fc69964d61737643dd60e3de90204de8.ppt
- Количество слайдов: 40

Enterprise Botnet Detection & Mitigation DHS Phase II SBIR Contract Bob Slapnik Vice President Business Development

Agenda ØNABC • Technical Accomplishments • Milestones, Deliverables, and Schedule • Recent Public Relations • Technology Transition Plan • Quad Chart
Are Cybercriminals Targeting You? Next Generation Software to Detect, Diagnose, & respond See what you’ve been missing

Business Needs • Sophisticated attackers – Have time, resources and skill – Criminals motivated by financial gain – State sponsored espionage • Any cyber defense can and will be defeated

Business Needs • Loss of sensitive data and intellectual property – FBI - $100 Billion lost annually • National security is compromised

SANS Institute’s Top 5 Attacks for 2008 Web Browse r exploit s Ins i Thr der eat M Ph obi Th o le re ne s at s net Bot r be nag Cy io p e Es

Problems • 80% of new malware is not detected – Stealthy rootkits – Malware variants – Targeted attacks • Lack of endpoint visibility • Traditional disk security and forensics tools are not enough
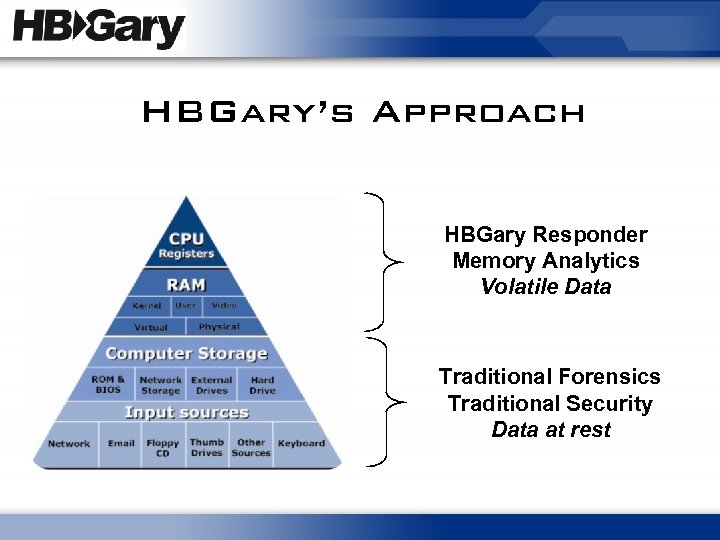
HBGary’s Approach HBGary Responder Memory Analytics Volatile Data Traditional Forensics Traditional Security Data at rest

Information found in RAM • • Running processes and drivers Unpacked bots and malware Unencrypted network data Open ports and network sockets Open files and file contents Strings and symbols Passwords and keys in clear text Registry info
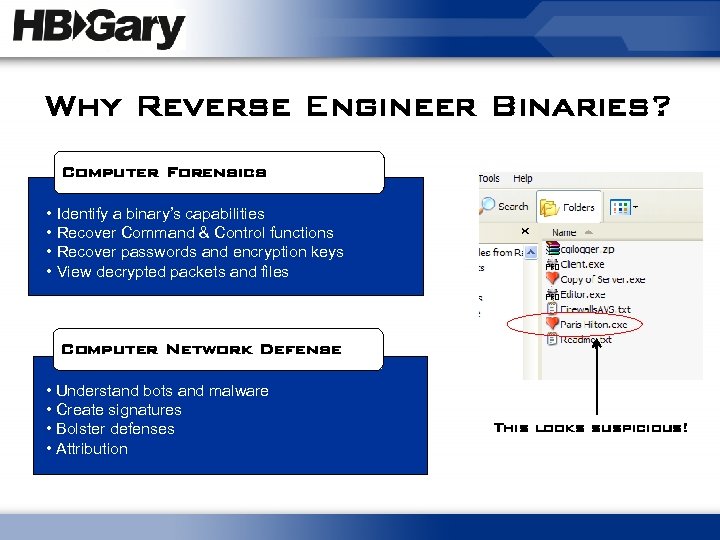
Why Reverse Engineer Binaries? Computer Forensics • Identify a binary’s capabilities • Recover Command & Control functions • Recover passwords and encryption keys • View decrypted packets and files Computer Network Defense • Understand bots and malware • Create signatures • Bolster defenses • Attribution This looks suspicious!

HBGary’s Approach • Automated host analysis – Physical Memory (RAM) – Binaries, bots and malware • Detect, Diagnose, Respond – Find the bad guy on computers and tell you what he is doing • Workstation product Enterprise product
Benefits • Best memory analysis system • Automated behavioral detection to identify suspect binaries • Automated bot and malware forensics – Lower the skills bar • Enterprise host visibility
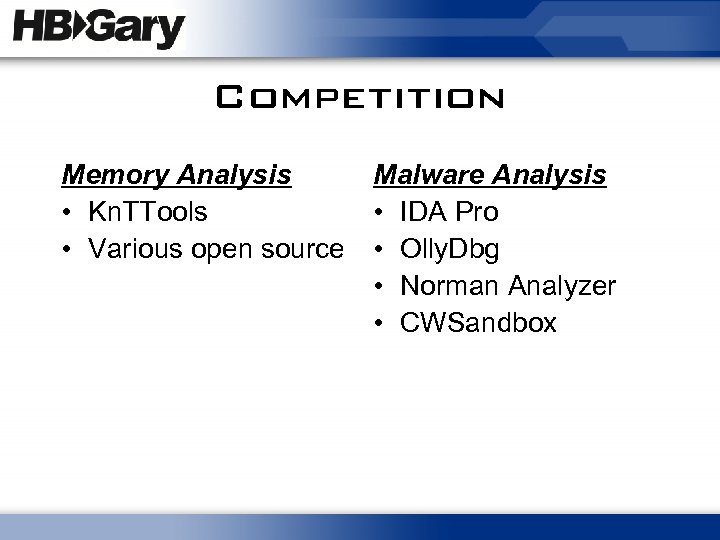
Competition Memory Analysis • Kn. TTools • Various open source Malware Analysis • IDA Pro • Olly. Dbg • Norman Analyzer • CWSandbox

• NABC ØTechnical Accomplishments • Milestones, Deliverables, and Schedule • Recent Public Relations • Technology Transition Plan • Quad Chart

Technical Accomplishments • Commercial software released in April 2008 – HBGary Responder

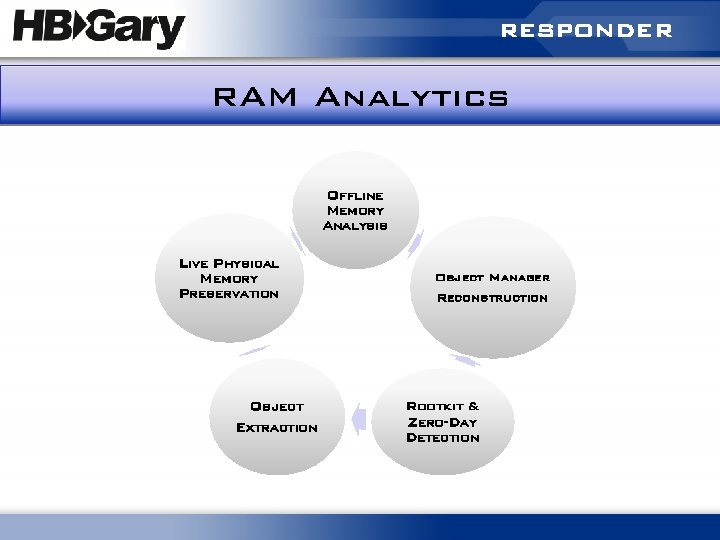
RESPONDER RAM Analytics Offline Memory Analysis Live Physical Memory Preservation Object Extraction Object Manager Reconstruction Rootkit & Zero-Day Detection

RESPONDER Runtime & Binary Forensics Automated Malware Analysis & Reporting Recover Malware executed instructions Analyze Packed & Obfuscated Malware Runtime Forensics “live binary” Analysis Binary Forensics “static Analysis”

RESPONDER Malware Analysis Plugin Stealth Techniques Network Communications How is it installed? File System Access & Modifications Registry Access & Modifications Malware Survivability Cryptographic Routines File Packing & Obfuscation Remote Command Control Intelligence
Responder Screenshot
Responder Screenshot

Interactive Binary Graphing
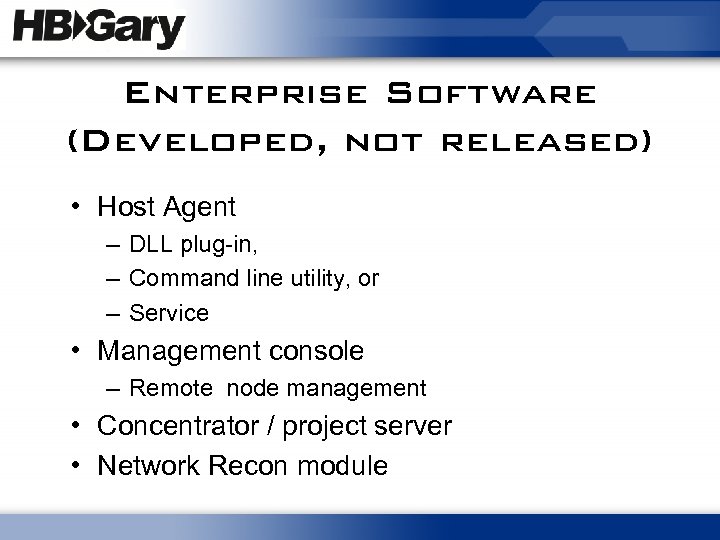
Enterprise Software (Developed, not released) • Host Agent – DLL plug-in, – Command line utility, or – Service • Management console – Remote node management • Concentrator / project server • Network Recon module
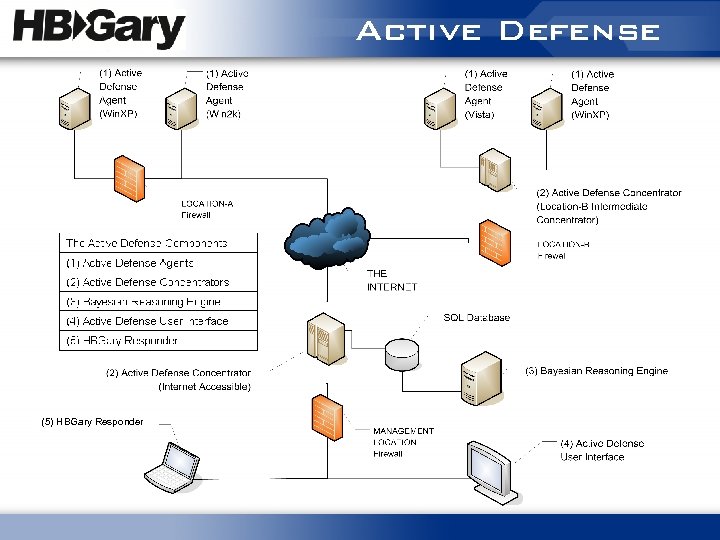
Active Defense (5) HBGary Responder
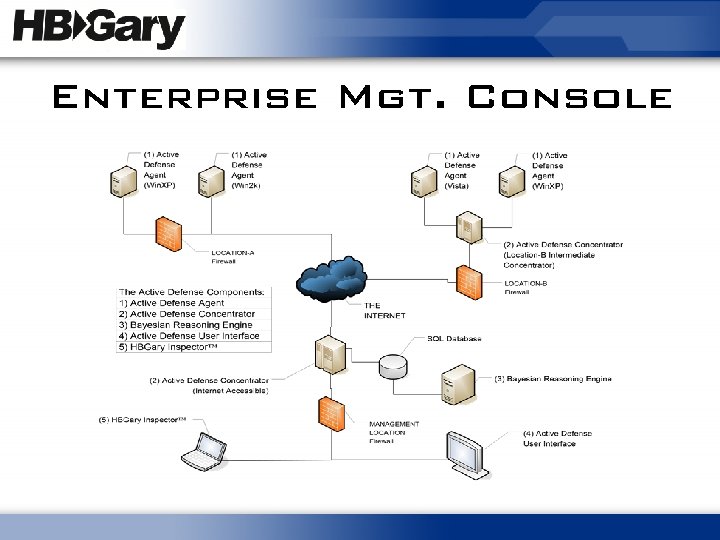
Enterprise Mgt. Console
Digital DNA • In-memory fuzzy hashing – Partial matching – Calculate DDNA from disk object – Detection within memory • Detect malware variants • Developed with HBGary IR&D private funds – outside of the SBIR contract – Patent pending
Flypaper • • • New runtime analysis system Observe binary behaviors Causes processes to “stick” in memory Analyze “droppers” Used with Responder Developed with HBGary IR&D private funds – outside of the SBIR contract

• NABC • Technical Accomplishments ØMilestones, Deliverables, and Schedule • Recent Public Relations • Technology Transition Plan • Quad Chart

Milestones • HBGary Responder™ – Released April 2008 • Enterprise Active Defense – Pilot site in Q 1 2009 • Bayesian Reasoning Engine – Q 2 2009

Schedule Oct 2008 Nov 2008 Dec 2008 Jan 2009 Feb 2009 Mar 2009 Apr 2009 May 2009 Jul 2009 Recover passwords and keys from RAM Recover page file Recover hiberfil. sys file FIPS compliant encryption (open. SSL) Pilot enterprise deployment / “ 1000 nodes” Recover NDIS buffers and PCAP files Complete first set of reasoning models Integrate the Bayesian Reasoning Engine Extend detection rules for indirect indicators

• NABC • Technical Accomplishments • Milestones, Deliverables, and Schedule ØRecent Public Relations • Technology Transition Plan • Quad Chart

Press Releases • Guidance Software to Offer HBGary Responder for Live Memory Analysis in Digital Investigations, May 22, 2008 • HBGary Joins Mc. Afee Partner Program, the Mc. Afee Security Innovation Alliance, August 25, 2008

Conference Trade Shows • Guidance’s CEIC – May 2008 • Black. Hat – August 2008 • Mc. Afee FOCUS 2008 – Oct 20 -23, 2008

• NABC • Technical Accomplishments • Milestones, Deliverables, and Schedule • Recent Public Relations ØTechnology Transition Plan • Quad Chart

Technology Transition Plan • Sell HBGary Responder as a workstation product now • Go to market with an enterprise product in near future • Sell direct and through partners
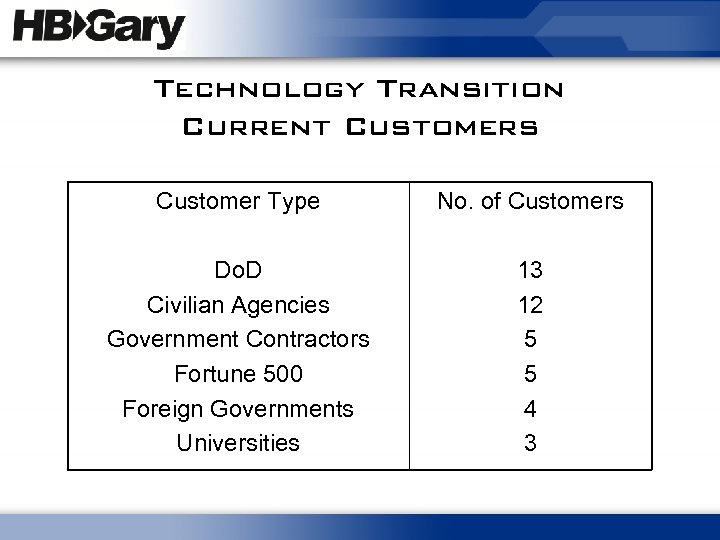
Technology Transition Current Customers Customer Type No. of Customers Do. D Civilian Agencies Government Contractors Fortune 500 Foreign Governments Universities 13 12 5 5 4 3

Strategic Partners • Guidance Software (Encase) – Reselling Responder worldwide – Integrating Responder to Encase Enterprise • Mc. Afee – Integration with e. Policy Orchestrator – Do. D’s HBSS Program Multiple strategies for enterprise deployable solution

• NABC • Technical Accomplishments • Milestones, Deliverables, and Schedule • Recent Public Relations • Technology Transition Plan ØQuad Chart
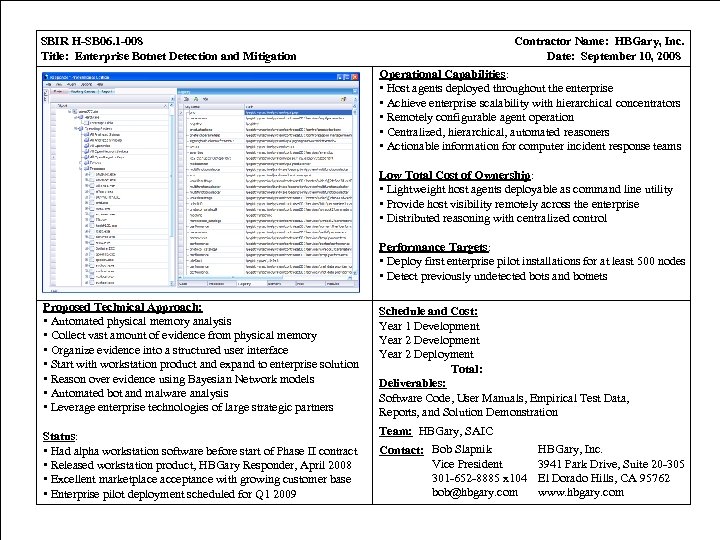
SBIR H-SB 06. 1 -008 Title: Enterprise Botnet Detection and Mitigation Contractor Name: HBGary, Inc. Date: September 10, 2008 Operational Capabilities: • Host agents deployed throughout the enterprise • Achieve enterprise scalability with hierarchical concentrators • Remotely configurable agent operation • Centralized, hierarchical, automated reasoners • Actionable information for computer incident response teams Low Total Cost of Ownership: • Lightweight host agents deployable as command line utility • Provide host visibility remotely across the enterprise • Distributed reasoning with centralized control Performance Targets: • Deploy first enterprise pilot installations for at least 500 nodes • Detect previously undetected bots and botnets Proposed Technical Approach: • Automated physical memory analysis • Collect vast amount of evidence from physical memory • Organize evidence into a structured user interface • Start with workstation product and expand to enterprise solution • Reason over evidence using Bayesian Network models • Automated bot and malware analysis • Leverage enterprise technologies of large strategic partners Schedule and Cost: Year 1 Development Year 2 Deployment Total: Deliverables: Software Code, User Manuals, Empirical Test Data, Reports, and Solution Demonstration Status: • Had alpha workstation software before start of Phase II contract • Released workstation product, HBGary Responder, April 2008 • Excellent marketplace acceptance with growing customer base • Enterprise pilot deployment scheduled for Q 1 2009 Team: HBGary, SAIC Contact: Bob Slapnik Vice President 301 -652 -8885 x 104 bob@hbgary. com HBGary, Inc. 3941 Park Drive, Suite 20 -305 El Dorado Hills, CA 95762 www. hbgary. com

Thank you Any Questions? www. hbgary. com
fc69964d61737643dd60e3de90204de8.ppt