9341d97b6d45045ddcb739c24b0bd392.ppt
- Количество слайдов: 31
 Enterprise Secure and Assured Solutions for the Enterprise Space Claus Troppmair Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 1
Enterprise Secure and Assured Solutions for the Enterprise Space Claus Troppmair Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 1
 AGENDA § Juniper Networks Today § Critical Networking Issues § Secure and Assured Networking Solutions § The Juniper Difference § Conclusion Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 2
AGENDA § Juniper Networks Today § Critical Networking Issues § Secure and Assured Networking Solutions § The Juniper Difference § Conclusion Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 2
 Leader in Secure and Assured Communications § The most complex and strategic networks in the world are built on Juniper platforms • Thousands of service providers, including the top 25 globally • 77% of the Fortune 100 • Network intensive businesses, governments and educational institutions • IT is strategic to the business • high rate of change in their businesses • reducing non-IP protocols to address rapid business changes • Recognized market leader in secure and assured networking § More than $1. 3 B in revenue, over 170% earnings growth on over 90% revenue growth in 2004 Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 3
Leader in Secure and Assured Communications § The most complex and strategic networks in the world are built on Juniper platforms • Thousands of service providers, including the top 25 globally • 77% of the Fortune 100 • Network intensive businesses, governments and educational institutions • IT is strategic to the business • high rate of change in their businesses • reducing non-IP protocols to address rapid business changes • Recognized market leader in secure and assured networking § More than $1. 3 B in revenue, over 170% earnings growth on over 90% revenue growth in 2004 Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 3
 Juniper Networks Corporate Facts Juniper Networks revenue* Juniper Security Products revenue (proforma) 58% revenue growth year-over-year * * Includes Q 1 Net. Screen revenue and proforma Q 2 Juniper security revenues of $101 M Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 4
Juniper Networks Corporate Facts Juniper Networks revenue* Juniper Security Products revenue (proforma) 58% revenue growth year-over-year * * Includes Q 1 Net. Screen revenue and proforma Q 2 Juniper security revenues of $101 M Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 4
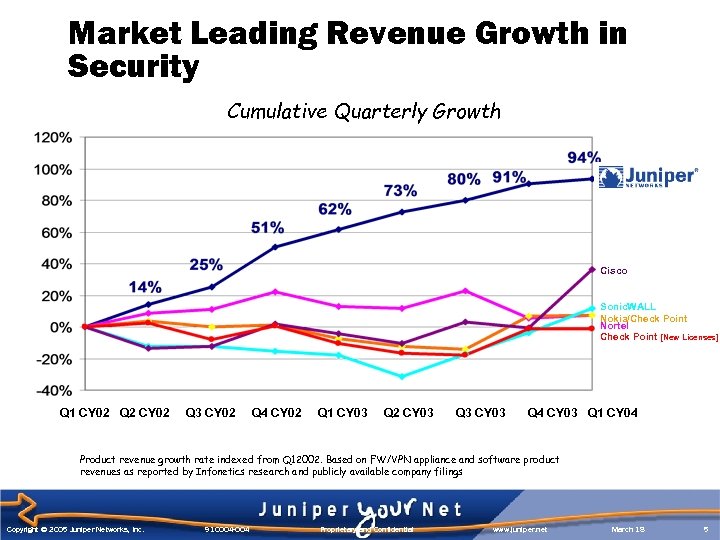 Market Leading Revenue Growth in Security Cumulative Quarterly Growth Cisco Sonic. WALL Nokia/Check Point Nortel Check Point [New Licenses] Q 1 CY 02 Q 2 CY 02 Q 3 CY 02 Q 4 CY 02 Q 1 CY 03 Q 2 CY 03 Q 3 CY 03 Q 4 CY 03 Q 1 CY 04 Product revenue growth rate indexed from Q 12002. Based on FW/VPN appliance and software product revenues as reported by Infonetics research and publicly available company filings Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 5
Market Leading Revenue Growth in Security Cumulative Quarterly Growth Cisco Sonic. WALL Nokia/Check Point Nortel Check Point [New Licenses] Q 1 CY 02 Q 2 CY 02 Q 3 CY 02 Q 4 CY 02 Q 1 CY 03 Q 2 CY 03 Q 3 CY 03 Q 4 CY 03 Q 1 CY 04 Product revenue growth rate indexed from Q 12002. Based on FW/VPN appliance and software product revenues as reported by Infonetics research and publicly available company filings Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 5
 Juniper Brasil Since 2000 with offices in Sao Paulo, Rio de Janeiro and Brasilia In charge of all NGN networks currently available in Brazil Enterprise customers in Govern, Education, Finance, Manufacturing, Services In country 24 x 7 Service and Support Training Centre in Brazil Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 6
Juniper Brasil Since 2000 with offices in Sao Paulo, Rio de Janeiro and Brasilia In charge of all NGN networks currently available in Brazil Enterprise customers in Govern, Education, Finance, Manufacturing, Services In country 24 x 7 Service and Support Training Centre in Brazil Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 6
 Vision is Supported by Long History of Innovation § § § § § t Firs Integrated firewall/VPN appliance based on custom ASIC t 8 x. OC-48/STM-16 MPLS cable router Firs t Firs Edge-optimized router and policy-based management control platform t Firs Full-performance 8 x. OC-192 c/STM-64 platform t Firs 1 Gbps firewall/VPN and 12 Gbps firewall appliances t Edge control for speeds up to OC 12 Firs rst Router with integrated XML instrumentation Fi t Firs Virtual system architecture for efficient security segmentation t Production-ready, high-performance IPv 6 routing solution Firs t Half-rack platform with 32 OC-192 c/ STM-64 Firs t Firs Stateful Signature Detection to reducetfalse alarms s t Edge control for speeds up to OC 48 Firs Production-ready GMPLS solution on a router t t Deep Inspection firewall technology Firs BGP-based VPLS implementation, operating concurrently t with all other VPN types Firs t First SSL VPN appliance First secure cross-enterprise meeting appliance Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 7
Vision is Supported by Long History of Innovation § § § § § t Firs Integrated firewall/VPN appliance based on custom ASIC t 8 x. OC-48/STM-16 MPLS cable router Firs t Firs Edge-optimized router and policy-based management control platform t Firs Full-performance 8 x. OC-192 c/STM-64 platform t Firs 1 Gbps firewall/VPN and 12 Gbps firewall appliances t Edge control for speeds up to OC 12 Firs rst Router with integrated XML instrumentation Fi t Firs Virtual system architecture for efficient security segmentation t Production-ready, high-performance IPv 6 routing solution Firs t Half-rack platform with 32 OC-192 c/ STM-64 Firs t Firs Stateful Signature Detection to reducetfalse alarms s t Edge control for speeds up to OC 48 Firs Production-ready GMPLS solution on a router t t Deep Inspection firewall technology Firs BGP-based VPLS implementation, operating concurrently t with all other VPN types Firs t First SSL VPN appliance First secure cross-enterprise meeting appliance Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 7
 Routing Marketshare – 2004 Rollup Total SP Routing RBAK 3% NT 2% Core Routing JNPR 31% Other 5% CSCO 57% CSCO 62% Edge Routing RBAK 6% NT 4% JNPR 33% Broadband Aggregation JNPR 30% RBAK 7% CSCO 53% NT 9% JNPR 34% CSCO 50% Source: Gartner Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 8
Routing Marketshare – 2004 Rollup Total SP Routing RBAK 3% NT 2% Core Routing JNPR 31% Other 5% CSCO 57% CSCO 62% Edge Routing RBAK 6% NT 4% JNPR 33% Broadband Aggregation JNPR 30% RBAK 7% CSCO 53% NT 9% JNPR 34% CSCO 50% Source: Gartner Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 8
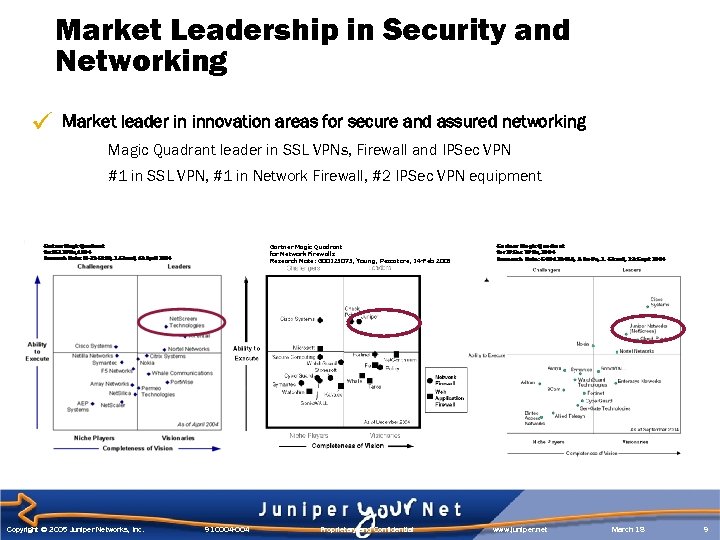 Market Leadership in Security and Networking Market leader in innovation areas for secure and assured networking Magic Quadrant leader in SSL VPNs, Firewall and IPSec VPN #1 in SSL VPN, #1 in Network Firewall, #2 IPSec VPN equipment Gartner Magic Quadrant for Network Firewalls Research Note: G 00125075, Young, Pescatore, 14 -Feb 2005 Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 9
Market Leadership in Security and Networking Market leader in innovation areas for secure and assured networking Magic Quadrant leader in SSL VPNs, Firewall and IPSec VPN #1 in SSL VPN, #1 in Network Firewall, #2 IPSec VPN equipment Gartner Magic Quadrant for Network Firewalls Research Note: G 00125075, Young, Pescatore, 14 -Feb 2005 Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 9
 Juniper Acquisitions • Peribit Networks • Peribit improves enterprise business efficiencies by resolving the technical limitations of WANs. • Peribit platforms and software provide customers with increased WAN capacity, faster application performance, prioritized application delivery, and total WAN visibility. • Redline Networks designs and manufactures network appliances that maximize the performance, flexibility and scalability of web-enabled enterprise data centers and sites. • The company's family of E|X application front ends enable users to control and customize any HTTP-based environment while reducing infrastructure cost and complexity. • Multi-function “Application Front End” (AFE) appliances offload backend servers, accelerate user response time over the WAN and collapse multiple legacy data center boxes into a single appliance • Kagoor Networks • Kagoor designs and delivers session border controllers (SBC) • Platforms overcome technical roadblocks including security, service assurance, interworking, regulatory compliance, and management issues typically encountered at Vo. IP network borders • Kagoor enables seamless, secure, and reliable end-to-end Vo. IP networks Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 10
Juniper Acquisitions • Peribit Networks • Peribit improves enterprise business efficiencies by resolving the technical limitations of WANs. • Peribit platforms and software provide customers with increased WAN capacity, faster application performance, prioritized application delivery, and total WAN visibility. • Redline Networks designs and manufactures network appliances that maximize the performance, flexibility and scalability of web-enabled enterprise data centers and sites. • The company's family of E|X application front ends enable users to control and customize any HTTP-based environment while reducing infrastructure cost and complexity. • Multi-function “Application Front End” (AFE) appliances offload backend servers, accelerate user response time over the WAN and collapse multiple legacy data center boxes into a single appliance • Kagoor Networks • Kagoor designs and delivers session border controllers (SBC) • Platforms overcome technical roadblocks including security, service assurance, interworking, regulatory compliance, and management issues typically encountered at Vo. IP network borders • Kagoor enables seamless, secure, and reliable end-to-end Vo. IP networks Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 10
 Serving over 8, 000 of the World’s Most Strategic Networks Service Providers Copyright © 2005 Juniper Networks, Inc. 910004 -004 Enterprises Proprietary and Confidential www. juniper. net March 18 11
Serving over 8, 000 of the World’s Most Strategic Networks Service Providers Copyright © 2005 Juniper Networks, Inc. 910004 -004 Enterprises Proprietary and Confidential www. juniper. net March 18 11
 Juniper Networks Global Alliances Juniper Works with Best-of-breed Partners Global Elite Partners Security Alliances Copyright © 2005 Juniper Networks, Inc. 910004 -004 Infrastructure Alliances Proprietary and Confidential www. juniper. net March 18 12
Juniper Networks Global Alliances Juniper Works with Best-of-breed Partners Global Elite Partners Security Alliances Copyright © 2005 Juniper Networks, Inc. 910004 -004 Infrastructure Alliances Proprietary and Confidential www. juniper. net March 18 12
 Business Cycles Accelerating growth § Faster, deeper cycles § Globally extended enterprise § Fixed costs low hamper business flexibility, variable cost structure needed § “On demand” business & network 4% 2% 0% -2% -4% time Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 13
Business Cycles Accelerating growth § Faster, deeper cycles § Globally extended enterprise § Fixed costs low hamper business flexibility, variable cost structure needed § “On demand” business & network 4% 2% 0% -2% -4% time Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 13
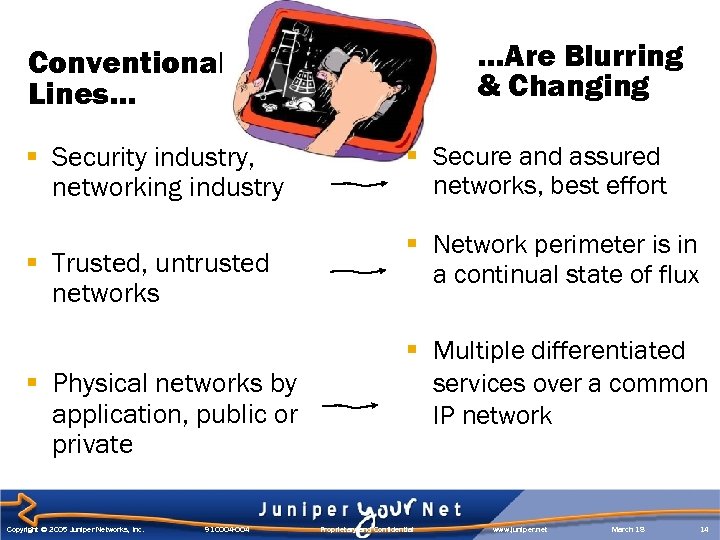 …Are Blurring & Changing Conventional Lines… § Security industry, networking industry § Trusted, untrusted networks § Physical networks by application, public or private Copyright © 2005 Juniper Networks, Inc. 910004 -004 § Secure and assured networks, best effort § Network perimeter is in a continual state of flux § Multiple differentiated services over a common IP network Proprietary and Confidential www. juniper. net March 18 14
…Are Blurring & Changing Conventional Lines… § Security industry, networking industry § Trusted, untrusted networks § Physical networks by application, public or private Copyright © 2005 Juniper Networks, Inc. 910004 -004 § Secure and assured networks, best effort § Network perimeter is in a continual state of flux § Multiple differentiated services over a common IP network Proprietary and Confidential www. juniper. net March 18 14
 These Changes Bring Difficult Problems Historic Trade Off In Networking You can have great economics and sharing OR you can have great security, quality, reliability and control…. you can’t have both together in one place of ee ucture r Deg astr r Inf ring Sha Degree of Assurance (Security, Reliability, Quality) Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 15
These Changes Bring Difficult Problems Historic Trade Off In Networking You can have great economics and sharing OR you can have great security, quality, reliability and control…. you can’t have both together in one place of ee ucture r Deg astr r Inf ring Sha Degree of Assurance (Security, Reliability, Quality) Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 15
 Juniper’s Success Comes From Breaking Through This Trade-off Secure and Assured Network of ee ucture r Deg astr r Inf ring Sha Degree of Assurance (Security, Reliability, Quality) Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 16
Juniper’s Success Comes From Breaking Through This Trade-off Secure and Assured Network of ee ucture r Deg astr r Inf ring Sha Degree of Assurance (Security, Reliability, Quality) Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 16
 Evolution of the Enterprise Increasing Demands Require New Approaches § Increasing use of small packet applications: multi-media, streaming media, Vo. IP, etc. § Make traffic decisions with low latency to ensure applications are not affected § Increasing demand for remote network connectivity: from home, on the road, on the go. PDA’s wireless § Application vulnerabilities are on the rise, application attacks are growing in sophistication Copyright © 2005 Juniper Networks, Inc. 910004 -004 Ave Lat rag e Pa cke enc y /Ji tte r. T t. S ole ran ize ce s& on n i o ct ne ecti n n ion Co onn tio tect a of /c lic pro # alue p v Ap ss/ ne re a aw Proprietary and Confidential Time www. juniper. net March 18 17
Evolution of the Enterprise Increasing Demands Require New Approaches § Increasing use of small packet applications: multi-media, streaming media, Vo. IP, etc. § Make traffic decisions with low latency to ensure applications are not affected § Increasing demand for remote network connectivity: from home, on the road, on the go. PDA’s wireless § Application vulnerabilities are on the rise, application attacks are growing in sophistication Copyright © 2005 Juniper Networks, Inc. 910004 -004 Ave Lat rag e Pa cke enc y /Ji tte r. T t. S ole ran ize ce s& on n i o ct ne ecti n n ion Co onn tio tect a of /c lic pro # alue p v Ap ss/ ne re a aw Proprietary and Confidential Time www. juniper. net March 18 17
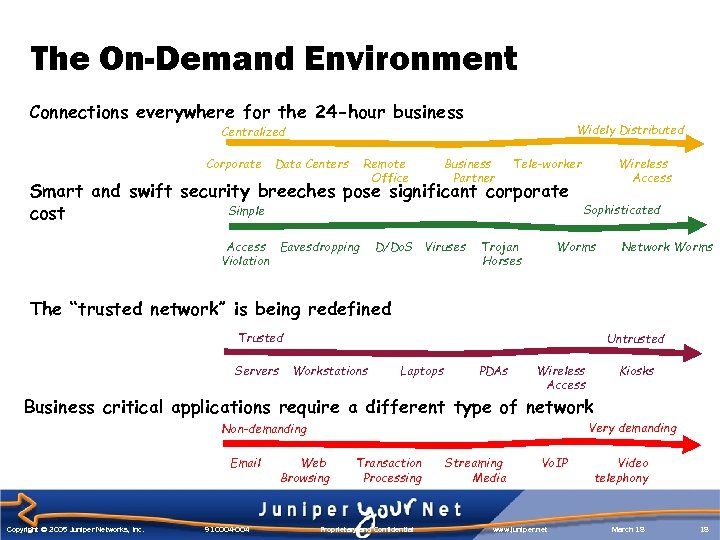 The On-Demand Environment Connections everywhere for the 24 -hour business Widely Distributed Centralized Corporate Data Centers Remote Office Business Partner Tele-worker Smart and swift security breeches pose significant corporate Simple cost Access Eavesdropping Violation D/Do. S Viruses Trojan Horses Wireless Access Sophisticated Worms Network Worms The “trusted network” is being redefined Trusted Servers Untrusted Workstations Laptops PDAs Wireless Access Kiosks Business critical applications require a different type of network Very demanding Non-demanding Email Copyright © 2005 Juniper Networks, Inc. 910004 -004 Web Browsing Transaction Processing Proprietary and Confidential Streaming Media Vo. IP www. juniper. net Video telephony March 18 18
The On-Demand Environment Connections everywhere for the 24 -hour business Widely Distributed Centralized Corporate Data Centers Remote Office Business Partner Tele-worker Smart and swift security breeches pose significant corporate Simple cost Access Eavesdropping Violation D/Do. S Viruses Trojan Horses Wireless Access Sophisticated Worms Network Worms The “trusted network” is being redefined Trusted Servers Untrusted Workstations Laptops PDAs Wireless Access Kiosks Business critical applications require a different type of network Very demanding Non-demanding Email Copyright © 2005 Juniper Networks, Inc. 910004 -004 Web Browsing Transaction Processing Proprietary and Confidential Streaming Media Vo. IP www. juniper. net Video telephony March 18 18
 Secure and Assured Networking Branch Office Internet Regional Office or Medium Central Site Infranet IP/MPLS Layer 2, FR, ATM DMZ Remote or Mobile Employee/ Partner/Customer Central Site Upward Application Intelligence INWARD OUTWARD Employees, Applications, Information Assets Data and Intellectual Property Copyright © 2005 Juniper Networks, Inc. 910004 -004 External Users, Public Networks, Devices Proprietary and Confidential www. juniper. net March 18 19
Secure and Assured Networking Branch Office Internet Regional Office or Medium Central Site Infranet IP/MPLS Layer 2, FR, ATM DMZ Remote or Mobile Employee/ Partner/Customer Central Site Upward Application Intelligence INWARD OUTWARD Employees, Applications, Information Assets Data and Intellectual Property Copyright © 2005 Juniper Networks, Inc. 910004 -004 External Users, Public Networks, Devices Proprietary and Confidential www. juniper. net March 18 19
 Secure and Assured Platforms for Carriers and Enterprises Inside Enterprise Gateway Carrier Edge Core Access Network Extended Customers Enterprise Mobile Workers Day Extenders Sales Business Partners HR Finance Fixed Telecommuters Department Servers Branch Offices DMZ Data Center • Purpose-built platforms delivering performance, stability and control • Applications and services supported at scale • User and application aware Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 20
Secure and Assured Platforms for Carriers and Enterprises Inside Enterprise Gateway Carrier Edge Core Access Network Extended Customers Enterprise Mobile Workers Day Extenders Sales Business Partners HR Finance Fixed Telecommuters Department Servers Branch Offices DMZ Data Center • Purpose-built platforms delivering performance, stability and control • Applications and services supported at scale • User and application aware Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 20
 Juniper Vision Status Quo Networking is Not Good Enough § Networks are laboring under extraneous traffic loads • Average of 30% of network traffic consists of worms, file sharing or peer-to-peer traffic that is not officially allowed Economics dictating a converged IP infrastructure for key applications. • IP must evolve to support any application with assurance § Performance § Juniper Status quo Protection of Network infrastructure is as important as protecting the applications and users Risk Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 21
Juniper Vision Status Quo Networking is Not Good Enough § Networks are laboring under extraneous traffic loads • Average of 30% of network traffic consists of worms, file sharing or peer-to-peer traffic that is not officially allowed Economics dictating a converged IP infrastructure for key applications. • IP must evolve to support any application with assurance § Performance § Juniper Status quo Protection of Network infrastructure is as important as protecting the applications and users Risk Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 21
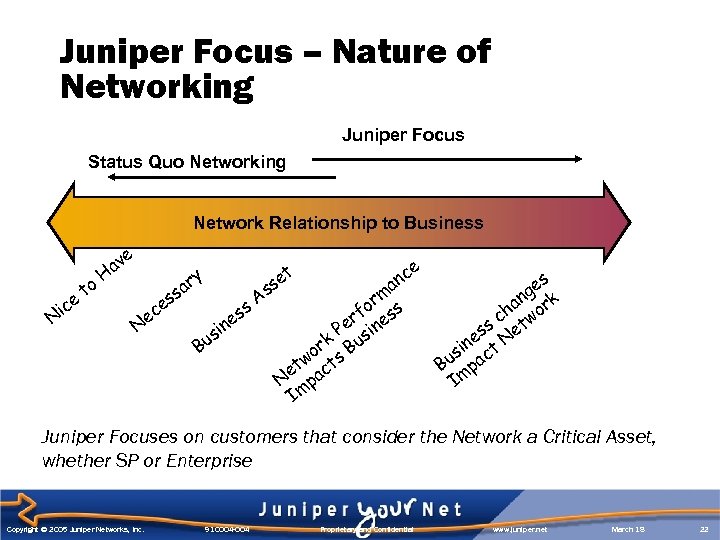 Juniper Focus – Nature of Networking Juniper Focus Status Quo Networking Network Relationship to Business e e ic N to av H s ce e N y ar s Bu sin ss e As t se e nc a m or ss f er ine P s rk Bu o tw cts e N pa Im s ge k n ha wor c s et s ne t N i us pac B Im Juniper Focuses on customers that consider the Network a Critical Asset, whether SP or Enterprise Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 22
Juniper Focus – Nature of Networking Juniper Focus Status Quo Networking Network Relationship to Business e e ic N to av H s ce e N y ar s Bu sin ss e As t se e nc a m or ss f er ine P s rk Bu o tw cts e N pa Im s ge k n ha wor c s et s ne t N i us pac B Im Juniper Focuses on customers that consider the Network a Critical Asset, whether SP or Enterprise Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 22
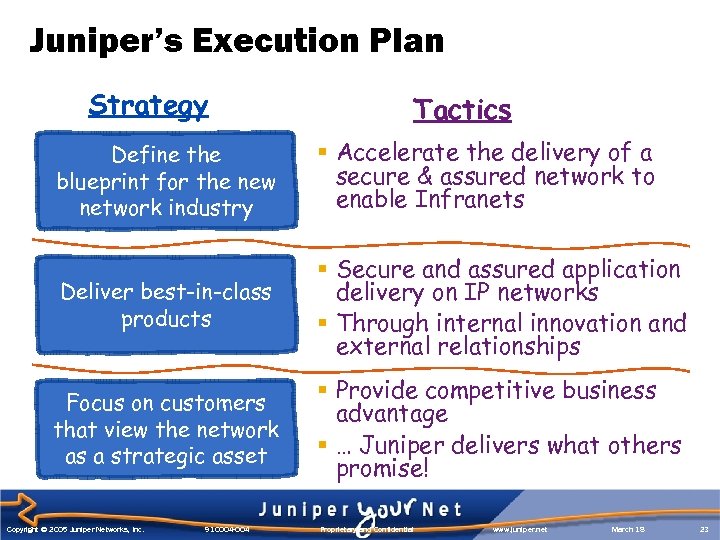 Juniper’s Execution Plan Strategy Tactics Define the blueprint for the new network industry § Accelerate the delivery of a secure & assured network to enable Infranets Deliver best-in-class products § Secure and assured application delivery on IP networks § Through internal innovation and external relationships Focus on customers that view the network as a strategic asset § Provide competitive business advantage § … Juniper delivers what others promise! Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 23
Juniper’s Execution Plan Strategy Tactics Define the blueprint for the new network industry § Accelerate the delivery of a secure & assured network to enable Infranets Deliver best-in-class products § Secure and assured application delivery on IP networks § Through internal innovation and external relationships Focus on customers that view the network as a strategic asset § Provide competitive business advantage § … Juniper delivers what others promise! Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 23
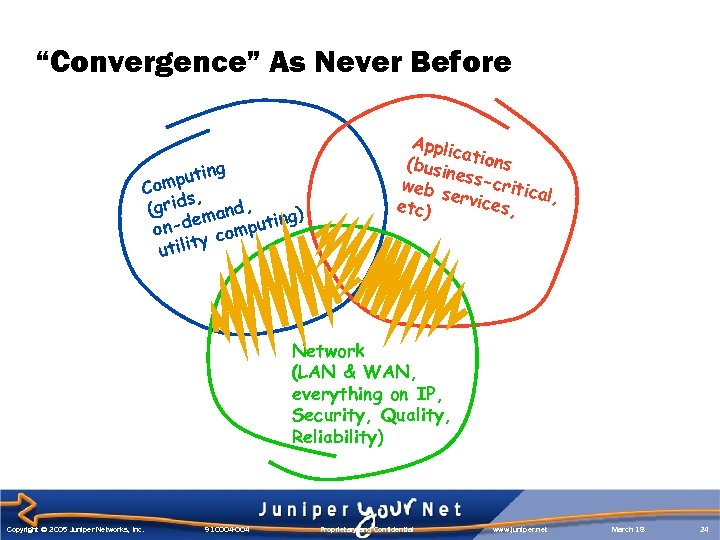 “Convergence” As Never Before g putin Com , s (grid mand, g) n-de computin o y utilit Appli ca (busi tions nessc web servi ritical, ces, etc) Network (LAN & WAN, everything on IP, Security, Quality, Reliability) Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 24
“Convergence” As Never Before g putin Com , s (grid mand, g) n-de computin o y utilit Appli ca (busi tions nessc web servi ritical, ces, etc) Network (LAN & WAN, everything on IP, Security, Quality, Reliability) Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 24
 Juniper Networking Advantages strong Security high § Modularity for full router control while under attack § Strong attack defense ensures system stability § Next Gen CLI for fast editing of filters while under attack § Minor problems do not lead to system crashes § Next Gen CLI prevents operator error § Add many filter terms without degradation % of Line Rate predictable Performance Juniper Addition of new service features Traditional Router Complexity of Packet Processing Copyright © 2005 Juniper Networks, Inc. reduced § Predictable performance for voice, video and other time critical apps § Comprehensive QOS functions to classify, prioritize and schedule traffic 910004 -004 Uptime 6. 4 7. 0 7. 1 One Train! Proprietary and Confidential Operations cost § One software train § Multiple management tools, including J-Web § XML-based API § Restoration features § Feature licensing § Interoperability www. juniper. net March 18 25
Juniper Networking Advantages strong Security high § Modularity for full router control while under attack § Strong attack defense ensures system stability § Next Gen CLI for fast editing of filters while under attack § Minor problems do not lead to system crashes § Next Gen CLI prevents operator error § Add many filter terms without degradation % of Line Rate predictable Performance Juniper Addition of new service features Traditional Router Complexity of Packet Processing Copyright © 2005 Juniper Networks, Inc. reduced § Predictable performance for voice, video and other time critical apps § Comprehensive QOS functions to classify, prioritize and schedule traffic 910004 -004 Uptime 6. 4 7. 0 7. 1 One Train! Proprietary and Confidential Operations cost § One software train § Multiple management tools, including J-Web § XML-based API § Restoration features § Feature licensing § Interoperability www. juniper. net March 18 25
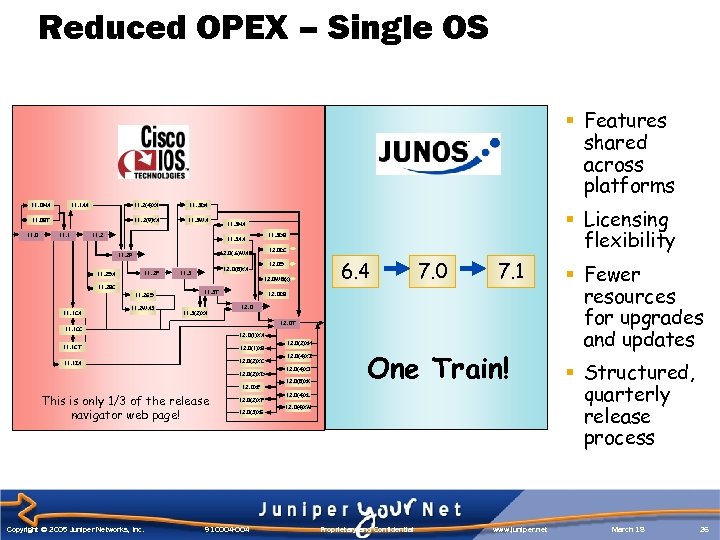 Reduced OPEX – Single OS § Features shared across platforms 11. 1 AA 11. 0 NA 11. 2(4)XA 11. 2(9)XA 11. 0 BT 11. 0 11. 1 11. 3 DA 11. 3 WA 11. 2 11. 3 AA 11. 2 F 11. 2 SA 11. 2 BC 11. 2 GS 11. 1 CA 11. 3 DB 12. 0 DC 12. 0(. 6)WAS 11. 2 P 11. 2 WA 3 12. 0 S 12. 0(5)XA 11. 3 12. 0 W 5(x) 11. 3 T 11. 3(2)XA 6. 4 7. 0 7. 1 12. 0 DB 12. 0 T 11. 1 CC 12. 0(1)XA 11. 1 CT 12. 0(1)XB 11. 1 IA 12. 0(2)XC 12. 0(2)XD 12. 0 XE This is only 1/3 of the release navigator web page! Copyright © 2005 Juniper Networks, Inc. § Licensing flexibility 11. 3 NA 12. 0(2)XF 12. 0(3)XG 910004 -004 12. 0(2)XH 12. 0(4)XI 12. 0(4)XJ 12. 0(5)XK One Train! 12. 0(4)XL 12. 0(4)XM Proprietary and Confidential www. juniper. net § Fewer resources for upgrades and updates § Structured, quarterly release process March 18 26
Reduced OPEX – Single OS § Features shared across platforms 11. 1 AA 11. 0 NA 11. 2(4)XA 11. 2(9)XA 11. 0 BT 11. 0 11. 1 11. 3 DA 11. 3 WA 11. 2 11. 3 AA 11. 2 F 11. 2 SA 11. 2 BC 11. 2 GS 11. 1 CA 11. 3 DB 12. 0 DC 12. 0(. 6)WAS 11. 2 P 11. 2 WA 3 12. 0 S 12. 0(5)XA 11. 3 12. 0 W 5(x) 11. 3 T 11. 3(2)XA 6. 4 7. 0 7. 1 12. 0 DB 12. 0 T 11. 1 CC 12. 0(1)XA 11. 1 CT 12. 0(1)XB 11. 1 IA 12. 0(2)XC 12. 0(2)XD 12. 0 XE This is only 1/3 of the release navigator web page! Copyright © 2005 Juniper Networks, Inc. § Licensing flexibility 11. 3 NA 12. 0(2)XF 12. 0(3)XG 910004 -004 12. 0(2)XH 12. 0(4)XI 12. 0(4)XJ 12. 0(5)XK One Train! 12. 0(4)XL 12. 0(4)XM Proprietary and Confidential www. juniper. net § Fewer resources for upgrades and updates § Structured, quarterly release process March 18 26
 Single OS – More Uptime RO 001> show system uptime Current time: 2005 -01 -24 17: 14: 10 EDT System booted: 2001 -12 -28 17: 39: 48 EDT (160 w 2 d 23: 34 ago) Protocols started: 2001 -12 -28 17: 39: 02 EDT (160 w 2 d 23: 35 ago) Last configured: 2005 -01 -21 19: 18: 48 EDT (2 d 21: 55 ago) 5: 14 PM up 1122 days, 23: 34, 1 user, load averages: 0. 21, 0. 05, 0. 02 RO 002> show system uptime Current time: 2005 -01 -24 17: 14: 51 EDT System booted: 2001 -08 -16 05: 16 EST (179 w 4 d 11: 09 ago) Protocols started: 2003 -01 -22 22: 57: 59 EDT (104 w 4 d 18: 16 ago) Last configured: 2004 -11 -30 11: 28: 27 EDT (7 w 6 d 05: 46 ago) 5: 14 PM up 1257 days, 11: 10, 1 user, load averages: 1. 10, 1. 14, 0. 96 Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 27
Single OS – More Uptime RO 001> show system uptime Current time: 2005 -01 -24 17: 14: 10 EDT System booted: 2001 -12 -28 17: 39: 48 EDT (160 w 2 d 23: 34 ago) Protocols started: 2001 -12 -28 17: 39: 02 EDT (160 w 2 d 23: 35 ago) Last configured: 2005 -01 -21 19: 18: 48 EDT (2 d 21: 55 ago) 5: 14 PM up 1122 days, 23: 34, 1 user, load averages: 0. 21, 0. 05, 0. 02 RO 002> show system uptime Current time: 2005 -01 -24 17: 14: 51 EDT System booted: 2001 -08 -16 05: 16 EST (179 w 4 d 11: 09 ago) Protocols started: 2003 -01 -22 22: 57: 59 EDT (104 w 4 d 18: 16 ago) Last configured: 2004 -11 -30 11: 28: 27 EDT (7 w 6 d 05: 46 ago) 5: 14 PM up 1257 days, 11: 10, 1 user, load averages: 1. 10, 1. 14, 0. 96 Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 27
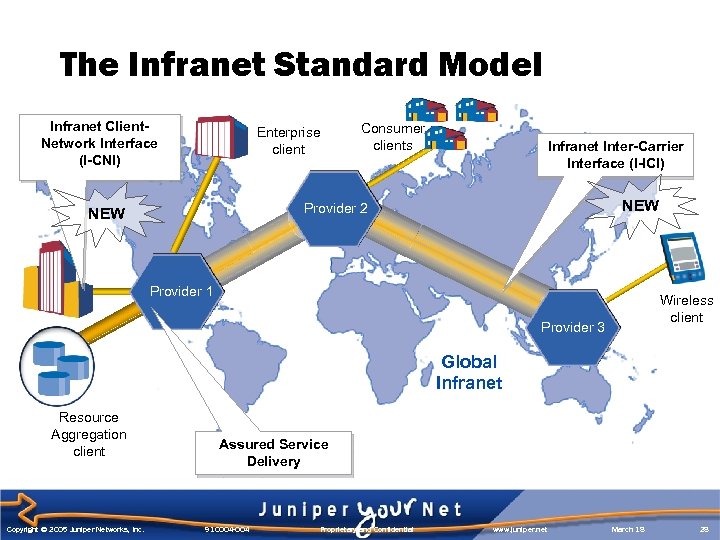 The Infranet Standard Model Infranet Client. Network Interface (I-CNI) Enterprise client Consumer clients Infranet Inter-Carrier Interface (I-ICI) NEW Provider 2 NEW Provider 1 Wireless client Provider 3 Global Infranet Resource Aggregation client Copyright © 2005 Juniper Networks, Inc. Assured Service Delivery 910004 -004 Proprietary and Confidential www. juniper. net March 18 28
The Infranet Standard Model Infranet Client. Network Interface (I-CNI) Enterprise client Consumer clients Infranet Inter-Carrier Interface (I-ICI) NEW Provider 2 NEW Provider 1 Wireless client Provider 3 Global Infranet Resource Aggregation client Copyright © 2005 Juniper Networks, Inc. Assured Service Delivery 910004 -004 Proprietary and Confidential www. juniper. net March 18 28
 Current Infranet Initiative Council Membership Executive Members Working Group Participants Copyright © 2005 Juniper Networks, Inc. Copyright © 2004 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net Confidential Proprietary and Marchwww. juniper. net 18 29 29
Current Infranet Initiative Council Membership Executive Members Working Group Participants Copyright © 2005 Juniper Networks, Inc. Copyright © 2004 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net Confidential Proprietary and Marchwww. juniper. net 18 29 29
 Summary § Status Quo Is Not an Option § Juniper Networks for Growing Businesses § Delivering Smart Security and Active Assurance § Designed Differently § Many Enabling Choices § The BEST Choice § Take the Next Steps Now … Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 30
Summary § Status Quo Is Not an Option § Juniper Networks for Growing Businesses § Delivering Smart Security and Active Assurance § Designed Differently § Many Enabling Choices § The BEST Choice § Take the Next Steps Now … Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 30
 Thank you! Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 31
Thank you! Copyright © 2005 Juniper Networks, Inc. 910004 -004 Proprietary and Confidential www. juniper. net March 18 31


