7b397357d0513ea0069a64ea9afcdffa.ppt
- Количество слайдов: 13

Enabling Authentication & Network Admission Control Steve Pettit
Great Bay Software Inc. Value Statements § Provide the critical first step towards NAC/802. 1 X § Dramatically shorten the deployment time for NAC and network-based authentication § Provide Trusted Access to non-NAC endpoints § Provide data for all network attached endpoints including: • • • Real-time Location and Identity Historical Addressing, Identity, and Location Contextual views of all Enterprise owned assets Impact § St. John’s Hospital reduced 156 man-weeks of discovery and documentation work into 2 man weeks Endpoint Profiling
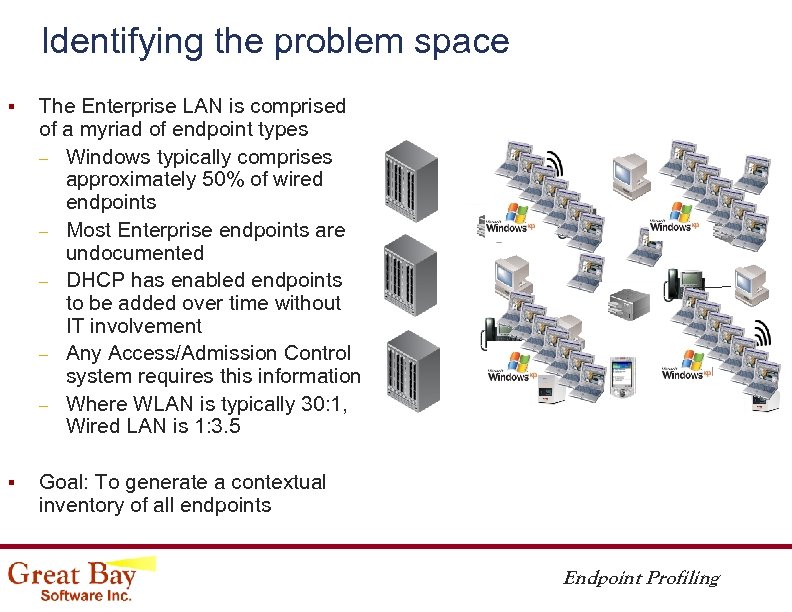
Identifying the problem space § The Enterprise LAN is comprised of a myriad of endpoint types – Windows typically comprises approximately 50% of wired endpoints – Most Enterprise endpoints are undocumented – DHCP has enabled endpoints to be added over time without IT involvement – Any Access/Admission Control system requires this information – Where WLAN is typically 30: 1, Wired LAN is 1: 3. 5 § Goal: To generate a contextual inventory of all endpoints Endpoint Profiling
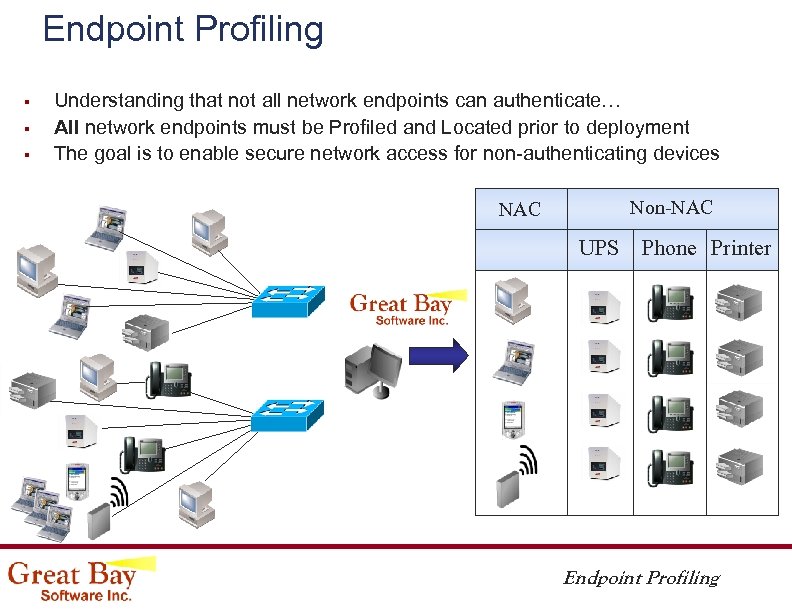
Endpoint Profiling § § § Understanding that not all network endpoints can authenticate… All network endpoints must be Profiled and Located prior to deployment The goal is to enable secure network access for non-authenticating devices Non-NAC UPS Phone Printer Endpoint Profiling
Sample non-NAC Aliases § § § § Printers Fax Machines ISLs IP Phones Wireless Access Points Managed UPS Hubs Multi. Cast video displays Kiosks Medical imaging machines Video Conferencing stations HVAC Cash Registers § § § § Turnstiles Time Clocks Vending Machines Parking Gates Doors Firewalls Proxy Refrigerators IP Cameras Servers UNIX stations Alarm Systems RMON Probes Endpoint Profiling

Applications for Endpoint Profiling § § § Authentication of non-authenticating hosts Network configuration for static access provisioning Monitoring of non-authenticating devices for behavior Addressing audit findings “do you know what is plugged into your network” Provide data for all network attached endpoints including: • • • Real-time Location and Identity Historical Addressing, Identity, and Location Contextual views of all Enterprise owned assets Endpoint Profiling
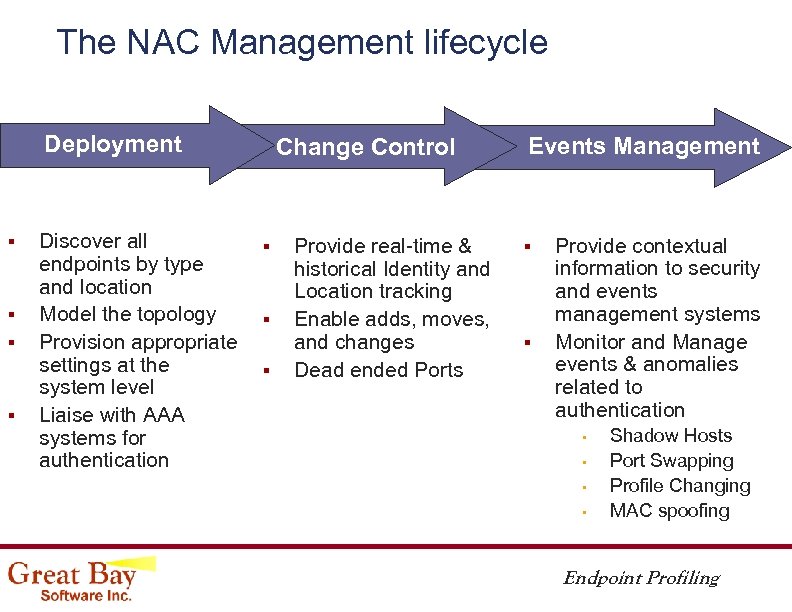
The NAC Management lifecycle Deployment § § Discover all endpoints by type and location Model the topology Provision appropriate settings at the system level Liaise with AAA systems for authentication Change Control § § § Provide real-time & historical Identity and Location tracking Enable adds, moves, and changes Dead ended Ports Events Management § § Provide contextual information to security and events management systems Monitor and Manage events & anomalies related to authentication • • Shadow Hosts Port Swapping Profile Changing MAC spoofing Endpoint Profiling
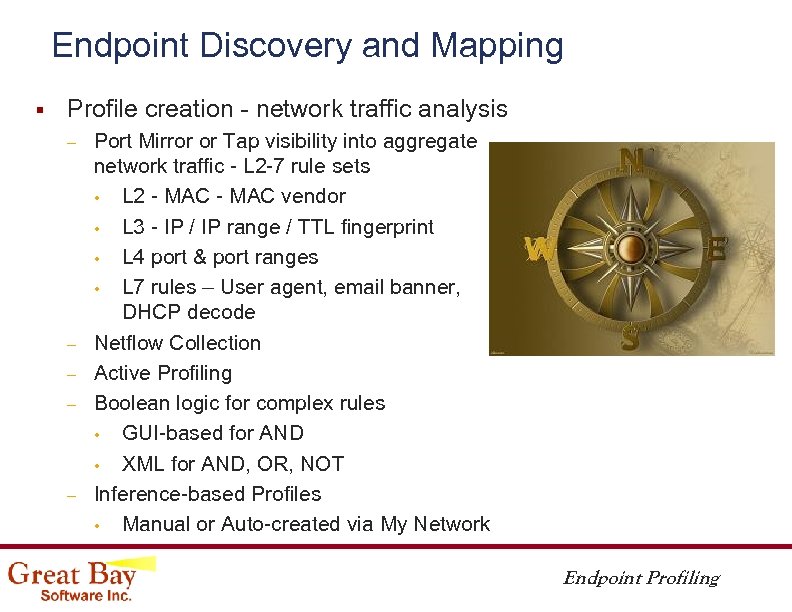
Endpoint Discovery and Mapping § Profile creation - network traffic analysis – – – Port Mirror or Tap visibility into aggregate network traffic - L 2 -7 rule sets • L 2 - MAC vendor • L 3 - IP / IP range / TTL fingerprint • L 4 port & port ranges • L 7 rules – User agent, email banner, DHCP decode Netflow Collection Active Profiling Boolean logic for complex rules • GUI-based for AND • XML for AND, OR, NOT Inference-based Profiles • Manual or Auto-created via My Network Endpoint Profiling
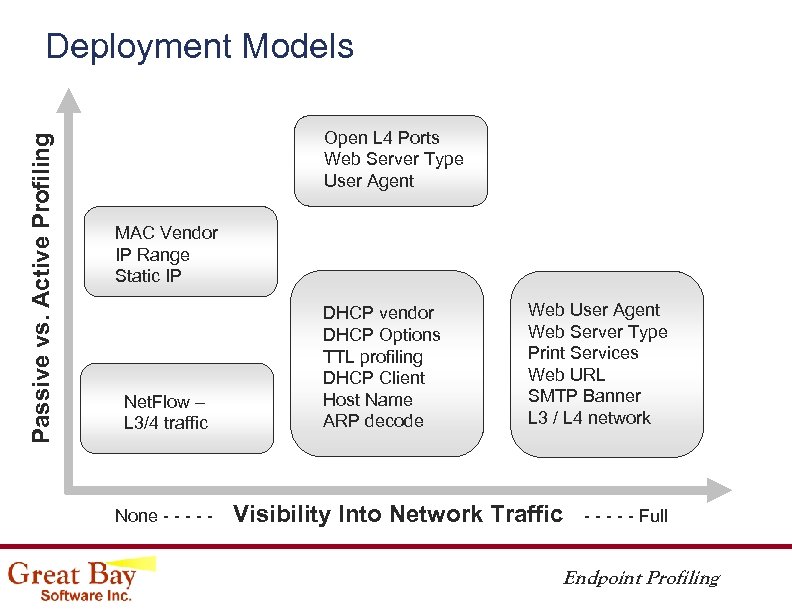
Passive vs. Active Profiling Deployment Models Open L 4 Ports Web Server Type User Agent MAC Vendor IP Range Static IP Net. Flow – L 3/4 traffic None - - - DHCP vendor DHCP Options TTL profiling DHCP Client Host Name ARP decode Web User Agent Web Server Type Print Services Web URL SMTP Banner L 3 / L 4 network Visibility Into Network Traffic - - - Full Endpoint Profiling
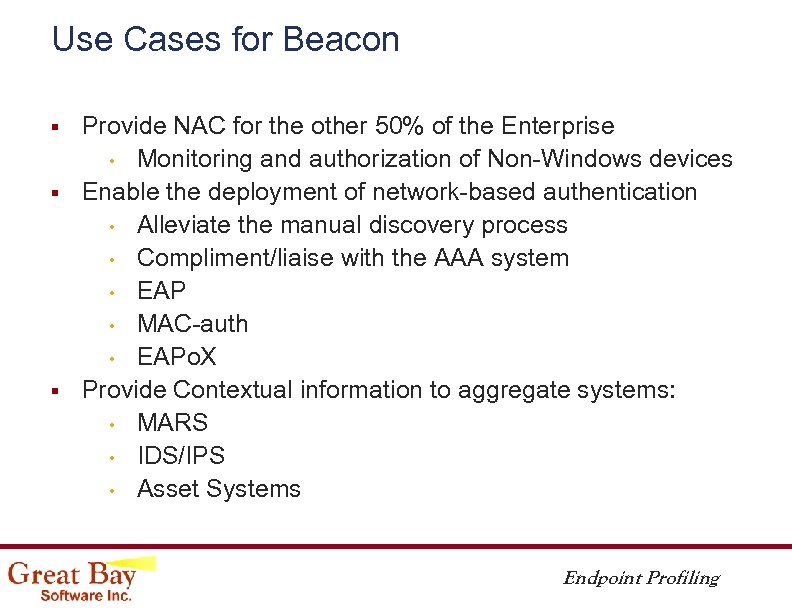
Use Cases for Beacon § § § Provide NAC for the other 50% of the Enterprise • Monitoring and authorization of Non-Windows devices Enable the deployment of network-based authentication • Alleviate the manual discovery process • Compliment/liaise with the AAA system • EAP • MAC-auth • EAPo. X Provide Contextual information to aggregate systems: • MARS • IDS/IPS • Asset Systems Endpoint Profiling
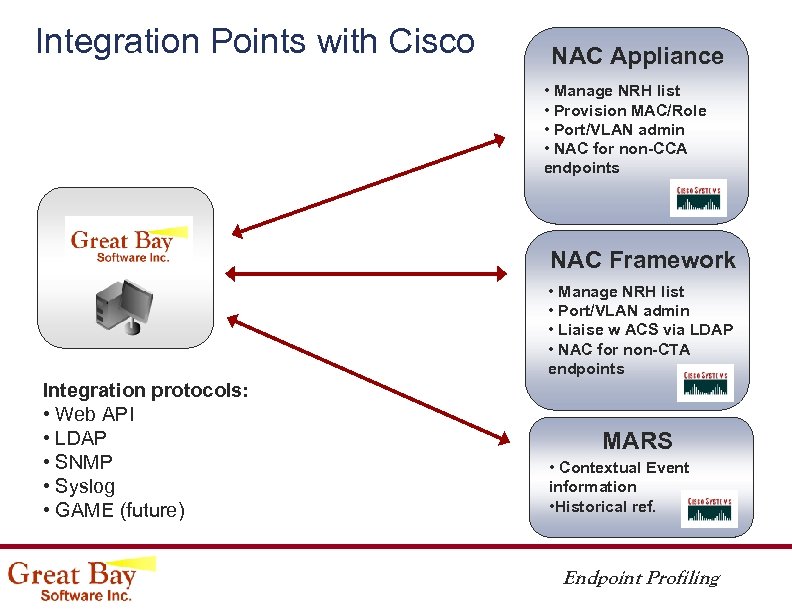
Integration Points with Cisco NAC Appliance • Manage NRH list • Provision MAC/Role • Port/VLAN admin • NAC for non-CCA endpoints NAC Framework • Manage NRH list • Port/VLAN admin • Liaise w ACS via LDAP • NAC for non-CTA endpoints Integration protocols: • Web API • LDAP • SNMP • Syslog • GAME (future) MARS • Contextual Event information • Historical ref. Endpoint Profiling
Summary § Reduces 156 man weeks of work to 2 weeks § Automated discovery and system-level provisioning § Ongoing monitoring of non-NAC endpoints § Flexible Deployment model Endpoint Profiling

Endpoint Profiling
7b397357d0513ea0069a64ea9afcdffa.ppt