5dd07aa150f7034f468196bb010d83d1.ppt
- Количество слайдов: 90
Encryption Basics • Uses mathematics to scramble data • Uses a key and an algorithm • Symmetric key • Asymmetric keys November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 1

Encryption • Link encryption – Each host enciphers message so host at “next hop” can read it – Message can be read at intermediate hosts • End-to-end encryption – Host enciphers message so host at other end of communication can read it – Message cannot be read at intermediate hosts November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 2
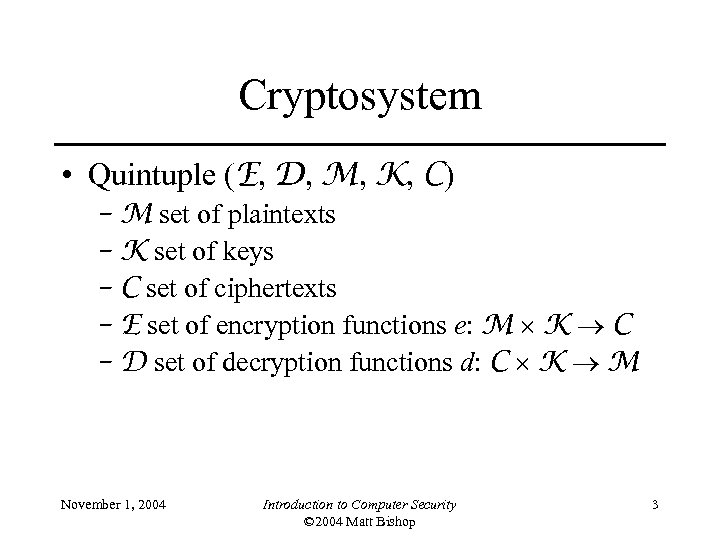
Cryptosystem • Quintuple (E, D, M, K, C) – M set of plaintexts – K set of keys – C set of ciphertexts – E set of encryption functions e: M K C – D set of decryption functions d: C K M November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 3

Attacks • Opponent whose goal is to break cryptosystem is the adversary – Assume adversary knows algorithm used, but not key • Three types of attacks: – ciphertext only: adversary has only ciphertext; goal is to find plaintext, possibly key – known plaintext: adversary has ciphertext, corresponding plaintext; goal is to find key – chosen plaintext: adversary may supply plaintexts and obtain corresponding ciphertext; goal is to find key November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 4

Basis for Attacks • Mathematical attacks – Based on analysis of underlying mathematics • Statistical attacks – Make assumptions about the distribution of letters, pairs of letters (digrams), triplets of letters (trigrams), etc. • Called models of the language – Examine ciphertext, correlate properties with the assumptions. November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 5

Classical Cryptography • Sender, receiver share common key – Keys may be the same, or trivial to derive from one another – Sometimes called symmetric cryptography • Two basic types – Transposition ciphers – Substitution ciphers – Combinations are called product ciphers November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 6

Transposition Cipher • Rearrange letters in plaintext to produce ciphertext • Example (Rail-Fence Cipher) – Plaintext is HELLO WORLD – Rearrange as HLOOL ELWRD – Ciphertext is HLOOL ELWRD November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 7
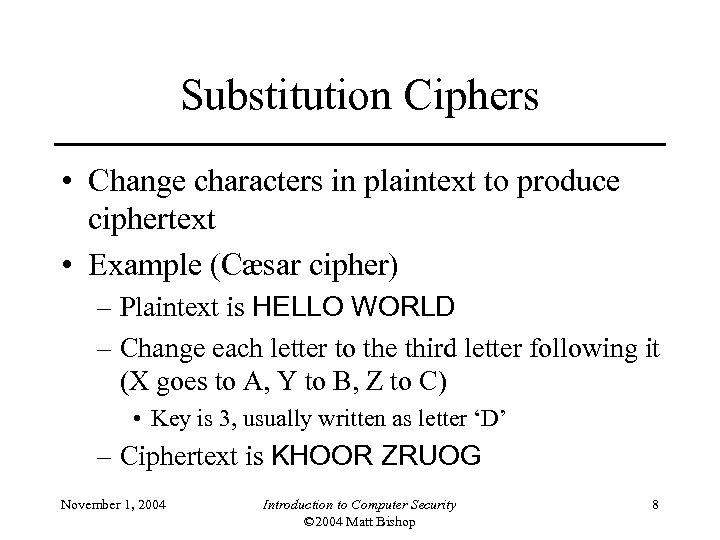
Substitution Ciphers • Change characters in plaintext to produce ciphertext • Example (Cæsar cipher) – Plaintext is HELLO WORLD – Change each letter to the third letter following it (X goes to A, Y to B, Z to C) • Key is 3, usually written as letter ‘D’ – Ciphertext is KHOOR ZRUOG November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 8

Character Frequencies a 0. 080 h 0. 060 n 0. 070 t 0. 090 b 0. 015 i 0. 065 o 0. 080 u 0. 030 c 0. 030 j 0. 005 p 0. 020 v 0. 010 d 0. 040 k 0. 005 q 0. 002 w 0. 015 e 0. 130 l 0. 035 r 0. 065 x 0. 005 f 0. 020 m 0. 030 s 0. 060 y 0. 020 g 0. 015 z 0. 002 November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 9

Cæsar’s Problem • Key is too short – Can be found by exhaustive search – Statistical frequencies not concealed well • They look too much like regular English letters • So make it longer – Multiple letters in key – Idea is to smooth the statistical frequencies to make cryptanalysis harder November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 10

Problems • Using cipher requires knowledge of environment, and threats in the environment, in which cipher will be used – Is the set of possible messages small? – Do the messages exhibit regularities that remain after encipherment? – Can an active wiretapper rearrange or change parts of the message? November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 11
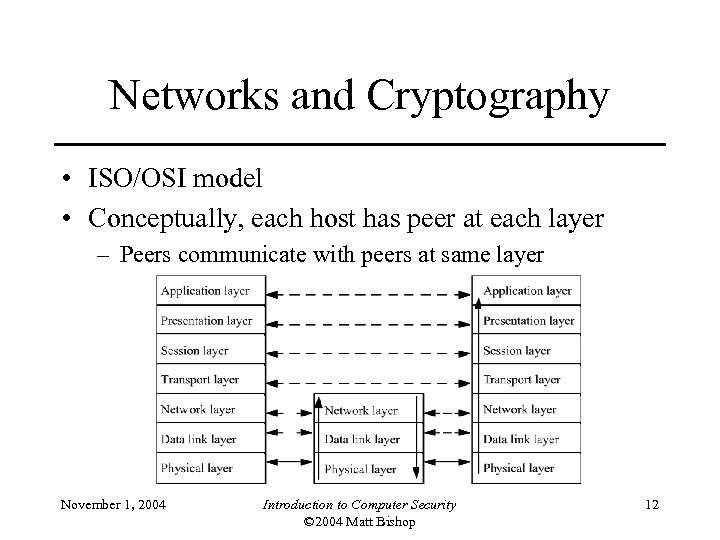
Networks and Cryptography • ISO/OSI model • Conceptually, each host has peer at each layer – Peers communicate with peers at same layer November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 12

Cryptographic Considerations • Link encryption – Each host shares key with neighbor – Can be set on per-host or per-host-pair basis • Windsor, stripe, seaview each have own keys • One key for (windsor, stripe); one for (stripe, seaview); one for (windsor, seaview) • End-to-end – Each host shares key with destination – Can be set on per-host or per-host-pair basis – Message cannot be read at intermediate nodes November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 13
Traffic Analysis • Link encryption – Can protect headers of packets – Possible to hide source and destination • Note: may be able to deduce this from traffic flows • End-to-end encryption – Cannot hide packet headers • Intermediate nodes need to route packet – Attacker can read source, destination November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 14
Example Protocols • Privacy-Enhanced Electronic Mail (PEM) – Applications layer protocol • IP Security (IPSec) – Network layer protocol November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 15
Design Principles • Do not change related existing protocols – Cannot alter SMTP • Do not change existing software – Need compatibility with existing software • Make use of PEM optional – Available if desired, but email still works without them – Some recipients may use it, others not • Enable communication without prearrangement – Out-of-bands authentication, key exchange problematic November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 16

Basic Design: Keys • Two keys – Interchange keys tied to sender, recipients and is static (for some set of messages) • Like a public/private key pair • Must be available before messages sent – Data exchange keys generated for each message • Like a session key, session being the message November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 17
Overview of the DES • A block cipher: – encrypts blocks of 64 bits using a 64 bit key – outputs 64 bits of ciphertext • A product cipher – basic unit is the bit – performs both substitution and transposition (permutation) on the bits • Cipher consists of 16 rounds (iterations) each with a round key generated from the user-supplied key November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 18
Controversy • Considered too weak – Diffie, Hellman said in a few years technology would allow DES to be broken in days • Design using 1999 technology published – Design decisions not public • S-boxes may have backdoors November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 19

Current Status of DES • Design for computer system, associated software that could break any DES-enciphered message in a few days published in 1998 • Several challenges to break DES messages solved using distributed computing • NIST selected Rijndael as Advanced Encryption Standard, successor to DES – Designed to withstand attacks that were successful on DES November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 20

Public Key Cryptography • Two keys – Private key known only to individual – Public key available to anyone • Public key, private key inverses • Idea – Confidentiality: encipher using public key, decipher using private key – Integrity/authentication: encipher using private key, decipher using public one November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 21

Requirements 1. It must be computationally easy to encipher or decipher a message given the appropriate key 2. It must be computationally infeasible to derive the private key from the public key 3. It must be computationally infeasible to determine the private key from a chosen plaintext attack November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 22

RSA • Exponentiation cipher • Relies on the difficulty of determining the number of numbers relatively prime to a large integer n November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 23
Background • Totient function (n) – Number of positive integers less than n and relatively prime to n • Relatively prime means with no factors in common with n • Example: (10) = 4 – 1, 3, 7, 9 are relatively prime to 10 • Example: (21) = 12 – 1, 2, 4, 5, 8, 10, 11, 13, 16, 17, 19, 20 are relatively prime to 21 November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 24

Security Services • Confidentiality – Only the owner of the private key knows it, so text enciphered with public key cannot be read by anyone except the owner of the private key • Authentication – Only the owner of the private key knows it, so text enciphered with private key must have been generated by the owner November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 25

More Security Services • Integrity – Enciphered letters cannot be changed undetectably without knowing private key • Non-Repudiation – Message enciphered with private key came from someone who knew it November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 26
Cryptographic Checksums • Mathematical function to generate a set of k bits from a set of n bits (where k ≤ n). – k is smaller then n except in unusual circumstances • Example: ASCII parity bit – ASCII has 7 bits; 8 th bit is “parity” – Even parity: even number of 1 bits – Odd parity: odd number of 1 bits November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 27
Example Use • Bob receives “ 10111101” as bits. – Sender is using even parity; 6 1 bits, so character was received correctly • Note: could be garbled, but 2 bits would need to have been changed to preserve parity – Sender is using odd parity; even number of 1 bits, so character was not received correctly November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 28
Collisions • If x ≠ x and h(x) = h(x ), x and x are a collision – Pigeonhole principle: if there are n containers for n+1 objects, then at least one container will have 2 objects in it. – Application: if there are 32 files and 8 possible cryptographic checksum values, at least one value corresponds to at least 4 files November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 29
Keys • Keyed cryptographic checksum: requires cryptographic key – DES in chaining mode: encipher message, use last n bits. Requires a key to encipher, so it is a keyed cryptographic checksum. • Keyless cryptographic checksum: requires no cryptographic key – MD 5 and SHA-1 are best known; others include MD 4, HAVAL, and Snefru November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 30
Key Exchange Algorithms • Goal: Alice, Bob get shared key – Key cannot be sent in clear • Attacker can listen in • Key can be sent enciphered, or derived from exchanged data plus data not known to an eavesdropper – Alice, Bob may trust third party – All cryptosystems, protocols publicly known • Only secret data is the keys, ancillary information known only to Alice and Bob needed to derive keys • Anything transmitted is assumed known to attacker November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 31
Classical Key Exchange • Bootstrap problem: how do Alice, Bob begin? – Alice can’t send it to Bob in the clear! • Assume trusted third party, Cathy – Alice and Cathy share secret key k. A – Bob and Cathy share secret key k. B • Use this to exchange shared key ks November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 32
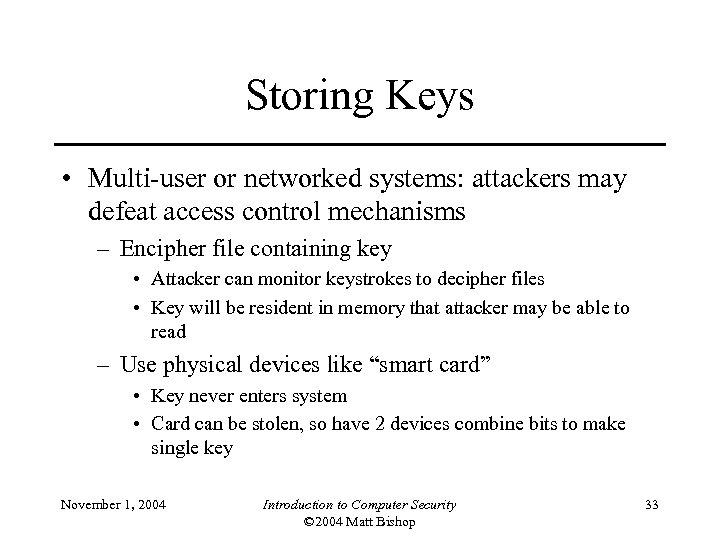
Storing Keys • Multi-user or networked systems: attackers may defeat access control mechanisms – Encipher file containing key • Attacker can monitor keystrokes to decipher files • Key will be resident in memory that attacker may be able to read – Use physical devices like “smart card” • Key never enters system • Card can be stolen, so have 2 devices combine bits to make single key November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 33

Key Revocation • Certificates invalidated before expiration – Usually due to compromised key – May be due to change in circumstance (e. g. , someone leaving company) • Problems – Entity revoking certificate authorized to do so – Revocation information circulates to everyone fast enough • Network delays, infrastructure problems may delay information November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 34

CRLs • Certificate revocation lists certificates that are revoked • X. 509: only certificate issuer can revoke certificate – Added to CRL • PGP: signers can revoke signatures; owners can revoke certificates, or allow others to do so – Revocation message placed in PGP packet and signed – Flag marks it as revocation message November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 35

Problems • How does Bob know he is talking to Alice? – Replay attack: Eve records message from Alice to Bob, later replays it; Bob may think he’s talking to Alice, but he isn’t – Session key reuse: Eve replays message from Alice to Bob, so Bob re-uses session key • Protocols must provide authentication and defense against replay November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 36

Argument: Alice talking to Bob • Second message – Enciphered using key only she, Cathy knows • So Cathy enciphered it – Response to first message • As r 1 in it matches r 1 in first message • Third message – Alice knows only Bob can read it • As only Bob can derive session key from message – Any messages enciphered with that key are from Bob November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 37

Argument: Bob talking to Alice • Third message – Enciphered using key only he, Cathy know • So Cathy enciphered it – Names Alice, session key • Cathy provided session key, says Alice is other party • Fourth message – Uses session key to determine if it is replay from Eve • If not, Alice will respond correctly in fifth message • If so, Eve can’t decipher r 2 and so can’t respond, or responds incorrectly November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 38

Solution • In protocol above, Eve impersonates Alice • Problem: replay in third step – First in previous slide • Solution: use time stamp T to detect replay • Weakness: if clocks not synchronized, may either reject valid messages or accept replays – Parties with either slow or fast clocks vulnerable to replay – Resetting clock does not eliminate vulnerability November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 39
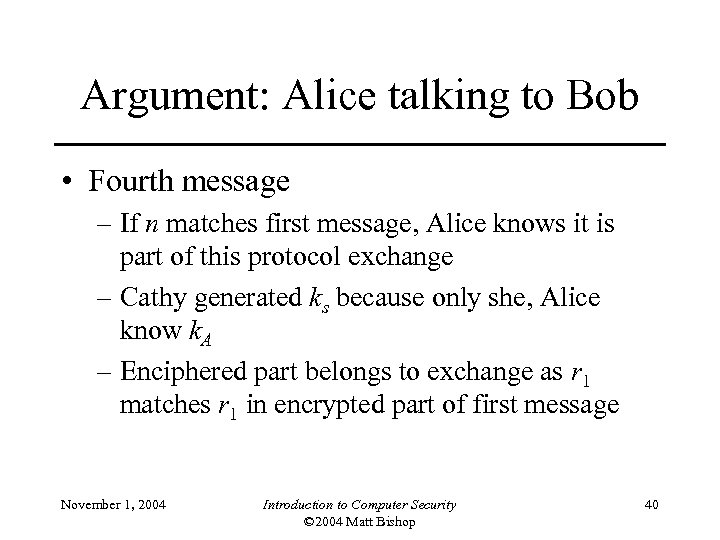
Argument: Alice talking to Bob • Fourth message – If n matches first message, Alice knows it is part of this protocol exchange – Cathy generated ks because only she, Alice know k. A – Enciphered part belongs to exchange as r 1 matches r 1 in encrypted part of first message November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 40

Argument: Bob talking to Alice • Third message – If n matches second message, Bob knows it is part of this protocol exchange – Cathy generated ks because only she, Bob know k. B – Enciphered part belongs to exchange as r 2 matches r 2 in encrypted part of second message November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 41
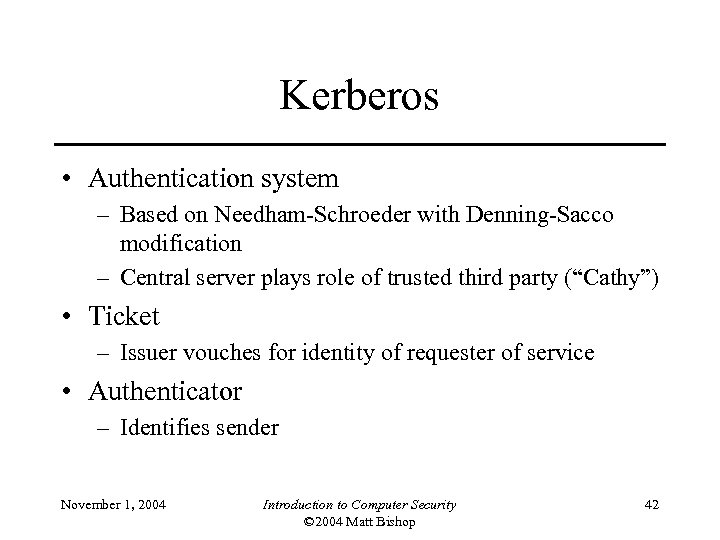
Kerberos • Authentication system – Based on Needham-Schroeder with Denning-Sacco modification – Central server plays role of trusted third party (“Cathy”) • Ticket – Issuer vouches for identity of requester of service • Authenticator – Identifies sender November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 42
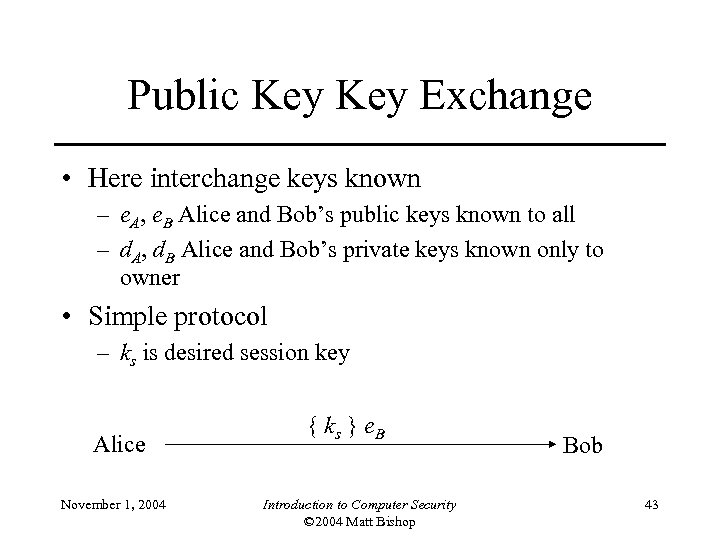
Public Key Exchange • Here interchange keys known – e. A, e. B Alice and Bob’s public keys known to all – d. A, d. B Alice and Bob’s private keys known only to owner • Simple protocol – ks is desired session key Alice November 1, 2004 { ks } e. B Introduction to Computer Security © 2004 Matt Bishop Bob 43

Man-in-the-Middle Attack Alice send Bob’s public key Eve Alice e. E send Bob’s public key e. B Eve Cathy Eve { ks } e. E Eve intercepts message Eve November 1, 2004 Eve intercepts request { ks } e. B Introduction to Computer Security © 2004 Matt Bishop Bob 44

Cryptographic Key Infrastructure • Goal: bind identity to key • Classical: not possible as all keys are shared – Use protocols to agree on a shared key (see earlier) • Public key: bind identity to public key – Crucial as people will use key to communicate with principal whose identity is bound to key – Erroneous binding means no secrecy between principals – Assume principal identified by an acceptable name November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 45

Encryption Strength • The secrecy of the key • The length of the key • The rigour of the algorithm November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 46

Weaknesses of Symmetric Key • More easily compromised by a third party • A large number of keys is required • Secure key delivery a challenge • Formula is (n 2 – n) / 2 November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 47

Weaknesses of Symmetric Keys • This means 8 million keys for 4, 000 users • How many public keys would you need for 4, 000 people? (8, 000) • Cannot be used for digital signature November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 48

Public/Private Keys – Simple Rules • Encrypt a message – use the recipient’s public key • Encrypt a signature – use your own private key • Decrypt a message – use your own private key November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 49
Private/public Key – Simple Rules and Protocol • Decrypt a signature – use the sender’s public key. • Private key resides on the PC or in a smart card. • Smart card private encrypts on the card, key not transferred to computer. November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 50

What to Encrypt • Assess data confidentiality • Assess regulatory requirements • Consider internal and external risks • Recipient’s capacity to decrypt November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 51

What to Encrypt • High sensitive material • Medium sensitive material when stored in portal media outside the office November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 52
Common Encryption Tools • Secure Socket Layer (SSL) • Pretty Good Privacy • IP Sec (used in VPN’s) • S/MIME • Elliptic curve (for wireless devices) November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 53

Symmetric Key Encryption • The same key is used to decrypt and encrypt • Simple to encrypt and decrypt • Large number of keys required for one-onone secret communication • Number of keys for N people is N(N-1)/2 • Need to secure the key November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 54

Asymmetric Encryption • A pair of key is generated by a user, a private key and a corresponding public key. • The public key can be disclosed. The private key is secured. • People can use the public key to encrypt material. November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 55
Asymmetric Encryption • The corresponding private key is needed to decrypt. • The 2 keys cannot be reengineered, i. e. , you cannot use the public key to derive the private key. • Longer keys than symmetric and therefore a longer process to encrypt and decrypt. November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 56

Asymmetric Encryption • Needed for email encryption. • Used for e-commerce, digital certificates and digital signatures. • Number of keys for N users is 2 N. November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 57

SSL Process • HTTPS, uses port 443 • The client opens a connection and sends a Hello • The server sends back a Hello • They may exchange certificates November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 58

SSL Process • They exchange public keys • Handshake • All subsequent messages are encrypted November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 59

E-commerce Encryption • Uses both symmetric keys and asymmetric keys • Enforced by the merchant • Merchant sends its certificate and public key to the browser November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 60
E-commerce Encryption • Browser generates a symmetric key • Browser encrypts the symmetric key with the merchant’s public key • Browser authenticates the digital certificate • Encrypted symmetric key is sent to merchant November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 61
E-commerce Encryption • Merchant decrypts the symmetric key with its private key • The symmetric key is used for all subsequent transfer of information between the 2 parties until the user logs off. November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 62

Pretty Good Privacy (PGP) • A complete working system for the cryptographic protection of email and files • Uses the RSA public key encryption for key management and IDEA symmetric cipher for the bulk encryption of data November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 63

PGP • Available as a corporate PKI product or a client based program • No need for certificate authority • Users exchange public keys • Each user can certify the public keys of other users November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 64

PGP • Encrypt first then sign, prevents surreptitious forwarding. • File encryption. • Symmetric key encryption enables people who don’t have PGP to open encrypted files. November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 65

PGP Chains • Open. PGP certificates structured into packets – One public key packet – Zero or more signature packets • Public key packet: – Version (3 or 4; 3 compatible with all versions of PGP, 4 not compatible with older versions of PGP) – Creation time – Validity period (not present in version 3) – Public key algorithm, associated parameters – Public key November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 66

S/MIME • Secured Multipurpose Internet Mail Extensions. • Can be implemented as non-proprietary, open standard product. • Uses public key system for key encryption and symmetric key for data encryption. November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 67

Digital Certificates • CA certificate • Server certificate • Personal certificate • Software publisher certificate November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 68

Digital Certificate • An electronic business card that establishes your credentials when doing business or other transactions on the Web. • It is issued and digitally signed by a certification authority. It contains your name, a serial number, expiration dates, the certificate authority’s name and public key, and your public key. • People can use the certificate authority’s public key to verify the signature. November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 69
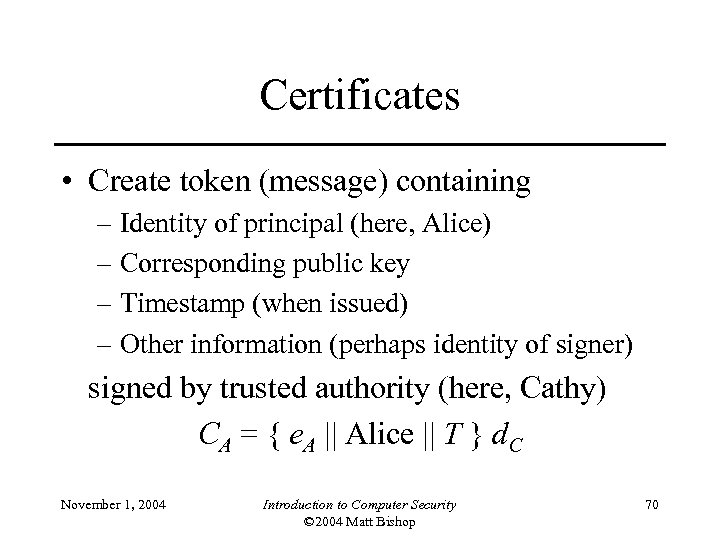
Certificates • Create token (message) containing – Identity of principal (here, Alice) – Corresponding public key – Timestamp (when issued) – Other information (perhaps identity of signer) signed by trusted authority (here, Cathy) CA = { e. A || Alice || T } d. C November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 70
Use • Bob gets Alice’s certificate – If he knows Cathy’s public key, he can decipher the certificate • When was certificate issued? • Is the principal Alice? – Now Bob has Alice’s public key • Problem: Bob needs Cathy’s public key to validate certificate – Problem pushed “up” a level – Two approaches: Merkle’s tree, signature chains November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 71

Certificate Signature Chains • Create certificate – Generate hash of certificate – Encipher hash with issuer’s private key • Validate – Obtain issuer’s public key – Decipher enciphered hash – Recompute hash from certificate and compare • Problem: getting issuer’s public key November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 72
X. 509 Chains • Some certificate components in X. 509 v 3: – – – – Version Serial number Signature algorithm identifier: hash algorithm Issuer’s name; uniquely identifies issuer Interval of validity Subject’s name; uniquely identifies subject Subject’s public key Signature: enciphered hash November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 73

X. 509 Certificate Validation • Obtain issuer’s public key – The one for the particular signature algorithm • Decipher signature – Gives hash of certificate • Recompute hash from certificate and compare – If they differ, there’s a problem • Check interval of validity – This confirms that certificate is current November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 74

Issuers • Certification Authority (CA): entity that issues certificates – Multiple issuers pose validation problem – Alice’s CA is Cathy; Bob’s CA is Don; how can Alice validate Bob’s certificate? – Have Cathy and Don cross-certify • Each issues certificate for the other November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 75

Certificate Authority • An organization that issues digital certificates to companies and individuals • An organization can issue digital certificates to its own customers or employees to authenticate local transactions • The certificate authority will do due diligence to confirm the existence and authenticity of the party before issuing a certificate. November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 76

Digital Signature • A message digest that is encrypted with a private key, thereby identifying the source. • The message digest is decrypted using the sender’s public key. November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 77
Digital Signature • A digital signature is an electronic signature that can be used to authenticate the identity of the sender of a message or the signer of a document, and to ensure that the original content of the message or document that has been sent is unchanged. November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 78

Digital Signature • The sender uses an algorithm to compute a hash (garbled digest) of the document • Sender uses its private key to encrypt the hash. • Recipient uses same algorithm to hash the plain text document when received. • Recipient uses the public key to decrypt the digital signature and compare to the hash the recipient created, to confirm integrity. November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 79

Digital Signature • Construct that authenticated origin, contents of message in a manner provable to a disinterested third party (“judge”) • Sender cannot deny having sent message (service is “nonrepudiation”) – Limited to technical proofs • Inability to deny one’s cryptographic key was used to sign – One could claim the cryptographic key was stolen or compromised • Legal proofs, etc. , probably required; not dealt with here November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 80

Common Error • Classical: Alice, Bob share key k – Alice sends m || { m } k to Bob This is a digital signature WRONG This is not a digital signature – Why? Third party cannot determine whether Alice or Bob generated message November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 81
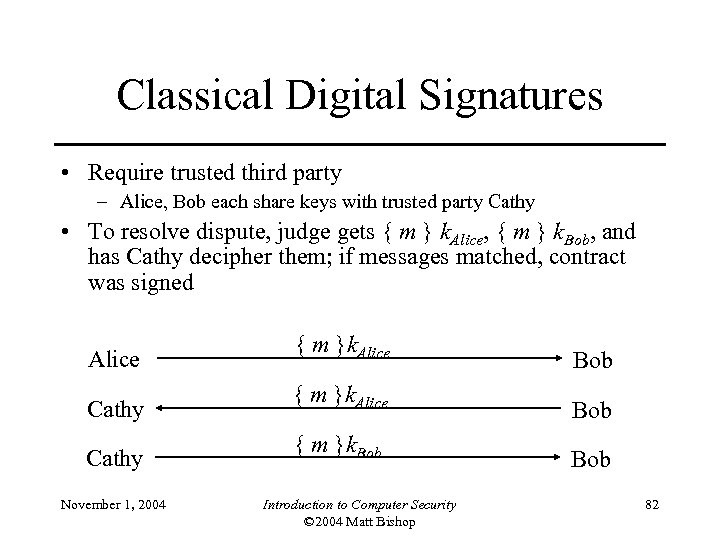
Classical Digital Signatures • Require trusted third party – Alice, Bob each share keys with trusted party Cathy • To resolve dispute, judge gets { m } k. Alice, { m } k. Bob, and has Cathy decipher them; if messages matched, contract was signed Alice { m }k. Alice Bob Cathy { m }k. Bob November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 82

RSA Digital Signatures • Use private key to encipher message – Protocol for use is critical • Key points: – Never sign random documents, and when signing, always sign hash and never document • Mathematical properties can be turned against signer – Sign message first, then encipher • Changing public keys causes forgery November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 83

Limitations and Conflicts • Cannot prevent file deletion • Limits the functions of firewalls and antivirus software • Encrypted email still not popular because of the need for common software November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 84
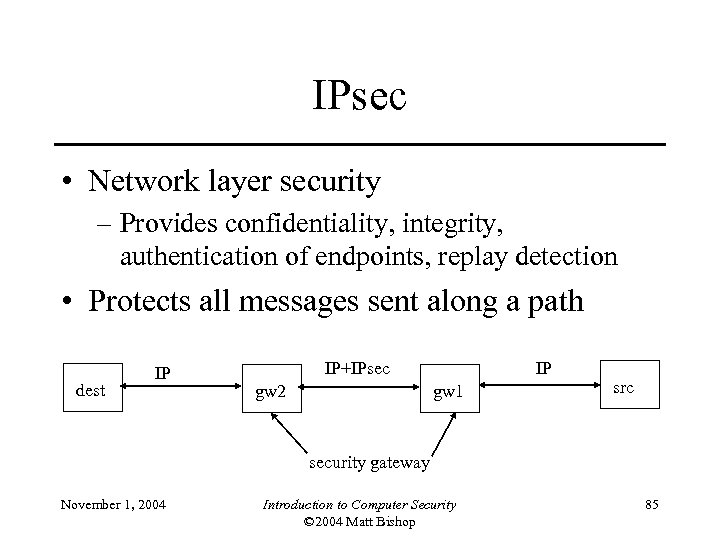
IPsec • Network layer security – Provides confidentiality, integrity, authentication of endpoints, replay detection • Protects all messages sent along a path dest IP IP+IPsec gw 2 IP gw 1 src security gateway November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 85

IPsec Protocols • Authentication Header (AH) – Message integrity – Origin authentication – Anti-replay • Encapsulating Security Payload (ESP) – Confidentiality – Others provided by AH November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 86
IPsec Architecture • Security Policy Database (SPD) – Says how to handle messages (discard them, add security services, forward message unchanged) – SPD associated with network interface – SPD determines appropriate entry from packet attributes • Including source, destination, transport protocol November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 87

IPsec Architecture • Packet arrives • Look in SPD – Find appropriate entry – Get dest address, security protocol, SPI • Find associated SA in SAD – Use dest address, security protocol, SPI – Apply security services in SA (if any) November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 88
Which to Use: PEM, IPsec • What do the security services apply to? – If applicable to one application and application layer mechanisms available, use that • PEM for electronic mail – If more generic services needed, look to lower layers • IPsec for network layer, either end-to-end or link mechanisms, for connectionless channels as well as connections – If endpoint is host, IPsec sufficient; if endpoint is user, application layer mechanism such as PEM needed November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 89

Key Points • Key management critical to effective use of cryptosystems – Different levels of keys (session vs. interchange) • Keys need infrastructure to identify holders, allow revoking – Key escrowing complicates infrastructure • Digital signatures provide integrity of origin and content Much easier with public key cryptosystems than with classical cryptosystems November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop 90
5dd07aa150f7034f468196bb010d83d1.ppt