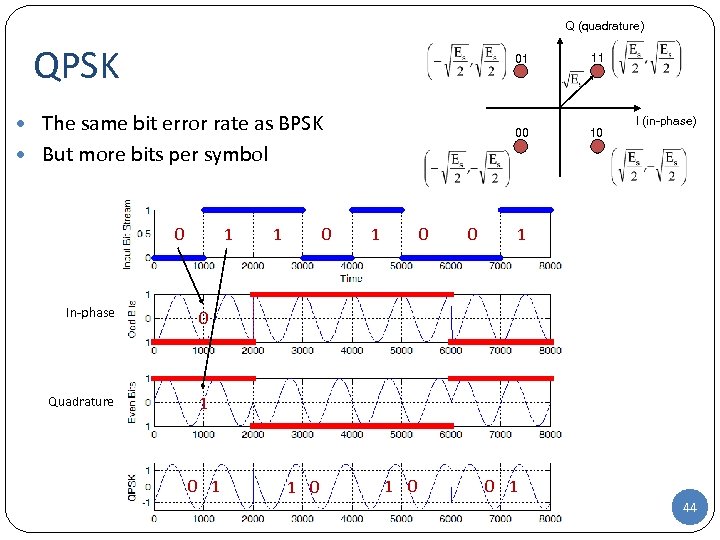 Q (quadrature) QPSK 01 00 • The same bit error rate as BPSK 11 10 I (in-phase) • But more bits per symbol 0 1 In-phase 0 1 0 Quadrature 1 1 0 1 0 0 1 44
Q (quadrature) QPSK 01 00 • The same bit error rate as BPSK 11 10 I (in-phase) • But more bits per symbol 0 1 In-phase 0 1 0 Quadrature 1 1 0 1 0 0 1 44
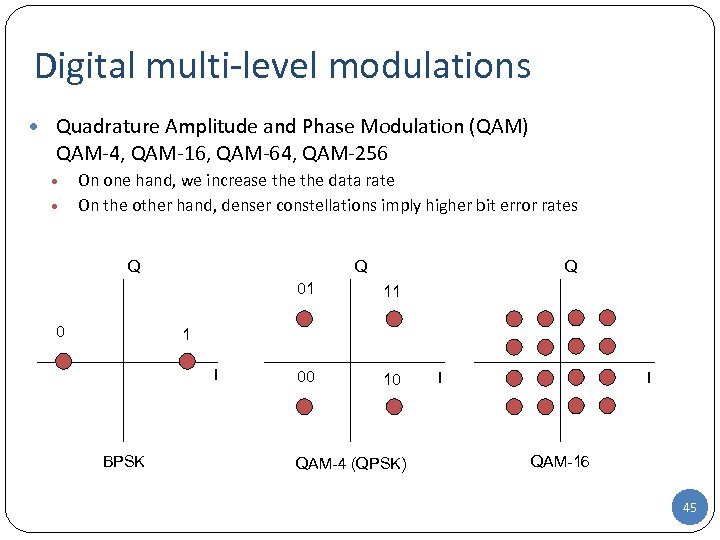 Digital multi-level modulations • Quadrature Amplitude and Phase Modulation (QAM) QAM-4, QAM-16, QAM-64, QAM-256 • • On one hand, we increase the data rate On the other hand, denser constellations imply higher bit error rates Q Q Q 01 0 11 00 10 1 I BPSK QAM-4 (QPSK) I I QAM-16 45
Digital multi-level modulations • Quadrature Amplitude and Phase Modulation (QAM) QAM-4, QAM-16, QAM-64, QAM-256 • • On one hand, we increase the data rate On the other hand, denser constellations imply higher bit error rates Q Q Q 01 0 11 00 10 1 I BPSK QAM-4 (QPSK) I I QAM-16 45
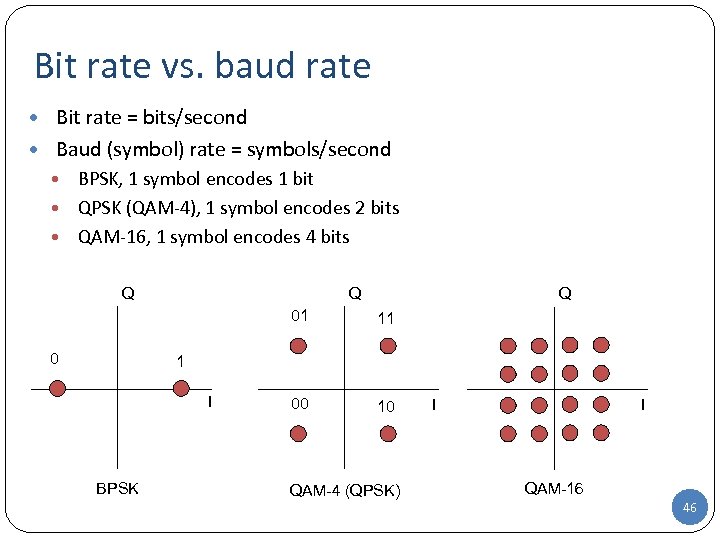 Bit rate vs. baud rate • Bit rate = bits/second • Baud (symbol) rate = symbols/second BPSK, 1 symbol encodes 1 bit • QPSK (QAM-4), 1 symbol encodes 2 bits • QAM-16, 1 symbol encodes 4 bits • Q Q Q 01 0 11 00 10 1 I BPSK QAM-4 (QPSK) I I QAM-16 46
Bit rate vs. baud rate • Bit rate = bits/second • Baud (symbol) rate = symbols/second BPSK, 1 symbol encodes 1 bit • QPSK (QAM-4), 1 symbol encodes 2 bits • QAM-16, 1 symbol encodes 4 bits • Q Q Q 01 0 11 00 10 1 I BPSK QAM-4 (QPSK) I I QAM-16 46
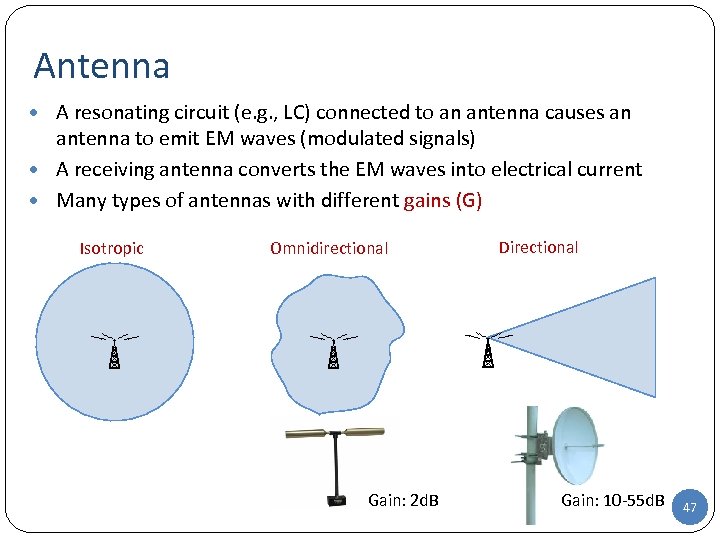 Antenna • A resonating circuit (e. g. , LC) connected to an antenna causes an antenna to emit EM waves (modulated signals) • A receiving antenna converts the EM waves into electrical current • Many types of antennas with different gains (G) Isotropic Omnidirectional Gain: 2 d. B Directional Gain: 10 -55 d. B 47 47
Antenna • A resonating circuit (e. g. , LC) connected to an antenna causes an antenna to emit EM waves (modulated signals) • A receiving antenna converts the EM waves into electrical current • Many types of antennas with different gains (G) Isotropic Omnidirectional Gain: 2 d. B Directional Gain: 10 -55 d. B 47 47
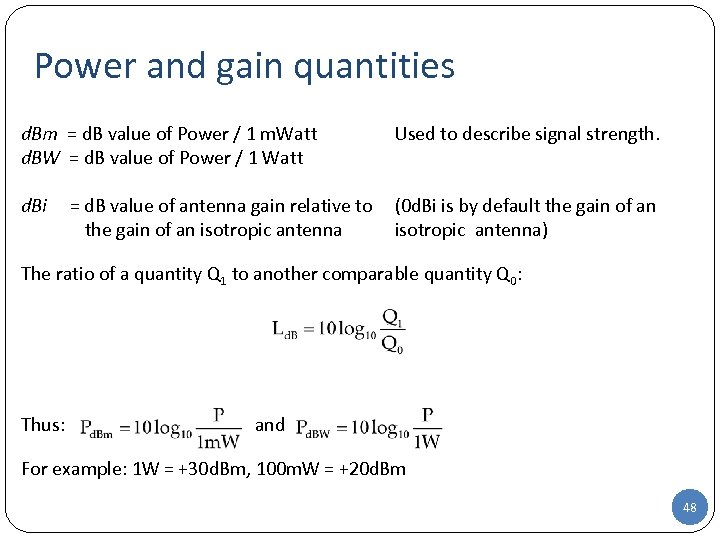 Power and gain quantities d. Bm = d. B value of Power / 1 m. Watt d. BW = d. B value of Power / 1 Watt Used to describe signal strength. d. Bi = d. B value of antenna gain relative to (0 d. Bi is by default the gain of an the gain of an isotropic antenna) The ratio of a quantity Q 1 to another comparable quantity Q 0: Thus: and For example: 1 W = +30 d. Bm, 100 m. W = +20 d. Bm 48
Power and gain quantities d. Bm = d. B value of Power / 1 m. Watt d. BW = d. B value of Power / 1 Watt Used to describe signal strength. d. Bi = d. B value of antenna gain relative to (0 d. Bi is by default the gain of an the gain of an isotropic antenna) The ratio of a quantity Q 1 to another comparable quantity Q 0: Thus: and For example: 1 W = +30 d. Bm, 100 m. W = +20 d. Bm 48
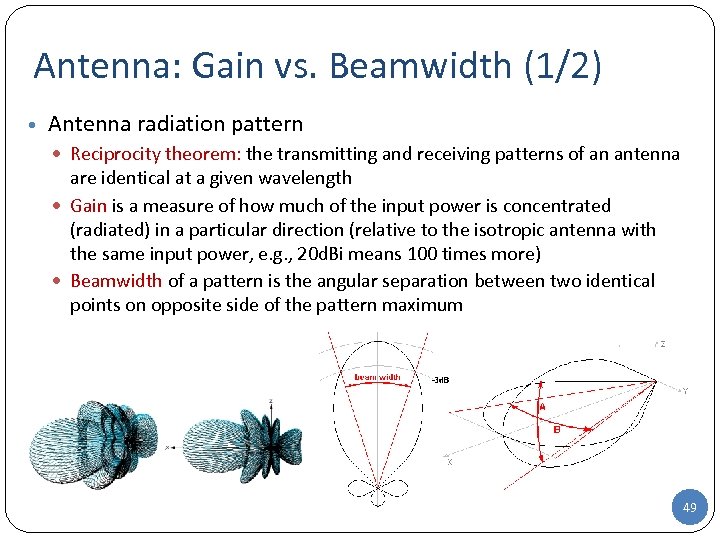 Antenna: Gain vs. Beamwidth (1/2) • Antenna radiation pattern Reciprocity theorem: the transmitting and receiving patterns of an antenna are identical at a given wavelength Gain is a measure of how much of the input power is concentrated (radiated) in a particular direction (relative to the isotropic antenna with the same input power, e. g. , 20 d. Bi means 100 times more) Beamwidth of a pattern is the angular separation between two identical points on opposite side of the pattern maximum 49
Antenna: Gain vs. Beamwidth (1/2) • Antenna radiation pattern Reciprocity theorem: the transmitting and receiving patterns of an antenna are identical at a given wavelength Gain is a measure of how much of the input power is concentrated (radiated) in a particular direction (relative to the isotropic antenna with the same input power, e. g. , 20 d. Bi means 100 times more) Beamwidth of a pattern is the angular separation between two identical points on opposite side of the pattern maximum 49
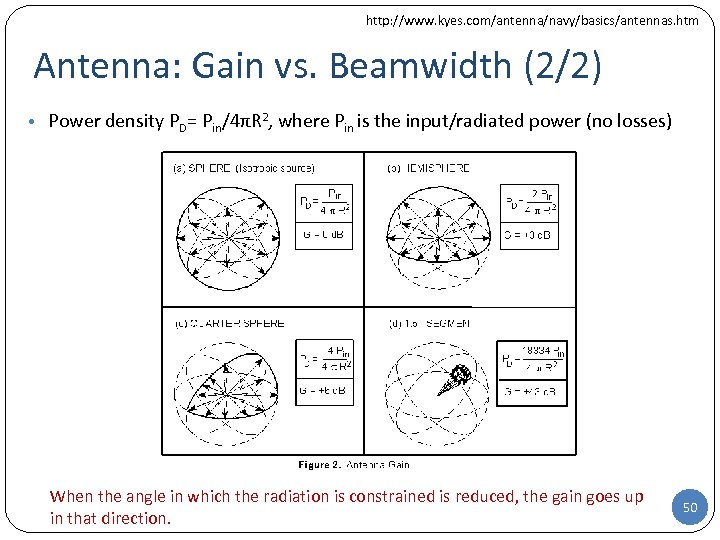 http: //www. kyes. com/antenna/navy/basics/antennas. htm Antenna: Gain vs. Beamwidth (2/2) • Power density PD= Pin/4πR 2, where Pin is the input/radiated power (no losses) When the angle in which the radiation is constrained is reduced, the gain goes up in that direction. 50
http: //www. kyes. com/antenna/navy/basics/antennas. htm Antenna: Gain vs. Beamwidth (2/2) • Power density PD= Pin/4πR 2, where Pin is the input/radiated power (no losses) When the angle in which the radiation is constrained is reduced, the gain goes up in that direction. 50
 Signal propagation Wireless transmission distorts a transmitted signal Results in uncertainty at receiver about which bit sequence originally caused the transmitted signal Abstraction: Wireless channel describes these distortion effects Sources of distortion Attenuation – energy is distributed to larger areas with increasing distance Reflection/refraction – bounce of a surface; enter material Diffraction – start “new wave” from a sharp edge Scattering – multiple reflections at rough surfaces Doppler fading – shift in frequencies (loss of center) 51
Signal propagation Wireless transmission distorts a transmitted signal Results in uncertainty at receiver about which bit sequence originally caused the transmitted signal Abstraction: Wireless channel describes these distortion effects Sources of distortion Attenuation – energy is distributed to larger areas with increasing distance Reflection/refraction – bounce of a surface; enter material Diffraction – start “new wave” from a sharp edge Scattering – multiple reflections at rough surfaces Doppler fading – shift in frequencies (loss of center) 51
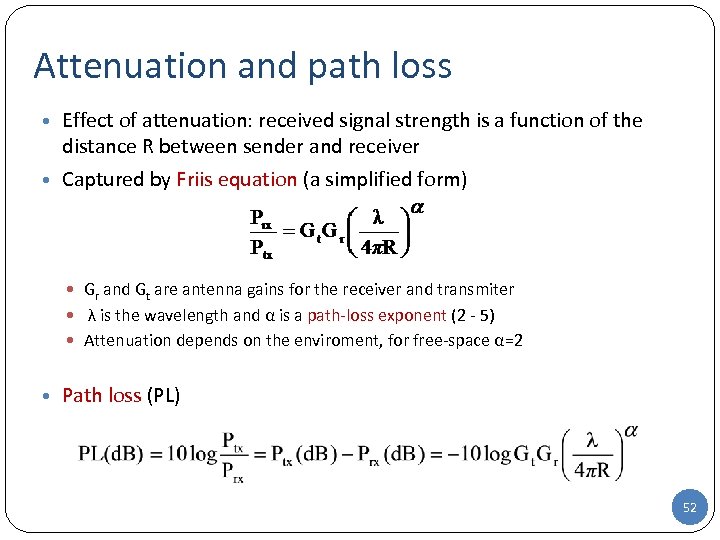 Attenuation and path loss • Effect of attenuation: received signal strength is a function of the distance R between sender and receiver • Captured by Friis equation (a simplified form) Gr and Gt are antenna gains for the receiver and transmiter λ is the wavelength and α is a path-loss exponent (2 - 5) Attenuation depends on the enviroment, for free-space α=2 • Path loss (PL) 52
Attenuation and path loss • Effect of attenuation: received signal strength is a function of the distance R between sender and receiver • Captured by Friis equation (a simplified form) Gr and Gt are antenna gains for the receiver and transmiter λ is the wavelength and α is a path-loss exponent (2 - 5) Attenuation depends on the enviroment, for free-space α=2 • Path loss (PL) 52
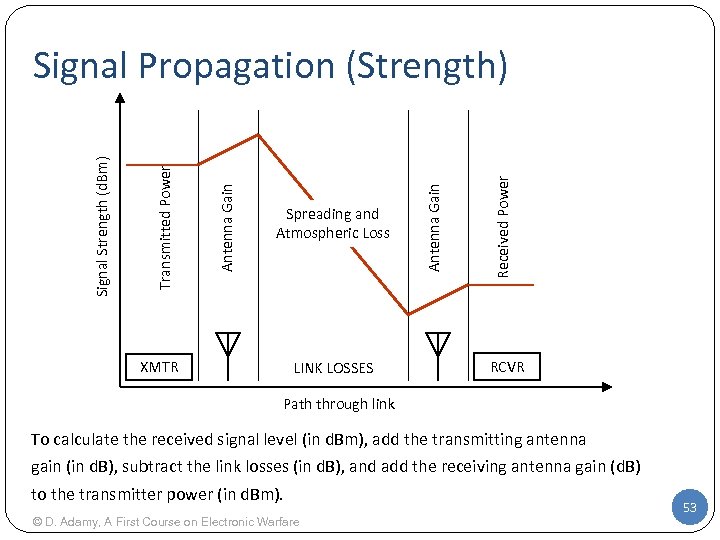 XMTR LINK LOSSES Received Power Spreading and Atmospheric Loss Antenna Gain Transmitted Power Signal Strength (d. Bm) Signal Propagation (Strength) RCVR Path through link To calculate the received signal level (in d. Bm), add the transmitting antenna gain (in d. B), subtract the link losses (in d. B), and add the receiving antenna gain (d. B) to the transmitter power (in d. Bm). © D. Adamy, A First Course on Electronic Warfare 53
XMTR LINK LOSSES Received Power Spreading and Atmospheric Loss Antenna Gain Transmitted Power Signal Strength (d. Bm) Signal Propagation (Strength) RCVR Path through link To calculate the received signal level (in d. Bm), add the transmitting antenna gain (in d. B), subtract the link losses (in d. B), and add the receiving antenna gain (d. B) to the transmitter power (in d. Bm). © D. Adamy, A First Course on Electronic Warfare 53
 Receiver sensitivity • The smallest signal (the lowest signal strength) that a receiver can receive and still provide the proper specified output. • Example: • • • Transmitter Power (1 W) = +30 d. Bm Transmitting Antenna Gain = +10 d. B Spreading Loss = 100 d. B Atmospheric Loss = 2 d. B Receiving Antenna Gain = +3 d. B Receiver Power (d. Bm) = +30 d. Bm + 10 d. B – 100 d. B – 2 d. B + 3 d. B = -59 d. Bm Receiver 1 sensitivity is -62 d. Bm and the receiver 2 is -65 d. Bm: receiver 1 and 2 will receive the signal as if there is still 3 d. Bm and 6 d. Bm of margin on the link, respectively. Recv 2 is 3 d. B (a factor of two) better than recv 1; recv 2 can hear signals that are half the strength of those heard by recv 1. 54
Receiver sensitivity • The smallest signal (the lowest signal strength) that a receiver can receive and still provide the proper specified output. • Example: • • • Transmitter Power (1 W) = +30 d. Bm Transmitting Antenna Gain = +10 d. B Spreading Loss = 100 d. B Atmospheric Loss = 2 d. B Receiving Antenna Gain = +3 d. B Receiver Power (d. Bm) = +30 d. Bm + 10 d. B – 100 d. B – 2 d. B + 3 d. B = -59 d. Bm Receiver 1 sensitivity is -62 d. Bm and the receiver 2 is -65 d. Bm: receiver 1 and 2 will receive the signal as if there is still 3 d. Bm and 6 d. Bm of margin on the link, respectively. Recv 2 is 3 d. B (a factor of two) better than recv 1; recv 2 can hear signals that are half the strength of those heard by recv 1. 54
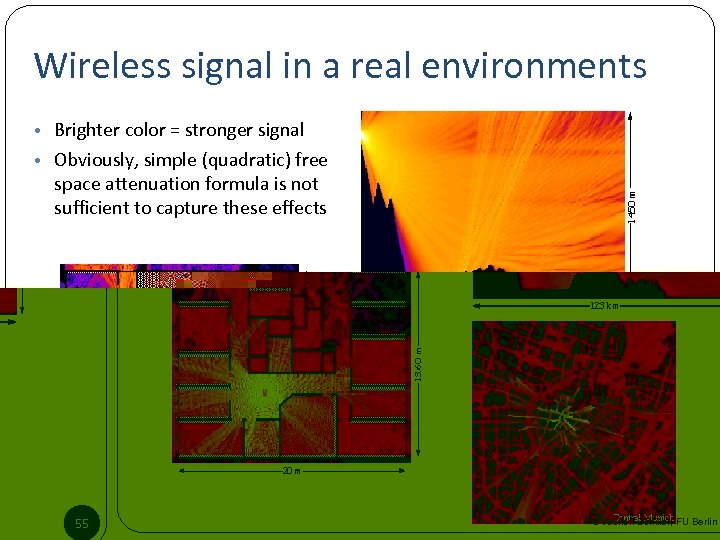 Wireless signal in a real environments • Brighter color = stronger signal • Obviously, simple (quadratic) free space attenuation formula is not sufficient to capture these effects 55 © Jochen Schiller, FU Berlin
Wireless signal in a real environments • Brighter color = stronger signal • Obviously, simple (quadratic) free space attenuation formula is not sufficient to capture these effects 55 © Jochen Schiller, FU Berlin
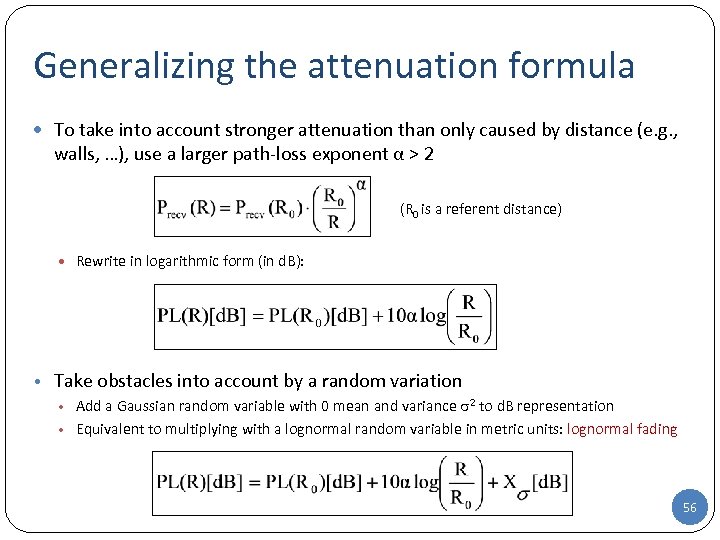 Generalizing the attenuation formula To take into account stronger attenuation than only caused by distance (e. g. , walls, …), use a larger path-loss exponent α > 2 (R 0 is a referent distance) Rewrite in logarithmic form (in d. B): • Take obstacles into account by a random variation • Add a Gaussian random variable with 0 mean and variance 2 to d. B representation • Equivalent to multiplying with a lognormal random variable in metric units: lognormal fading 56
Generalizing the attenuation formula To take into account stronger attenuation than only caused by distance (e. g. , walls, …), use a larger path-loss exponent α > 2 (R 0 is a referent distance) Rewrite in logarithmic form (in d. B): • Take obstacles into account by a random variation • Add a Gaussian random variable with 0 mean and variance 2 to d. B representation • Equivalent to multiplying with a lognormal random variable in metric units: lognormal fading 56
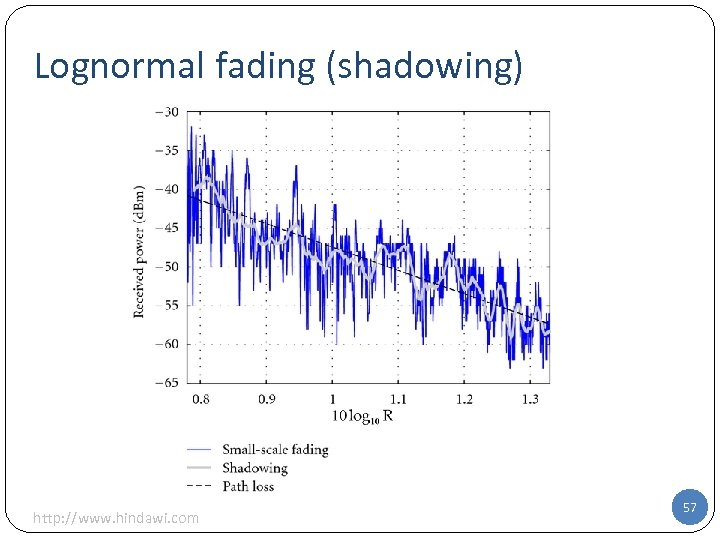 Lognormal fading (shadowing) http: //www. hindawi. com 57
Lognormal fading (shadowing) http: //www. hindawi. com 57
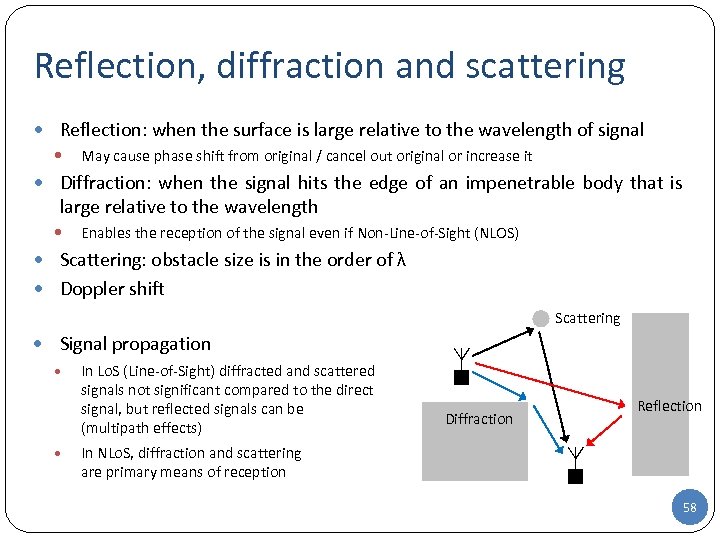 Reflection, diffraction and scattering Reflection: when the surface is large relative to the wavelength of signal May cause phase shift from original / cancel out original or increase it Diffraction: when the signal hits the edge of an impenetrable body that is large relative to the wavelength Enables the reception of the signal even if Non-Line-of-Sight (NLOS) Scattering: obstacle size is in the order of λ Doppler shift Scattering Signal propagation In Lo. S (Line-of-Sight) diffracted and scattered signals not significant compared to the direct signal, but reflected signals can be (multipath effects) Diffraction Reflection In NLo. S, diffraction and scattering are primary means of reception 58
Reflection, diffraction and scattering Reflection: when the surface is large relative to the wavelength of signal May cause phase shift from original / cancel out original or increase it Diffraction: when the signal hits the edge of an impenetrable body that is large relative to the wavelength Enables the reception of the signal even if Non-Line-of-Sight (NLOS) Scattering: obstacle size is in the order of λ Doppler shift Scattering Signal propagation In Lo. S (Line-of-Sight) diffracted and scattered signals not significant compared to the direct signal, but reflected signals can be (multipath effects) Diffraction Reflection In NLo. S, diffraction and scattering are primary means of reception 58
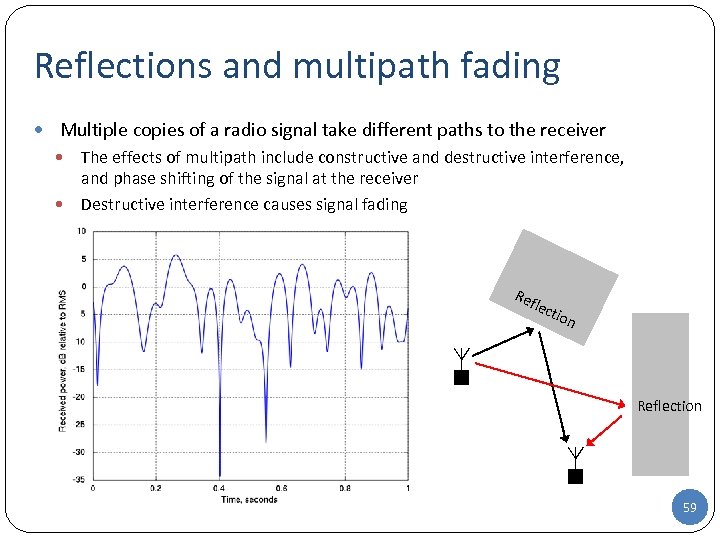 Reflections and multipath fading Multiple copies of a radio signal take different paths to the receiver The effects of multipath include constructive and destructive interference, and phase shifting of the signal at the receiver Destructive interference causes signal fading Ref lec tion Reflection 59
Reflections and multipath fading Multiple copies of a radio signal take different paths to the receiver The effects of multipath include constructive and destructive interference, and phase shifting of the signal at the receiver Destructive interference causes signal fading Ref lec tion Reflection 59
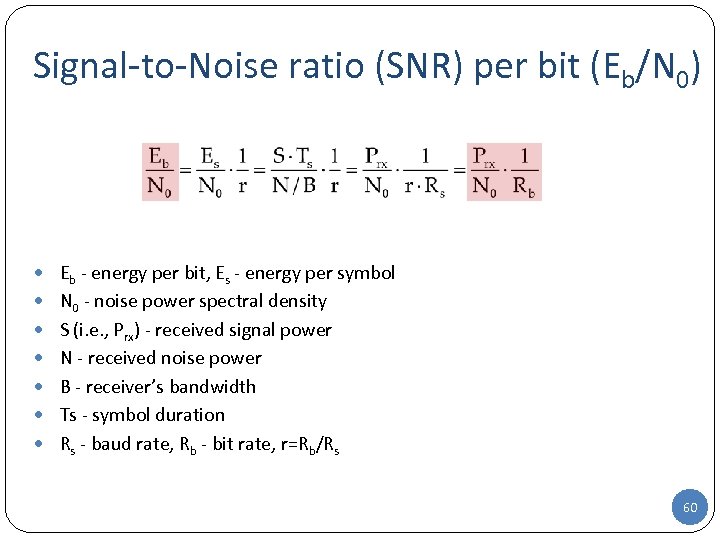 Signal-to-Noise ratio (SNR) per bit (Eb/N 0) Eb - energy per bit, Es - energy per symbol N 0 - noise power spectral density S (i. e. , Prx) - received signal power N - received noise power B - receiver’s bandwidth Ts - symbol duration Rs - baud rate, Rb - bit rate, r=Rb/Rs 60
Signal-to-Noise ratio (SNR) per bit (Eb/N 0) Eb - energy per bit, Es - energy per symbol N 0 - noise power spectral density S (i. e. , Prx) - received signal power N - received noise power B - receiver’s bandwidth Ts - symbol duration Rs - baud rate, Rb - bit rate, r=Rb/Rs 60
 Message eavesdropping and insertion – message relay attacks
Message eavesdropping and insertion – message relay attacks
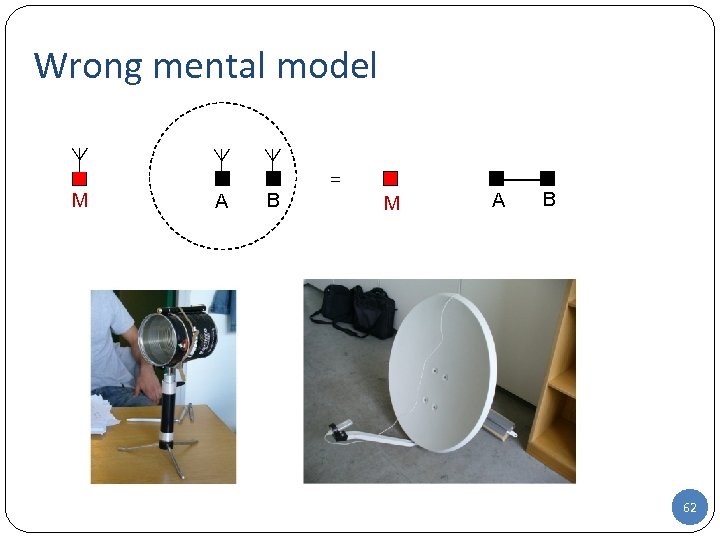 Wrong mental model M A B = M A B 62 62
Wrong mental model M A B = M A B 62 62
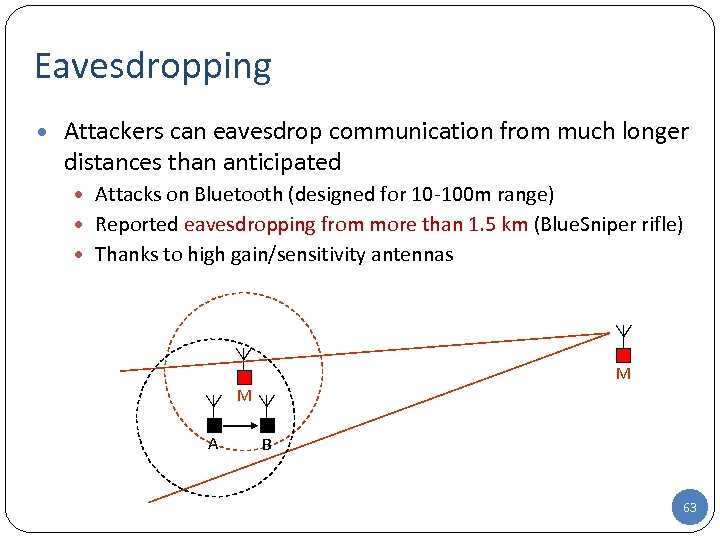 Eavesdropping • Attackers can eavesdrop communication from much longer distances than anticipated Attacks on Bluetooth (designed for 10 -100 m range) Reported eavesdropping from more than 1. 5 km (Blue. Sniper rifle) Thanks to high gain/sensitivity antennas M M A B 63 63
Eavesdropping • Attackers can eavesdrop communication from much longer distances than anticipated Attacks on Bluetooth (designed for 10 -100 m range) Reported eavesdropping from more than 1. 5 km (Blue. Sniper rifle) Thanks to high gain/sensitivity antennas M M A B 63 63
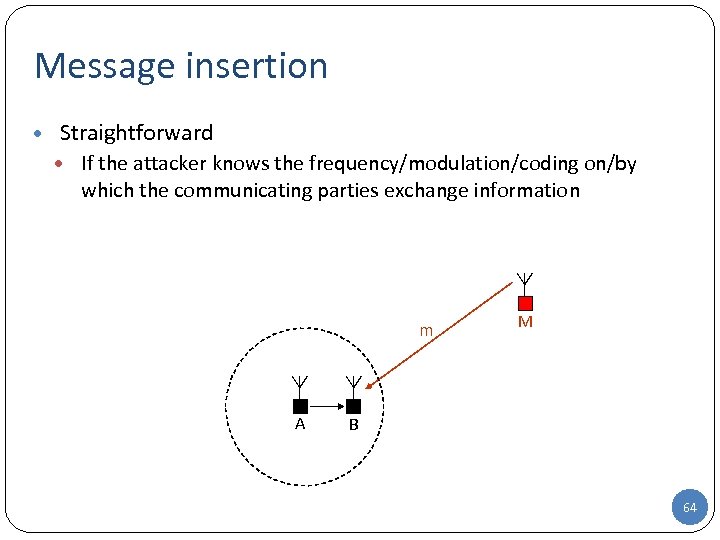 Message insertion • Straightforward • If the attacker knows the frequency/modulation/coding on/by which the communicating parties exchange information m A M B 64
Message insertion • Straightforward • If the attacker knows the frequency/modulation/coding on/by which the communicating parties exchange information m A M B 64
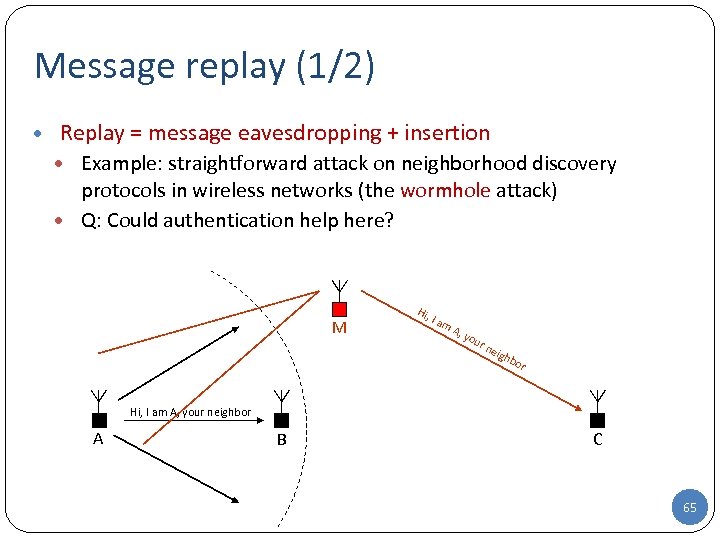 Message replay (1/2) • Replay = message eavesdropping + insertion • Example: straightforward attack on neighborhood discovery protocols in wireless networks (the wormhole attack) • Q: Could authentication help here? M Hi, I a m A , yo ur nei g hbo r Hi, I am A, your neighbor A B C 65
Message replay (1/2) • Replay = message eavesdropping + insertion • Example: straightforward attack on neighborhood discovery protocols in wireless networks (the wormhole attack) • Q: Could authentication help here? M Hi, I a m A , yo ur nei g hbo r Hi, I am A, your neighbor A B C 65
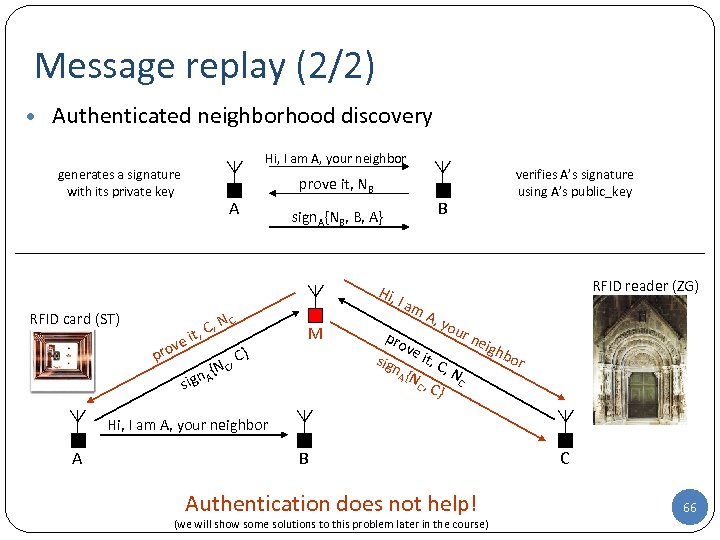 Message replay (2/2) • Authenticated neighborhood discovery Hi, I am A, your neighbor generates a signature with its private key prove it, NB A B sign. A{NB, B, A} Hi, RFID card (ST) N C , C, it p ove r , C} RFID reader (ZG) I am M NC n A{ g si verifies A’s signature using A’s public_key A, you r ne pro igh ve bor it, sig C, N n. A { N, C C C } Hi, I am A, your neighbor A B Authentication does not help! (we will show some solutions to this problem later in the course) C 66
Message replay (2/2) • Authenticated neighborhood discovery Hi, I am A, your neighbor generates a signature with its private key prove it, NB A B sign. A{NB, B, A} Hi, RFID card (ST) N C , C, it p ove r , C} RFID reader (ZG) I am M NC n A{ g si verifies A’s signature using A’s public_key A, you r ne pro igh ve bor it, sig C, N n. A { N, C C C } Hi, I am A, your neighbor A B Authentication does not help! (we will show some solutions to this problem later in the course) C 66
 Relay attacks in practice Chip & PIN (EMV) relay attacks http: //www. cl. cam. ac. uk/research/security/banking/relay Cracking keyless car systems http: //www. youtube. com/watch? v=bfj. Mj 8 fgs. Bo Practical NFC Peer-to-Peer Relay Attack using Mobile Phones http: //eprint. iacr. org/2010/228. pdf 67
Relay attacks in practice Chip & PIN (EMV) relay attacks http: //www. cl. cam. ac. uk/research/security/banking/relay Cracking keyless car systems http: //www. youtube. com/watch? v=bfj. Mj 8 fgs. Bo Practical NFC Peer-to-Peer Relay Attack using Mobile Phones http: //eprint. iacr. org/2010/228. pdf 67


