d7fdd893f9fb5b6bcfdd1e622974babe.ppt
- Количество слайдов: 53
 EMS 2012 SERSCIS has received EC Research Funding UKSIM – AMSS : 6 th European Modelling Symposium On Mathematical Modelling and Computer Simulation Malta 14 -16 , Nov. 2012. Semantically Enhanced Resilient and Secure Critical Infrastructure Services
EMS 2012 SERSCIS has received EC Research Funding UKSIM – AMSS : 6 th European Modelling Symposium On Mathematical Modelling and Computer Simulation Malta 14 -16 , Nov. 2012. Semantically Enhanced Resilient and Secure Critical Infrastructure Services
 Subtitle Presenter- Contributor: Vasilis Tsoulkas, Center for Security Studies (KEMEA)/Ministry of Citizen Protection & University of Athens, GR. Co-Contributors: Dimitris Kostopoulos KEMEA / Ministry of Citizen Protection, Athens, GR George Leventakis KEMEA & University of the Aegean, Dept. Of Shipping, Trade and Transport. Mike Surridge IT Innovation Centre, Univ. of Southampton, UK 2
Subtitle Presenter- Contributor: Vasilis Tsoulkas, Center for Security Studies (KEMEA)/Ministry of Citizen Protection & University of Athens, GR. Co-Contributors: Dimitris Kostopoulos KEMEA / Ministry of Citizen Protection, Athens, GR George Leventakis KEMEA & University of the Aegean, Dept. Of Shipping, Trade and Transport. Mike Surridge IT Innovation Centre, Univ. of Southampton, UK 2
 SERSCIS Group Subtitle • IT Innovation Centre – University of Southampton, UK • Joanneum Research (JRS) – Graz, Austria • Center for Security Studies (KEMEA) – Athens, Greece • Austro Control Gmb. H (ACG) – Vienna, Austria • Port Authority Gijon (PAG) – Gijon, Spain 3
SERSCIS Group Subtitle • IT Innovation Centre – University of Southampton, UK • Joanneum Research (JRS) – Graz, Austria • Center for Security Studies (KEMEA) – Athens, Greece • Austro Control Gmb. H (ACG) – Vienna, Austria • Port Authority Gijon (PAG) – Gijon, Spain 3
 Presentation Sections Subtitle 1. 2. 3. 4. 5. Ø 6. 7. 8. 9. 10. Objectives Brief SERSCIS Architecture description Basics of SERSCIS System Modeling Strategy SERSCIS – Proof of Concept A-CDM (Airport - Collaborative Data Management)Ground Handler case (EUROCONTROL) ACDM-components, Info. Sharing Concept, Traffic Critical Parameters, Data quality of KPIs & Metrics SERSCIS Proof of Concept (Ground Handler) SERSCIS Domain core (complete) Ontology and Semantic Models SERSCIS Decision Support Tool (DST) SERSCIS Stream Reasoning Process. Conclusions- Impact 4
Presentation Sections Subtitle 1. 2. 3. 4. 5. Ø 6. 7. 8. 9. 10. Objectives Brief SERSCIS Architecture description Basics of SERSCIS System Modeling Strategy SERSCIS – Proof of Concept A-CDM (Airport - Collaborative Data Management)Ground Handler case (EUROCONTROL) ACDM-components, Info. Sharing Concept, Traffic Critical Parameters, Data quality of KPIs & Metrics SERSCIS Proof of Concept (Ground Handler) SERSCIS Domain core (complete) Ontology and Semantic Models SERSCIS Decision Support Tool (DST) SERSCIS Stream Reasoning Process. Conclusions- Impact 4
 Objectives Subtitle • Critical infrastructure ICT components are increasingly interconnected Ø information sharing → greater operational efficiency, but also reduced slack and flexibility Ø interconnections → new risks from ICT failure cascade effects • SERSCIS approach: use agile Service Oriented Architecture (SOA) to offset these threats Ø adapt ICT components and networks to meet changing needs Ø adapt ICT connections to prevent cascades and contain threats 5
Objectives Subtitle • Critical infrastructure ICT components are increasingly interconnected Ø information sharing → greater operational efficiency, but also reduced slack and flexibility Ø interconnections → new risks from ICT failure cascade effects • SERSCIS approach: use agile Service Oriented Architecture (SOA) to offset these threats Ø adapt ICT components and networks to meet changing needs Ø adapt ICT connections to prevent cascades and contain threats 5
 Objectives Subtitle • To exploit agile Service Oriented Technology to – compose ICT connections related to critical infrastructure – monitor and manage ICT components against welldefined dependability criteria – adapt ICT connections in response to disruption or threats • To validate this approach in Proof of Concept Scenarios from the air traffic sector (A-CDM EUROCONTROL) 6
Objectives Subtitle • To exploit agile Service Oriented Technology to – compose ICT connections related to critical infrastructure – monitor and manage ICT components against welldefined dependability criteria – adapt ICT connections in response to disruption or threats • To validate this approach in Proof of Concept Scenarios from the air traffic sector (A-CDM EUROCONTROL) 6
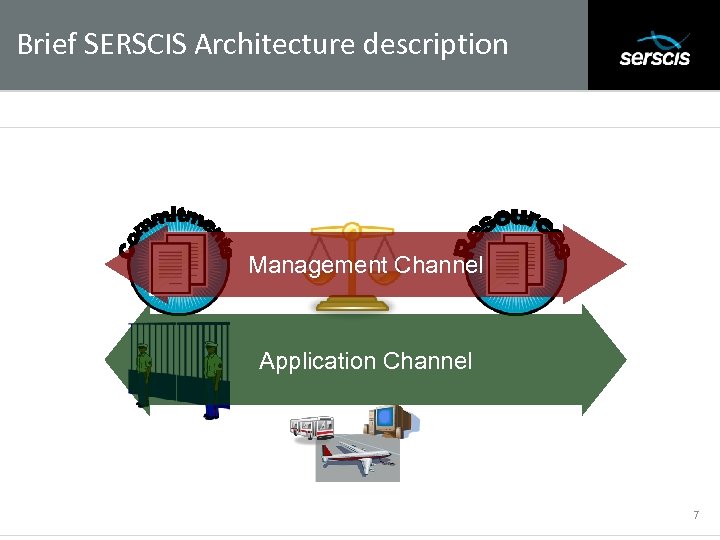 Brief SERSCIS Architecture description Subtitle Management Channel Application Channel 7
Brief SERSCIS Architecture description Subtitle Management Channel Application Channel 7
 A-CDM (basic concepts) EUROCONTROL Subtitle Ø Airport Collaborative Decision Making (A-CDM): To improve Air Traffic Flow & Capacity Management (ATFCM) at airports by reducing delays, improving event predictability and optimizing the utilization of services and resources. Ø Implementation of Airport CDM: allows each Airport CDM Partner to optimise their decisions in collaboration with other ACDM Partners Ø The decision making by the Airport CDM Partners is facilitated by the sharing of accurate and timely information and by adapted procedures, mechanisms and tools. 9
A-CDM (basic concepts) EUROCONTROL Subtitle Ø Airport Collaborative Decision Making (A-CDM): To improve Air Traffic Flow & Capacity Management (ATFCM) at airports by reducing delays, improving event predictability and optimizing the utilization of services and resources. Ø Implementation of Airport CDM: allows each Airport CDM Partner to optimise their decisions in collaboration with other ACDM Partners Ø The decision making by the Airport CDM Partners is facilitated by the sharing of accurate and timely information and by adapted procedures, mechanisms and tools. 9
 A-CDM components Subtitle The Airport CDM concept is divided in the following Components: • Airport CDM Information Sharing Component • CDM Turn-around Process – Milestones Approach • Variable Taxi Time Calculation • Collaborative Management of Flight Updates • Collaborative Pre-departure Sequence • Advanced CDM The efficiency of the Air Transport System is highly dependant on the traffic predictability critical parameters. 11
A-CDM components Subtitle The Airport CDM concept is divided in the following Components: • Airport CDM Information Sharing Component • CDM Turn-around Process – Milestones Approach • Variable Taxi Time Calculation • Collaborative Management of Flight Updates • Collaborative Pre-departure Sequence • Advanced CDM The efficiency of the Air Transport System is highly dependant on the traffic predictability critical parameters. 11
 Airport CDM Information Sharing Concept Component (ACIS) ØThe Airport CDM Information Sharing Component : Subtitle Defines the sharing of accurate and timely information between the Airport CDM Partners to achieve common situational awareness and to improve traffic parameters predictability. Ø • • • The main Airport CDM Partners are: Airport Operator Aircraft Operators Ground Handlers De-icing companies Air Traffic Service Provider CFMU 12
Airport CDM Information Sharing Concept Component (ACIS) ØThe Airport CDM Information Sharing Component : Subtitle Defines the sharing of accurate and timely information between the Airport CDM Partners to achieve common situational awareness and to improve traffic parameters predictability. Ø • • • The main Airport CDM Partners are: Airport Operator Aircraft Operators Ground Handlers De-icing companies Air Traffic Service Provider CFMU 12
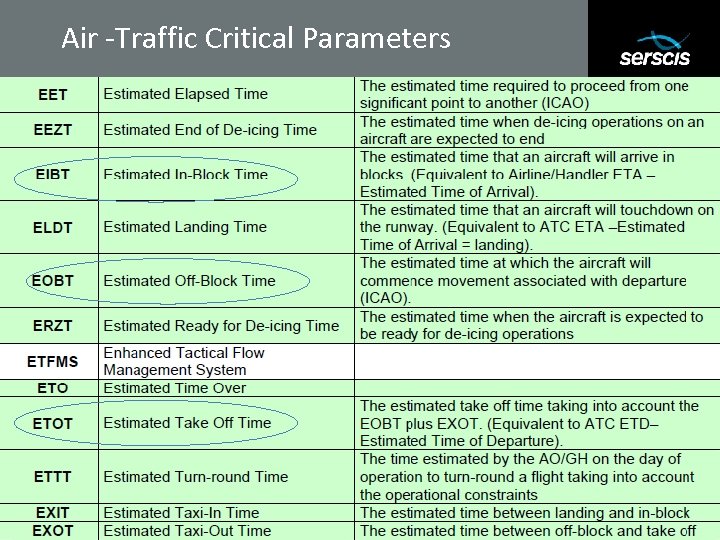 Air -Traffic Critical Parameters Subtitle 13
Air -Traffic Critical Parameters Subtitle 13
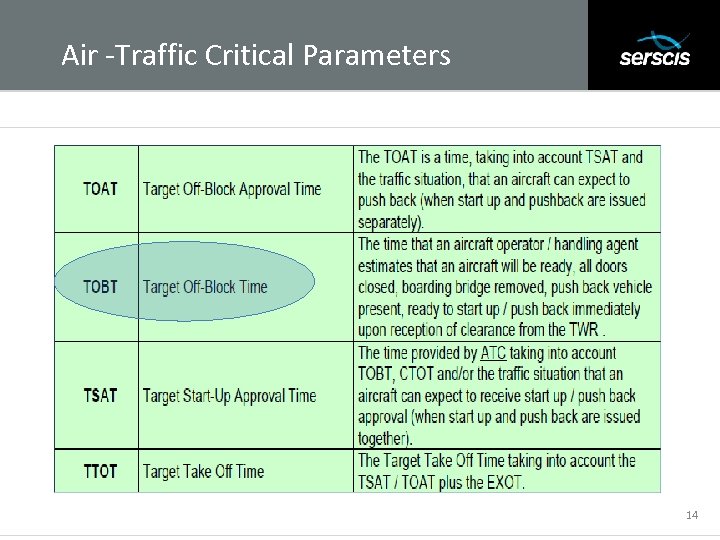 Air -Traffic Critical Parameters Subtitle 14
Air -Traffic Critical Parameters Subtitle 14
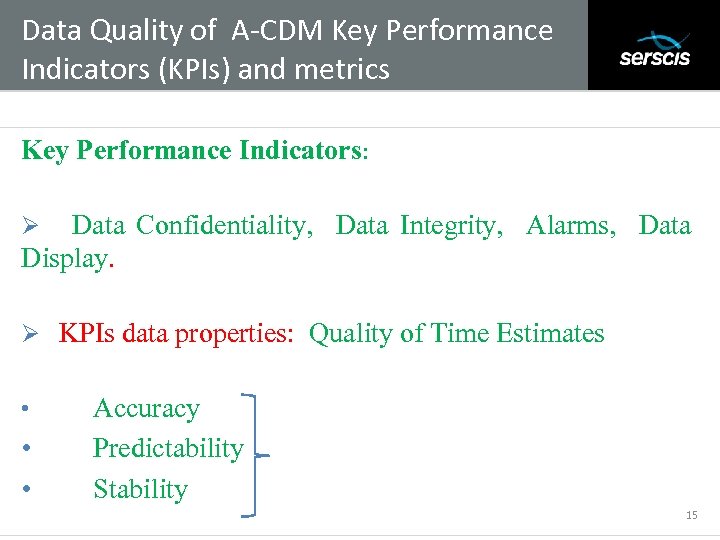 Data Quality of A-CDM Key Performance Indicators (KPIs) and metrics Subtitle Key Performance Indicators: Data Confidentiality, Data Integrity, Alarms, Data Display. Ø Ø KPIs data properties: Quality of Time Estimates • • • Accuracy Predictability Stability 15
Data Quality of A-CDM Key Performance Indicators (KPIs) and metrics Subtitle Key Performance Indicators: Data Confidentiality, Data Integrity, Alarms, Data Display. Ø Ø KPIs data properties: Quality of Time Estimates • • • Accuracy Predictability Stability 15
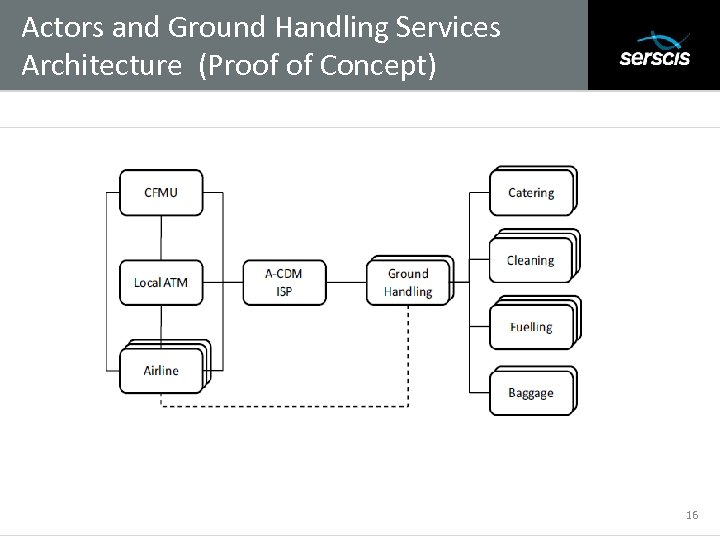 Actors and Ground Handling Services Architecture (Proof of Concept) Subtitle 16
Actors and Ground Handling Services Architecture (Proof of Concept) Subtitle 16
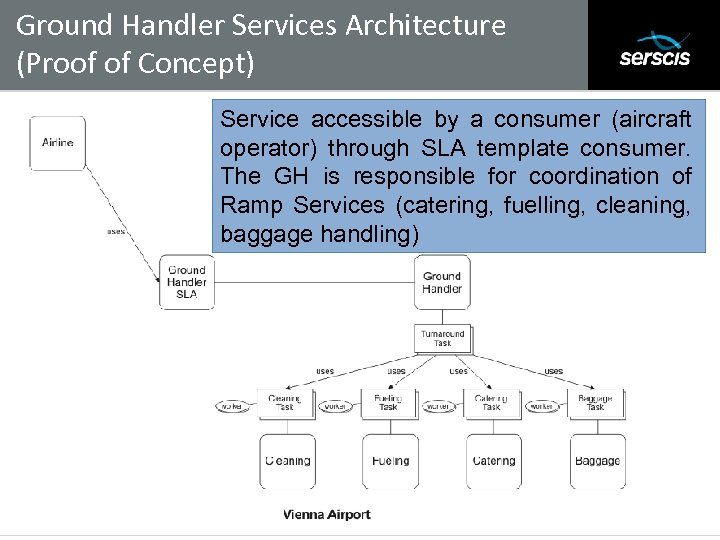 Ground Handler Services Architecture (Proof of Concept) Subtitle Service accessible by a consumer (aircraft operator) through SLA template consumer. The GH is responsible for coordination of Ramp Services (catering, fuelling, cleaning, baggage handling) 17
Ground Handler Services Architecture (Proof of Concept) Subtitle Service accessible by a consumer (aircraft operator) through SLA template consumer. The GH is responsible for coordination of Ramp Services (catering, fuelling, cleaning, baggage handling) 17
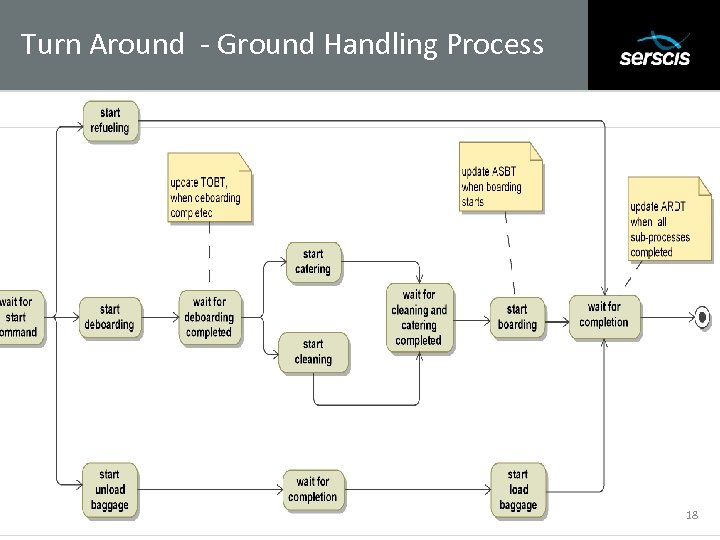 Turn Around - Ground Handling Process Subtitle 18
Turn Around - Ground Handling Process Subtitle 18
 Ground Handling Basic Services Subtitle • Information Sharing Platform Component • – Provides methods to update data – Performs internal consistency checks of data • CFMU (Central Flow Management Unit) – Provides ELDT update of inbound flights • ATC (Air Traffic Control ) – Drives simulation by providing milestone events • Aircraft Operator / Ground Handler – Orchestrates turn around process – Triggers sub-services • Aircraft Crew – Report ready to ATC – Request startup 19
Ground Handling Basic Services Subtitle • Information Sharing Platform Component • – Provides methods to update data – Performs internal consistency checks of data • CFMU (Central Flow Management Unit) – Provides ELDT update of inbound flights • ATC (Air Traffic Control ) – Drives simulation by providing milestone events • Aircraft Operator / Ground Handler – Orchestrates turn around process – Triggers sub-services • Aircraft Crew – Report ready to ATC – Request startup 19
 Ground Handler Basic Services and Functions • Subtitle • Fuelling Service • Baggage Handling Service • Catering Service • Aircraft Cleaning Service • All triggered by aircraft operator or ground handler • Provide specific service within turn-around • Methods Ø Schedule and reschedule a service Ø Prepare for service delivery Ø Start service delivery Ø Provide status on remaining service time 20
Ground Handler Basic Services and Functions • Subtitle • Fuelling Service • Baggage Handling Service • Catering Service • Aircraft Cleaning Service • All triggered by aircraft operator or ground handler • Provide specific service within turn-around • Methods Ø Schedule and reschedule a service Ø Prepare for service delivery Ø Start service delivery Ø Provide status on remaining service time 20
 Ground Handling Workflow Execution Phase (austro control partner) Subtitle • 21
Ground Handling Workflow Execution Phase (austro control partner) Subtitle • 21
 Ground Handler Possible Services Workflow Disruption – Execution Phase Subtitle • Passenger no-show • Ø TOBT delayed, potentially resulting in new slot (CTOT) Ø Offload baggage • Landing of inbound aircraft delayed Ø Changes in workflow and service choice Ø Changes in TOBT (Targeted Off Block Time) • Ground handling resource problems • Heightened security status Ø Alternate workflow path Ø Reduced choice of service providers 22
Ground Handler Possible Services Workflow Disruption – Execution Phase Subtitle • Passenger no-show • Ø TOBT delayed, potentially resulting in new slot (CTOT) Ø Offload baggage • Landing of inbound aircraft delayed Ø Changes in workflow and service choice Ø Changes in TOBT (Targeted Off Block Time) • Ground handling resource problems • Heightened security status Ø Alternate workflow path Ø Reduced choice of service providers 22
 General SERSCIS Modeling Approach Subtitle The SERSCIS system modelling approach is based on: ü A generic dependability model - domain ontology - composed of OWL classes. : 1). This model captures generic types of SOA system assets such as: services, resources, customers, threats to those assets, and controls that can mitigate those threats. 2). The dependability model captures expertise in security of Service. Oriented Systems (SOA). 3) controls relevant to the Proof-of-Concept evaluation scenario, 23
General SERSCIS Modeling Approach Subtitle The SERSCIS system modelling approach is based on: ü A generic dependability model - domain ontology - composed of OWL classes. : 1). This model captures generic types of SOA system assets such as: services, resources, customers, threats to those assets, and controls that can mitigate those threats. 2). The dependability model captures expertise in security of Service. Oriented Systems (SOA). 3) controls relevant to the Proof-of-Concept evaluation scenario, 23
 SERSCIS Modeling Achieved Objectives Subtitle q. Development of modelling tools and models capturing üsystem requirements and interdependencies üsystem threats and vulnerabilities üsystem degradation and relevant countermeasures q. Development of system level models for CI in airports q. Provide a basis for wider application of the approach modelling 24
SERSCIS Modeling Achieved Objectives Subtitle q. Development of modelling tools and models capturing üsystem requirements and interdependencies üsystem threats and vulnerabilities üsystem degradation and relevant countermeasures q. Development of system level models for CI in airports q. Provide a basis for wider application of the approach modelling 24
 Creation of a new Semantic Dependability Modeling Approach and SERSCIS Ontology Subtitle New Domain Ontologies have been created : a critical infrastructure systems of systems ontology to model interdependencies of: airport services such as fuel, food, telecommunications, ATM, etc; (assets and dependabilities) a cause and effect ontology that models potential threats and consequences; a resource dependability metrics ontology that models the dynamic behavior of system entities. 25
Creation of a new Semantic Dependability Modeling Approach and SERSCIS Ontology Subtitle New Domain Ontologies have been created : a critical infrastructure systems of systems ontology to model interdependencies of: airport services such as fuel, food, telecommunications, ATM, etc; (assets and dependabilities) a cause and effect ontology that models potential threats and consequences; a resource dependability metrics ontology that models the dynamic behavior of system entities. 25
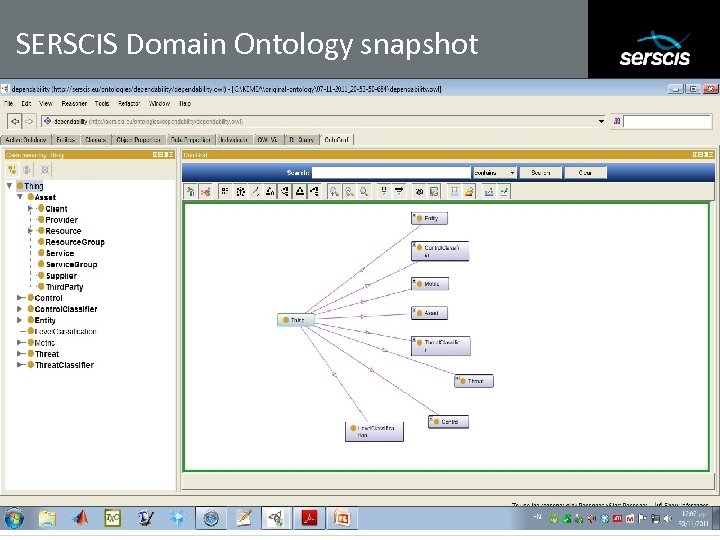 SERSCIS Domain Ontology snapshot Subtitle 05/08/2009 Copyright © 2008 University of Southampton IT Innovation Centre and other Members of the SERSCIS Consortium 26
SERSCIS Domain Ontology snapshot Subtitle 05/08/2009 Copyright © 2008 University of Southampton IT Innovation Centre and other Members of the SERSCIS Consortium 26
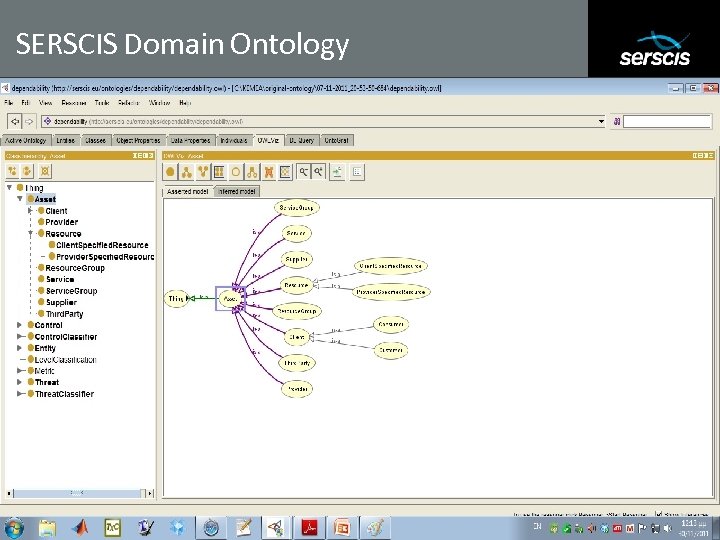 SERSCIS Domain Ontology Subtitle 05/08/2009 Copyright © 2008 University of Southampton IT Innovation Centre and other Members of the SERSCIS Consortium 27
SERSCIS Domain Ontology Subtitle 05/08/2009 Copyright © 2008 University of Southampton IT Innovation Centre and other Members of the SERSCIS Consortium 27
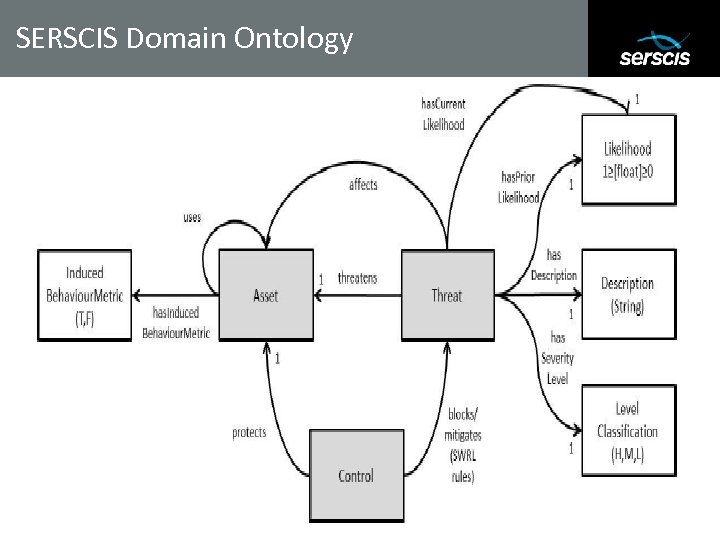 SERSCIS Domain Ontology Subtitle 05/08/2009 Copyright © 2008 University of Southampton IT Innovation Centre and other Members of the SERSCIS Consortium 28
SERSCIS Domain Ontology Subtitle 05/08/2009 Copyright © 2008 University of Southampton IT Innovation Centre and other Members of the SERSCIS Consortium 28
 SERSCIS Semantic Model Subtitle ü A core structure to model a system comprising assets, which may be subject to threats, and can be protected by controls; ü A dependability semantic model that describes generic types of assets, threats & controls using OWL classes, with their relationships; ü An abstract system semantic model that describes system-specific assets, threats and controls, extending the dependability model classes by incorporating system-specific security knowledge; ü A concrete system semantic model that provides snapshots of a running system, with instances to represent participating assets, plus contextualised threats and controls. 29
SERSCIS Semantic Model Subtitle ü A core structure to model a system comprising assets, which may be subject to threats, and can be protected by controls; ü A dependability semantic model that describes generic types of assets, threats & controls using OWL classes, with their relationships; ü An abstract system semantic model that describes system-specific assets, threats and controls, extending the dependability model classes by incorporating system-specific security knowledge; ü A concrete system semantic model that provides snapshots of a running system, with instances to represent participating assets, plus contextualised threats and controls. 29
 Core structure of the system modelling approach (Dependability Semantic Model) Subtitle The approach is designed to capture 3 -types of system entities: 1. generic asset classes: the types of assets that can be found in a system; 2. generic threat classes: ways in which these generic types of assets could be compromised; 3. generic control classes: describing the types of controls that could be used to protect these asset types from these threats. 30
Core structure of the system modelling approach (Dependability Semantic Model) Subtitle The approach is designed to capture 3 -types of system entities: 1. generic asset classes: the types of assets that can be found in a system; 2. generic threat classes: ways in which these generic types of assets could be compromised; 3. generic control classes: describing the types of controls that could be used to protect these asset types from these threats. 30
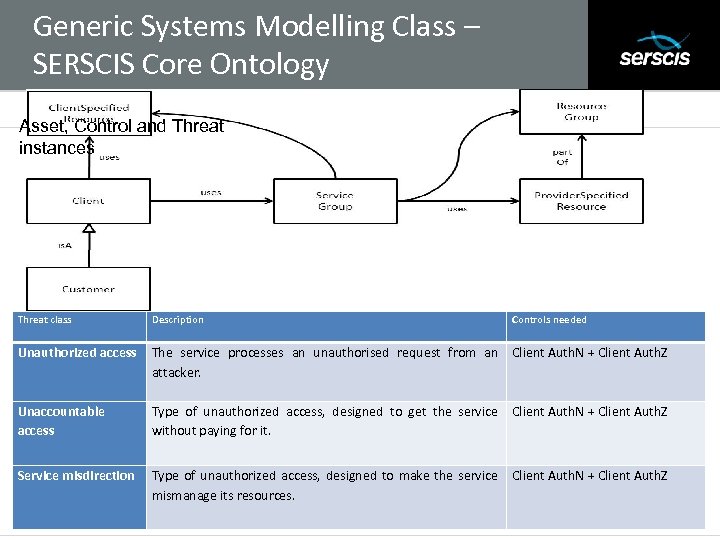 Generic Systems Modelling Class – SERSCIS Core Ontology Subtitle Asset, Control and Threat instances Threat class Description Controls needed Unauthorized access The service processes an unauthorised request from an Client Auth. N + Client Auth. Z attacker. Unaccountable access Type of unauthorized access, designed to get the service without paying for it. Client Auth. N + Client Auth. Z Service misdirection Type of unauthorized access, designed to make the service mismanage its resources. Client Auth. N + Client Auth. Z 31
Generic Systems Modelling Class – SERSCIS Core Ontology Subtitle Asset, Control and Threat instances Threat class Description Controls needed Unauthorized access The service processes an unauthorised request from an Client Auth. N + Client Auth. Z attacker. Unaccountable access Type of unauthorized access, designed to get the service without paying for it. Client Auth. N + Client Auth. Z Service misdirection Type of unauthorized access, designed to make the service mismanage its resources. Client Auth. N + Client Auth. Z 31
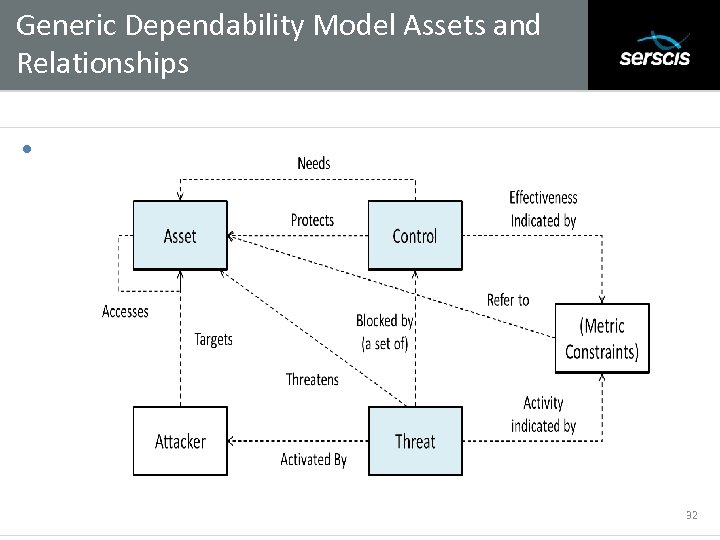 Generic Dependability Model Assets and Relationships Subtitle • 32
Generic Dependability Model Assets and Relationships Subtitle • 32
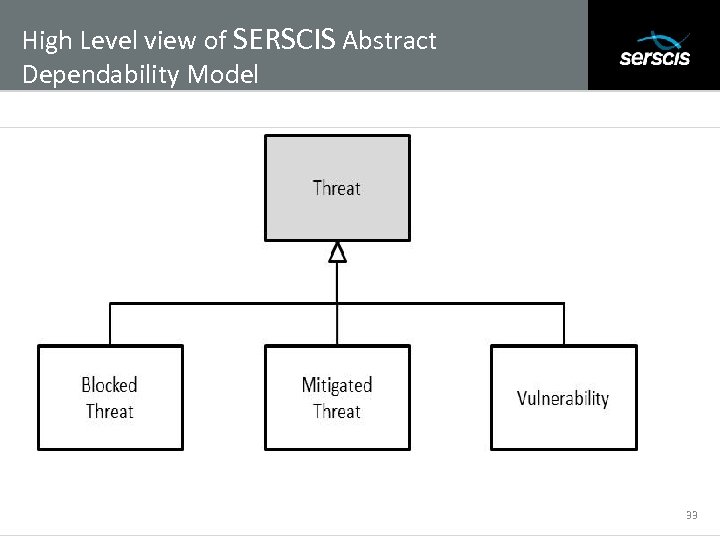 High Level view of SERSCIS Abstract Dependability Model Subtitle 33
High Level view of SERSCIS Abstract Dependability Model Subtitle 33
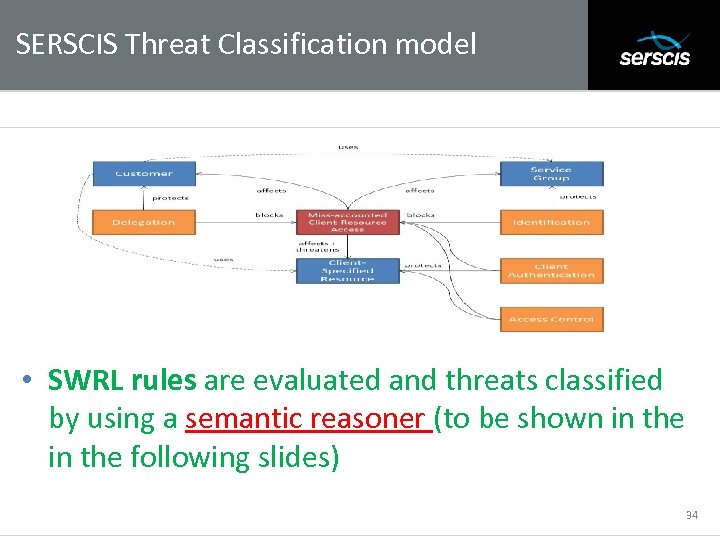 SERSCIS Threat Classification model Subtitle • SWRL rules are evaluated and threats classified by using a semantic reasoner (to be shown in the following slides) 34
SERSCIS Threat Classification model Subtitle • SWRL rules are evaluated and threats classified by using a semantic reasoner (to be shown in the following slides) 34
 High Level view of SERSCIS Abstract Dependability Model Subtitle • Services: Are Systems Components that provide services • Clients: Are Systems Components that access these services • Threat Types: 1. 2. 3. 4. 5. Unauthorized Access (to the service) Data traffic Snooping Man in the Middle Client Impersonation Resource Failure 35
High Level view of SERSCIS Abstract Dependability Model Subtitle • Services: Are Systems Components that provide services • Clients: Are Systems Components that access these services • Threat Types: 1. 2. 3. 4. 5. Unauthorized Access (to the service) Data traffic Snooping Man in the Middle Client Impersonation Resource Failure 35
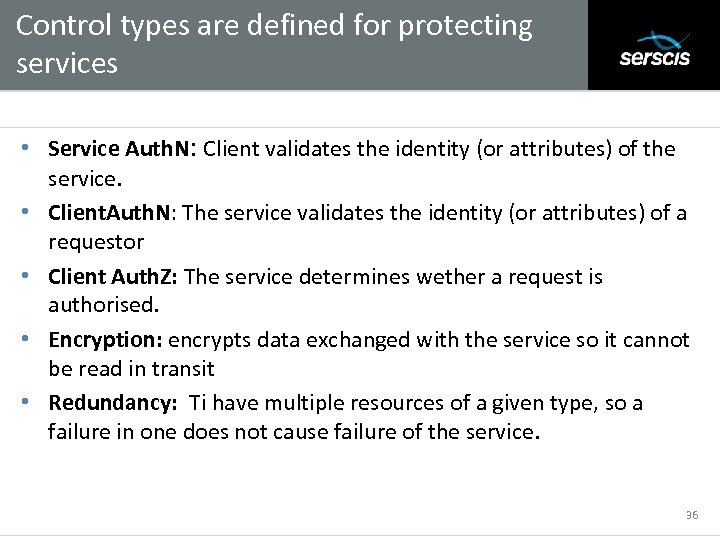 Control types are defined for protecting services Subtitle • Service Auth. N: Client validates the identity (or attributes) of the service. • Client. Auth. N: The service validates the identity (or attributes) of a requestor • Client Auth. Z: The service determines wether a request is authorised. • Encryption: encrypts data exchanged with the service so it cannot be read in transit • Redundancy: Ti have multiple resources of a given type, so a failure in one does not cause failure of the service. 36
Control types are defined for protecting services Subtitle • Service Auth. N: Client validates the identity (or attributes) of the service. • Client. Auth. N: The service validates the identity (or attributes) of a requestor • Client Auth. Z: The service determines wether a request is authorised. • Encryption: encrypts data exchanged with the service so it cannot be read in transit • Redundancy: Ti have multiple resources of a given type, so a failure in one does not cause failure of the service. 36
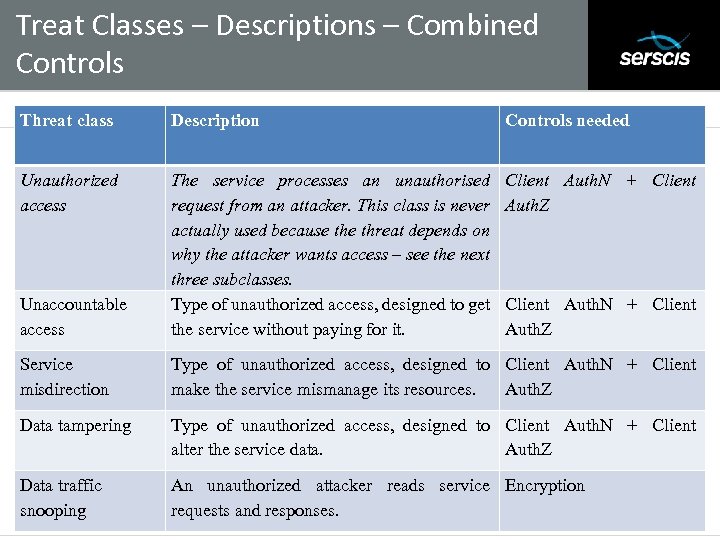 Treat Classes – Descriptions – Combined Controls Subtitle • Threat class Description Controls needed Client Auth. N + Client Auth. Z Unaccountable access The service processes an unauthorised request from an attacker. This class is never actually used because threat depends on why the attacker wants access – see the next three subclasses. Type of unauthorized access, designed to get the service without paying for it. Service misdirection Type of unauthorized access, designed to Client Auth. N + Client make the service mismanage its resources. Auth. Z Data tampering Type of unauthorized access, designed to Client Auth. N + Client alter the service data. Auth. Z Data traffic snooping An unauthorized attacker reads service Encryption requests and responses. Unauthorized access Client Auth. N + Client Auth. Z 37
Treat Classes – Descriptions – Combined Controls Subtitle • Threat class Description Controls needed Client Auth. N + Client Auth. Z Unaccountable access The service processes an unauthorised request from an attacker. This class is never actually used because threat depends on why the attacker wants access – see the next three subclasses. Type of unauthorized access, designed to get the service without paying for it. Service misdirection Type of unauthorized access, designed to Client Auth. N + Client make the service mismanage its resources. Auth. Z Data tampering Type of unauthorized access, designed to Client Auth. N + Client alter the service data. Auth. Z Data traffic snooping An unauthorized attacker reads service Encryption requests and responses. Unauthorized access Client Auth. N + Client Auth. Z 37
 Threat Vulnerability Classification Subtitle classifications are used as is shown previously 3 possible • • Blocked threat: if an attacker should carry out the threat (intentionally or otherwise), the system has controls that will prevent the attack from succeeding. • Mitigated threat: if an attacker should carry out the threat, the attack cannot be prevented, but the system controls provide a response that will counteract its effect on the targeted asset. • Vulnerability: the system does not have any means to prevent the attack or counteract its effects on the targeted system asset. 38
Threat Vulnerability Classification Subtitle classifications are used as is shown previously 3 possible • • Blocked threat: if an attacker should carry out the threat (intentionally or otherwise), the system has controls that will prevent the attack from succeeding. • Mitigated threat: if an attacker should carry out the threat, the attack cannot be prevented, but the system controls provide a response that will counteract its effect on the targeted asset. • Vulnerability: the system does not have any means to prevent the attack or counteract its effects on the targeted system asset. 38
 Threat Vulnerability Classification – Controlling a Miss. Accounted. Client. Resource. Access threat Subtitle • Classification is performed by semantic reasoning over the concrete system model, using SWRL rules from the SERSCIS dependability model • For example, the rules are : for Miss. Accounted. Client. Resource. Access (SWRL rules) • Miss. Accounted. Client. Resource. Access(? t) Client. Specified. Resource(? a 1) affects(? t, ? a 1) Customer(? t, ? a 2) affects(? t, ? a 2) Service. Group(? t, ? a 3) affects(? t, ? a 3) Client. Authentication(? c 1) protects(? c 1, ? a 1) Access. Control(? c 2) protects(? c 2, ? a 1) Delegation(? c 3) protects(? c 3, ? a 2) Identification(? c 4) protects(? c 4, ? a 3) Blocked. Threat (? t) 39
Threat Vulnerability Classification – Controlling a Miss. Accounted. Client. Resource. Access threat Subtitle • Classification is performed by semantic reasoning over the concrete system model, using SWRL rules from the SERSCIS dependability model • For example, the rules are : for Miss. Accounted. Client. Resource. Access (SWRL rules) • Miss. Accounted. Client. Resource. Access(? t) Client. Specified. Resource(? a 1) affects(? t, ? a 1) Customer(? t, ? a 2) affects(? t, ? a 2) Service. Group(? t, ? a 3) affects(? t, ? a 3) Client. Authentication(? c 1) protects(? c 1, ? a 1) Access. Control(? c 2) protects(? c 2, ? a 1) Delegation(? c 3) protects(? c 3, ? a 2) Identification(? c 4) protects(? c 4, ? a 3) Blocked. Threat (? t) 39
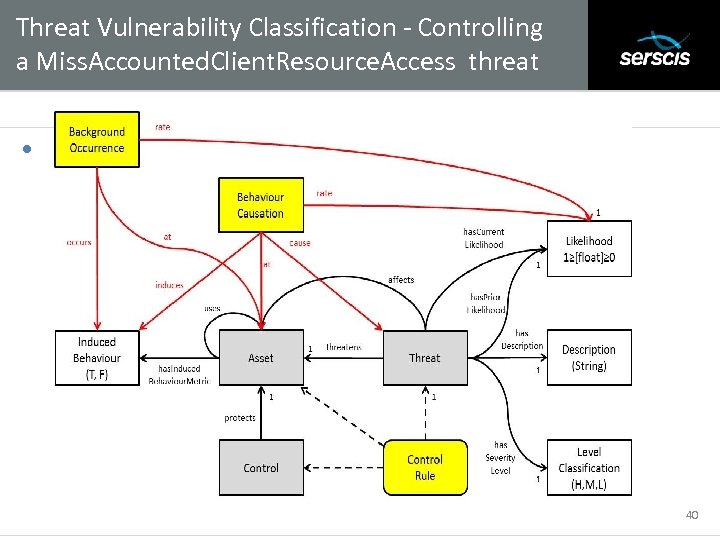 Threat Vulnerability Classification - Controlling a Miss. Accounted. Client. Resource. Access threat Subtitle • 40
Threat Vulnerability Classification - Controlling a Miss. Accounted. Client. Resource. Access threat Subtitle • 40
 Main ideas embodied in the SERSCIS Ontology Subtitle • Assets, threats and controls are described as OWL • • classes Assets may have associated metrics for presence or absence of threat-induced behaviors Threats have a human readable description, impact severity and prior & current likelihood ratings. In the following schematic dashed arrows does not represent a conventional OWL relationship but SWRL rules. These rules classify threat instances as: Mitigated or Blocked based on the presence of adequate controls. 41
Main ideas embodied in the SERSCIS Ontology Subtitle • Assets, threats and controls are described as OWL • • classes Assets may have associated metrics for presence or absence of threat-induced behaviors Threats have a human readable description, impact severity and prior & current likelihood ratings. In the following schematic dashed arrows does not represent a conventional OWL relationship but SWRL rules. These rules classify threat instances as: Mitigated or Blocked based on the presence of adequate controls. 41
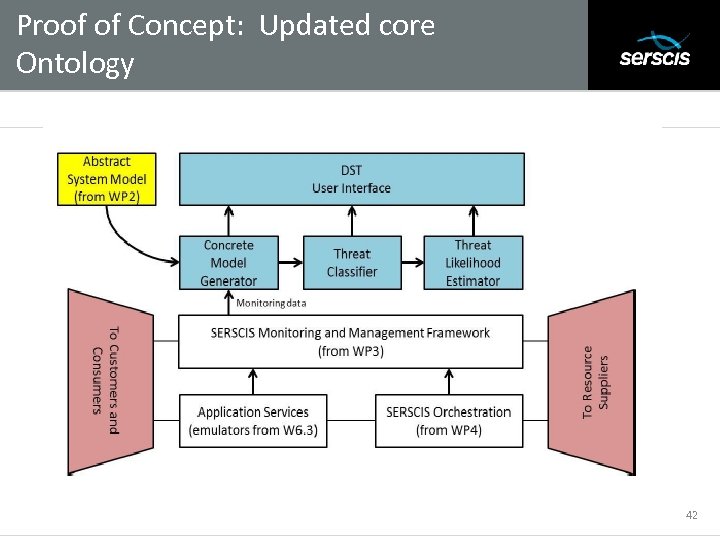 Proof of Concept: Updated core Ontology Subtitle 42
Proof of Concept: Updated core Ontology Subtitle 42
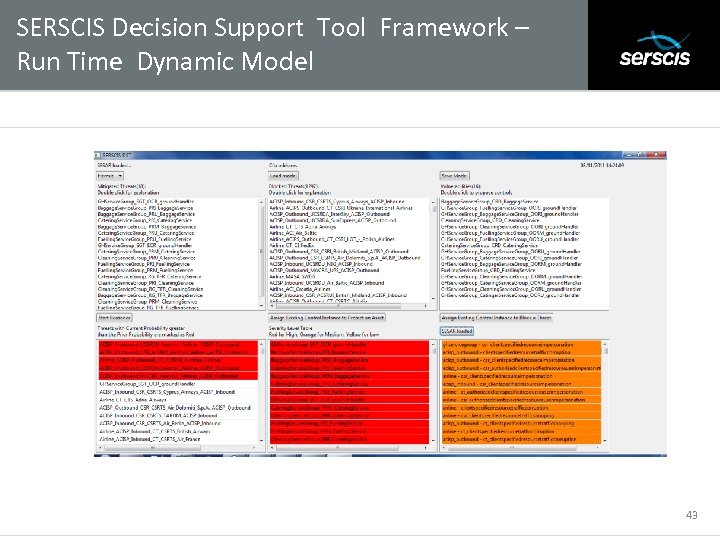 SERSCIS Decision Support Tool Framework – Run Time Dynamic Model Subtitle 43
SERSCIS Decision Support Tool Framework – Run Time Dynamic Model Subtitle 43
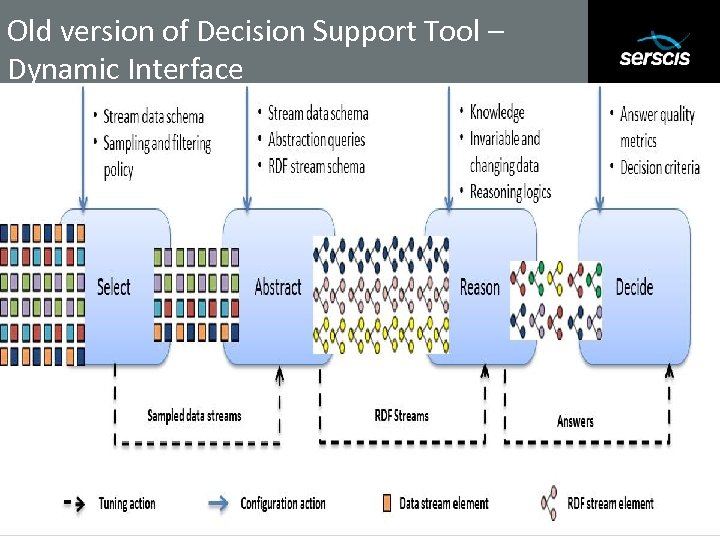 Old version of Decision Support Tool – Dynamic Interface Subtitle 44
Old version of Decision Support Tool – Dynamic Interface Subtitle 44
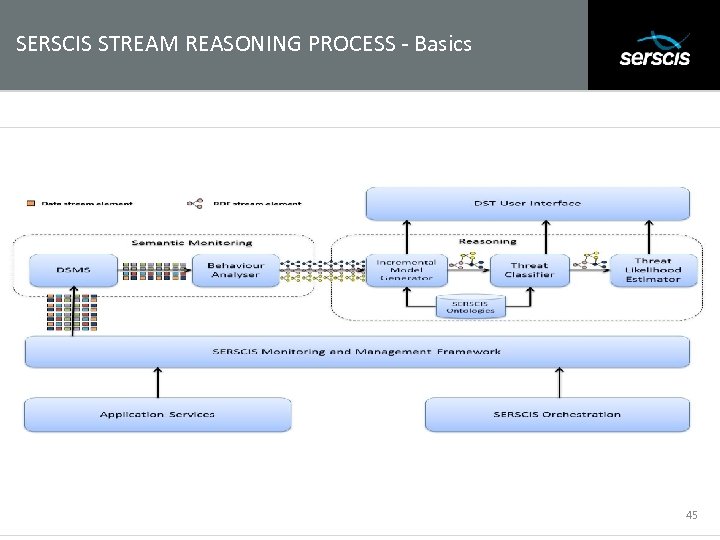 SERSCIS STREAM REASONING PROCESS - Basics Subtitle 45
SERSCIS STREAM REASONING PROCESS - Basics Subtitle 45
 SERSCIS STREAM REASONING PROCESS - Basics • Subtitle It allows the concrete system model to be continuously updated, • It reduces the time lag between the evolution of the real system and that of the concrete system model, making it possible to resolve recent and rapid changes in the real system; • It represents protracted as well as instantaneously observed behaviours in the model by including information over an extended (sliding) time window; • It allows reasoning algorithms to take account of system changes during the time window, target than only the instantaneous system composition and status. 46
SERSCIS STREAM REASONING PROCESS - Basics • Subtitle It allows the concrete system model to be continuously updated, • It reduces the time lag between the evolution of the real system and that of the concrete system model, making it possible to resolve recent and rapid changes in the real system; • It represents protracted as well as instantaneously observed behaviours in the model by including information over an extended (sliding) time window; • It allows reasoning algorithms to take account of system changes during the time window, target than only the instantaneous system composition and status. 46
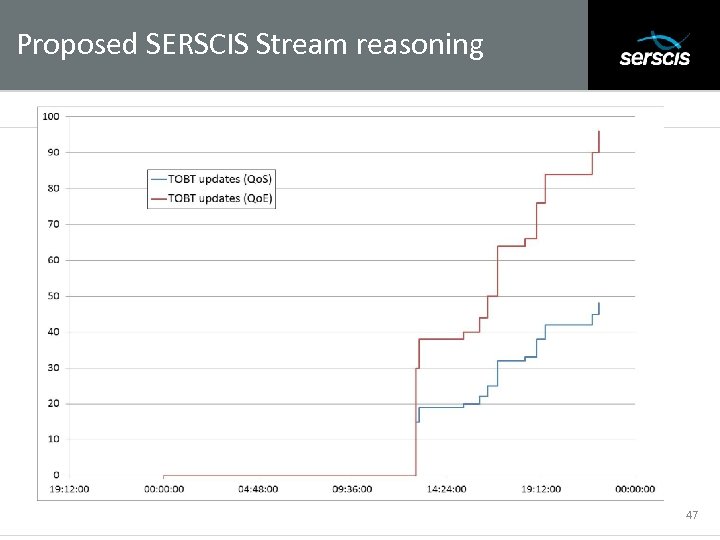 Proposed SERSCIS Stream reasoning Subtitle 47
Proposed SERSCIS Stream reasoning Subtitle 47
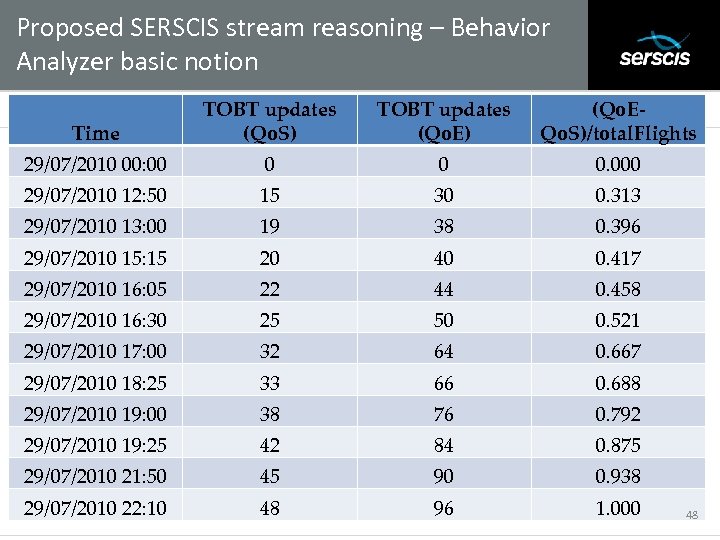 Proposed SERSCIS stream reasoning – Behavior Analyzer basic notion Time TOBT updates (Qo. S) TOBT updates (Qo. E) (Qo. EQo. S)/total. Flights 29/07/2010 00: 00 0 0 0. 000 29/07/2010 12: 50 15 30 0. 313 29/07/2010 13: 00 19 38 0. 396 29/07/2010 15: 15 20 40 0. 417 29/07/2010 16: 05 22 44 0. 458 29/07/2010 16: 30 25 50 0. 521 29/07/2010 17: 00 32 64 0. 667 29/07/2010 18: 25 33 66 0. 688 29/07/2010 19: 00 38 76 0. 792 29/07/2010 19: 25 42 84 0. 875 29/07/2010 21: 50 45 90 0. 938 29/07/2010 22: 10 48 96 1. 000 Subtitle 48
Proposed SERSCIS stream reasoning – Behavior Analyzer basic notion Time TOBT updates (Qo. S) TOBT updates (Qo. E) (Qo. EQo. S)/total. Flights 29/07/2010 00: 00 0 0 0. 000 29/07/2010 12: 50 15 30 0. 313 29/07/2010 13: 00 19 38 0. 396 29/07/2010 15: 15 20 40 0. 417 29/07/2010 16: 05 22 44 0. 458 29/07/2010 16: 30 25 50 0. 521 29/07/2010 17: 00 32 64 0. 667 29/07/2010 18: 25 33 66 0. 688 29/07/2010 19: 00 38 76 0. 792 29/07/2010 19: 25 42 84 0. 875 29/07/2010 21: 50 45 90 0. 938 29/07/2010 22: 10 48 96 1. 000 Subtitle 48
 Evolution of Qo. S and Qo. E in time Subtitle 49
Evolution of Qo. S and Qo. E in time Subtitle 49
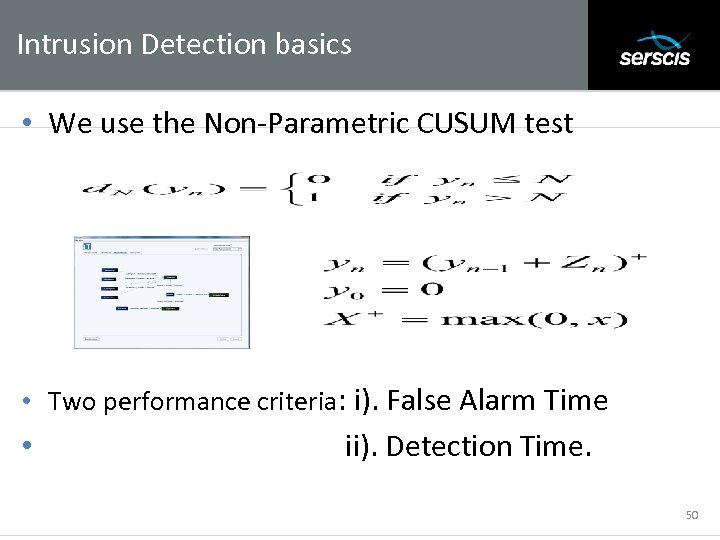 Intrusion Detection basics Subtitle • We use the Non-Parametric CUSUM test • Two performance criteria: i). False Alarm Time • ii). Detection Time. 50
Intrusion Detection basics Subtitle • We use the Non-Parametric CUSUM test • Two performance criteria: i). False Alarm Time • ii). Detection Time. 50
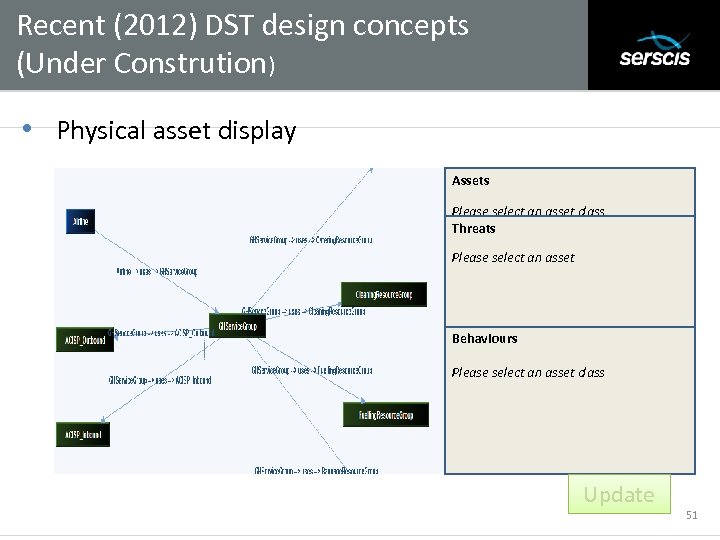 Recent (2012) DST design concepts (Under Constrution) Subtitle • Physical asset display Assets Please select an asset class Threats Please select an asset Behaviours Please select an asset class Up to date Update 51
Recent (2012) DST design concepts (Under Constrution) Subtitle • Physical asset display Assets Please select an asset class Threats Please select an asset Behaviours Please select an asset class Up to date Update 51
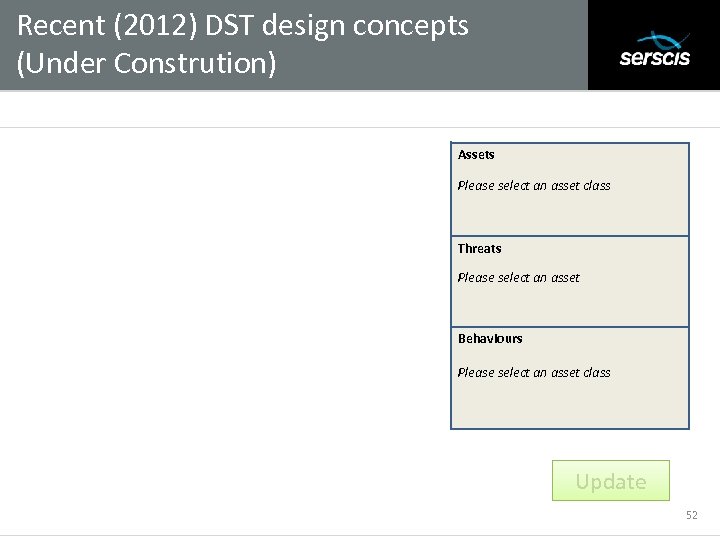 Recent (2012) DST design concepts (Under Constrution) Subtitle Assets Please select an asset class Threats Please select an asset Behaviours Please select an asset class Update 52
Recent (2012) DST design concepts (Under Constrution) Subtitle Assets Please select an asset class Threats Please select an asset Behaviours Please select an asset class Update 52
 SERSCIS INNOVATIONS • Semantic system modelling of critical infrastructure ICT including inter. Subtitle dependency and other risks • Semantic service dependability models encoded in SLA üsemi-automatic management of services against dependability criteria • Semantic service orchestration models exploiting dependability criteria üautomatic composition of service inter-connections against dependability criteria üautomated re-composition in response to dependability threats • Dynamic security and trust management to control threat propagation between services üautomatic policy updates driven by service dependability management • Advanced Decision support interface based on semantic system models to assist human operators • Innovative Stream reasoning technologies for Event Analytics and Behavior Assets Reasoning in conjunction with detection algorithms. 53
SERSCIS INNOVATIONS • Semantic system modelling of critical infrastructure ICT including inter. Subtitle dependency and other risks • Semantic service dependability models encoded in SLA üsemi-automatic management of services against dependability criteria • Semantic service orchestration models exploiting dependability criteria üautomatic composition of service inter-connections against dependability criteria üautomated re-composition in response to dependability threats • Dynamic security and trust management to control threat propagation between services üautomatic policy updates driven by service dependability management • Advanced Decision support interface based on semantic system models to assist human operators • Innovative Stream reasoning technologies for Event Analytics and Behavior Assets Reasoning in conjunction with detection algorithms. 53
 CONCLUSIONS- IMPACT Subtitle Airport Collaborative Decision Making – (A-CDM) üsharing information between air-traffic control, airports, airlines and airport service providers üallows greater operational efficiency, but also creates interdependencies that need to be managed SERSCIS will enable improved risk management ügoal is not to enable A-CDM, but to better manage it üIntroduction of state of the art risk analysis procedures üStream reasoning processes and event processing in risk management Other applications will be considered (especially Port Community Operations) Expected impact ügreater awareness of risks in A-CDM especially from interdependency analysis of requirements and application in other sectors ünovel risk management capabilities based on agile SOA especially for managing interdependency and cascading threats 54
CONCLUSIONS- IMPACT Subtitle Airport Collaborative Decision Making – (A-CDM) üsharing information between air-traffic control, airports, airlines and airport service providers üallows greater operational efficiency, but also creates interdependencies that need to be managed SERSCIS will enable improved risk management ügoal is not to enable A-CDM, but to better manage it üIntroduction of state of the art risk analysis procedures üStream reasoning processes and event processing in risk management Other applications will be considered (especially Port Community Operations) Expected impact ügreater awareness of risks in A-CDM especially from interdependency analysis of requirements and application in other sectors ünovel risk management capabilities based on agile SOA especially for managing interdependency and cascading threats 54
 Subtitle SE THANK YOU for your attention Email: tsoulkas. kemea@gmail. com 55
Subtitle SE THANK YOU for your attention Email: tsoulkas. kemea@gmail. com 55


