0865c50a0797f6940405186a01bb7c1c.ppt
- Количество слайдов: 14
 EU-US Cooperation in Network and Information Security 17 Mar, 2008 – Yale, US Jacques Bus, Head of Unit DG Information Society and Media
EU-US Cooperation in Network and Information Security 17 Mar, 2008 – Yale, US Jacques Bus, Head of Unit DG Information Society and Media
 Content § Current research in EU programme § Motivation and modalities § Past and ongoing actions
Content § Current research in EU programme § Motivation and modalities § Past and ongoing actions
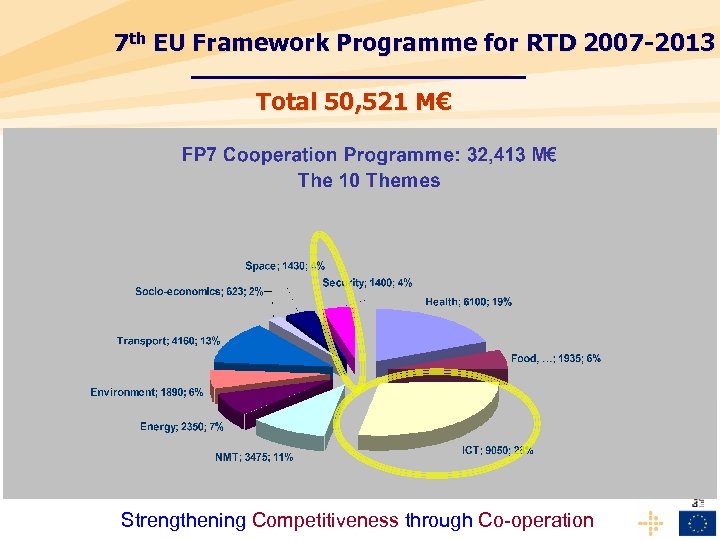 7 th EU Framework Programme for RTD 2007 -2013 Total 50, 521 M€ Strengthening Competitiveness through Co-operation
7 th EU Framework Programme for RTD 2007 -2013 Total 50, 521 M€ Strengthening Competitiveness through Co-operation
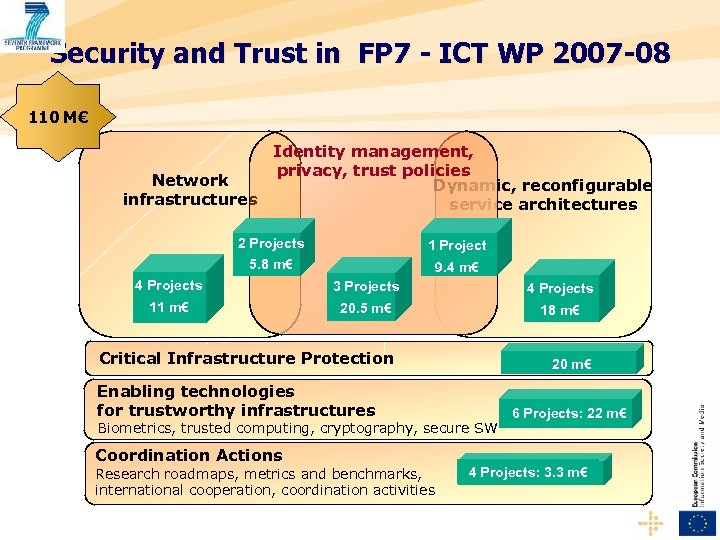 Security and Trust in FP 7 - ICT WP 2007 -08 110 M€ Identity management, privacy, trust policies Network Dynamic, reconfigurable infrastructures service architectures 2 Projects 5. 8 m€ 1 Project 9. 4 m€ 4 Projects 3 Projects 4 Projects 11 m€ 20. 5 m€ 18 m€ Critical Infrastructure Protection Enabling technologies for trustworthy infrastructures 20 m€ Biometrics, trusted computing, cryptography, secure SW Coordination Actions Research roadmaps, metrics and benchmarks, international cooperation, coordination activities 6 Projects: 22 m€ 4 Projects: 3. 3 m€
Security and Trust in FP 7 - ICT WP 2007 -08 110 M€ Identity management, privacy, trust policies Network Dynamic, reconfigurable infrastructures service architectures 2 Projects 5. 8 m€ 1 Project 9. 4 m€ 4 Projects 3 Projects 4 Projects 11 m€ 20. 5 m€ 18 m€ Critical Infrastructure Protection Enabling technologies for trustworthy infrastructures 20 m€ Biometrics, trusted computing, cryptography, secure SW Coordination Actions Research roadmaps, metrics and benchmarks, international cooperation, coordination activities 6 Projects: 22 m€ 4 Projects: 3. 3 m€
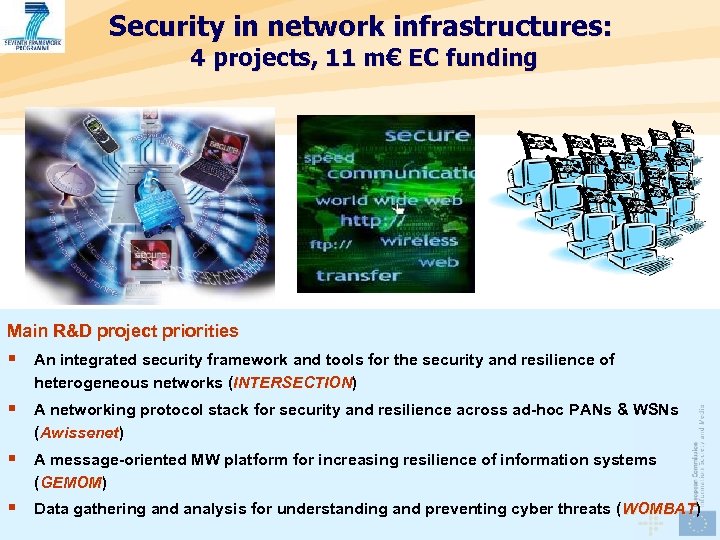 Security in network infrastructures: 4 projects, 11 m€ EC funding Main R&D project priorities § An integrated security framework and tools for the security and resilience of heterogeneous networks (INTERSECTION) INTERSECTION § A networking protocol stack for security and resilience across ad-hoc PANs & WSNs (Awissenet) Awissenet § A message-oriented MW platform for increasing resilience of information systems (GEMOM) GEMOM § Data gathering and analysis for understanding and preventing cyber threats (WOMBAT) WOMBAT
Security in network infrastructures: 4 projects, 11 m€ EC funding Main R&D project priorities § An integrated security framework and tools for the security and resilience of heterogeneous networks (INTERSECTION) INTERSECTION § A networking protocol stack for security and resilience across ad-hoc PANs & WSNs (Awissenet) Awissenet § A message-oriented MW platform for increasing resilience of information systems (GEMOM) GEMOM § Data gathering and analysis for understanding and preventing cyber threats (WOMBAT) WOMBAT
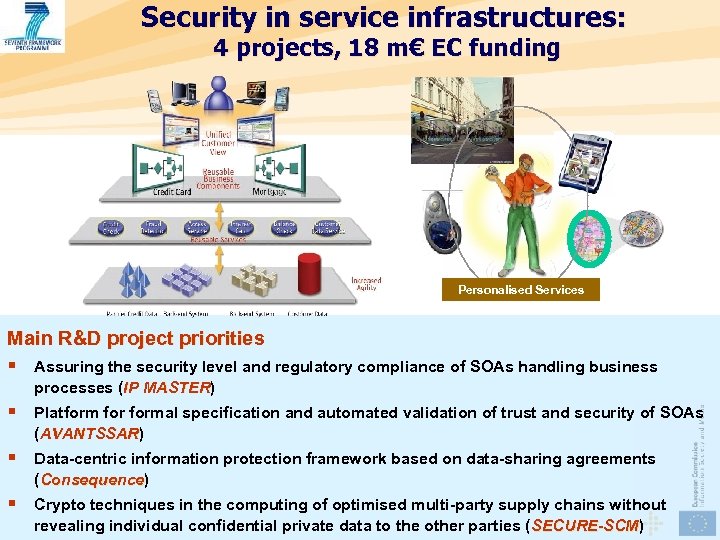 Security in service infrastructures: 4 projects, 18 m€ EC funding Personalised Services Main R&D project priorities § Assuring the security level and regulatory compliance of SOAs handling business processes (IP MASTER) MASTER § Platformal specification and automated validation of trust and security of SOAs (AVANTSSAR) AVANTSSAR § Data-centric information protection framework based on data-sharing agreements (Consequence) Consequence § Crypto techniques in the computing of optimised multi-party supply chains without revealing individual confidential private data to the other parties ( SECURE-SCM) SECURE-SCM
Security in service infrastructures: 4 projects, 18 m€ EC funding Personalised Services Main R&D project priorities § Assuring the security level and regulatory compliance of SOAs handling business processes (IP MASTER) MASTER § Platformal specification and automated validation of trust and security of SOAs (AVANTSSAR) AVANTSSAR § Data-centric information protection framework based on data-sharing agreements (Consequence) Consequence § Crypto techniques in the computing of optimised multi-party supply chains without revealing individual confidential private data to the other parties ( SECURE-SCM) SECURE-SCM
 User-centric Privacy and ID-Management (1) 6 projects, 35. 7 m€ EC funding Main R&D project priorities § Bringing Sustainable Privacy and Identity Management to Future Networks and Services; Privacy-enhancing identity management ‘for life’ (IP-PRIMELIFE) IP-PRIMELIFE § Revocable, user-controlled, fingerprint-based biometric identities (IP-TURBINE) IP-TURBINE § A platform for trust, privacy and identity management of community services and applications on the Internet and in mobile networks ( PICOS) PICOS
User-centric Privacy and ID-Management (1) 6 projects, 35. 7 m€ EC funding Main R&D project priorities § Bringing Sustainable Privacy and Identity Management to Future Networks and Services; Privacy-enhancing identity management ‘for life’ (IP-PRIMELIFE) IP-PRIMELIFE § Revocable, user-controlled, fingerprint-based biometric identities (IP-TURBINE) IP-TURBINE § A platform for trust, privacy and identity management of community services and applications on the Internet and in mobile networks ( PICOS) PICOS
 User-centric Privacy and ID-Management (2) 6 projects, 35. 7 m€ EC funding Main R&D project priorities § Trusted SOA architectures enabling dynamic and secure services that are managing and processing personal information based on user-centric data management policies (IP-TAS 3) IP-TAS 3 § Cross-layer identity framework for network infrastructures (SWIFT) SWIFT § Privacy-preserving network monitoring system with data protection (PRISM) PRISM
User-centric Privacy and ID-Management (2) 6 projects, 35. 7 m€ EC funding Main R&D project priorities § Trusted SOA architectures enabling dynamic and secure services that are managing and processing personal information based on user-centric data management policies (IP-TAS 3) IP-TAS 3 § Cross-layer identity framework for network infrastructures (SWIFT) SWIFT § Privacy-preserving network monitoring system with data protection (PRISM) PRISM
 Security enabling Technologies 6 projects, 22 m€ EC funding Main R&D project priorities § Trusted Computing IP TECOM trusted embedded systems: HW platforms with integrated trust components § § Cryptography No. E e. Crypt II Multi-modal Biometrics multi-biometric authentication (based on face and voice) for mobile devices ( MOBIO) MOBIO activity related and soft biometrics technologies for supporting continuous authentication and monitoring of users in ambient environments (ACTIBIO) ACTIBIO § Secure SW implementation providing SW developers with the means to prevent occurrences of known vulnerabilities when building software (SHIELDS) SHIELDS A toolbox for cryptographic software engineering (CACE) CACE
Security enabling Technologies 6 projects, 22 m€ EC funding Main R&D project priorities § Trusted Computing IP TECOM trusted embedded systems: HW platforms with integrated trust components § § Cryptography No. E e. Crypt II Multi-modal Biometrics multi-biometric authentication (based on face and voice) for mobile devices ( MOBIO) MOBIO activity related and soft biometrics technologies for supporting continuous authentication and monitoring of users in ambient environments (ACTIBIO) ACTIBIO § Secure SW implementation providing SW developers with the means to prevent occurrences of known vulnerabilities when building software (SHIELDS) SHIELDS A toolbox for cryptographic software engineering (CACE) CACE
 Content § Current research in EU programme § Motivation and modalities § Past and ongoing actions
Content § Current research in EU programme § Motivation and modalities § Past and ongoing actions
 International Cooperation Why , What WHY § Cyber activities intrinsically crosses borders § No authentication in international network traffic § Internet facilitates international “underground economy” § Nation-state cyberwarfare § Free, industrialised world must protect its values WHAT § Cooperation in research for common goal § Sharing information on incidents, problems § International coordination of R&D and policy
International Cooperation Why , What WHY § Cyber activities intrinsically crosses borders § No authentication in international network traffic § Internet facilitates international “underground economy” § Nation-state cyberwarfare § Free, industrialised world must protect its values WHAT § Cooperation in research for common goal § Sharing information on incidents, problems § International coordination of R&D and policy
 International Cooperation Framework § S&T Agreement between NSF and EU FP-RTD, within this framework we organised jointly: – cooperation between projects on both sides: extra travel budget from NSF for US participants; part of project budget in EU projects – organisation of workshops with cost born by “own side” – participation in other side’s project at own costs, unless exception § Cooperation between EU initiative on Future Internet and NSF GENI/FIND § Ongoing discussions with US-DHS and EU Security and ICT programmes
International Cooperation Framework § S&T Agreement between NSF and EU FP-RTD, within this framework we organised jointly: – cooperation between projects on both sides: extra travel budget from NSF for US participants; part of project budget in EU projects – organisation of workshops with cost born by “own side” – participation in other side’s project at own costs, unless exception § Cooperation between EU initiative on Future Internet and NSF GENI/FIND § Ongoing discussions with US-DHS and EU Security and ICT programmes
 Content § Current research in EU programme § Motivation and modalities § Past and ongoing actions
Content § Current research in EU programme § Motivation and modalities § Past and ongoing actions
 Past and Ongoing cooperation actions § EU-US Summits on Cyber Trust: Systems dependability and security (~ 60 participants on invitation) – Dublin, IRL 15 -16 Nov 2006 – Urbana-Champaign, Illinois, USA 26 -27 April 2007 § INCOTRUST: continuation and extension of EU-US activities of Dublin and Illinois. Financial support from EU and support by NSF for similar activities § FORWARD: bringing together industry and academia to discuss trends in threats and the RTD agenda for it. Cooperation with CMU-Cylab
Past and Ongoing cooperation actions § EU-US Summits on Cyber Trust: Systems dependability and security (~ 60 participants on invitation) – Dublin, IRL 15 -16 Nov 2006 – Urbana-Champaign, Illinois, USA 26 -27 April 2007 § INCOTRUST: continuation and extension of EU-US activities of Dublin and Illinois. Financial support from EU and support by NSF for similar activities § FORWARD: bringing together industry and academia to discuss trends in threats and the RTD agenda for it. Cooperation with CMU-Cylab


