9de91d9e43f8d5269f32e0160486d54c.ppt
- Количество слайдов: 25
 EU’s Information Security Expectations Aleksandar Klaić Office of the National Security Council – Croatian National Security Authority (NSA)
EU’s Information Security Expectations Aleksandar Klaić Office of the National Security Council – Croatian National Security Authority (NSA)
 Session parts 1. Introduction - Information Space 2. Information security Requirements 3. Conclusion 2
Session parts 1. Introduction - Information Space 2. Information security Requirements 3. Conclusion 2
 Part 1 1. Introduction – Information Space 3
Part 1 1. Introduction – Information Space 3
 Single European Information Space • “i 2010: European Information Society 2010” – five-year strategy – European Commission, COM(2005) 229 final, Brussels 1. 6. 2005 – Growth & employment strategy – Priorities: • Single European Information Space, Innovation and Investment, Inclusive European Information Society – Single European Information Space: • affordable & secure high bandwidth communications, • rich & diverse content and digital services 4
Single European Information Space • “i 2010: European Information Society 2010” – five-year strategy – European Commission, COM(2005) 229 final, Brussels 1. 6. 2005 – Growth & employment strategy – Priorities: • Single European Information Space, Innovation and Investment, Inclusive European Information Society – Single European Information Space: • affordable & secure high bandwidth communications, • rich & diverse content and digital services 4
 Foundations of the Information Space 5
Foundations of the Information Space 5
 Information Domains • Traditional information domains like: – Classified information domain (secrecy, legal persons – Government/military; confidential) – Unclassified information domain (privacy, legal persons; sensitive but not classified ) – Personal information domain (privacy, physical persons) – Public information domain (disclosure is not welcome but would not cause any adverse impact) • Contemporary democratic concepts like: – Freedom of information – Open & transparent Government (e-Government) • Information Society paradigm 6
Information Domains • Traditional information domains like: – Classified information domain (secrecy, legal persons – Government/military; confidential) – Unclassified information domain (privacy, legal persons; sensitive but not classified ) – Personal information domain (privacy, physical persons) – Public information domain (disclosure is not welcome but would not cause any adverse impact) • Contemporary democratic concepts like: – Freedom of information – Open & transparent Government (e-Government) • Information Society paradigm 6
 Information Society • Paradigm that arose at the turn of 20 th & 21 st centuries – (wide) national & society oriented – Private Government & public ICT infrastructure (CERTs) • “Successor” of e-Government paradigm – (narrow) government & technically oriented – Primarily private Government ICT infrastructure • Connection with information security – Standardization of ICT and IS fields • CEN (ISSS), CENELEC, ETSI, ISO – IS in the foundation of information society • COM(2006)251 final – A Strategy for a Secure Information Society – Prioritized interoperability issue • technical, semantic, and organizational level • IDABC (Interoperable pan-European e. Gov services) 7
Information Society • Paradigm that arose at the turn of 20 th & 21 st centuries – (wide) national & society oriented – Private Government & public ICT infrastructure (CERTs) • “Successor” of e-Government paradigm – (narrow) government & technically oriented – Primarily private Government ICT infrastructure • Connection with information security – Standardization of ICT and IS fields • CEN (ISSS), CENELEC, ETSI, ISO – IS in the foundation of information society • COM(2006)251 final – A Strategy for a Secure Information Society – Prioritized interoperability issue • technical, semantic, and organizational level • IDABC (Interoperable pan-European e. Gov services) 7
 Part 2 2. Information Security Requirements – legislation and policy requirements 8
Part 2 2. Information Security Requirements – legislation and policy requirements 8
 Information Security Requirements • Explicit requirements (legislative) – General Legislative requirements • e. g. Personal Data Protection Act – Specific Legislative Requirements • e. g. Code on Corporate Governance, Sarbonnes-Oxleey Act – Accession/membership program requirements • e. g. EU e-signatures Directive 1999/93/EC • Implicit requirements (policy) – Security Agreement - Security policy • e. g. EU Council’s Security Regulations 2001/264/EC – Community Programs • e. g. i 2010 - COM(2005) 229 final – Sectoral requirements • e. g. Basel II (finance sector) 9
Information Security Requirements • Explicit requirements (legislative) – General Legislative requirements • e. g. Personal Data Protection Act – Specific Legislative Requirements • e. g. Code on Corporate Governance, Sarbonnes-Oxleey Act – Accession/membership program requirements • e. g. EU e-signatures Directive 1999/93/EC • Implicit requirements (policy) – Security Agreement - Security policy • e. g. EU Council’s Security Regulations 2001/264/EC – Community Programs • e. g. i 2010 - COM(2005) 229 final – Sectoral requirements • e. g. Basel II (finance sector) 9
 Legislation Puzzle 10
Legislation Puzzle 10
 EU Reference legislation • eur-lex. europa. eu – Council Decision 92/242/EEC in the area of security of information – Council Resolution on a common approach and specific actions in the area of network and information security (OJ 2002/C 43/02, 28 January 2002) – Directive 95/46/EC on the protection of individuals with regard to the processing of personal data and on the free movement of such data – Telecommunications Data Protection Directive 97/66/EC – Directive 2002/58/EC on Privacy and Electronic Communications – Data Retention Directive 2006/24/EC – Commission Communication to counter spam (COM (2004)28) – Council Resolution 2000/C 293/02 on the organization and management of the Internet – EU Parliament and Council Decision 854/2005/EC on promoting safer use of the Internet, Decision 1151/2003/EC on combating illegal and harmful content on global networks – Safer Internet plus Programme (europa. eu. int/saferinternet) • www. iso. org – ISO 15489 -1: 2001, ISO 15489 -2: 2001, ISO/IEC 17799: 2005, ISO/IEC 27001: 2005, ISO/IEC 13335 -x • • www. cornwell. co. uk/moreq. html - European testing framework for Electronic Records Management System (ERM) www. nn. hr – Agreement Between the Republic of Croatia and the European Union on Security Procedures for the Exchange of Classified Information, 9/2006, 18 October 2006 – Memorandum of Understanding between European Community and the Republic of Croatia on the participation of the Republic of Croatia in the Community program on the interoperable delivery of pan-European e-Government services to public administrations, businesses and citizens (IDABC), 2/2007, 28 February 2007 11
EU Reference legislation • eur-lex. europa. eu – Council Decision 92/242/EEC in the area of security of information – Council Resolution on a common approach and specific actions in the area of network and information security (OJ 2002/C 43/02, 28 January 2002) – Directive 95/46/EC on the protection of individuals with regard to the processing of personal data and on the free movement of such data – Telecommunications Data Protection Directive 97/66/EC – Directive 2002/58/EC on Privacy and Electronic Communications – Data Retention Directive 2006/24/EC – Commission Communication to counter spam (COM (2004)28) – Council Resolution 2000/C 293/02 on the organization and management of the Internet – EU Parliament and Council Decision 854/2005/EC on promoting safer use of the Internet, Decision 1151/2003/EC on combating illegal and harmful content on global networks – Safer Internet plus Programme (europa. eu. int/saferinternet) • www. iso. org – ISO 15489 -1: 2001, ISO 15489 -2: 2001, ISO/IEC 17799: 2005, ISO/IEC 27001: 2005, ISO/IEC 13335 -x • • www. cornwell. co. uk/moreq. html - European testing framework for Electronic Records Management System (ERM) www. nn. hr – Agreement Between the Republic of Croatia and the European Union on Security Procedures for the Exchange of Classified Information, 9/2006, 18 October 2006 – Memorandum of Understanding between European Community and the Republic of Croatia on the participation of the Republic of Croatia in the Community program on the interoperable delivery of pan-European e-Government services to public administrations, businesses and citizens (IDABC), 2/2007, 28 February 2007 11
 Information Security Definition • General: – Information security is characterized as the preservation of confidentiality, integrity, and availability of information, and it is achieved by implementing a suitable set of controls. • Information Society: – Information security is not a right in itself, it is an instrument to exercise and enjoy other basic rights like the right to confidentiality, personal data protection, or trade secrets. 12
Information Security Definition • General: – Information security is characterized as the preservation of confidentiality, integrity, and availability of information, and it is achieved by implementing a suitable set of controls. • Information Society: – Information security is not a right in itself, it is an instrument to exercise and enjoy other basic rights like the right to confidentiality, personal data protection, or trade secrets. 12
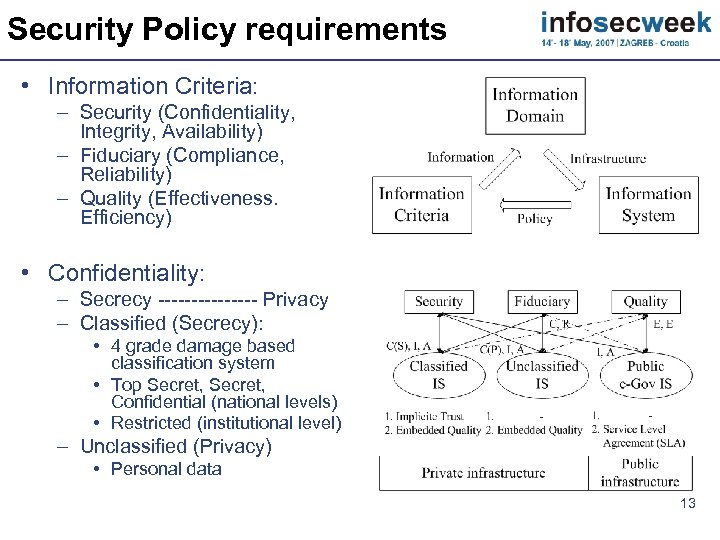 Security Policy requirements • Information Criteria: – Security (Confidentiality, Integrity, Availability) – Fiduciary (Compliance, Reliability) – Quality (Effectiveness. Efficiency) • Confidentiality: – Secrecy -------- Privacy – Classified (Secrecy): • 4 grade damage based classification system • Top Secret, Confidential (national levels) • Restricted (institutional level) – Unclassified (Privacy) • Personal data 13
Security Policy requirements • Information Criteria: – Security (Confidentiality, Integrity, Availability) – Fiduciary (Compliance, Reliability) – Quality (Effectiveness. Efficiency) • Confidentiality: – Secrecy -------- Privacy – Classified (Secrecy): • 4 grade damage based classification system • Top Secret, Confidential (national levels) • Restricted (institutional level) – Unclassified (Privacy) • Personal data 13
 Security Agreement • Security procedures for the exchange of classified information • Bilateral between two countries – Mutual trust in security policies (no assessment) – The level of protection of foreign data is equal or higher than the one of national data • Bilateral between a country and an international organization like EU or NATO – Minimal Security Requirements - Baseline standards – Assessment based trust • Legislation, organization, procedures • Designated Security Authority – National Security Authority (NSA) 14
Security Agreement • Security procedures for the exchange of classified information • Bilateral between two countries – Mutual trust in security policies (no assessment) – The level of protection of foreign data is equal or higher than the one of national data • Bilateral between a country and an international organization like EU or NATO – Minimal Security Requirements - Baseline standards – Assessment based trust • Legislation, organization, procedures • Designated Security Authority – National Security Authority (NSA) 14
 EU’s Inf. Security Organization • Council of the EU – General Secretariat • European Commission – Security Directorate • Security/Infosec Offices • Departments – Agency ENISA – – Judiciary body (national) MS ministers Policy making Inspections of Accession Countries – – Executive body EU institution Policy implementation Cooperation with national (MS) authorities 15
EU’s Inf. Security Organization • Council of the EU – General Secretariat • European Commission – Security Directorate • Security/Infosec Offices • Departments – Agency ENISA – – Judiciary body (national) MS ministers Policy making Inspections of Accession Countries – – Executive body EU institution Policy implementation Cooperation with national (MS) authorities 15
 Harmonization based on Sec. Agr. • Security policy – key document – Council Decision, 19 March 2001, adopting the Council’s security regulations (2001/264/EC) – Commission Decision, 29 November 2001, amending its internal Rules of Procedure (2001/844/EC) • Security organization: – National Security Authority (NSA) - central coordinating institution, – Infosec Authority (IA or NCSA) – auxiliary specialized institution, – Planning and Implementation Authority (PIA) – auxiliary specialized institution, – CISO/LISO – Central/Local Inf. Sec. Officers • Security Areas: – Personnel Security, Physical Security, Security of Information, INFOSEC (Information System Security), Industrial Security • Baseline standards 16
Harmonization based on Sec. Agr. • Security policy – key document – Council Decision, 19 March 2001, adopting the Council’s security regulations (2001/264/EC) – Commission Decision, 29 November 2001, amending its internal Rules of Procedure (2001/844/EC) • Security organization: – National Security Authority (NSA) - central coordinating institution, – Infosec Authority (IA or NCSA) – auxiliary specialized institution, – Planning and Implementation Authority (PIA) – auxiliary specialized institution, – CISO/LISO – Central/Local Inf. Sec. Officers • Security Areas: – Personnel Security, Physical Security, Security of Information, INFOSEC (Information System Security), Industrial Security • Baseline standards 16
 Baseline Standards • Information security standards that shall be applied in each member state • Why not risk assessment/management process? – Baseline procedures are the result of risk assessment/management on the highest org. level: • Periodic changes of security policy and implementing directives – Org. concept follows the model of central/HQ organization with subsidiaries that are usually: • Lack of field expertise and/or senior management resources – Recommendation for national risk management process: • Different environments (legislation, culture, tradition) • Old-fashioned way but successful in an extremely heterogeneous environment as government sector 17
Baseline Standards • Information security standards that shall be applied in each member state • Why not risk assessment/management process? – Baseline procedures are the result of risk assessment/management on the highest org. level: • Periodic changes of security policy and implementing directives – Org. concept follows the model of central/HQ organization with subsidiaries that are usually: • Lack of field expertise and/or senior management resources – Recommendation for national risk management process: • Different environments (legislation, culture, tradition) • Old-fashioned way but successful in an extremely heterogeneous environment as government sector 17
 Security Policy Development 18
Security Policy Development 18
 Information Infrastructure Approach EU Security Policy (2001): • Classified infrastructure (isolated, air-gap) – “Top Secret“, “Secret”, “Confidential” • Protected Private infrastructure NATO Security Policy(2006): • Classified infrastructure (isolated, air-gap) – “Top Secret“, “Secret”, “Confidential” • – Unclassified, (“Restricted”) – “Restricted”, (non-classified) – TESTA Network (IDABC) • Public infrastructure – GW connectivity w/protected private infrastructure – Portal Your Europe Unclassified infrastructure • Public infrastructure – GW connectivity w/unclassified infrastructure http: //ec. europa. eu/youreurope/ EU Inf. Society (2010) 19
Information Infrastructure Approach EU Security Policy (2001): • Classified infrastructure (isolated, air-gap) – “Top Secret“, “Secret”, “Confidential” • Protected Private infrastructure NATO Security Policy(2006): • Classified infrastructure (isolated, air-gap) – “Top Secret“, “Secret”, “Confidential” • – Unclassified, (“Restricted”) – “Restricted”, (non-classified) – TESTA Network (IDABC) • Public infrastructure – GW connectivity w/protected private infrastructure – Portal Your Europe Unclassified infrastructure • Public infrastructure – GW connectivity w/unclassified infrastructure http: //ec. europa. eu/youreurope/ EU Inf. Society (2010) 19
 Plan–Do–Check–Act Process 20
Plan–Do–Check–Act Process 20
 ENISA • European Network and Information Security Agency establishing, 10 March 2004, (2004/460/EC) • “Connects” all phases of the PDCA process and all participants in the information society • Primarily Security Awareness responsibility • Expert Analysis in the field of: – Risk Management, Security Technologies and Policies, … • Coordination of: – EU bodies and MS – Industry and International Organizations – CERTs in EU 21
ENISA • European Network and Information Security Agency establishing, 10 March 2004, (2004/460/EC) • “Connects” all phases of the PDCA process and all participants in the information society • Primarily Security Awareness responsibility • Expert Analysis in the field of: – Risk Management, Security Technologies and Policies, … • Coordination of: – EU bodies and MS – Industry and International Organizations – CERTs in EU 21
 Other Initiatives • Focus on Small and Medium Enterprises (SMEs) – ENISA: Information Package for SMEs (RM/RA), February 2007 – http: //www. enisa. europa. eu • EU Regulatory Framework for electronic communications networks and services – Review of the EU Regulatory Framework for el. communications networks and services, Jun 2006, COM(2006)334 final • Breaches of security – notifications, keep users informed • Authorization of national authorities – specific security measures that implement Commission recommendations of decisions • Network integrity – to modernize provisions – Based on A strategy for a Secure Information Society, May 2006, COM(2006)251 final (i 2010) • European Program for Critical Infrastructure Protection (EPCIP) – CI Sectors (Energy, ICT, Water, Food, …) – All-hazards approach, terrorism priority – Green Paper on EPCIP, COM(2005)576 final, November 2005 22
Other Initiatives • Focus on Small and Medium Enterprises (SMEs) – ENISA: Information Package for SMEs (RM/RA), February 2007 – http: //www. enisa. europa. eu • EU Regulatory Framework for electronic communications networks and services – Review of the EU Regulatory Framework for el. communications networks and services, Jun 2006, COM(2006)334 final • Breaches of security – notifications, keep users informed • Authorization of national authorities – specific security measures that implement Commission recommendations of decisions • Network integrity – to modernize provisions – Based on A strategy for a Secure Information Society, May 2006, COM(2006)251 final (i 2010) • European Program for Critical Infrastructure Protection (EPCIP) – CI Sectors (Energy, ICT, Water, Food, …) – All-hazards approach, terrorism priority – Green Paper on EPCIP, COM(2005)576 final, November 2005 22
 Part 3 3. Conclusion 23
Part 3 3. Conclusion 23
 Conclusion • EU has complex regulation framework in the field of information security • Information security requirements: – Traditional scope of the security policy – Contemporary demands of information society • Very similar security policy strategies – EU & NATO (and generally Member States) • Private Protected or Unclassified (+ “Restricted”) Infrastructure: – Similar approaches in MSs, EU (even NATO) based on society factors – More and more focused on international information security standards like the area of personal data protection 24
Conclusion • EU has complex regulation framework in the field of information security • Information security requirements: – Traditional scope of the security policy – Contemporary demands of information society • Very similar security policy strategies – EU & NATO (and generally Member States) • Private Protected or Unclassified (+ “Restricted”) Infrastructure: – Similar approaches in MSs, EU (even NATO) based on society factors – More and more focused on international information security standards like the area of personal data protection 24
 Questions ? THANK YOU !!! Aleksandar. Klaic@uvns. vlada. hr aklaic@hi. t-com. hr 25
Questions ? THANK YOU !!! Aleksandar. Klaic@uvns. vlada. hr aklaic@hi. t-com. hr 25


