56d79320e451bcb9e60ad03ebbcad867.ppt
- Количество слайдов: 29
 Entity Authentication (1) Frank Flanagan
Entity Authentication (1) Frank Flanagan
 Authentication n n (cf. chapter 10 of Handbook of Applied Cryptography) Entity Authentication § People, computers etc § Normally interactive Protocol § Proves timeliness n Message Authentication § Message must contain everything necessary to authenticate itself n Both forms may be used to establish session keys
Authentication n n (cf. chapter 10 of Handbook of Applied Cryptography) Entity Authentication § People, computers etc § Normally interactive Protocol § Proves timeliness n Message Authentication § Message must contain everything necessary to authenticate itself n Both forms may be used to establish session keys
 Definition n Entity Authentication is a process where a claimant or prover (A) proves, to the satisfaction of a verifier (B), § its identity § That A took part in the proof n Desirable Properties § A can authenticate itself to B § B can not reuse information from the exchange to impersonate A to another party § The probability that C can successfully convince B that it is actually A is negligibly small even with C has observed all the communications from a large number of authentications by A to B
Definition n Entity Authentication is a process where a claimant or prover (A) proves, to the satisfaction of a verifier (B), § its identity § That A took part in the proof n Desirable Properties § A can authenticate itself to B § B can not reuse information from the exchange to impersonate A to another party § The probability that C can successfully convince B that it is actually A is negligibly small even with C has observed all the communications from a large number of authentications by A to B
 Assurances n n n Not all authentication protocols provide all of the properties we might want Authentication protocols only provide an assurance of identity at the completion of the protocol Session Hijacking!
Assurances n n n Not all authentication protocols provide all of the properties we might want Authentication protocols only provide an assurance of identity at the completion of the protocol Session Hijacking!
 What is Authentication Based on n n A Secret Types of Authentication § Information – password, PINs and demonstration of knowledge with challenge response protocols § Possession – smart cards, Secure. ID tokens etc § Inherent attributes of the entity, biometrics, processor ID numbers etc.
What is Authentication Based on n n A Secret Types of Authentication § Information – password, PINs and demonstration of knowledge with challenge response protocols § Possession – smart cards, Secure. ID tokens etc § Inherent attributes of the entity, biometrics, processor ID numbers etc.
 Properties of Authentication Protocols n Unilateral or Mutual authentication § A proves its identity to B or § A and B prove their identities to one another n n n Computational efficiency – this may be counter intuitive Communication efficiency Third party involvement Provable security Zero knowledge Storage of secrets – stored plaintext and even encrypted secrets are a weak point
Properties of Authentication Protocols n Unilateral or Mutual authentication § A proves its identity to B or § A and B prove their identities to one another n n n Computational efficiency – this may be counter intuitive Communication efficiency Third party involvement Provable security Zero knowledge Storage of secrets – stored plaintext and even encrypted secrets are a weak point
 Basic Password Scheme n B stores a plaintext file of passwords including A’s password § Password file should be read and write protected using OS mechanisms § User enters password and is compared with file § No protection against privileged users § No protection against exploit that obtain file § Unlikely as it may seem such schemes are still in use typically as application passwords by programmers who should know better
Basic Password Scheme n B stores a plaintext file of passwords including A’s password § Password file should be read and write protected using OS mechanisms § User enters password and is compared with file § No protection against privileged users § No protection against exploit that obtain file § Unlikely as it may seem such schemes are still in use typically as application passwords by programmers who should know better
 “Encrypted” Password File n Replaces the password file of the previous example with one in which a one way function has been applied to the passwords § Replay attacks – straight wire tap a la telnet § Masquerading as verifier - Program that produces login prompt around since early 1970’s - Privately owned ATM installed to capture magnetic strips and PINs then issue error message without issuing cash § Early Unix systems allowed deletion or replacement of the hash - Fixed using shadow file § Offline cracking of file
“Encrypted” Password File n Replaces the password file of the previous example with one in which a one way function has been applied to the passwords § Replay attacks – straight wire tap a la telnet § Masquerading as verifier - Program that produces login prompt around since early 1970’s - Privately owned ATM installed to capture magnetic strips and PINs then issue error message without issuing cash § Early Unix systems allowed deletion or replacement of the hash - Fixed using shadow file § Offline cracking of file
 The Memory Problem n People can not remember, nor are they willing to type, passwords with sufficient entropy § Do you want to type “ 5*c]v 9 Hc, >n. Mp{T^” every time you want to log in? § Do you think you could remember this? § People pick passwords that are reasonably short, consist of a word or a combination of words in their own native language § English has very little entropy (~2. 3 bits/character) - Therefore a 20 character English password has about 46 bits entropy; this is nearly enough but nobody uses 20 character passwords § Entropy can be increased by using non English characters - Do not pick English words and substitute 1 for A, 2 for B … This is well known - Must use mixed case
The Memory Problem n People can not remember, nor are they willing to type, passwords with sufficient entropy § Do you want to type “ 5*c]v 9 Hc, >n. Mp{T^” every time you want to log in? § Do you think you could remember this? § People pick passwords that are reasonably short, consist of a word or a combination of words in their own native language § English has very little entropy (~2. 3 bits/character) - Therefore a 20 character English password has about 46 bits entropy; this is nearly enough but nobody uses 20 character passwords § Entropy can be increased by using non English characters - Do not pick English words and substitute 1 for A, 2 for B … This is well known - Must use mixed case
 Entropy n n Basically uncertainty Flipping a coin gives one bit on entropy ASCII (which is what passwords are usually based on) is a 7 bit code, discounting control characters such as
Entropy n n Basically uncertainty Flipping a coin gives one bit on entropy ASCII (which is what passwords are usually based on) is a 7 bit code, discounting control characters such as
 Passwords from Social Engineering n There a number of good bets for passwords: § Post-its with passwords written on them § Something with a password written on it in the pen drawer of a pedestal § Standing over some bodies shoulder § Even listening to the number of keystrokes gives useful information for a cracking program - If the user can actually type non alphabetics will take longer - A timing analysis of the keystrokes could reveal a lot
Passwords from Social Engineering n There a number of good bets for passwords: § Post-its with passwords written on them § Something with a password written on it in the pen drawer of a pedestal § Standing over some bodies shoulder § Even listening to the number of keystrokes gives useful information for a cracking program - If the user can actually type non alphabetics will take longer - A timing analysis of the keystrokes could reveal a lot
 Online Attacks n n Online attacks consist of either typing usernames/ passwords interactively or via a program to an active verifier A number of measures have restricted the usefulness of such attacks: § Many systems lock out users after a small number of tries § Most systems deliberately waste considerable time after a failed attempts n Locking out users may lead to a denial of service attack
Online Attacks n n Online attacks consist of either typing usernames/ passwords interactively or via a program to an active verifier A number of measures have restricted the usefulness of such attacks: § Many systems lock out users after a small number of tries § Most systems deliberately waste considerable time after a failed attempts n Locking out users may lead to a denial of service attack
 Password Files n Passwords are normally processed through a one way function not actually encrypted § Main reason is export control § Unix uses a modified DES - Function is iterated a number of times to consume extra CPU in a cracking attack - Modification makes most DES chips unusable for cracking attack - High speed FPGA would make excellent cracker n Password is reduced to a hash
Password Files n Passwords are normally processed through a one way function not actually encrypted § Main reason is export control § Unix uses a modified DES - Function is iterated a number of times to consume extra CPU in a cracking attack - Modification makes most DES chips unusable for cracking attack - High speed FPGA would make excellent cracker n Password is reduced to a hash
 Password Cracking n Could just try all combinations of characters starting at minimum length § § This is a lot of effort Remember that English has very low entropy Dictionary attacks reduce the search space dramatically Modified dictionary attacks can cope with known rules - Must contain a single non alphabetic - Must contain mixed case - Must not be in a standard dictionary § Remember users will do almost anything possible to minimize their effort - Rule 6 character password with one non alphabetic - Password FRED 6 - Perpetrator experienced engineer with poor typing skills – very easy to pick out with one finger
Password Cracking n Could just try all combinations of characters starting at minimum length § § This is a lot of effort Remember that English has very low entropy Dictionary attacks reduce the search space dramatically Modified dictionary attacks can cope with known rules - Must contain a single non alphabetic - Must contain mixed case - Must not be in a standard dictionary § Remember users will do almost anything possible to minimize their effort - Rule 6 character password with one non alphabetic - Password FRED 6 - Perpetrator experienced engineer with poor typing skills – very easy to pick out with one finger
 Naive Password Cracking n n Take a copy of the password file and a dictionary Sort the password file by hash value Hash words from the dictionary Compare hashes § Birthday paradox limits number of trials that will be needed n This simple attack is restricted somewhat by salting § A per user value (sometimes the username) is used to modify the entered password prior to the one way function § With salting two users with the same password will not have the same encrypted password § Exhaustive search for a single user’s password reminds the same § Salting does however reduce the efficiency of an attack against a large password file
Naive Password Cracking n n Take a copy of the password file and a dictionary Sort the password file by hash value Hash words from the dictionary Compare hashes § Birthday paradox limits number of trials that will be needed n This simple attack is restricted somewhat by salting § A per user value (sometimes the username) is used to modify the entered password prior to the one way function § With salting two users with the same password will not have the same encrypted password § Exhaustive search for a single user’s password reminds the same § Salting does however reduce the efficiency of an attack against a large password file
 Pass Phrases n n n Pass Phrases are phrases of language used in place of passwords Being longer than passwords they have more entropy and are somewhat better Phrases as absurd as possible (but unlike these examples original): § A cup of fur § Tangerine trees and marmalade skies
Pass Phrases n n n Pass Phrases are phrases of language used in place of passwords Being longer than passwords they have more entropy and are somewhat better Phrases as absurd as possible (but unlike these examples original): § A cup of fur § Tangerine trees and marmalade skies
 PINs n n Personal Identification Numbers (PINs) are much beloved of banks Given their length and the fact that they are only decimal digits (~3. 5 bits of entropy each) a 4 digit PIN is only about 14 bits of entropy PINs are truly awful except perhaps in the ATM type context where the card is confiscated after 3 attempts GSM SIM cards use a variant where on three bad attempts to enter a PIN the user must move to enter a PUK which has significant entropy
PINs n n Personal Identification Numbers (PINs) are much beloved of banks Given their length and the fact that they are only decimal digits (~3. 5 bits of entropy each) a 4 digit PIN is only about 14 bits of entropy PINs are truly awful except perhaps in the ATM type context where the card is confiscated after 3 attempts GSM SIM cards use a variant where on three bad attempts to enter a PIN the user must move to enter a PUK which has significant entropy
 Password Ageing n Password Ageing helps from at least two perspectives: § A hacker in possession of a password file may not be able to complete an attack prior to the passwords being replaced § If re-use of earlier passwords is disallowed passwords may improve with time § Passwords gathered through social engineering are replaced n It hurts from one main perspective § Users often do not remember the new password § This produces an admin overhead § It is critical not to make users feel like idiots when they forget passwords – next time they will write it down
Password Ageing n Password Ageing helps from at least two perspectives: § A hacker in possession of a password file may not be able to complete an attack prior to the passwords being replaced § If re-use of earlier passwords is disallowed passwords may improve with time § Passwords gathered through social engineering are replaced n It hurts from one main perspective § Users often do not remember the new password § This produces an admin overhead § It is critical not to make users feel like idiots when they forget passwords – next time they will write it down
 One Time Passwords n n n An improvement on conventional passwords is to use a shared list of passwords each of which can only be used once This involves a lot of shared secrets and is not really suitable for use by humans directly It is possible for the verifier to generate a new password, encrypt it and transmit it to the user at the start of the session (iterated passwords) in the event of communications failures/aborted sessions this does not work well.
One Time Passwords n n n An improvement on conventional passwords is to use a shared list of passwords each of which can only be used once This involves a lot of shared secrets and is not really suitable for use by humans directly It is possible for the verifier to generate a new password, encrypt it and transmit it to the user at the start of the session (iterated passwords) in the event of communications failures/aborted sessions this does not work well.
 Challenge Response (Strong Authentication) n Verifier generates a time varying challenge § Typically random n Response is a function of challenge + secret and proves timely knowledge of the secret without divulging
Challenge Response (Strong Authentication) n Verifier generates a time varying challenge § Typically random n Response is a function of challenge + secret and proves timely knowledge of the secret without divulging
 Multi Factor Authentication n Two factor uses two of: § Knowledge § Possession § Inherent attribute n n Three Factor uses all three Knowledge + Possession is often known as “know something bring something”
Multi Factor Authentication n Two factor uses two of: § Knowledge § Possession § Inherent attribute n n Three Factor uses all three Knowledge + Possession is often known as “know something bring something”
 Token Based Authentication n n … Secure. ID – Username - Password Smart Card – U to T Casque Username - Password Bank Cards - Pin I-Button – U - T
Token Based Authentication n n … Secure. ID – Username - Password Smart Card – U to T Casque Username - Password Bank Cards - Pin I-Button – U - T
 Token Based Authentication n n In many cases user authenticates to token giving effective two factor authentication In other cases the user also enters a username/password pair again giving two factor authentication Tokens are difficult to duplicate Stolen tokens are usually of little use except in side channel attacks
Token Based Authentication n n In many cases user authenticates to token giving effective two factor authentication In other cases the user also enters a username/password pair again giving two factor authentication Tokens are difficult to duplicate Stolen tokens are usually of little use except in side channel attacks
 Side Channel n n n n Anything other then the intended means of communication that conveys information Power Electromagnetic Waves Timing Audio Modulation of LED’s by power Modulation of amplitude on signals by internal operations Side channel leakage is an analogue quantity, it can be attenuated but it will never go away
Side Channel n n n n Anything other then the intended means of communication that conveys information Power Electromagnetic Waves Timing Audio Modulation of LED’s by power Modulation of amplitude on signals by internal operations Side channel leakage is an analogue quantity, it can be attenuated but it will never go away
 Side Channel – A simple example n n A burglar is stealing from your house when you return home He hides in a cupboard in a bedroom in which the lights are on After about 10 minutes the lights dim slightly; he pauses a couple of moments and then he casually gets out of the cupboard and walks out the front door How could he have known it was safe to leave
Side Channel – A simple example n n A burglar is stealing from your house when you return home He hides in a cupboard in a bedroom in which the lights are on After about 10 minutes the lights dim slightly; he pauses a couple of moments and then he casually gets out of the cupboard and walks out the front door How could he have known it was safe to leave
 SIde Channel Physical Basis n n Power supplies are not perfect they exhibit some resistance and inductance PCB traces are not perfect they are radio antennas, they exhibit cross talk to nearby traces, they have resistance Optical fibres if bent just below their minimum radius of curvature leak sufficient light to be coupled to Ideally all security algorithms should take uniform time for all data and for all keys § They should not reject early with failure § They should behave identically for all failures not provide a choice of errors – Invalid Login not Invalid Username and Invalid Password
SIde Channel Physical Basis n n Power supplies are not perfect they exhibit some resistance and inductance PCB traces are not perfect they are radio antennas, they exhibit cross talk to nearby traces, they have resistance Optical fibres if bent just below their minimum radius of curvature leak sufficient light to be coupled to Ideally all security algorithms should take uniform time for all data and for all keys § They should not reject early with failure § They should behave identically for all failures not provide a choice of errors – Invalid Login not Invalid Username and Invalid Password
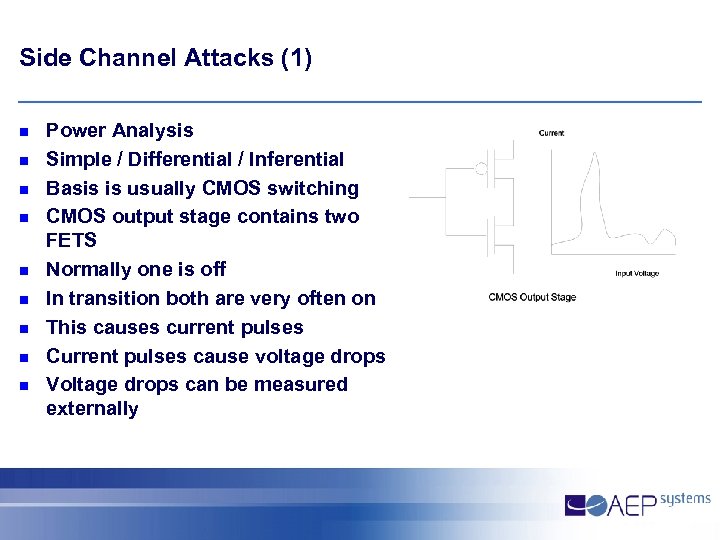 Side Channel Attacks (1) n n n n n Power Analysis Simple / Differential / Inferential Basis is usually CMOS switching CMOS output stage contains two FETS Normally one is off In transition both are very often on This causes current pulses Current pulses cause voltage drops Voltage drops can be measured externally
Side Channel Attacks (1) n n n n n Power Analysis Simple / Differential / Inferential Basis is usually CMOS switching CMOS output stage contains two FETS Normally one is off In transition both are very often on This causes current pulses Current pulses cause voltage drops Voltage drops can be measured externally
 IPA n n n I believe the neatest power attack of all time was Paul Fahan’s IPA attack CHES 99 or 2000 C 20, 000 signings were performed with a single smart card Subsequently the recorded power consumption from one signing from by any smart card from the same family (die) allowed the key to be recovered This would be capable of use in say a petrol station with a digital storage oscilloscope or equivalent under the counter capturing each customer’s card Smart cards have been improved since this attack and as presented this attack would not work against the current generation There is no reason to presume that a new and improved attack would fail
IPA n n n I believe the neatest power attack of all time was Paul Fahan’s IPA attack CHES 99 or 2000 C 20, 000 signings were performed with a single smart card Subsequently the recorded power consumption from one signing from by any smart card from the same family (die) allowed the key to be recovered This would be capable of use in say a petrol station with a digital storage oscilloscope or equivalent under the counter capturing each customer’s card Smart cards have been improved since this attack and as presented this attack would not work against the current generation There is no reason to presume that a new and improved attack would fail
 The Problem with Compromised Tokens n n n It is reasonably easy to convince say a credit card company that your magnetic stripe card has been cloned and used fraudulently Everyone puts substantially more trust in devices such as smart cards Excessive trust in technology will place the victims of such fraud in an invidious position
The Problem with Compromised Tokens n n n It is reasonably easy to convince say a credit card company that your magnetic stripe card has been cloned and used fraudulently Everyone puts substantially more trust in devices such as smart cards Excessive trust in technology will place the victims of such fraud in an invidious position


