ed2a279f956ded3d15bc8b3e4ea67e1a.ppt
- Количество слайдов: 37
 Experience with Tripwire: Using Integrity Checkers for Intrusion Detection by Gene H. Kim and Eugene H. Spafford 10/06
Experience with Tripwire: Using Integrity Checkers for Intrusion Detection by Gene H. Kim and Eugene H. Spafford 10/06
 Presentation Outline n n 10/06 Motivation for Tripwire design Experiences Conclusion
Presentation Outline n n 10/06 Motivation for Tripwire design Experiences Conclusion
 Motivation - A Scary Story n n Ellen is system admin for large network Ellen realizes someone has logged on as root on several machines Sneaky intruder deleted all accounting & auditing files before logging out Ellen’s concern: – Did intruder leave a backdoor (for re-entry)? – Was sensitive information compromised? 10/06
Motivation - A Scary Story n n Ellen is system admin for large network Ellen realizes someone has logged on as root on several machines Sneaky intruder deleted all accounting & auditing files before logging out Ellen’s concern: – Did intruder leave a backdoor (for re-entry)? – Was sensitive information compromised? 10/06
 Security Policy - Integrity of Data n n 10/06 Assure that file data (in permanent storage) are not altered except by those authorized to do so More precisely, assure that if a file is altered improperly, that the alteration can be detected
Security Policy - Integrity of Data n n 10/06 Assure that file data (in permanent storage) are not altered except by those authorized to do so More precisely, assure that if a file is altered improperly, that the alteration can be detected
 Tripwire n n Gives system admins ability to monitor for added, deleted & modified files Checks for changes in file attributes, e. g. : – size, – access & modification timestamps, – permissions, – inode number – signature (more on signature later) 10/06
Tripwire n n Gives system admins ability to monitor for added, deleted & modified files Checks for changes in file attributes, e. g. : – size, – access & modification timestamps, – permissions, – inode number – signature (more on signature later) 10/06
 Ellen’s Challenge n n n 10/06 How does Ellen determine which (if any!) files have been altered w/o authorization? Tens of thousands of files in dozens of gigabytes of disk on dozens of different architectures Ellen needs to examine every file as well as check for deleted or added files
Ellen’s Challenge n n n 10/06 How does Ellen determine which (if any!) files have been altered w/o authorization? Tens of thousands of files in dozens of gigabytes of disk on dozens of different architectures Ellen needs to examine every file as well as check for deleted or added files
 Checking Techniques n n 10/06 Established techniques: maintaining checklists, comparison copies, checksum records or backup tapes These methods are costly, prone to error and susceptible to easy spoofing Intruders w/ root privileges can alter checklists or compromise utilities (eg “ls” Changes to a file can be made w/out changing its length or checksum!
Checking Techniques n n 10/06 Established techniques: maintaining checklists, comparison copies, checksum records or backup tapes These methods are costly, prone to error and susceptible to easy spoofing Intruders w/ root privileges can alter checklists or compromise utilities (eg “ls” Changes to a file can be made w/out changing its length or checksum!
 Define Integrity of File Data n n 10/06 Can we define a notion of the integrity of both data and the file structure (including directories) in which that data is stored? Define it as a set of characteristics Monitor change of those characteristics Tripwire system is said to “enforce the integrity of file system” if unauthorized change to characteristics is detected
Define Integrity of File Data n n 10/06 Can we define a notion of the integrity of both data and the file structure (including directories) in which that data is stored? Define it as a set of characteristics Monitor change of those characteristics Tripwire system is said to “enforce the integrity of file system” if unauthorized change to characteristics is detected
 The Ideal Integrity Checker. . . n n 10/06 High level of automation Simple description of attributes of the file system that are monitored/checked Easy way to update database used to control monitoring - small changes shouldn’t require massive regeneration Automate regular checks (use UNIX scheduler, cron); allow manual checks
The Ideal Integrity Checker. . . n n 10/06 High level of automation Simple description of attributes of the file system that are monitored/checked Easy way to update database used to control monitoring - small changes shouldn’t require massive regeneration Automate regular checks (use UNIX scheduler, cron); allow manual checks
 Ideal Integrity Checker cont. n n n 10/06 Generate output that’s easy to scan Allow specification of file system “exceptions” that are NOT reported Allow reuse and sharing of configuration files (for networks of lots of machines that differ only slightly)
Ideal Integrity Checker cont. n n n 10/06 Generate output that’s easy to scan Allow specification of file system “exceptions” that are NOT reported Allow reuse and sharing of configuration files (for networks of lots of machines that differ only slightly)
 Tripwire Program Inputs n Configuration file (tw. config) – list of files & directories to be monitored – their associated selection mask (list attributes that can safely be ignored) n Database file --describes each “file” – automatically generated – set of file names, inode attribute values, signature info. , associated tw. config entry 10/06
Tripwire Program Inputs n Configuration file (tw. config) – list of files & directories to be monitored – their associated selection mask (list attributes that can safely be ignored) n Database file --describes each “file” – automatically generated – set of file names, inode attribute values, signature info. , associated tw. config entry 10/06
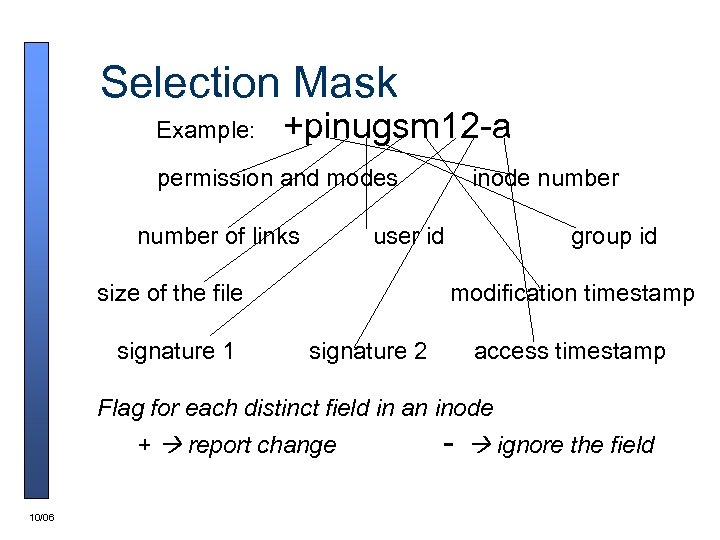 Selection Mask Example: +pinugsm 12 -a permission and modes number of links user id size of the file signature 1 inode number group id modification timestamp signature 2 access timestamp Flag for each distinct field in an inode + report change 10/06 - ignore the field
Selection Mask Example: +pinugsm 12 -a permission and modes number of links user id size of the file signature 1 inode number group id modification timestamp signature 2 access timestamp Flag for each distinct field in an inode + report change 10/06 - ignore the field
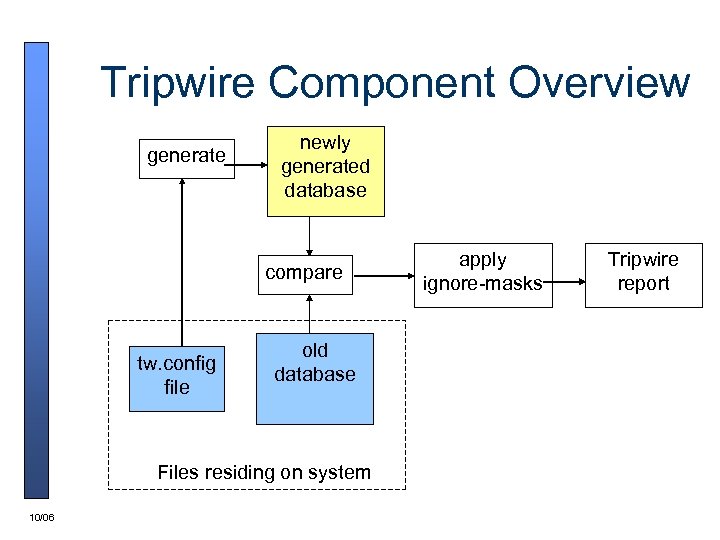 Tripwire Component Overview generate newly generated database compare tw. config file old database Files residing on system 10/06 apply ignore-masks Tripwire report
Tripwire Component Overview generate newly generated database compare tw. config file old database Files residing on system 10/06 apply ignore-masks Tripwire report
 Database Initialization Mode n n Tripwire generates baseline database file based on tw. config indicates – files to monitor – files to ignore (e. g. no recursion below directory with name “DDD”) – whether to ignore file size change (e. g. ignore increase in log files, but report decrease!!!) 10/06
Database Initialization Mode n n Tripwire generates baseline database file based on tw. config indicates – files to monitor – files to ignore (e. g. no recursion below directory with name “DDD”) – whether to ignore file size change (e. g. ignore increase in log files, but report decrease!!!) 10/06
 Integrity Checking Mode n n 10/06 Generate new database Compare new database with baseline db Produce report of added & deleted files Apply selection mask to modified files
Integrity Checking Mode n n 10/06 Generate new database Compare new database with baseline db Produce report of added & deleted files Apply selection mask to modified files
 Signature Support n n n For each file – up to 10 signatures What’s a signature? Any pattern that “represents” the file – By default, MD 5 and Snefru signatures are recorded and checked for each file 10/06
Signature Support n n n For each file – up to 10 signatures What’s a signature? Any pattern that “represents” the file – By default, MD 5 and Snefru signatures are recorded and checked for each file 10/06
 Supported Platforms n n n n 10/06 Windows NT, version 4. 0 Solaris (SPARC), versions 2. 6, 7. 0 Solaris (Intel), version 2. 6, 7. 0 HP-UX, versions 10. 20, 11. 00 IBM AIX, versions 4. 2, 4. 3 SGI Irix, version 6. 5 Compaq TRU 64 UNIX, version 4. 0 Linux
Supported Platforms n n n n 10/06 Windows NT, version 4. 0 Solaris (SPARC), versions 2. 6, 7. 0 Solaris (Intel), version 2. 6, 7. 0 HP-UX, versions 10. 20, 11. 00 IBM AIX, versions 4. 2, 4. 3 SGI Irix, version 6. 5 Compaq TRU 64 UNIX, version 4. 0 Linux
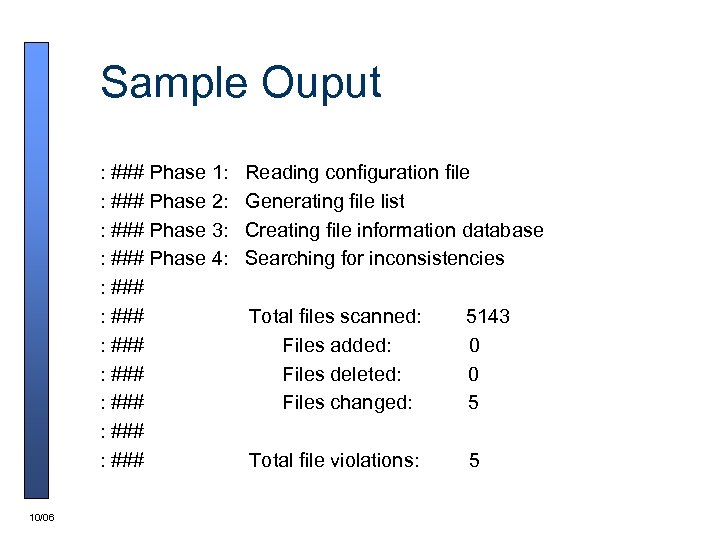 Sample Ouput : ### Phase 1: : ### Phase 2: : ### Phase 3: : ### Phase 4: : ### : ### 10/06 Reading configuration file Generating file list Creating file information database Searching for inconsistencies Total files scanned: Files added: Files deleted: Files changed: 5143 0 0 5 Total file violations: 5
Sample Ouput : ### Phase 1: : ### Phase 2: : ### Phase 3: : ### Phase 4: : ### : ### 10/06 Reading configuration file Generating file list Creating file information database Searching for inconsistencies Total files scanned: Files added: Files deleted: Files changed: 5143 0 0 5 Total file violations: 5
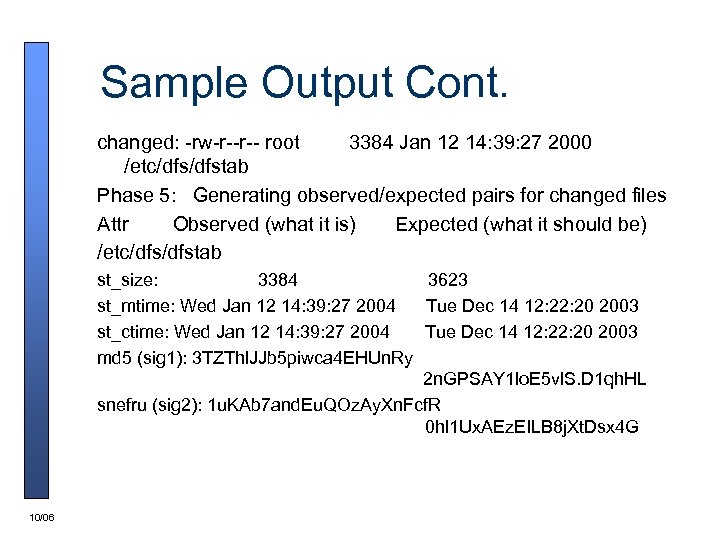 Sample Output Cont. changed: -rw-r--r-- root 3384 Jan 12 14: 39: 27 2000 /etc/dfstab Phase 5: Generating observed/expected pairs for changed files Attr Observed (what it is) Expected (what it should be) /etc/dfstab st_size: 3384 3623 st_mtime: Wed Jan 12 14: 39: 27 2004 Tue Dec 14 12: 20 2003 st_ctime: Wed Jan 12 14: 39: 27 2004 Tue Dec 14 12: 20 2003 md 5 (sig 1): 3 TZThl. JJb 5 piwca 4 EHUn. Ry 2 n. GPSAY 1 lo. E 5 vl. S. D 1 qh. HL snefru (sig 2): 1 u. KAb 7 and. Eu. QOz. Ay. Xn. Fcf. R 0 hl 1 Ux. AEz. EILB 8 j. Xt. Dsx 4 G 10/06
Sample Output Cont. changed: -rw-r--r-- root 3384 Jan 12 14: 39: 27 2000 /etc/dfstab Phase 5: Generating observed/expected pairs for changed files Attr Observed (what it is) Expected (what it should be) /etc/dfstab st_size: 3384 3623 st_mtime: Wed Jan 12 14: 39: 27 2004 Tue Dec 14 12: 20 2003 st_ctime: Wed Jan 12 14: 39: 27 2004 Tue Dec 14 12: 20 2003 md 5 (sig 1): 3 TZThl. JJb 5 piwca 4 EHUn. Ry 2 n. GPSAY 1 lo. E 5 vl. S. D 1 qh. HL snefru (sig 2): 1 u. KAb 7 and. Eu. QOz. Ay. Xn. Fcf. R 0 hl 1 Ux. AEz. EILB 8 j. Xt. Dsx 4 G 10/06
 Conclusion n n 10/06 Portable Self-contained Adaptable to large and small sites Very restricted in what it sees -- only OS attribute changes of files It has no clue as to what users are actually doing!
Conclusion n n 10/06 Portable Self-contained Adaptable to large and small sites Very restricted in what it sees -- only OS attribute changes of files It has no clue as to what users are actually doing!
 The End 10/06
The End 10/06
 Templates – read-only files: Only the access timestamp is ignored. – log files: Changes to the file size, access and modification timestamp, and signatures are ignored. – growing log files: Same flags as log files except increasing files sizes are ignored. – ignore nothing – ignore everything 10/06
Templates – read-only files: Only the access timestamp is ignored. – log files: Changes to the file size, access and modification timestamp, and signatures are ignored. – growing log files: Same flags as log files except increasing files sizes are ignored. – ignore nothing – ignore everything 10/06
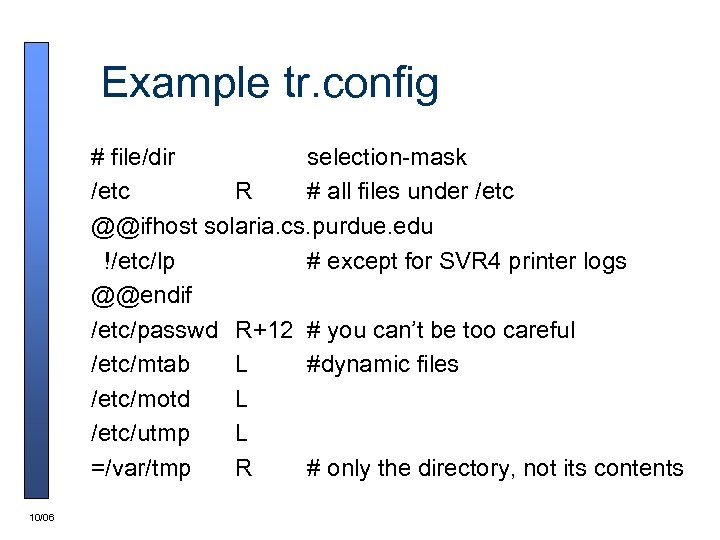 Example tr. config # file/dir selection-mask /etc R # all files under /etc @@ifhost solaria. cs. purdue. edu !/etc/lp # except for SVR 4 printer logs @@endif /etc/passwd R+12 # you can’t be too careful /etc/mtab L #dynamic files /etc/motd L /etc/utmp L =/var/tmp R # only the directory, not its contents 10/06
Example tr. config # file/dir selection-mask /etc R # all files under /etc @@ifhost solaria. cs. purdue. edu !/etc/lp # except for SVR 4 printer logs @@endif /etc/passwd R+12 # you can’t be too careful /etc/mtab L #dynamic files /etc/motd L /etc/utmp L =/var/tmp R # only the directory, not its contents 10/06
 You use Tripwire for what? n n 10/06 Many system admin. use Tripwire as a tool to enforce local policy - changes by one system admin. is noticed quickly by others Tripwire helps salvage file systems not completely repaired by fsck - program that ensures consistency between file data and their inodes – a file can be rebound to its original name by searching the database for a matching signature
You use Tripwire for what? n n 10/06 Many system admin. use Tripwire as a tool to enforce local policy - changes by one system admin. is noticed quickly by others Tripwire helps salvage file systems not completely repaired by fsck - program that ensures consistency between file data and their inodes – a file can be rebound to its original name by searching the database for a matching signature
 Stealth-Tripwire n n 10/06 Several system admins. have tried very hard to conceal their use of Tripwire and don’t run it through programs like cron Authors disagree - advertising the use of Tripwire (even if not true) could help avert attacks
Stealth-Tripwire n n 10/06 Several system admins. have tried very hard to conceal their use of Tripwire and don’t run it through programs like cron Authors disagree - advertising the use of Tripwire (even if not true) could help avert attacks
 Paranoia n n n 10/06 Tripwire is designed to run on a regular basis, such as daily Two reported cases of Tripwire being run hourly - not a good idea Good paranoia - “plant” files on the system, such as master-passwords prime targets for intruders
Paranoia n n n 10/06 Tripwire is designed to run on a regular basis, such as daily Two reported cases of Tripwire being run hourly - not a good idea Good paranoia - “plant” files on the system, such as master-passwords prime targets for intruders
 Portability n n 10/06 Tripwire reported to be running on 28 different UNIX platforms Only 8 example tw. config files necessary Authors receive requests to help system admins. compile Tripwire on machines they have never heard of - such as one only sold in Australia that came with incorrect system libraries Often, a group of system admins. with similarly “orphaned” machines will put
Portability n n 10/06 Tripwire reported to be running on 28 different UNIX platforms Only 8 example tw. config files necessary Authors receive requests to help system admins. compile Tripwire on machines they have never heard of - such as one only sold in Australia that came with incorrect system libraries Often, a group of system admins. with similarly “orphaned” machines will put
 You Added WHAT to Tripwire? n 10/06 Authors received a report from a user who is adding support for Intel machines running UNIX to allow Tripwire to check mounted MSDOS file systems
You Added WHAT to Tripwire? n 10/06 Authors received a report from a user who is adding support for Intel machines running UNIX to allow Tripwire to check mounted MSDOS file systems
 Mega & Micro - Tripwire n n 10/06 Many system administrators of large sites create one configuration file to be shared by all machines, using the @@ifhost directive to segregate noncommon file groups A configuration file consisting solely of “/” has proved adequate for some system administrators of smaller sites
Mega & Micro - Tripwire n n 10/06 Many system administrators of large sites create one configuration file to be shared by all machines, using the @@ifhost directive to segregate noncommon file groups A configuration file consisting solely of “/” has proved adequate for some system administrators of smaller sites
 CS Dept. & Tripwire n n 10/06 Tripwire runs on all essential servers every night Scripts were written to run Tripwire on all the various servers, gather the results, and send them by email to the system admins. Very usable out-of-the-box, took a staff member only 10 hours to set up Installed for 9 months - haven’t seen anything suspicious, Paco occasionally
CS Dept. & Tripwire n n 10/06 Tripwire runs on all essential servers every night Scripts were written to run Tripwire on all the various servers, gather the results, and send them by email to the system admins. Very usable out-of-the-box, took a staff member only 10 hours to set up Installed for 9 months - haven’t seen anything suspicious, Paco occasionally
 Interactive Database Update n n 10/06 Tripwire generates list of all changes (ala integrity checking mode) Tripwire asks system admin. to specify which entries to update in the database file
Interactive Database Update n n 10/06 Tripwire generates list of all changes (ala integrity checking mode) Tripwire asks system admin. to specify which entries to update in the database file
 Database Update Mode n n 10/06 Tripwire regenerates database entries for a list of files or configuration entries given on the command line Tripwire instructs system admin to move new database to secure media
Database Update Mode n n 10/06 Tripwire regenerates database entries for a list of files or configuration entries given on the command line Tripwire instructs system admin to move new database to secure media
 Configurability Aids n Preprocessor support allows system admin. to write configuration files that support numerous configurations of machines – Note: Machines that share a configuration file still generate their own database files n 10/06 Prefixes to the tw. config allow for pruning - a directory and/or its contents can be excluded from monitoring
Configurability Aids n Preprocessor support allows system admin. to write configuration files that support numerous configurations of machines – Note: Machines that share a configuration file still generate their own database files n 10/06 Prefixes to the tw. config allow for pruning - a directory and/or its contents can be excluded from monitoring
 Configurability Aids (Cont. ) n Example selection mask: +pinugsm 12 -a – “Report changes in permission and modes, inode number, number of links, user id, group id, size of the file, modification timestamp, and signatures 1 and 2. Disregard changes to access timestamp. ” n 10/06 Templates allow system admin. to quickly classify files into categories that use common sets of flags
Configurability Aids (Cont. ) n Example selection mask: +pinugsm 12 -a – “Report changes in permission and modes, inode number, number of links, user id, group id, size of the file, modification timestamp, and signatures 1 and 2. Disregard changes to access timestamp. ” n 10/06 Templates allow system admin. to quickly classify files into categories that use common sets of flags
 Good News n n n 10/06 Seven reported cases of Tripwire alerting system administrators to intruders Dozens of cases of Tripwire being used as a system admin. enforcement tool One reported case of Tripwire detecting a failing disk
Good News n n n 10/06 Seven reported cases of Tripwire alerting system administrators to intruders Dozens of cases of Tripwire being used as a system admin. enforcement tool One reported case of Tripwire detecting a failing disk
 Where are the Bad Guys? n Out of thousands of machines running Tripwire, why only 7 Tripwire-discovered breakins in two years? – Intruders have given up? Don’t you wish! – Sites running Tripwire aren’t interesting? Nope – Site admins aren’t telling? Maybe – Tripwire sites are more security-conscious? Maybe 10/06
Where are the Bad Guys? n Out of thousands of machines running Tripwire, why only 7 Tripwire-discovered breakins in two years? – Intruders have given up? Don’t you wish! – Sites running Tripwire aren’t interesting? Nope – Site admins aren’t telling? Maybe – Tripwire sites are more security-conscious? Maybe 10/06
 Bad Guys (Cont. ) n Sites have already been attacked – maybe baseline databases are being generated on machines that have already been compromised n Intruders have completely subverted integrity checking schemes – it would be very hard for an intruder to alter a file in a way that it preserves its original signature 10/06
Bad Guys (Cont. ) n Sites have already been attacked – maybe baseline databases are being generated on machines that have already been compromised n Intruders have completely subverted integrity checking schemes – it would be very hard for an intruder to alter a file in a way that it preserves its original signature 10/06


