9a17ca1c326ac572ff6daea025a29d78.ppt
- Количество слайдов: 18
 Extended Validation Models in PKI Alternatives and Implications Marc Branchaud John Linn marcnarc@rsasecurity. com jlinn@rsasecurity. com
Extended Validation Models in PKI Alternatives and Implications Marc Branchaud John Linn marcnarc@rsasecurity. com jlinn@rsasecurity. com
 Overview n n n Existing PKI practices Delegated path processing Cross-domain delegated validation Implications and future directions Conclusions 2
Overview n n n Existing PKI practices Delegated path processing Cross-domain delegated validation Implications and future directions Conclusions 2
 Existing PKI Practice: CRLs n Original assumptions n n n Online, untrusted Directory as repository Intermittent inter-site connectivity Trusted authorities (CAs) kept off-line Path discovery & validation is clientbased, using data from repository and messages Limitations include timeliness, large volumes of data to manage and transport 3
Existing PKI Practice: CRLs n Original assumptions n n n Online, untrusted Directory as repository Intermittent inter-site connectivity Trusted authorities (CAs) kept off-line Path discovery & validation is clientbased, using data from repository and messages Limitations include timeliness, large volumes of data to manage and transport 3
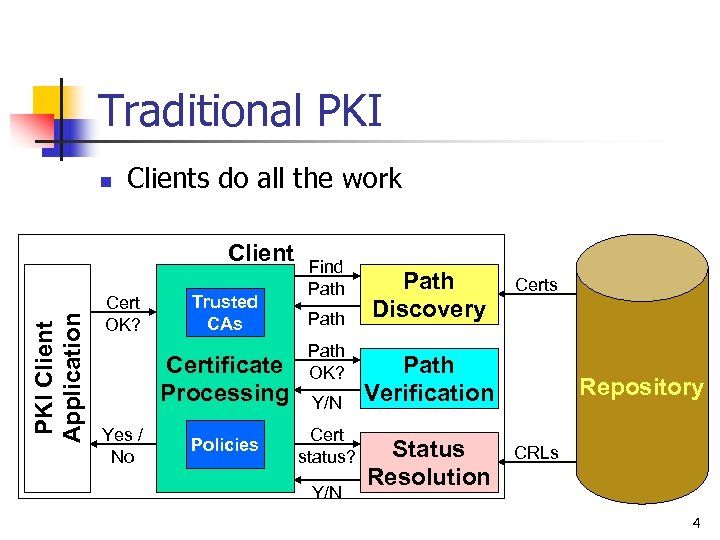 Traditional PKI n Clients do all the work PKI Client Application Client Cert OK? Trusted CAs Certificate Processing Yes / No Policies Find Path OK? Y/N Cert status? Y/N Path Discovery Certs Path Verification Status Resolution Repository CRLs 4
Traditional PKI n Clients do all the work PKI Client Application Client Cert OK? Trusted CAs Certificate Processing Yes / No Policies Find Path OK? Y/N Cert status? Y/N Path Discovery Certs Path Verification Status Resolution Repository CRLs 4
 Existing PKI Practice: OCSP n n OCSP is seeing widespread adoption CAs delegate to OCSP responders that provide signed revocation information n n Designed to enable migration from CRLs Preserves client-based processing model, many semantics Allows improved timeliness Scope constrained to revocation status, not full validation of certificates or paths 5
Existing PKI Practice: OCSP n n OCSP is seeing widespread adoption CAs delegate to OCSP responders that provide signed revocation information n n Designed to enable migration from CRLs Preserves client-based processing model, many semantics Allows improved timeliness Scope constrained to revocation status, not full validation of certificates or paths 5
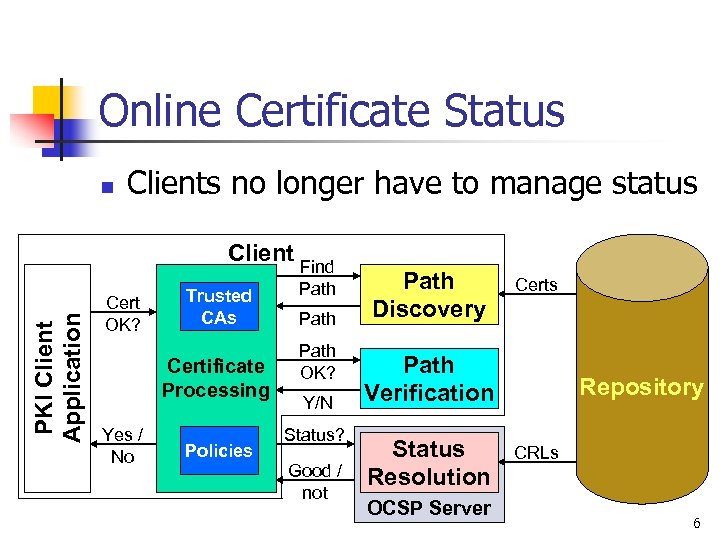 Online Certificate Status n Clients no longer have to manage status PKI Client Application Client Cert OK? Trusted CAs Certificate Processing Yes / No Policies Find Path OK? Y/N Status? Good / not Path Discovery Certs Path Verification Status Resolution OCSP Server Repository CRLs 6
Online Certificate Status n Clients no longer have to manage status PKI Client Application Client Cert OK? Trusted CAs Certificate Processing Yes / No Policies Find Path OK? Y/N Status? Good / not Path Discovery Certs Path Verification Status Resolution OCSP Server Repository CRLs 6
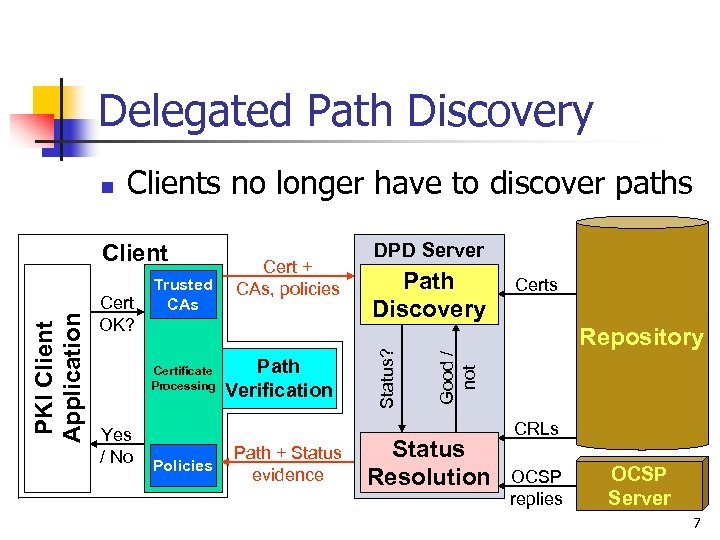 Delegated Path Discovery Clients no longer have to discover paths Cert OK? Trusted CAs Certificate Processing Yes / No Policies Cert + CAs, policies Path Verification Path + Status evidence DPD Server Path Discovery Certs Repository Good / not PKI Client Application Client Status? n Status Resolution CRLs OCSP replies OCSP Server 7
Delegated Path Discovery Clients no longer have to discover paths Cert OK? Trusted CAs Certificate Processing Yes / No Policies Cert + CAs, policies Path Verification Path + Status evidence DPD Server Path Discovery Certs Repository Good / not PKI Client Application Client Status? n Status Resolution CRLs OCSP replies OCSP Server 7
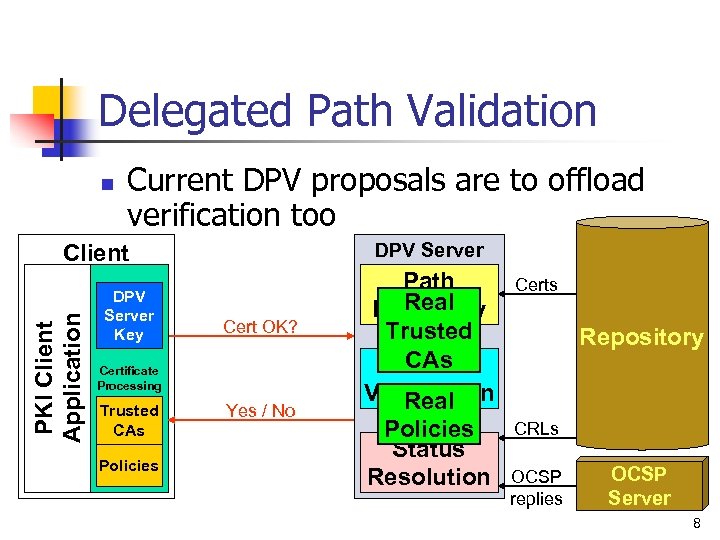 Delegated Path Validation n Current DPV proposals are to offload verification too DPV Server PKI Client Application Client DPV Server Key Cert OK? Certificate Processing Trusted CAs Policies Yes / No Path Real Discovery Trusted CAs Path Verification Real Policies Status Resolution Certs Repository CRLs OCSP replies OCSP Server 8
Delegated Path Validation n Current DPV proposals are to offload verification too DPV Server PKI Client Application Client DPV Server Key Cert OK? Certificate Processing Trusted CAs Policies Yes / No Path Real Discovery Trusted CAs Path Verification Real Policies Status Resolution Certs Repository CRLs OCSP replies OCSP Server 8
 Delegated Path Validation n Advantages of DPV model: n n n Vastly simpler client applications Centralized domain administration Disadvantages of DPV model: n n Online availability & security issues Convenient monitoring point (privacy) 9
Delegated Path Validation n Advantages of DPV model: n n n Vastly simpler client applications Centralized domain administration Disadvantages of DPV model: n n Online availability & security issues Convenient monitoring point (privacy) 9
 Trust and DPV n The DPV server is the trust anchor n n Easier to manage authority compromise The DPV server is the trust dictator n n Clients do not validate the server’s “correctness” Client inputs are merely hints n Still useful for client to identify context 10
Trust and DPV n The DPV server is the trust anchor n n Easier to manage authority compromise The DPV server is the trust dictator n n Clients do not validate the server’s “correctness” Client inputs are merely hints n Still useful for client to identify context 10
 Delegating Trust Across Domain Boundaries n DPV servers consult other domains’ services to build responses to queries n n n Clients rely on their DPV server to select the right sources to validate arbitrary certificates Different DPV servers’ views may differ Validation combines issuer domain information (certificates and status) with RP domain policies 11
Delegating Trust Across Domain Boundaries n DPV servers consult other domains’ services to build responses to queries n n n Clients rely on their DPV server to select the right sources to validate arbitrary certificates Different DPV servers’ views may differ Validation combines issuer domain information (certificates and status) with RP domain policies 11
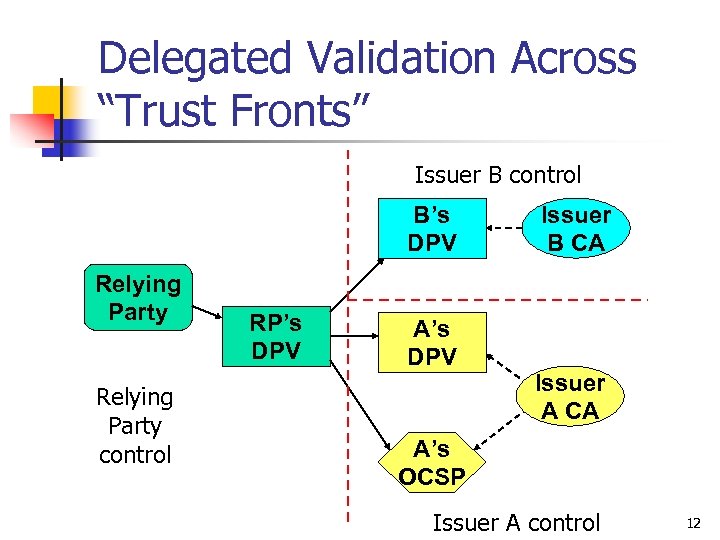 Delegated Validation Across “Trust Fronts” Issuer B control B’s DPV Relying Party control RP’s DPV A’s DPV Issuer B CA Issuer A CA A’s OCSP Issuer A control 12
Delegated Validation Across “Trust Fronts” Issuer B control B’s DPV Relying Party control RP’s DPV A’s DPV Issuer B CA Issuer A CA A’s OCSP Issuer A control 12
 Forms of Delegated Validation n Chained: n n n Referred: n n n Client gets authoritative reply via intermediary Intermediaries on path may be included Clients redirected to authoritative server Responses may be traceable to it Recursive: n n Each server aggregates data and generates its own responses 13 Limited traceability
Forms of Delegated Validation n Chained: n n n Referred: n n n Client gets authoritative reply via intermediary Intermediaries on path may be included Clients redirected to authoritative server Responses may be traceable to it Recursive: n n Each server aggregates data and generates its own responses 13 Limited traceability
 DPV Implications for Cross-Certificates n n Domains can consider inter-domain trust relationships in formulating their DPV responses Fine-grain activation of trust relationships n n n Available only for some clients Available only in some circumstances Like having multiple cross-certificates between domains 14
DPV Implications for Cross-Certificates n n Domains can consider inter-domain trust relationships in formulating their DPV responses Fine-grain activation of trust relationships n n n Available only for some clients Available only in some circumstances Like having multiple cross-certificates between domains 14
 DPV Implications for Revocation n Path construction actively involves intermediate domains Domains can consider status in formulating their responses No need to explicitly query for status n n Status is simply another factor in the availability of certain paths There is no path to a revoked certificate 15
DPV Implications for Revocation n Path construction actively involves intermediate domains Domains can consider status in formulating their responses No need to explicitly query for status n n Status is simply another factor in the availability of certain paths There is no path to a revoked certificate 15
 DPV Implications for Certificates n Queries eventually reach the issuer n n Necessary to obtain certificate status Issuer can assert more than just status n Could respond with individual certificate elements, e. g. : n n n Subject’s DN changes after cert is issued Can return new DN in DPV response Could even return subject’s public key No revocation publishing at all 16
DPV Implications for Certificates n Queries eventually reach the issuer n n Necessary to obtain certificate status Issuer can assert more than just status n Could respond with individual certificate elements, e. g. : n n n Subject’s DN changes after cert is issued Can return new DN in DPV response Could even return subject’s public key No revocation publishing at all 16
 DPV Implications for Certificates n n In the limit, certificates become obsolete Certificate-free PKI: n n n Authorities assign identifiers to entities’ public keys Entities present identifiers instead of certs RPs resolve identifiers to public keys via fully -delegated DPV n n XKMS already supports URLs for keys Active assertions are a new paradigm for PKI – X. 509 didn’t consider them 17
DPV Implications for Certificates n n In the limit, certificates become obsolete Certificate-free PKI: n n n Authorities assign identifiers to entities’ public keys Entities present identifiers instead of certs RPs resolve identifiers to public keys via fully -delegated DPV n n XKMS already supports URLs for keys Active assertions are a new paradigm for PKI – X. 509 didn’t consider them 17
 Conclusions n n Current trend towards simplifying PKI clients challenges basic assumptions Delegating trust & distributing validation creates active authorities and intermediaries n n Introduces new issues: availability, latencies Facilities to constrain trust gain prominence Implications for revocation, certification 18 Caveat adopter!
Conclusions n n Current trend towards simplifying PKI clients challenges basic assumptions Delegating trust & distributing validation creates active authorities and intermediaries n n Introduces new issues: availability, latencies Facilities to constrain trust gain prominence Implications for revocation, certification 18 Caveat adopter!


