c81cc51f809a8116fa84ef03e05f12a9.ppt
- Количество слайдов: 22

ENgine FOR Controlling Emergent Hierarchical Role-Based Access (ENfor. CE HRBAccess) Osama Khaleel Thesis Defense May 2007 Master of Science in Computer Science University of Colorado, Colorado Springs 4/26/2007 okhaleel/Enforce 1

ENgine FOR Controlling Emergent Hierarchical Role-Based Access (ENfor. CE HRBAccess) Committee Members: Dr. Edward Chow, Chair Dr. Terry Boult Dr. Xiaobo Zhou 4/26/2007 okhaleel/Enforce 2

Thesis Defense Outlines n n n n Intro & Background Design Implementation Performance Analysis Future Work Contribution Demo Q&A 4/26/2007 okhaleel/Enforce 3

Introduction n Roles in any organization are Hierarchical by their nature. n Resources in any organization vary: n n n Mission becomes more complicated when users should access resources: n n n From a simple HTML web page, To RDP/SSH access in which a user can gain full control. Securely And based on their ROLES. Password-based protection is way far from satisfying highlevel security requirements. 4/26/2007 okhaleel/Enforce 4
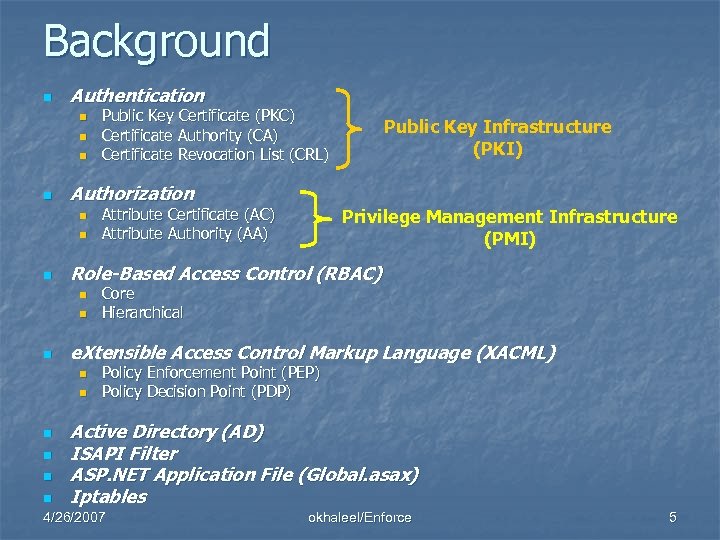
Background n Authentication n n Authorization n n n n Privilege Management Infrastructure (PMI) Core Hierarchical e. Xtensible Access Control Markup Language (XACML) n n Attribute Certificate (AC) Attribute Authority (AA) Public Key Infrastructure (PKI) Role-Based Access Control (RBAC) n n Public Key Certificate (PKC) Certificate Authority (CA) Certificate Revocation List (CRL) Policy Enforcement Point (PEP) Policy Decision Point (PDP) Active Directory (AD) ISAPI Filter ASP. NET Application File (Global. asax) Iptables 4/26/2007 okhaleel/Enforce 5

n n Authentication: the process in which someone provides some kind of credentials to prove his or her identity. CA: a trusted third party that issues digital certificates to be used by other parties. It guarantees that the individual granted the certificate is really who claims to be. n PKC: a digitally signed document that binds a public key to a subject (identity). This binding is asserted by a trusted CA. n CRL: a list signed by the issuing CA that contains the serial numbers of the revoked certificates. n Authorization: the process that is used to determine whether the subject has the required permissions to access some protected resources. n AC: a digitally signed document that binds a set of attributes like membership, role, or security clearance to the AC holder. n AA: a trusted third party that is responsible for issuing, maintaining, and revoking ACs. 4/26/2007 okhaleel/Enforce 6

n AD: a distributed directory service included in the Windows server 2000/2003 n n n ISAPI filters: DLLs that can be used to enhance and modify the functionality of IIS. n n Powerful -> they can modify both incoming and outgoing Data. Stream for EVERY request. Global. asax: a file resides in the root directory of the ASP. NET application. n n The Microsoft's implementation of LDAP Used to store and manage all information about network resources across the domain: computers, groups, users, … Contains code to handle application-level and session-level events raised by ASP. NET. Iptables: a generic table structure for defining a set of rules to deal with network packets. n n n Rules are grouped into chains. Chains are grouped into tables Each table is associated with a different kind of packet processing. 4/26/2007 okhaleel/Enforce 7

n RBAC: a mechanism/model for restricting access based on the role of authorized users. n n n Core: roles are assigned to users, and permissions are associated with roles – not directly with users. Hierarchical: an enhancement to the core, in which senior roles inherit permissions from more junior roles. XACML: an XML-based OASIS standard that describes: n n A policy language A request/response language n The main three components in XACML are Rule, Policy, and Policy. Set n XACML RBAC profile has two main components: n n n Permission Policy. Set (PPS) Role Policy. Set (RPS). One PPS and one RPS for each defined Role. 4/26/2007 okhaleel/Enforce 8
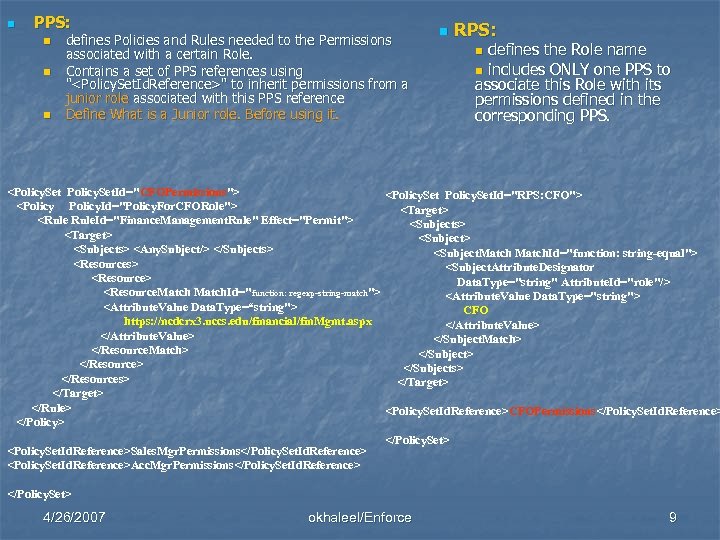
n PPS: n n n defines Policies and Rules needed to the Permissions associated with a certain Role. Contains a set of PPS references using "<Policy. Set. Id. Reference>" to inherit permissions from a junior role associated with this PPS reference Define What is a Junior role. Before using it. n RPS: defines the Role name n includes ONLY one PPS to associate this Role with its permissions defined in the corresponding PPS. n <Policy. Set. Id="CFOPermissions"> <Policy. Set. Id="RPS: CFO"> <Policy. Id="Policy. For. CFORole"> <Target> <Rule. Id="Finance. Management. Rule" Effect="Permit"> <Subjects> <Target> <Subjects> <Any. Subject/> </Subjects> <Subject. Match. Id="function: string-equal"> <Resources> <Subject. Attribute. Designator <Resource> Data. Type="string" Attribute. Id="role"/> <Resource. Match. Id="function: regexp-string-match"> <Attribute. Value Data. Type="string"> <Attribute. Value Data. Type=“string"> CFO https: //ncdcrx 3. uccs. edu/financial/fin. Mgmt. aspx </Attribute. Value> </Subject. Match> </Resource. Match> </Subject> </Resource> </Subjects> </Resources> </Target> </Rule> <Policy. Set. Id. Reference>CFOPermissions</Policy. Set. Id. Reference> </Policy. Set> <Policy. Set. Id. Reference>Sales. Mgr. Permissions</Policy. Set. Id. Reference> <Policy. Set. Id. Reference>Acc. Mgr. Permissions</Policy. Set. Id. Reference> </Policy. Set> 4/26/2007 okhaleel/Enforce 9

Design n By taking advantage of the concepts & technologies just mentioned, the goal is to build a structure/engine that provides: Authentication n Authorization n Secure access based on users ROLES n Protection for ANY type of resources n Fine grained control based on active sessions n PKI & PMI management tool n 4/26/2007 okhaleel/Enforce 10

ENfor. CE “Big Picture” User Request Protected web resources IIS Authentication ISAPI ASP. NET Global. asax Application Http request XML response RPS PPS Networkresource Access Policy Decision Point XML response Get Decision Policy Enforcement Point Open/Close commands Check session policy Session policy source Get User's AC Iptables Control Service FC 4 machine (Firewall) Active Directory Domain Controller Protected Network resources 4/26/2007 okhaleel/Enforce 11

ENfor. CE Test-Bed 128. 198. 162. 53 128. 198. 162. 52 128. 198. 162. 51 128. 198. 162. 50 Main switch Fedora. Core 4 Gateway/Firewall 10. 0. 0. 1 Local switch 10. 0. 0. 11 10. 0. 0. 13 Win 2003 IIS 4/26/2007 10. 0. 0. 12 Windows XP okhaleel/Enforce 10. 0. 0. 10 Win 2003 DC 12
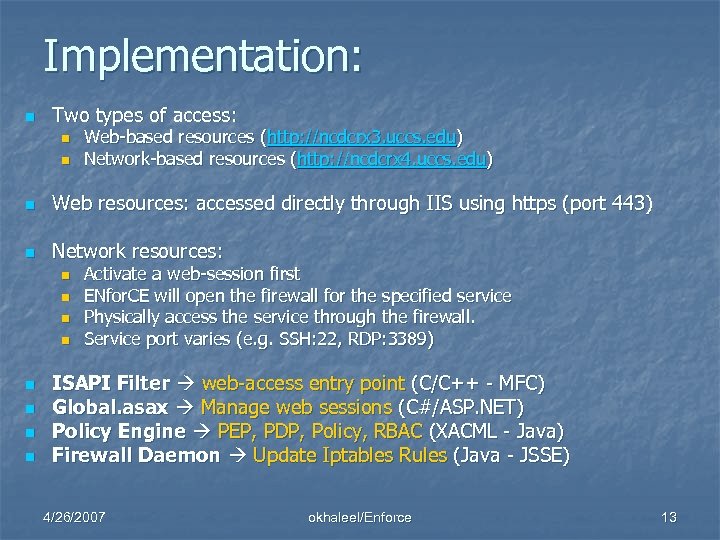
Implementation: n Two types of access: n n Web-based resources (http: //ncdcrx 3. uccs. edu) Network-based resources (http: //ncdcrx 4. uccs. edu) n Web resources: accessed directly through IIS using https (port 443) n Network resources: n n n n Activate a web-session first ENfor. CE will open the firewall for the specified service Physically access the service through the firewall. Service port varies (e. g. SSH: 22, RDP: 3389) ISAPI Filter web-access entry point (C/C++ - MFC) Global. asax Manage web sessions (C#/ASP. NET) Policy Engine PEP, PDP, Policy, RBAC (XACML - Java) Firewall Daemon Update Iptables Rules (Java - JSSE) 4/26/2007 okhaleel/Enforce 13

Web resources (ISAPI) 1) Web request IIS Authentication 2) Http request with attributes ISAPI 5) XML response with decision 6) Permit/Deny access Protected web resources 4) Get Decision Policy Decision Point Policy Enforcement Point 3) Get User's AC Active Directory Domain Controller 4/26/2007 okhaleel/Enforce 14
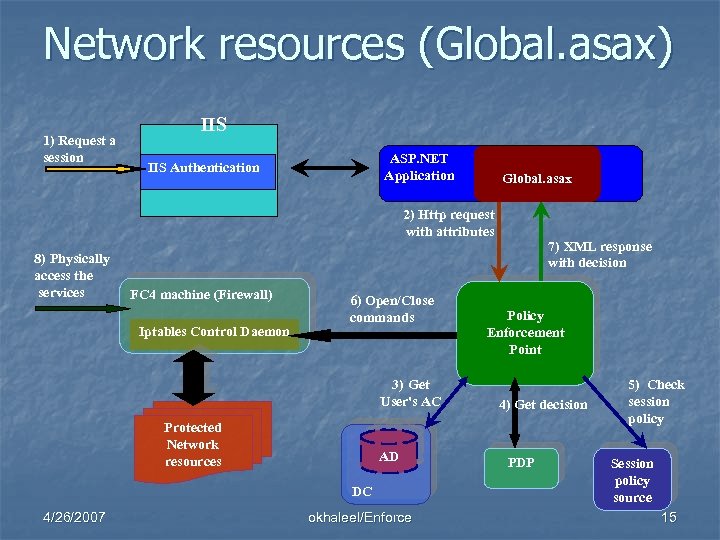
Network resources (Global. asax) 1) Request a session IIS ASP. NET Application IIS Authentication Global. asax 2) Http request with attributes 8) Physically access the services FC 4 machine (Firewall) Iptables Control Daemon 6) Open/Close commands 3) Get User's AC Protected Network resources AD DC 4/26/2007 okhaleel/Enforce 7) XML response with decision Policy Enforcement Point 4) Get decision PDP 5) Check session policy Session policy source 15

Requests to PEP 1) From ISAPI (Access a web resource): http: //localhost: 8080/sispep/servlets/sispep ? • • 2) From Global. asax (Open a network resource): http: //localhost: 8080/sispep/servlets/sispep ? • • • 3) subject= CN=Edward Chow, C=US, S=CO, . . , E=chow@sis. uccs. edu, OU=Computer Science & URL=https: //ncdcrx 3. uccs. edu/it/img. jpg & method=GET & service=web subject= CN=Edward Chow, C=US, S=CO, …. , E=chow@sis. uccs. edu, OU=Computer Science & URL=https: //ncdcrx 4. uccs. edu/ssh/session. aspx & service=ssh & IP=128. 198. 55. 11 & session. ID=23 hjh. Y 43 & action=open From Global. asax (Close a network resource): http: //localhost: 8080/sispep/servlets/sispep ? • subject= CN=Edward Chow, C=US, S=CO, …. , E=chow@sis. uccs. edu, OU=Computer Science & • URL=https: //ncdcrx 4. uccs. edu/ssh/session. aspx & • service=ssh & • IP=128. 198. 55. 11 & • session. ID=23 hjf 73 G 2 & • action=close 4/26/2007 okhaleel/Enforce 16
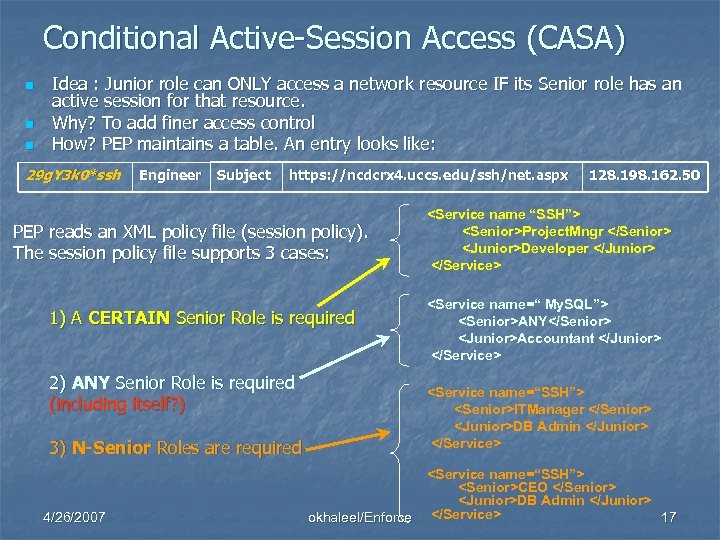
Conditional Active-Session Access (CASA) n n n Idea : Junior role can ONLY access a network resource IF its Senior role has an active session for that resource. Why? To add finer access control How? PEP maintains a table. An entry looks like: 29 g. Y 3 k 0*ssh Engineer Subject https: //ncdcrx 4. uccs. edu/ssh/net. aspx PEP reads an XML policy file (session policy). The session policy file supports 3 cases: 1) A CERTAIN Senior Role is required 2) ANY Senior Role is required (including itself? ) <Service name “SSH”> <Senior>Project. Mngr </Senior> <Junior>Developer </Junior> </Service> <Service name=“ My. SQL”> <Senior>ANY</Senior> <Junior>Accountant </Junior> </Service> <Service name=“SSH”> <Senior>ITManager </Senior> <Junior>DB Admin </Junior> </Service> 3) N-Senior Roles are required 4/26/2007 128. 198. 162. 50 okhaleel/Enforce <Service name=“SSH”> <Senior>CEO </Senior> <Junior>DB Admin </Junior> </Service> 17
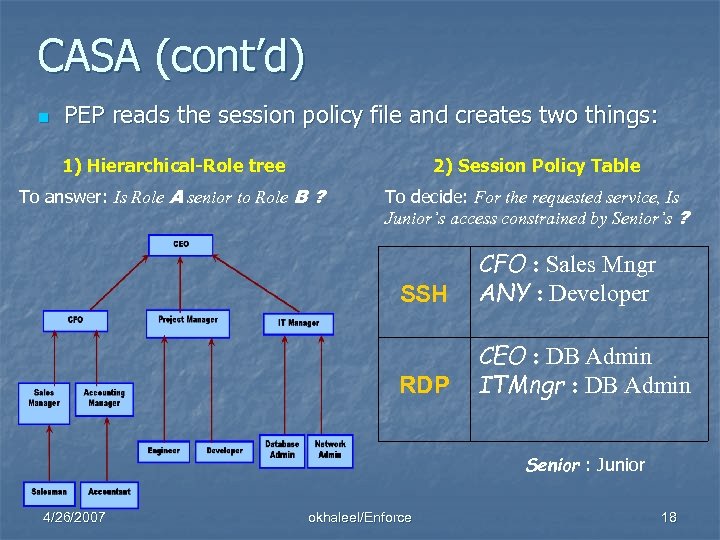
CASA (cont’d) n PEP reads the session policy file and creates two things: 1) Hierarchical-Role tree 2) Session Policy Table To answer: Is Role A senior to Role B ? To decide: For the requested service, Is Junior’s access constrained by Senior’s ? SSH CFO : Sales Mngr ANY : Developer RDP CEO : DB Admin ITMngr : DB Admin Senior : Junior 4/26/2007 okhaleel/Enforce 18

Performance Analysis Web resources (ISAPI) Unit: ms Resource Retrieve AC from AD PDP decision Total request time Finance Mgmnt 5. 4750 3. 0345 10. 3476 Sales Write 6. 2864 4. 3872 13. 7203 Posting orders 6. 9820 4. 92345 13. 8433 View orders 5. 1734 4. 1093 11. 7390 Network resource (Global. asax) – new session Resource Retrieve AC from AD PDP decision CASA decision Firewall update SSH 5. 8730 RDP My. SQL Total request time 3. 8264 2. 3654 15. 5093 29. 4374 5. 7639 4. 9276 3. 1093 17. 1204 32. 2841 6. 1927 3. 1043 2. 5831 14. 7627 30. 6392 Network resource (Global. asax) – session refresh Resource Retrieve AC from AD PDP decision CASA decision Total request time SSH 6. 8093 4. 3298 3. 9485 20. 5912 RDP 7. 7602 3. 8749 2. 2037 20. 5382 My. SQL 6. 3175 3. 7829 2. 5582 19. 7045 4/26/2007 okhaleel/Enforce 19

Future Work n Extend the system to work in a multi-agency environment. n Develop more services that can take advantage of the existing RBAC architecture. For instance: n n RBAC E-Voting: users can vote based on their roles. RBAC Instant Messenger: users can chat based on their roles. RBAC E-Mail: users can send e-mails based on their roles. RBAC XXX and so on… n Support more Operating systems (Mac, Solaris …) n Improve the Admin tool to initialize and modify Active Directory, and to be able to generate XACML policies. n Support Wireless access. 4/26/2007 okhaleel/Enforce 20

Thesis Contributions n Provide a robust architecture for large-scale companies to address accessing sensitive resources securely according to hierarchical role-based access policy. n n Extend XACML to handle Hierarchical Role-Based Access Control (HRBAC) model. Add a totally new concept of secure access in which a Senior Role can restrict its Junior Role's access using active session's management. n Enhance IIS 6. 0 with two components, ISAPI filter and Global. asax. n Simplify PKI and PMI management, therefore, reducing management cost and errors. 4/26/2007 okhaleel/Enforce 21

ENfor. CE Demo Q&A 4/26/2007 okhaleel/Enforce 22
c81cc51f809a8116fa84ef03e05f12a9.ppt