7a1c78e526545b60789a6f191db6bab6.ppt
- Количество слайдов: 37

Enabling Grids for E-scienc. E Security on g. Lite middleware Matthieu Reichstadt CNRS/IN 2 P 3 ACGRID School, Hanoi (Vietnam) November 5 th, 2007 Credits: Valeria Ardizzone, Jinny Chien, and other EGEE colleagues… www. eu-egee. org
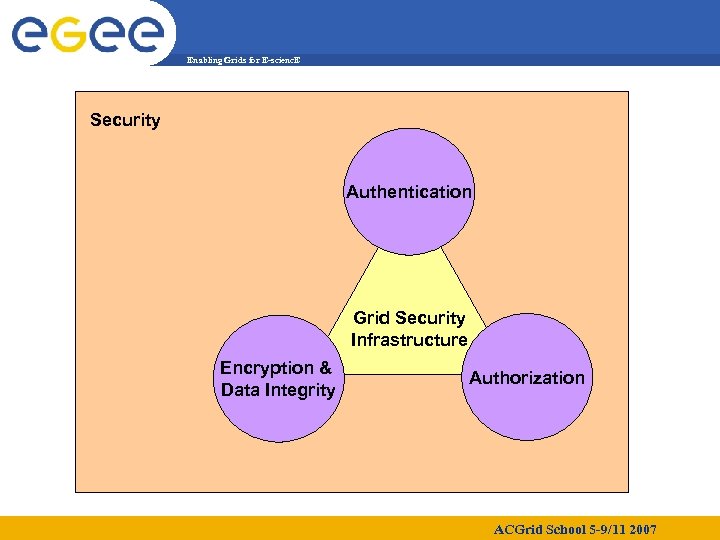
Enabling Grids for E-scienc. E Security Authentication Grid Security Infrastructure Encryption & Data Integrity Authorization ACGrid School 5 -9/11 2007

Overview Enabling Grids for E-scienc. E • Glossary • Encryption – Symmetric algorithms – Asymmetric algorithms: PKI • Certificates – Digital Signatures – X 509 certificates • Grid Security – Basic concepts – Grid Security Infrastructure – Proxy certificates – Command line interfaces • Virtual Organisation – Concept of VO and authorization – VOMS, LCAS, LCMAPS ACGrid School 5 -9/11 2007

Overview Enabling Grids for E-scienc. E • Glossary • Encryption – Symmetric algorithms – Asymmetric algorithms: PKI • Certificates – Digital Signatures – X 509 certificates • Grid Security – Basic concepts – Grid Security Infrastructure – Proxy certificates – Command line interfaces • Virtual Organisation – Concept of VO and authorization – VOMS, LCAS, LCMAPS ACGrid School 5 -9/11 2007

Glossary Enabling Grids for E-scienc. E • Principal – An entity: a user, a program, or a machine • Credentials – Some data providing a proof of identity • Authentication – Verify the identity of a principal • Authorization – Map an entity to some set of privileges • Confidentiality – Encrypt the message so that only the recipient can understand it • Integrity – Ensure that the message has not been altered in the transmission • Non-repudiation – Impossibility of denying the authenticity of a digital signature ACGrid School 5 -9/11 2007

Overview Enabling Grids for E-scienc. E • Glosary • Encryption – Symmetric algorithms – Asymmetric algorithms: PKI • Certificates – Digital Signatures – X 509 certificates • Grid Security – Basic concepts – Grid Security Infrastructure – Proxy certificates – Command line interfaces • Virtual Organisation – Concept of VO and authorization – VOMS, LCAS, LCMAPS ACGrid School 5 -9/11 2007
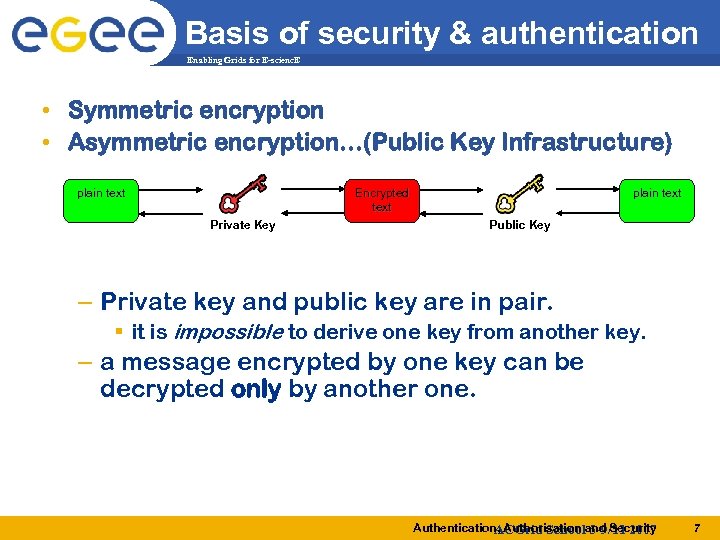
Basis of security & authentication Enabling Grids for E-scienc. E • Symmetric encryption • Asymmetric encryption…(Public Key Infrastructure) plain text Encrypted text Private Key Public Key – Private key and public key are in pair. it is impossible to derive one key from another key. – a message encrypted by one key can be decrypted only by another one. Authentication, Authorisation and Security ACGrid School 5 -9/11 2007 7
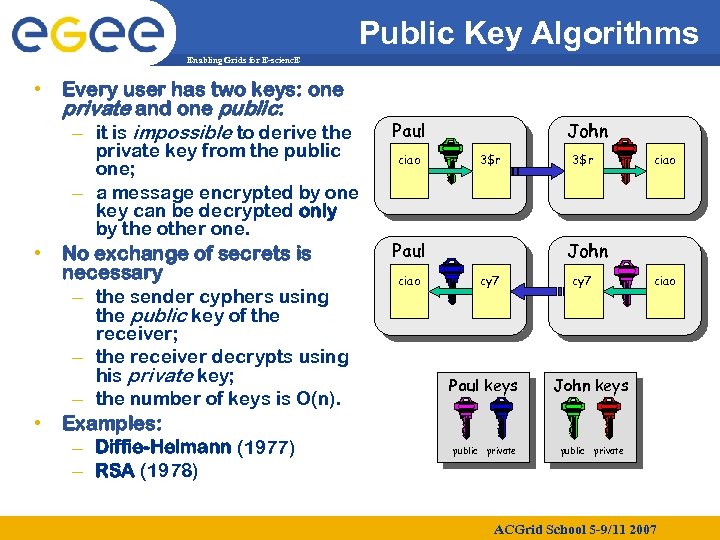
Public Key Algorithms Enabling Grids for E-scienc. E • Every user has two keys: one private and one public: – it is impossible to derive the private key from the public one; – a message encrypted by one key can be decrypted only by the other one. • No exchange of secrets is necessary – the sender cyphers using the public key of the receiver; – the receiver decrypts using his private key; – the number of keys is O(n). • Examples: – Diffie-Helmann (1977) – RSA (1978) Paul ciao John 3$r Paul ciao 3$r ciao John cy 7 Paul keys John keys public private ciao public private ACGrid School 5 -9/11 2007
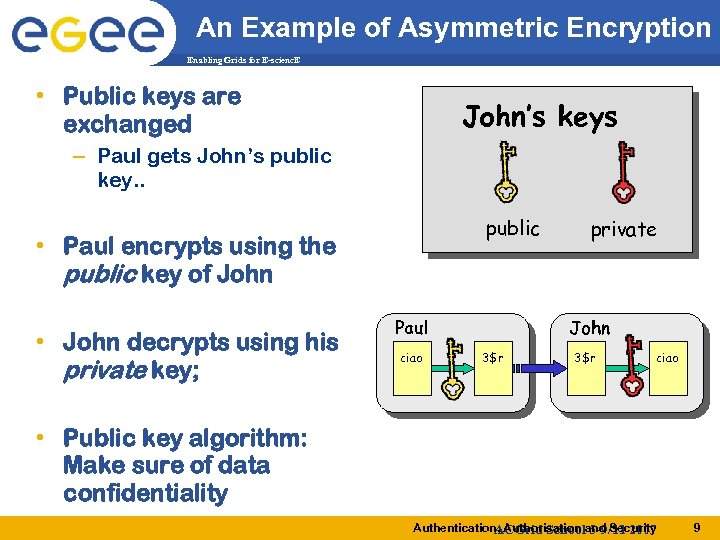
An Example of Asymmetric Encryption Enabling Grids for E-scienc. E • Public keys are exchanged John’s keys – Paul gets John’s public key. . public • Paul encrypts using the public key of John • John decrypts using his private key; Paul ciao private John 3$r ciao • Public key algorithm: Make sure of data confidentiality Authentication, Authorisation and Security ACGrid School 5 -9/11 2007 9

Overview Enabling Grids for E-scienc. E • Glossary • Encryption – Symmetric algorithms – Asymmetric algorithms: PKI • Certificates – Digital Signatures – X 509 certificates • Grid Security – Basic concepts – Grid Security Infrastructure – Proxy certificates – Command line interfaces • Virtual Organisation – Concept of VO and authorization – VOMS, LCAS, LCMAPS ACGrid School 5 -9/11 2007
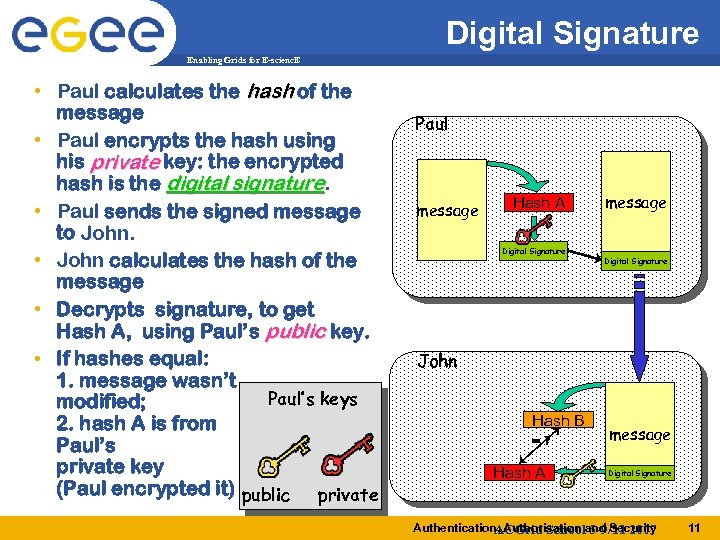
Digital Signature Enabling Grids for E-scienc. E • Paul calculates the hash of the message • Paul encrypts the hash using his private key: the encrypted hash is the digital signature. • Paul sends the signed message to John. • John calculates the hash of the message • Decrypts signature, to get Hash A, using Paul’s public key. • If hashes equal: 1. message wasn’t Paul’s keys modified; 2. hash A is from Paul’s private key (Paul encrypted it) public private Paul message Hash A Digital Signature message Digital Signature John Hash B =? Hash A message Digital Signature Authentication, Authorisation and Security ACGrid School 5 -9/11 2007 11

Digital Certificates Enabling Grids for E-scienc. E • Paul’s digital signature is safe if: 1. 2. • Paul’s private key is not compromised John knows Paul’s public key How can John be sure that Paul’s public key is really Paul’s public key and not someone else’s? – A third party guarantees the correspondence between public key and owner’s identity. – Both A and B must trust this third party • Two models: – X. 509: hierarchical organization; – PGP: “web of trust”. ACGrid School 5 -9/11 2007

X. 509 Enabling Grids for E-scienc. E The “third party” is called Certification Authority (CA). • Issue Digital Certificates for users, programs and machines • Check the identity and the personal data of the requestor – Registration Authorities (RAs) do the actual validation • CA’s periodically publish a list of compromised certificates – Certificate Revocation Lists (CRL): contain all the revoked certificates yet to expire • CA certificates are self-signed ACGrid School 5 -9/11 2007
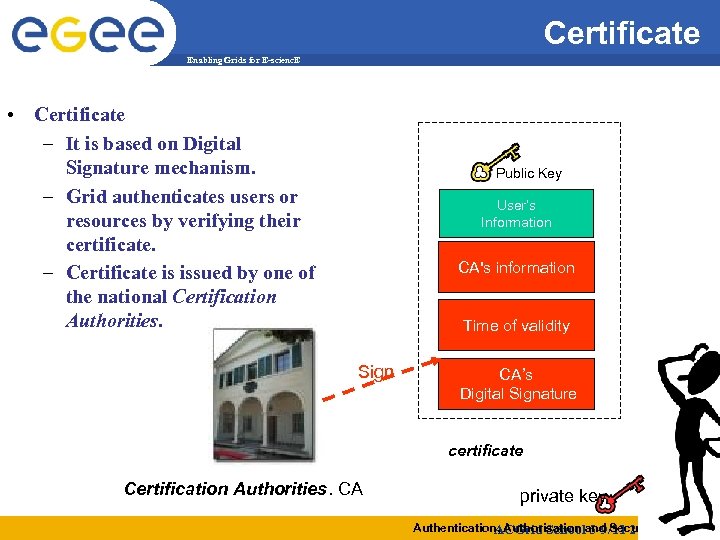
Certificate Enabling Grids for E-scienc. E • Certificate – It is based on Digital Signature mechanism. – Grid authenticates users or resources by verifying their certificate. – Certificate is issued by one of the national Certification Authorities. Public Key User’s Information CA's information Time of validity Sign CA’s Digital Signature certificate Certification Authorities. CA private key Authentication, Authorisation and Security ACGrid School 5 -9/11 2007 14
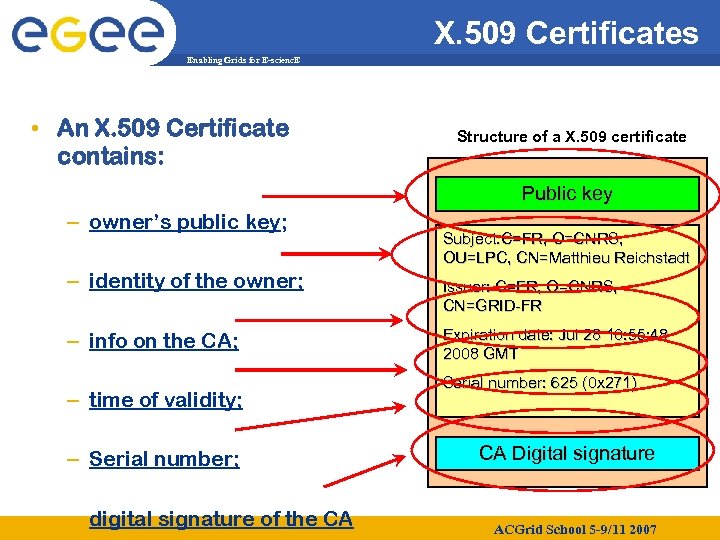
X. 509 Certificates Enabling Grids for E-scienc. E • An X. 509 Certificate contains: Structure of a X. 509 certificate Public key – owner’s public key; – identity of the owner; – info on the CA; – time of validity; – Serial number; – digital signature of the CA Subject: C=FR, O=CNRS, OU=LPC, CN=Matthieu Reichstadt Issuer: C=FR, O=CNRS, CN=GRID-FR Expiration date: Jul 28 10: 55: 48 2008 GMT Serial number: 625 (0 x 271) CA Digital signature ACGrid School 5 -9/11 2007
![Example of X. 509 certificate Enabling Grids for E-scienc. E [reichma@clrlcgui 01 reichma]$ grid-cert-info Example of X. 509 certificate Enabling Grids for E-scienc. E [reichma@clrlcgui 01 reichma]$ grid-cert-info](https://present5.com/presentation/7a1c78e526545b60789a6f191db6bab6/image-16.jpg)
Example of X. 509 certificate Enabling Grids for E-scienc. E [reichma@clrlcgui 01 reichma]$ grid-cert-info Certificate: Data: Version: 3 (0 x 2) Serial Number: 2360 (0 x 938) Signature Algorithm: sha 1 With. RSAEncryption Issuer: C=FR, O=CNRS, CN=GRID-FR Validity Not Before: Jul 24 08: 55: 48 2007 GMT Not After : Jul 24 08: 55: 48 2008 GMT Subject: O=GRID-FR, C=FR, O=CNRS, OU=LPC, CN=Matthieu Reichstadt Subject Public Key Info: Public Key Algorithm: rsa. Encryption RSA Public Key: (1024 bit). . . . ACGrid School 5 -9/11 2007

Overview Enabling Grids for E-scienc. E • Glossary • Encryption – Symmetric algorithms – Asymmetric algorithms: PKI • Certificates – Digital Signatures – X 509 certificates • Grid Security – Basic concepts – Grid Security Infrastructure – Proxy certificates – Command line interfaces • Virtual Organisation – Concept of VO and authorization – VOMS, LCAS, LCMAPS ACGrid School 5 -9/11 2007

More on CA’s Enabling Grids for E-scienc. E • In the grid world one single CA usually covers a predefined geographic region or administrative domain: – Organization – Country – A set of countries • A common trust domain for grid computing has been created to join the several existing certification authorities into a single authentication domain and thus enabling sharing of grid resources worldwide. – The International Grid Trust Federation (IGTF) has been created to coordinate and manage this trust domain. – IGTF is divided in three Policy Management Authorities (PMAs) covering the Asia Pacific, Europe and Americas. ACGrid School 5 -9/11 2007
Classic Profile of a CA : RA Enabling Grids for E-scienc. E ACGrid School 5 -9/11 2007
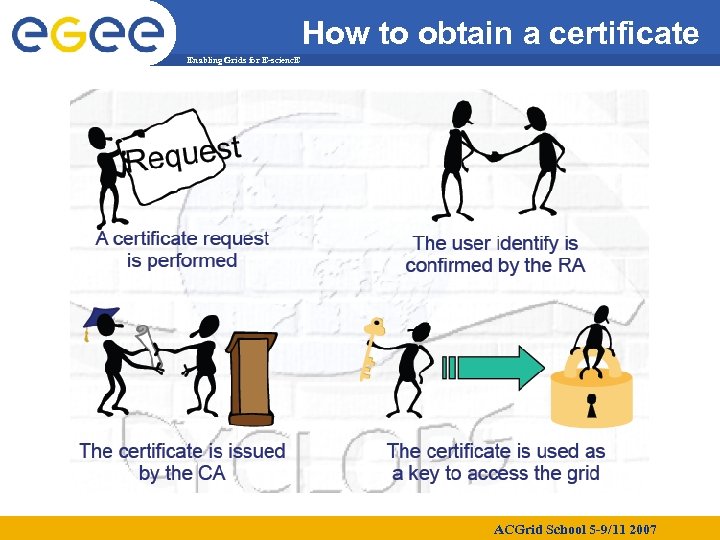
How to obtain a certificate Enabling Grids for E-scienc. E ACGrid School 5 -9/11 2007
Certificate Management Enabling Grids for E-scienc. E • Import your certificate in your browser – If you received a. pem certificate you need to convert it to PKCS 12 – Use openssl command line (available in each egee/LCG UI) openssl pkcs 12 –export –in usercert. pem –inkey userkey. pem –out my_cert. p 12 –name ’My Name’ • Most of other CA’s: – You receive already a PKCS 12 certificate (can import it directly into the web browser) – For future use, you will need usercert. pem and userkey. pem in a directory ~/. globus on your UI – Export the PKCS 12 cert to a local dir on UI and use again openssl: openssl pkcs 12 -nocerts -in my_cert. p 12 -out userkey. pem openssl pkcs 12 -clcerts -nokeys -in my_cert. p 12 -out usercert. pem ACGrid School 5 -9/11 2007

X. 509 Proxy Certificate Enabling Grids for E-scienc. E • • • GSI extension to X. 509 Identity Certificates – signed by the normal end entity cert (or by another proxy). Enables single sign-on Support some important features – Delegation – Mutual authentication Has a limited lifetime (minimized risk of “compromised credentials”) It is created by the grid-proxy-init command: % grid-proxy-init Enter PEM pass phrase: ****** – Options for grid-proxy-init: -hours <lifetime of credential> -bits <length of key> -help ACGrid School 5 -9/11 2007
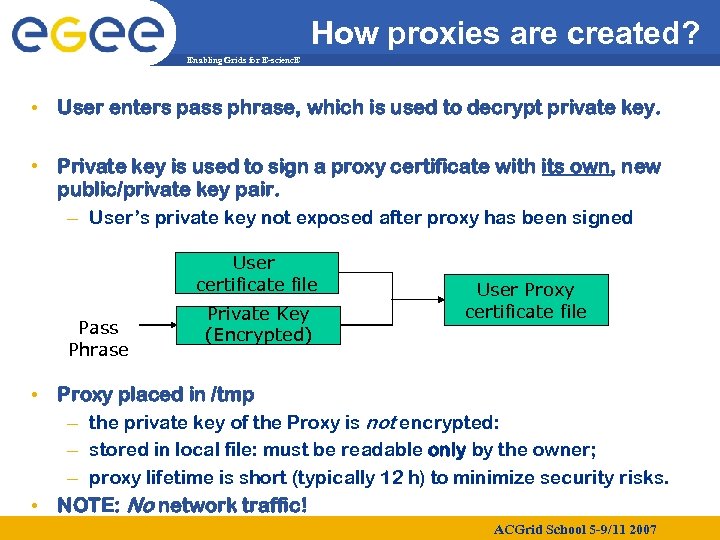
How proxies are created? Enabling Grids for E-scienc. E • User enters pass phrase, which is used to decrypt private key. • Private key is used to sign a proxy certificate with its own, new public/private key pair. – User’s private key not exposed after proxy has been signed User certificate file Pass Phrase Private Key (Encrypted) User Proxy certificate file • Proxy placed in /tmp – the private key of the Proxy is not encrypted: – stored in local file: must be readable only by the owner; – proxy lifetime is short (typically 12 h) to minimize security risks. • NOTE: No network traffic! ACGrid School 5 -9/11 2007

Proxy again … Enabling Grids for E-scienc. E • VOMS: Virtual Organization Membership Service • voms-proxy-init ≡ “login to the Grid” • To “logout” you have to destroy your proxy: – voms-proxy-destroy – This does NOT destroy any proxies that were delegated from this proxy. – You cannot revoke a remote proxy – Usually create proxies with short lifetimes • To gather information about your proxy: – voms-proxy-info – Options for printing proxy information -subject -type -strength -issuer -timeleft -help ACGrid School 5 -9/11 2007
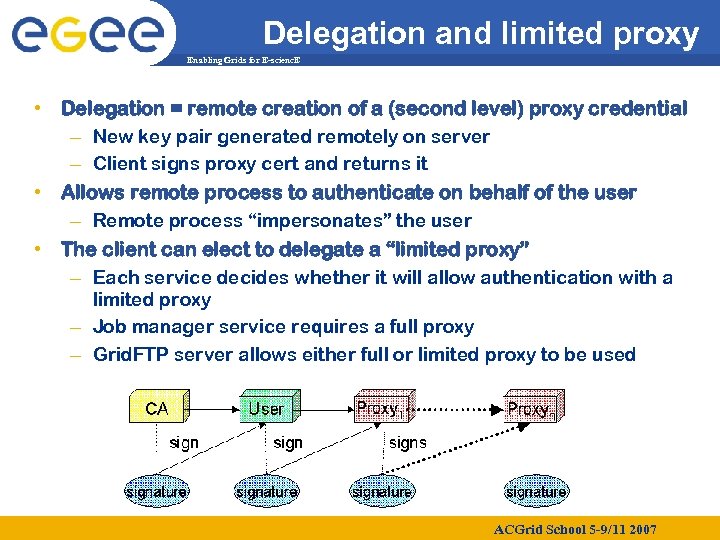
Delegation and limited proxy Enabling Grids for E-scienc. E • Delegation = remote creation of a (second level) proxy credential – New key pair generated remotely on server – Client signs proxy cert and returns it • Allows remote process to authenticate on behalf of the user – Remote process “impersonates” the user • The client can elect to delegate a “limited proxy” – Each service decides whether it will allow authentication with a limited proxy – Job manager service requires a full proxy – Grid. FTP server allows either full or limited proxy to be used ACGrid School 5 -9/11 2007

Long term proxy Enabling Grids for E-scienc. E • • • Proxy has limited lifetime (default is 12 h) – Bad idea to have longer proxy However, a grid task might need to use a proxy for a much longer time – Grid jobs in HEP Data Challenges on LCG last up to 2 days myproxy server: – Allows to create and store a long term proxy certificate: – myproxy-init -s <host_name> -s: <host_name> specifies the hostname of the myproxy server – myproxy-info Get information about stored long living proxy – myproxy-get-delegation Get a new proxy from the My. Proxy server • • – myproxy-destroy – Chech out the myproxy-xxx - - help option A dedicated service on the RB can renew automatically the proxy File transfer services in g. Lite validates user request and eventually renew proxies – contacting myproxy server ACGrid School 5 -9/11 2007

Overview Enabling Grids for E-scienc. E • Glossary • Encryption – Symmetric algorithms – Asymmetric algorithms: PKI • Certificates – Digital Signatures – X 509 certificates • Grid Security – Basic concepts – Grid Security Infrastructure – Proxy certificates – Command line interfaces • Virtual Organisation – Concept of VO and authorization – VOMS, LCAS, LCMAPS ACGrid School 5 -9/11 2007

Virtual Organizations and authorization Enabling Grids for E-scienc. E • Grid users MUST belong to virtual organizations – – What we previously called “groups” Sets of users belonging to a collaboration User must sign the usage guidelines for the VO You will be registered in the VO server (wait for notification) • Vos maintained a list of their members on a LDAP Server – The list is downloaded by grid machines to map user certificate subjects to local “pool” accounts. . . "/C=CH/O=CERN/OU=GRID/CN=Simone Campana 7461". dteam "/C=CH/O=CERN/OU=GRID/CN=Andrea Sciaba 8968". cms "/C=CH/O=CERN/OU=GRID/CN=Patricia Mendez Lorenzo-ALICE". alice. . . – Sites decide which vos to accept /etc/grid-security/grid-mapfile ACGrid School 5 -9/11 2007
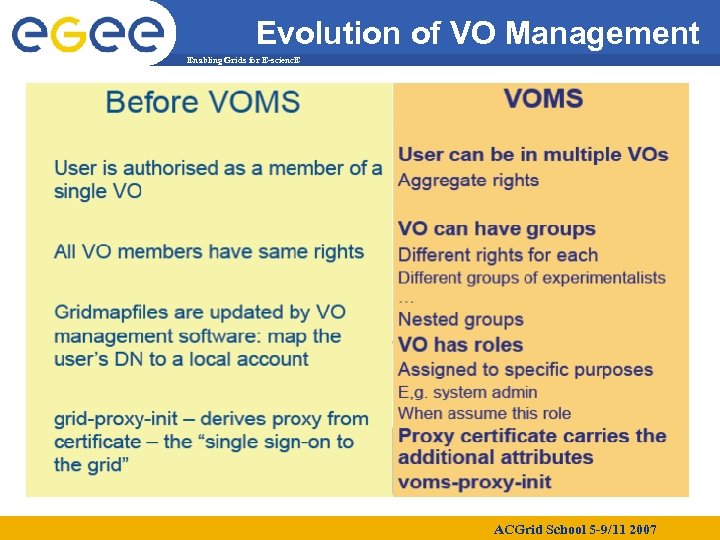
Evolution of VO Management Enabling Grids for E-scienc. E ACGrid School 5 -9/11 2007

The VOMS client Enabling Grids for E-scienc. E • Virtual Organization Membership Service – Extends the proxy with info on VO membership, group, roles – Fully compatible with Globus Toolkit – Each VO has a database containing group membership, roles and capabilities informations for each user – User contacts voms server requesting his authorization info – Server send authorization info to the client, which includes them in a proxy certificate [reichma@clrlcgui 01 repeat_install]$ voms-proxy-init --voms auvergrid: /Role=lcgadmin Your identity: /O=GRID-FR/C=FR/O=CNRS/OU=LPC/CN=Matthieu Reichstadt Enter GRID pass phrase: Creating temporary proxy. . . . . . Done Contacting cclcgvomsli 01. in 2 p 3. fr: 15002 [/O=GRID-FR/C=FR/O=CNRS/OU=CCLYON/CN=cclcgvomsli 01. in 2 p 3. fr] "auvergrid" Done Creating proxy. . . . Done Your proxy is valid until Thu Oct 4 01: 20: 51 2007 ACGrid School 5 -9/11 2007

FQAN and AC Enabling Grids for E-scienc. E • FQAN (Fully Qualified Attribute Name) is what VOMS uses to express membership and other authorization info • Groups membership, roles and capabilities may be expressed in a format that bounds them together <group>/Role=[<role>][/Capability=<capability>] [reichma@clrlcgui 01 repeat_install]$ voms-proxy-info -fqan /auvergrid/Role=lcgadmin/Capability=NULL /auvergrid/Role=NULL/Capability=NULL • FQAN are included in an Attribute Certificate (AC) • AC are used to bind a set of attributes (like membership, roles, authorization info etc) with an identity • AC are digitally signed • VOMS uses AC to include the attributes of a user in a proxy certificate ACGrid School 5 -9/11 2007
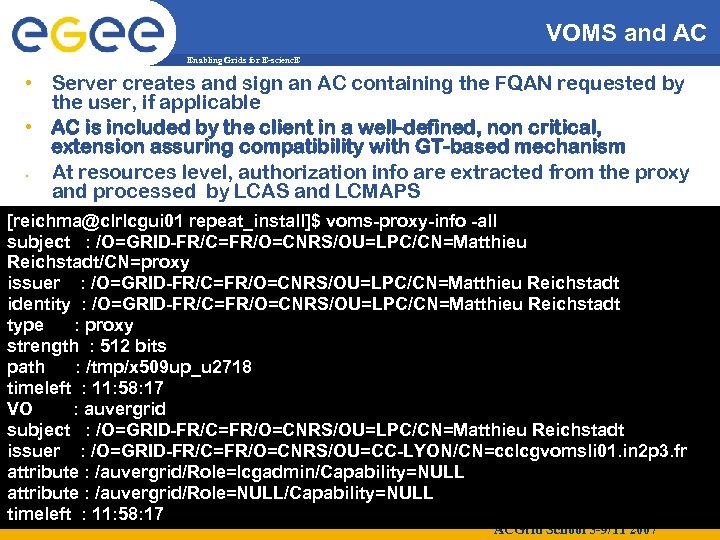
VOMS and AC Enabling Grids for E-scienc. E • Server creates and sign an AC containing the FQAN requested by the user, if applicable • AC is included by the client in a well-defined, non critical, extension assuring compatibility with GT-based mechanism • At resources level, authorization info are extracted from the proxy and processed by LCAS and LCMAPS [reichma@clrlcgui 01 repeat_install]$ voms-proxy-info -all subject : /O=GRID-FR/C=FR/O=CNRS/OU=LPC/CN=Matthieu Reichstadt/CN=proxy issuer : /O=GRID-FR/C=FR/O=CNRS/OU=LPC/CN=Matthieu Reichstadt identity : /O=GRID-FR/C=FR/O=CNRS/OU=LPC/CN=Matthieu Reichstadt type : proxy strength : 512 bits path : /tmp/x 509 up_u 2718 timeleft : 11: 58: 17 VO : auvergrid subject : /O=GRID-FR/C=FR/O=CNRS/OU=LPC/CN=Matthieu Reichstadt issuer : /O=GRID-FR/C=FR/O=CNRS/OU=CC-LYON/CN=cclcgvomsli 01. in 2 p 3. fr attribute : /auvergrid/Role=lcgadmin/Capability=NULL attribute : /auvergrid/Role=NULL/Capability=NULL timeleft : 11: 58: 17 ACGrid School 5 -9/11 2007

Roles Enabling Grids for E-scienc. E • Roles are specific roles a user has and that distinguishes him from others in his group: – Software manager – VO-Administrator • Difference between roles and groups: – Roles have no hierarchical structure – there is no sub-role – Roles are not used in ‘normal operation’ They are not added to the proxy by default when running voms-proxyinit But they can be added to the proxy for special purposes when running voms-proxy-init • Example: – User Reuillon has the following membership VO=auvergrid, Role=Software. Manager – During normal operation the role is not taken into account, e. g. Reuillon can work as a normal user – For special things he can obtain the role “Software Manager” ACGrid School 5 -9/11 2007

LCAS & LCMAPS Enabling Grids for E-scienc. E At resources level, authorization info are extracted from the proxy and processed by LCAS and LCMAPS • Local Centre Authorization Service (LCAS) – Checks if the user is authorized (currently using the grid-mapfile) – Checks if the user is banned at the site – Checks if at that time the site accepts jobs • Local Credential Mapping Service (LCMAPS) – Maps grid credentials to local credentials (eg. UNIX uid/gid, AFS tokens, etc. ) – Map also VOMS group and roles (full support of FQAN) "/VO=biomed/GROUP=/biomed" "/VO=biomed/GROUP=/biomed/prod/ROLE=manager" . biomedprodman ACGrid School 5 -9/11 2007
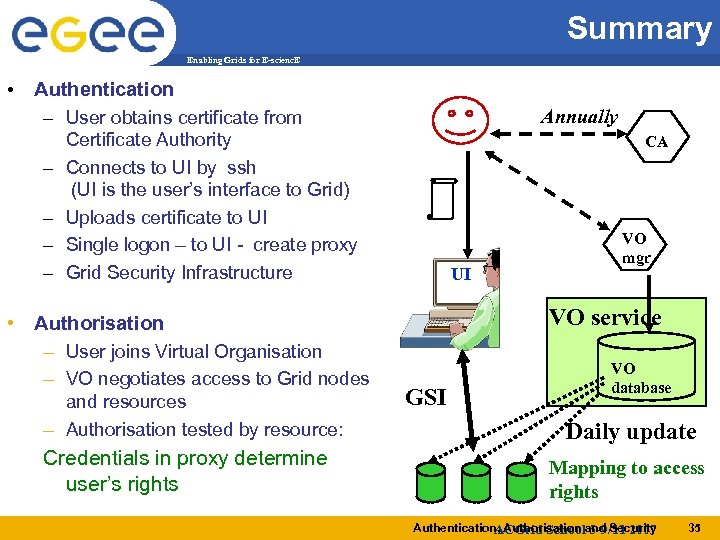
Summary Enabling Grids for E-scienc. E • Authentication – User obtains certificate from – – Annually Certificate Authority Connects to UI by ssh (UI is the user’s interface to Grid) Uploads certificate to UI Single logon – to UI - create proxy Grid Security Infrastructure • Authorisation – User joins Virtual Organisation – VO negotiates access to Grid nodes and resources – Authorisation tested by resource: Credentials in proxy determine user’s rights CA UI VO mgr VO service GSI VO database Daily update Mapping to access rights Authentication, Authorisation and Security ACGrid School 5 -9/11 2007 35
User Responsibilities Enabling Grids for E-scienc. E • Keep your private key secure – on USB drive only • Do not loan your certificate to anyone. • Report to your local/regional contact if your certificate has been compromised. • Do not launch a delegation service for longer than your current task needs. If your certificate or delegated service is used by someone other than you, it cannot be proven that it was not you. ACGrid School 5 -9/11 2007

Enabling Grids for E-scienc. E Thank you ACGrid School 5 -9/11 2007
7a1c78e526545b60789a6f191db6bab6.ppt