7dfb2a4d7321799f895505c88466129b.ppt
- Количество слайдов: 19
 Federal Approach to Electronic Credentials For services to citizens, businesses, other governments, and employees Mary J. Mitchell Office of Electronic Government mary. mitchell@gsa. gov web: egov. gov Federal PKI efforts: www. cio. gov/fpkisc
Federal Approach to Electronic Credentials For services to citizens, businesses, other governments, and employees Mary J. Mitchell Office of Electronic Government mary. mitchell@gsa. gov web: egov. gov Federal PKI efforts: www. cio. gov/fpkisc
 E-Government Management Initiative Vision: deliver an order of magnitude improvement in the federal government’s value to the citizen. Integral Part of President’s Management Agenda Definition: use of digital technologies to transform government operations in order to improve effectiveness, efficiency, and service delivery. The Principles: r Citizen-centered, Market-based, Resultsoriented r Simplify & Unify
E-Government Management Initiative Vision: deliver an order of magnitude improvement in the federal government’s value to the citizen. Integral Part of President’s Management Agenda Definition: use of digital technologies to transform government operations in order to improve effectiveness, efficiency, and service delivery. The Principles: r Citizen-centered, Market-based, Resultsoriented r Simplify & Unify
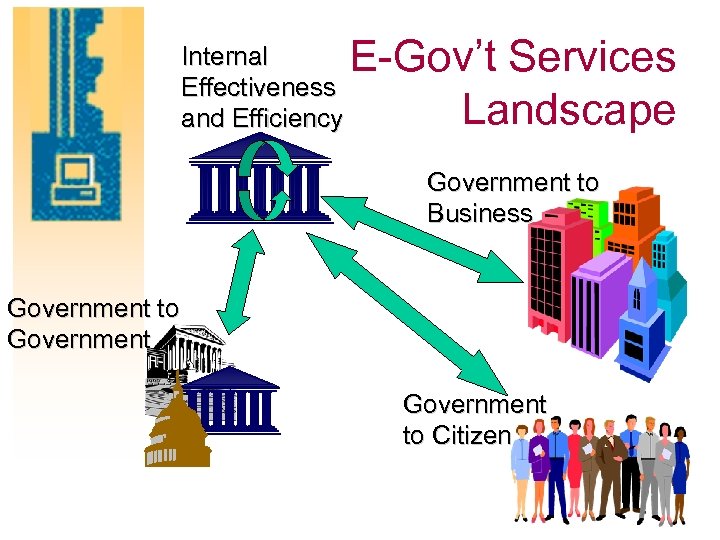 Internal Effectiveness and Efficiency E-Gov’t Services Landscape Government to Business Government to Citizen
Internal Effectiveness and Efficiency E-Gov’t Services Landscape Government to Business Government to Citizen
 When Web Interactions Need Strong Security • To protect privacy, government must know whom it is dealing with • Operations exceed reasonable risk • User Authentication – Knowing who your correspondent is • Transaction Integrity – Ensuring the message sent is the message received • Non-Repudiation – Correspondent cannot deny conducting transaction • Confidentiality – Only authorized persons can read the message
When Web Interactions Need Strong Security • To protect privacy, government must know whom it is dealing with • Operations exceed reasonable risk • User Authentication – Knowing who your correspondent is • Transaction Integrity – Ensuring the message sent is the message received • Non-Repudiation – Correspondent cannot deny conducting transaction • Confidentiality – Only authorized persons can read the message
 Identity Credentials • Driver’s License • Employee Identification Card • Passport • Birth Certificate • Physical Presence • Social Security Number • Signature • Electronic Credentials (including PKI Certificates)
Identity Credentials • Driver’s License • Employee Identification Card • Passport • Birth Certificate • Physical Presence • Social Security Number • Signature • Electronic Credentials (including PKI Certificates)
 Obstacles to Issuing Citizens Digital Certificates • Some populations (e. g. , students, lowincome) lack sufficient means for identity proofing like a credit history, permanent address, etc. • Certain individuals object to divulging personal information (lack of trust in who and if adequately safeguarded) • Cost and administrative complexity of the certificate issuance
Obstacles to Issuing Citizens Digital Certificates • Some populations (e. g. , students, lowincome) lack sufficient means for identity proofing like a credit history, permanent address, etc. • Certain individuals object to divulging personal information (lack of trust in who and if adequately safeguarded) • Cost and administrative complexity of the certificate issuance
 E-Gov’t Strategy: Solutions to Barriers Incorporates PKI
E-Gov’t Strategy: Solutions to Barriers Incorporates PKI
 e. Authentication Direction Simplify and Unify • Efforts focused on PMC approved E-Gov e -Authentication Initiative and tie to Firstgov • Assist other E-Gov’t initiatives in defining their identity authentication needs • Develop applications for cross-governmental use • Coordinate aggregated buy of authentication products and services • Promote interoperability with other entities through FBCA
e. Authentication Direction Simplify and Unify • Efforts focused on PMC approved E-Gov e -Authentication Initiative and tie to Firstgov • Assist other E-Gov’t initiatives in defining their identity authentication needs • Develop applications for cross-governmental use • Coordinate aggregated buy of authentication products and services • Promote interoperability with other entities through FBCA
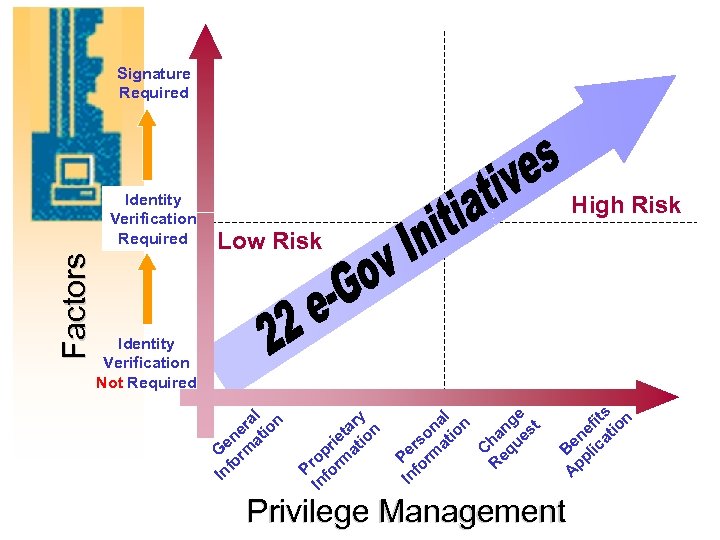 Signature Required Factors Identity Verification Required High Risk Low Risk Identity Verification Not Required l ra ion ne at e G rm o nf I y ar n t rie atio p ro rm P fo In e al n n io ng st o ha ue rs at C eq Pe orm R nf I Privilege Management s fit ion ne at e B plic p A
Signature Required Factors Identity Verification Required High Risk Low Risk Identity Verification Not Required l ra ion ne at e G rm o nf I y ar n t rie atio p ro rm P fo In e al n n io ng st o ha ue rs at C eq Pe orm R nf I Privilege Management s fit ion ne at e B plic p A
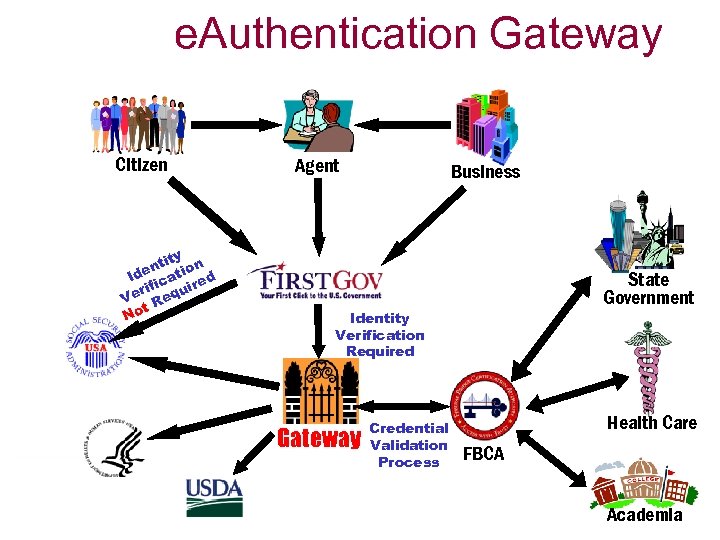 e. Authentication Gateway Citizen ty nti tion Ide ica ed rif quir Ve Re t No Agent Business State Government Identity Verification Required Gateway Credential Validation Process Health Care FBCA Academia
e. Authentication Gateway Citizen ty nti tion Ide ica ed rif quir Ve Re t No Agent Business State Government Identity Verification Required Gateway Credential Validation Process Health Care FBCA Academia
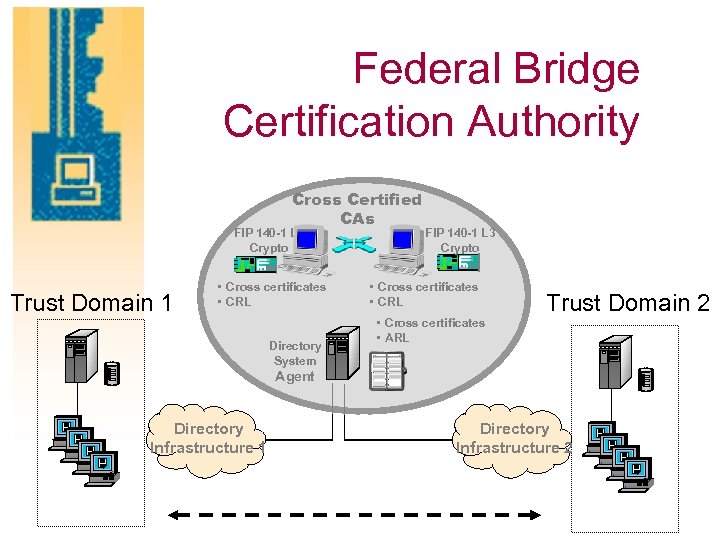 Federal Bridge Certification Authority Cross Certified CAs FIP 140 -1 L 3 Crypto Trust Domain 1 • Cross certificates • CRL Directory System FIP 140 -1 L 3 Crypto • Cross certificates • CRL Trust Domain 2 • Cross certificates • ARL Agent Directory Infrastructure 1 Directory Infrastructure 2
Federal Bridge Certification Authority Cross Certified CAs FIP 140 -1 L 3 Crypto Trust Domain 1 • Cross certificates • CRL Directory System FIP 140 -1 L 3 Crypto • Cross certificates • CRL Trust Domain 2 • Cross certificates • ARL Agent Directory Infrastructure 1 Directory Infrastructure 2
 Selected Agency PKI Efforts • The Evolving Federal Public Key Infrastructure document: www. cio. gov/fpkisc • Department of Labor’s Career Management Account • National Institute of Standards’ Advanced Technology Grants System • Social Security Administration’s Wage Reporting and Medical Evidence • Drug Enforcement Agency’s Electronic Prescriptions for Controlled Substances
Selected Agency PKI Efforts • The Evolving Federal Public Key Infrastructure document: www. cio. gov/fpkisc • Department of Labor’s Career Management Account • National Institute of Standards’ Advanced Technology Grants System • Social Security Administration’s Wage Reporting and Medical Evidence • Drug Enforcement Agency’s Electronic Prescriptions for Controlled Substances

 Nat’l Institute of. Standards and Technology (NIST) • ACES used for the electronic submission and review of proposals for the Advanced Technology Program (ATP) • Uses digitally signed documents to send proprietary information over the Internet, digitally signs and encrypts forms, captures data and populates ATP database • Uses a web server for downloads/ submission of forms and documents, then pulls them behind NIST and ATP firewall • Pilot with 12 proposal submissions completed in Sept 2001 • Goes “live” for ATP’s FY 2002 competition
Nat’l Institute of. Standards and Technology (NIST) • ACES used for the electronic submission and review of proposals for the Advanced Technology Program (ATP) • Uses digitally signed documents to send proprietary information over the Internet, digitally signs and encrypts forms, captures data and populates ATP database • Uses a web server for downloads/ submission of forms and documents, then pulls them behind NIST and ATP firewall • Pilot with 12 proposal submissions completed in Sept 2001 • Goes “live” for ATP’s FY 2002 competition
 Social Security Administration (SSA) • Piloting ACES Digital Signature Certificates for on-line annual wage reporting • Following pilot, SSA had a 90 percent approval by the 100 businesses participating • Automating W-2 submissions critical to agency where nearly 6. 5 million employers submit over 240 million W-2 forms for their employees • Continuing to expand pilot capabilities and implementing digitally signed forms
Social Security Administration (SSA) • Piloting ACES Digital Signature Certificates for on-line annual wage reporting • Following pilot, SSA had a 90 percent approval by the 100 businesses participating • Automating W-2 submissions critical to agency where nearly 6. 5 million employers submit over 240 million W-2 forms for their employees • Continuing to expand pilot capabilities and implementing digitally signed forms
 SSA’s Electronic Medical Evidence Pilots. California • Third party providers submit encrypted Medical Evidence of Record and encrypted and signed Consultative Exams • Using Secure e-Mail • Expanding to include Web based Secure Messaging and Secure FTP SSA/VA • Mississippi requests Medical Evidence from VAMCs in Jackson and Biloxi. VAMCs send encrypted response to DDS via secure e-mail. • Phase I decreased turnaround time from 25 days to 3
SSA’s Electronic Medical Evidence Pilots. California • Third party providers submit encrypted Medical Evidence of Record and encrypted and signed Consultative Exams • Using Secure e-Mail • Expanding to include Web based Secure Messaging and Secure FTP SSA/VA • Mississippi requests Medical Evidence from VAMCs in Jackson and Biloxi. VAMCs send encrypted response to DDS via secure e-mail. • Phase I decreased turnaround time from 25 days to 3
 DEA’s Controlled Substances • Secure electronic transmission of controlled substance prescriptions • Reduces prescription forgeries and medical mistakes • Pharmacists, Medical practitioners, Long Office of Diversion Control May 2001 term care facilities • Pilot program in concert with Veterans Administration (VA) Outpatient Pharmacies • Baltimore Technologies Uni. Cert CA
DEA’s Controlled Substances • Secure electronic transmission of controlled substance prescriptions • Reduces prescription forgeries and medical mistakes • Pharmacists, Medical practitioners, Long Office of Diversion Control May 2001 term care facilities • Pilot program in concert with Veterans Administration (VA) Outpatient Pharmacies • Baltimore Technologies Uni. Cert CA
 In the future, what role does PKI play? • PKI is not the answer for all needs but it can add the required authentication for trustworthy e-gov services • Using PKI technology for strong authentication needs addresses mandates such as HIPPA and e. Sign • Federal bridge CA facilitates unifying islands of automation • e-Authentication initiative will organize authentication needs for critical government business lines
In the future, what role does PKI play? • PKI is not the answer for all needs but it can add the required authentication for trustworthy e-gov services • Using PKI technology for strong authentication needs addresses mandates such as HIPPA and e. Sign • Federal bridge CA facilitates unifying islands of automation • e-Authentication initiative will organize authentication needs for critical government business lines
 Closing Words • The Vision: Enable e-Government through – A cross-governmental, ubiquitous, interoperable Public Key Infrastructure. – The development and use of applications which employ that PKI in support of Agency business processes. • Government-wide initiatives include: – – Federal PKI Policy Authority Federal Bridge Certification Authority Access Certificates for Electronic Services Leveraging other authentication investments where appropriate
Closing Words • The Vision: Enable e-Government through – A cross-governmental, ubiquitous, interoperable Public Key Infrastructure. – The development and use of applications which employ that PKI in support of Agency business processes. • Government-wide initiatives include: – – Federal PKI Policy Authority Federal Bridge Certification Authority Access Certificates for Electronic Services Leveraging other authentication investments where appropriate


