f4b951e9a9fa1d2b778e4b096a40301c.ppt
- Количество слайдов: 53
 Enforcing Network Compliance at ORNL A Progress Report of NAC at ORNL By Paige Stafford NLIT 2008, Chicago Managed by UT-Battelle for the Department of Energy
Enforcing Network Compliance at ORNL A Progress Report of NAC at ORNL By Paige Stafford NLIT 2008, Chicago Managed by UT-Battelle for the Department of Energy
 Outline · NAC – Definition – ORNL’s Implementation · NACmgr – – – Objectives Implementation Strengths and Weaknesses Future Direction of NACmgr Conclusion · Future of NAC 2 Managed by UT-Battelle for the Department of Energy
Outline · NAC – Definition – ORNL’s Implementation · NACmgr – – – Objectives Implementation Strengths and Weaknesses Future Direction of NACmgr Conclusion · Future of NAC 2 Managed by UT-Battelle for the Department of Energy
 Definition of NAC · Network Access Control (NAC) is a set of technologies and defined processes that aim to control access to the network, allowing only authorized and compliant devices to access and operate on a network. From Ofir Arkin: Bypassing NAC v 2. 0 -- http: //www. insightix. com 3 Managed by UT-Battelle for the Department of Energy
Definition of NAC · Network Access Control (NAC) is a set of technologies and defined processes that aim to control access to the network, allowing only authorized and compliant devices to access and operate on a network. From Ofir Arkin: Bypassing NAC v 2. 0 -- http: //www. insightix. com 3 Managed by UT-Battelle for the Department of Energy
 Definition of NAC, Cont. · NAC is made up of seven elements: 1. 2. 3. 4. 5. 6. 7. 4 Detection Authentication Compliance Quarantine and Remediation Enforcement Authorization Post-Admission Protection Managed by UT-Battelle for the Department of Energy
Definition of NAC, Cont. · NAC is made up of seven elements: 1. 2. 3. 4. 5. 6. 7. 4 Detection Authentication Compliance Quarantine and Remediation Enforcement Authorization Post-Admission Protection Managed by UT-Battelle for the Department of Energy
 Implementation of NAC at ORNL -- The Pieces of NAC · DHCP & DNS – Harvesting of DHCP log files – Net. Jail – Quarantine & Remediation Quarantine and Remediation, Compliance, Enforcement · Network Registration – Assigns network and protection zone (PZ) – Cyber sensitivity defined Compliance (register) and Central store of Data 5 Managed by UT-Battelle for the Department of Energy
Implementation of NAC at ORNL -- The Pieces of NAC · DHCP & DNS – Harvesting of DHCP log files – Net. Jail – Quarantine & Remediation Quarantine and Remediation, Compliance, Enforcement · Network Registration – Assigns network and protection zone (PZ) – Cyber sensitivity defined Compliance (register) and Central store of Data 5 Managed by UT-Battelle for the Department of Energy
 Implementation of NAC at ORNL, Cont. · Network Infrastructure – FW isolation of distinct protection zones Authorization, Enforcement · CSR: Cyber Security Reporting Compliance · Vsweb: Vulnerability tracking Compliance · Cyber-security scanning, Gateway & Internal IDS Post-Admission Protection, Compliance, enforcement, detection 6 Managed by UT-Battelle for the Department of Energy
Implementation of NAC at ORNL, Cont. · Network Infrastructure – FW isolation of distinct protection zones Authorization, Enforcement · CSR: Cyber Security Reporting Compliance · Vsweb: Vulnerability tracking Compliance · Cyber-security scanning, Gateway & Internal IDS Post-Admission Protection, Compliance, enforcement, detection 6 Managed by UT-Battelle for the Department of Energy
 Implementation of NAC at ORNL, Cont. · AD (for MS) and LDAP (for Macs/Linux) Authentication · SMS, Red Hat Patch Server, mobile system encryption, Core. IT access, Virus protection Compliance, post-admission protection · NACmgr: Network compliance enforcement Detection, Quarantine and Remediation, Enforcement, Post-Admission Protection, Compliance, system Authorization (post access) 7 Managed by UT-Battelle for the Department of Energy
Implementation of NAC at ORNL, Cont. · AD (for MS) and LDAP (for Macs/Linux) Authentication · SMS, Red Hat Patch Server, mobile system encryption, Core. IT access, Virus protection Compliance, post-admission protection · NACmgr: Network compliance enforcement Detection, Quarantine and Remediation, Enforcement, Post-Admission Protection, Compliance, system Authorization (post access) 7 Managed by UT-Battelle for the Department of Energy
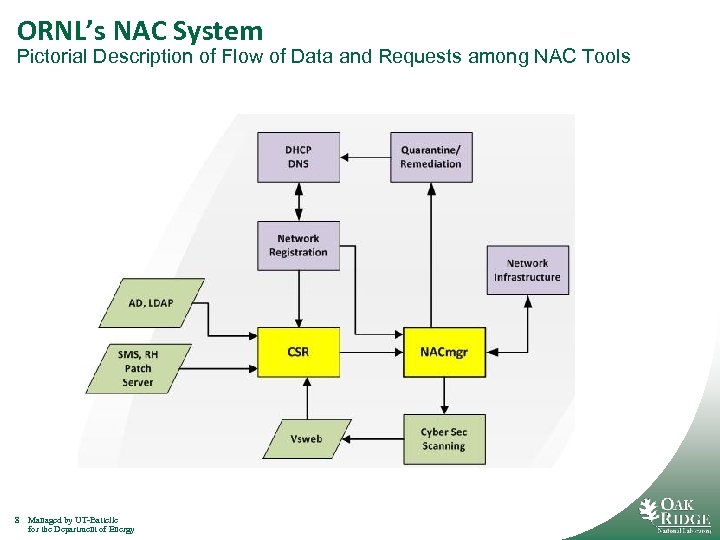 ORNL’s NAC System Pictorial Description of Flow of Data and Requests among NAC Tools 8 Managed by UT-Battelle for the Department of Energy
ORNL’s NAC System Pictorial Description of Flow of Data and Requests among NAC Tools 8 Managed by UT-Battelle for the Department of Energy
 NACmgr Network Access Control Manager · “Network Detective and Policy Enforcer” – Detection of network activity – Enforcement of network compliance – Of all hosts on the ORNL network · A out-of-band network service – Uses SNMP to control switches at the Network Edge – Fail-Open Network Access – No user supplicant 9 Managed by UT-Battelle for the Department of Energy
NACmgr Network Access Control Manager · “Network Detective and Policy Enforcer” – Detection of network activity – Enforcement of network compliance – Of all hosts on the ORNL network · A out-of-band network service – Uses SNMP to control switches at the Network Edge – Fail-Open Network Access – No user supplicant 9 Managed by UT-Battelle for the Department of Energy
 NACmgr Objectives · Monitor for Compliance – – Unregistered Protection Zone (PZ) violations Misuse of IP address assignment Invalid registration 10 Managed by UT-Battelle for the Department of Energy
NACmgr Objectives · Monitor for Compliance – – Unregistered Protection Zone (PZ) violations Misuse of IP address assignment Invalid registration 10 Managed by UT-Battelle for the Department of Energy
 NACmgr Objectives, Cont. · Enforce Compliance – Detection Compliance Monitoring Isolation – Speak softly and carry a big stick · Policies well defined and publicized · No intrusion upon “normal” operation · Quarantine / L 2 -Block “Speak softly and carry a big stick and you will go far. ” West African proverb used by Teddy Roosevelt in 1900. http: //www. loc. gov/exhibits/treasures/trm 139. html 11 Managed by UT-Battelle for the Department of Energy
NACmgr Objectives, Cont. · Enforce Compliance – Detection Compliance Monitoring Isolation – Speak softly and carry a big stick · Policies well defined and publicized · No intrusion upon “normal” operation · Quarantine / L 2 -Block “Speak softly and carry a big stick and you will go far. ” West African proverb used by Teddy Roosevelt in 1900. http: //www. loc. gov/exhibits/treasures/trm 139. html 11 Managed by UT-Battelle for the Department of Energy
 How NACmgr works · A set of executable tasks distributed among a main server and outposts – Number of outposts ∝ network size – ORNL’s setup · Powerful main server · Two outpost servers · 574 switches and routers polled every 5 min – ~ 9, 500 unique mac addresses. 12 Managed by UT-Battelle for the Department of Energy
How NACmgr works · A set of executable tasks distributed among a main server and outposts – Number of outposts ∝ network size – ORNL’s setup · Powerful main server · Two outpost servers · 574 switches and routers polled every 5 min – ~ 9, 500 unique mac addresses. 12 Managed by UT-Battelle for the Department of Energy
 NACmgr Code Specifications · Written in C++ · Calls expect scripts · Libraries: – – Net-SNMP: SNMP for C pqxx: Postgre. SQL for C++ Rude. CGI: C++ for CGI p. Threads: POSIX threads 13 Managed by UT-Battelle for the Department of Energy
NACmgr Code Specifications · Written in C++ · Calls expect scripts · Libraries: – – Net-SNMP: SNMP for C pqxx: Postgre. SQL for C++ Rude. CGI: C++ for CGI p. Threads: POSIX threads 13 Managed by UT-Battelle for the Department of Energy
 Main Server · 16 GB memory · Four dual core processors · Red Hat Linux · Web interface NACmgr. ornl. gov · NAC database · Handles most of the task load 14 Managed by UT-Battelle for the Department of Energy
Main Server · 16 GB memory · Four dual core processors · Red Hat Linux · Web interface NACmgr. ornl. gov · NAC database · Handles most of the task load 14 Managed by UT-Battelle for the Department of Energy
 Outposts · Four Outposts – NAC 1, NAC 2, NAC 3, NACmgr · Smaller outposts – two dual core processors and 8 GB memory – Red Hat Linux · Primary function is Polling – Remotely connects to main server · NAC 1 is backup for DB and CGI 15 Managed by UT-Battelle for the Department of Energy
Outposts · Four Outposts – NAC 1, NAC 2, NAC 3, NACmgr · Smaller outposts – two dual core processors and 8 GB memory – Red Hat Linux · Primary function is Polling – Remotely connects to main server · NAC 1 is backup for DB and CGI 15 Managed by UT-Battelle for the Department of Energy
 NACmgr Sandbox Environment · Open Sandbox for development – Needed to manipulate on a per-task basis · Main process forks off each assigned task – Each server (outpost or not) is started the same way · Note on forks: Not just a sandbox necessity – Database shared resource problematic – process specific signals · e. g. timeout for polling 16 Managed by UT-Battelle for the Department of Energy
NACmgr Sandbox Environment · Open Sandbox for development – Needed to manipulate on a per-task basis · Main process forks off each assigned task – Each server (outpost or not) is started the same way · Note on forks: Not just a sandbox necessity – Database shared resource problematic – process specific signals · e. g. timeout for polling 16 Managed by UT-Battelle for the Department of Energy
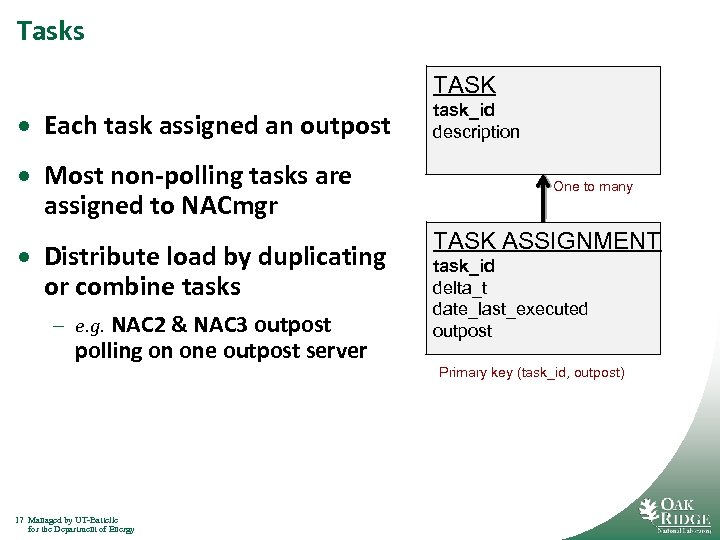 Tasks TASK · Each task assigned an outpost · Most non-polling tasks are assigned to NACmgr · Distribute load by duplicating or combine tasks – e. g. NAC 2 & NAC 3 outpost polling on one outpost server task_id description One to many TASK ASSIGNMENT task_id delta_t date_last_executed outpost Primary key (task_id, outpost) 17 Managed by UT-Battelle for the Department of Energy
Tasks TASK · Each task assigned an outpost · Most non-polling tasks are assigned to NACmgr · Distribute load by duplicating or combine tasks – e. g. NAC 2 & NAC 3 outpost polling on one outpost server task_id description One to many TASK ASSIGNMENT task_id delta_t date_last_executed outpost Primary key (task_id, outpost) 17 Managed by UT-Battelle for the Department of Energy
 Some Defined Tasks Enforcement Based · NP, NP 1, NP 2, NP 3 – NACmgr Polling · DW – Compare DHCP activity to Polling activity · UM – Automated block of the Unregistered · PW – Process warrants -- make arrests · MB – Monitoring blocked MACs 18 Managed by UT-Battelle for the Department of Energy
Some Defined Tasks Enforcement Based · NP, NP 1, NP 2, NP 3 – NACmgr Polling · DW – Compare DHCP activity to Polling activity · UM – Automated block of the Unregistered · PW – Process warrants -- make arrests · MB – Monitoring blocked MACs 18 Managed by UT-Battelle for the Department of Energy
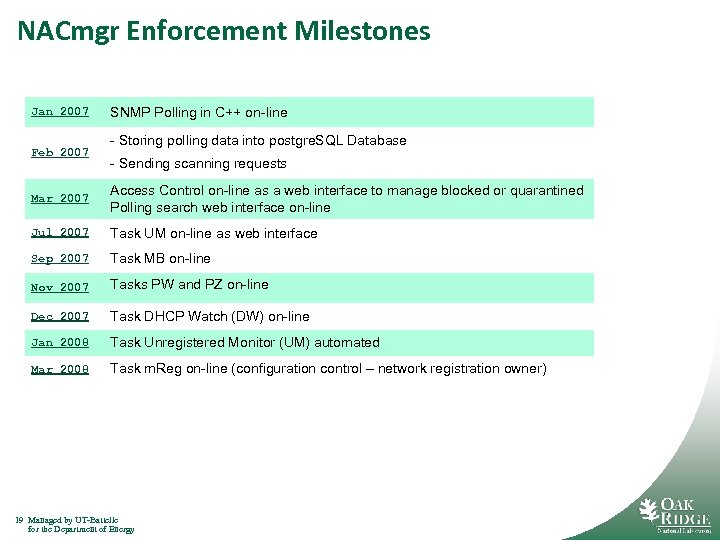 NACmgr Enforcement Milestones Jan 2007 Feb 2007 SNMP Polling in C++ on-line - Storing polling data into postgre. SQL Database - Sending scanning requests Mar 2007 Access Control on-line as a web interface to manage blocked or quarantined Polling search web interface on-line Jul 2007 Task UM on-line as web interface Sep 2007 Task MB on-line Nov 2007 Tasks PW and PZ on-line Dec 2007 Task DHCP Watch (DW) on-line Jan 2008 Task Unregistered Monitor (UM) automated Mar 2008 Task m. Reg on-line (configuration control – network registration owner) 19 Managed by UT-Battelle for the Department of Energy Jul 2007
NACmgr Enforcement Milestones Jan 2007 Feb 2007 SNMP Polling in C++ on-line - Storing polling data into postgre. SQL Database - Sending scanning requests Mar 2007 Access Control on-line as a web interface to manage blocked or quarantined Polling search web interface on-line Jul 2007 Task UM on-line as web interface Sep 2007 Task MB on-line Nov 2007 Tasks PW and PZ on-line Dec 2007 Task DHCP Watch (DW) on-line Jan 2008 Task Unregistered Monitor (UM) automated Mar 2008 Task m. Reg on-line (configuration control – network registration owner) 19 Managed by UT-Battelle for the Department of Energy Jul 2007
 Polling NAC Detection 20 Managed by UT-Battelle for the Department of Energy
Polling NAC Detection 20 Managed by UT-Battelle for the Department of Energy
![Polling Task ID: NP[1. . n] · Each L 3 Network is assigned to Polling Task ID: NP[1. . n] · Each L 3 Network is assigned to](https://present5.com/presentation/f4b951e9a9fa1d2b778e4b096a40301c/image-21.jpg) Polling Task ID: NP[1. . n] · Each L 3 Network is assigned to an outpost – Tasks serve to distribute polling 21 Managed by UT-Battelle for the Department of Energy
Polling Task ID: NP[1. . n] · Each L 3 Network is assigned to an outpost – Tasks serve to distribute polling 21 Managed by UT-Battelle for the Department of Energy
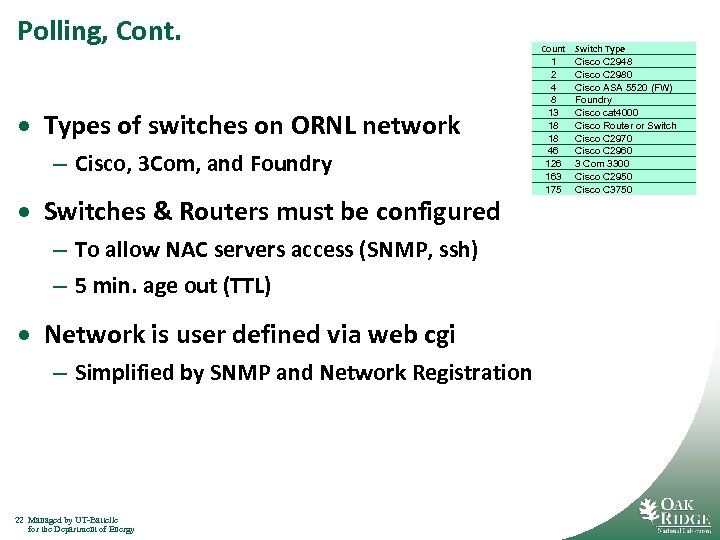 Polling, Cont. · Types of switches on ORNL network – Cisco, 3 Com, and Foundry · Switches & Routers must be configured – To allow NAC servers access (SNMP, ssh) – 5 min. age out (TTL) · Network is user defined via web cgi – Simplified by SNMP and Network Registration 22 Managed by UT-Battelle for the Department of Energy Count 1 2 4 8 13 18 18 46 126 163 175 Switch Type Cisco C 2948 Cisco C 2980 Cisco ASA 5520 (FW) Foundry Cisco cat 4000 Cisco Router or Switch Cisco C 2970 Cisco C 2960 3 Com 3300 Cisco C 2950 Cisco C 3750
Polling, Cont. · Types of switches on ORNL network – Cisco, 3 Com, and Foundry · Switches & Routers must be configured – To allow NAC servers access (SNMP, ssh) – 5 min. age out (TTL) · Network is user defined via web cgi – Simplified by SNMP and Network Registration 22 Managed by UT-Battelle for the Department of Energy Count 1 2 4 8 13 18 18 46 126 163 175 Switch Type Cisco C 2948 Cisco C 2980 Cisco ASA 5520 (FW) Foundry Cisco cat 4000 Cisco Router or Switch Cisco C 2970 Cisco C 2960 3 Com 3300 Cisco C 2950 Cisco C 3750
 Polling, Cont. · Uplink ports on switches – Defined in NACmgr via cgi – Simplified via SNMP · Active interfaces on port · CDP (where Cisco) 23 Managed by UT-Battelle for the Department of Energy
Polling, Cont. · Uplink ports on switches – Defined in NACmgr via cgi – Simplified via SNMP · Active interfaces on port · CDP (where Cisco) 23 Managed by UT-Battelle for the Department of Energy
 Polling, Cont. · Port conflicts monitored – Conflict means · same mac address · active at the same time · on two different ports/switches – Occurs when · Uplink port not set properly · MAC is spoofed · Network Loop 24 Managed by UT-Battelle for the Department of Energy
Polling, Cont. · Port conflicts monitored – Conflict means · same mac address · active at the same time · on two different ports/switches – Occurs when · Uplink port not set properly · MAC is spoofed · Network Loop 24 Managed by UT-Battelle for the Department of Energy
 Polling, Cont. · DHCP activity used to verify polling – ORNL requires all Desktops/Laptops use DHCP · 99. 7% laptops/desktops DHCP use – Produces a list of DHCP active MACs not in polling · Used to identify – Networks with missing switches – Switches with incorrect ignore ports – Task ID: DW 25 Managed by UT-Battelle for the Department of Energy
Polling, Cont. · DHCP activity used to verify polling – ORNL requires all Desktops/Laptops use DHCP · 99. 7% laptops/desktops DHCP use – Produces a list of DHCP active MACs not in polling · Used to identify – Networks with missing switches – Switches with incorrect ignore ports – Task ID: DW 25 Managed by UT-Battelle for the Department of Energy
 Polling, Cont. · All network devices polled < 5 min – Distribution of polling optimized among outposts – Load monitored on three scales (L 3, VLAN, L 2) – Serious use of Posix threads to make this happen · For each L 3 -network (thread a 1. . n) – For each VLAN in L 3 -network (thread b 1…n) · For each L 2 in VLAN in L 3 -network (thread c 1. . n) · ARP/Bridge TTL – Optimal periodicity = 5 min 26 Managed by UT-Battelle for the Department of Energy
Polling, Cont. · All network devices polled < 5 min – Distribution of polling optimized among outposts – Load monitored on three scales (L 3, VLAN, L 2) – Serious use of Posix threads to make this happen · For each L 3 -network (thread a 1. . n) – For each VLAN in L 3 -network (thread b 1…n) · For each L 2 in VLAN in L 3 -network (thread c 1. . n) · ARP/Bridge TTL – Optimal periodicity = 5 min 26 Managed by UT-Battelle for the Department of Energy
 Polling, Cont. · All hosts that have been inactive for more than 4 hours will be scanned upon re-entry – Part of the polling process – Nessus, policy based on · ISS X-Force’s Catastrophic Risk Index · SANS top 20 vulnerabilities 27 Managed by UT-Battelle for the Department of Energy
Polling, Cont. · All hosts that have been inactive for more than 4 hours will be scanned upon re-entry – Part of the polling process – Nessus, policy based on · ISS X-Force’s Catastrophic Risk Index · SANS top 20 vulnerabilities 27 Managed by UT-Battelle for the Department of Energy
 Polling - Accessing the Data · Polling data accessible via web interface – – – – Time polled L 2 switch port L 2 switch VLAN name and number L 3 router Mac address and IP address Scanning history Network Registration info based on MAC address 28 Managed by UT-Battelle for the Department of Energy
Polling - Accessing the Data · Polling data accessible via web interface – – – – Time polled L 2 switch port L 2 switch VLAN name and number L 3 router Mac address and IP address Scanning history Network Registration info based on MAC address 28 Managed by UT-Battelle for the Department of Energy
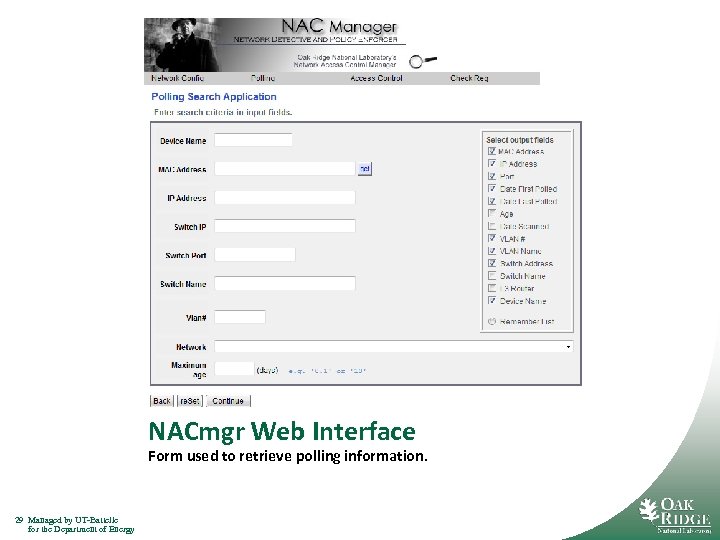 NACmgr Web Interface Form used to retrieve polling information. 29 Managed by UT-Battelle for the Department of Energy
NACmgr Web Interface Form used to retrieve polling information. 29 Managed by UT-Battelle for the Department of Energy
 Polling – Trouble Spots · Engineer/Tech manually adds network config – NACmgr is complicated – Training, communication, additional work · Switches may not be set up correctly – Passwords, SNMP access, TTL, etc · Wrong switch type defined in NACmgr – Engineer upgrades switch from 3 com to Cisco, but doesn’t update NACmgr – Results in no polling 30 Managed by UT-Battelle for the Department of Energy
Polling – Trouble Spots · Engineer/Tech manually adds network config – NACmgr is complicated – Training, communication, additional work · Switches may not be set up correctly – Passwords, SNMP access, TTL, etc · Wrong switch type defined in NACmgr – Engineer upgrades switch from 3 com to Cisco, but doesn’t update NACmgr – Results in no polling 30 Managed by UT-Battelle for the Department of Energy
 Polling – Trouble Spots, Cont. · SNMP issues – cache roll-over potential · Not tested – incomplete records – Switch not responding within 5 minutes · NAC polling sends SIGALARM to terminate process · Happens occasionally w/ large stacks of old 3 Com 3300 s · Bad unit in old 3 Com stack – Switch still functioning – NACmgr polling it, but not from bad unit 31 Managed by UT-Battelle for the Department of Energy
Polling – Trouble Spots, Cont. · SNMP issues – cache roll-over potential · Not tested – incomplete records – Switch not responding within 5 minutes · NAC polling sends SIGALARM to terminate process · Happens occasionally w/ large stacks of old 3 Com 3300 s · Bad unit in old 3 Com stack – Switch still functioning – NACmgr polling it, but not from bad unit 31 Managed by UT-Battelle for the Department of Energy
 Polling – Trouble Spots, Cont. · Tasked Solutions: – Task ‘DW’ · Diff of Polling and DHCP activity · Large turn-around time and very manual process – Task ‘t. C’ (not in production) · Tests connectivity of switches and routers · VLAN and Port uplink verification 32 Managed by UT-Battelle for the Department of Energy
Polling – Trouble Spots, Cont. · Tasked Solutions: – Task ‘DW’ · Diff of Polling and DHCP activity · Large turn-around time and very manual process – Task ‘t. C’ (not in production) · Tests connectivity of switches and routers · VLAN and Port uplink verification 32 Managed by UT-Battelle for the Department of Energy
 Monitoring for Unregistered NAC Compliance and Enforcement 33 Managed by UT-Battelle for the Department of Energy
Monitoring for Unregistered NAC Compliance and Enforcement 33 Managed by UT-Battelle for the Department of Energy
 Unregistered Monitor Task ID: UM · Automated · Checks mac registration · If not registered and not using Net-Jail IP address – Assume statically configured – Must be L 2 -blocked · Disabling port on 3 Com/Foundry switch · MAC drop on Cisco – Network Registration updated · Users can search to see if blocked · Cannot modify MAC address record – Help. Line request 34 Managed by UT-Battelle for the Department of Energy
Unregistered Monitor Task ID: UM · Automated · Checks mac registration · If not registered and not using Net-Jail IP address – Assume statically configured – Must be L 2 -blocked · Disabling port on 3 Com/Foundry switch · MAC drop on Cisco – Network Registration updated · Users can search to see if blocked · Cannot modify MAC address record – Help. Line request 34 Managed by UT-Battelle for the Department of Energy
 Unregistered Monitor (UM), Cont. · Not all networks Auto. Block enabled – E. g. · Server (Infrastructure) LAN · Open Public (web server) LAN – Solution: · Create NACmgr config option – VLAN configured autoblock=[Y/N] · Only send nag messages (NAGmgr) – Network must be isolated (protection zone enclave) – Physically locked server room - IT staff access only 35 Managed by UT-Battelle for the Department of Energy
Unregistered Monitor (UM), Cont. · Not all networks Auto. Block enabled – E. g. · Server (Infrastructure) LAN · Open Public (web server) LAN – Solution: · Create NACmgr config option – VLAN configured autoblock=[Y/N] · Only send nag messages (NAGmgr) – Network must be isolated (protection zone enclave) – Physically locked server room - IT staff access only 35 Managed by UT-Battelle for the Department of Energy
 UM Trouble Spots · Combining two sets of large data 1. Network Registration MAC address records 2. Polling records – Solution · Import into NAC database the list of registered mac addresses · To minimize overhead have to – truncate table /usr/bin/psql -d NAC -c "truncate table Net. Reg_macs” – and do a system call to add the data from a flat file /usr/bin/psql -d NAC –c “copy Net. Reg_macs from ‘filename’” 36 Managed by UT-Battelle for the Department of Energy
UM Trouble Spots · Combining two sets of large data 1. Network Registration MAC address records 2. Polling records – Solution · Import into NAC database the list of registered mac addresses · To minimize overhead have to – truncate table /usr/bin/psql -d NAC -c "truncate table Net. Reg_macs” – and do a system call to add the data from a flat file /usr/bin/psql -d NAC –c “copy Net. Reg_macs from ‘filename’” 36 Managed by UT-Battelle for the Department of Energy
 UM Trouble Spots, Cont. · Managing blocks and quarantines – Unregistered attach registration record to dummy – Quarantine works only if registered and using DHCP · Management of Unregistered L 2 -Blocks – To minimize size of list: · Un-block after 60 days · If still on the network, um will automatically block them again 37 Managed by UT-Battelle for the Department of Energy
UM Trouble Spots, Cont. · Managing blocks and quarantines – Unregistered attach registration record to dummy – Quarantine works only if registered and using DHCP · Management of Unregistered L 2 -Blocks – To minimize size of list: · Un-block after 60 days · If still on the network, um will automatically block them again 37 Managed by UT-Battelle for the Department of Energy
 UM Trouble Spots, Cont. · Conflict with users and IT Support staff – Host must be configured for DHCP BEFORE connecting to the network – If statically configured, user must remove from network before deleting registration · Un-routed mac addresses – Virtual and dynamically allocated (block) · Don’t know what it is until on the network – DHCP-DISCOVER packets not routed (don’t block) 38 Managed by UT-Battelle for the Department of Energy
UM Trouble Spots, Cont. · Conflict with users and IT Support staff – Host must be configured for DHCP BEFORE connecting to the network – If statically configured, user must remove from network before deleting registration · Un-routed mac addresses – Virtual and dynamically allocated (block) · Don’t know what it is until on the network – DHCP-DISCOVER packets not routed (don’t block) 38 Managed by UT-Battelle for the Department of Energy
 Processing Warrants for Non-Compliant NAC Enforcement 39 Managed by UT-Battelle for the Department of Energy
Processing Warrants for Non-Compliant NAC Enforcement 39 Managed by UT-Battelle for the Department of Energy
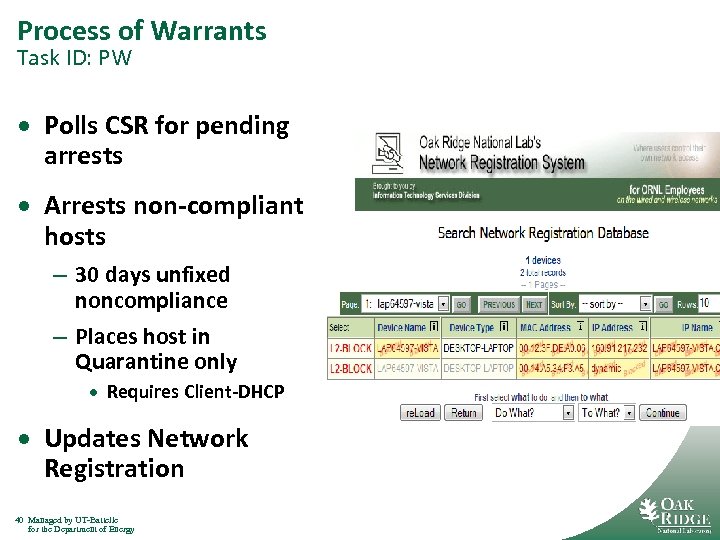 Process of Warrants Task ID: PW · Polls CSR for pending arrests · Arrests non-compliant hosts – 30 days unfixed noncompliance – Places host in Quarantine only · Requires Client-DHCP · Updates Network Registration 40 Managed by UT-Battelle for the Department of Energy
Process of Warrants Task ID: PW · Polls CSR for pending arrests · Arrests non-compliant hosts – 30 days unfixed noncompliance – Places host in Quarantine only · Requires Client-DHCP · Updates Network Registration 40 Managed by UT-Battelle for the Department of Energy
 PW Trouble Spots · Limited to DHCP Quarantines · Does not test client for DHCP activity – Web based user check – Different task (TBD) to be developed 41 Managed by UT-Battelle for the Department of Energy
PW Trouble Spots · Limited to DHCP Quarantines · Does not test client for DHCP activity – Web based user check – Different task (TBD) to be developed 41 Managed by UT-Battelle for the Department of Energy
 Monitoring L 2 Blocks NAC Enforcement 42 Managed by UT-Battelle for the Department of Energy
Monitoring L 2 Blocks NAC Enforcement 42 Managed by UT-Battelle for the Department of Energy
 Monitor L 2 Blocks Task ID: MB · Block at switch · Easy to regain access – Port Disabled · Move to a different port – MAC dropped · Change network · Spoof mac 43 Managed by UT-Battelle for the Department of Energy
Monitor L 2 Blocks Task ID: MB · Block at switch · Easy to regain access – Port Disabled · Move to a different port – MAC dropped · Change network · Spoof mac 43 Managed by UT-Battelle for the Department of Energy
 NACmb: Monitor L 2 Blocks, Cont. · Active and Blocked hosts – Will be automatically re-blocked – Limit mac drops on [L 2 -switch, port] · Avoid the possibility of dynamically allocated spoofed MAC addresses on compromised host 44 Managed by UT-Battelle for the Department of Energy
NACmb: Monitor L 2 Blocks, Cont. · Active and Blocked hosts – Will be automatically re-blocked – Limit mac drops on [L 2 -switch, port] · Avoid the possibility of dynamically allocated spoofed MAC addresses on compromised host 44 Managed by UT-Battelle for the Department of Energy
 NACmgr Strengths · Managed Out-of-Band w/ No supplicant · Cost Effective · Simple deployment and operation – Speak softly and carry big stick · Accommodates current network – All switch types · Good solution – vs. No solution – DHCP was the only other way 45 Managed by UT-Battelle for the Department of Energy
NACmgr Strengths · Managed Out-of-Band w/ No supplicant · Cost Effective · Simple deployment and operation – Speak softly and carry big stick · Accommodates current network – All switch types · Good solution – vs. No solution – DHCP was the only other way 45 Managed by UT-Battelle for the Department of Energy
 NACmgr Weaknesses · The host is already on the network – Before non-compliance is detected · Unable to detect masquerading hosts – NAT (network address translation) · E. g. IP Sharing w/Microsoft – Virtualization software · e. g. Virtual PC, Vmware 46 Managed by UT-Battelle for the Department of Energy
NACmgr Weaknesses · The host is already on the network – Before non-compliance is detected · Unable to detect masquerading hosts – NAT (network address translation) · E. g. IP Sharing w/Microsoft – Virtualization software · e. g. Virtual PC, Vmware 46 Managed by UT-Battelle for the Department of Energy
 Future Direction · More Cisco · Refine how to define uplink ports – CDP – Interface testing · Working out SNMP issues – Incomplete data · Tasks Development – m. IP, m. PZ, Post-quarantine activity check 47 Managed by UT-Battelle for the Department of Energy
Future Direction · More Cisco · Refine how to define uplink ports – CDP – Interface testing · Working out SNMP issues – Incomplete data · Tasks Development – m. IP, m. PZ, Post-quarantine activity check 47 Managed by UT-Battelle for the Department of Energy
 Conclusion · Enforces compliance – Detects, Monitors, and Isolates · Determines compliance – UM, PZ, m. IP, m. Reg, etc · Monitors for rogue activity – Unregistered – “Port conflicts” · No standard NAC solution – Is NACmgr just as good as what’s out there? 48 Managed by UT-Battelle for the Department of Energy
Conclusion · Enforces compliance – Detects, Monitors, and Isolates · Determines compliance – UM, PZ, m. IP, m. Reg, etc · Monitors for rogue activity – Unregistered – “Port conflicts” · No standard NAC solution – Is NACmgr just as good as what’s out there? 48 Managed by UT-Battelle for the Department of Energy
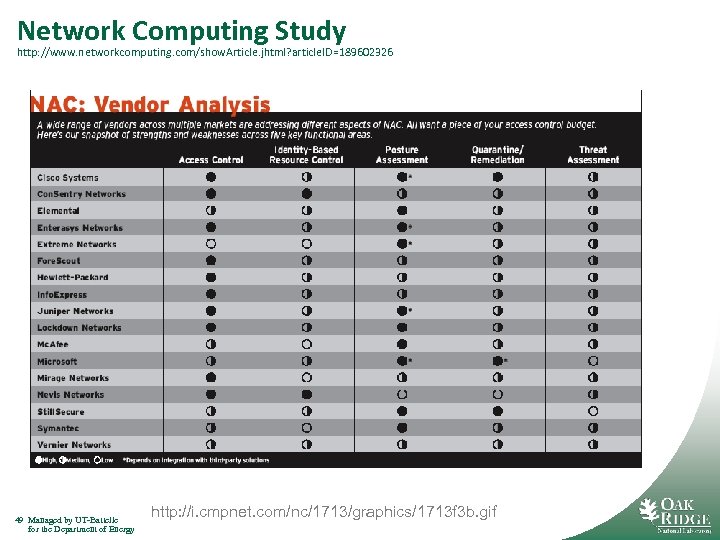 Network Computing Study http: //www. networkcomputing. com/show. Article. jhtml? article. ID=189602326 49 Managed by UT-Battelle for the Department of Energy http: //i. cmpnet. com/nc/1713/graphics/1713 f 3 b. gif
Network Computing Study http: //www. networkcomputing. com/show. Article. jhtml? article. ID=189602326 49 Managed by UT-Battelle for the Department of Energy http: //i. cmpnet. com/nc/1713/graphics/1713 f 3 b. gif
 Future of NAC · Articles: Trying To Have It Both Ways and Shimel's New Rules on NAC – NAC is not going to stop the most determined hacker, but a dirty machine is more likely to cause trouble than a clean machine – NAC is an ecosystem, not a single product – Expect 802. 1 x to become dominant standard in networking – NAC was never meant as a silver bullet · Just another security layer 50 Managed by UT-Battelle for the Department of Energy
Future of NAC · Articles: Trying To Have It Both Ways and Shimel's New Rules on NAC – NAC is not going to stop the most determined hacker, but a dirty machine is more likely to cause trouble than a clean machine – NAC is an ecosystem, not a single product – Expect 802. 1 x to become dominant standard in networking – NAC was never meant as a silver bullet · Just another security layer 50 Managed by UT-Battelle for the Department of Energy
 Future of NAC, Cont. · NAC will eventually be standardized – The IETF NEA Working Group has decided to adopt several of the latest TNC standards as Working Group drafts – There are two versions of each spec: the IETF version and the TCG version · The IETF specs are PA-TNC and PB-TNC. – The IETF has created a working group to develop NAC standards and Cisco, which does not participate in the TCG, supports the IETF effort. · The TCG specs are IF-M 1. 0 and IF-TNCCS 2. 0. – The TCG is writing NAC standards to promote multivendor interoperability. – http: //nacblog. juniper. net – http: //www. networkworld. com/buzz/2006/111306 -nac-faq. html? page=2 51 Managed by UT-Battelle for the Department of Energy
Future of NAC, Cont. · NAC will eventually be standardized – The IETF NEA Working Group has decided to adopt several of the latest TNC standards as Working Group drafts – There are two versions of each spec: the IETF version and the TCG version · The IETF specs are PA-TNC and PB-TNC. – The IETF has created a working group to develop NAC standards and Cisco, which does not participate in the TCG, supports the IETF effort. · The TCG specs are IF-M 1. 0 and IF-TNCCS 2. 0. – The TCG is writing NAC standards to promote multivendor interoperability. – http: //nacblog. juniper. net – http: //www. networkworld. com/buzz/2006/111306 -nac-faq. html? page=2 51 Managed by UT-Battelle for the Department of Energy
 More Information on ORNL’s Network Security · Update on Network Enhancements for DID at ORNL Implementation of Network Infrastructural changes – relevant to NAC Enforcement and Authorization – Clark Piercy – Room: Columbus H – Starting date: 12 -May-2008 15: 30 (Today) · Who’s Your System Administrator? Relevant to Endpoint Security and NAC Compliance – Suzanne Willoughby – Room: Columbus E-F – Starting date: 13 -May-2008 16: 15 (Tomorrow) 52 Managed by UT-Battelle for the Department of Energy
More Information on ORNL’s Network Security · Update on Network Enhancements for DID at ORNL Implementation of Network Infrastructural changes – relevant to NAC Enforcement and Authorization – Clark Piercy – Room: Columbus H – Starting date: 12 -May-2008 15: 30 (Today) · Who’s Your System Administrator? Relevant to Endpoint Security and NAC Compliance – Suzanne Willoughby – Room: Columbus E-F – Starting date: 13 -May-2008 16: 15 (Tomorrow) 52 Managed by UT-Battelle for the Department of Energy
 Questions? 53 Managed by UT-Battelle for the Department of Energy
Questions? 53 Managed by UT-Battelle for the Department of Energy


