545c32417d3c430159db02affcc33eb3.ppt
- Количество слайдов: 31
 Ether: Malware Analysis via Hardware Virtualization Extensions Author: Artem Dinaburg, Paul Royal, Monirul Sharif, Wenke Lee Presenter: Yi Yang 1
Ether: Malware Analysis via Hardware Virtualization Extensions Author: Artem Dinaburg, Paul Royal, Monirul Sharif, Wenke Lee Presenter: Yi Yang 1
 Agenda ● Motivation ● Transparency Requirements ● Ether Framework ● Experiments and Evaluation ●Conclusion 2
Agenda ● Motivation ● Transparency Requirements ● Ether Framework ● Experiments and Evaluation ●Conclusion 2
 Motivation • Malware Definition: short for malicious software, is software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. • Malware Categories: computer viruses, worms, trojan horses, rootkits, spyware, adware, rogue security software, and other malicious programs. • Malware Problem: Malware has become the centerpiece of most security threats on the Internet 3
Motivation • Malware Definition: short for malicious software, is software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. • Malware Categories: computer viruses, worms, trojan horses, rootkits, spyware, adware, rogue security software, and other malicious programs. • Malware Problem: Malware has become the centerpiece of most security threats on the Internet 3
 Malware Analysis • There is a profound need to understand malware behavior: • -Forensics and Asset Remediation • -Threat Analysis • Malware authors make analysis very challenging • Direct financial motivation • Focal point of malware analysis: how to detect versus , how to hide a malware analyzer from malware during runtime 4
Malware Analysis • There is a profound need to understand malware behavior: • -Forensics and Asset Remediation • -Threat Analysis • Malware authors make analysis very challenging • Direct financial motivation • Focal point of malware analysis: how to detect versus , how to hide a malware analyzer from malware during runtime 4
 Two Types of Malware Analysis • • • Static Analysis What a program would do Complete view of program behavior Requires accurate disassembly of x 86 machine code Often impossible to do in practice Dynamic Analysis Shows what a program actually did when executed Only gives a partial view of program behavior Question: How do you hide your analyzer? 5
Two Types of Malware Analysis • • • Static Analysis What a program would do Complete view of program behavior Requires accurate disassembly of x 86 machine code Often impossible to do in practice Dynamic Analysis Shows what a program actually did when executed Only gives a partial view of program behavior Question: How do you hide your analyzer? 5
 The Malware Uncertainty Principle • An important practical problem • bserver affecting the observed environment • obust and detailed analyzers are typically invasive • Malware will refuse to run 6
The Malware Uncertainty Principle • An important practical problem • bserver affecting the observed environment • obust and detailed analyzers are typically invasive • Malware will refuse to run 6
 Solving Malware Uncertainty Principle • n analyzer’s aim should be transparent. • – efining transparency • The execution of the malware and the malware analyzer is governed by the principle of noninterference. 7
Solving Malware Uncertainty Principle • n analyzer’s aim should be transparent. • – efining transparency • The execution of the malware and the malware analyzer is governed by the principle of noninterference. 7
 Transparency Requirements • • • Higher Privilege No non-privileged side effects Same instruction execution semantics Transparent exception handling Identical notion of time 8
Transparency Requirements • • • Higher Privilege No non-privileged side effects Same instruction execution semantics Transparent exception handling Identical notion of time 8
 Fulfilling Transparency Requirements • • • Reduced Privilege Guests (VMWare, etc) – on-privileged side effects Emulation (full system emulator: QEMU) – nstruction execution semantics Idea: Use hardware assisted virtualization Poses complex analysis challenges 9
Fulfilling Transparency Requirements • • • Reduced Privilege Guests (VMWare, etc) – on-privileged side effects Emulation (full system emulator: QEMU) – nstruction execution semantics Idea: Use hardware assisted virtualization Poses complex analysis challenges 9
 Ether Framework • Software that can utilize hardware virtualization extensions: Xen hypervisor • Hardware virtualization platform: Intel VT • Target operating system : Windows XP 10
Ether Framework • Software that can utilize hardware virtualization extensions: Xen hypervisor • Hardware virtualization platform: Intel VT • Target operating system : Windows XP 10
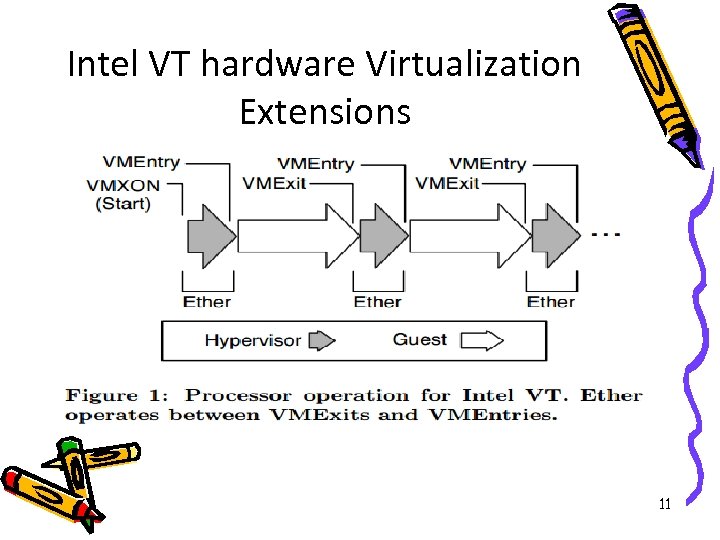 Intel VT hardware Virtualization Extensions 11
Intel VT hardware Virtualization Extensions 11
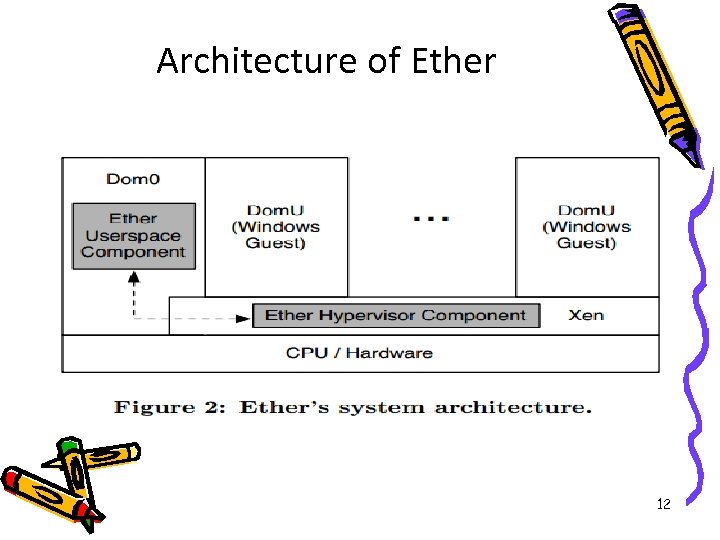 Architecture of Ether 12
Architecture of Ether 12
 Using Intel VT for Malware Analysis • Ether should be able to monitor some instructions • Instructions executed by a guest process, any memory writes a guest process performs, and any system calls a guest process makes. • Intel VT extensions do not provide support for these monitoring activities 13
Using Intel VT for Malware Analysis • Ether should be able to monitor some instructions • Instructions executed by a guest process, any memory writes a guest process performs, and any system calls a guest process makes. • Intel VT extensions do not provide support for these monitoring activities 13
 Monitoring Activities • Monitoring Instruction Execution • Monitoring Memory Writes • Monitoring System Call Execution 14
Monitoring Activities • Monitoring Instruction Execution • Monitoring Memory Writes • Monitoring System Call Execution 14
 Maintaining Analyzer Transparency • Despite making several modifications to the guest, Ether maintains transparency of the analyzer by ensuring such changes are undetectable 15
Maintaining Analyzer Transparency • Despite making several modifications to the guest, Ether maintains transparency of the analyzer by ensuring such changes are undetectable 15
 Potential Attacks • While theoretically resilient against in-guest detection attacks, current architectural restrictions make some of these attacks possible • Ether is vulnerable to a class of timing attacks using external timing sources • Detection methods : • In-Memory Presence • CPU Registers • Memory Protection • Privileged Instruction Handling • Instruction Emulation • Timing Attacks 16
Potential Attacks • While theoretically resilient against in-guest detection attacks, current architectural restrictions make some of these attacks possible • Ether is vulnerable to a class of timing attacks using external timing sources • Detection methods : • In-Memory Presence • CPU Registers • Memory Protection • Privileged Instruction Handling • Instruction Emulation • Timing Attacks 16
 Potential Attacks • While theoretically resilient against in-guest detection attacks, current architectural restrictions make some of these attacks possible • Ether is vulnerable to a class of timing attacks using external timing sources • Detection methods : • In-Memory Presence • CPU Registers • Memory Protection • Privileged Instruction Handling • Instruction Emulation • Timing Attacks 17
Potential Attacks • While theoretically resilient against in-guest detection attacks, current architectural restrictions make some of these attacks possible • Ether is vulnerable to a class of timing attacks using external timing sources • Detection methods : • In-Memory Presence • CPU Registers • Memory Protection • Privileged Instruction Handling • Instruction Emulation • Timing Attacks 17
 Architectural Limitation • Intel VT suffers from some architectural limitations which may allow Ether to be detected under certain circumstances. • Different hardware virtualization extensions exist that do not suffer from such limitations. • Intel VT suffers from two main flaws which allow the current implementation to be detected by observing implicit changes to the memory hierarchy: • Intel flushed the TLB on every VMExit; • Paging mode must be turned on before entering VMX Root code. 18
Architectural Limitation • Intel VT suffers from some architectural limitations which may allow Ether to be detected under certain circumstances. • Different hardware virtualization extensions exist that do not suffer from such limitations. • Intel VT suffers from two main flaws which allow the current implementation to be detected by observing implicit changes to the memory hierarchy: • Intel flushed the TLB on every VMExit; • Paging mode must be turned on before entering VMX Root code. 18
 Experiments and Evaluation • Two tools based on Ether: Ether. Unpack and Ether. Trace. • Ether. Unpack traces memory writes and single instructions (i. e. , fine-grained tracing) • Ether. Trace traces system calls (i. e. , coarsegrained tracing). • Using these tools to evaluate Ether and compare • it against current approaches. 19
Experiments and Evaluation • Two tools based on Ether: Ether. Unpack and Ether. Trace. • Ether. Unpack traces memory writes and single instructions (i. e. , fine-grained tracing) • Ether. Trace traces system calls (i. e. , coarsegrained tracing). • Using these tools to evaluate Ether and compare • it against current approaches. 19
 Experiments and Evaluation • Two tools based on Ether: Ether. Unpack and Ether. Trace. • Ether. Unpack traces memory writes and single instructions (i. e. , fine-grained tracing) • Ether. Trace traces system calls (i. e. , coarsegrained tracing). • Using these tools to evaluate Ether and compare • it against current approaches. 20
Experiments and Evaluation • Two tools based on Ether: Ether. Unpack and Ether. Trace. • Ether. Unpack traces memory writes and single instructions (i. e. , fine-grained tracing) • Ether. Trace traces system calls (i. e. , coarsegrained tracing). • Using these tools to evaluate Ether and compare • it against current approaches. 20
 Packing vs Unpacking • Packing is a term used to describe the obfuscation and encryption of program code to thwart static analysis. • The result of packing is that signature-based approaches fail to identify packed malware as malicious. • Opposite to packers, unpackers are programs which attempt to obtain the original code hidden by the packer. 21
Packing vs Unpacking • Packing is a term used to describe the obfuscation and encryption of program code to thwart static analysis. • The result of packing is that signature-based approaches fail to identify packed malware as malicious. • Opposite to packers, unpackers are programs which attempt to obtain the original code hidden by the packer. 21
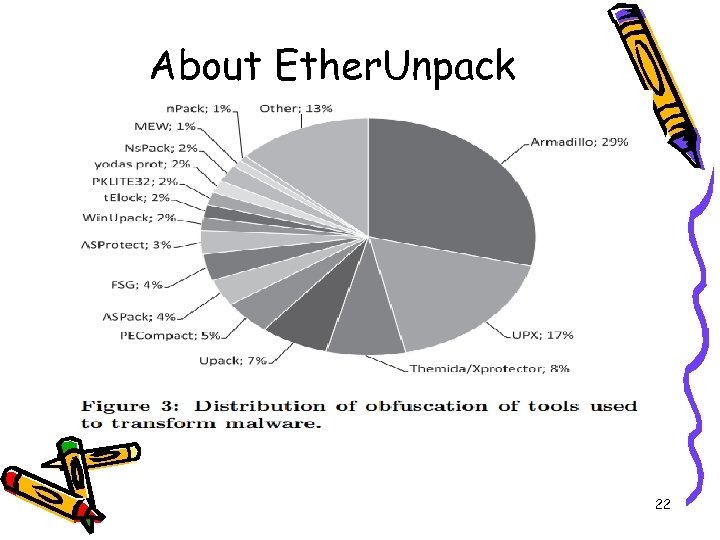 About Ether. Unpack 22
About Ether. Unpack 22
 About Ether. Unpack • Precision universal automated unpacker • Uses instruction-by-instruction tracing (fine grained tracing) to detect unpack execute behavior • If code written is later executed, unpack execution occurred • Able to handle multiple packing layers • umps unpacked memory images to disk 23
About Ether. Unpack • Precision universal automated unpacker • Uses instruction-by-instruction tracing (fine grained tracing) to detect unpack execute behavior • If code written is later executed, unpack execution occurred • Able to handle multiple packing layers • umps unpacked memory images to disk 23
 Evaluation: Ether. Unpack • Looked for a 32 byte string present in the original code section • Not a random string 24
Evaluation: Ether. Unpack • Looked for a 32 byte string present in the original code section • Not a random string 24
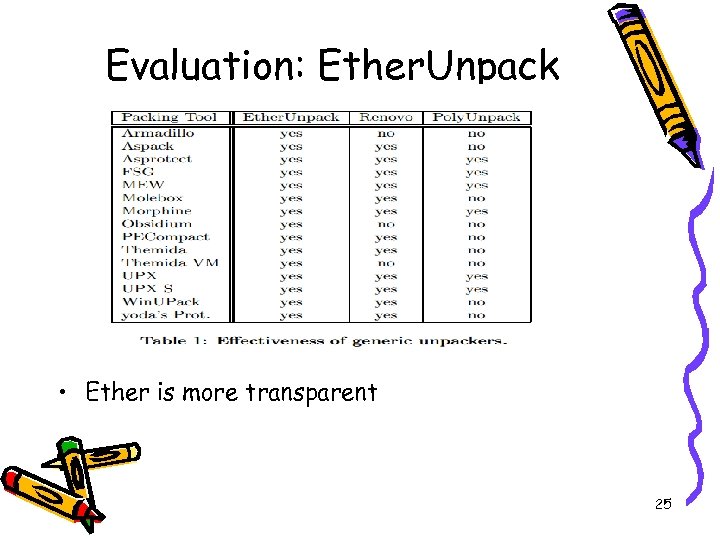 Evaluation: Ether. Unpack • Ether is more transparent 25
Evaluation: Ether. Unpack • Ether is more transparent 25
 About Ether. Trace • An implementation of a coarse grained tracer using the Ether framework • Traces the Windows equivalent of system calls (Native API) • Information Provided: • – Call name • – Typed arguments • – Return values • – Context (Process ID, Thread ID) 26
About Ether. Trace • An implementation of a coarse grained tracer using the Ether framework • Traces the Windows equivalent of system calls (Native API) • Information Provided: • – Call name • – Typed arguments • – Return values • – Context (Process ID, Thread ID) 26
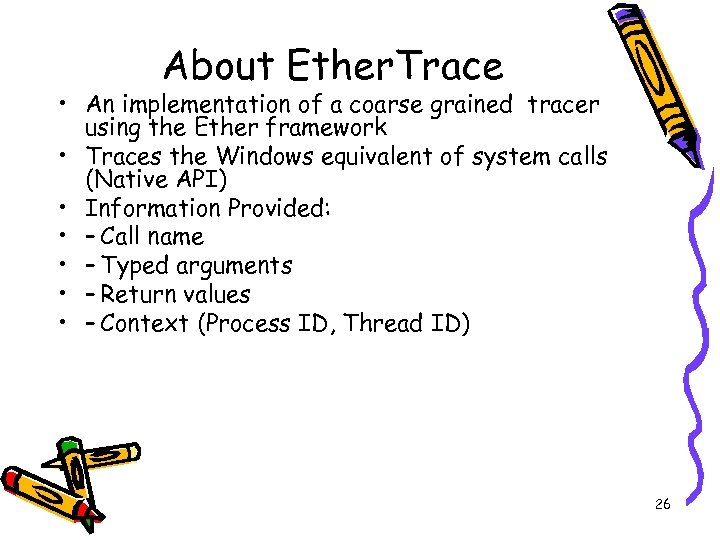
 Evaluation: Ether. Trace • Examine trace logs for expected actions • – File • – Registry 27
Evaluation: Ether. Trace • Examine trace logs for expected actions • – File • – Registry 27
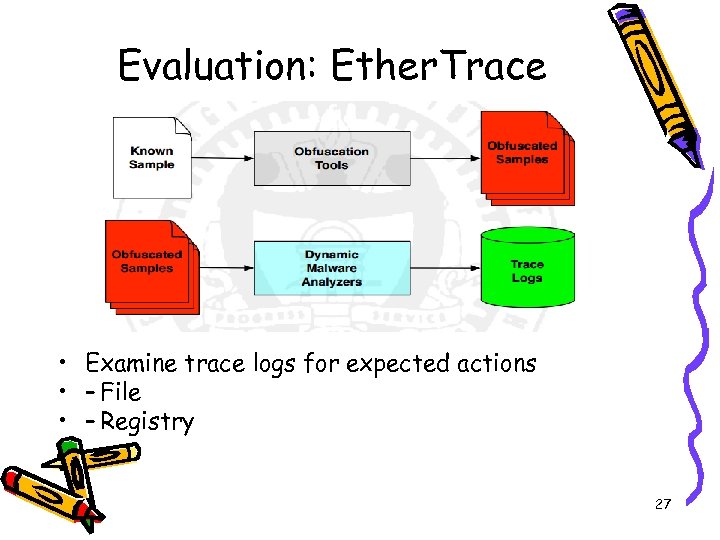
 Evaluation: Ether. Trace • Ether is more transparent 28
Evaluation: Ether. Trace • Ether is more transparent 28
 Conclusion • Ether, a transparent and external malware analyzer that is based on hardware virtualization extensions such as Intel VT. • Ether is an implementation of a different approach • Evaluation confirms Ether is more transparent • Theoretically, can do better: • improving resistance to timing attacks and memory hierarchy detection attacks. 29
Conclusion • Ether, a transparent and external malware analyzer that is based on hardware virtualization extensions such as Intel VT. • Ether is an implementation of a different approach • Evaluation confirms Ether is more transparent • Theoretically, can do better: • improving resistance to timing attacks and memory hierarchy detection attacks. 29
 Reference • http: //ether. gtisc. gatech. edu/ 30
Reference • http: //ether. gtisc. gatech. edu/ 30
 Questions? 31
Questions? 31


