5c18e22c6416e712e7ac419b19e423d5.ppt
- Количество слайдов: 13
 FAA Next Generation Air Transportation System DHS / TSCP Collaboration Enterprise Engineering Services, LLC. Identity and Access Management Discussion William J. Hoffman CISSP, CISO This presentation is my own work. If I used data, ideas, words, diagrams, pictures, or other information from any source, I have cited them. The opinions, conclusions and recommendations expressed or implied are those of the author and do not necessarily reflect the views of the Federal Aviation Administration or the Department of Transportation Federal Aviation Administration 1
FAA Next Generation Air Transportation System DHS / TSCP Collaboration Enterprise Engineering Services, LLC. Identity and Access Management Discussion William J. Hoffman CISSP, CISO This presentation is my own work. If I used data, ideas, words, diagrams, pictures, or other information from any source, I have cited them. The opinions, conclusions and recommendations expressed or implied are those of the author and do not necessarily reflect the views of the Federal Aviation Administration or the Department of Transportation Federal Aviation Administration 1
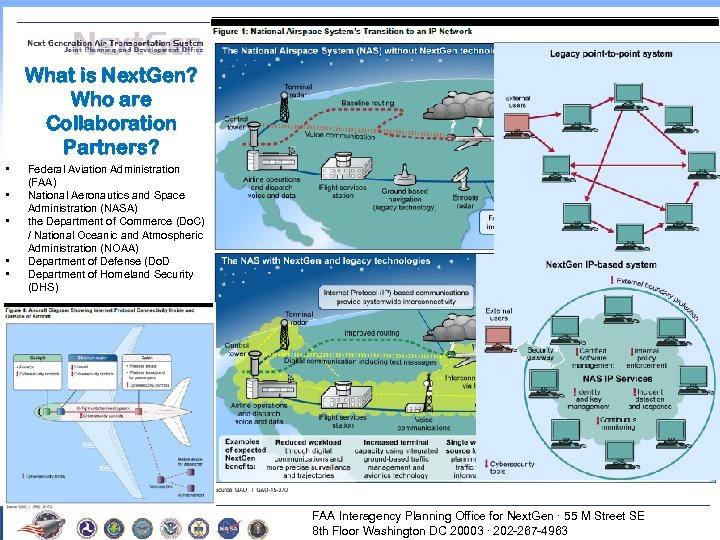 What is Next. Gen? Who are Collaboration Partners? • • • Federal Aviation Administration (FAA) National Aeronautics and Space Administration (NASA) the Department of Commerce (Do. C) / National Oceanic and Atmospheric Administration (NOAA) Department of Defense (Do. D Department of Homeland Security (DHS) FAA Interagency Planning Office Enterprise Engineering Services, LLC. for Next. Gen ∙ 55 M Street SE 8 th Floor Washington DC 20003 ∙ 202 -267 -4963 2
What is Next. Gen? Who are Collaboration Partners? • • • Federal Aviation Administration (FAA) National Aeronautics and Space Administration (NASA) the Department of Commerce (Do. C) / National Oceanic and Atmospheric Administration (NOAA) Department of Defense (Do. D Department of Homeland Security (DHS) FAA Interagency Planning Office Enterprise Engineering Services, LLC. for Next. Gen ∙ 55 M Street SE 8 th Floor Washington DC 20003 ∙ 202 -267 -4963 2
 US, Eurocontrol , ICAO & Cyber Harmonzation Enterprise Engineering Services, LLC. 3
US, Eurocontrol , ICAO & Cyber Harmonzation Enterprise Engineering Services, LLC. 3
 The Aeronautical Information Exchange Model (AIXM) The Flight Information Exchange Model (FIXM) The Weather Information Exchange Model (WXXM) Enterprise Engineering Services, LLC. 4
The Aeronautical Information Exchange Model (AIXM) The Flight Information Exchange Model (FIXM) The Weather Information Exchange Model (WXXM) Enterprise Engineering Services, LLC. 4
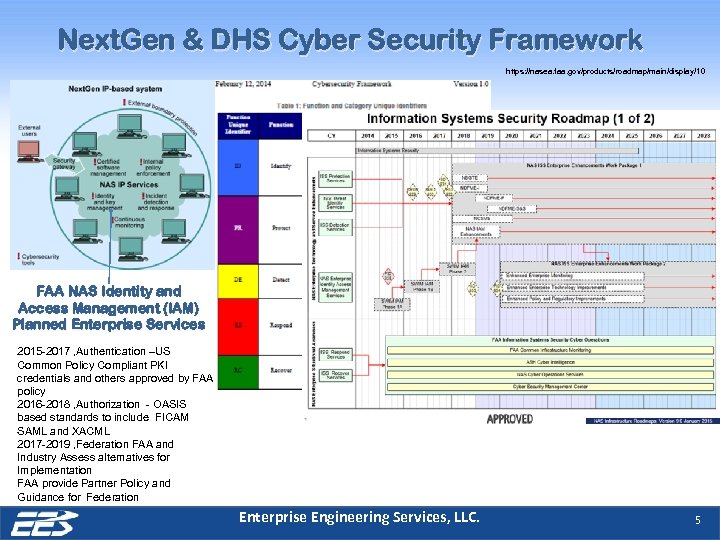 Next. Gen & DHS Cyber Security Framework https: //nasea. faa. gov/products/roadmap/main/display/10 FAA NAS Identity and Access Management (IAM) Planned Enterprise Services 2015 -2017 , Authentication –US Common Policy Compliant PKI credentials and others approved by FAA policy 2016 -2018 , Authorization - OASIS based standards to include FICAM SAML and XACML 2017 -2019 , Federation FAA and Industry Assess alternatives for Implementation FAA provide Partner Policy and Guidance for Federation Enterprise Engineering Services, LLC. 5
Next. Gen & DHS Cyber Security Framework https: //nasea. faa. gov/products/roadmap/main/display/10 FAA NAS Identity and Access Management (IAM) Planned Enterprise Services 2015 -2017 , Authentication –US Common Policy Compliant PKI credentials and others approved by FAA policy 2016 -2018 , Authorization - OASIS based standards to include FICAM SAML and XACML 2017 -2019 , Federation FAA and Industry Assess alternatives for Implementation FAA provide Partner Policy and Guidance for Federation Enterprise Engineering Services, LLC. 5
 Feb 2015 FAA/DHS/TSCP IAM Collaboration Meeting Attendees Jim Daum, FAA Enterprise Safety and Information Security Division Manager John Chung, FAA Information Security Branch Manager Kelly Mesveskas, FAA SWIM Prototype Lead Frank Happel, FAA NAS ISS Engineering Team Manager Jim Laymon, FAA NAS IAM Development and Implementation Team Lead Keith Ward, TSCP Director Philippe Laflandre, Airbus ICAM VP Bill Hoffman, EES Chief Information Security Officer John Daniels, EES Federal Programs VP Overview Keith - proposed Pilot Program plan for FAA to demonstrate IAM technologies Philippe - stressed the value and scope of these investments; as well as need for continued international harmonization Jim Daum - stressed need of identifying FAA requirements related to IAM collaboration efforts Action/Results • Bill Hoffman to collaborate with TSCP to develop Pilot Program to demonstrate TSCP Trust Framework in the Aeronautical Information Management (AIM) domain; particularly the use of a digital credential by AIM stakeholders to access data and/or services. • Keith Ward indicated that TSCP may be able to obtain funding through DHS Science & Technology by submitting white-paper. • TSCP, Airbus, and EES will work together to produce white-paper approach. • FAA will determine viability of AIM Program as target source. Enterprise Engineering Services, LLC. 6
Feb 2015 FAA/DHS/TSCP IAM Collaboration Meeting Attendees Jim Daum, FAA Enterprise Safety and Information Security Division Manager John Chung, FAA Information Security Branch Manager Kelly Mesveskas, FAA SWIM Prototype Lead Frank Happel, FAA NAS ISS Engineering Team Manager Jim Laymon, FAA NAS IAM Development and Implementation Team Lead Keith Ward, TSCP Director Philippe Laflandre, Airbus ICAM VP Bill Hoffman, EES Chief Information Security Officer John Daniels, EES Federal Programs VP Overview Keith - proposed Pilot Program plan for FAA to demonstrate IAM technologies Philippe - stressed the value and scope of these investments; as well as need for continued international harmonization Jim Daum - stressed need of identifying FAA requirements related to IAM collaboration efforts Action/Results • Bill Hoffman to collaborate with TSCP to develop Pilot Program to demonstrate TSCP Trust Framework in the Aeronautical Information Management (AIM) domain; particularly the use of a digital credential by AIM stakeholders to access data and/or services. • Keith Ward indicated that TSCP may be able to obtain funding through DHS Science & Technology by submitting white-paper. • TSCP, Airbus, and EES will work together to produce white-paper approach. • FAA will determine viability of AIM Program as target source. Enterprise Engineering Services, LLC. 6
 Pilot Plan – team with Airport Council International/ North America & use DHS/TSCP framework Team will deliver an operational pilot using a Federated Aviation Information Cloud Service (FAICS) capability in a productionready mode Criteria for Selection of Participating Airport Authorities The proposed pilot calls for 3 Airport authorities to participate that were recommended by Chris Oswalt and Matt Griffin of the Airport Council International, North America at the Next. Gen Federated Identity Credentialing and Access Management (FICAM) Workshop June, 2013 meeting. Recommended participation: • Port Authority of NY and NJ • Denver International Airport • Los Angeles World Airports Authority During discussions with Chris Oswalt, the selection of these 3 was based on: 1. Geographic diversity. 2. Available resources to include very technically competent personnel. 3. All have significant on airport law enforcement personnel, interactions with external Law enforcement and various organizations within DHS and emergency response operations. 4. All have significant interactions with Aviation Military operations functional entities and on airport Military and or Coast Guard Fleet assets. 5. Approximately 40% to 50% of all international flights originate and terminate at airports controlled by them which will help international airport operators buy into this collaboration effort and ACI NA would help bring them on board. 6. PANYNJ and LAWA control the 2 largest General Aviation and Business jet airports in the world (Teterboro and Van Nuys) which will help with future collaboration efforts with AOPA and the Business Jet owners associations. Enterprise Engineering Services, LLC. 7
Pilot Plan – team with Airport Council International/ North America & use DHS/TSCP framework Team will deliver an operational pilot using a Federated Aviation Information Cloud Service (FAICS) capability in a productionready mode Criteria for Selection of Participating Airport Authorities The proposed pilot calls for 3 Airport authorities to participate that were recommended by Chris Oswalt and Matt Griffin of the Airport Council International, North America at the Next. Gen Federated Identity Credentialing and Access Management (FICAM) Workshop June, 2013 meeting. Recommended participation: • Port Authority of NY and NJ • Denver International Airport • Los Angeles World Airports Authority During discussions with Chris Oswalt, the selection of these 3 was based on: 1. Geographic diversity. 2. Available resources to include very technically competent personnel. 3. All have significant on airport law enforcement personnel, interactions with external Law enforcement and various organizations within DHS and emergency response operations. 4. All have significant interactions with Aviation Military operations functional entities and on airport Military and or Coast Guard Fleet assets. 5. Approximately 40% to 50% of all international flights originate and terminate at airports controlled by them which will help international airport operators buy into this collaboration effort and ACI NA would help bring them on board. 6. PANYNJ and LAWA control the 2 largest General Aviation and Business jet airports in the world (Teterboro and Van Nuys) which will help with future collaboration efforts with AOPA and the Business Jet owners associations. Enterprise Engineering Services, LLC. 7
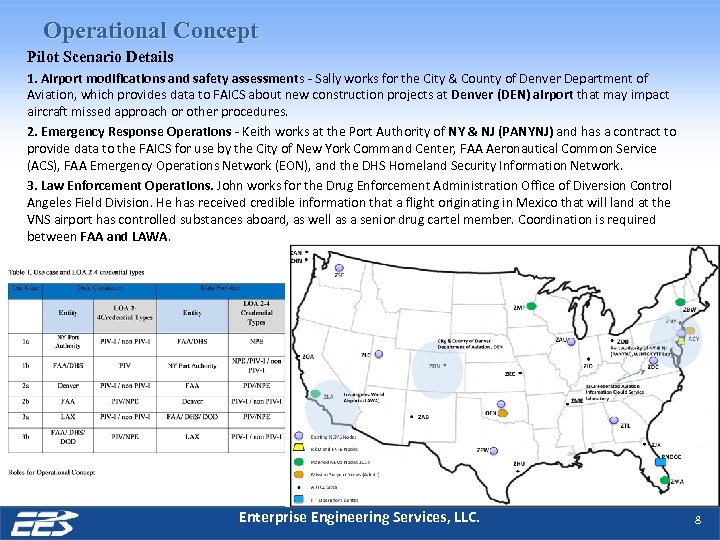 Operational Concept Pilot Scenario Details 1. Airport modifications and safety assessments - Sally works for the City & County of Denver Department of Aviation, which provides data to FAICS about new construction projects at Denver (DEN) airport that may impact aircraft missed approach or other procedures. 2. Emergency Response Operations - Keith works at the Port Authority of NY & NJ (PANYNJ) and has a contract to provide data to the FAICS for use by the City of New York Command Center, FAA Aeronautical Common Service (ACS), FAA Emergency Operations Network (EON), and the DHS Homeland Security Information Network. 3. Law Enforcement Operations. John works for the Drug Enforcement Administration Office of Diversion Control Angeles Field Division. He has received credible information that a flight originating in Mexico that will land at the VNS airport has controlled substances aboard, as well as a senior drug cartel member. Coordination is required between FAA and LAWA. Enterprise Engineering Services, LLC. 8
Operational Concept Pilot Scenario Details 1. Airport modifications and safety assessments - Sally works for the City & County of Denver Department of Aviation, which provides data to FAICS about new construction projects at Denver (DEN) airport that may impact aircraft missed approach or other procedures. 2. Emergency Response Operations - Keith works at the Port Authority of NY & NJ (PANYNJ) and has a contract to provide data to the FAICS for use by the City of New York Command Center, FAA Aeronautical Common Service (ACS), FAA Emergency Operations Network (EON), and the DHS Homeland Security Information Network. 3. Law Enforcement Operations. John works for the Drug Enforcement Administration Office of Diversion Control Angeles Field Division. He has received credible information that a flight originating in Mexico that will land at the VNS airport has controlled substances aboard, as well as a senior drug cartel member. Coordination is required between FAA and LAWA. Enterprise Engineering Services, LLC. 8
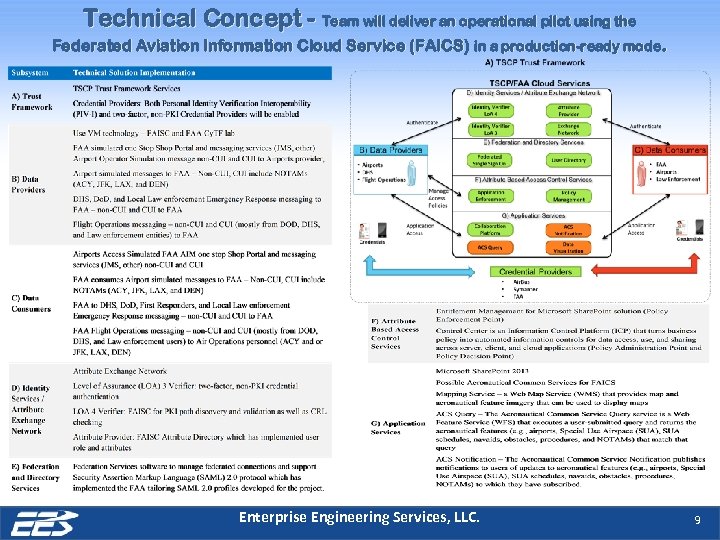 Technical Concept - Team will deliver an operational pilot using the Federated Aviation Information Cloud Service (FAICS) in a production-ready mode. Enterprise Engineering Services, LLC. 9
Technical Concept - Team will deliver an operational pilot using the Federated Aviation Information Cloud Service (FAICS) in a production-ready mode. Enterprise Engineering Services, LLC. 9
 Pilot Goals and Objectives Support Department of Homeland Security’s (DHS) specific mission to develop “advanced cyber security and information assurance solutions to secure the Nation’s current and future cyber and critical infrastructures against persistent threats and dynamic attacks” with particular attention to CSD. 05, Identity Management. DHS S&T help the advancement of FAA IAM initiatives as depicted in the NAS Infrastructure Roadmap. Goals/Objectives 1. Conduct a pilot for FAA’s mission need to perform IAM for its service-oriented architecture – data source provider confidence aviation Controlled Unclassified Information (CUI) data entered into the system will be shared with, and accessible only by, identity-vetted, authorized personnel. (e. g. , civil aviation, space transportation, law enforcement, First Responders, DHS and Do. D stakeholders etc. ) 2. Develop business authorization rules for access control. 3. Create a policy framework (including a trust agreement) to enable data sharing. 4. Test the access management policy framework in a pilot environment with participants from FAA’s critical infrastructure relationships. Use cases will simulate secure access to shared data transported within, and across, aviation systems and subsystems. 5. Leverage and expand the DHS Backend Attribute Exchange (BAE) to enable access control for shared aviation data. 6. Create, validate, and/or update existing TSCP and FAA Security documents and specifications Enterprise Engineering Services, LLC. 10
Pilot Goals and Objectives Support Department of Homeland Security’s (DHS) specific mission to develop “advanced cyber security and information assurance solutions to secure the Nation’s current and future cyber and critical infrastructures against persistent threats and dynamic attacks” with particular attention to CSD. 05, Identity Management. DHS S&T help the advancement of FAA IAM initiatives as depicted in the NAS Infrastructure Roadmap. Goals/Objectives 1. Conduct a pilot for FAA’s mission need to perform IAM for its service-oriented architecture – data source provider confidence aviation Controlled Unclassified Information (CUI) data entered into the system will be shared with, and accessible only by, identity-vetted, authorized personnel. (e. g. , civil aviation, space transportation, law enforcement, First Responders, DHS and Do. D stakeholders etc. ) 2. Develop business authorization rules for access control. 3. Create a policy framework (including a trust agreement) to enable data sharing. 4. Test the access management policy framework in a pilot environment with participants from FAA’s critical infrastructure relationships. Use cases will simulate secure access to shared data transported within, and across, aviation systems and subsystems. 5. Leverage and expand the DHS Backend Attribute Exchange (BAE) to enable access control for shared aviation data. 6. Create, validate, and/or update existing TSCP and FAA Security documents and specifications Enterprise Engineering Services, LLC. 10
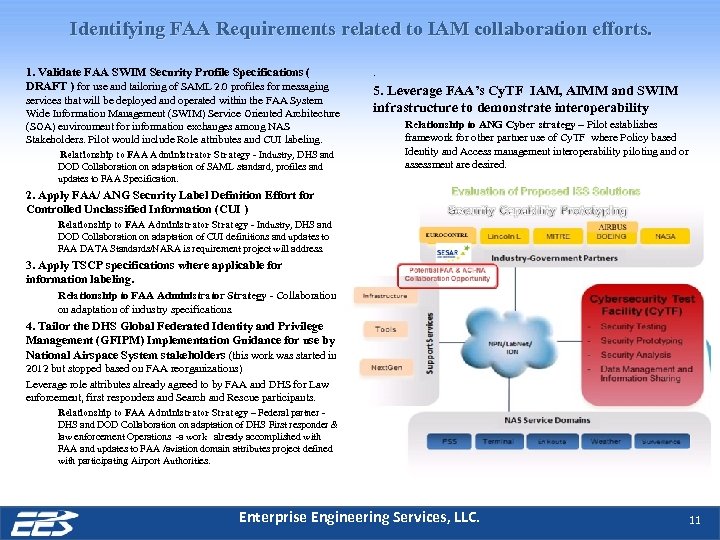 Identifying FAA Requirements related to IAM collaboration efforts. 1. Validate FAA SWIM Security Profile Specifications ( DRAFT ) for use and tailoring of SAML 2. 0 profiles for messaging services that will be deployed and operated within the FAA System Wide Information Management (SWIM) Service Oriented Architecture (SOA) environment for information exchanges among NAS Stakeholders. Pilot would include Role attributes and CUI labeling. Relationship to FAA Administrator Strategy - Industry, DHS and DOD Collaboration on adaptation of SAML standard, profiles and updates to FAA Specification. . 5. Leverage FAA’s Cy. TF IAM, AIMM and SWIM infrastructure to demonstrate interoperability Relationship to ANG Cyber strategy – Pilot establishes framework for other partner use of Cy. TF where Policy based Identity and Access management interoperability piloting and or assessment are desired. 2. Apply FAA/ ANG Security Label Definition Effort for Controlled Unclassified Information (CUI ) Relationship to FAA Administrator Strategy - Industry, DHS and DOD Collaboration on adaptation of CUI definitions and updates to FAA DATA Standards/NARA is requirement project will address. 3. Apply TSCP specifications where applicable for information labeling. Relationship to FAA Administrator Strategy - Collaboration on adaptation of industry specifications. 4. Tailor the DHS Global Federated Identity and Privilege Management (GFIPM) Implementation Guidance for use by National Airspace System stakeholders (this work was started in 2012 but stopped based on FAA reorganizations) Leverage role attributes already agreed to by FAA and DHS for Law enforcement, first responders and Search and Rescue participants. Relationship to FAA Administrator Strategy – Federal partner - DHS and DOD Collaboration on adaptation of DHS First responder & law enforcement Operations -a work already accomplished with FAA and updates to FAA /aviation domain attributes project defined with participating Airport Authorities. Enterprise Engineering Services, LLC. 11
Identifying FAA Requirements related to IAM collaboration efforts. 1. Validate FAA SWIM Security Profile Specifications ( DRAFT ) for use and tailoring of SAML 2. 0 profiles for messaging services that will be deployed and operated within the FAA System Wide Information Management (SWIM) Service Oriented Architecture (SOA) environment for information exchanges among NAS Stakeholders. Pilot would include Role attributes and CUI labeling. Relationship to FAA Administrator Strategy - Industry, DHS and DOD Collaboration on adaptation of SAML standard, profiles and updates to FAA Specification. . 5. Leverage FAA’s Cy. TF IAM, AIMM and SWIM infrastructure to demonstrate interoperability Relationship to ANG Cyber strategy – Pilot establishes framework for other partner use of Cy. TF where Policy based Identity and Access management interoperability piloting and or assessment are desired. 2. Apply FAA/ ANG Security Label Definition Effort for Controlled Unclassified Information (CUI ) Relationship to FAA Administrator Strategy - Industry, DHS and DOD Collaboration on adaptation of CUI definitions and updates to FAA DATA Standards/NARA is requirement project will address. 3. Apply TSCP specifications where applicable for information labeling. Relationship to FAA Administrator Strategy - Collaboration on adaptation of industry specifications. 4. Tailor the DHS Global Federated Identity and Privilege Management (GFIPM) Implementation Guidance for use by National Airspace System stakeholders (this work was started in 2012 but stopped based on FAA reorganizations) Leverage role attributes already agreed to by FAA and DHS for Law enforcement, first responders and Search and Rescue participants. Relationship to FAA Administrator Strategy – Federal partner - DHS and DOD Collaboration on adaptation of DHS First responder & law enforcement Operations -a work already accomplished with FAA and updates to FAA /aviation domain attributes project defined with participating Airport Authorities. Enterprise Engineering Services, LLC. 11
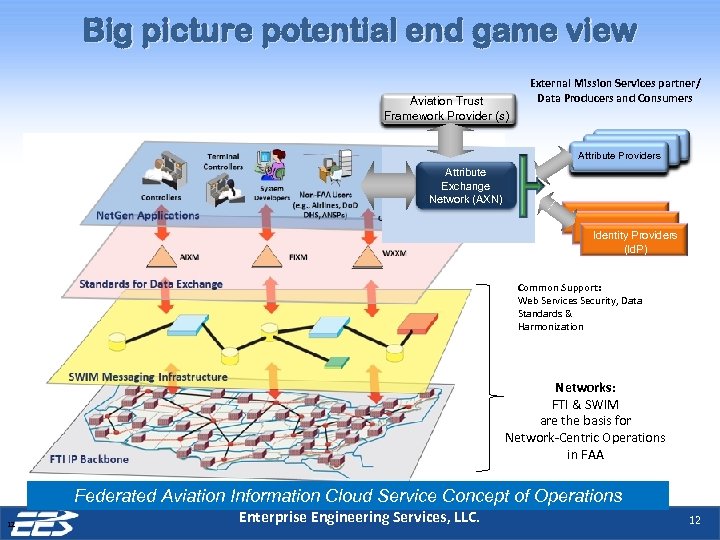 Big picture potential end game view Aviation Trust Framework Provider (s) External Mission Services partner/ Data Producers and Consumers Attribute Providers Attribute Exchange Network (AXN) Identity Providers (Id. P) Common Support: Web Services Security, Data Standards & Harmonization Networks: FTI & SWIM are the basis for Network-Centric Operations in FAA Federated Aviation Information Cloud Service Concept of Operations 12 Enterprise Engineering Services, LLC. 12
Big picture potential end game view Aviation Trust Framework Provider (s) External Mission Services partner/ Data Producers and Consumers Attribute Providers Attribute Exchange Network (AXN) Identity Providers (Id. P) Common Support: Web Services Security, Data Standards & Harmonization Networks: FTI & SWIM are the basis for Network-Centric Operations in FAA Federated Aviation Information Cloud Service Concept of Operations 12 Enterprise Engineering Services, LLC. 12
 Significance Of Pilot Demonstration • Establishment of an environment featuring cross organizational trust through Common Operating Rules – The application owner does not need to issue any new credentials – Reduced costs of credential management – Reuse of existing strong credentials • Automated enforcement of CUI & Intellectual Property Controls – Reduced business risks of data loss or leakage • Allows the setup of a secure collaborative environment – User friendly experience using sign on screens users are familiar with – Rapidly deployable architecture 13 Enterprise Engineering Services, LLC. 13
Significance Of Pilot Demonstration • Establishment of an environment featuring cross organizational trust through Common Operating Rules – The application owner does not need to issue any new credentials – Reduced costs of credential management – Reuse of existing strong credentials • Automated enforcement of CUI & Intellectual Property Controls – Reduced business risks of data loss or leakage • Allows the setup of a secure collaborative environment – User friendly experience using sign on screens users are familiar with – Rapidly deployable architecture 13 Enterprise Engineering Services, LLC. 13


