Mod 1 - MVA Defense-in-Depth Windows Security.pptx
- Количество слайдов: 23

Erdal Ozkaya | Most Valuable Professional, KEMP Technologies Milad Aslaner | Premier Field Engineer, Microsoft
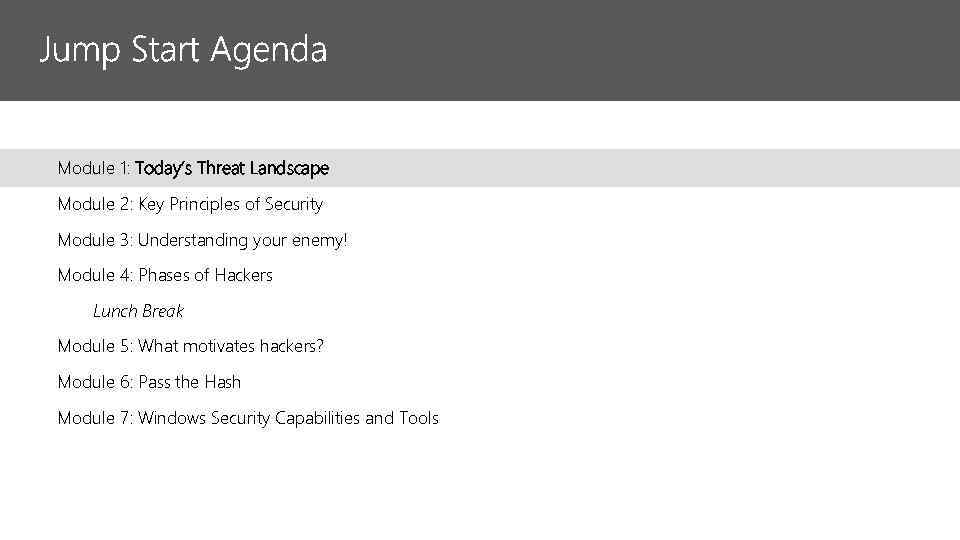
Module 1: Today’s Threat Landscape Module 2: Key Principles of Security Module 3: Understanding your enemy! Module 4: Phases of Hackers Lunch Break Module 5: What motivates hackers? Module 6: Pass the Hash Module 7: Windows Security Capabilities and Tools

Module Insights We will talk about the rapidly changing threat landscape and the importance of strong mitigation capabilities.

Erdal Ozkaya • @Erdal_Ozkaya • KEMP Technologies • Charles Sturt University • Microsoft MVP • Certified Ethical Hacker

DEMO How do you get hacked?

Warning! This Presentation Contains many information which you should not use in live targets or networks without permissions.

Target Audience This course is helpful for anyone interested in security, particularly IT Pros and Security Architects at midsized and enterprise organizations.

The threat landscape is changing rapidly. But this time it’s not just the attackers driving change, it’s your users.

2009 Defined environment 2014 Disappearing perimeter Mobility represents the end perimeter based security. Your perimeter is fading, maybe it’s already gone.

BYOD is a top priority and one of the biggest challenges But it’s not the only one when it comes to security.
The improvements that we’ve made in the Windows platforms have driven our adversaries to new tactics.

Attackers have set their sights on identity theft and they’re breaking into systems as you!
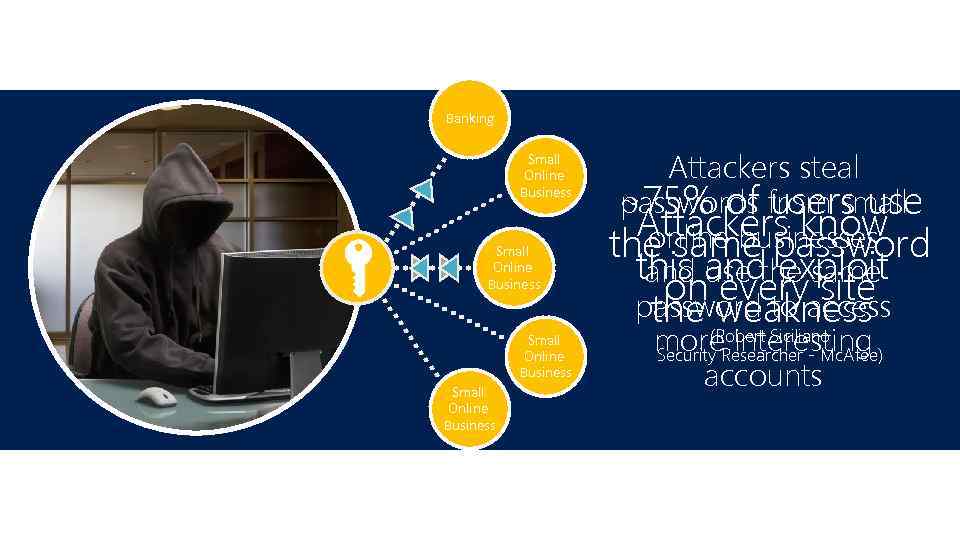
Banking Small Online Business Attackers steal passwords users use ~75% of from small Attackers know online businesses the same password this and exploit and use the same on everyaccess site password to the (Robert Siciliano weakness more. Researcher - Mc. Afee) interesting Security accounts

DEMO Need to knows on complex passwords…

There is a prolific and easily accessible black market that facilitates the buying and selling of identities, credit cards, etc. Personal information about you can almost certainly be found there!
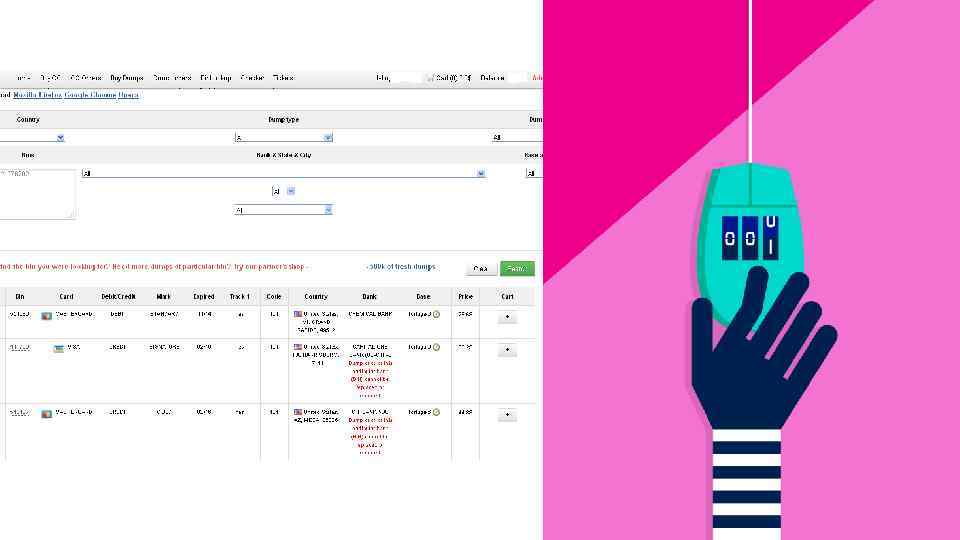

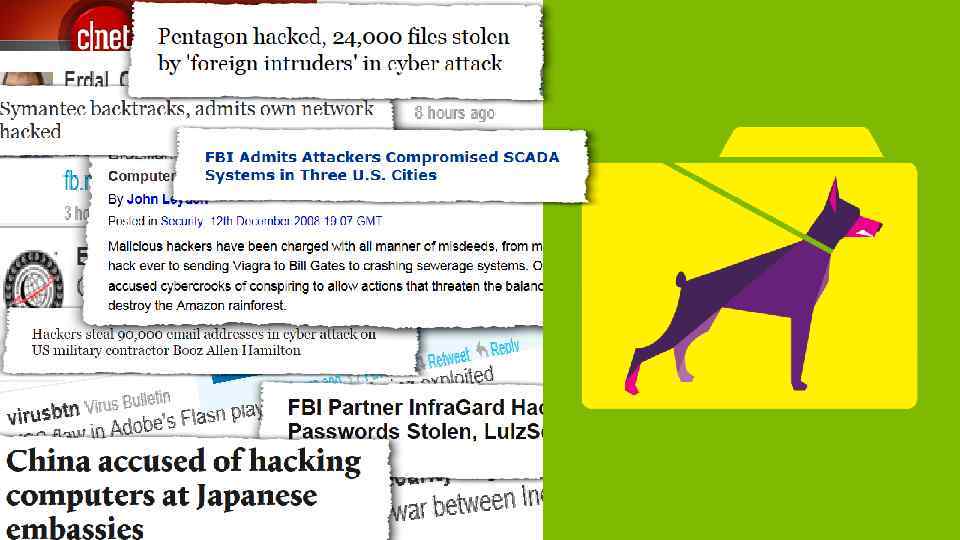
And so we have a perfect storm.
Connect with the speakers! @Erdal. Ozkaya @Milad. PFE http: //erdalozkaya. com/ https: //www. facebook. com/milad. aslaner

Tech. Net Virtual Labs Deep technical content and free product evaluations Hands-on deep technical labs Free, online, technical courses Download Microsoftware trials today. Find Hand On Labs. Take a free online course. Technet. microsoft. com/evalcenter Technet. microsoft. com/virtuallabs microsoftvirtualacademy. com

© 2013 Microsoft Corporation. All rights reserved. Microsoft, Windows, Office, Azure, System Center, Dynamics and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.
Mod 1 - MVA Defense-in-Depth Windows Security.pptx