759c7da95016566e5bc54c19fa2ad77a.ppt
- Количество слайдов: 16

Enabling Grids for E-scienc. E Status update on suexec, WSS, LCMAPS Martijn Steenbakkers for JRA 3 University of Amsterdam, NIKHEF www. eu-egee. org INFSO-RI-508833

Outline Enabling Grids for E-scienc. E • Isolation (sandboxing) – – – Work. Space Service (WSS) and LCMAPS suexec wrapper program How does this fit in the g. Lite CE? Implementation status Issues/todo • (Local) authorization – Policy Decision Points (PDPs) • Timeline • Next talk by Oscar: Job Repository (auditing) INFSO-RI-508833 All hands meeting, Brno, 20 -22 June 2005 2
Isolation (sandboxing) Enabling Grids for E-scienc. E • Roadmap – virtualization of resources (VM) or assigning of local credentials – should be indistinguishable from ‘outside’ • EGEE Architecture – – – only based on credential mapping do as little as possible with ‘root’ privileges: suexec minimizing local management: poolaccounts & poolgroups credential mapping and manipulation: LCMAPS management capabilities on these accounts: Work. Space Service (WSS) INFSO-RI-508833 All hands meeting, Brno, 20 -22 June 2005 5

Workspace Service and LCMAPS Enabling Grids for E-scienc. E Workspace Service (WSS) is part of GT 4 -core and in g. Lite-1 (preview) – Account creation and account management • Provides lifetime management and will provide quota management • Account clean-up mechanism: – Possibility to put account in quarantine first – Example clean-up script provided • Access control to Workspace Service based on DN and VOMS attr. • Access control to account – Currently based on DN – Will provide ACLs on VOMS attributes (? ) • Support of poolaccounts – Clean-up of poolaccounts – Uses LCMAPS as a back-end to manage gridmapdir (poolindex) INFSO-RI-508833 All hands meeting, Brno, 20 -22 June 2005 6
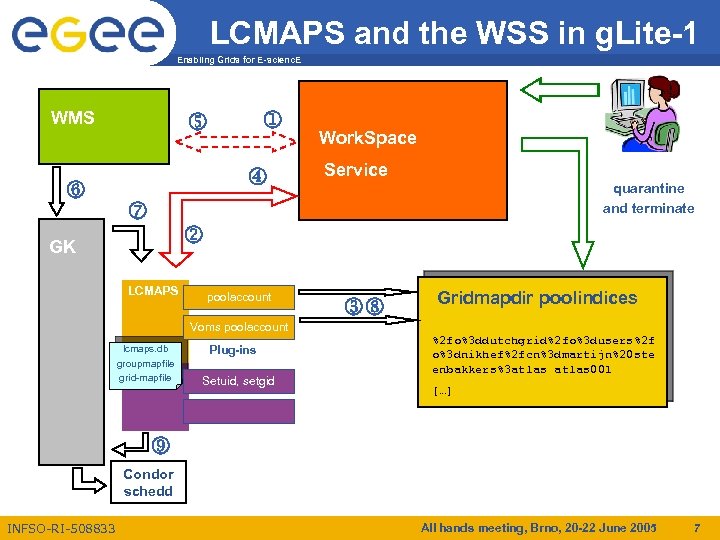
LCMAPS Workspace Service and the WSS in g. Lite-1 Enabling Grids for E-scienc. E WMS o j n Work. Space m p Service poolaccount lq quarantine and terminate k GK LCMAPS Voms poolaccount lcmaps. db groupmapfile grid-mapfile Plug-ins Setuid, setgid Gridmapdir poolindices %2 fo%3 ddutchgrid%2 fo%3 dusers%2 f o%3 dnikhef%2 fcn%3 dmartijn%20 ste enbakkers%3 atlas 001 […] r Condor schedd INFSO-RI-508833 All hands meeting, Brno, 20 -22 June 2005 7

suexec wrapper Enabling Grids for E-scienc. E Thin layer with root privileges will replace gatekeeper • Intended for identity-switching services: – condor, gridsite, globus gram, cream. • Internal – Uses LCMAPS/Workspace service as credential mapping mechanism – Executes the requested command with local credentials • External interface – Should be usable by C, java (, perl? ) services: program executable. – A (user) credential should be passed to suexec. – In- and outgoing pipes, file descriptors should be preserved as much as possible. INFSO-RI-508833 All hands meeting, Brno, 20 -22 June 2005 8
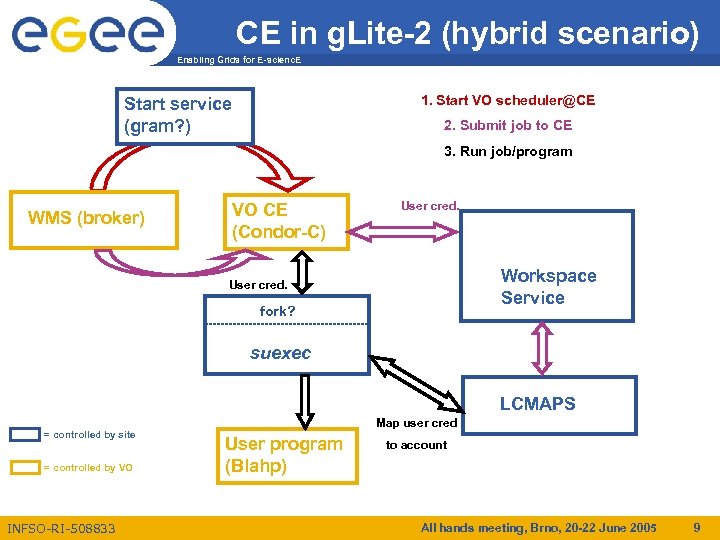
CE in g. Lite-2 (hybrid scenario) Enabling Grids for E-scienc. E 1. Start VO scheduler@CE Start service (gram? ) 2. Submit job to CE 3. Run job/program WMS (broker) VO CE (Condor-C) User cred. Workspace Service User cred. fork? suexec LCMAPS = controlled by site = controlled by VO INFSO-RI-508833 Map user cred User program (Blahp) to account All hands meeting, Brno, 20 -22 June 2005 9
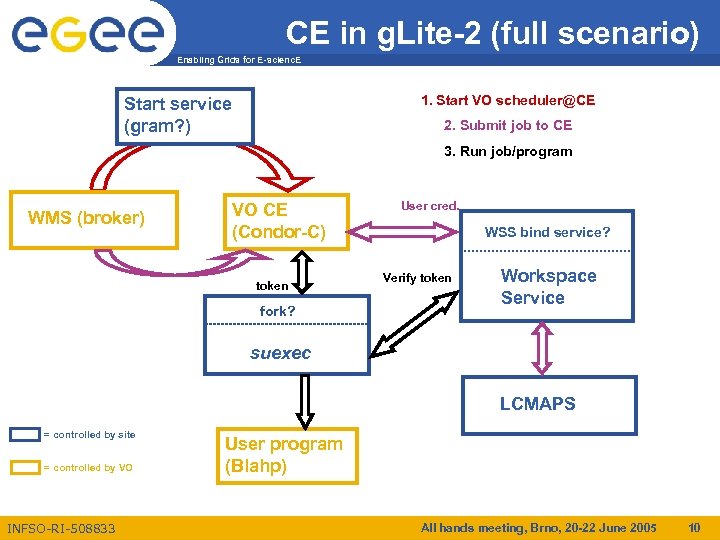
CE in g. Lite-2 (full scenario) Enabling Grids for E-scienc. E 1. Start VO scheduler@CE Start service (gram? ) 2. Submit job to CE 3. Run job/program WMS (broker) VO CE (Condor-C) token fork? User cred. WSS bind service? Verify token Workspace Service suexec LCMAPS = controlled by site = controlled by VO INFSO-RI-508833 User program (Blahp) All hands meeting, Brno, 20 -22 June 2005 10

suexec implementation (1) Enabling Grids for E-scienc. E • Started from apache su. EXEC – Safe code, has proven itself – Works with apache (gridsite) • Input parameters: – Hybrid scenario: Environment variable with location of proxy (PEM-encoded) – Full scenario: Attribute certificate from WSS bind service. – Environment variable with mapcounter (to support multiple mappings per set of credentials) – Optional: the uid and gid to run the executable. INFSO-RI-508833 All hands meeting, Brno, 20 -22 June 2005 11
suexec implementation (2) Enabling Grids for E-scienc. E • Two run-modes depending on setuid bit settings: – suexec is setuid-root: setuid()/setgid() to local user in suexec code and execute the program -r-s--x--- 1 root apache /usr/sbin/gsuexec – suexec runs as special user: suexec uses sudo for identity switching and program execution: -r-s--x--- 1 gsuexec /opt/glite/sbin/gsuexec § sudo preserves only stdin, stdout, stderr § sudo can be configured to allow the user “gsuexec” to run a predefined set of programs (blahpd, qsub) INFSO-RI-508833 All hands meeting, Brno, 20 -22 June 2005 12

Todo/issues (1) Enabling Grids for E-scienc. E Suexec • callout to lcmaps (almost ready, Hybrid scenario) • • Allow suexec only to run programs from a list: /usr/bin/sudo, …? Where should the fork() go? – Can create (small) C client wrapper lib that does the fork. – Needed for Java as well? Need to chdir() to home directory? Need to chown() files (user proxy)? • • Integration on the g. Lite prototype with Condor, (Cream? ) • • callout to the WSS (Full scenario). Use as a backend for gt 4 GRAM? INFSO-RI-508833 All hands meeting, Brno, 20 -22 June 2005 13
Todo/issues (2) Enabling Grids for E-scienc. E • Workspace service – Multiple account mapping support (ready, released today? ) – Ban list (soon) – WSS bind service (NIKHEF can help) § ‘Proves’ that the caller of suexec is entitled to use the account – Callout to auth. Z service (SAML) • LCMAPS – Working on PEM interface (almost ready) – Verify proxy (including full/limited proxy check) – Not directly related to suexec (see DM security model): § dual certificate support § Plug into new globus gridftp server using standard GSI auth. Z callouts. INFSO-RI-508833 All hands meeting, Brno, 20 -22 June 2005 14

Local Authorization Enabling Grids for E-scienc. E • Roadmap – – – all assertions carried as SAML statements all local (and global) policies expressed in XACML separate authorization service using standard protocols site policy, AND-ed with user and VO policy, evaluated together policy evaluation never requires special local privs (‘root’) • EGEE Architecture – – Authorization Framework (Java) and LCAS (C/C++ world) both provide set of PDPs Authorization Service via OGSA-Auth. Z-WG spec (EGEE-2) PDPs: user white/blacklist, VOMS-ACL, Proxy-lifetime, Limited proxy (OID) checks, peer-system name validation, central CRL checking INFSO-RI-508833 All hands meeting, Brno, 20 -22 June 2005 15

Local Authorization - PDPs Enabling Grids for E-scienc. E • Policy Decision Points (PDPs): – VOMS-ACL: Java auth. Z framework – proxy lifetime check: C + Java § SAAARG requirement 1. 4. 1. 1 for proxies – Limited proxy check: C + Java § Decides to accept limited proxies or not § Old (gt 2) style proxies: DN contains “CN=limited proxy” § RFC 3820 proxies: check proxy policy language OID (defined by globus) INFSO-RI-508833 All hands meeting, Brno, 20 -22 June 2005 16
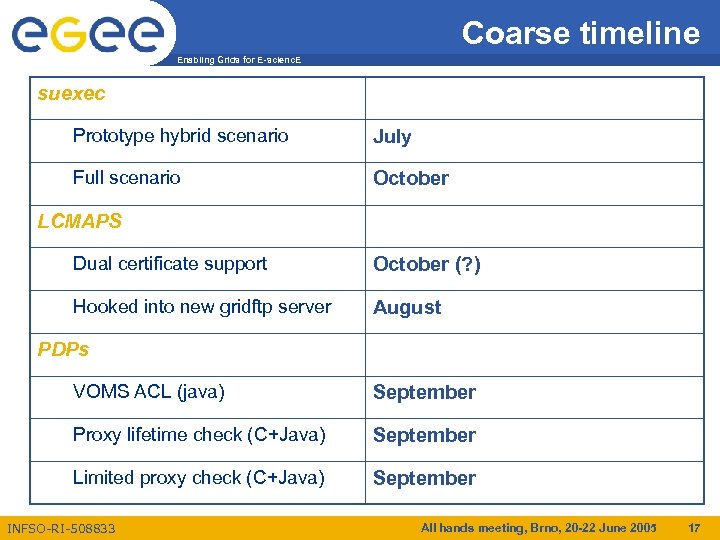
Coarse timeline Enabling Grids for E-scienc. E suexec Prototype hybrid scenario July Full scenario October LCMAPS Dual certificate support October (? ) Hooked into new gridftp server August PDPs VOMS ACL (java) September Proxy lifetime check (C+Java) September Limited proxy check (C+Java) September INFSO-RI-508833 All hands meeting, Brno, 20 -22 June 2005 17

References Enabling Grids for E-scienc. E LCMAPS and LCAS http: //www. nikhef. nl/grid/lcaslcmaps/ Work. Space Service http: //www-unix. mcs. anl. gov/workspace/ DJRA 3. 2 : Site Access Control Architecture https: //edms. cern. ch/document/523948/ INFSO-RI-508833 All hands meeting, Brno, 20 -22 June 2005 18
759c7da95016566e5bc54c19fa2ad77a.ppt