c786784066210ceaefd272715dec441d.ppt
- Количество слайдов: 31

Ethical Hacking Penetrating Web 2. 0 Security Hands-On Ethical Hacking and Network Defense

Contact Sam Bowne n Computer Networking and Information Technology n City College San Francisco n Email: sbowne@ccsf. edu n Web: samsclass. info n 2

Two Hacking Classes CNIT 123: Ethical Hacking and Network Defense Has been taught since Spring 2007 (four times) Face-to-face and Online sections available Fall 2008 CNIT 124: Advanced Ethical Hacking Taught for the first time in Spring 2008 3

Supplemental Materials Projects from recent research n Students get extra credit by attending conferences n 4

Certified Ethical Hacker n Those two classes prepare students for CEH Certification 5
Certificate in Network Security 6
Associate of Science Degree 7

Four Vulnerabilities n SQL Injection n n Cross-Site Scripting n n 65% of major sites vulnerable Cross-Site Request Forgery n n 16% of Web sites vulnerable Almost every Web site with a login is vulnerable Layer 7 Denial of Service n Every site with active content is vulnerable 8

SQL Injection Hands-On Ethical Hacking and Network Defense
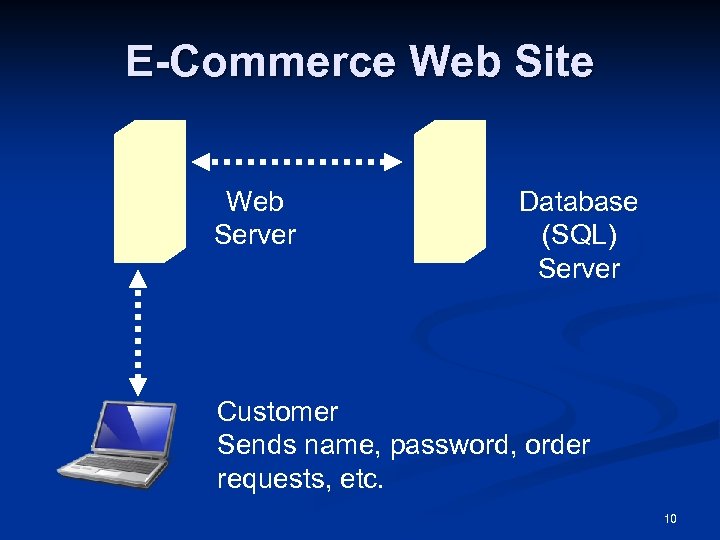
E-Commerce Web Site Web Server Database (SQL) Server Customer Sends name, password, order requests, etc. 10
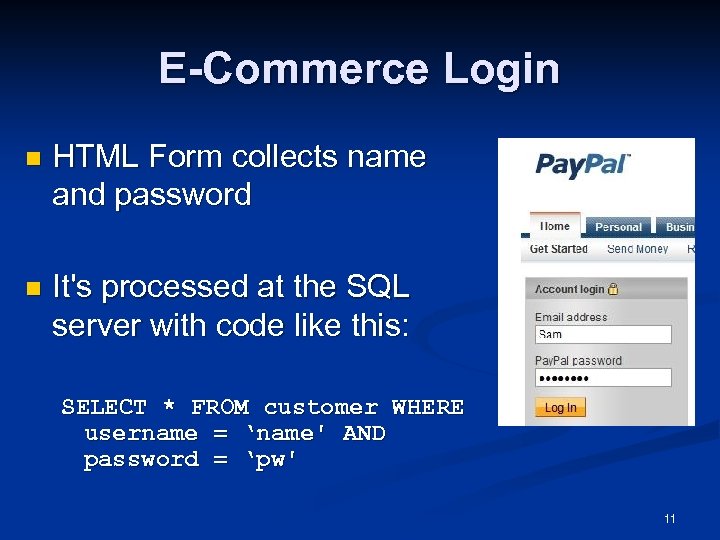
E-Commerce Login n HTML Form collects name and password n It's processed at the SQL server with code like this: SELECT * FROM customer WHERE username = ‘name' AND password = ‘pw' 11

SQL Injection If a hacker enters a name of ’ OR 1=1 -The SQL becomes: SELECT * FROM customer WHERE username = ‘’ OR 1=1 --' AND password = ‘pw‘ The -- ends the statement, making the rest of the line a comment 1=1 is always true, so this makes the condition true 12
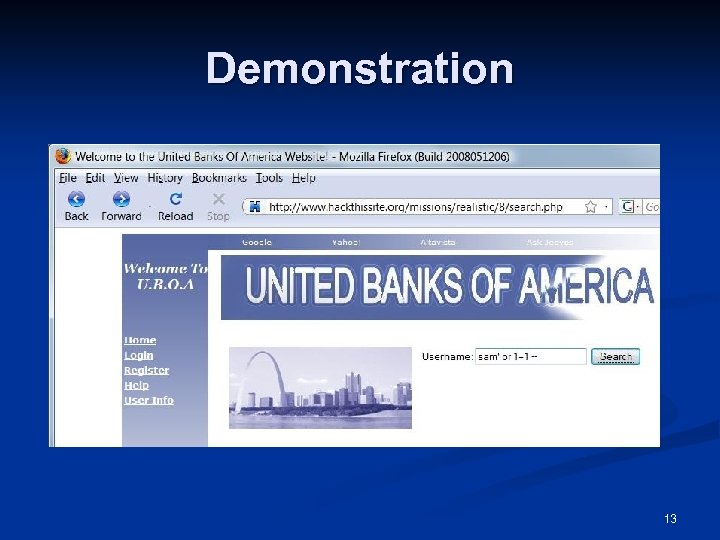
Demonstration 13
SQL Injection Effects n This can cause the user to be authenticated as administrator, dump the entire database, or have other drastic effects n Comic from xkcd. org 14

Sanitize your Inputs All user input should be checked, and special characters like ' or '' or < or > discarded n That will reduce vulnerability to SQL injection n n The typical SQL Injection vulnerability takes more than four months to locate and fix 15

Cross-Site Scripting (XSS) Hands-On Ethical Hacking and Network Defense
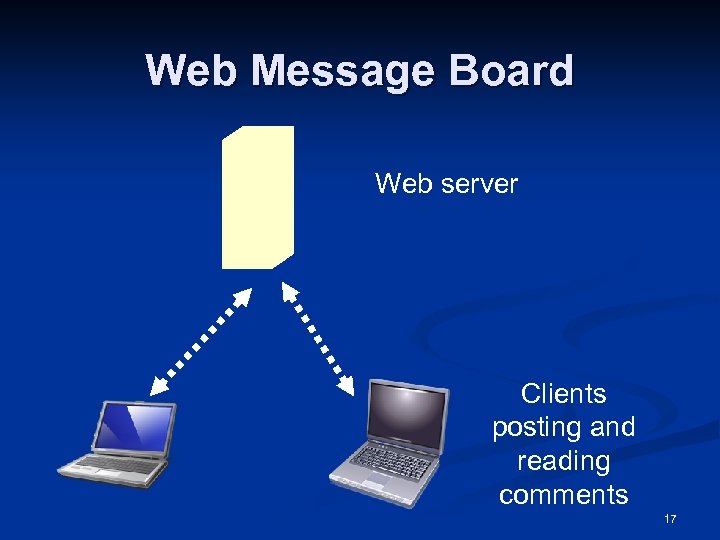
Web Message Board Web server Clients posting and reading comments 17

Cross-Site Scripting (XSS) One client posts active content, with <script> tags or other programming content n When another client reads the messages, the scripts are executed in his or her browser n One user attacks another user, using the vulnerable Web application as a weapon n 18
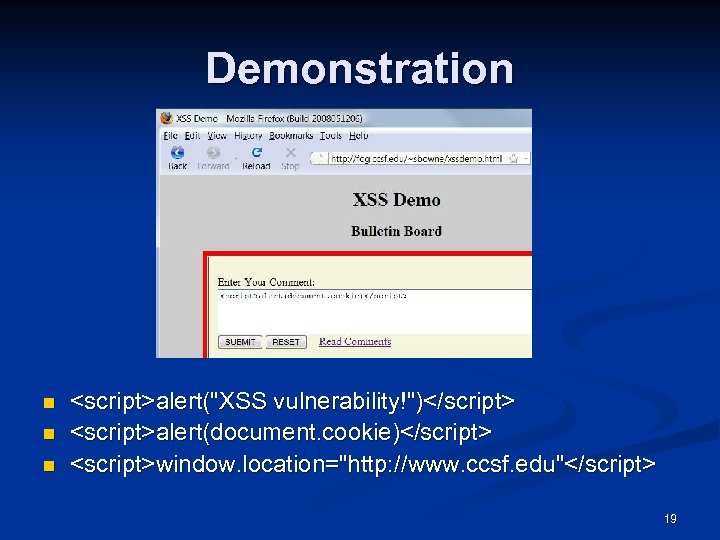
Demonstration n <script>alert("XSS vulnerability!")</script> <script>alert(document. cookie)</script> <script>window. location="http: //www. ccsf. edu"</script> 19

XSS Scripting Effects n Steal another user's authentication cookie n Hijack session Harvest stored passwords from the target's browser n Take over machine through browser vulnerability n Redirect Webpage n Many, many other evil things… n 20

Cross-Site Request Forgery (XSRF) Hands-On Ethical Hacking and Network Defense
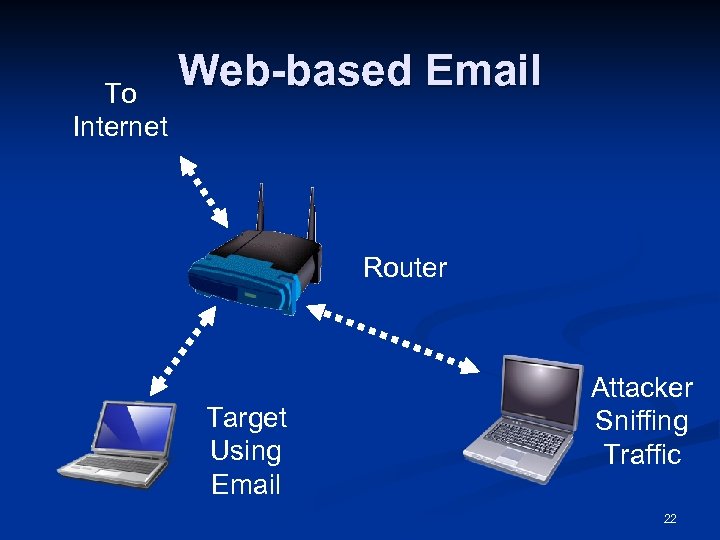
To Internet Web-based Email Router Target Using Email Attacker Sniffing Traffic 22

Cross-Site Request Forgery (XSRF) n Gmail sends the password through a secure HTTPS connection n n But the cookie identifying the user is sent in the clear—with HTTP n n That cannot be captured by the attacker That can easily be captured by the attacker The attacker gets into your account without learning your password 23
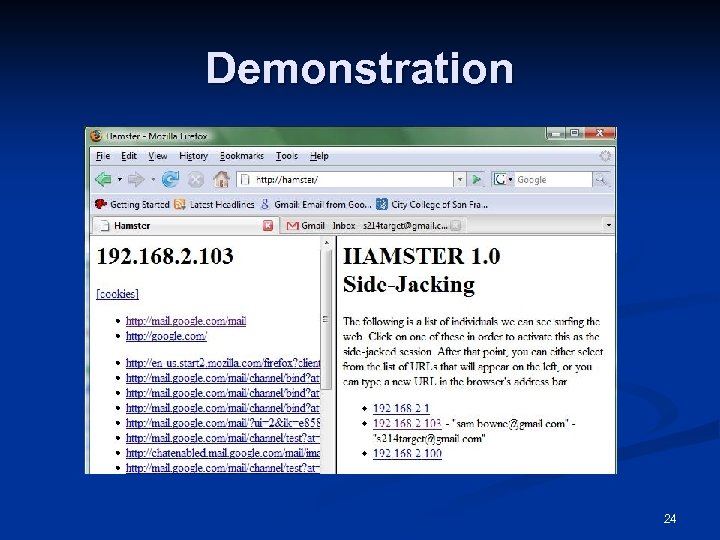
Demonstration 24

XSRF Countermeasure Use https: //mail. google. com instead of http: //gmail. com n No other mail service has this option at all, as far as I know n 25

Application-Layer Denial of Service Hands-On Ethical Hacking and Network Defense

Application-Layer Do. S Find small requests that consume a lot of server resources n Application Crashing n Data Destruction n Resource Depletion n Memory n CPU n Bandwidth n Disk Space n 27
Resource Depletion Example n CPU Consumption On a large forum n Create a complicated regular expression search n Use a script to launch the search over and over n 28

Real-World Test n Hacktics, a security company, brought down a large corporate network with just three laptops in an authorized test Global company with branches in Israel, Europe and the USA n Internet Connectivity – 3 x 50 Mbps lines with load balancing. ISPs provide Cisco (Riverhead) based Anti DDo. S solutions n High security network, 30+ Web servers, backend servers, Mail Relay, databases n 29

Hacktics Results Do. S was successful to all systems but one n Two applications crashed completely after a few dozen requests only n Most other applications stopped responding after 5 -15 minutes of script execution from up to three laptops (though with most a single laptop was sufficient) n Main cause of Do. S was CPU exhaustion n 30

References n Where the Web is Weak n n http: //www. forbes. com/2008/05/14/webhacking-google-tech-security 08 cx_ag_0514 webhack. html Application-Layer DDo. S Attacks n networks. rice. edu/papers/2006 -04 -Infocomfinal. ppt 31
c786784066210ceaefd272715dec441d.ppt