92b8cacef25fe454913860d67568ebec.ppt
- Количество слайдов: 47
 Federated Identity Management in Healthcare: What is Needed and What is Feasible 2006 Spring Member Meeting April 26, 2006 Holt Anderson – NCHICA Executive Director William Weems, Univ. of Texas Health Science Center at Houston Casey Webster, IBM 1
Federated Identity Management in Healthcare: What is Needed and What is Feasible 2006 Spring Member Meeting April 26, 2006 Holt Anderson – NCHICA Executive Director William Weems, Univ. of Texas Health Science Center at Houston Casey Webster, IBM 1
 Session Outline • Holt Anderson • Background of National HIT Initiatives from ONC • Casey Webster • Challenges & Approaches in Developing the Nationwide Health Information Network (NHIN) Architecture • Bill Weems • What is Possible Today! • Question & Answer Session 2
Session Outline • Holt Anderson • Background of National HIT Initiatives from ONC • Casey Webster • Challenges & Approaches in Developing the Nationwide Health Information Network (NHIN) Architecture • Bill Weems • What is Possible Today! • Question & Answer Session 2
 Background of National HIT Initiatives from ONC Holt Anderson 3
Background of National HIT Initiatives from ONC Holt Anderson 3
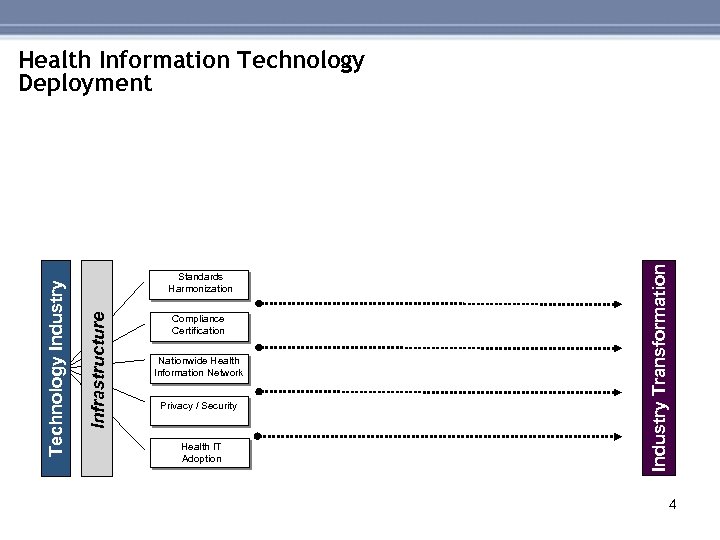 Compliance Certification Nationwide Health Information Network Privacy / Security Health IT Adoption Industry Transformation Standards Harmonization Infrastructure Technology Industry Health Information Technology Deployment 4
Compliance Certification Nationwide Health Information Network Privacy / Security Health IT Adoption Industry Transformation Standards Harmonization Infrastructure Technology Industry Health Information Technology Deployment 4
 Standards Harmonization Process – HHS awarded a contract valued at $3. 3 million to the American National Standards Institute, a non-profit organization that administers and coordinates the U. S. voluntary standardization activities, to convene the Health Information Technology Standards Panel (HITSP). – The HITSP will develop, prototype, and evaluate a harmonization process for achieving a widely accepted and useful set of health IT standards that will support interoperability among health care software applications, particularly EHRs. 5
Standards Harmonization Process – HHS awarded a contract valued at $3. 3 million to the American National Standards Institute, a non-profit organization that administers and coordinates the U. S. voluntary standardization activities, to convene the Health Information Technology Standards Panel (HITSP). – The HITSP will develop, prototype, and evaluate a harmonization process for achieving a widely accepted and useful set of health IT standards that will support interoperability among health care software applications, particularly EHRs. 5
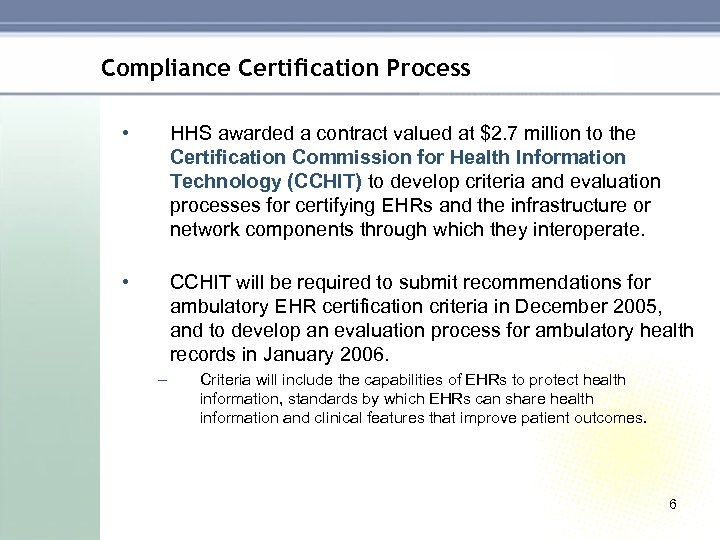 Compliance Certification Process • HHS awarded a contract valued at $2. 7 million to the Certification Commission for Health Information Technology (CCHIT) to develop criteria and evaluation processes for certifying EHRs and the infrastructure or network components through which they interoperate. • CCHIT will be required to submit recommendations for ambulatory EHR certification criteria in December 2005, and to develop an evaluation process for ambulatory health records in January 2006. – Criteria will include the capabilities of EHRs to protect health information, standards by which EHRs can share health information and clinical features that improve patient outcomes. 6
Compliance Certification Process • HHS awarded a contract valued at $2. 7 million to the Certification Commission for Health Information Technology (CCHIT) to develop criteria and evaluation processes for certifying EHRs and the infrastructure or network components through which they interoperate. • CCHIT will be required to submit recommendations for ambulatory EHR certification criteria in December 2005, and to develop an evaluation process for ambulatory health records in January 2006. – Criteria will include the capabilities of EHRs to protect health information, standards by which EHRs can share health information and clinical features that improve patient outcomes. 6
 Privacy and Security Solutions • HHS awarded a contract valued at $11. 5 million to RTI International, a private, non-profit corporation, to lead the Health Information Security and Privacy Collaboration (HISPC), a collaboration that includes the National Governors Association (NGA), up to 40 state and territorial governments, and a multi-disciplinary team of experts. • RTI will oversee the HISPC to assess and develop plans to address variations in organization-level business policies and state laws that affect privacy and security practices that may pose challenges to interoperable electronic health information exchange while maintaining privacy protections. 7
Privacy and Security Solutions • HHS awarded a contract valued at $11. 5 million to RTI International, a private, non-profit corporation, to lead the Health Information Security and Privacy Collaboration (HISPC), a collaboration that includes the National Governors Association (NGA), up to 40 state and territorial governments, and a multi-disciplinary team of experts. • RTI will oversee the HISPC to assess and develop plans to address variations in organization-level business policies and state laws that affect privacy and security practices that may pose challenges to interoperable electronic health information exchange while maintaining privacy protections. 7
 Health Information Technology Adoption Initiative • HHS awarded a contract valued in excess of $1 million to the George Washington University and Massachusetts General Hospital Harvard Institute for Health Policy to support the Health IT Adoption Initiative. • The new initiative is aimed at better characterizing and measuring the state of EHR adoption and determining the effectiveness of policies to accelerate adoption of EHRs and interoperability. • For more information visit: http: //www. hitadoption. org/ 8
Health Information Technology Adoption Initiative • HHS awarded a contract valued in excess of $1 million to the George Washington University and Massachusetts General Hospital Harvard Institute for Health Policy to support the Health IT Adoption Initiative. • The new initiative is aimed at better characterizing and measuring the state of EHR adoption and determining the effectiveness of policies to accelerate adoption of EHRs and interoperability. • For more information visit: http: //www. hitadoption. org/ 8
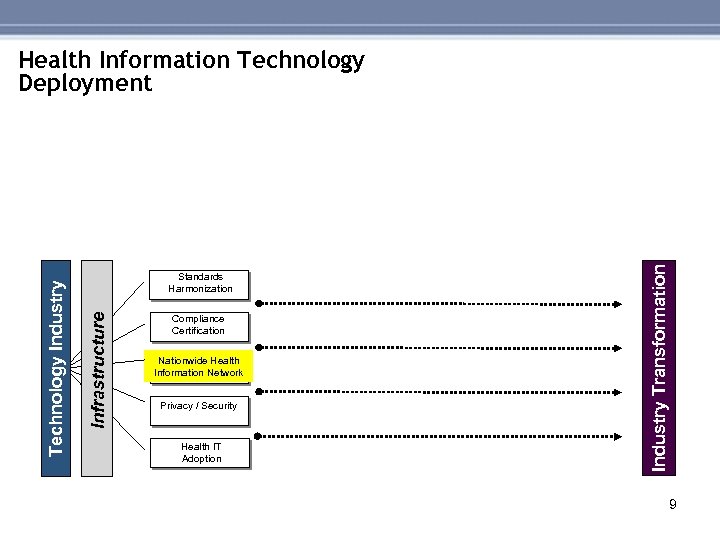 Compliance Certification Nationwide Health Information Network Privacy / Security Health IT Adoption Industry Transformation Standards Harmonization Infrastructure Technology Industry Health Information Technology Deployment 9
Compliance Certification Nationwide Health Information Network Privacy / Security Health IT Adoption Industry Transformation Standards Harmonization Infrastructure Technology Industry Health Information Technology Deployment 9
 Nationwide Health Information Network (NHIN) • Contracts have been awarded by HHS totaling $18. 6 million to four consortia of health care and health information technology organizations to develop prototypes for the Nationwide Health Information Network (NHIN) architecture. – • The contracts were awarded to: Accenture, Computer Sciences Corporation, IBM, and Northrop Grumman, along with their affiliated partners and health care market areas. The four consortia will move the nation toward the President’s goal of personal electronic health records by creating a uniform architecture for health care information that can follow consumers throughout their lives. 10
Nationwide Health Information Network (NHIN) • Contracts have been awarded by HHS totaling $18. 6 million to four consortia of health care and health information technology organizations to develop prototypes for the Nationwide Health Information Network (NHIN) architecture. – • The contracts were awarded to: Accenture, Computer Sciences Corporation, IBM, and Northrop Grumman, along with their affiliated partners and health care market areas. The four consortia will move the nation toward the President’s goal of personal electronic health records by creating a uniform architecture for health care information that can follow consumers throughout their lives. 10
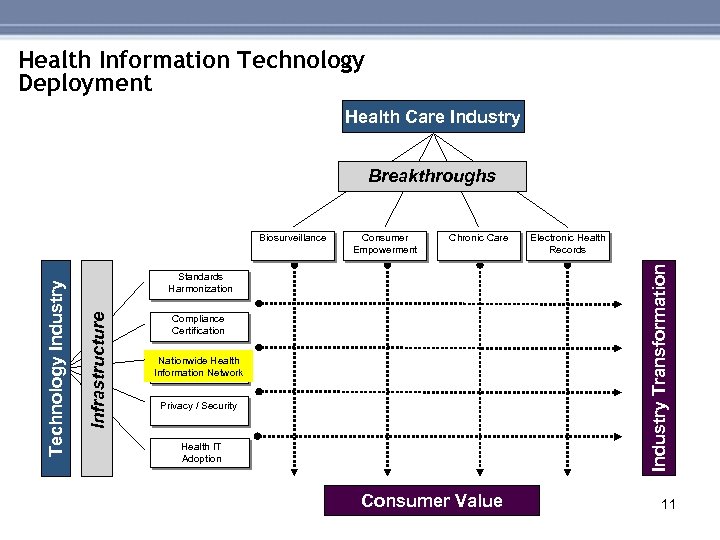 Health Information Technology Deployment Health Care Industry Breakthroughs Chronic Care Electronic Health Records Industry Transformation Consumer Empowerment Standards Harmonization Infrastructure Technology Industry Biosurveillance Compliance Certification Nationwide Health Information Network Privacy / Security Health IT Adoption Consumer Value 11
Health Information Technology Deployment Health Care Industry Breakthroughs Chronic Care Electronic Health Records Industry Transformation Consumer Empowerment Standards Harmonization Infrastructure Technology Industry Biosurveillance Compliance Certification Nationwide Health Information Network Privacy / Security Health IT Adoption Consumer Value 11
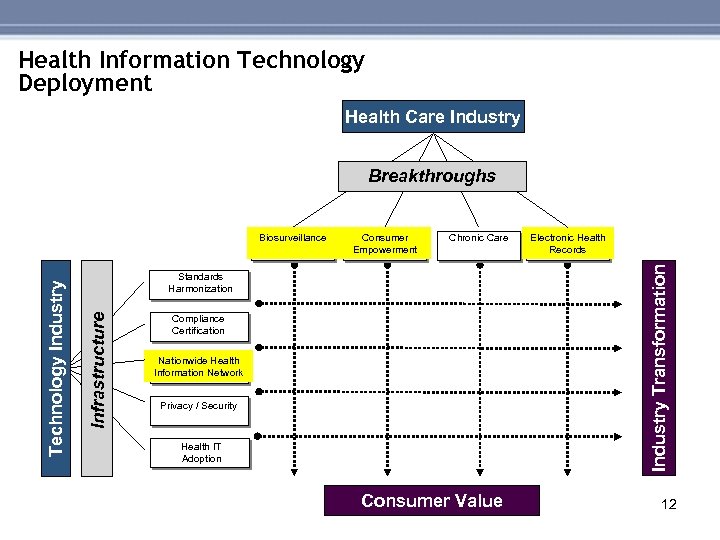 Health Information Technology Deployment Health Care Industry Breakthroughs Chronic Care Electronic Health Records Industry Transformation Consumer Empowerment Standards Harmonization Infrastructure Technology Industry Biosurveillance Compliance Certification Nationwide Health Information Network Privacy / Security Health IT Adoption Consumer Value 12
Health Information Technology Deployment Health Care Industry Breakthroughs Chronic Care Electronic Health Records Industry Transformation Consumer Empowerment Standards Harmonization Infrastructure Technology Industry Biosurveillance Compliance Certification Nationwide Health Information Network Privacy / Security Health IT Adoption Consumer Value 12
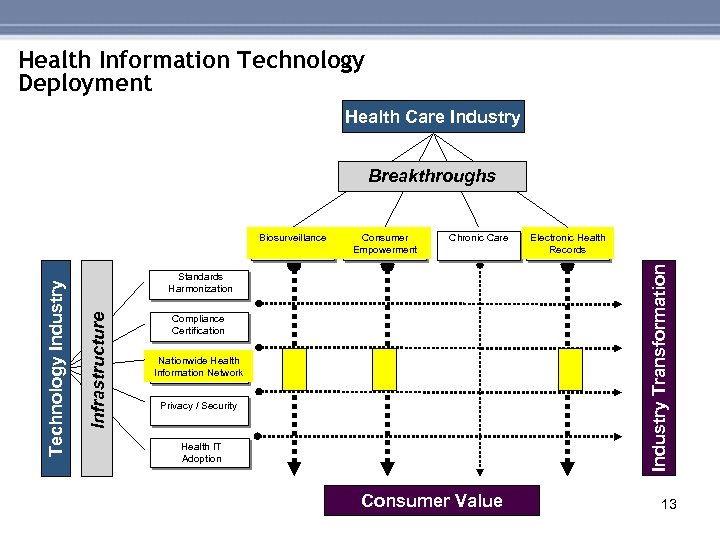 Health Information Technology Deployment Health Care Industry Breakthroughs Chronic Care Electronic Health Records Industry Transformation Consumer Empowerment Standards Harmonization Infrastructure Technology Industry Biosurveillance Compliance Certification Nationwide Health Information Network Privacy / Security Health IT Adoption Consumer Value 13
Health Information Technology Deployment Health Care Industry Breakthroughs Chronic Care Electronic Health Records Industry Transformation Consumer Empowerment Standards Harmonization Infrastructure Technology Industry Biosurveillance Compliance Certification Nationwide Health Information Network Privacy / Security Health IT Adoption Consumer Value 13
 Challenges & Approaches in Developing the Nationwide Health Information Network (NHIN) Architecture Casey Webster 14
Challenges & Approaches in Developing the Nationwide Health Information Network (NHIN) Architecture Casey Webster 14
 Business Consulting Services The Nationwide Health Information Network (NHIN) Architecture Prototype Project Internet 2 Spring Member Meeting April 26, 2006 © 2006 IBM Corporation
Business Consulting Services The Nationwide Health Information Network (NHIN) Architecture Prototype Project Internet 2 Spring Member Meeting April 26, 2006 © 2006 IBM Corporation
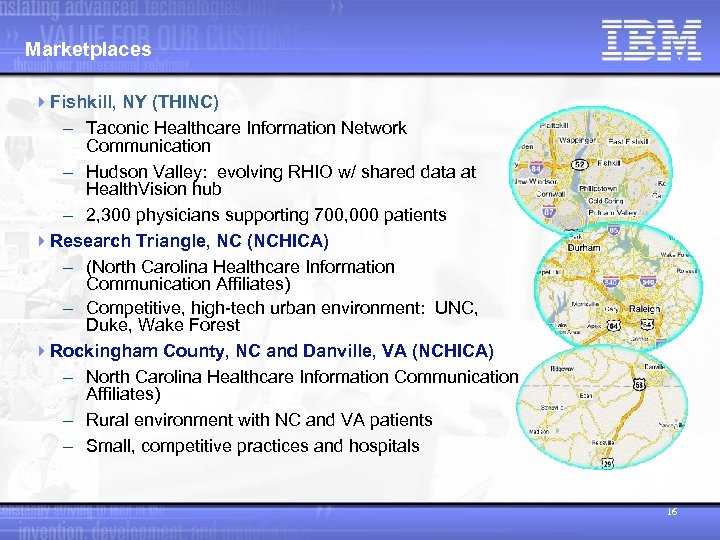 Marketplaces 4 Fishkill, NY (THINC) - Taconic Healthcare Information Network Communication - Hudson Valley: evolving RHIO w/ shared data at Health. Vision hub - 2, 300 physicians supporting 700, 000 patients 4 Research Triangle, NC (NCHICA) - (North Carolina Healthcare Information Communication Affiliates) - Competitive, high-tech urban environment: UNC, Duke, Wake Forest 4 Rockingham County, NC and Danville, VA (NCHICA) - North Carolina Healthcare Information Communication Affiliates) - Rural environment with NC and VA patients - Small, competitive practices and hospitals 16
Marketplaces 4 Fishkill, NY (THINC) - Taconic Healthcare Information Network Communication - Hudson Valley: evolving RHIO w/ shared data at Health. Vision hub - 2, 300 physicians supporting 700, 000 patients 4 Research Triangle, NC (NCHICA) - (North Carolina Healthcare Information Communication Affiliates) - Competitive, high-tech urban environment: UNC, Duke, Wake Forest 4 Rockingham County, NC and Danville, VA (NCHICA) - North Carolina Healthcare Information Communication Affiliates) - Rural environment with NC and VA patients - Small, competitive practices and hospitals 16
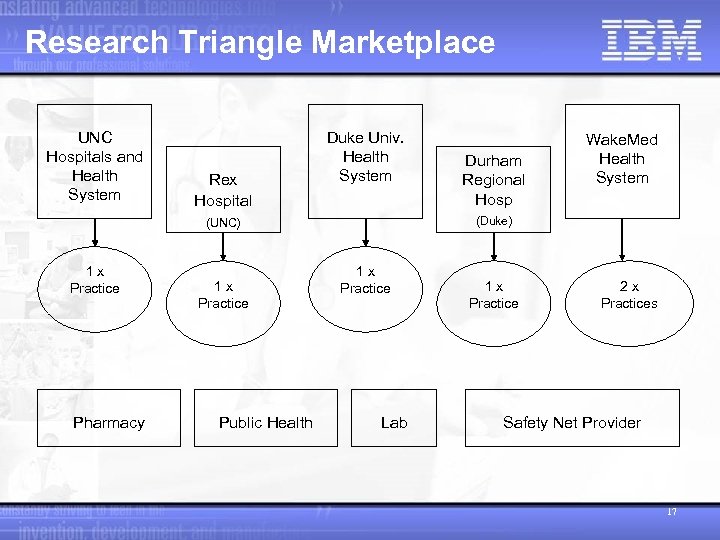 Research Triangle Marketplace UNC Hospitals and Health System Rex Hospital Duke Univ. Health System (Duke) (UNC) 1 x Practice Pharmacy 1 x Practice Public Health Durham Regional Hosp Wake. Med Health System 1 x Practice Lab 1 x Practice 2 x Practices Safety Net Provider 17
Research Triangle Marketplace UNC Hospitals and Health System Rex Hospital Duke Univ. Health System (Duke) (UNC) 1 x Practice Pharmacy 1 x Practice Public Health Durham Regional Hosp Wake. Med Health System 1 x Practice Lab 1 x Practice 2 x Practices Safety Net Provider 17
 Rockingham Co. , NC / Danville, VA Marketplace Annie Penn Hospital Morehead Memorial Hospital (Moses Cone) Moses Cone Health System 1 x Practice Pharmacy (unaffiliated) Public Health 1 x Practice Lab 2 x Practices Safety Net Provider 18
Rockingham Co. , NC / Danville, VA Marketplace Annie Penn Hospital Morehead Memorial Hospital (Moses Cone) Moses Cone Health System 1 x Practice Pharmacy (unaffiliated) Public Health 1 x Practice Lab 2 x Practices Safety Net Provider 18
 Architecture Guiding Principles 4 Community-Centric - Document repositories normalize and store clinical data within a community 4 Can be hosted by individual hospitals/practices and/or shared within the community - Community hub provides MPI, document locator, security and support services - The community hub is the gateway to other communities 4 Drive and conform to standards - Instantiation of IHE interoperability framework (XDS, PIX/PDQ, ATNA & CT profiles) - Clinical events stored as HL 7 CDA(r 2)-compliant documents - Java/J 2 EE implementation is hardware & software vendor agnostic - Proven Internet protocols for authentication, authorization, and security 4 Provide security & privacy w/o sacrificing usability or research value - Anonymous/pseudonymous data that can be re-identified as needed/permitted - Supports other data aggregates (registries, biosurveillance, outcomes analysis) 4 Practical - Scalable and cost-effective at every level of practice - Point-of-care performance is critical to adoption 19
Architecture Guiding Principles 4 Community-Centric - Document repositories normalize and store clinical data within a community 4 Can be hosted by individual hospitals/practices and/or shared within the community - Community hub provides MPI, document locator, security and support services - The community hub is the gateway to other communities 4 Drive and conform to standards - Instantiation of IHE interoperability framework (XDS, PIX/PDQ, ATNA & CT profiles) - Clinical events stored as HL 7 CDA(r 2)-compliant documents - Java/J 2 EE implementation is hardware & software vendor agnostic - Proven Internet protocols for authentication, authorization, and security 4 Provide security & privacy w/o sacrificing usability or research value - Anonymous/pseudonymous data that can be re-identified as needed/permitted - Supports other data aggregates (registries, biosurveillance, outcomes analysis) 4 Practical - Scalable and cost-effective at every level of practice - Point-of-care performance is critical to adoption 19
 IBM Business Consulting Services Architecture Community Architecture MPI Services Registry Services PDQ Access Control Authentication Authorization Patient Consent XDR NHIN Interface CAD Search/Retrieval CAD Policies/Security Admin/Maintenance Qo. S Support Services ATNA Logging CT Community Services Biosurveillance PHR Portal Security Services PIX Community Hub Document Locator Community XDS Hospital or Physician Practice Interface Data Services Integration Engine or Data Source HCN Gateway Xform/Xlate IHE Adapter Document Services Document Storage and Retrieval XDS 20
IBM Business Consulting Services Architecture Community Architecture MPI Services Registry Services PDQ Access Control Authentication Authorization Patient Consent XDR NHIN Interface CAD Search/Retrieval CAD Policies/Security Admin/Maintenance Qo. S Support Services ATNA Logging CT Community Services Biosurveillance PHR Portal Security Services PIX Community Hub Document Locator Community XDS Hospital or Physician Practice Interface Data Services Integration Engine or Data Source HCN Gateway Xform/Xlate IHE Adapter Document Services Document Storage and Retrieval XDS 20
 Architecture Cross-Community Interaction 4 All cross-community interactions are brokered through the NHIN interface, using other community services as needed 4 Authentication and authority uses a federated model, with trust relationships established at the NHIN level 4 Cross-community patient lookup is based on demographic matching - Identity is established by matching demographic data between the local and remote PDQ databases, with a conservative threshold - IBM research is working on open issues such as patient mobility, multiresident patients (“snowbirds”), directed searches, and undirected bounded searches 4 Once a positive patient match is obtained, document search and retrieval is identical to the intra-community model 21
Architecture Cross-Community Interaction 4 All cross-community interactions are brokered through the NHIN interface, using other community services as needed 4 Authentication and authority uses a federated model, with trust relationships established at the NHIN level 4 Cross-community patient lookup is based on demographic matching - Identity is established by matching demographic data between the local and remote PDQ databases, with a conservative threshold - IBM research is working on open issues such as patient mobility, multiresident patients (“snowbirds”), directed searches, and undirected bounded searches 4 Once a positive patient match is obtained, document search and retrieval is identical to the intra-community model 21
 Business Consulting Services NHIN Architecture Prototype – Introduction Acronyms § IHE (Integrating the Healthcare Enterprise) Profiles – XDS – Cross-Enterprise Document Sharing • Supports saving, registering, querying and retrieving documents across enterprises but within an administrative domain – PIX – Patient Identifier Cross-referencing • Supports cross referencing of patient identifiers across domains – PDQ – Patient Demographics Query • Supports query for patients given a minimal set of demographic criteria (e. g. ID or partial name) returning all the demographics and a patient identifier within a domain – ATNA – Audit Trail and Node Authentication • Supports auditing and secure communications – CT – Consistent Time • Supports consistent time across multiple systems § J 2 EE – Java 2 Enterprise Edition – Sun’s Java-based framework for developing and deploying complex, scalable business solutions in a standardized manner, leveraging the following technologies – JDBC – Java Database Connectivity • A vendor-neutral means of accessing relational data from within a Java/J 2 EE application. Note that the data itself does not necessarily have to be stored in a relational database. – EJB – Enterprise Java. Beans • Java. Beans are reusable components within the J 2 EE architecture – JMS – Java Messaging Service • 22 A vendor-neutral means of accessing message queuing systems (eg, MQ Series) from within a Java/J 2 EE application © 2006 IBM Corporation
Business Consulting Services NHIN Architecture Prototype – Introduction Acronyms § IHE (Integrating the Healthcare Enterprise) Profiles – XDS – Cross-Enterprise Document Sharing • Supports saving, registering, querying and retrieving documents across enterprises but within an administrative domain – PIX – Patient Identifier Cross-referencing • Supports cross referencing of patient identifiers across domains – PDQ – Patient Demographics Query • Supports query for patients given a minimal set of demographic criteria (e. g. ID or partial name) returning all the demographics and a patient identifier within a domain – ATNA – Audit Trail and Node Authentication • Supports auditing and secure communications – CT – Consistent Time • Supports consistent time across multiple systems § J 2 EE – Java 2 Enterprise Edition – Sun’s Java-based framework for developing and deploying complex, scalable business solutions in a standardized manner, leveraging the following technologies – JDBC – Java Database Connectivity • A vendor-neutral means of accessing relational data from within a Java/J 2 EE application. Note that the data itself does not necessarily have to be stored in a relational database. – EJB – Enterprise Java. Beans • Java. Beans are reusable components within the J 2 EE architecture – JMS – Java Messaging Service • 22 A vendor-neutral means of accessing message queuing systems (eg, MQ Series) from within a Java/J 2 EE application © 2006 IBM Corporation
 What is Possible Today! Bill Weems 23
What is Possible Today! Bill Weems 23
 Internet 2 Spring Mtg. 2006 University of Texas Health Science Center at Houston UTHSC-H • Six Schools – Graduate School of Biomedical Sciences – Dental School – Medical School – Nursing School – School of Health Information Sciences – School of Public Health • ~ 10, 000 Students, Faculty and Staff
Internet 2 Spring Mtg. 2006 University of Texas Health Science Center at Houston UTHSC-H • Six Schools – Graduate School of Biomedical Sciences – Dental School – Medical School – Nursing School – School of Health Information Sciences – School of Public Health • ~ 10, 000 Students, Faculty and Staff
 Internet 2 Spring Mtg. 2006 Texas Medical Center www. tmc. edu • • • Forty One Institutions on 740 Acres Approximately 65, 000 Employees Seven Large Hospitals 6, 176 Licensed Beds & 334 Bassinets 5. 2 Million Patient Visits in 2004 Baylor College of Medicine Rice University Texas A&M Institution of Biotechnology University of Texas Health Science Center at Houston University of Texas M. D. Anderson Cancer Center
Internet 2 Spring Mtg. 2006 Texas Medical Center www. tmc. edu • • • Forty One Institutions on 740 Acres Approximately 65, 000 Employees Seven Large Hospitals 6, 176 Licensed Beds & 334 Bassinets 5. 2 Million Patient Visits in 2004 Baylor College of Medicine Rice University Texas A&M Institution of Biotechnology University of Texas Health Science Center at Houston University of Texas M. D. Anderson Cancer Center
 Internet 2 Spring Mtg. 2006 Scenario I • UT-Houston Residency Programs have some attending physicians that are non-university personnel – e. g. M. D. Anderson & Baylor • Dr. James at M. D. Anderson is to be an attending physician in the UT-Houston Internal Medicine Residency Program. • On-line Graduate Medical Education Information System (GMEIS) contains confidential and sensitive information - including HIPAA data. • Dr. James needs access to GMEIS. • How is Dr. James’ identity verified, authenticated and authorized to have access as an attending physician? • If Dr. James suddenly leaves M. D. Anderson, is his access to UTHouston Residency Program immediately abolished?
Internet 2 Spring Mtg. 2006 Scenario I • UT-Houston Residency Programs have some attending physicians that are non-university personnel – e. g. M. D. Anderson & Baylor • Dr. James at M. D. Anderson is to be an attending physician in the UT-Houston Internal Medicine Residency Program. • On-line Graduate Medical Education Information System (GMEIS) contains confidential and sensitive information - including HIPAA data. • Dr. James needs access to GMEIS. • How is Dr. James’ identity verified, authenticated and authorized to have access as an attending physician? • If Dr. James suddenly leaves M. D. Anderson, is his access to UTHouston Residency Program immediately abolished?
 Internet 2 Spring Mtg. 2006 Scenario I - Problems • Dr. James has no digital credentials. • U. T. Houston policy requires that a responsible party at U. T. Houston assume responsibility for Dr. James and sponsor him as a “guest”. • Dr. James must appear before a Local Registration Administration Agent (LRAA) to have his identity verified and be credentialed. – Does not verify his status with M. D. Anderson. • If Dr. James leaves M. D. Anderson, there is no automatic process in place to revoke his access rights.
Internet 2 Spring Mtg. 2006 Scenario I - Problems • Dr. James has no digital credentials. • U. T. Houston policy requires that a responsible party at U. T. Houston assume responsibility for Dr. James and sponsor him as a “guest”. • Dr. James must appear before a Local Registration Administration Agent (LRAA) to have his identity verified and be credentialed. – Does not verify his status with M. D. Anderson. • If Dr. James leaves M. D. Anderson, there is no automatic process in place to revoke his access rights.
 Internet 2 Spring Mtg. 2006 Ideally, individuals would each like a single digital credential that can be securely used to authenticate his or her identity anytime authentication of identity is required to secure any transaction.
Internet 2 Spring Mtg. 2006 Ideally, individuals would each like a single digital credential that can be securely used to authenticate his or her identity anytime authentication of identity is required to secure any transaction.
 Internet 2 Spring Mtg. 2006 Identity Vetting & Credentialing Identity Provider (Id. P) uth. tmc. edu Assigns Everlasting Identifier Permanently Bound Id. P Obtains Physical Characteristics Person Permanent Identity Database Issues Digital Credential Person Only Digital Credential Activation
Internet 2 Spring Mtg. 2006 Identity Vetting & Credentialing Identity Provider (Id. P) uth. tmc. edu Assigns Everlasting Identifier Permanently Bound Id. P Obtains Physical Characteristics Person Permanent Identity Database Issues Digital Credential Person Only Digital Credential Activation
 Internet 2 Spring Mtg. 2006 UTHSC-H: An Identity Provider (Id. P) It is critical to recognize that the university functions as an identity provider (Id. P) in that UTHSC-H provides individuals with digital credentials that consist of an identifier and an authenticator. As an Id. P, the university assumes specific responsibilities and liabilities.
Internet 2 Spring Mtg. 2006 UTHSC-H: An Identity Provider (Id. P) It is critical to recognize that the university functions as an identity provider (Id. P) in that UTHSC-H provides individuals with digital credentials that consist of an identifier and an authenticator. As an Id. P, the university assumes specific responsibilities and liabilities.
 Internet 2 Spring Mtg. 2006 Two Categories of Identity • Physical Identity – Assigned Identifier - Authentication – Facial picture, – Fingerprints – DNA sample • Identity Attributes – Authorization Attributes – Common name, – Address, – Institutional affiliations - e. g. faculty, student, staff, contractor, – Specific group memberships, – Roles, – Etc.
Internet 2 Spring Mtg. 2006 Two Categories of Identity • Physical Identity – Assigned Identifier - Authentication – Facial picture, – Fingerprints – DNA sample • Identity Attributes – Authorization Attributes – Common name, – Address, – Institutional affiliations - e. g. faculty, student, staff, contractor, – Specific group memberships, – Roles, – Etc.
 UTHSC-H Identity Management System HRMS SIS GMEIS INDIS Identity Reconciliation & Provisioning Processes Authoritative Enterprise Directories OAC 7 Sync Secondary Directories UTP Person Registry OAC 47 Guest MS User Administration Tools Authentication Service Attribute Management Authorization Service Change Password
UTHSC-H Identity Management System HRMS SIS GMEIS INDIS Identity Reconciliation & Provisioning Processes Authoritative Enterprise Directories OAC 7 Sync Secondary Directories UTP Person Registry OAC 47 Guest MS User Administration Tools Authentication Service Attribute Management Authorization Service Change Password
 Internet 2 Spring Mtg. 2006 Source of Authority (SOA) Responsibilities An organizational entity officially responsible for identifying individuals having explicitly defined affiliations with the university constitutes a “source of authority” (SOA). The SOA is responsible for • Identifying an individual, • Maintaining the appropriate records that define a person's affiliation, • Providing others with information about the specifics of an affiliation and, • Determining if an affiliation is currently active or inactive – i. e. can a person be credentialed
Internet 2 Spring Mtg. 2006 Source of Authority (SOA) Responsibilities An organizational entity officially responsible for identifying individuals having explicitly defined affiliations with the university constitutes a “source of authority” (SOA). The SOA is responsible for • Identifying an individual, • Maintaining the appropriate records that define a person's affiliation, • Providing others with information about the specifics of an affiliation and, • Determining if an affiliation is currently active or inactive – i. e. can a person be credentialed
 Internet 2 Spring Mtg. 2006 Person Registry • Identity Reconciliation – Unique Identifiers Generated by Source of Record • SSN – If Available (HRMS, GMEIS, UTP, Guest, SIS) • Student ID, • Employee Number - HRMS – Full Name • First, Middle, Last – Birth Information • Date of Birth, • City of Birth, • Country of Birth – Gender • UUID – An everlasting unique identifier
Internet 2 Spring Mtg. 2006 Person Registry • Identity Reconciliation – Unique Identifiers Generated by Source of Record • SSN – If Available (HRMS, GMEIS, UTP, Guest, SIS) • Student ID, • Employee Number - HRMS – Full Name • First, Middle, Last – Birth Information • Date of Birth, • City of Birth, • Country of Birth – Gender • UUID – An everlasting unique identifier
 Internet 2 Spring Mtg. 2006 Issuing a Digital Credential • Individual appears before an Identity Provider (Id. P) which accepts the responsibility to – positively determine and catalog a person's uniquely identifying physical characteristics (e. g. picture, two fingerprints, DNA sample), – assign a unique, everlasting digital identifier to each person identified, – issue each identified person a digital credential that can only be used by that person to authenticate his or her identity, – maintain a defined affiliation with each individual whereby the validity of the digital credential is renewed at specified intervals.
Internet 2 Spring Mtg. 2006 Issuing a Digital Credential • Individual appears before an Identity Provider (Id. P) which accepts the responsibility to – positively determine and catalog a person's uniquely identifying physical characteristics (e. g. picture, two fingerprints, DNA sample), – assign a unique, everlasting digital identifier to each person identified, – issue each identified person a digital credential that can only be used by that person to authenticate his or her identity, – maintain a defined affiliation with each individual whereby the validity of the digital credential is renewed at specified intervals.
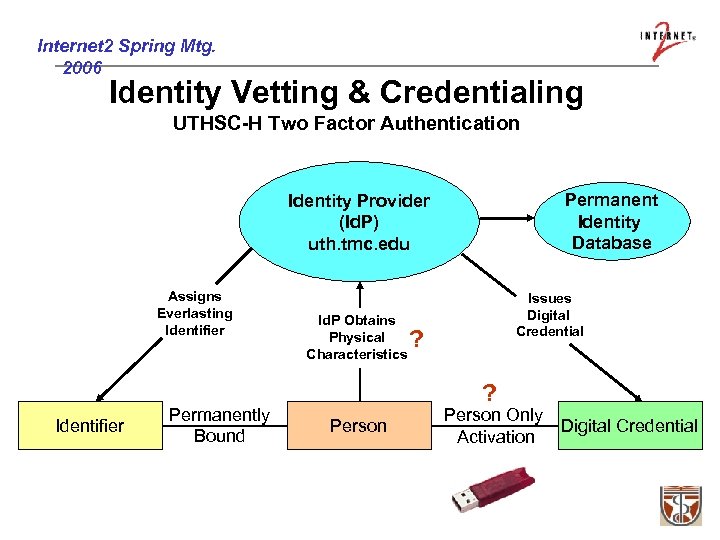 Internet 2 Spring Mtg. 2006 Identity Vetting & Credentialing UTHSC-H Two Factor Authentication Permanent Identity Database Identity Provider (Id. P) uth. tmc. edu Assigns Everlasting Identifier Permanently Bound Id. P Obtains Physical Characteristics Issues Digital Credential ? ? Person Only Digital Credential Activation
Internet 2 Spring Mtg. 2006 Identity Vetting & Credentialing UTHSC-H Two Factor Authentication Permanent Identity Database Identity Provider (Id. P) uth. tmc. edu Assigns Everlasting Identifier Permanently Bound Id. P Obtains Physical Characteristics Issues Digital Credential ? ? Person Only Digital Credential Activation
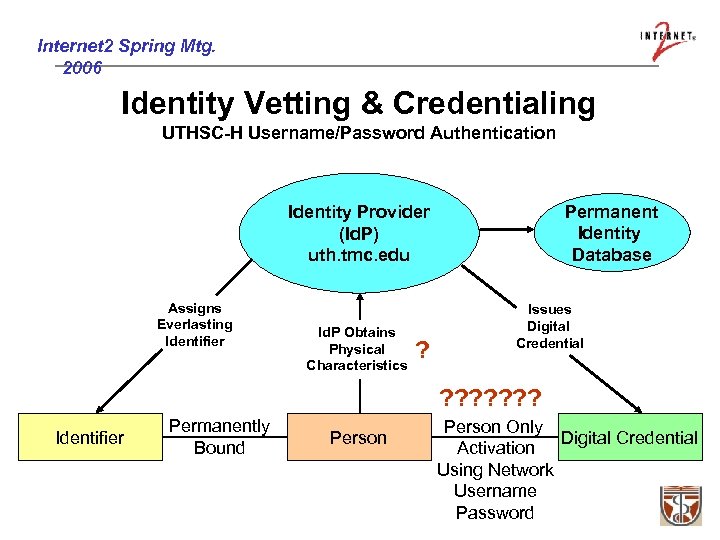 Internet 2 Spring Mtg. 2006 Identity Vetting & Credentialing UTHSC-H Username/Password Authentication Permanent Identity Database Identity Provider (Id. P) uth. tmc. edu Assigns Everlasting Identifier Id. P Obtains Physical Characteristics ? Issues Digital Credential ? ? ? ? Identifier Permanently Bound Person Only Digital Credential Activation Using Network Username Password
Internet 2 Spring Mtg. 2006 Identity Vetting & Credentialing UTHSC-H Username/Password Authentication Permanent Identity Database Identity Provider (Id. P) uth. tmc. edu Assigns Everlasting Identifier Id. P Obtains Physical Characteristics ? Issues Digital Credential ? ? ? ? Identifier Permanently Bound Person Only Digital Credential Activation Using Network Username Password
 Internet 2 Spring Mtg. 2006 Federal E-Authentication Initiative http: //www. cio. gov/eauthentication/ • Levels of assurance (Different Requirements) – – Level 1 – e. g. no identity vetting Level 2 - e. g. specific identity vetting requirements Level 3 – e. g. cryptographic tokens required Level 4 – e. g. cryptographic hard tokens required • Credential Assessment Framework Suite (CAF)
Internet 2 Spring Mtg. 2006 Federal E-Authentication Initiative http: //www. cio. gov/eauthentication/ • Levels of assurance (Different Requirements) – – Level 1 – e. g. no identity vetting Level 2 - e. g. specific identity vetting requirements Level 3 – e. g. cryptographic tokens required Level 4 – e. g. cryptographic hard tokens required • Credential Assessment Framework Suite (CAF)
 Internet 2 Spring Mtg. 2006 UTHSC-H Strategic Authentication Goals • Two authentication mechanisms. – Single university ID (UID) and password – Public Key Digital ID on Token (two-factor authentication) • Digital Signatures – Authenticates senders – Guarantees messages are unaltered, i. e. message integrity – Provides for non-repudiation – Legal signature • Encryption of email and other documents • Highly Secure Access Control • Potential for inherent global trust
Internet 2 Spring Mtg. 2006 UTHSC-H Strategic Authentication Goals • Two authentication mechanisms. – Single university ID (UID) and password – Public Key Digital ID on Token (two-factor authentication) • Digital Signatures – Authenticates senders – Guarantees messages are unaltered, i. e. message integrity – Provides for non-repudiation – Legal signature • Encryption of email and other documents • Highly Secure Access Control • Potential for inherent global trust
 Internet 2 Spring Mtg. 2006 Mass Mailing of Signed & Encrypted E-mail Mailing List jdoe@uth. tmc. edu jsmith@bcm. edu gmarks@mhhs. org Message Automated Mailer Request Recipient's Digital Cert. LDAP Directory Service Signed & Encrypted jdoe@uth. tmc. edu jsmith@bcm. edu gmarks@mhhs. org
Internet 2 Spring Mtg. 2006 Mass Mailing of Signed & Encrypted E-mail Mailing List jdoe@uth. tmc. edu jsmith@bcm. edu gmarks@mhhs. org Message Automated Mailer Request Recipient's Digital Cert. LDAP Directory Service Signed & Encrypted jdoe@uth. tmc. edu jsmith@bcm. edu gmarks@mhhs. org
 Internet 2 Spring Mtg. 2006 • • • The University of Texas System STRATEGIC LEADERSHIP COUNCIL Statement of Direction Identity Management April 27, 2004 LDAP (Lightweight Directory Access Protocol) compliant directory services, eduperson schema as promulgated by EDUCAUSE and Internet 2, utperson schema (to be developed) inter-institutional access control utilizing Internet 2 Shibboleth, and consistent institutional definitions and identity management trust policies for students, faculty, and staff as well as sponsored affiliates.
Internet 2 Spring Mtg. 2006 • • • The University of Texas System STRATEGIC LEADERSHIP COUNCIL Statement of Direction Identity Management April 27, 2004 LDAP (Lightweight Directory Access Protocol) compliant directory services, eduperson schema as promulgated by EDUCAUSE and Internet 2, utperson schema (to be developed) inter-institutional access control utilizing Internet 2 Shibboleth, and consistent institutional definitions and identity management trust policies for students, faculty, and staff as well as sponsored affiliates.
 Federated Services Identity (Id. P) & Service Providers (SP) Identity Provider (Id. P) uth. tmc. edu Identity Provider (Id. P) utsystem. edu Identity Provider (Id. P) bcm. edu Public Key Resource Provider (SP) library. tmc. edu Federation WAYF Service In. Common GMEIS (SP) uth. tmc. edu Infrastructure Identity Provider (Id. P) mdanderson. org Blackboard (SP) uth. tmc. edu Identity Provider (Id. P) utmb. edu
Federated Services Identity (Id. P) & Service Providers (SP) Identity Provider (Id. P) uth. tmc. edu Identity Provider (Id. P) utsystem. edu Identity Provider (Id. P) bcm. edu Public Key Resource Provider (SP) library. tmc. edu Federation WAYF Service In. Common GMEIS (SP) uth. tmc. edu Infrastructure Identity Provider (Id. P) mdanderson. org Blackboard (SP) uth. tmc. edu Identity Provider (Id. P) utmb. edu
 Home Organization Id. P Service Provider Browser Authentication System (ISO/SSO/Cert) SP SHIRE Handle Service Federation WAYF SERVICE SHAR (IN COMMON) Resource Manager Attribute Authority Attributes determined by ARP RBAC Authorization System - LDAP (eduperson) Shib Software = Web Site
Home Organization Id. P Service Provider Browser Authentication System (ISO/SSO/Cert) SP SHIRE Handle Service Federation WAYF SERVICE SHAR (IN COMMON) Resource Manager Attribute Authority Attributes determined by ARP RBAC Authorization System - LDAP (eduperson) Shib Software = Web Site
 How Does Shibboleth Work? I am satisfied with the attributes. You are allowed access 11 Shibboleth Your request is forwarded to Home University your Browser Organization Handle Service What is your Id. P Organization? Authentication 4 3 Who are You? System (ISO/SSO/Cert) Can you login? WAYF 5 Resource Provider Who are 1 2 (In Common) 6 SHAR 7 Resource Manager Handle Service What are who you are. I know the 8 attributes for Your request and Attribute this user? Authority handle is redirected to Target 9 LDAP (eduperson) you and where you SP come from? Now I know who you are. What are your SHIRE user attributes? 10 Attributes determined by ARP Your attributes are returned to Target Web Site
How Does Shibboleth Work? I am satisfied with the attributes. You are allowed access 11 Shibboleth Your request is forwarded to Home University your Browser Organization Handle Service What is your Id. P Organization? Authentication 4 3 Who are You? System (ISO/SSO/Cert) Can you login? WAYF 5 Resource Provider Who are 1 2 (In Common) 6 SHAR 7 Resource Manager Handle Service What are who you are. I know the 8 attributes for Your request and Attribute this user? Authority handle is redirected to Target 9 LDAP (eduperson) you and where you SP come from? Now I know who you are. What are your SHIRE user attributes? 10 Attributes determined by ARP Your attributes are returned to Target Web Site
 Internet 2 Spring Mtg. 2006 Lessons Learned The focus of planning should be on how Identity Management makes life great for people in cyberspace!!! Don’t focus on underlying theory, arcane concepts and minute implementation details. If basic infrastructure is in place along with user applications, people will use it and demand more.
Internet 2 Spring Mtg. 2006 Lessons Learned The focus of planning should be on how Identity Management makes life great for people in cyberspace!!! Don’t focus on underlying theory, arcane concepts and minute implementation details. If basic infrastructure is in place along with user applications, people will use it and demand more.
 Internet 2 Spring Mtg. 2006 What Is Needed To Reach Critical Mass? • Develop a core group that operationally believes in & understands Identity Management! • Identity Management basic policies and procedures. • Identity reconciliation & provisioning systems • Operational LDAP directory service. • As many “real” applications as possible! – Solutions that use signing & encryption. – Cherished resources PKI and Shibboleth enabled for access.
Internet 2 Spring Mtg. 2006 What Is Needed To Reach Critical Mass? • Develop a core group that operationally believes in & understands Identity Management! • Identity Management basic policies and procedures. • Identity reconciliation & provisioning systems • Operational LDAP directory service. • As many “real” applications as possible! – Solutions that use signing & encryption. – Cherished resources PKI and Shibboleth enabled for access.
 Thank You Questions ? 47
Thank You Questions ? 47


