701d26e938dd99e9e4a7ec386bd6d77b.ppt
- Количество слайдов: 27
 Evolving Counterfeit Component Threats and Industry Mitigation Efforts Stephen Schoppe Glenn Robertson Process Sciences, Inc. Leander, Texas 512. 259. 7070 www. process-sciences. com
Evolving Counterfeit Component Threats and Industry Mitigation Efforts Stephen Schoppe Glenn Robertson Process Sciences, Inc. Leander, Texas 512. 259. 7070 www. process-sciences. com
 Introduction n n A growing problem in all industry sectors Openings for counterfeiting • • • n High price components High demand/scarcity Obsolete/out of production Potential for introducing malicious code • Sabotage – immediate or future • Potential espionage
Introduction n n A growing problem in all industry sectors Openings for counterfeiting • • • n High price components High demand/scarcity Obsolete/out of production Potential for introducing malicious code • Sabotage – immediate or future • Potential espionage
 Introduction n How do counterfeits enter the supply chain? • Often starts with remarking of reclaim/e. Waste n n n • • Refurbished used part represented as new Altered date code Consumer grade marked as mil Upgrade to later/preferred/scarce part type Low-grade passives marked as precision value (low tolerance) type Completely different part Manufacturing defects diverted from scrap bin Surplus production from OEM (“ 4 th shift”) Acquisitions/Purchase of surplus inventories Return of mixed inventories to distributor
Introduction n How do counterfeits enter the supply chain? • Often starts with remarking of reclaim/e. Waste n n n • • Refurbished used part represented as new Altered date code Consumer grade marked as mil Upgrade to later/preferred/scarce part type Low-grade passives marked as precision value (low tolerance) type Completely different part Manufacturing defects diverted from scrap bin Surplus production from OEM (“ 4 th shift”) Acquisitions/Purchase of surplus inventories Return of mixed inventories to distributor
 Mitigation Strategies - Users n n Essential to establish Due Diligence Establish supply chain policies • • Evaluate risks from “lowest bidder” Use authorized distributors where possible Write purchase contract carefully Supplier Qualification n n n History with reporting organizations - BBB, D&B, etc. Google search, including street view of address Memberships – ERAI, GIDEP, IDEA etc. Certifications - ISO, IDEA-1010, CCAP-101, etc. Quality systems for receiving inspection, ESD, etc. Onsite audit if possible
Mitigation Strategies - Users n n Essential to establish Due Diligence Establish supply chain policies • • Evaluate risks from “lowest bidder” Use authorized distributors where possible Write purchase contract carefully Supplier Qualification n n n History with reporting organizations - BBB, D&B, etc. Google search, including street view of address Memberships – ERAI, GIDEP, IDEA etc. Certifications - ISO, IDEA-1010, CCAP-101, etc. Quality systems for receiving inspection, ESD, etc. Onsite audit if possible
 Mitigation Strategies - Users n n n Access to industry database(s) Decision process for authentication testing and quarantine/reporting of suspect parts Disposition • Don’t just return to distributor inventory • Destroy & verify? n Staff training/qualification
Mitigation Strategies - Users n n n Access to industry database(s) Decision process for authentication testing and quarantine/reporting of suspect parts Disposition • Don’t just return to distributor inventory • Destroy & verify? n Staff training/qualification
 Mitigation Strategies - Distributors n Anti-Counterfeit Policies • • n n Increased scrutiny of sources Awareness of evolving counterfeiting methods Use of industry resources – ERAI, GIDEP, IDEA Establish incoming inspection procedures Authentication testing – in house or outsource Staff training/qualification
Mitigation Strategies - Distributors n Anti-Counterfeit Policies • • n n Increased scrutiny of sources Awareness of evolving counterfeiting methods Use of industry resources – ERAI, GIDEP, IDEA Establish incoming inspection procedures Authentication testing – in house or outsource Staff training/qualification
 Industry Mitigation Efforts n Counterfeits Databases • Searchable databases of suspect components n n Information from reports submitted online Only members can access, anyone can submit report • GIDEP (www. gidep. org) n Operated by US Government, established 1959 • ERAI (www. erai. com) n n Privately held reporting and investigation service Escrow and dispute resolution services • IDEA (www. idofea. org) n n Privately held association Maintains extensive Membership Code of Ethics
Industry Mitigation Efforts n Counterfeits Databases • Searchable databases of suspect components n n Information from reports submitted online Only members can access, anyone can submit report • GIDEP (www. gidep. org) n Operated by US Government, established 1959 • ERAI (www. erai. com) n n Privately held reporting and investigation service Escrow and dispute resolution services • IDEA (www. idofea. org) n n Privately held association Maintains extensive Membership Code of Ethics
 Industry Mitigation Efforts n Standards Organizations • SAE G 19 Committee “chartered to address aspects of preventing, detecting, responding to and counteracting the threat of counterfeit electronic components” n AS 5553 (released 2009, rev A in progress) • Counterfeit avoidance requirements for OEMs and CMs • Adopted by DOD n AS 6081 (released December 2011) • Similar to AS 5553 • Prescriptive avoidance requirements for distributors n AS 6171 (in preparation) • Intended to standardize test methods • Covers a variety of tests • Includes sampling plans n ARP 6178 (in preparation) • Methods for risk assessment of distributors
Industry Mitigation Efforts n Standards Organizations • SAE G 19 Committee “chartered to address aspects of preventing, detecting, responding to and counteracting the threat of counterfeit electronic components” n AS 5553 (released 2009, rev A in progress) • Counterfeit avoidance requirements for OEMs and CMs • Adopted by DOD n AS 6081 (released December 2011) • Similar to AS 5553 • Prescriptive avoidance requirements for distributors n AS 6171 (in preparation) • Intended to standardize test methods • Covers a variety of tests • Includes sampling plans n ARP 6178 (in preparation) • Methods for risk assessment of distributors
 Industry Mitigation Efforts n Standards Organizations (continued) • IDEA (Independent Distributors of Electronics Assoc. ) n n n IDEA-STD-1010 B Visual inspection practices and requirements Includes acceptability criteria • ISO (Europe) n n PC 246 and TC 247 committees established (2009) to develop standards related to combating fraud Coordinating with ANSI in USA • i. NEMI Consortium n n Develop and assess improved methods for data exchange, authentication and traceability Includes development of metrics to assess the problem and measure program(s) effectiveness/cost
Industry Mitigation Efforts n Standards Organizations (continued) • IDEA (Independent Distributors of Electronics Assoc. ) n n n IDEA-STD-1010 B Visual inspection practices and requirements Includes acceptability criteria • ISO (Europe) n n PC 246 and TC 247 committees established (2009) to develop standards related to combating fraud Coordinating with ANSI in USA • i. NEMI Consortium n n Develop and assess improved methods for data exchange, authentication and traceability Includes development of metrics to assess the problem and measure program(s) effectiveness/cost
 Industry Mitigation Efforts n Training & Certification Programs • IDEA n n Certification to IDEA quality standards Inspector training and certification based on 1010 B • CTI CCAP Program n n Counterfeit components avoidance and certification program for Independent Distributors Training addresses detection and prevention of counterfeit components • Seminars and Workshops from SMTA, CALCE, and other organizations
Industry Mitigation Efforts n Training & Certification Programs • IDEA n n Certification to IDEA quality standards Inspector training and certification based on 1010 B • CTI CCAP Program n n Counterfeit components avoidance and certification program for Independent Distributors Training addresses detection and prevention of counterfeit components • Seminars and Workshops from SMTA, CALCE, and other organizations
 Government Initiatives n International efforts to reduce supply • Take-back laws n n Divert e. Waste to reuse/recycle Varies by country/state • Restrictions on e. Waste disposal n n n Regulated under the Basel Convention on Hazardous Waste (1992) Includes 170 member countries, USA not a member Regulated in USA under RCRA as “Hazardous Waste” • Currently no provisions specific to e. Waste • Possible future updates • Direct USA diplomatic initiatives
Government Initiatives n International efforts to reduce supply • Take-back laws n n Divert e. Waste to reuse/recycle Varies by country/state • Restrictions on e. Waste disposal n n n Regulated under the Basel Convention on Hazardous Waste (1992) Includes 170 member countries, USA not a member Regulated in USA under RCRA as “Hazardous Waste” • Currently no provisions specific to e. Waste • Possible future updates • Direct USA diplomatic initiatives
 Government Initiatives n n n Increased US Customs Scrutiny Congress hearings/proposed legislation National Defense Authorization Act (FY ’ 12) • Levin/Mc. Cain amendment provisions n n n Requires DOD to define “counterfeit part” Increases counterfeiting penalties for DOD contracts Requires improved counterfeit avoidance methodology for DOD and its contractors Mandatory counterfeits reporting (when discovered) for military and DOD contractor personnel Contractors are responsible for remediation cost when counterfeits are discovered
Government Initiatives n n n Increased US Customs Scrutiny Congress hearings/proposed legislation National Defense Authorization Act (FY ’ 12) • Levin/Mc. Cain amendment provisions n n n Requires DOD to define “counterfeit part” Increases counterfeiting penalties for DOD contracts Requires improved counterfeit avoidance methodology for DOD and its contractors Mandatory counterfeits reporting (when discovered) for military and DOD contractor personnel Contractors are responsible for remediation cost when counterfeits are discovered
 Authentication Testing n n The second line of defense Non-Destructive (sampling or 100%) • • Visual/Component data Radiographic (X-ray) X-ray Fluorescence (XRF) Electrical test n n n DC Functional Destructive • Reveals surface of Silicon chip • Chemical Decapsulation or Mechanical Delid
Authentication Testing n n The second line of defense Non-Destructive (sampling or 100%) • • Visual/Component data Radiographic (X-ray) X-ray Fluorescence (XRF) Electrical test n n n DC Functional Destructive • Reveals surface of Silicon chip • Chemical Decapsulation or Mechanical Delid
 Authentication Testing n External Visual Inspection • Inspect external packaging materials and labels • Compare appearance and font/symbology with “Golden” part if available • Inspect package for evidence of remarking: n n n Blacktopping Sanding scratches Discrepancies in surface texture
Authentication Testing n External Visual Inspection • Inspect external packaging materials and labels • Compare appearance and font/symbology with “Golden” part if available • Inspect package for evidence of remarking: n n n Blacktopping Sanding scratches Discrepancies in surface texture
 Authentication Testing n External Visual Inspection • Inspect Lead Condition n n Surface Appearance Straightness and Coplanarity • Marking permanency test n n n Mineral Spirits (JEDEC JESD 22 -B 107 C) MEK, Acetone, Alcohol also used Change in markings or surface appearance/texture
Authentication Testing n External Visual Inspection • Inspect Lead Condition n n Surface Appearance Straightness and Coplanarity • Marking permanency test n n n Mineral Spirits (JEDEC JESD 22 -B 107 C) MEK, Acetone, Alcohol also used Change in markings or surface appearance/texture
 Authentication Testing n Check component information • Consult Manufacturers’ Data Sheets n n n OCMs data sheets/websites Distributors Other sources (e. g. , prior inspections, customer data) • Date/Lot Code histories • Company histories n n SC OEMs Mergers, name changes, plant closings/relocations
Authentication Testing n Check component information • Consult Manufacturers’ Data Sheets n n n OCMs data sheets/websites Distributors Other sources (e. g. , prior inspections, customer data) • Date/Lot Code histories • Company histories n n SC OEMs Mergers, name changes, plant closings/relocations
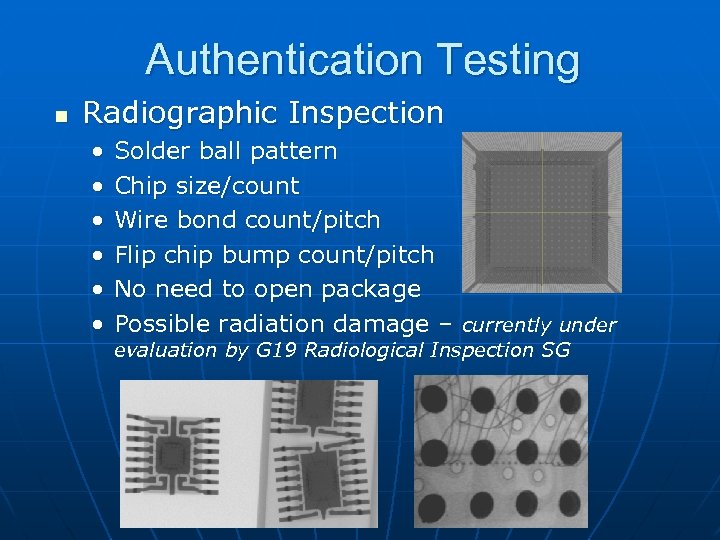 Authentication Testing n Radiographic Inspection • • • Solder ball pattern Chip size/count Wire bond count/pitch Flip chip bump count/pitch No need to open package Possible radiation damage – currently under evaluation by G 19 Radiological Inspection SG
Authentication Testing n Radiographic Inspection • • • Solder ball pattern Chip size/count Wire bond count/pitch Flip chip bump count/pitch No need to open package Possible radiation damage – currently under evaluation by G 19 Radiological Inspection SG
 Authentication Testing n XRF Testing • Rapid semi-quantitative elemental analysis • Typically used for: n n n Ro. HS compliance screening Verify Pb-free lead finish, or presence where required Ceramics analysis (typically caps)
Authentication Testing n XRF Testing • Rapid semi-quantitative elemental analysis • Typically used for: n n n Ro. HS compliance screening Verify Pb-free lead finish, or presence where required Ceramics analysis (typically caps)
 Authentication Testing n Electrical testing • Broad range of tests depending on component type and level of risk • DC testing (VOM, curve tracer) for discretes • ICs/actives require specialized test equipment and programming • Basic functional test vs full specification range
Authentication Testing n Electrical testing • Broad range of tests depending on component type and level of risk • DC testing (VOM, curve tracer) for discretes • ICs/actives require specialized test equipment and programming • Basic functional test vs full specification range
 Authentication Testing n Chemical Decapsulation • • • Exposes surface of Silicon chip Used on epoxy packages Acid etching most common
Authentication Testing n Chemical Decapsulation • • • Exposes surface of Silicon chip Used on epoxy packages Acid etching most common
 Authentication Testing n Mechanical Delidding • • • Metal or ceramic packages Diamond saw or Dremel Lid pry-off
Authentication Testing n Mechanical Delidding • • • Metal or ceramic packages Diamond saw or Dremel Lid pry-off
 Some Concerns n Increased direct and indirect costs • • • n Maintain process documentation/certifications Staffing/training Cost and time required for testing Authentication testing issues • Availability of historical data – date codes, etc. • New remarking methods n n New Blacktop material resistant to test solvents Use of micro-sandblasting to remove original markings – now under study by G 19 SG • Functional test challenges n n Test equipment/fixtures availability and support Availability of programming expertise
Some Concerns n Increased direct and indirect costs • • • n Maintain process documentation/certifications Staffing/training Cost and time required for testing Authentication testing issues • Availability of historical data – date codes, etc. • New remarking methods n n New Blacktop material resistant to test solvents Use of micro-sandblasting to remove original markings – now under study by G 19 SG • Functional test challenges n n Test equipment/fixtures availability and support Availability of programming expertise
 Some Concerns n Legal • Clear agreed definitions for “counterfeit, ” “fraudulent, ” “suspect, ” etc. • Clarify mandatory reporting requirements n n n By whom and to whom? When required? – includes “suspect” parts? Protection of customer/supplier confidentiality • Define liabilities n n n Parts falsely identified as non-conforming (alpha risk) Failure to identify counterfeits (beta risk) Responsibilities for consequences of incorporation of counterfeits into equipment • Evaluate/maintain/demonstrate “Due Diligence”
Some Concerns n Legal • Clear agreed definitions for “counterfeit, ” “fraudulent, ” “suspect, ” etc. • Clarify mandatory reporting requirements n n n By whom and to whom? When required? – includes “suspect” parts? Protection of customer/supplier confidentiality • Define liabilities n n n Parts falsely identified as non-conforming (alpha risk) Failure to identify counterfeits (beta risk) Responsibilities for consequences of incorporation of counterfeits into equipment • Evaluate/maintain/demonstrate “Due Diligence”
 Conclusions n n Counterfeits constitute a serious and growing threat for users of electronics Government and industry mitigation efforts are ongoing • Procedural, communication, training, etc. • Technical solutions n Users and distributors must assess their risk and establish a comprehensive plan • • Challenge to balance risks vs. costs Counterfeit threats always evolving Authentication testing for suspect components Maintain awareness of legal requirements
Conclusions n n Counterfeits constitute a serious and growing threat for users of electronics Government and industry mitigation efforts are ongoing • Procedural, communication, training, etc. • Technical solutions n Users and distributors must assess their risk and establish a comprehensive plan • • Challenge to balance risks vs. costs Counterfeit threats always evolving Authentication testing for suspect components Maintain awareness of legal requirements
 Conclusions “There is a flood of counterfeit microchips into the military, including in critical weapons systems… The counterfeiters are utterly ruthless, nimble, and getting increasingly better at their copies. ” - Dr. James A. Hayward, Applied DNA Sciences “No one practice or combination of practices will prevent counterfeit components from entering the supply chain, but every element of the supply chain must work together to solve the problem. ” - Dan Di. Mase, G 19 Committee Chairman
Conclusions “There is a flood of counterfeit microchips into the military, including in critical weapons systems… The counterfeiters are utterly ruthless, nimble, and getting increasingly better at their copies. ” - Dr. James A. Hayward, Applied DNA Sciences “No one practice or combination of practices will prevent counterfeit components from entering the supply chain, but every element of the supply chain must work together to solve the problem. ” - Dan Di. Mase, G 19 Committee Chairman
 Some References n n n Defense Industrial Base Assessment: Counterfeit Electronics, report available at www. bis. doc. gov Best Practices in the Fight Against Global Counterfeiting, report available at www. ansi. org US Senate Passes Anti-Counterfeit Electronics Bill, article available at www. circuitsassembly. com China Counterfeit Parts in U. S. Military Boeing, L 3 Aircraft, article available at www. businessweek. com Counterfeit Parts Control Plan Implementation, presentation by Dan Di. Mase, available at http: //supplychain. gsfc. nasa. gov/SC 2010%20 -%20 Dimase-rev. pdf n n www. anticounterfeitingforum. org. uk, list of UK-based resources ERAI, IDEA, GIDEP websites Linked. In anti-counterfeiting groups Missile Defense Agency Will Fight Parts Defects, article available at www. bloomberg. com/news/2011 -12 -29/u-s-missile-defense-agency-tocrack-down-on-poor-quality. html
Some References n n n Defense Industrial Base Assessment: Counterfeit Electronics, report available at www. bis. doc. gov Best Practices in the Fight Against Global Counterfeiting, report available at www. ansi. org US Senate Passes Anti-Counterfeit Electronics Bill, article available at www. circuitsassembly. com China Counterfeit Parts in U. S. Military Boeing, L 3 Aircraft, article available at www. businessweek. com Counterfeit Parts Control Plan Implementation, presentation by Dan Di. Mase, available at http: //supplychain. gsfc. nasa. gov/SC 2010%20 -%20 Dimase-rev. pdf n n www. anticounterfeitingforum. org. uk, list of UK-based resources ERAI, IDEA, GIDEP websites Linked. In anti-counterfeiting groups Missile Defense Agency Will Fight Parts Defects, article available at www. bloomberg. com/news/2011 -12 -29/u-s-missile-defense-agency-tocrack-down-on-poor-quality. html
 Thank You! Questions…? Stephen Schoppe sms@process-sciences. com Glenn Robertson glennr@process-sciences. com
Thank You! Questions…? Stephen Schoppe sms@process-sciences. com Glenn Robertson glennr@process-sciences. com


