05bedce0f5395ff5d79c031f568f78f3.ppt
- Количество слайдов: 45

Enabling Grids for E-scienc. E Grid Security Tutorial 2006 David Groep NIKHEF www. eu-egee. org INFSO-RI-508833

Grid Security Tutorial Enabling Grids for E-scienc. E • You and the Grid – organising collaborations in virtual organisations – trust and your identity – cryptography and signing • Getting access to resources – attribute-based authorization and VOMS – proxies, delegation, forwarding and renewal • How it works in practice: grid security commands – – getting your certificate the GSI protocol getting a voms-enabled proxy what happens on the server side INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 2
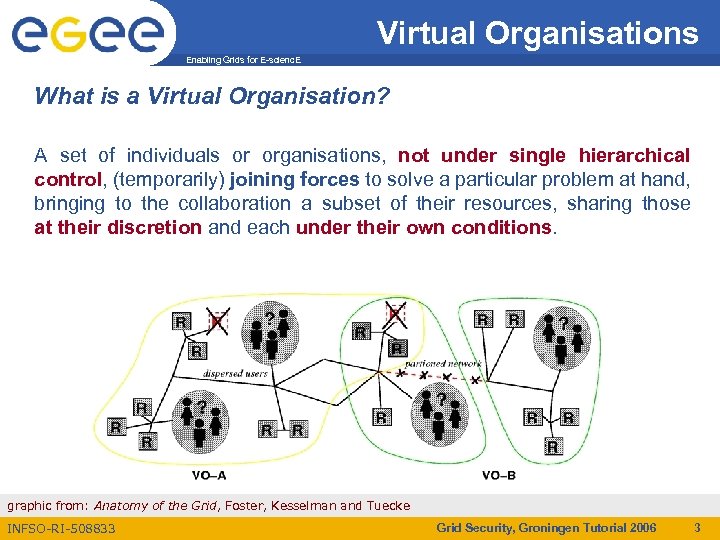
Virtual Organisations Enabling Grids for E-scienc. E What is a Virtual Organisation? A set of individuals or organisations, not under single hierarchical control, (temporarily) joining forces to solve a particular problem at hand, bringing to the collaboration a subset of their resources, sharing those at their discretion and each under their own conditions. graphic from: Anatomy of the Grid, Foster, Kesselman and Tuecke INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 3

VOs Enabling Grids for E-scienc. E Typical VO examples • Each of the VL-e application sub programmes • Collaborations like the LHC experiments, or LOFAR, or … • testing/deployment groups like “pvier” • … • Users (you) are usually a member of more than one VO • Any “large” VO will have an internal structure, with groups, subgroups, and various roles INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 4
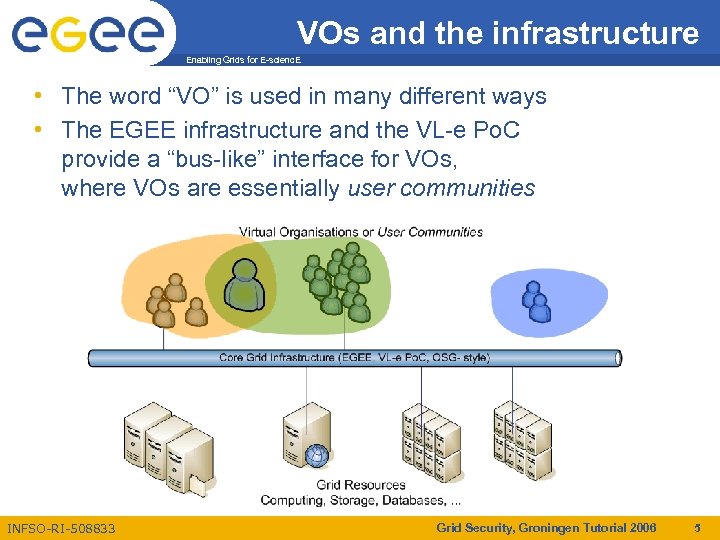
VOs and the infrastructure Enabling Grids for E-scienc. E • The word “VO” is used in many different ways • The EGEE infrastructure and the VL-e Po. C provide a “bus-like” interface for VOs, where VOs are essentially user communities INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 5
VOs Enabling Grids for E-scienc. E INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 6
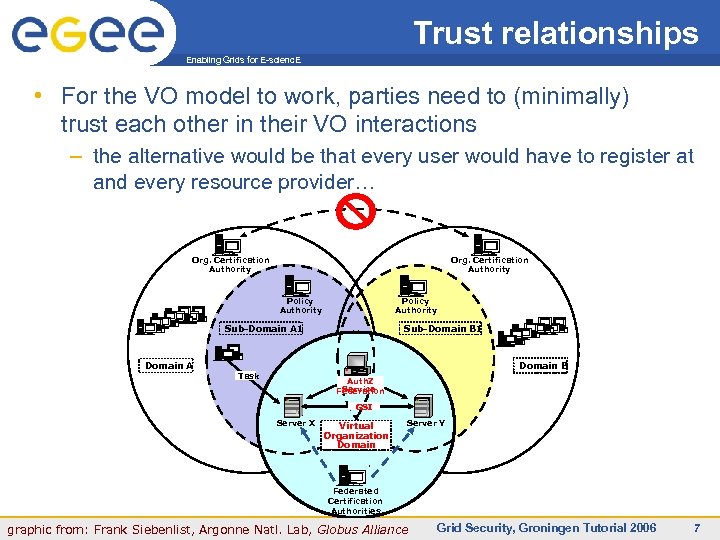
Trust relationships Enabling Grids for E-scienc. E • For the VO model to work, parties need to (minimally) trust each other in their VO interactions – the alternative would be that every user would have to register at and every resource provider… Org. Certification Authority Policy Authority Sub-Domain B 1 Sub-Domain A 1 Domain A Domain B Task Auth. Z Service Federation GSI Server X Virtual Organization Domain Server Y Federated Certification Authorities INFSO-RI-508833 Siebenlist, Argonne Natl. Lab, Globus Alliance graphic from: Frank Grid Security, Groningen Tutorial 2006 7
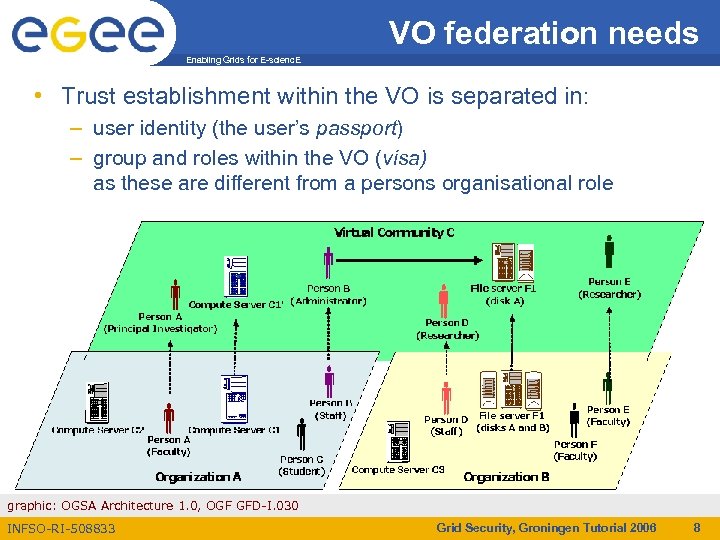
VO federation needs Enabling Grids for E-scienc. E • Trust establishment within the VO is separated in: – user identity (the user’s passport) – group and roles within the VO (visa) as these are different from a persons organisational role graphic: OGSA Architecture 1. 0, OGF GFD-I. 030 INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 8

User Identity Enabling Grids for E-scienc. E • Users and resources are typically part of more than one VO, • but don’t want many passwords • Users and resource get a single authentication token (identity certificate) – that works across virtual organisations – issued by a party trusted by all (“CA”), – recognised by many resource providers, users, and VOs – satisfy traceability and persistency requirement – in itself does not grant any access, but provides a unique binding between an identifier and the subject • This is called your (identity) certificate • It is a cryptographically protected statement by the CA • that you can use to prove your identity in combination with a private key and its passphrase INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 9
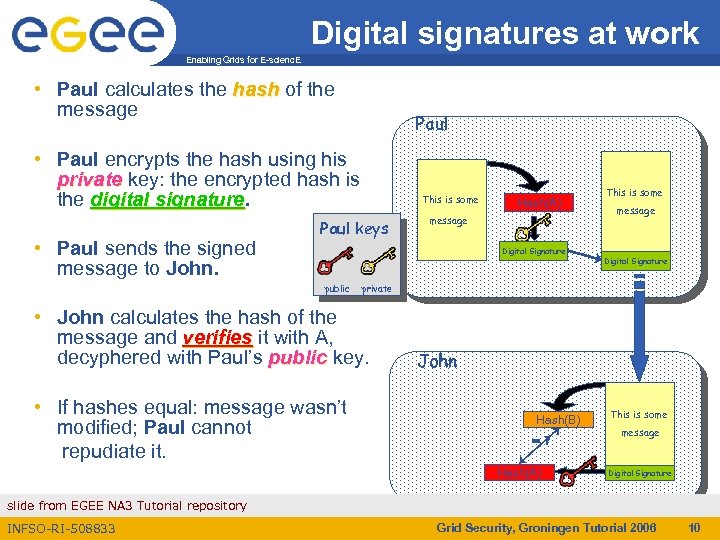
Digital signatures at work Enabling Grids for E-scienc. E • Paul calculates the hash of the message Paul • Paul encrypts the hash using his private key: the encrypted hash is the digital signature • Paul sends the signed message to John. This is some Paul keys Hash(A) message Digital Signature public message Digital Signature private • John calculates the hash of the message and verifies it with A, decyphered with Paul’s public key. • If hashes equal: message wasn’t modified; Paul cannot repudiate it. This is some John Hash(B) =? Hash(A) This is some message Digital Signature slide from EGEE NA 3 Tutorial repository INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 10

Trusting the signature Enabling Grids for E-scienc. E • Paul’s digital signature is safe if: 1. 2. Paul’s private key is not compromised John knows Paul’s public key • How can John be sure that Paul’s public key is really Paul’s public key and not someone else’s? – A third party guarantees the correspondence between public key and owner’s identity. – Both A and B must trust this third party slide from EGEE NA 3 Tutorial repository INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 11
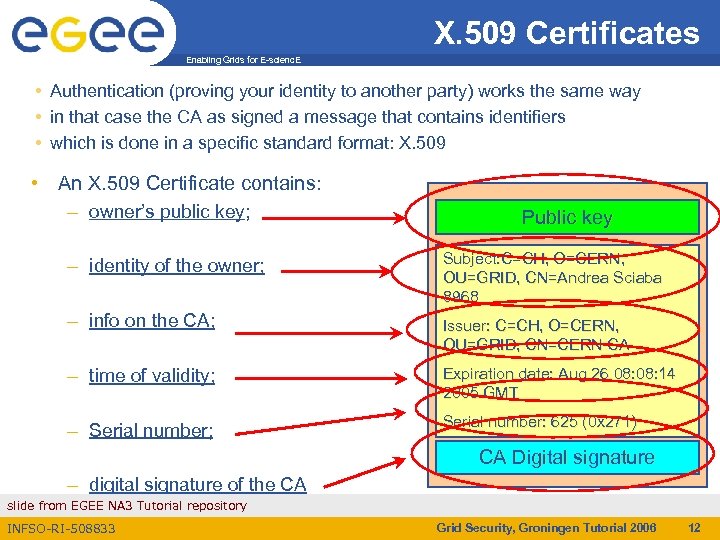
X. 509 Certificates Enabling Grids for E-scienc. E • Authentication (proving your identity to another party) works the same way • in that case the CA as signed a message that contains identifiers • which is done in a specific standard format: X. 509 • An X. 509 Certificate contains: – owner’s public key; Public key – identity of the owner; Subject: C=CH, O=CERN, OU=GRID, CN=Andrea Sciaba 8968 – info on the CA; Issuer: C=CH, O=CERN, OU=GRID, CN=CERN CA – time of validity; Expiration date: Aug 26 08: 14 2005 GMT – Serial number; Serial number: 625 (0 x 271) CA Digital signature – digital signature of the CA slide from EGEE NA 3 Tutorial repository INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 12
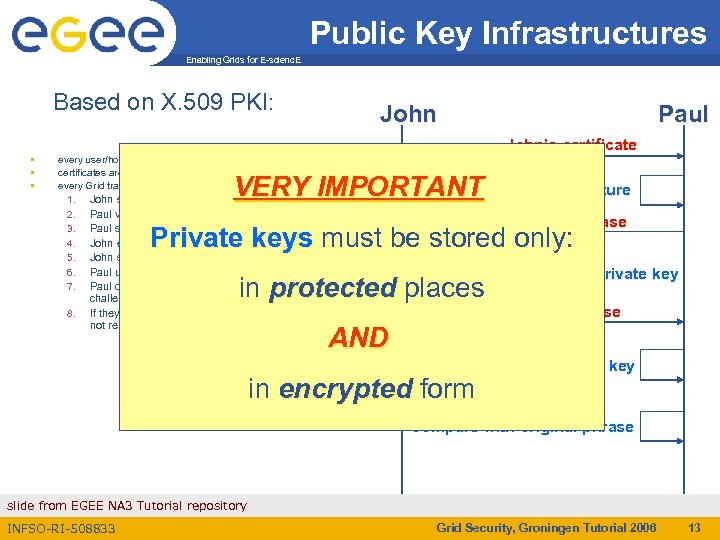
Public Key Infrastructures Enabling Grids for E-scienc. E Based on X. 509 PKI: • • • John every user/host/service has an X. 509 certificate; certificates are signed by trusted (by the local sites) CA’s; every Grid transaction is mutually authenticated: 1. John sends his certificate; 2. Paul verifies signature in John’s certificate; 3. Paul sends to John a challenge string; 4. John encrypts the challenge string with his private key; 5. John sends encrypted challenge to Paul 6. Paul uses John’s public key to decrypt the challenge. 7. Paul compares the decrypted string with the original Paul John’s certificate VERY IMPORTANTVerify CA signature Random phrase Private keys must be stored only: Encrypt with J. ’ s private key in protected places 8. challenge If they match, Paul verified John’s identity and John can not repudiate it. Encrypted phrase AND Decrypt with J. ’ s public key in encrypted form Compare with original phrase slide from EGEE NA 3 Tutorial repository INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 13
Trusted third parties Enabling Grids for E-scienc. E • All research grid infrastructures share the same base set of trusted third parties (‘CAs’) • There is typically one in each country • The credentials they issue are comparable in quality INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 14

Requirements for (inter)national trust Enabling Grids for E-scienc. E • Identity vetting procedures – Based on (national) photo ID’s – Face-to-face verification of applicants via a network of Registration Authorities – possible to trace the user in case of unlawful misconduct – Secure binding between the request and the identity vetting – Periodic renewal (once every year) • Secure operation – off-line signing key or HSM-backed on-line secured systems • Response to incidents – Timely revocation of compromised certificates new models and guidelines are being agreed on right now, but are not yet available. INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 15

VO affiliation Enabling Grids for E-scienc. E • Per-VO Authorisations (“visa”) – – granted to a person or service by a virtual organisation based on the ‘passport’ name acknowledged by the resource owners providers can still ban individual users, and decide which privileges are granted to which VO attributes • In your case, these ‘visa’ are called VOMS credentials • It is a cryptographically protected statement by the VO • which is bound (by the VO) to your subject name C=IT/O=INFN /L=CNAF /CN=Pinco Palla /CN=proxy INFSO-RI-508833 Pinco’s VO attributes Grid Security, Groningen Tutorial 2006 16

Single sign-on and delegation Enabling Grids for E-scienc. E • To authenticate with your certificate directly you would have to type a passphrase every time • Also you need a way to send you VOMS credentials across • In the Grid Security Infrastructure today, this is solved by ‘proxy certificates’ – – a temporary key pair in a temporary certificate signed by your ‘long term’ private key valid for a limited time (default: 12 hours) and itself not protected by a passphrase INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 17
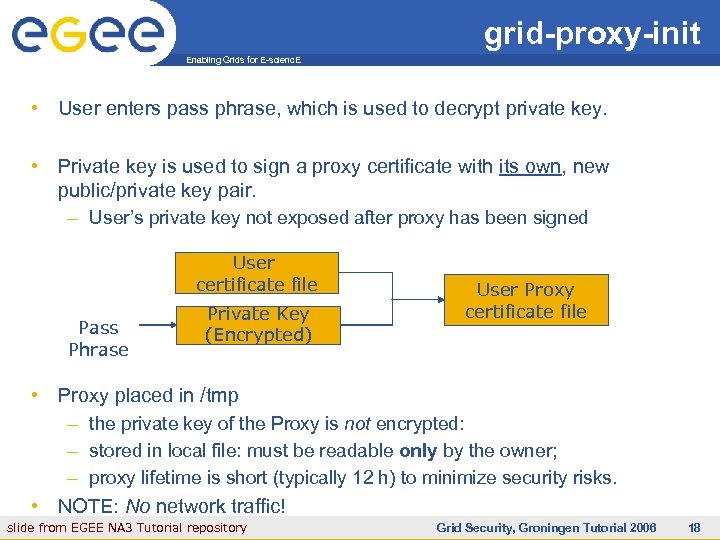
grid-proxy-init Enabling Grids for E-scienc. E • User enters pass phrase, which is used to decrypt private key. • Private key is used to sign a proxy certificate with its own, new public/private key pair. – User’s private key not exposed after proxy has been signed User certificate file Pass Phrase Private Key (Encrypted) User Proxy certificate file • Proxy placed in /tmp – the private key of the Proxy is not encrypted: – stored in local file: must be readable only by the owner; – proxy lifetime is short (typically 12 h) to minimize security risks. • NOTE: No network traffic! slide from EGEE NA 3 Tutorial repository INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 18
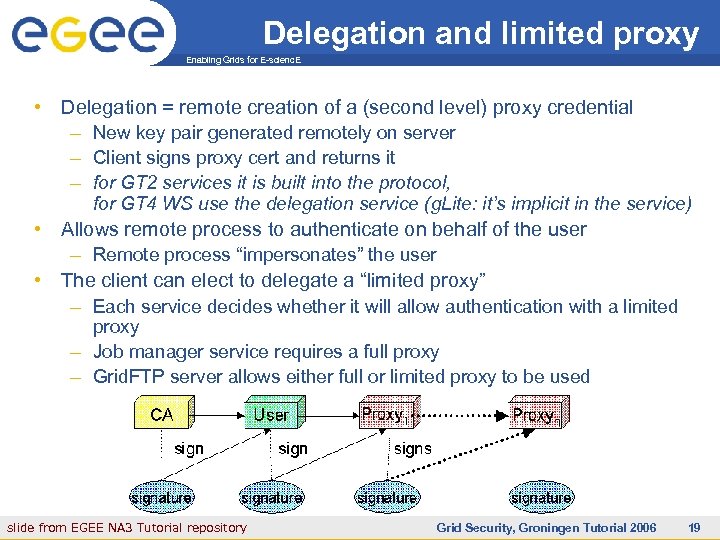
Delegation and limited proxy Enabling Grids for E-scienc. E • Delegation = remote creation of a (second level) proxy credential – New key pair generated remotely on server – Client signs proxy cert and returns it – for GT 2 services it is built into the protocol, for GT 4 WS use the delegation service (g. Lite: it’s implicit in the service) • Allows remote process to authenticate on behalf of the user – Remote process “impersonates” the user • The client can elect to delegate a “limited proxy” – Each service decides whether it will allow authentication with a limited proxy – Job manager service requires a full proxy – Grid. FTP server allows either full or limited proxy to be used slide from EGEE NA 3 Tutorial repository INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 19

Proxy again … Enabling Grids for E-scienc. E • grid-proxy-init ≡ “login to the Grid” • To “logout” you have to destroy your proxy: – grid-proxy-destroy – This does NOT destroy any proxies that were delegated from this proxy. – You cannot revoke a remote proxy – Usually create proxies with short lifetimes • To gather information about your proxy: – grid-proxy-info – Options for printing proxy information -subject -type -strength -issuer -timeleft -help slide from EGEE NA 3 Tutorial repository INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 20
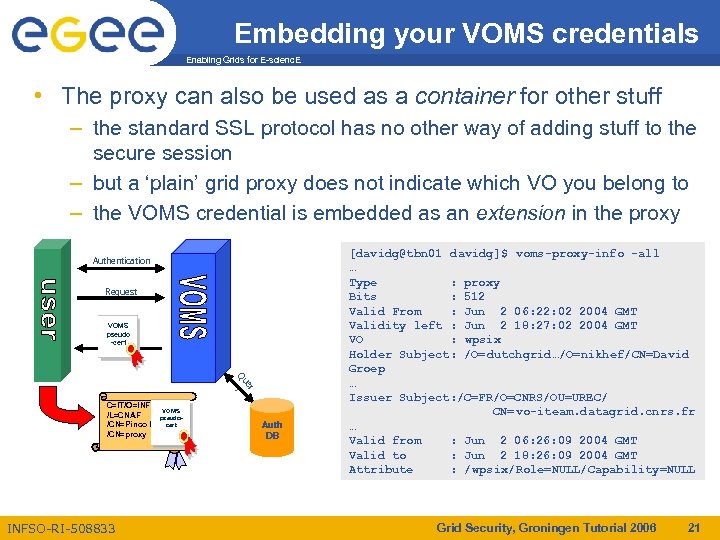
Embedding your VOMS credentials Enabling Grids for E-scienc. E • The proxy can also be used as a container for other stuff – the standard SSL protocol has no other way of adding stuff to the secure session – but a ‘plain’ grid proxy does not indicate which VO you belong to – the VOMS credential is embedded as an extension in the proxy Authentication Request VOMS pseudo -cert er Qu y C=IT/O=INFN VOMS /L=CNAF pseudocert /CN=Pinco Palla /CN=proxy INFSO-RI-508833 Auth DB [davidg@tbn 01 davidg]$ voms-proxy-info -all … Type : proxy Bits : 512 Valid From : Jun 2 06: 22: 02 2004 GMT Validity left : Jun 2 18: 27: 02 2004 GMT VO : wpsix Holder Subject: /O=dutchgrid…/O=nikhef/CN=David Groep … Issuer Subject: /C=FR/O=CNRS/OU=UREC/ CN=vo-iteam. datagrid. cnrs. fr … Valid from : Jun 2 06: 26: 09 2004 GMT Valid to : Jun 2 18: 26: 09 2004 GMT Attribute : /wpsix/Role=NULL/Capability=NULL Grid Security, Groningen Tutorial 2006 21
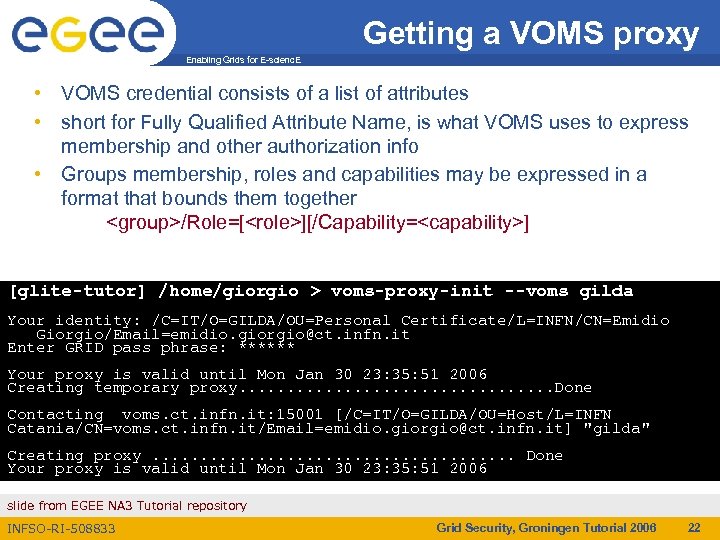
Getting a VOMS proxy Enabling Grids for E-scienc. E • VOMS credential consists of a list of attributes • short for Fully Qualified Attribute Name, is what VOMS uses to express membership and other authorization info • Groups membership, roles and capabilities may be expressed in a format that bounds them together <group>/Role=[<role>][/Capability=<capability>] [glite-tutor] /home/giorgio > voms-proxy-init --voms gilda Your identity: /C=IT/O=GILDA/OU=Personal Certificate/L=INFN/CN=Emidio Giorgio/Email=emidio. giorgio@ct. infn. it Enter GRID pass phrase: ****** Your proxy is valid until Mon Jan 30 23: 35: 51 2006 Creating temporary proxy. . . . Done Contacting voms. ct. infn. it: 15001 [/C=IT/O=GILDA/OU=Host/L=INFN Catania/CN=voms. ct. infn. it/Email=emidio. giorgio@ct. infn. it] "gilda" Creating proxy. . . . . Done Your proxy is valid until Mon Jan 30 23: 35: 51 2006 slide from EGEE NA 3 Tutorial repository INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 22

Long term proxies Enabling Grids for E-scienc. E • • • Proxy has limited lifetime (default is 12 h) – Bad idea to have longer proxy However, a grid task might need to use a proxy for a much longer time – Grid jobs in HEP Data Challenges on LCG last up to 2 days myproxy server: – Allows to create and store a long term proxy certificate: – myproxy-init -s <host_name> § -s: <host_name> specifies the hostname of the myproxy server – myproxy-info § Get information about stored long living proxy – myproxy-get-delegation § Get a new proxy from the My. Proxy server • • – myproxy-destroy – Chech out the myproxy-xxx - - help option A dedicated service on the RB can renew automatically the proxy File transfer services in g. Lite validates user request and eventually renew proxies – contacting myproxy server slide from EGEE NA 3 Tutorial repository INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 23
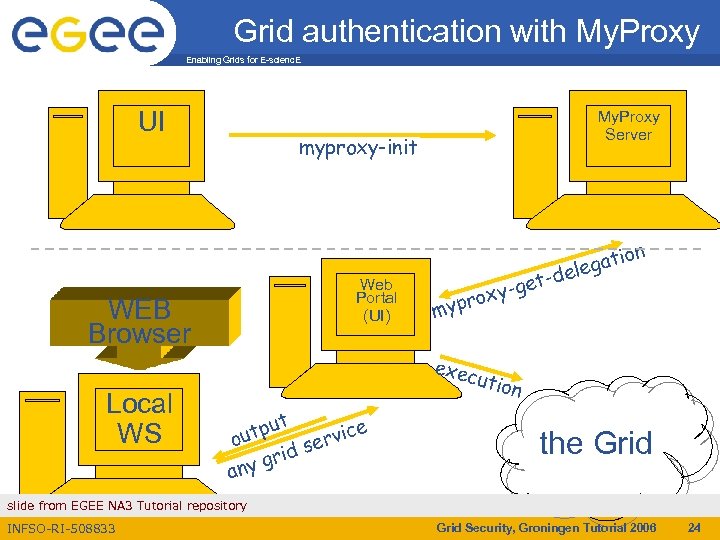
Grid authentication with My. Proxy Enabling Grids for E-scienc. E UI myproxy-init Web Portal (UI) WEB Browser Local WS My. Proxy Server r myp -d t y-ge ox n gatio ele exec ution ut e utp rvic o se rid g any the Grid slide from EGEE NA 3 Tutorial repository INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 24

Enabling Grids for E-scienc. E But what do I have to do? A Grid Security walk-through www. eu-egee. org INFSO-RI-508833
A walk-through Enabling Grids for E-scienc. E CA service user VO INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 26
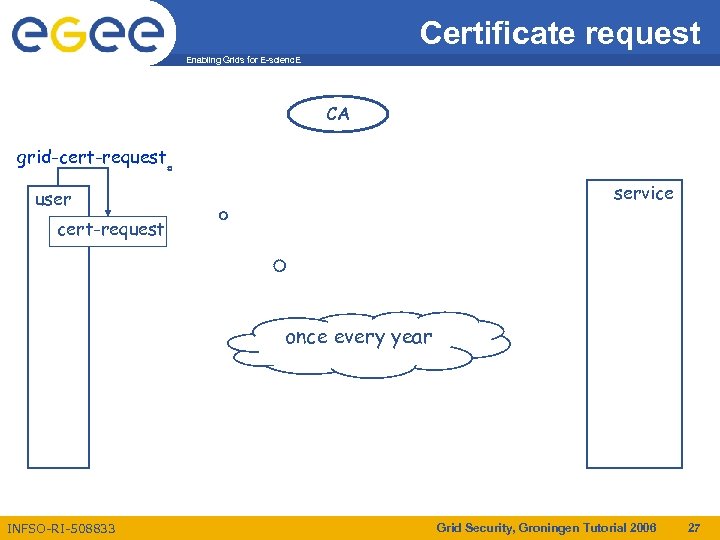
Certificate request Enabling Grids for E-scienc. E CA grid-cert-request service user cert-request once every year VO INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 27

Contacting the CA Enabling Grids for E-scienc. E • Each CA has different policies and practices • Generate a cryptographic key pair – using a script like grid-cert-request – with your web browser – using a Java Applet • Appear in-person to the Registration Authority (RA) • RA approves your request • CA signs the approved request and sends you the cert – via mail: copy to your home directory – via the web: download into your browser and export to disk • All use a network of RAs close to you INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 28
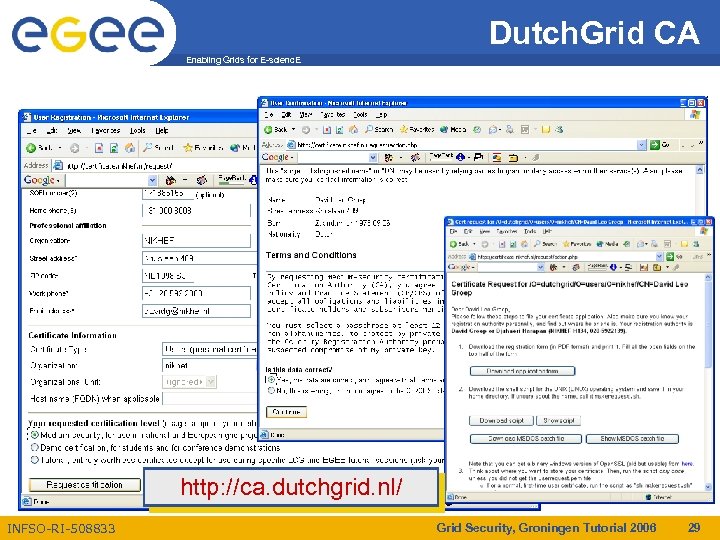
Dutch. Grid CA Enabling Grids for E-scienc. E http: //ca. dutchgrid. nl/ INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 29
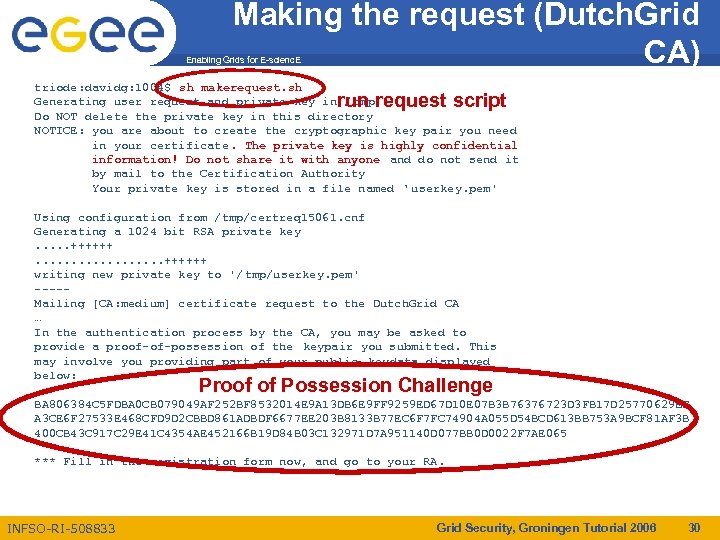
Making the request (Dutch. Grid CA) Enabling Grids for E-scienc. E triode: davidg: 1004$ sh makerequest. sh Generating user request and private key in / tmp Do NOT delete the private key in this directory NOTICE: you are about to create the cryptographic key pair you need in your certificate. The private key is highly confidential information! Do not share it with anyone and do not send it by mail to the Certification Authority Your private key is stored in a file named ‘ userkey. pem' run request script Using configuration from /tmp/certreq 15061. cnf Generating a 1024 bit RSA private key. . . ++++++. . . . ++++++ writing new private key to '/ tmp/userkey. pem' ----Mailing [CA: medium] certificate request to the Dutch. Grid CA … In the authentication process by the CA, you may be asked to provide a proof-of-possession of the keypair you submitted. This may involve you providing part of your public keydata displayed below: Proof of Possession Challenge BA 806384 C 5 FDBA 0 CB 079049 AF 252 BF 8532014 E 9 A 13 DB 6 E 9 FF 9259 ED 67 D 10 E 07 B 3 B 76376723 D 3 FB 17 D 25770629 EF A 3 CE 6 F 27533 E 468 CFD 9 D 2 CBBD 861 ADBDF 6677 EE 203 B 8133 B 77 EC 6 F 7 FC 74904 A 055 D 54 BCD 613 BB 753 A 9 BCF 81 AF 3 B 400 CB 43 C 917 C 29 E 41 C 4354 AE 452166 B 19 D 84 B 03 C 132971 D 7 A 951140 D 077 BB 0 D 0022 F 7 AE 065 *** Fill in the registration form now, and go to your RA. INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 30
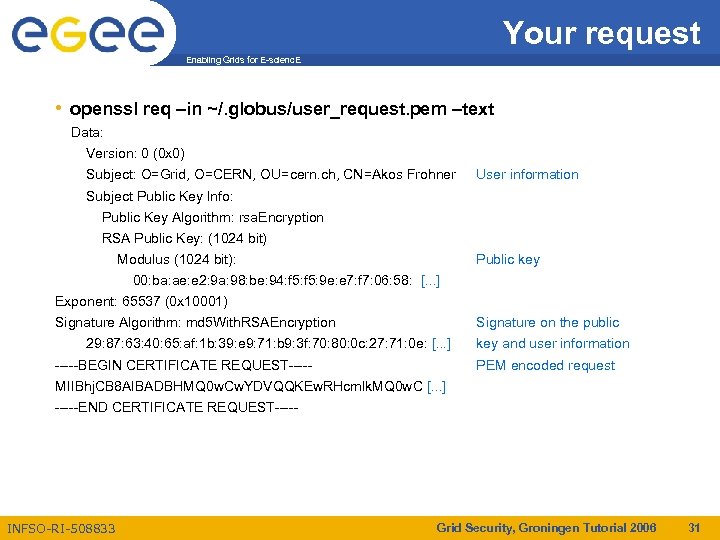
Your request Enabling Grids for E-scienc. E • openssl req –in ~/. globus/user_request. pem –text Data: Version: 0 (0 x 0) Subject: O=Grid, O=CERN, OU=cern. ch, CN=Akos Frohner User information Subject Public Key Info: Public Key Algorithm: rsa. Encryption RSA Public Key: (1024 bit) Modulus (1024 bit): Public key 00: ba: ae: e 2: 9 a: 98: be: 94: f 5: 9 e: e 7: f 7: 06: 58: [. . . ] Exponent: 65537 (0 x 10001) Signature Algorithm: md 5 With. RSAEncryption Signature on the public 29: 87: 63: 40: 65: af: 1 b: 39: e 9: 71: b 9: 3 f: 70: 80: 0 c: 27: 71: 0 e: [. . . ] -----BEGIN CERTIFICATE REQUEST----- key and user information PEM encoded request MIIBhj. CB 8 AIBADBHMQ 0 w. Cw. YDVQQKEw. RHcmlk. MQ 0 w. C [. . . ] -----END CERTIFICATE REQUEST----- INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 31
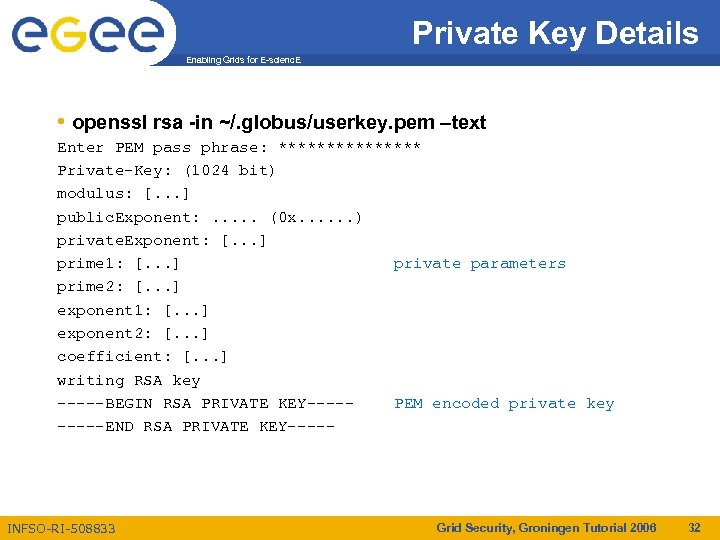
Private Key Details Enabling Grids for E-scienc. E • openssl rsa -in ~/. globus/userkey. pem –text Enter PEM pass phrase: ******** Private-Key: (1024 bit) modulus: [. . . ] public. Exponent: . . . (0 x. . . ) private. Exponent: [. . . ] prime 1: [. . . ] private parameters prime 2: [. . . ] exponent 1: [. . . ] exponent 2: [. . . ] coefficient: [. . . ] writing RSA key -----BEGIN RSA PRIVATE KEY----PEM encoded private key -----END RSA PRIVATE KEY----- INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 32
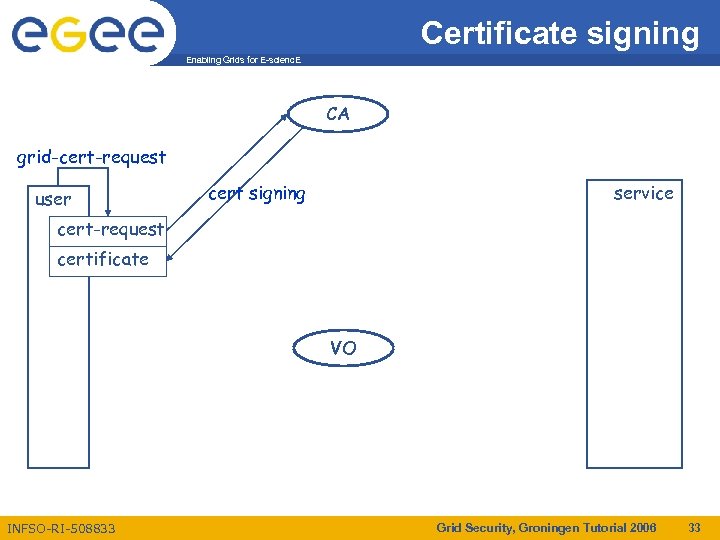
Certificate signing Enabling Grids for E-scienc. E CA grid-cert-request user cert signing service cert-request certificate VO INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 33
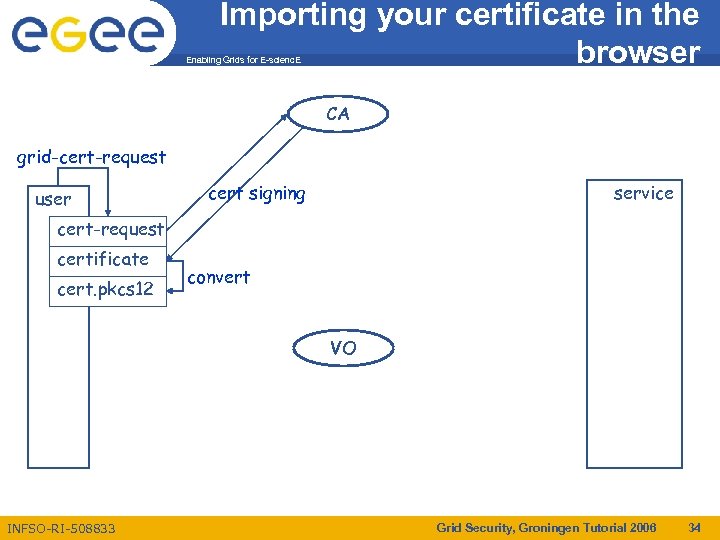
Importing your certificate in the browser Enabling Grids for E-scienc. E CA grid-cert-request user cert signing service cert-request certificate cert. pkcs 12 convert VO INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 34
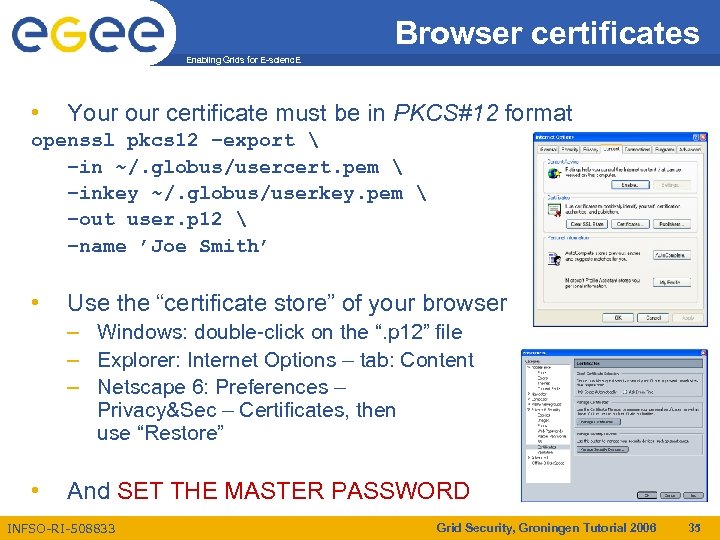
Browser certificates Enabling Grids for E-scienc. E • Your certificate must be in PKCS#12 format openssl pkcs 12 –export –in ~/. globus/usercert. pem –inkey ~/. globus/userkey. pem –out user. p 12 –name ’Joe Smith’ • Use the “certificate store” of your browser – Windows: double-click on the “. p 12” file – Explorer: Internet Options – tab: Content – Netscape 6: Preferences – Privacy&Sec – Certificates, then use “Restore” • And SET THE MASTER PASSWORD INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 35
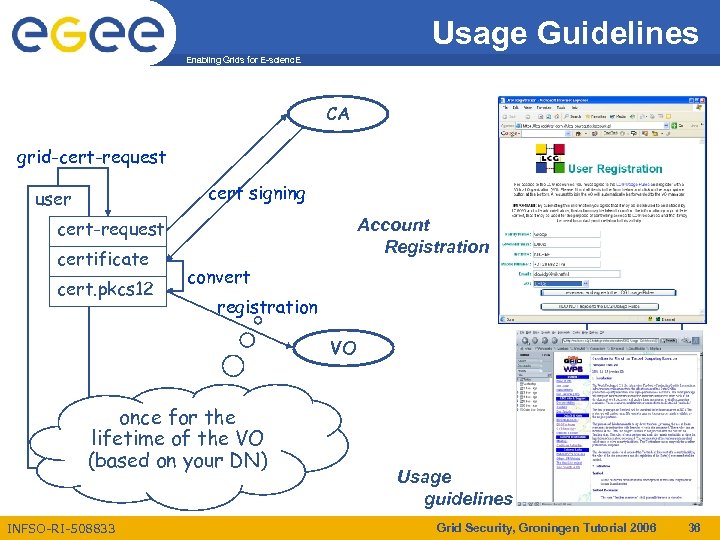
Usage Guidelines Enabling Grids for E-scienc. E CA grid-cert-request cert signing user service Account Registration cert-request certificate cert. pkcs 12 convert registration VO once for the lifetime of the VO (based on your DN) INFSO-RI-508833 Usage guidelines Grid Security, Groningen Tutorial 2006 36
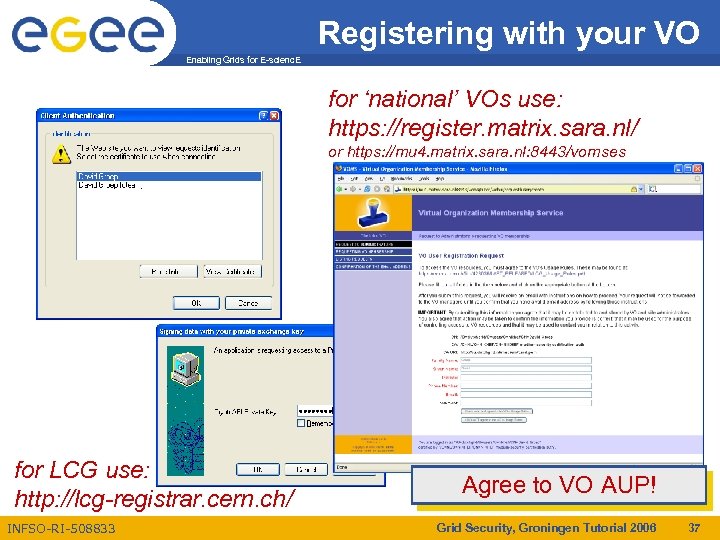
Registering with your VO Enabling Grids for E-scienc. E for ‘national’ VOs use: https: //register. matrix. sara. nl/ or https: //mu 4. matrix. sara. nl: 8443/vomses for LCG use: http: //lcg-registrar. cern. ch/ INFSO-RI-508833 Agree to VO AUP! Grid Security, Groningen Tutorial 2006 37
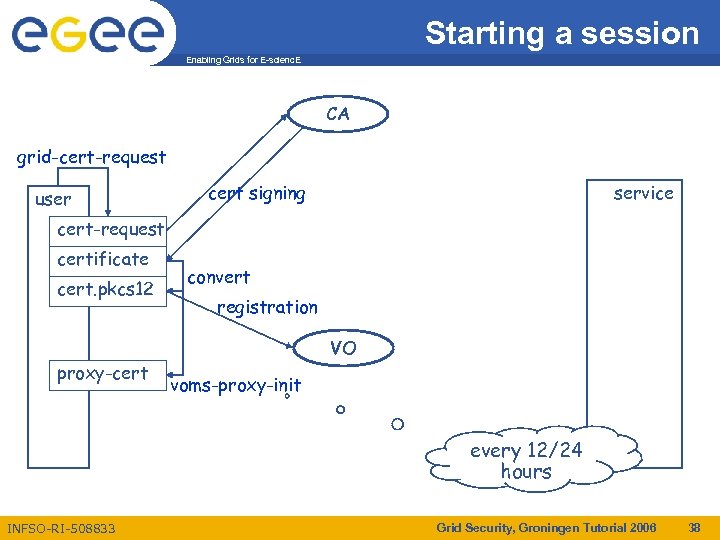
Starting a session Enabling Grids for E-scienc. E CA grid-cert-request user cert signing service cert-request certificate cert. pkcs 12 convert registration VO proxy-cert voms-proxy-init every 12/24 hours INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 38
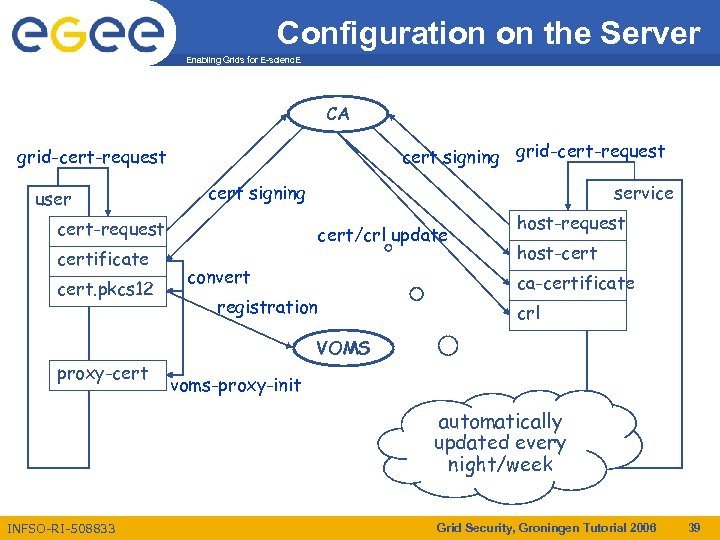
Configuration on the Server Enabling Grids for E-scienc. E CA cert signing grid-cert-request user cert signing service cert-request certificate cert. pkcs 12 cert/crl update convert registration host-request host-cert ca-certificate crl VOMS proxy-cert voms-proxy-init automatically updated every night/week INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 39
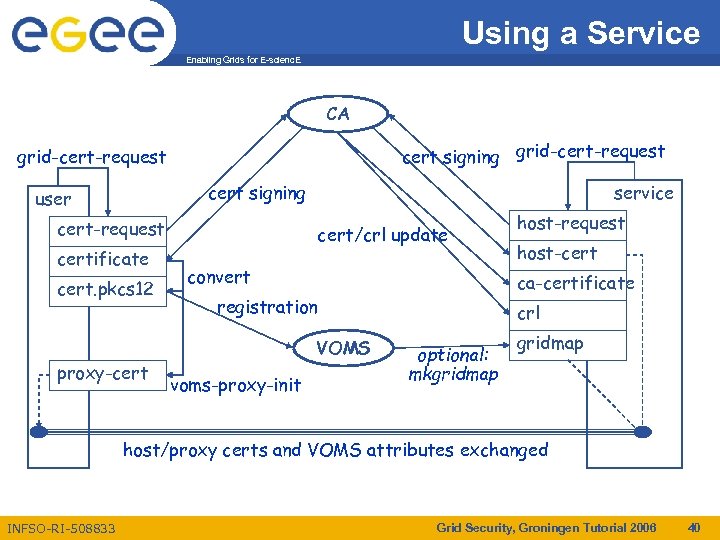
Using a Service Enabling Grids for E-scienc. E CA cert signing grid-cert-request cert signing user service cert-request certificate cert. pkcs 12 cert/crl update convert proxy-cert voms-proxy-init host-cert ca-certificate registration VOMS host-request crl optional: mkgridmap host/proxy certs and VOMS attributes exchanged INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 40

Summary Enabling Grids for E-scienc. E CA: authentication VO: AUP, authorization and access • new certificate: follow the web page instructions • send to the appropriate CA (e. g. ca@dutchgrid. nl) • save the answer – ~/. globus/usercert. pem • import in web browser (. p 12) and register with VO • new proxy certificate: voms-proxy-init –vo foobar – /tmp/x 509 up_u<uid> • use the Grid INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 41

Extra: certificate renewal Enabling Grids for E-scienc. E • Your certificate has a validity of 12 months, then you will have to renew – you get an email warning 4 weeks in advance (and at ~ 2 weeks) – download the script from the web site – run it on a unix system with Open. SSL installed (no macs!) • The script generates a signed email message – send the signed message to ca@dutchgrid. nl – do not modify the message in any way, preferably use sendmail –t < newrequest. txt as the script tells you at the end – your Registration Authority will be contacted for confirmation – after response from the RA, a new certificate is mailed to you • When you get the new certificate, remember to also put the newkey. pem file in the proper place! INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 42
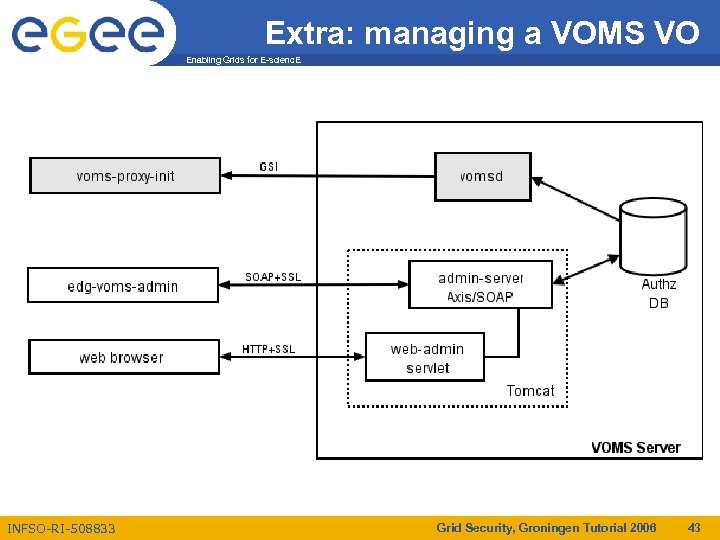
Extra: managing a VOMS VO Enabling Grids for E-scienc. E INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 43
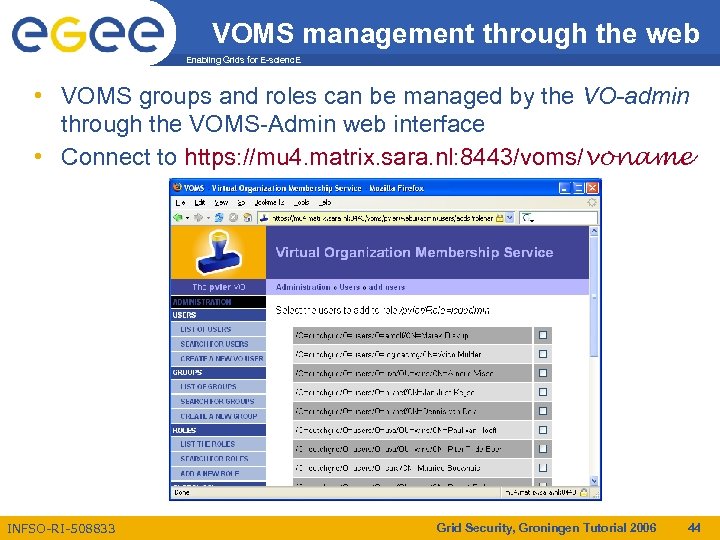
VOMS management through the web Enabling Grids for E-scienc. E • VOMS groups and roles can be managed by the VO-admin through the VOMS-Admin web interface • Connect to https: //mu 4. matrix. sara. nl: 8443/voms/voname INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 44

extra: on the USB key Enabling Grids for E-scienc. E 1. 2. 3. 4. go to the CA web site at http: //ca. dutchgrid. nl/ complete all web forms, and print out the paper download the Unix shell script run the makerequest. sh script, specifying where the keys should be created: mkdir /mnt/flash/. globus sh makerequest. sh /mnt/flash/. globus/ 5. write down the proof-of-possession challenge on the paper Back home 1. receive the mail from the CA 2. insert your USB flash drive again, and copy the mail to /mnt/flash/. globus/usercert. pem 3. make a symlink in your home directory on the UI: ln –s /mnt/flash/. globus $HOME/. globus 4. login to the grid with grid-proxy-init INFSO-RI-508833 Grid Security, Groningen Tutorial 2006 45
05bedce0f5395ff5d79c031f568f78f3.ppt