d9cfd0a8f269a75d6017c7e373fbfd30.ppt
- Количество слайдов: 14
 Exploiting the User Privacy and Security Concerns with HTTP Cookies Presentation by: Robert Bobek
Exploiting the User Privacy and Security Concerns with HTTP Cookies Presentation by: Robert Bobek
 Introduction What are HTTP Cookies? ◦ We need some understanding of HTTP first! Hypertext Transfer Protocol (HTTP) is the communication protocol used to transfer data on the Internet. ◦ HTTP is a request /reply protocol ◦ Stateless Protocol! Breaks Web Applications! So, what are HTTP Cookies? ◦ Cookies have become and attractive solution to solve this problem ◦ Textual piece of information
Introduction What are HTTP Cookies? ◦ We need some understanding of HTTP first! Hypertext Transfer Protocol (HTTP) is the communication protocol used to transfer data on the Internet. ◦ HTTP is a request /reply protocol ◦ Stateless Protocol! Breaks Web Applications! So, what are HTTP Cookies? ◦ Cookies have become and attractive solution to solve this problem ◦ Textual piece of information
 HTTP Cookies – First Party HTTP Cookies are either First Party or Third Party Web Applications use First-Party Cookies for many purposes ◦ User session tracking ◦ Personalization of profiles ◦ Auto-complete fields
HTTP Cookies – First Party HTTP Cookies are either First Party or Third Party Web Applications use First-Party Cookies for many purposes ◦ User session tracking ◦ Personalization of profiles ◦ Auto-complete fields
 Security Concerns Executing basic attacks on First Party Cookies ◦ Browser history fishing ◦ Cookie theft and data extraction Easily accomplished on ◦ Public terminals ◦ Single user-account OS configurations
Security Concerns Executing basic attacks on First Party Cookies ◦ Browser history fishing ◦ Cookie theft and data extraction Easily accomplished on ◦ Public terminals ◦ Single user-account OS configurations
 Security Concerns Executing Advanced attacks on First Party Cookies ◦ Cookie Theft (packet sniffing) ◦ Cookie Poisoning ◦ Cross-Site Cooking Used to hijack sessions
Security Concerns Executing Advanced attacks on First Party Cookies ◦ Cookie Theft (packet sniffing) ◦ Cookie Poisoning ◦ Cross-Site Cooking Used to hijack sessions
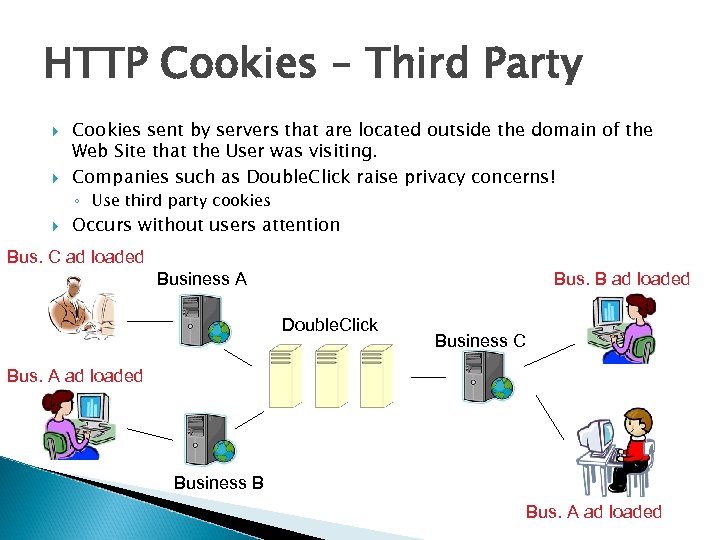 HTTP Cookies – Third Party Cookies sent by servers that are located outside the domain of the Web Site that the User was visiting. Companies such as Double. Click raise privacy concerns! ◦ Use third party cookies Occurs without users attention Bus. C ad loaded Business A Bus. B ad loaded Double. Click Business C Bus. A ad loaded Business B Bus. A ad loaded
HTTP Cookies – Third Party Cookies sent by servers that are located outside the domain of the Web Site that the User was visiting. Companies such as Double. Click raise privacy concerns! ◦ Use third party cookies Occurs without users attention Bus. C ad loaded Business A Bus. B ad loaded Double. Click Business C Bus. A ad loaded Business B Bus. A ad loaded
 Cookies. Card “Mobile Cookies Management on a Smart Card” created by Alvin T. S. Chan ◦ Motivation; General Security and Privacy problems Removing Machine-Cookie dependency Cookies held on Smart Card Technology ◦ Secured by PIN Authentication
Cookies. Card “Mobile Cookies Management on a Smart Card” created by Alvin T. S. Chan ◦ Motivation; General Security and Privacy problems Removing Machine-Cookie dependency Cookies held on Smart Card Technology ◦ Secured by PIN Authentication
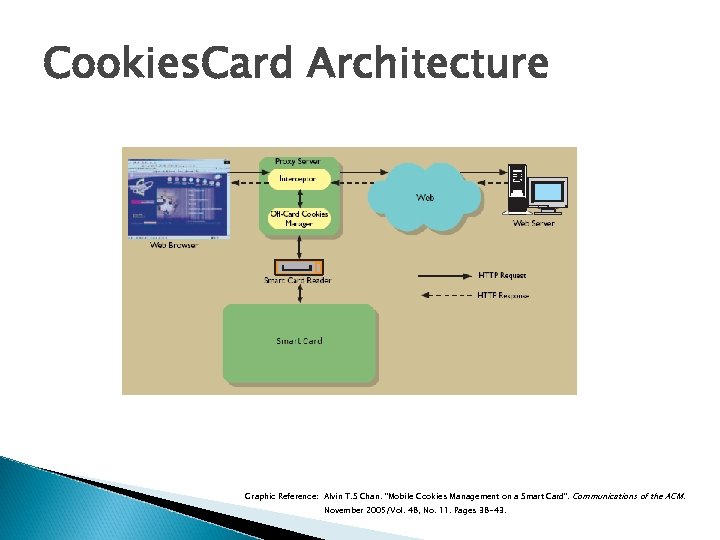 Cookies. Card Architecture Graphic Reference: Alvin T. S Chan. "Mobile Cookies Management on a Smart Card". Communications of the ACM. November 2005/Vol. 48, No. 11. Pages 38 -43.
Cookies. Card Architecture Graphic Reference: Alvin T. S Chan. "Mobile Cookies Management on a Smart Card". Communications of the ACM. November 2005/Vol. 48, No. 11. Pages 38 -43.
 Cookies. Card The Cookies. Card is an effective solution but it is still suffering from minor drawbacks ◦ Smart Readers Technology not very popular ◦ Proxy must reside with the browser ◦ No Cookies Management Interface
Cookies. Card The Cookies. Card is an effective solution but it is still suffering from minor drawbacks ◦ Smart Readers Technology not very popular ◦ Proxy must reside with the browser ◦ No Cookies Management Interface
 Cookies. Card 1. 1 The Cookies. Card can be improved using the following suggestions ◦ Replace Smart Card Technology with USB Flash devices Affordable Popular Ultra-portable ◦ Running Proxy Server from USB Flash device Localhost left untouched ◦ Control Panel Interface created as a 3 rd module Can be accessed through another listening port
Cookies. Card 1. 1 The Cookies. Card can be improved using the following suggestions ◦ Replace Smart Card Technology with USB Flash devices Affordable Popular Ultra-portable ◦ Running Proxy Server from USB Flash device Localhost left untouched ◦ Control Panel Interface created as a 3 rd module Can be accessed through another listening port
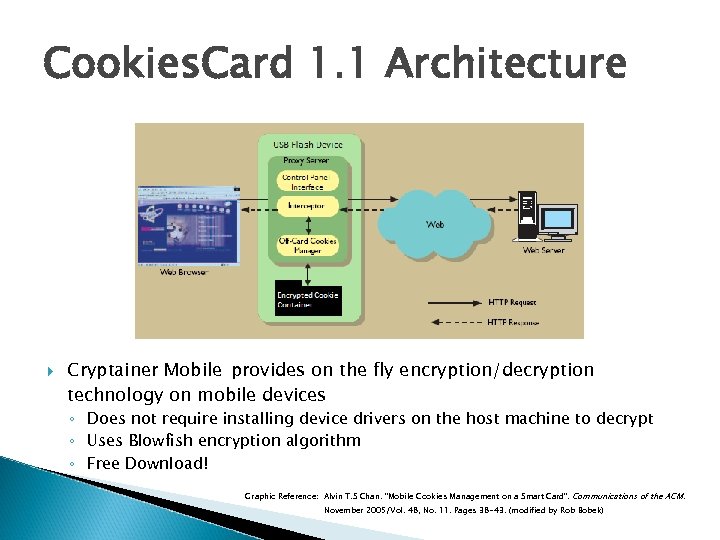 Cookies. Card 1. 1 Architecture Cryptainer Mobile provides on the fly encryption/decryption technology on mobile devices ◦ Does not require installing device drivers on the host machine to decrypt ◦ Uses Blowfish encryption algorithm ◦ Free Download! Graphic Reference: Alvin T. S Chan. "Mobile Cookies Management on a Smart Card". Communications of the ACM. November 2005/Vol. 48, No. 11. Pages 38 -43. (modified by Rob Bobek)
Cookies. Card 1. 1 Architecture Cryptainer Mobile provides on the fly encryption/decryption technology on mobile devices ◦ Does not require installing device drivers on the host machine to decrypt ◦ Uses Blowfish encryption algorithm ◦ Free Download! Graphic Reference: Alvin T. S Chan. "Mobile Cookies Management on a Smart Card". Communications of the ACM. November 2005/Vol. 48, No. 11. Pages 38 -43. (modified by Rob Bobek)
 Conclusion Cookies. Card 1. 1 better but not perfect!
Conclusion Cookies. Card 1. 1 better but not perfect!
 References David M. Kristol. "HTTP Cookies: Standards, Privacy, and Politics". ACM Transactions on Internet Technology. November 2001/Vol. 1, No. 2. Pages 151 -198. Alvin T. S Chan. "Mobile Cookies Management on a Smart Card". Communications of the ACM. November 2005/Vol. 48, No. 11. Pages 38 -43. The Cookie Controversy – Cookies and Internet Privacy. Wikipedia on HTTP Cookie. Central Cryptainer Mobile can be downloaded at http: //www. cookiecentral. com/ccstory/cc 3. htm http: //en. wikipedia. org/wiki/HTTP_cookie#Drawbacks_of_cookies http: //www. cookiecentral. com http: //www. cypherix. com/cryptainerle/
References David M. Kristol. "HTTP Cookies: Standards, Privacy, and Politics". ACM Transactions on Internet Technology. November 2001/Vol. 1, No. 2. Pages 151 -198. Alvin T. S Chan. "Mobile Cookies Management on a Smart Card". Communications of the ACM. November 2005/Vol. 48, No. 11. Pages 38 -43. The Cookie Controversy – Cookies and Internet Privacy. Wikipedia on HTTP Cookie. Central Cryptainer Mobile can be downloaded at http: //www. cookiecentral. com/ccstory/cc 3. htm http: //en. wikipedia. org/wiki/HTTP_cookie#Drawbacks_of_cookies http: //www. cookiecentral. com http: //www. cypherix. com/cryptainerle/
 Questions?
Questions?


