95b7a03ed6b651a7506c4a0a3d49f691.ppt
- Количество слайдов: 110
 Essays on using Formal Concept Analysis in Information Engineering AA Jonas Poelmans, Aspirant FWO Katholieke Universiteit Leuven Inno. com February 2011
Essays on using Formal Concept Analysis in Information Engineering AA Jonas Poelmans, Aspirant FWO Katholieke Universiteit Leuven Inno. com February 2011
 Outline 1. Formal Concept Analysis 2. FCA in data mining 2. 1 Literature study 2. 2 Domestic violence case study 3. FCA for mining temporal data 3. 1 Human trafficking 3. 2 Terrorist threat assessment 3. 3 Integrated care pathways 4. Future research
Outline 1. Formal Concept Analysis 2. FCA in data mining 2. 1 Literature study 2. 2 Domestic violence case study 3. FCA for mining temporal data 3. 1 Human trafficking 3. 2 Terrorist threat assessment 3. 3 Integrated care pathways 4. Future research
 Formal Concept Analysis (FCA) • • Initially a mathematical technique Visually represents the concepts available in the data Now: used as exploratory data analysis technique Starting point: cross table Rows: contain the objects Columns: contain the attributes Crosses: relationships between the objects and the attributes
Formal Concept Analysis (FCA) • • Initially a mathematical technique Visually represents the concepts available in the data Now: used as exploratory data analysis technique Starting point: cross table Rows: contain the objects Columns: contain the attributes Crosses: relationships between the objects and the attributes
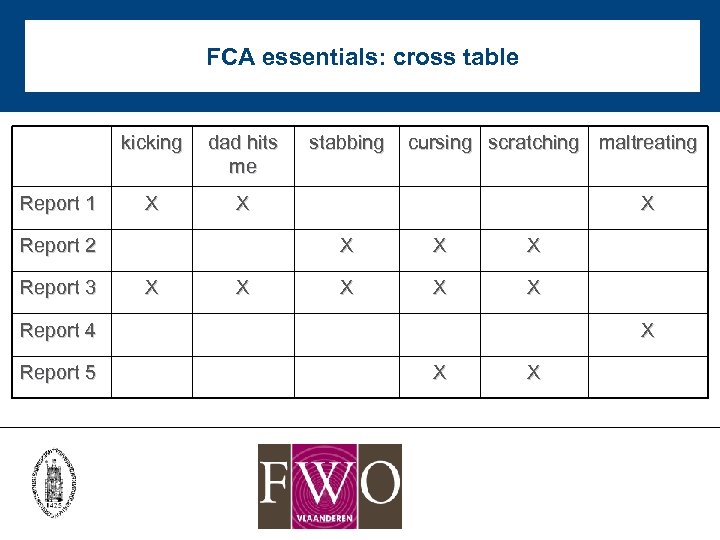 FCA essentials: cross table kicking Report 1 dad hits me X X Report 2 Report 3 stabbing cursing scratching maltreating X X X X X Report 4 Report 5 X X X
FCA essentials: cross table kicking Report 1 dad hits me X X Report 2 Report 3 stabbing cursing scratching maltreating X X X X X Report 4 Report 5 X X X
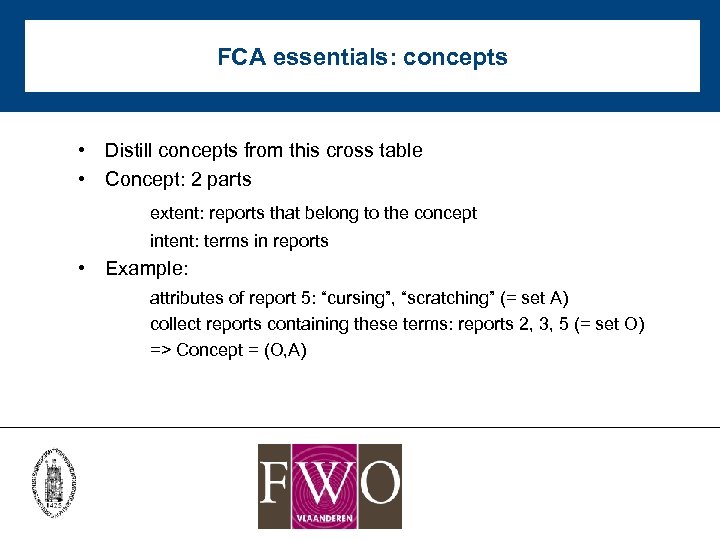 FCA essentials: concepts • Distill concepts from this cross table • Concept: 2 parts extent: reports that belong to the concept intent: terms in reports • Example: attributes of report 5: “cursing”, “scratching” (= set A) collect reports containing these terms: reports 2, 3, 5 (= set O) => Concept = (O, A)
FCA essentials: concepts • Distill concepts from this cross table • Concept: 2 parts extent: reports that belong to the concept intent: terms in reports • Example: attributes of report 5: “cursing”, “scratching” (= set A) collect reports containing these terms: reports 2, 3, 5 (= set O) => Concept = (O, A)
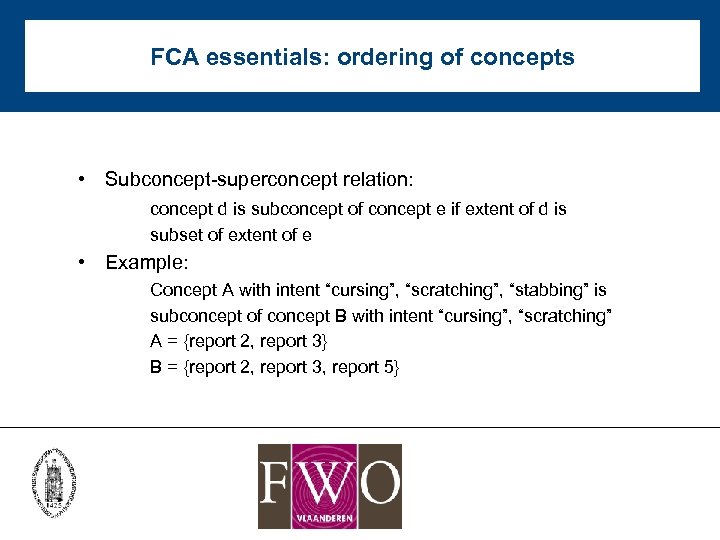 FCA essentials: ordering of concepts • Subconcept-superconcept relation: concept d is subconcept of concept e if extent of d is subset of extent of e • Example: Concept A with intent “cursing”, “scratching”, “stabbing” is subconcept of concept B with intent “cursing”, “scratching” A = {report 2, report 3} B = {report 2, report 3, report 5}
FCA essentials: ordering of concepts • Subconcept-superconcept relation: concept d is subconcept of concept e if extent of d is subset of extent of e • Example: Concept A with intent “cursing”, “scratching”, “stabbing” is subconcept of concept B with intent “cursing”, “scratching” A = {report 2, report 3} B = {report 2, report 3, report 5}
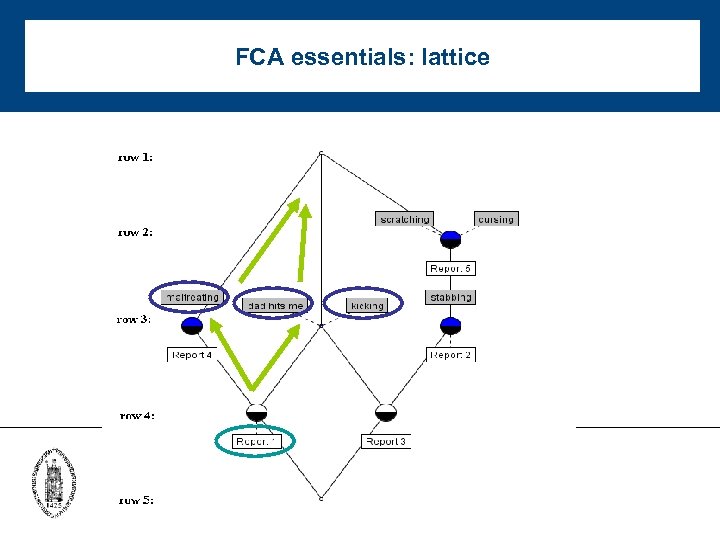 FCA essentials: lattice
FCA essentials: lattice
 Literature study • 702 papers on FCA published between 2003 -2009 • FCA is used to: cluster papers visually represent clusters and their relationships explore data • Cross table: objects = papers attributes = terms crosses = terms occuring in abstract of papers
Literature study • 702 papers on FCA published between 2003 -2009 • FCA is used to: cluster papers visually represent clusters and their relationships explore data • Cross table: objects = papers attributes = terms crosses = terms occuring in abstract of papers
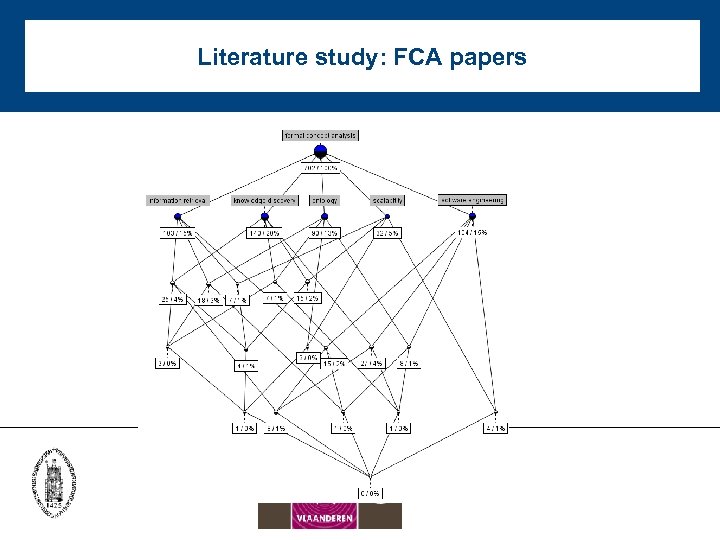 Literature study: FCA papers
Literature study: FCA papers
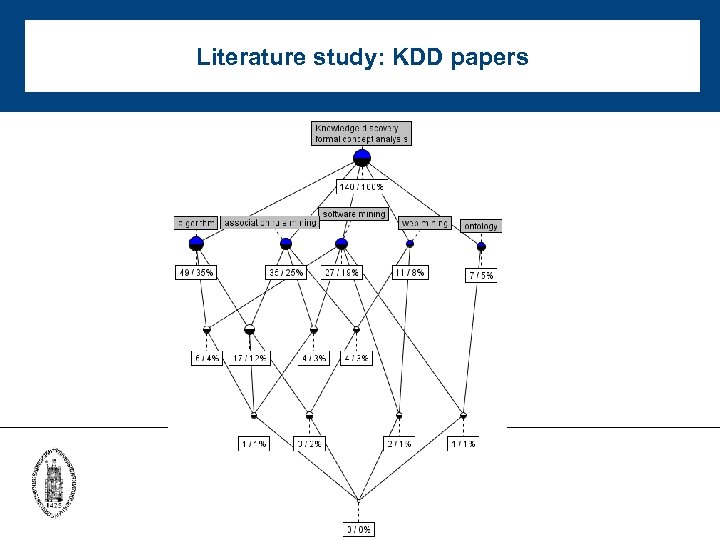 Literature study: KDD papers
Literature study: KDD papers
 Domestic violence case study • • Many theoretical papers Relatively few real life applications Now: FCA used as exploratory data analysis technique Aim: exploring and refining the concept of domestic violence to improve detection & handling of domestic violence cases
Domestic violence case study • • Many theoretical papers Relatively few real life applications Now: FCA used as exploratory data analysis technique Aim: exploring and refining the concept of domestic violence to improve detection & handling of domestic violence cases
 Emergent Self Organising Map (ESOM) ESOM: – – Topographic map Visualizing sparse high-dimensional datasets Now: used as exploratory data analysis technique Aim: exploring and refining the concept of domestic violence to improve detection and handling of domestic violence cases
Emergent Self Organising Map (ESOM) ESOM: – – Topographic map Visualizing sparse high-dimensional datasets Now: used as exploratory data analysis technique Aim: exploring and refining the concept of domestic violence to improve detection and handling of domestic violence cases
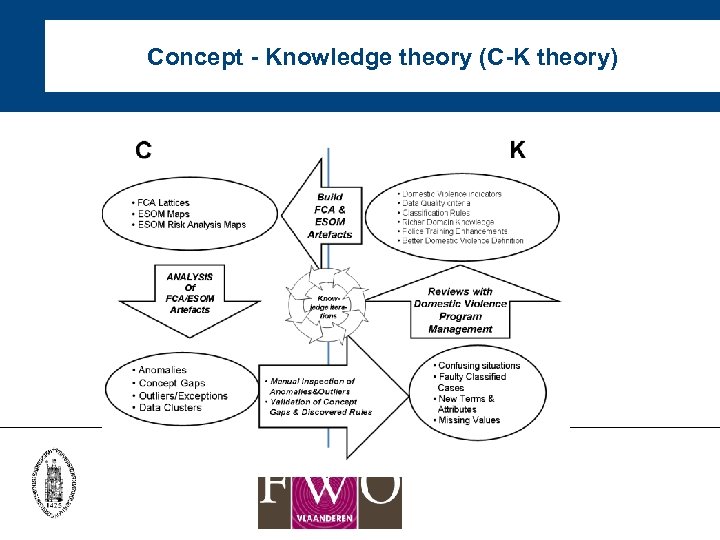 Concept - Knowledge theory (C-K theory)
Concept - Knowledge theory (C-K theory)
 Motivation • 1997: first inquiry into nature and scope of domestic violence. • 45% of population once fell victim to non-incidental domestic violence. • 27% of population: incidents occurred on a weekly or daily basis. • Pivotal project of Prime Minister Balkenende administration.
Motivation • 1997: first inquiry into nature and scope of domestic violence. • 45% of population once fell victim to non-incidental domestic violence. • 27% of population: incidents occurred on a weekly or daily basis. • Pivotal project of Prime Minister Balkenende administration.
 Dataset Selection of 4814 police reports from year 2007 Collection of terms: “kicking”, “mother”, “child”, etc. Each report is associated with a subset of terms. Title of incident …. Reporting of the crime Last night I was attacked by my husband. I was watching television in the living room when he suddenly attacked me with a knife. I fell on the floor. Then he tried to kick me in my stomach. I tried to escape through the back door while I was yelling for help. I ran to the neighbours for help. They called the emergency services. Meanwhile my son ran away. My leg was bleeding; my head was bouncing, etc.
Dataset Selection of 4814 police reports from year 2007 Collection of terms: “kicking”, “mother”, “child”, etc. Each report is associated with a subset of terms. Title of incident …. Reporting of the crime Last night I was attacked by my husband. I was watching television in the living room when he suddenly attacked me with a knife. I fell on the floor. Then he tried to kick me in my stomach. I tried to escape through the back door while I was yelling for help. I ran to the neighbours for help. They called the emergency services. Meanwhile my son ran away. My leg was bleeding; my head was bouncing, etc.
 Domestic violence definition 3 components: – Perpetrator is member of domestic sphere of victim: partners, ex-partners, family members, relatives, family friends – Act of violence: physical assault, sexual harassment, threatening – Dependency relationship between perpetrator and victim
Domestic violence definition 3 components: – Perpetrator is member of domestic sphere of victim: partners, ex-partners, family members, relatives, family friends – Act of violence: physical assault, sexual harassment, threatening – Dependency relationship between perpetrator and victim
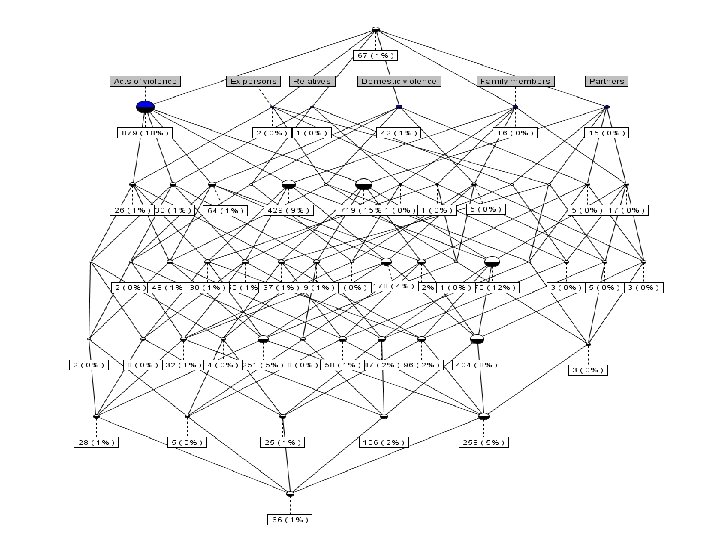
 Clustering terms for FCA Terms grouped together in clusters based on domestic violence definition: “kicking”, “scratching”, “maltreating”, etc. – ‘acts of violence’ “aunt”, “uncle”, “nephew”, etc. – ‘relatives’ “father”, “mother”, “son”, etc. – ‘family members’ etc.
Clustering terms for FCA Terms grouped together in clusters based on domestic violence definition: “kicking”, “scratching”, “maltreating”, etc. – ‘acts of violence’ “aunt”, “uncle”, “nephew”, etc. – ‘relatives’ “father”, “mother”, “son”, etc. – ‘family members’ etc.
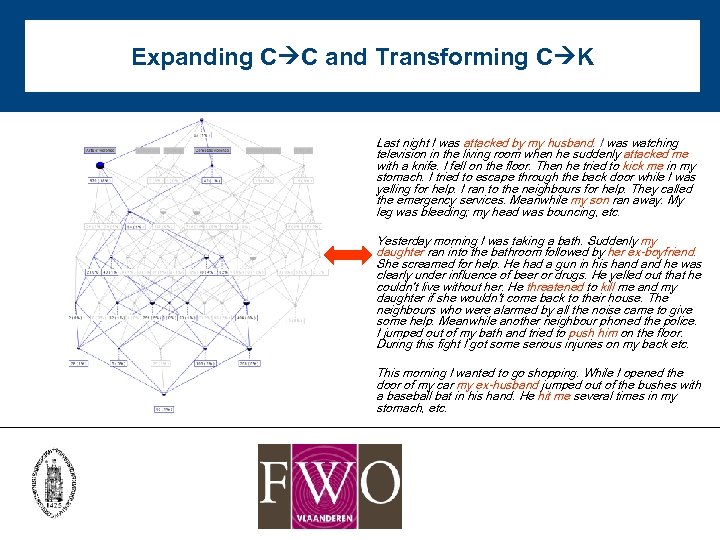 Expanding C C and Transforming C K Last night I was attacked by my husband. I was watching television in the living room when he suddenly attacked me with a knife. I fell on the floor. Then he tried to kick me in my stomach. I tried to escape through the back door while I was yelling for help. I ran to the neighbours for help. They called the emergency services. Meanwhile my son ran away. My leg was bleeding; my head was bouncing, etc. Yesterday morning I was taking a bath. Suddenly my daughter ran into the bathroom followed by her ex-boyfriend. She screamed for help. He had a gun in his hand he was clearly under influence of beer or drugs. He yelled out that he couldn’t live without her. He threatened to kill me and my daughter if she wouldn’t come back to their house. The neighbours who were alarmed by all the noise came to give some help. Meanwhile another neighbour phoned the police. I jumped out of my bath and tried to push him on the floor. During this fight I got some serious injuries on my back etc. This morning I wanted to go shopping. While I opened the door of my car my ex-husband jumped out of the bushes with a baseball bat in his hand. He hit me several times in my stomach, etc.
Expanding C C and Transforming C K Last night I was attacked by my husband. I was watching television in the living room when he suddenly attacked me with a knife. I fell on the floor. Then he tried to kick me in my stomach. I tried to escape through the back door while I was yelling for help. I ran to the neighbours for help. They called the emergency services. Meanwhile my son ran away. My leg was bleeding; my head was bouncing, etc. Yesterday morning I was taking a bath. Suddenly my daughter ran into the bathroom followed by her ex-boyfriend. She screamed for help. He had a gun in his hand he was clearly under influence of beer or drugs. He yelled out that he couldn’t live without her. He threatened to kill me and my daughter if she wouldn’t come back to their house. The neighbours who were alarmed by all the noise came to give some help. Meanwhile another neighbour phoned the police. I jumped out of my bath and tried to push him on the floor. During this fight I got some serious injuries on my back etc. This morning I wanted to go shopping. While I opened the door of my car my ex-husband jumped out of the bushes with a baseball bat in his hand. He hit me several times in my stomach, etc.
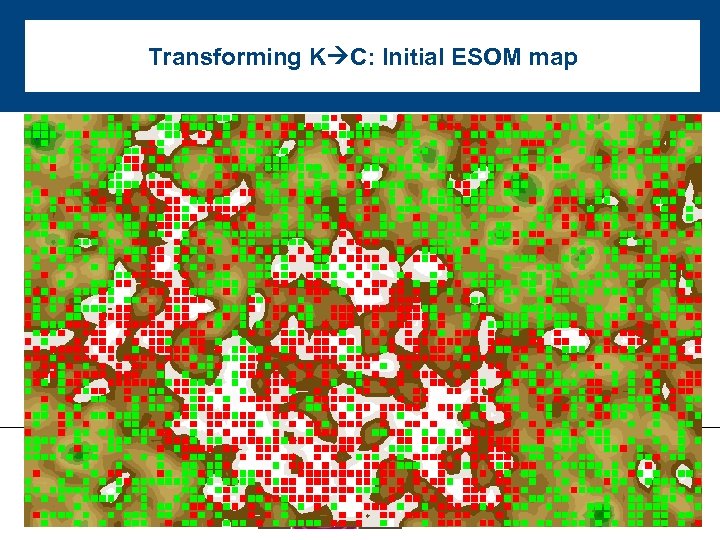 Transforming K C: Initial ESOM map
Transforming K C: Initial ESOM map
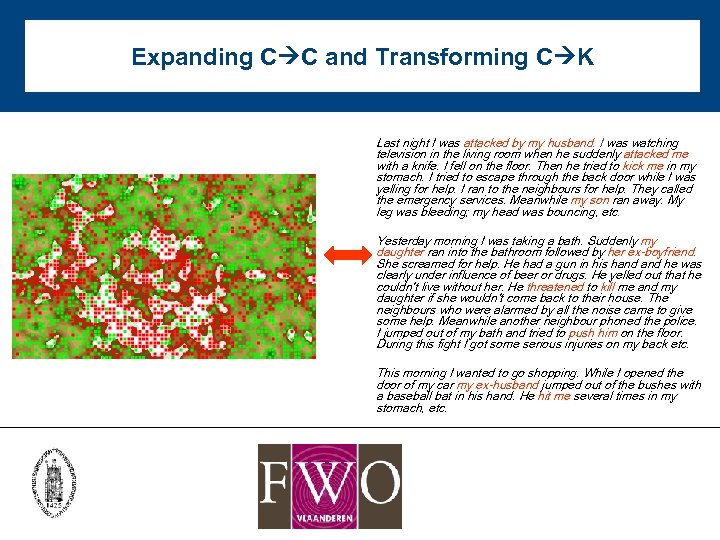 Expanding C C and Transforming C K Last night I was attacked by my husband. I was watching television in the living room when he suddenly attacked me with a knife. I fell on the floor. Then he tried to kick me in my stomach. I tried to escape through the back door while I was yelling for help. I ran to the neighbours for help. They called the emergency services. Meanwhile my son ran away. My leg was bleeding; my head was bouncing, etc. Yesterday morning I was taking a bath. Suddenly my daughter ran into the bathroom followed by her ex-boyfriend. She screamed for help. He had a gun in his hand he was clearly under influence of beer or drugs. He yelled out that he couldn’t live without her. He threatened to kill me and my daughter if she wouldn’t come back to their house. The neighbours who were alarmed by all the noise came to give some help. Meanwhile another neighbour phoned the police. I jumped out of my bath and tried to push him on the floor. During this fight I got some serious injuries on my back etc. This morning I wanted to go shopping. While I opened the door of my car my ex-husband jumped out of the bushes with a baseball bat in his hand. He hit me several times in my stomach, etc.
Expanding C C and Transforming C K Last night I was attacked by my husband. I was watching television in the living room when he suddenly attacked me with a knife. I fell on the floor. Then he tried to kick me in my stomach. I tried to escape through the back door while I was yelling for help. I ran to the neighbours for help. They called the emergency services. Meanwhile my son ran away. My leg was bleeding; my head was bouncing, etc. Yesterday morning I was taking a bath. Suddenly my daughter ran into the bathroom followed by her ex-boyfriend. She screamed for help. He had a gun in his hand he was clearly under influence of beer or drugs. He yelled out that he couldn’t live without her. He threatened to kill me and my daughter if she wouldn’t come back to their house. The neighbours who were alarmed by all the noise came to give some help. Meanwhile another neighbour phoned the police. I jumped out of my bath and tried to push him on the floor. During this fight I got some serious injuries on my back etc. This morning I wanted to go shopping. While I opened the door of my car my ex-husband jumped out of the bushes with a baseball bat in his hand. He hit me several times in my stomach, etc.
 Expanding K K: Newly discovered features Pepper spray Homosexual relationship, lesbian relationship Sexual abuse, incest Alternative spelling of some words (e. g. ex-boyfriend, ex boyfriend) Violence terms lacking in thesaurus: abduction, choke, strangle, etc. Weapons lacking in thesaurus: belt, kitchen knife, baseball bat, etc. Terms referring to persons: partner, fiancée, mistress, concubine, man next door, etc. Terms referring to relationships: romance, love affair, marriage problems, divorce proceedings, etc. Reception centers: woman’s refuge center, home for battered woman, etc. Terms referring to an extra marital affair: I have an another man, lover, I am unfaithful, etc.
Expanding K K: Newly discovered features Pepper spray Homosexual relationship, lesbian relationship Sexual abuse, incest Alternative spelling of some words (e. g. ex-boyfriend, ex boyfriend) Violence terms lacking in thesaurus: abduction, choke, strangle, etc. Weapons lacking in thesaurus: belt, kitchen knife, baseball bat, etc. Terms referring to persons: partner, fiancée, mistress, concubine, man next door, etc. Terms referring to relationships: romance, love affair, marriage problems, divorce proceedings, etc. Reception centers: woman’s refuge center, home for battered woman, etc. Terms referring to an extra marital affair: I have an another man, lover, I am unfaithful, etc.
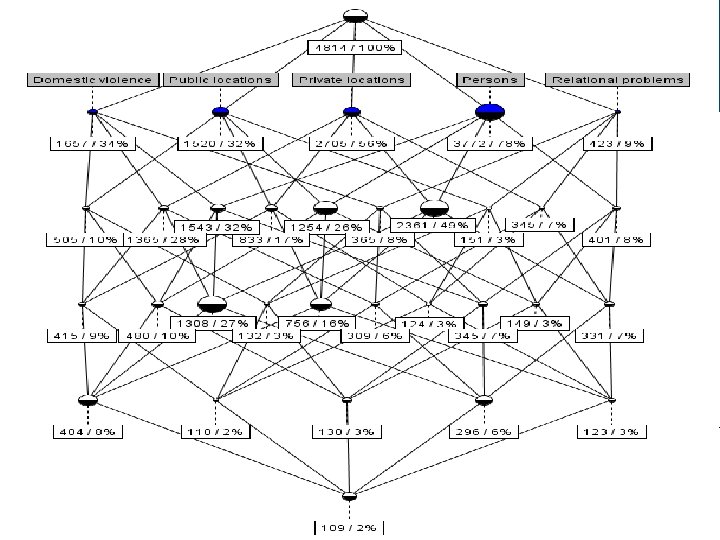
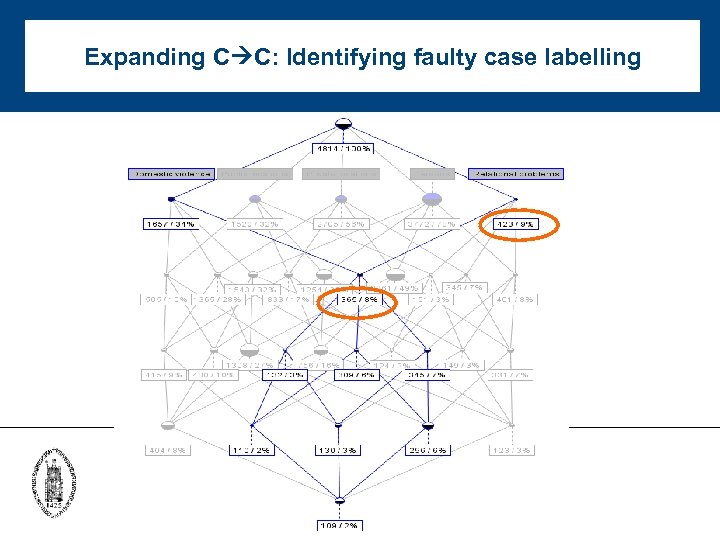 Expanding C C: Identifying faulty case labelling
Expanding C C: Identifying faulty case labelling
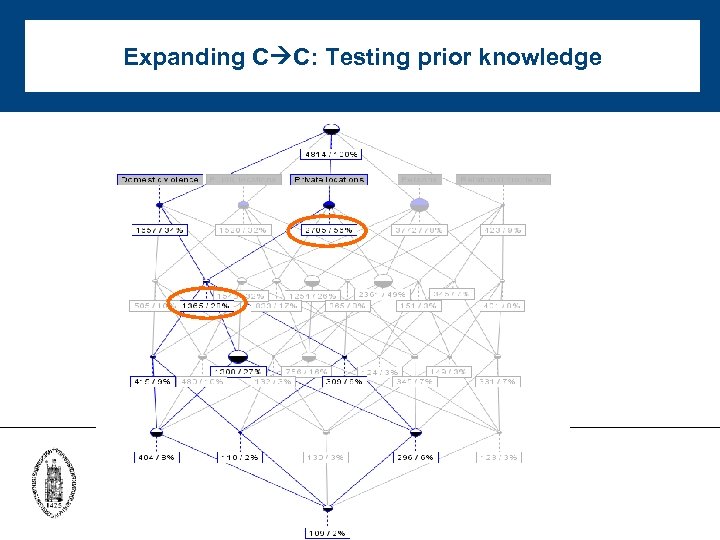 Expanding C C: Testing prior knowledge
Expanding C C: Testing prior knowledge
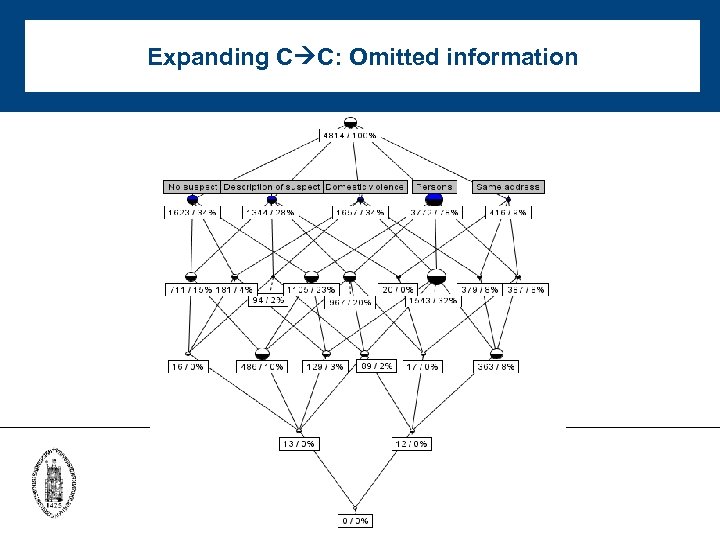 Expanding C C: Omitted information
Expanding C C: Omitted information
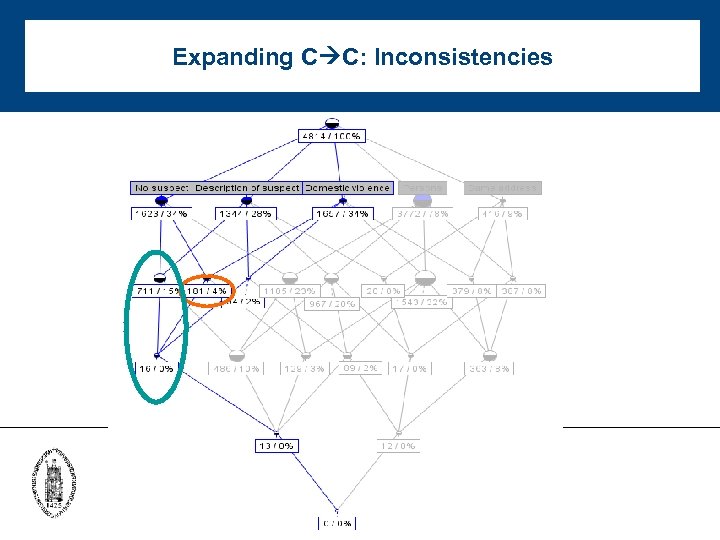 Expanding C C: Inconsistencies
Expanding C C: Inconsistencies
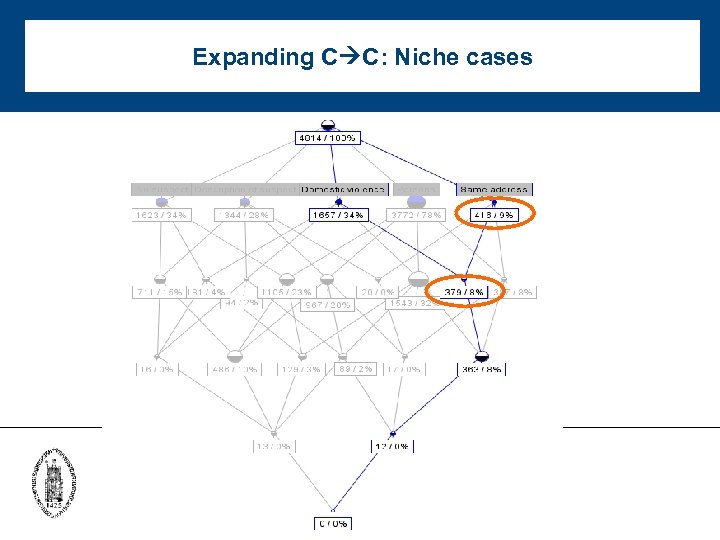 Expanding C C: Niche cases
Expanding C C: Niche cases
 Expanding K K: Omitted information and faulty case labellings - Burglary cases No suspect in domestic violence cases Third person makes statement to police Violence between a caretaker and an inhabitant of an institution
Expanding K K: Omitted information and faulty case labellings - Burglary cases No suspect in domestic violence cases Third person makes statement to police Violence between a caretaker and an inhabitant of an institution
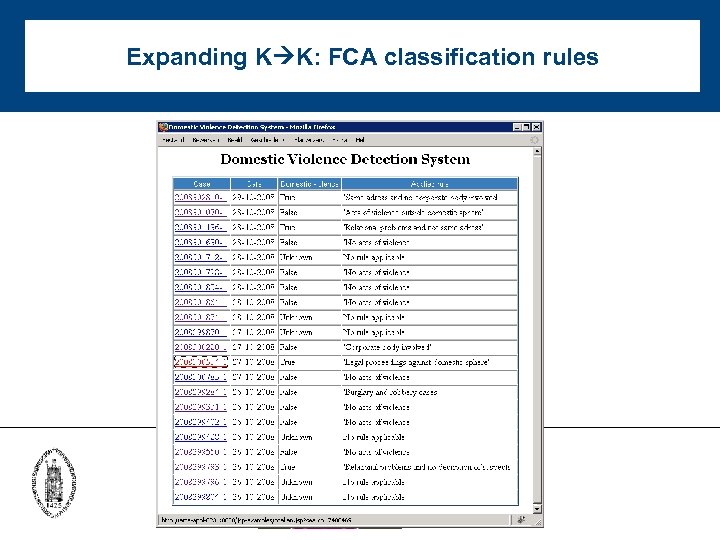 Expanding K K: FCA classification rules
Expanding K K: FCA classification rules
 FCA results: classification rules - 22 domestic violence and 15 non-domestic violence classification rules: label automatically and correctly 75% of incoming cases
FCA results: classification rules - 22 domestic violence and 15 non-domestic violence classification rules: label automatically and correctly 75% of incoming cases
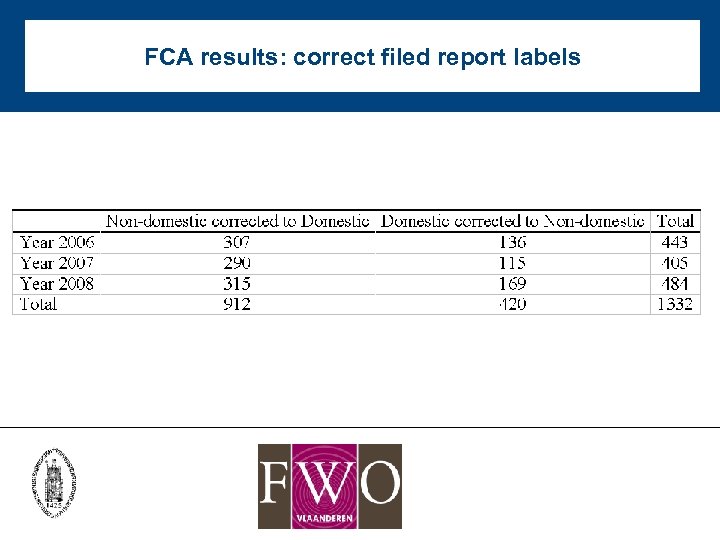 FCA results: correct filed report labels
FCA results: correct filed report labels
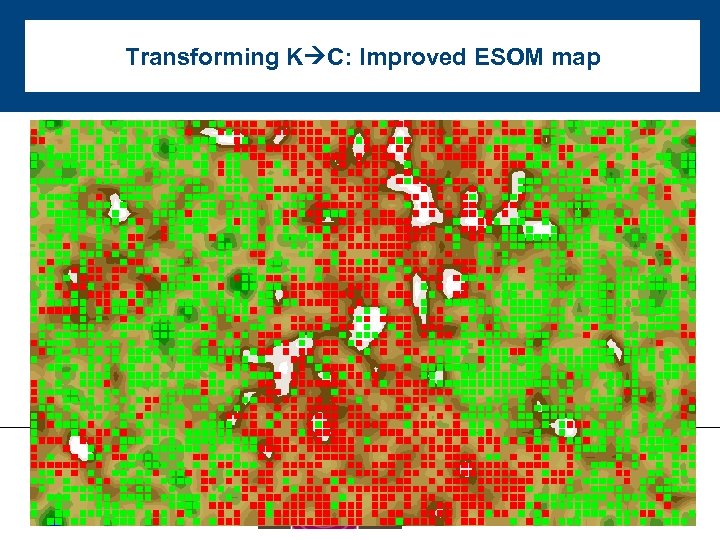 Transforming K C: Improved ESOM map
Transforming K C: Improved ESOM map
 Expanding K K: Confusing situations for police officers - Lover boys - Extramarital relationship - Violence between a caretaker and an inhabitant of an institution - Violence between colleagues - An ex-boyfriend attacks the new boyfriend - Third person makes statement to the police for somebody else
Expanding K K: Confusing situations for police officers - Lover boys - Extramarital relationship - Violence between a caretaker and an inhabitant of an institution - Violence between colleagues - An ex-boyfriend attacks the new boyfriend - Third person makes statement to the police for somebody else
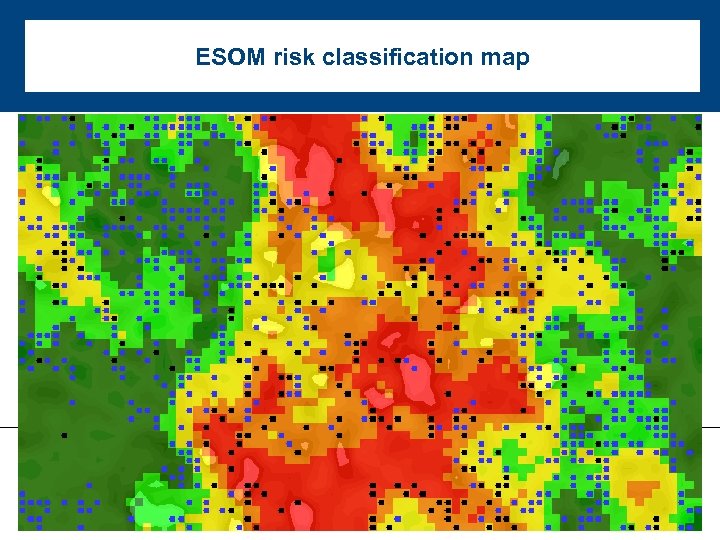 ESOM risk classification map
ESOM risk classification map
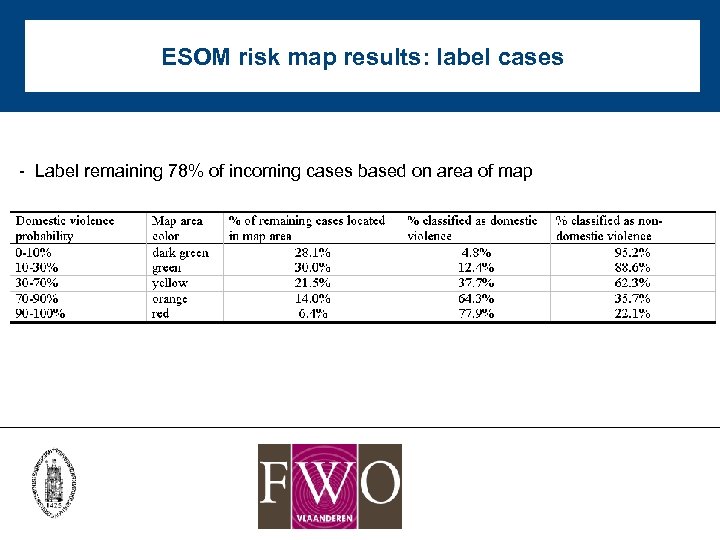 ESOM risk map results: label cases - Label remaining 78% of incoming cases based on area of map
ESOM risk map results: label cases - Label remaining 78% of incoming cases based on area of map
 FCA & ESOM results - Automatically label 91% of incoming cases correctly - Improved police training - Upgraded domestic violence definition - Identification of niche cases - Data quality improvement
FCA & ESOM results - Automatically label 91% of incoming cases correctly - Improved police training - Upgraded domestic violence definition - Identification of niche cases - Data quality improvement
 Conclusions • Combination of FCA & ESOM showcased as exploratory data analysis technique, with success • Refinement of the concept ‘domestic violence’ • Accurate case classification model
Conclusions • Combination of FCA & ESOM showcased as exploratory data analysis technique, with success • Refinement of the concept ‘domestic violence’ • Accurate case classification model
 Human trafficking • recruitment, transportation, harboring and receipt of people for slavery, forced labor and servitude • fastest growing criminal industry in the world • global annual market of 42. 5 billion • 700 000 to 2 million women and girls are trafficked across international borders every year
Human trafficking • recruitment, transportation, harboring and receipt of people for slavery, forced labor and servitude • fastest growing criminal industry in the world • global annual market of 42. 5 billion • 700 000 to 2 million women and girls are trafficked across international borders every year
 Human trafficking (2) • majority of victims are trafficked in commercial sexual exploitation • threats, violence, coercion, deception, abuse of power make victim consent to exploitation • victims of human trafficking rarely make official statement to the police • human trafficking team is installed to proactively search police database for signals of human trafficking
Human trafficking (2) • majority of victims are trafficked in commercial sexual exploitation • threats, violence, coercion, deception, abuse of power make victim consent to exploitation • victims of human trafficking rarely make official statement to the police • human trafficking team is installed to proactively search police database for signals of human trafficking
 Police challenges • databases contain large amount of observational reports • 10% of information containing human trafficking indicators is labeled as such by police officers • documents are spread over multiple database systems • limited browsing functionality is provided. • currently: officers have to search all these databases and manually inspect reports for indications
Police challenges • databases contain large amount of observational reports • 10% of information containing human trafficking indicators is labeled as such by police officers • documents are spread over multiple database systems • limited browsing functionality is provided. • currently: officers have to search all these databases and manually inspect reports for indications
 Investigation procedure • collect sufficient evidence and indications against potential suspect • construct document based on section 273 f of the code of criminal law • send request to Public Prosecutor to start in-depth investigation
Investigation procedure • collect sufficient evidence and indications against potential suspect • construct document based on section 273 f of the code of criminal law • send request to Public Prosecutor to start in-depth investigation
 Dataset • 69 788 general reports from 2008 • observations made by police officers during motor vehicle inspections, police patrols, etc.
Dataset • 69 788 general reports from 2008 • observations made by police officers during motor vehicle inspections, police patrols, etc.
 Temporal Concept Analysis (TCA) TCA: – Based on FCA – Addresses the problem of representing time – Is particularly suited as for visual representation of discrete temporal phenomena
Temporal Concept Analysis (TCA) TCA: – Based on FCA – Addresses the problem of representing time – Is particularly suited as for visual representation of discrete temporal phenomena
 Analysis method • FCA: – identify early warning indicators in police reports – detect and extract potential trafficking suspects • TCA: – profiling potential suspects and their evolution over time – gaining insight in their social network
Analysis method • FCA: – identify early warning indicators in police reports – detect and extract potential trafficking suspects • TCA: – profiling potential suspects and their evolution over time – gaining insight in their social network
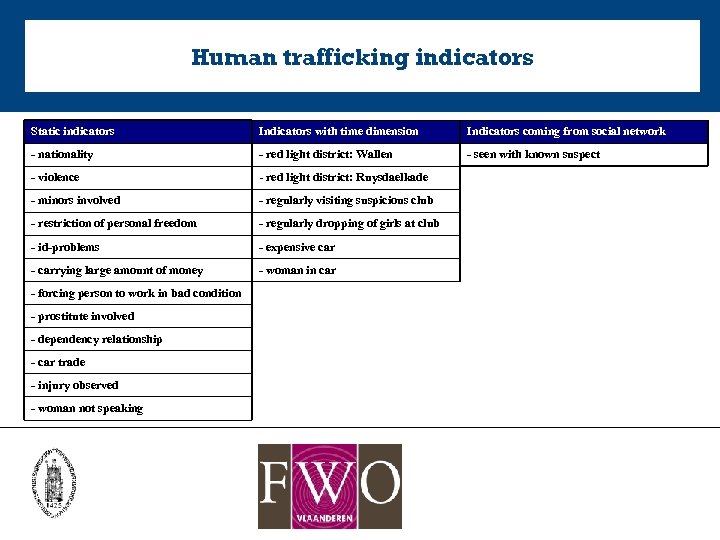 Human trafficking indicators Static indicators Indicators with time dimension Indicators coming from social network - nationality - red light district: Wallen - seen with known suspect - violence - red light district: Ruysdaelkade - minors involved - regularly visiting suspicious club - restriction of personal freedom - regularly dropping of girls at club - id-problems - expensive car - carrying large amount of money - woman in car - forcing person to work in bad condition - prostitute involved - dependency relationship - car trade - injury observed - woman not speaking
Human trafficking indicators Static indicators Indicators with time dimension Indicators coming from social network - nationality - red light district: Wallen - seen with known suspect - violence - red light district: Ruysdaelkade - minors involved - regularly visiting suspicious club - restriction of personal freedom - regularly dropping of girls at club - id-problems - expensive car - carrying large amount of money - woman in car - forcing person to work in bad condition - prostitute involved - dependency relationship - car trade - injury observed - woman not speaking
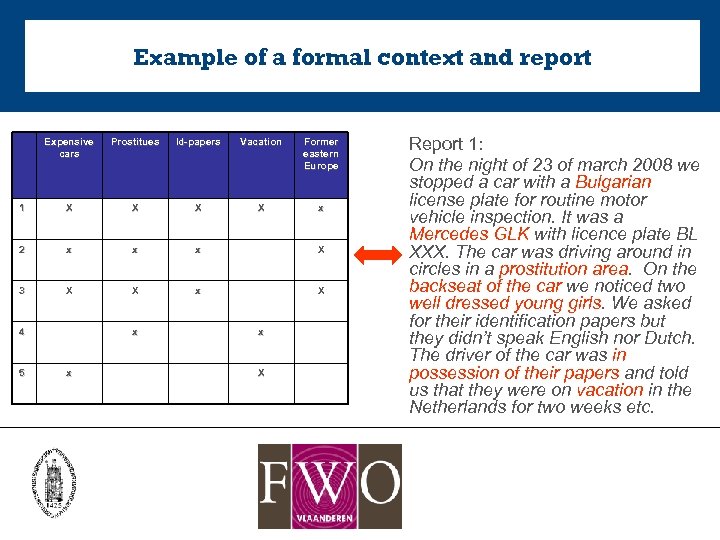 Example of a formal context and report Expensive cars Prostitues Id-papers Vacation Former eastern Europe 1 X X x 2 x x x X 3 X X x X 4 5 x x x X Report 1: On the night of 23 of march 2008 we stopped a car with a Bulgarian license plate for routine motor vehicle inspection. It was a Mercedes GLK with licence plate BL XXX. The car was driving around in circles in a prostitution area. On the backseat of the car we noticed two well dressed young girls. We asked for their identification papers but they didn’t speak English nor Dutch. The driver of the car was in possession of their papers and told us that they were on vacation in the Netherlands for two weeks etc.
Example of a formal context and report Expensive cars Prostitues Id-papers Vacation Former eastern Europe 1 X X x 2 x x x X 3 X X x X 4 5 x x x X Report 1: On the night of 23 of march 2008 we stopped a car with a Bulgarian license plate for routine motor vehicle inspection. It was a Mercedes GLK with licence plate BL XXX. The car was driving around in circles in a prostitution area. On the backseat of the car we noticed two well dressed young girls. We asked for their identification papers but they didn’t speak English nor Dutch. The driver of the car was in possession of their papers and told us that they were on vacation in the Netherlands for two weeks etc.
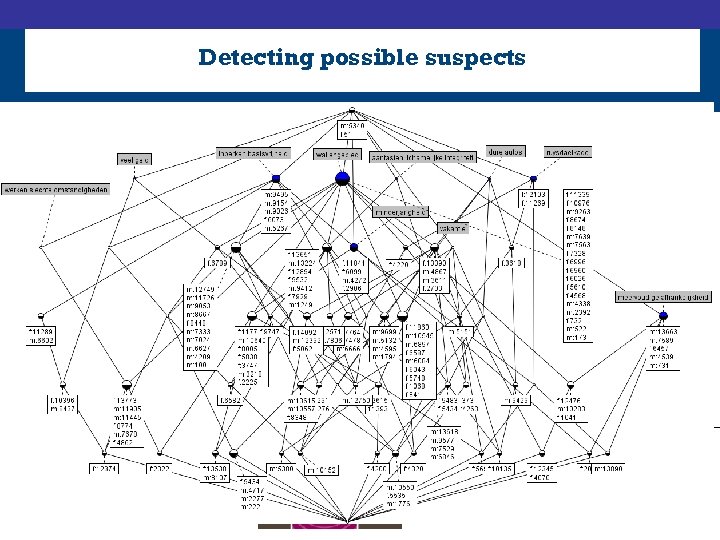 Detecting possible suspects
Detecting possible suspects
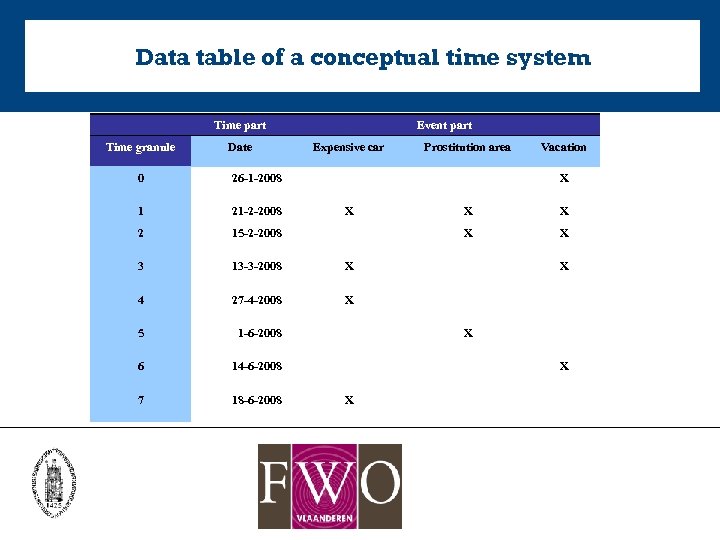 Data table of a conceptual time system Time part Time granule Date Event part Expensive car 0 26 -1 -2008 1 21 -2 -2008 2 15 -2 -2008 3 13 -3 -2008 X 4 27 -4 -2008 1 -6 -2008 6 14 -6 -2008 7 18 -6 -2008 Vacation X 5 Prostitution area X X X X X
Data table of a conceptual time system Time part Time granule Date Event part Expensive car 0 26 -1 -2008 1 21 -2 -2008 2 15 -2 -2008 3 13 -3 -2008 X 4 27 -4 -2008 1 -6 -2008 6 14 -6 -2008 7 18 -6 -2008 Vacation X 5 Prostitution area X X X X X
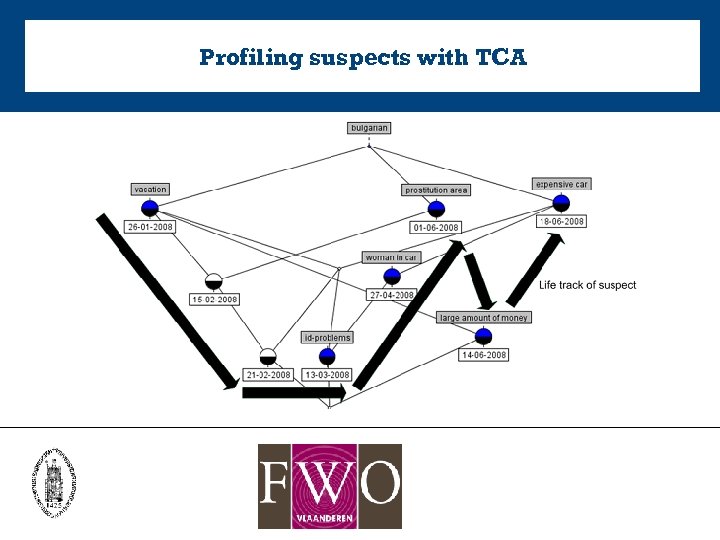 Profiling suspects with TCA
Profiling suspects with TCA
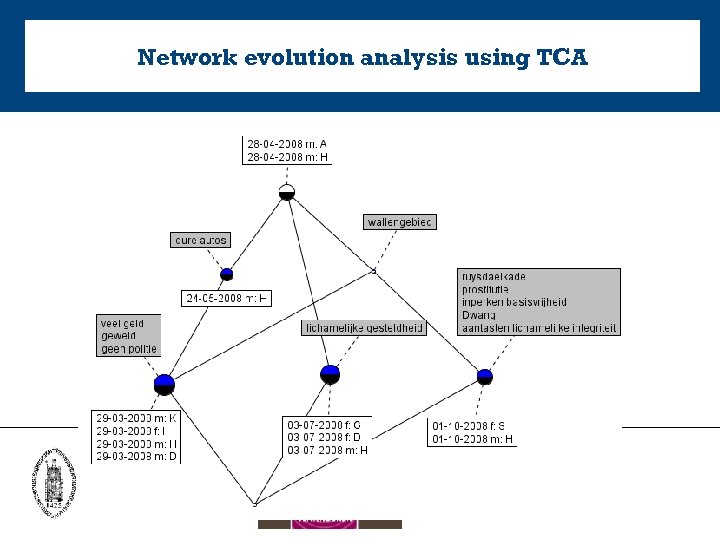 Network evolution analysis using TCA
Network evolution analysis using TCA
 Terrorist threat assessment with Formal Concept Analysis • Terrorism in the Netherlands: – the brute murder of the filmmaker Theo van Gogh. • Introduction of the term “European Jihad” by the secret services, most important trend is – the evolvement from exogenous foreign terrorist threat to indigenous home-grown terrorism • The law on terrorism in the Netherlands allows to proactively search for possible jihadists.
Terrorist threat assessment with Formal Concept Analysis • Terrorism in the Netherlands: – the brute murder of the filmmaker Theo van Gogh. • Introduction of the term “European Jihad” by the secret services, most important trend is – the evolvement from exogenous foreign terrorist threat to indigenous home-grown terrorism • The law on terrorism in the Netherlands allows to proactively search for possible jihadists.
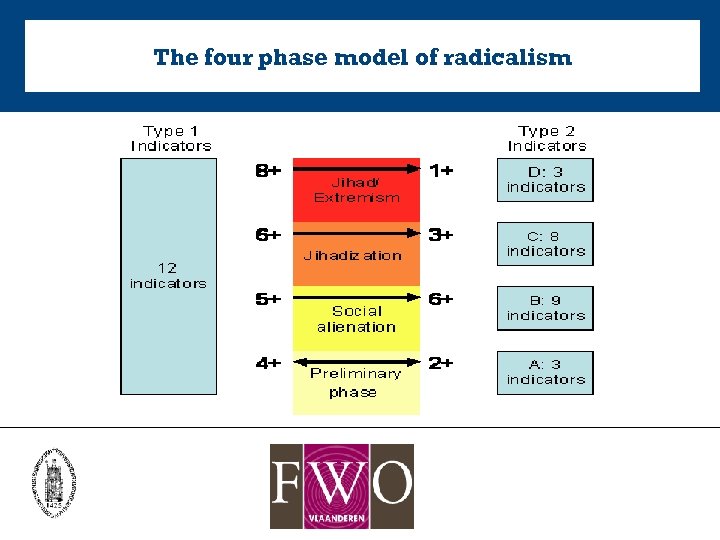 The four phase model of radicalism
The four phase model of radicalism
 The phases explained Incremental isolation • In the preliminary phase the subject experiences a crisis of confidence. • In the social alienation phase a small minority of these young Muslims cannot handle this situation. • In the Jihadization phase the subjects are characterized by strong radical Islamic convictions and the fact that they condone violence. • The Jihad/Extremism is a phase of total isolation. The subjects’ entire lives are governed by their radical Islamic beliefs.
The phases explained Incremental isolation • In the preliminary phase the subject experiences a crisis of confidence. • In the social alienation phase a small minority of these young Muslims cannot handle this situation. • In the Jihadization phase the subjects are characterized by strong radical Islamic convictions and the fact that they condone violence. • The Jihad/Extremism is a phase of total isolation. The subjects’ entire lives are governed by their radical Islamic beliefs.
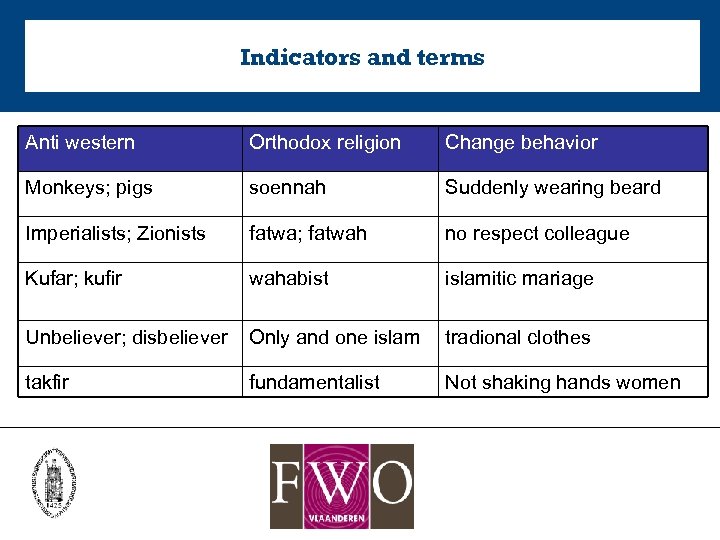 Indicators and terms Anti western Orthodox religion Change behavior Monkeys; pigs soennah Suddenly wearing beard Imperialists; Zionists fatwa; fatwah no respect colleague Kufar; kufir wahabist islamitic mariage Unbeliever; disbeliever Only and one islam tradional clothes takfir fundamentalist Not shaking hands women
Indicators and terms Anti western Orthodox religion Change behavior Monkeys; pigs soennah Suddenly wearing beard Imperialists; Zionists fatwa; fatwah no respect colleague Kufar; kufir wahabist islamitic mariage Unbeliever; disbeliever Only and one islam tradional clothes takfir fundamentalist Not shaking hands women
 Dataset • 166577 general reports – Contain observations made by police officers – Consequence of implementing Intelligence Led Policing in 2005 – Growing each year: • 2006: 41900 • 2007: 54799 • 2008: 69788 – The unstructured text describing the observations is explored • The observations are made within the communities of Amsterdam, Amstelveen, Uithoorn, Ouder. Amstel and Diemen
Dataset • 166577 general reports – Contain observations made by police officers – Consequence of implementing Intelligence Led Policing in 2005 – Growing each year: • 2006: 41900 • 2007: 54799 • 2008: 69788 – The unstructured text describing the observations is explored • The observations are made within the communities of Amsterdam, Amstelveen, Uithoorn, Ouder. Amstel and Diemen
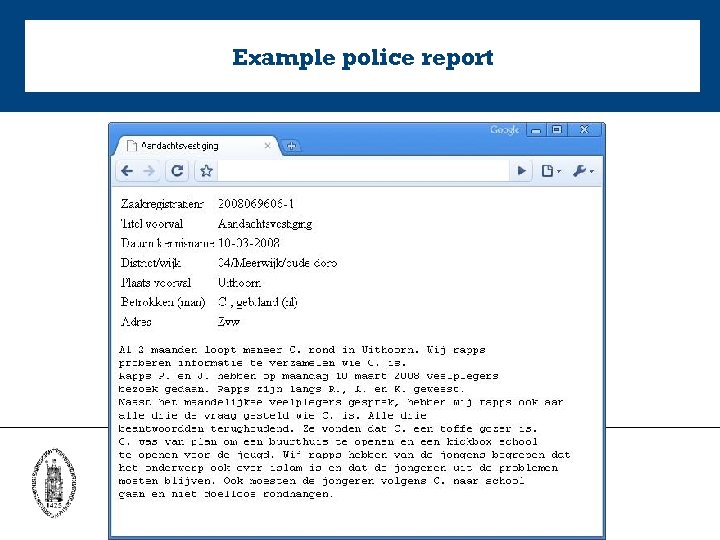 Example police report
Example police report
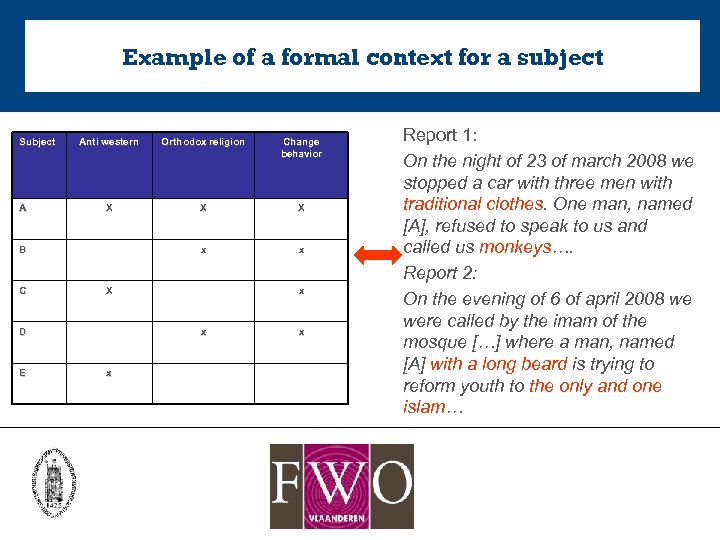 Example of a formal context for a subject Subject A Anti western Orthodox religion Change behavior X X X x x B C X D E x x Report 1: On the night of 23 of march 2008 we stopped a car with three men with traditional clothes. One man, named [A], refused to speak to us and called us monkeys…. Report 2: On the evening of 6 of april 2008 we were called by the imam of the mosque […] where a man, named [A] with a long beard is trying to reform youth to the only and one islam…
Example of a formal context for a subject Subject A Anti western Orthodox religion Change behavior X X X x x B C X D E x x Report 1: On the night of 23 of march 2008 we stopped a car with three men with traditional clothes. One man, named [A], refused to speak to us and called us monkeys…. Report 2: On the evening of 6 of april 2008 we were called by the imam of the mosque […] where a man, named [A] with a long beard is trying to reform youth to the only and one islam…
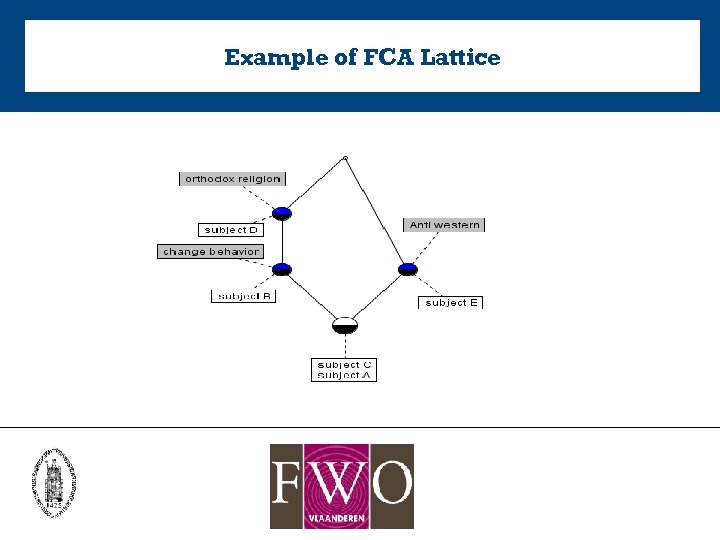 Example of FCA Lattice
Example of FCA Lattice
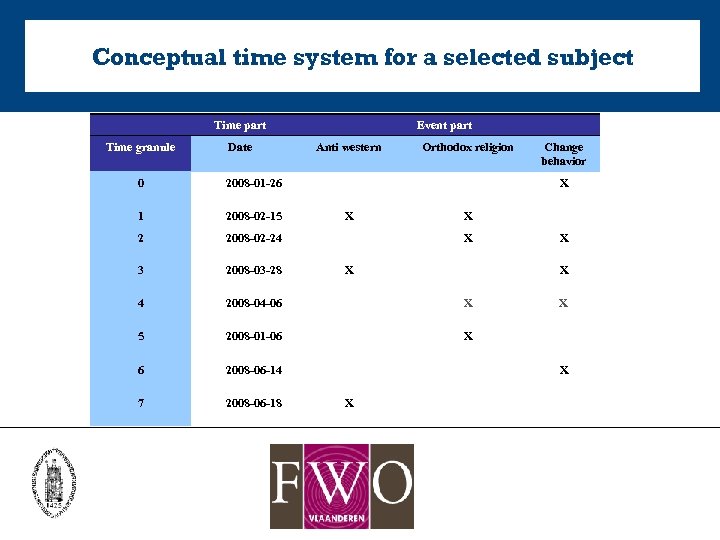 Conceptual time system for a selected subject Time part Time granule Date Event part Anti western Orthodox religion 0 2008 -01 -26 1 2008 -02 -15 2 2008 -02 -24 3 2008 -03 -28 4 2008 -04 -06 X 5 2008 -01 -06 X 6 2008 -06 -14 7 2008 -06 -18 Change behavior X X X X
Conceptual time system for a selected subject Time part Time granule Date Event part Anti western Orthodox religion 0 2008 -01 -26 1 2008 -02 -15 2 2008 -02 -24 3 2008 -03 -28 4 2008 -04 -06 X 5 2008 -01 -06 X 6 2008 -06 -14 7 2008 -06 -18 Change behavior X X X X
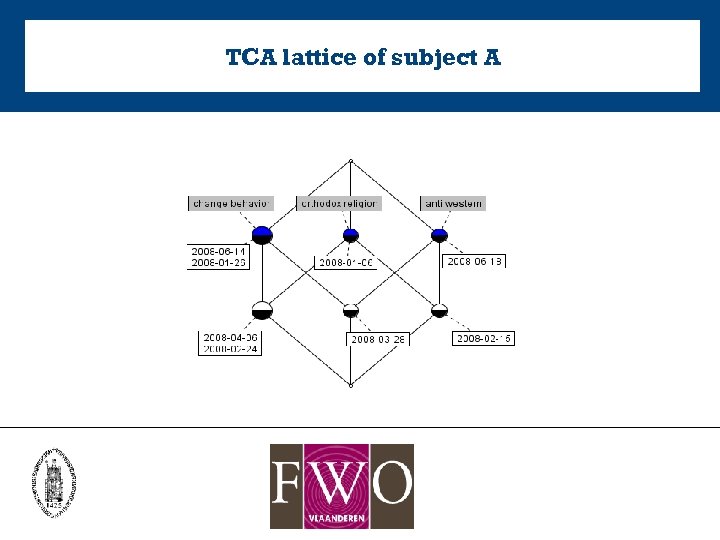 TCA lattice of subject A
TCA lattice of subject A
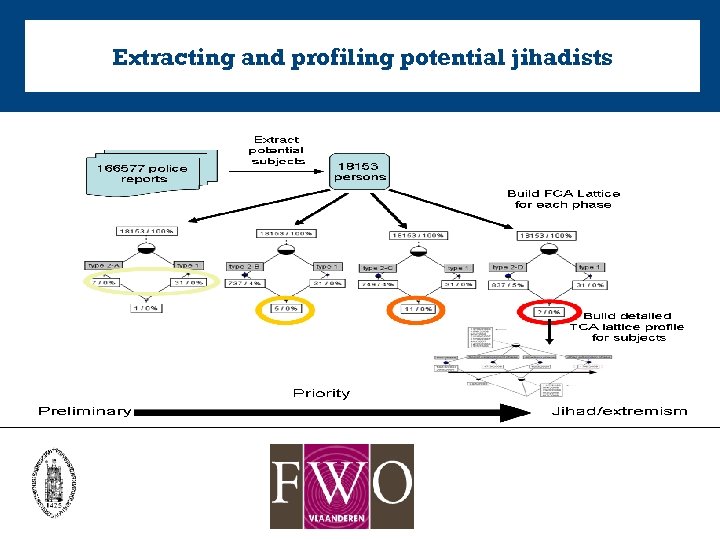 Extracting and profiling potential jihadists
Extracting and profiling potential jihadists
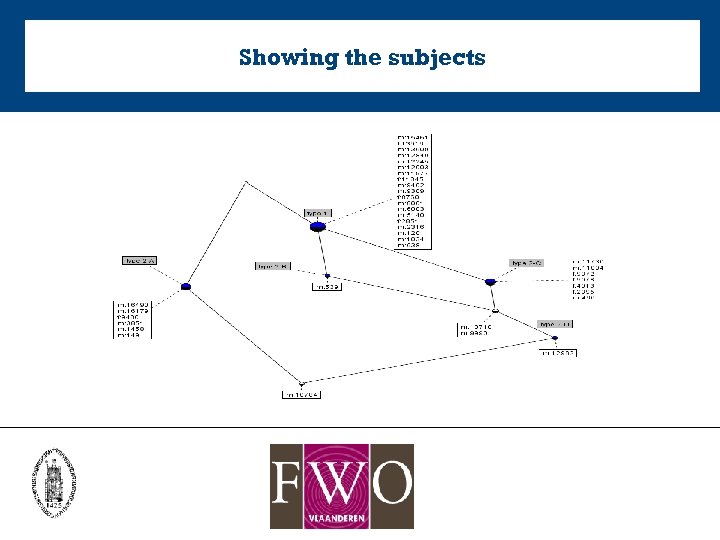 Showing the subjects
Showing the subjects
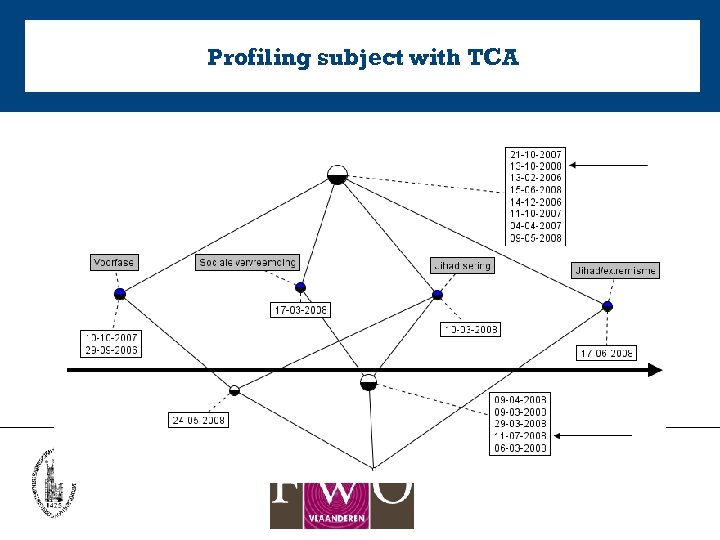 Profiling subject with TCA
Profiling subject with TCA
 Combining business process & data discovery techniques for analyzing and improving integrated care pathways • gaining insight in what happens in healthcare process for a group of patients with same diagnosis • goal: extract monitor and improve real processes by extracting knowledge from event logs. • few studies on process mining in healthcare • mostly Petri Nets.
Combining business process & data discovery techniques for analyzing and improving integrated care pathways • gaining insight in what happens in healthcare process for a group of patients with same diagnosis • goal: extract monitor and improve real processes by extracting knowledge from event logs. • few studies on process mining in healthcare • mostly Petri Nets.
 Integrated care pathway (ICP): Definition • • • Structured multidisciplinary care plan Details essential steps in the care process To achieve well defined goals For a patient with a specific clinical problem Description of the expected progress over a certain time period
Integrated care pathway (ICP): Definition • • • Structured multidisciplinary care plan Details essential steps in the care process To achieve well defined goals For a patient with a specific clinical problem Description of the expected progress over a certain time period
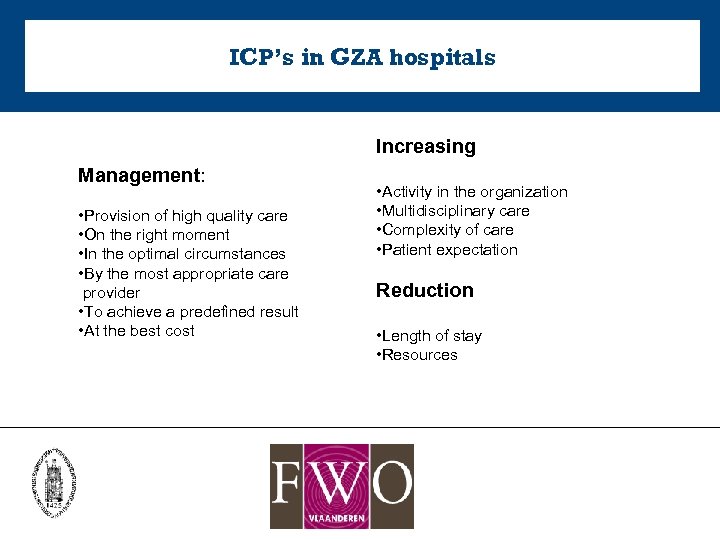 ICP’s in GZA hospitals Increasing Management: • Provision of high quality care • On the right moment • In the optimal circumstances • By the most appropriate care provider • To achieve a predefined result • At the best cost • Activity in the organization • Multidisciplinary care • Complexity of care • Patient expectation Reduction • Length of stay • Resources
ICP’s in GZA hospitals Increasing Management: • Provision of high quality care • On the right moment • In the optimal circumstances • By the most appropriate care provider • To achieve a predefined result • At the best cost • Activity in the organization • Multidisciplinary care • Complexity of care • Patient expectation Reduction • Length of stay • Resources
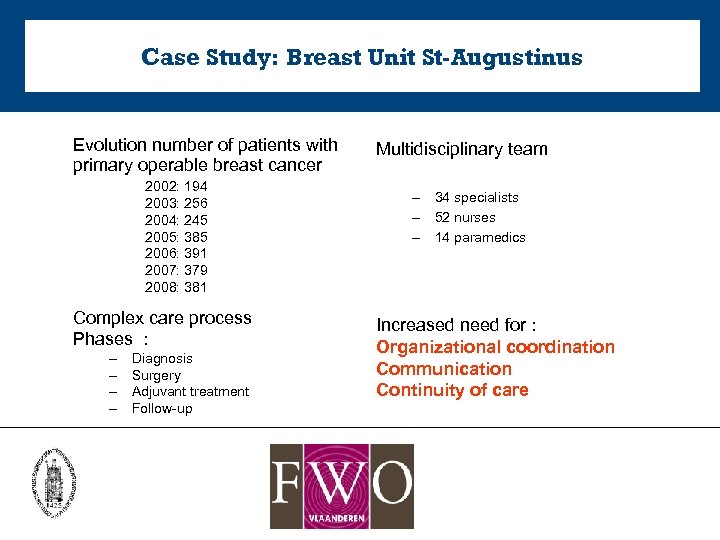 Case Study: Breast Unit St-Augustinus Evolution number of patients with primary operable breast cancer 2002: 194 2003: 256 2004: 245 2005: 385 2006: 391 2007: 379 2008: 381 Complex care process Phases : – – Diagnosis Surgery Adjuvant treatment Follow-up Multidisciplinary team – 34 specialists – 52 nurses – 14 paramedics Increased need for : Organizational coordination Communication Continuity of care
Case Study: Breast Unit St-Augustinus Evolution number of patients with primary operable breast cancer 2002: 194 2003: 256 2004: 245 2005: 385 2006: 391 2007: 379 2008: 381 Complex care process Phases : – – Diagnosis Surgery Adjuvant treatment Follow-up Multidisciplinary team – 34 specialists – 52 nurses – 14 paramedics Increased need for : Organizational coordination Communication Continuity of care
 Healthcare 1. 0: Pitfalls Traditional Business Process Model: • Do not capture process variations, process exceptions or root causes of the exceptions and variations • Only delta analyses to find impact on key performance indicators • Models the most standard frequent pathway • High workload for care process manager • Retrospective analysis (every 6 months) • Evaluation over the first semester of each year only
Healthcare 1. 0: Pitfalls Traditional Business Process Model: • Do not capture process variations, process exceptions or root causes of the exceptions and variations • Only delta analyses to find impact on key performance indicators • Models the most standard frequent pathway • High workload for care process manager • Retrospective analysis (every 6 months) • Evaluation over the first semester of each year only
 Innovation: Process Discovery Bottom up approach: • To discover process inefficiencies, exceptions and variations immediately • To gain sufficient understanding of the existing process and its outliers • Evaluation of the care process of all the patients • To search for the root causes of inefficiencies or improvements
Innovation: Process Discovery Bottom up approach: • To discover process inefficiencies, exceptions and variations immediately • To gain sufficient understanding of the existing process and its outliers • Evaluation of the care process of all the patients • To search for the root causes of inefficiencies or improvements
 Input for Clinical Path Discovery • Patient treatment records • Turned into event sequences • Compliant with HL 7
Input for Clinical Path Discovery • Patient treatment records • Turned into event sequences • Compliant with HL 7
 Expected Benefits of the research • • Possibility of what if analysis Reduced waiting times Decreased average length of stay Time interval between the interventions Evaluation immediately available Decreasing workload of the ICP coordinator High quality of care with optimal use of the resources
Expected Benefits of the research • • Possibility of what if analysis Reduced waiting times Decreased average length of stay Time interval between the interventions Evaluation immediately available Decreasing workload of the ICP coordinator High quality of care with optimal use of the resources
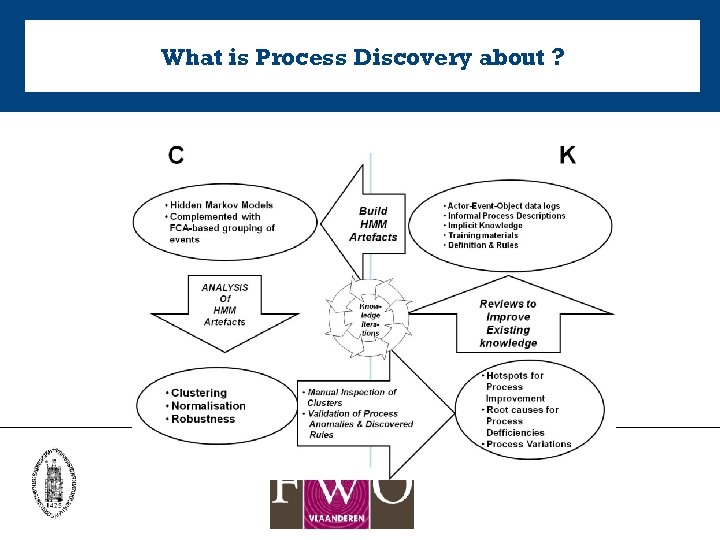 What is Process Discovery about ?
What is Process Discovery about ?
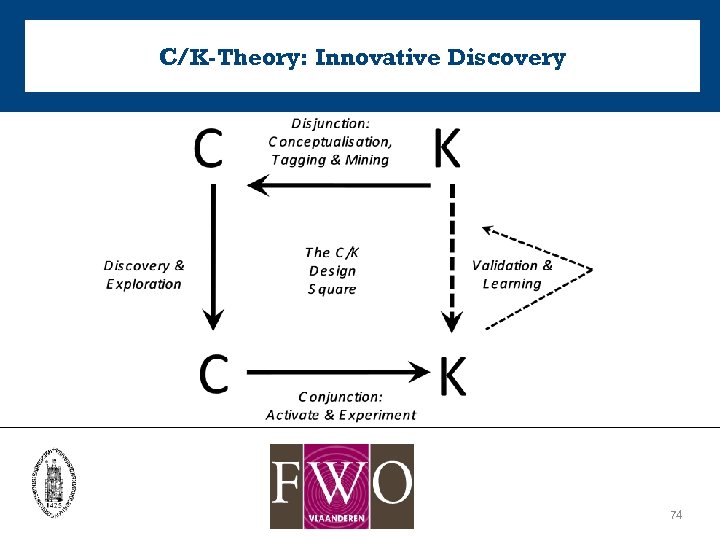 C/K-Theory: Innovative Discovery 74
C/K-Theory: Innovative Discovery 74
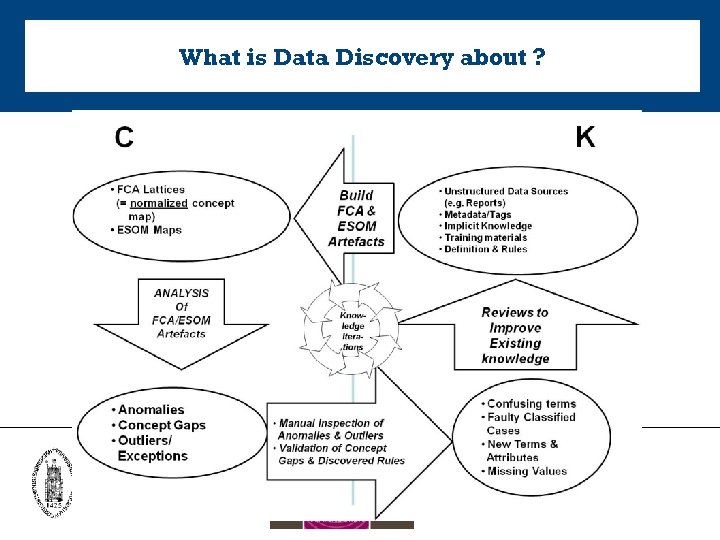 What is Data Discovery about ?
What is Data Discovery about ?
 Combination of process & data discovery (1) • to gain deeper understanding of existing breast cancer care process & actual activities performed on work floor • discover process inefficiencies, exceptions and variations immediately • search for root causes of inefficiencies
Combination of process & data discovery (1) • to gain deeper understanding of existing breast cancer care process & actual activities performed on work floor • discover process inefficiencies, exceptions and variations immediately • search for root causes of inefficiencies
 Combination of process & data discovery (2) • Hidden Markov Models to discover process models from event sequences. • Formal Concept Analysis: – analyze characteristics of clusters of patients that emerged from process discovery. – find groups of patients to feed into the process discovery methods.
Combination of process & data discovery (2) • Hidden Markov Models to discover process models from event sequences. • Formal Concept Analysis: – analyze characteristics of clusters of patients that emerged from process discovery. – find groups of patients to feed into the process discovery methods.
 Previous process mining research in healthcare • mostly Petri-Net models • Example: process models were built from simulated process logs of hospital-wide workflows containing events like "blood test" or “surgery” • Hidden Markov Model approach: model workflow inside Operation Room
Previous process mining research in healthcare • mostly Petri-Net models • Example: process models were built from simulated process logs of hospital-wide workflows containing events like "blood test" or “surgery” • Hidden Markov Model approach: model workflow inside Operation Room
 Hidden Markov Model • Probabilistic model with greater degree of flexibility • Better option for healthcare where traditional process mining does not work well, • Many (open source) algorithms have been published for analyzing and understanding HMMs • Micro patterns of actor behavior can be easily aggregated in one state • HMMs can be annotated with a variety of attributes such as probabilities, time duration, variances, etc.
Hidden Markov Model • Probabilistic model with greater degree of flexibility • Better option for healthcare where traditional process mining does not work well, • Many (open source) algorithms have been published for analyzing and understanding HMMs • Micro patterns of actor behavior can be easily aggregated in one state • HMMs can be annotated with a variety of attributes such as probabilities, time duration, variances, etc.
 Dataset • 148 breast cancer patients hospitalized from January 2008 till June 2008. • 469 activity identifiers in total • care trajectory Primary Operable Breast Cancer • breast cancer care process: 4 phases, 34 doctors, 52 nurses and 14 paramedics
Dataset • 148 breast cancer patients hospitalized from January 2008 till June 2008. • 469 activity identifiers in total • care trajectory Primary Operable Breast Cancer • breast cancer care process: 4 phases, 34 doctors, 52 nurses and 14 paramedics
 Breast cancer care process (1) • every activity performed to a patient is logged in a database • dataset includes all activities performed during surgery support phase
Breast cancer care process (1) • every activity performed to a patient is logged in a database • dataset includes all activities performed during surgery support phase
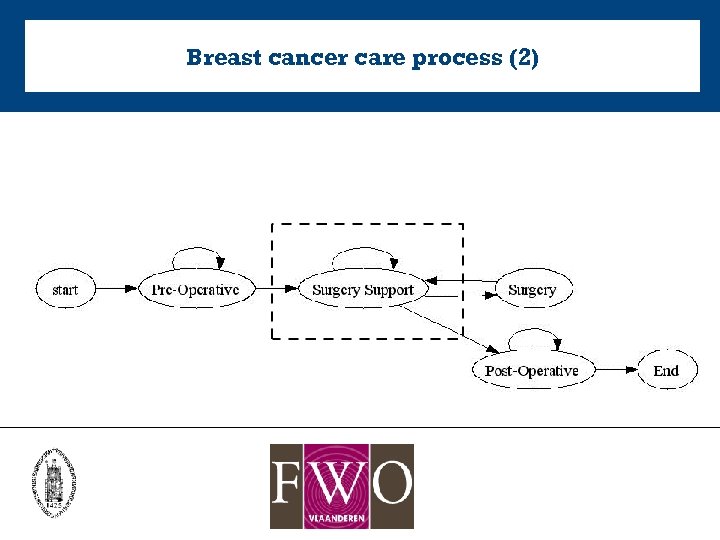 Breast cancer care process (2)
Breast cancer care process (2)
 Breast cancer data • each activity has unique identifier • timestamps assigned to performed activities • data was turned for each patient into a sequence of events • sequences of events were input for process discovery methods • activities with a similar semantic meaning were clustered to reduce complexity of lattices and process models
Breast cancer data • each activity has unique identifier • timestamps assigned to performed activities • data was turned for each patient into a sequence of events • sequences of events were input for process discovery methods • activities with a similar semantic meaning were clustered to reduce complexity of lattices and process models
 Analysis method • process models: extraction and visualization of most frequent standard care pathway • during analysis of these models: anomalies and process exceptions are found • FCA: zoom in on and analyze these observations in detail.
Analysis method • process models: extraction and visualization of most frequent standard care pathway • during analysis of these models: anomalies and process exceptions are found • FCA: zoom in on and analyze these observations in detail.
 Quality of care analysis • initial process model: 148 patients and 469 activity codes • length of stay in hospital < 10 days: linear process • length of stay > 9 days: 12 patients for which process was very complex
Quality of care analysis • initial process model: 148 patients and 469 activity codes • length of stay in hospital < 10 days: linear process • length of stay > 9 days: 12 patients for which process was very complex
 FCA analysis of 12 patients (1) • pain score reaches highest point on day 1 and 4 of hospitalization. • FCA lattice: overlooked connection between removal of wound drains and insufficient pain medication. • pain medication should be administered before removing the drains
FCA analysis of 12 patients (1) • pain score reaches highest point on day 1 and 4 of hospitalization. • FCA lattice: overlooked connection between removal of wound drains and insufficient pain medication. • pain medication should be administered before removing the drains
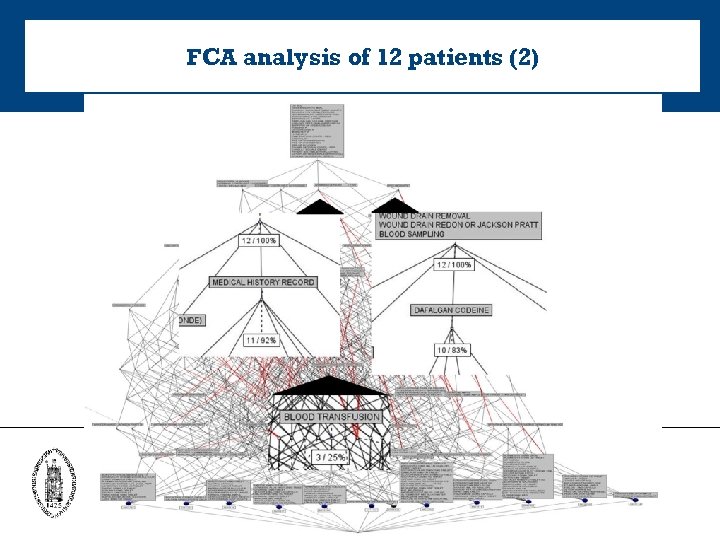 FCA analysis of 12 patients (2)
FCA analysis of 12 patients (2)
 FCA analysis of 12 patients (3) • main reason of increased length of stay: neurological / psychiatric problems, wound infection, subsequent bleeding. • cancer care process more complex resulting in more investigative tests. • since additional morbidities are a root cause for this increased length of stay: treatment should be anticipated on & optimalized during preoperative phase
FCA analysis of 12 patients (3) • main reason of increased length of stay: neurological / psychiatric problems, wound infection, subsequent bleeding. • cancer care process more complex resulting in more investigative tests. • since additional morbidities are a root cause for this increased length of stay: treatment should be anticipated on & optimalized during preoperative phase
 Process variations (1) 5 types of breast cancer surgery: – – – mastectomy breast conserving surgery lymph node removal combination of mastectomy and lymph node removal combination of breast conserving surgery and lymph node removal
Process variations (1) 5 types of breast cancer surgery: – – – mastectomy breast conserving surgery lymph node removal combination of mastectomy and lymph node removal combination of breast conserving surgery and lymph node removal
 Process variations (2) • For each surgery type: – process model was built – FCA lattice for analyzing characteristics of patient groups • Mastectomy vs. breast conserving surgery – more complex surgery type – FCA lattices were less complex for mastectomy than for breast conserving surgery.
Process variations (2) • For each surgery type: – process model was built – FCA lattice for analyzing characteristics of patient groups • Mastectomy vs. breast conserving surgery – more complex surgery type – FCA lattices were less complex for mastectomy than for breast conserving surgery.
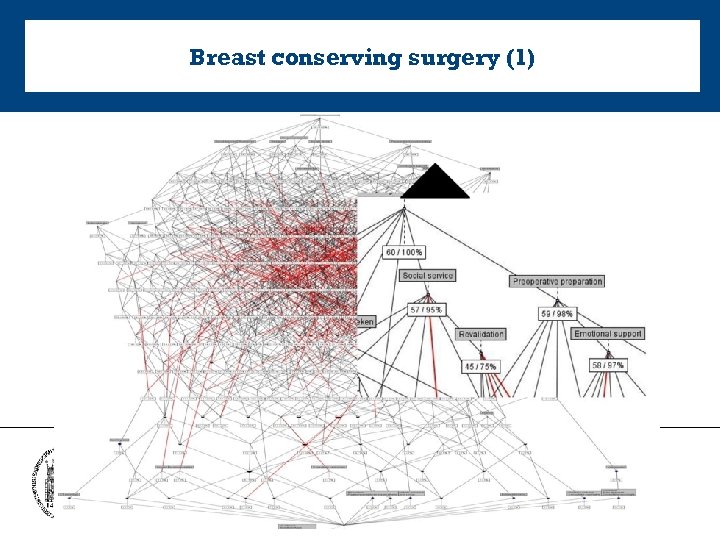 Breast conserving surgery (1)
Breast conserving surgery (1)
 Breast conserving surgery (2) • less uniformly structured care process • essential care interventions are missing – 3 patients did not receive consultation from social support service – 15 patients did not have appointment with physiotherapist & did not receive revalidation therapy. – 1 patient did not receive pre- operative preparation – 2 patients were missing emotional support before and after surgery
Breast conserving surgery (2) • less uniformly structured care process • essential care interventions are missing – 3 patients did not receive consultation from social support service – 15 patients did not have appointment with physiotherapist & did not receive revalidation therapy. – 1 patient did not receive pre- operative preparation – 2 patients were missing emotional support before and after surgery
 Breast conserving surgery (3) • original pathway was written for certain length of stay • length of stay was significantly reduced over past years without modifying the care process model • became impossible to execute prescribed process model in practice • patients are receiving suboptimal care
Breast conserving surgery (3) • original pathway was written for certain length of stay • length of stay was significantly reduced over past years without modifying the care process model • became impossible to execute prescribed process model in practice • patients are receiving suboptimal care
 Breast conserving surgery (4) • Solution: – activities performed to patients should be reorganized – care pathway taking into account this time restriction should be optimalized
Breast conserving surgery (4) • Solution: – activities performed to patients should be reorganized – care pathway taking into account this time restriction should be optimalized
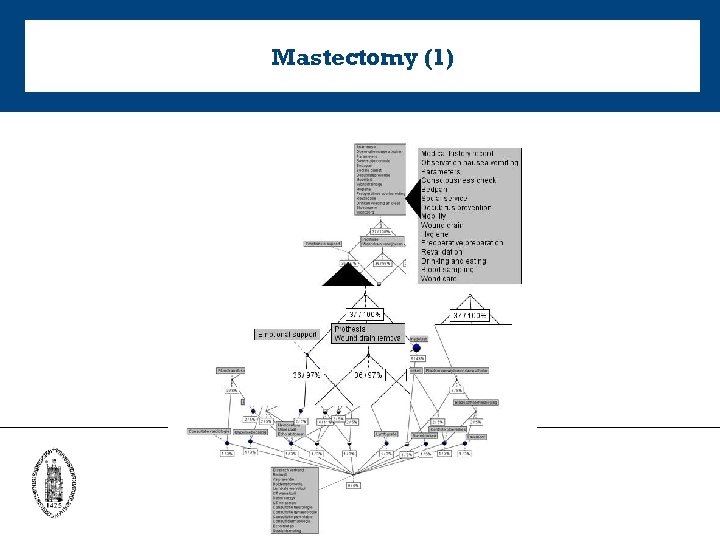 Mastectomy (1)
Mastectomy (1)
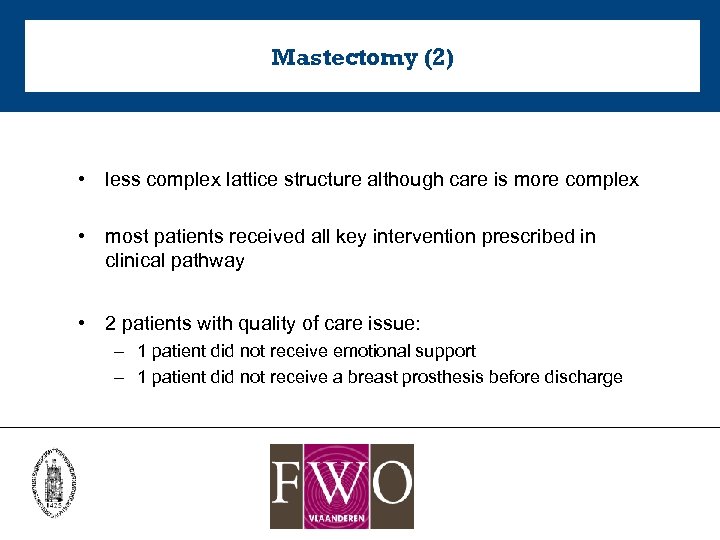 Mastectomy (2) • less complex lattice structure although care is more complex • most patients received all key intervention prescribed in clinical pathway • 2 patients with quality of care issue: – 1 patient did not receive emotional support – 1 patient did not receive a breast prosthesis before discharge
Mastectomy (2) • less complex lattice structure although care is more complex • most patients received all key intervention prescribed in clinical pathway • 2 patients with quality of care issue: – 1 patient did not receive emotional support – 1 patient did not receive a breast prosthesis before discharge
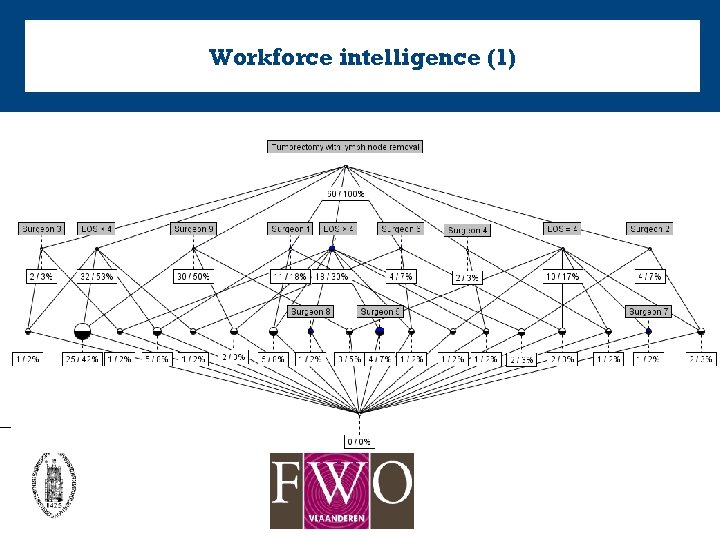 Workforce intelligence (1)
Workforce intelligence (1)
 Workforce intelligence (2) • 25 patients with LOS < 4 days are treated by surgeon 9. • patients treated by other doctors have longer LOS • process models were constructed for patients with – LOS smaller than 4 days – LOS equal to 4 days – LOS larger than 4 days. • extract best practices.
Workforce intelligence (2) • 25 patients with LOS < 4 days are treated by surgeon 9. • patients treated by other doctors have longer LOS • process models were constructed for patients with – LOS smaller than 4 days – LOS equal to 4 days – LOS larger than 4 days. • extract best practices.
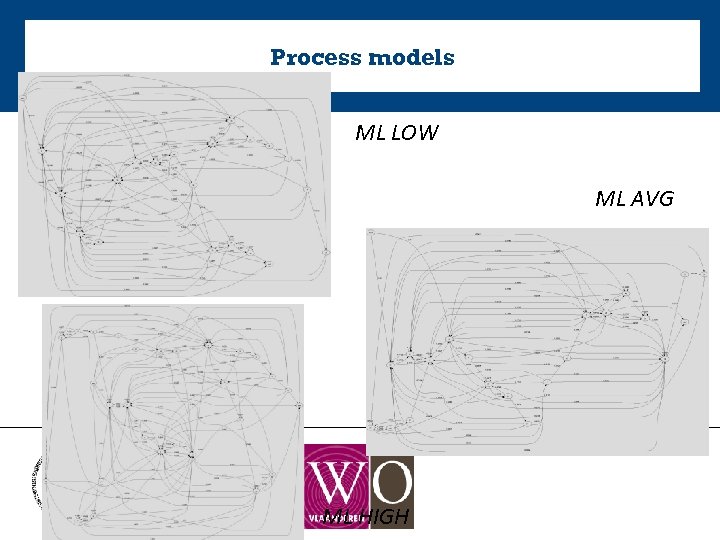 Process models ML LOW ML AVG ML HIGH
Process models ML LOW ML AVG ML HIGH
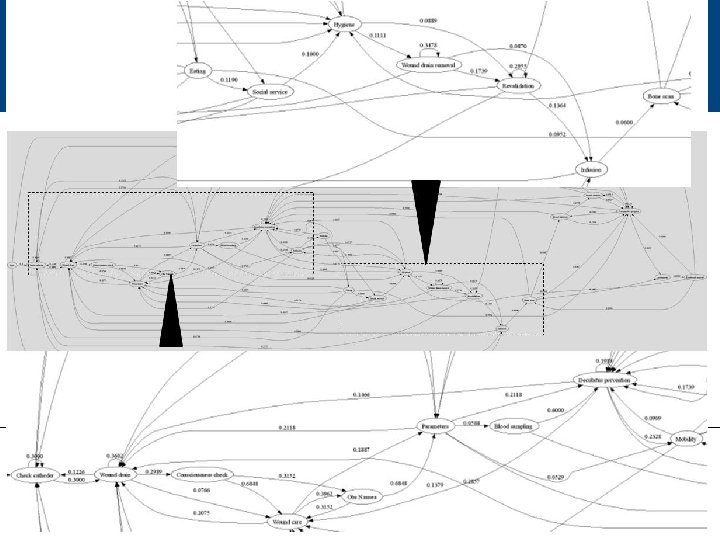
 Data entrance quality problems • some patients for who activities were registered after day of discharge • reason: error in computer program combined with sloppy data entry by nursing staff • semantically identical activities that had different activity numbers
Data entrance quality problems • some patients for who activities were registered after day of discharge • reason: error in computer program combined with sloppy data entry by nursing staff • semantically identical activities that had different activity numbers
 Data entrance quality problems (2) • process models have ordering of events that does not correspond to ordering in real life – reason: error in computer system which sometimes imposes certain sequences of events • discrepancy between built-in top-down developed model and reality – reason: insufficient insight into reality of working floor
Data entrance quality problems (2) • process models have ordering of events that does not correspond to ordering in real life – reason: error in computer system which sometimes imposes certain sequences of events • discrepancy between built-in top-down developed model and reality – reason: insufficient insight into reality of working floor
 Journal Articles: Published Poelmans, J. , Elzinga, P. , Viaene, S. , Van Hulle, M. & Dedene G. (2009). Gaining insight in domestic violence with emergent self organizing maps, Expert systems with applications, 36, (9), 11864 – 11874. [SCI=2. 596] Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. , Van Hulle, M. (2009). Analyzing domestic violence with topographic maps: a comparative study, Lecture Notes in Computer Science, 5629, 246 – 254, Advances in Self-organizing Maps, 7 th International Workshop on Self-Organizing Maps (WSOM). St. Augustine, Florida (USA), 8 -10 June 2009, Springer. [SCI=0. 295] Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. (2009). A case of using formal concept analysis in combination with emergent self organizing maps for detecting domestic violence, Lecture Notes in Computer Science, 5633, 247 – 260, Advances in Data Mining. Applications and Theoretical Aspects, 9 th Industrial Conference (ICDM), Leipzig, Germany, July 20 -22, 2009, Springer. [SCI=0. 295] Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. (2008). An exploration into the power of formal concept analysis for domestic violence analysis, Lecture Notes in Computer Science, 5077, 404 – 416, Advances in Data Mining. Applications and Theoretical Aspects, 8 th Industrial Conference (ICDM), Leipzig, Germany, July 16 -18, 2008, Springer. [SCI=0. 295]
Journal Articles: Published Poelmans, J. , Elzinga, P. , Viaene, S. , Van Hulle, M. & Dedene G. (2009). Gaining insight in domestic violence with emergent self organizing maps, Expert systems with applications, 36, (9), 11864 – 11874. [SCI=2. 596] Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. , Van Hulle, M. (2009). Analyzing domestic violence with topographic maps: a comparative study, Lecture Notes in Computer Science, 5629, 246 – 254, Advances in Self-organizing Maps, 7 th International Workshop on Self-Organizing Maps (WSOM). St. Augustine, Florida (USA), 8 -10 June 2009, Springer. [SCI=0. 295] Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. (2009). A case of using formal concept analysis in combination with emergent self organizing maps for detecting domestic violence, Lecture Notes in Computer Science, 5633, 247 – 260, Advances in Data Mining. Applications and Theoretical Aspects, 9 th Industrial Conference (ICDM), Leipzig, Germany, July 20 -22, 2009, Springer. [SCI=0. 295] Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. (2008). An exploration into the power of formal concept analysis for domestic violence analysis, Lecture Notes in Computer Science, 5077, 404 – 416, Advances in Data Mining. Applications and Theoretical Aspects, 8 th Industrial Conference (ICDM), Leipzig, Germany, July 16 -18, 2008, Springer. [SCI=0. 295]
 Journal Articles: Published Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. (2010), Formal Concept Analysis in knowledge discovery: a survey. Lecture Notes in Computer Science, 6208, 139 -153, 18 th international conference on conceptual structures (ICCS 2010): from information to intelligence. 26 - 30 July, Kuching, Sarawak, Malaysia. Springer. Manyakov, N. , Poelmans, J. , Vogels, R. , Van Hulle, M. (2010), Combining ESOMs trained on hierarchy of feature subsets for single-trial decoding of LFP responses in monkey area V 4. Lecture Notes in Artificial Intelligence, 6114, 548 -555, 10 th International Conference on Artificial Intelligence and Soft Computing. June 13 -17, Zakopane, Poland. Springer Poelmans, J. , Dedene, G. , Verheyden, G. , Van der Mussele, H. , Viaene, S. , Peters, E. (2010). Combining business process and data discovery techniques for analyzing and improving integrated care pathways. Lecture Notes in Computer Science, Advances in Data Mining. Applications and Theoretical Aspects, 10 th Industrial Conference (ICDM), Leipzig, Germany, July 12 -14, 2010. Springer Vuylsteke A. , Baesens B. , Poelmans J. (2010). Consumers’ search for information on the internet: how and why China differs from Western Europe, Accepted for Journal of interactive marketing.
Journal Articles: Published Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. (2010), Formal Concept Analysis in knowledge discovery: a survey. Lecture Notes in Computer Science, 6208, 139 -153, 18 th international conference on conceptual structures (ICCS 2010): from information to intelligence. 26 - 30 July, Kuching, Sarawak, Malaysia. Springer. Manyakov, N. , Poelmans, J. , Vogels, R. , Van Hulle, M. (2010), Combining ESOMs trained on hierarchy of feature subsets for single-trial decoding of LFP responses in monkey area V 4. Lecture Notes in Artificial Intelligence, 6114, 548 -555, 10 th International Conference on Artificial Intelligence and Soft Computing. June 13 -17, Zakopane, Poland. Springer Poelmans, J. , Dedene, G. , Verheyden, G. , Van der Mussele, H. , Viaene, S. , Peters, E. (2010). Combining business process and data discovery techniques for analyzing and improving integrated care pathways. Lecture Notes in Computer Science, Advances in Data Mining. Applications and Theoretical Aspects, 10 th Industrial Conference (ICDM), Leipzig, Germany, July 12 -14, 2010. Springer Vuylsteke A. , Baesens B. , Poelmans J. (2010). Consumers’ search for information on the internet: how and why China differs from Western Europe, Accepted for Journal of interactive marketing.
 Journal Articles: Submitted Verheyden, G. , Poelmans, J. , Viaene, S. , Van der Mussele, H. , Dedene, G. , van Dam, P. (2010). Key Success Factors for significantly improving Patient Satisfaction on Breast Cancer care: a Case Study, submitted for The Breast Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. (2010) Curbing domestic violence: Instantiating C-K theory with Formal Concept Analysis and Emergent Self Organizing Maps, submitted for IEEE transactions on knowledge and data engineering. Poelmans, J. , Elzinga, P. , Viaene, S. , Van Hulle, M. & Dedene G. (2010) Text Mining with Emergent Self Organizing Maps and Multi-Dimensional Scaling: A comparitive study on domestic violence, submitted for Applied Soft Computing. Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. (2010) Formal Concept Analysis in Information Engineering: a Survey, submitted for ACM Computing Surveys. Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. (2010) Formally Analyzing the Concepts of Domestic Violence, submitted for Expert Systems with Applications.
Journal Articles: Submitted Verheyden, G. , Poelmans, J. , Viaene, S. , Van der Mussele, H. , Dedene, G. , van Dam, P. (2010). Key Success Factors for significantly improving Patient Satisfaction on Breast Cancer care: a Case Study, submitted for The Breast Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. (2010) Curbing domestic violence: Instantiating C-K theory with Formal Concept Analysis and Emergent Self Organizing Maps, submitted for IEEE transactions on knowledge and data engineering. Poelmans, J. , Elzinga, P. , Viaene, S. , Van Hulle, M. & Dedene G. (2010) Text Mining with Emergent Self Organizing Maps and Multi-Dimensional Scaling: A comparitive study on domestic violence, submitted for Applied Soft Computing. Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. (2010) Formal Concept Analysis in Information Engineering: a Survey, submitted for ACM Computing Surveys. Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. (2010) Formally Analyzing the Concepts of Domestic Violence, submitted for Expert Systems with Applications.
 Journal Articles: Submitted Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. (2010) Informatiegestuurd handhaven: een slimme kijk naar bestaande data, submitted for Informatie. Elzinga, P. , Poelmans, J. , Viaene, S. , Dedene, G. (2010) Formele concept analyse: een nieuwe dimensie voor intelligence, submitted for Blauw.
Journal Articles: Submitted Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. (2010) Informatiegestuurd handhaven: een slimme kijk naar bestaande data, submitted for Informatie. Elzinga, P. , Poelmans, J. , Viaene, S. , Dedene, G. (2010) Formele concept analyse: een nieuwe dimensie voor intelligence, submitted for Blauw.
 Conference proceedings: Accepted Poelmans, J. , Dedene, G. , Snoeck, M. Viaene, S. (2010). Using Formal Concept Analysis for the Verification of Process-Data matrices in Conceptual Domain Models, Proc. IASTED International Conference on Software Engineering (SE 2010), Feb 16 - 18, Innsbruck, Austria. Acta Press, pp. . Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. (2010). A method based on Temporal Concept Analysis for detecting and profiling human trafficking suspects. Proc. IASTED International Conference on Artificial Intelligence (AIA 2010). Innsbruck, Austria, 15 -17 february. Acta Press ISBN 978 -0788986817 -5, pp. 330 -338. Elzinga, P. , Poelmans, J. , Viaene, S. , Dedene, G. (2009), Detecting domestic violence – Showcasing a Knowledge Browser based on Formal Concept Analysis and Emergent Self Organizing Maps, Proc. 11 th International Conference on Enterprise Information Systems ICEIS, Volume AIDSS, pp. 11 – 18, Milan, Italy, May 6 -10, 2009. Poelmans, J, Elzinga, P. , Van Hulle, M. , Viaene, S. , and Dedene, G. (2009). How Emergent Self Organizing Maps can help counter domestic violence, World Congress on Computer Science and Information Engineering (CSIE 2009), Los Angeles (USA), Vol. 4, IEEE Computer Society Press ISBN 978 -0 -7695 -3507 -4, 126 – 136.
Conference proceedings: Accepted Poelmans, J. , Dedene, G. , Snoeck, M. Viaene, S. (2010). Using Formal Concept Analysis for the Verification of Process-Data matrices in Conceptual Domain Models, Proc. IASTED International Conference on Software Engineering (SE 2010), Feb 16 - 18, Innsbruck, Austria. Acta Press, pp. . Poelmans, J. , Elzinga, P. , Viaene, S. , Dedene, G. (2010). A method based on Temporal Concept Analysis for detecting and profiling human trafficking suspects. Proc. IASTED International Conference on Artificial Intelligence (AIA 2010). Innsbruck, Austria, 15 -17 february. Acta Press ISBN 978 -0788986817 -5, pp. 330 -338. Elzinga, P. , Poelmans, J. , Viaene, S. , Dedene, G. (2009), Detecting domestic violence – Showcasing a Knowledge Browser based on Formal Concept Analysis and Emergent Self Organizing Maps, Proc. 11 th International Conference on Enterprise Information Systems ICEIS, Volume AIDSS, pp. 11 – 18, Milan, Italy, May 6 -10, 2009. Poelmans, J, Elzinga, P. , Van Hulle, M. , Viaene, S. , and Dedene, G. (2009). How Emergent Self Organizing Maps can help counter domestic violence, World Congress on Computer Science and Information Engineering (CSIE 2009), Los Angeles (USA), Vol. 4, IEEE Computer Society Press ISBN 978 -0 -7695 -3507 -4, 126 – 136.
 Conference proceedings: Accepted Vuylsteke, A. , Wen, Z. , Baesens, B. and Poelmans J. (2009). Consumers Online Information Search: A Cross-Cultural Study between China and Western Europe. Paper presented at Academic And Business Research Institute Conference 2009, Orlando, USA, available at http: //www. aabri. com/OC 09 manuscripts/OC 09043. pdf Elzinga, P. , Poelmans, J. , Viaene, S. , Dedene, G. , Morsing, S. (2010) Terrorist threat assessment with Formal Concept Analysis. Proc. IEEE International Conference on Intelligence and Security Informatics. May 23 -26, 2010 Vancouver, Canada. ISBN 978 -1 -42446460 -9/10, 77 -82.
Conference proceedings: Accepted Vuylsteke, A. , Wen, Z. , Baesens, B. and Poelmans J. (2009). Consumers Online Information Search: A Cross-Cultural Study between China and Western Europe. Paper presented at Academic And Business Research Institute Conference 2009, Orlando, USA, available at http: //www. aabri. com/OC 09 manuscripts/OC 09043. pdf Elzinga, P. , Poelmans, J. , Viaene, S. , Dedene, G. , Morsing, S. (2010) Terrorist threat assessment with Formal Concept Analysis. Proc. IEEE International Conference on Intelligence and Security Informatics. May 23 -26, 2010 Vancouver, Canada. ISBN 978 -1 -42446460 -9/10, 77 -82.
 Conference proceeding, book chapter & Dutch publications Dejaeger, K. , Hamers, B. , Poelmans, J. , Baesens, B. (2010) A novel approach to the evaluation and improvement of data quality in the financial sector, submitted for 15 th International Conference on Information Quality (ICIQ 2010) UALR, Little Rock, Arkansas USA, Poelmans J, Van Hulle M, Elzinga P, Viaene S, Dedene G (2008) Topographic maps for domestic violence analysis. Self-organizing maps and the related tools, pp. 136 - 145. Vuylsteke A. , Poelmans J. , Baesens B. (2009) Online zoekgedrag van consumenten: China vs West. Europa, Business In-Zicht, December, 2 -3. Dejaeger K. , Ruelens J. , Van Gestel T. , Jacobs J. , Baesens B. , Poelmans J. , Hamers B. (2009) Evaluatie en verbetering van de datakwaliteit. Informatie, November , Jaargang 51/9, 8 -15.
Conference proceeding, book chapter & Dutch publications Dejaeger, K. , Hamers, B. , Poelmans, J. , Baesens, B. (2010) A novel approach to the evaluation and improvement of data quality in the financial sector, submitted for 15 th International Conference on Information Quality (ICIQ 2010) UALR, Little Rock, Arkansas USA, Poelmans J, Van Hulle M, Elzinga P, Viaene S, Dedene G (2008) Topographic maps for domestic violence analysis. Self-organizing maps and the related tools, pp. 136 - 145. Vuylsteke A. , Poelmans J. , Baesens B. (2009) Online zoekgedrag van consumenten: China vs West. Europa, Business In-Zicht, December, 2 -3. Dejaeger K. , Ruelens J. , Van Gestel T. , Jacobs J. , Baesens B. , Poelmans J. , Hamers B. (2009) Evaluatie en verbetering van de datakwaliteit. Informatie, November , Jaargang 51/9, 8 -15.
 Awards Nominated for best paper award at 8 th Industrial Conference on Data Mining (ICDM), Leipzig, Germany, July 16 -18, 2008 Winner of young professionals best paper award at 9 th Industrial Conference on Data Mining (ICDM), Leipzig, Germany, July 20 -22, 2009 Winner of best paper award at 10 th Industrial Conference on Data Mining (ICDM), Berlin, Germany, July 12 -14, 2010
Awards Nominated for best paper award at 8 th Industrial Conference on Data Mining (ICDM), Leipzig, Germany, July 16 -18, 2008 Winner of young professionals best paper award at 9 th Industrial Conference on Data Mining (ICDM), Leipzig, Germany, July 20 -22, 2009 Winner of best paper award at 10 th Industrial Conference on Data Mining (ICDM), Berlin, Germany, July 12 -14, 2010


