4eadb28f09a3cfc08f7ab43d05036386.ppt
- Количество слайдов: 49

Electronic Society Public Policy: Control of the Internet Computing Science, University of Aberdeen 1

Overview Public Policy l Brief history of Internet l Hardware, Software, Standards. Domain names l Who should control the net/web? l http: //en. wikipedia. org/wiki/Internet_governance Computing Science, University of Aberdeen 2

Public Policy l l ``Public policy as government action is generally the principled guide to action taken by the administrative or executive branches of the state with regard to a class of issues in a manner consistent with law and institutional customs’’ or "courses of action, regulatory measures, laws, and funding priorities concerning a given topic promulgated by a governmental entity or its representatives. ” http: //en. wikipedia. org/wiki/Public_policy l l Whose interests does it serve? Whose interests should it serve? Computing Science, University of Aberdeen 3
Control of Internet l l Internet/Web is very important to modern life. Who controls it? » » » Specifies protocols Decides who can use/connect to it Specifies what activities are lawful/unlawful Gives out domain names Taxes it Etc. Computing Science, University of Aberdeen 4

Internet Governance l Suggested definition by World Summit on the Information Society (2005) ``Internet governance is the development and application by Governments, the private sector and civil society, in their respective roles, of shared principles, norms, rules, decisionmaking procedures, and programmes that shape the evolution and use of the Internet. ’’ l Ongoing interest at high-level, e. g. , the Internet Govenance Forum (IGF) sponsored by UN. Computing Science, University of Aberdeen 5
What is it? l Global network of computers. » The internetwork - a network of networks l Use shared protocols to communicate. » Currently, TCP/IP, a. k. a. the Internet Protocol Suite l Specific services sit on top of TCP/IP. Computing Science, University of Aberdeen 6

Prehistory l Telecomms networks » » » l … Transatlantic telephone cable 1859 Telephone, 1876 1909, Erlang invents Queuing Theory 1940 -60’s control of mainframes via terminals connected by wires. 1950’s and 60’s: » US military people worry about robust comm’s » Engineers and others dream of possibilities Computing Science, University of Aberdeen 7
Prehistory l Packet Switching: 1960’s » Transmission of data in packets of suitable, fixed size. » Paul Baran: reliable communications across unreliable network (robustness) » Donald Davies (UK): efficient use of channels (channel capacity) » Leonard Kleinrock: queuing theory of packet switchng » Optimizes latency: time for data to travel across network » First computer network implementation 1968 » First ARPANET message sent October 1969. Computing Science, University of Aberdeen 8
ARPANet Computing Science, University of Aberdeen 9
Brief history: 1970 s l ARPANet » first long-distance network » connected universities, military research labs. » US military owned and controlled it. l Protocols and standards start to develop » 1974 -ish: Vint Cerf and Bob Kahn develop TCP/IP. Computing Science, University of Aberdeen 10
1980 s: Multiple networks l Many more networks appeared » VNet: Internal IBM network – University offshoot: Bitnet, earn » JANet: UK universities » UUNet: cheap “network” formed using telephone dialup lines » Etc l Mostly email, not real-time client-server Computing Science, University of Aberdeen 11
1980 s: Internet Emerges l Connected together all of these networks into a global “Internet” » Virtual network, which combined ARPANet, VNet, JANet, etc – ARPANet user could easily email JANet, etc » Mostly based on protocols and conventions from US military » That is, everyone else changed to what the US military was doing » Everyone starts to use TCP/IP. l Internet Engineering Task Force (IETF): promotes standards Computing Science, University of Aberdeen 12
Integration example: email addresses l ARPANet: f. guerin@abdn. ac. uk l JANet: matthew. collinson@uk. ac. abdn l l collinson@UUNET: network path, e. g. , » fred. bloggs!aberdeen!dundee!edinburgh » Send email first to Edinburgh, then to Dundee, then to Aberdeen, then to fred. bloggs Everyone switched to ARPANet style Computing Science, University of Aberdeen 13
1980 s: control l l Who controlled the Internet in 1980 s? No-one controlled net as a whole » IBM controlled VNET » UK govt controlled JANet » UUNet nodes controlled themselves l l People switched to ARPANet standards because wanted to, their choice ARPANet replaced by NSFNet » Still US government. Computing Science, University of Aberdeen 14
Late ‘ 80 s, early ‘ 90 s: Integration l By about 1990 the integration efforts succeed » 1990 s internet truly looks like an integrated network to its users, not patchwork of hundreds of separate networks. » The High Performance Computing Act (Gore Bill) 1991: develop US National Information Infrastructure (Information Superhighway) integration, fiber-optics, Mosaic. Computing Science, University of Aberdeen 15

1990 s: ISPs l Internet Service Providers (ISP) formed. » Access to internet possible without going through university, research lab, military etc. Computing Science, University of Aberdeen 16

1990 s: World Wide Web l WWW invented in early 1990 s » A network of hypertext documents accessed via internet. » Proposal written by Tim Berners-Lee of CERN in 1989. » Developed by Berners-Lee and collaborators. » Services start to become available in 1991. » Web-browsers (http) – World. Wide. Web (Nexus), Viola. WWW, Mosaic, 1993. Computing Science, University of Aberdeen 17
1990 s World Wide Web Consortium, W 3 C, (international) quickly established (1994, Tim Berners-Lee at MIT) l Sets standards l – Technical: protocols, languages – Internationalization: should be accessible to all languages and cultures l Higher priority for standards because Web invented in Europe, instead of US? Computing Science, University of Aberdeen 18

1990 s: Commerce l Banned from ARPANet, then NSFNet » Some commercial ISPs and commerce on other networks. l 1992: US Congress passes Scientific and Advanced Technology Act. » Commerce then allowed. Computing Science, University of Aberdeen 19
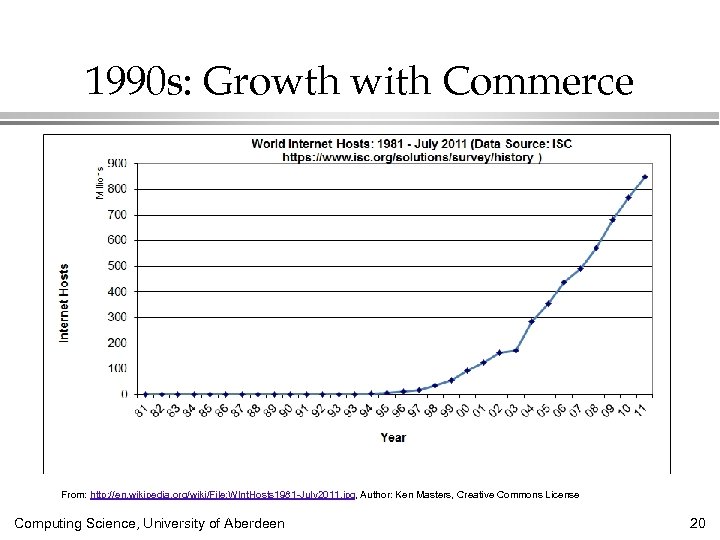
1990 s: Growth with Commerce From: http: //en. wikipedia. org/wiki/File: WInt. Hosts 1981 -July 2011. jpg, Author: Ken Masters, Creative Commons License Computing Science, University of Aberdeen 20

Commercial Importance l Largely because of Web, Internet became of much greater commercial interest » Dot. com boom » Domain names selling for $s – $7. 5 M for business. com (more for porn. com) » Beginnings of spam Computing Science, University of Aberdeen 21

1990 s: Who in control? Most control still resided with individual component networks. l International organisations increasingly set standards. l » W 3 C, IETF, ICANN (later slide), ISO » Lawyers increasingly involved – Lawsuits on domain names; e. g. , mcdonalds. com Computing Science, University of Aberdeen 22

2000 s: Internet essential l Many organizations rely on Internet » Insist that people use it. » E-gov’t, E-commerce, E-Science, etc. » Supply chains rely on it. » Banking, finance, payment systems. l Internet needs to work! » Must be fast, reliable, trusted, etc. Computing Science, University of Aberdeen 23

2000 s: Attackers l Huge growth in spam email » Dominates most inboxes » Makes email less reliable/useful – Anti-spam systems kill real emails » Also phishing (con emails) l Huge growth in viruses » Many computers taken over by attackers. Computing Science, University of Aberdeen 24

2000 s l Companies take security seriously » 1990 s: Microsoft treats computer security as marketing tool, to encourage upgrades – Questionnable whether it seriously tries to make software more secure. » 2000 s: Microsoft takes security very seriously. » Relative obscurity of Mac OS protects it. Computing Science, University of Aberdeen 25

Governance problems l Hard to stop bad guys when there is so little control over the net. » Change protocols – slow? » Spamming illegal – no international control? » Blacklist bad guys so can’t use – how? l Does global Internet community have a duty to help poor countries? » E. g. , help pay for East Africa fibre. Computing Science, University of Aberdeen 26
What is Internet/Web Hardware: routers, fibre-optic links, … l Software: browsers, servers, … l Standards: HTTP, HTML, … l Domain names l l People and organizations Computing Science, University of Aberdeen 27

Hardware l Routers, fibre-optic links, etc still owned by individual organizations, networks. » Individuals: you own your wireless router and (say) the network in your house. » Organizations: Aberdeen Uni. owns campus Ethernet wiring. » ISP/telecom: BT owns copper wires from your house, switches. » Govt: JANet (and Super. JANet) owns link between Aberdeen Uni. and Dundee Uni. Computing Science, University of Aberdeen 28
Hardware l l Very diverse ownership Internet backbone: high-speed data routes has multiple owners National infrastructure: LINX (more or less) provides central hardware for UK Almost no central hardware for Internet as a whole » root nameservers (resolve domain names into IP adresses) » Provided by LINX-like national sites Computing Science, University of Aberdeen 29

LINX l London Internet Exchange » http: //www. linx. net/ » Cooperative of UK ISPs Interconnect point for UK ISPs, International connections l Support services: name/time server l » Service to Internet as a whole Computing Science, University of Aberdeen 30

Control of Hardware l Who can plug hardware into Internet? » Anyone who can convince an organization which is currently on the net to link to you. – Person/company: convince ISP to connect you. – ISP: convince LINX to connect you. » Of course governments can regulate what happens in their countries. – Recent proposal in UK to require explicit opt-in by consumers for porn access. » Enforcement? Computing Science, University of Aberdeen 31

Hardware Anarchy l Surprising it works as well as it does. » Tribute to tech-support personnel keeping their bit of the Internet going. » Even more so to inventors of packetswitching, and other robust protocols. l Lack of control helps criminals (e. g. spammers)? » Always find someone to connect them to the net. Computing Science, University of Aberdeen 32

Software Environment l We need software to use the Internet and web. » Web browsers: Safari, Internet Explorer, Firefox, » Web server: Apache (C), Apache Tomcat (Java), » Apache Software Foundation, open community » Apache License, open source » OS support in Windows, Mac OS X, i. OS, Linux, Android, …. l Controlled by developers » Commercial: IE, Outlook, Safari, Entourage, … » Open-source: Unix, Tomcat, Firefox, …. » Mac OS and i. OS commercial, but based on Unix. Computing Science, University of Aberdeen 33

Control via Software l Can a commercial vendor control the Internet through its software? » If everyone uses IE, Microsoft can “tweak” IE to encourage people to use its products » IE bundled with Windows OS. – Antitrust case. United States vs. Microsoft (19982001 ish). Settled with US Do. J. » Recent change to IE. Default search engine. Deliberately difficult to change. » Deliberately degrade browsing on competitor websites. Computing Science, University of Aberdeen 34

Control via Software l Seems less of a problem now, because of blossoming of open-source » Apache, Tomcat, Firefox, Opera, etc. l Net software becoming more of a shared resource, less of a commercial product » Much harder for one individual or organization to control! Computing Science, University of Aberdeen 35

Standards l Standards are essential to Internet » Document formats: HTML, XML, PDF, GIF » Protocols: HTTP, HTTPS, SMTP, … » Low-level: TCP/IP » Other: Java, Unicode, … l Who controls these? Computing Science, University of Aberdeen 36
Protocols mostly controlled by international standards organizations l W 3 C consortium (web) l » http: //www. w 3. org/ » Most web protocols (e. g. , HTTP) l IETF (Internet) » http: //www. ietf. org/ » TCP/IP, other plumbing Computing Science, University of Aberdeen 37
Document Formats l l W 3 C controls many web ones » HTML, XML, RDF, OWL, …. Other standards bodies » PDF (open, ISO committee, since 2008), » JPEG (ISO committee, but patent situation complicated) » MPEG (ISO committee) Some controlled commercially » WMF graphics: Microsoft No one controls » GIF: Developed by Compuserve in 1980 s, now in public domain. Computing Science, University of Aberdeen 38
Commercial Formats l Is it OK for Adobe to control PDF, which is a de facto standard for the web? » Enables Adobe to sell related software? l Adobe has now made PDF an ISO standard » As of 1 Jul 2008 l Trend for most widely-used formats Computing Science, University of Aberdeen 39

Java l l Who controls Java programming language? Oracle » Bought SUN, the original developer » Hold trademark » Tried to control/restrict competitors – Especially MS – Sun vs. Microsoft – MS created C# instead… Now moving to open-source, standards. Apple just announced ‘deprecation’ of Java. » Have to download separately with OS X 10. 7. Computing Science, University of Aberdeen 40

Standards l 1990 s: there was a lot of concern about commercial control of standards » Java, PDF, GIF l Now trend is towards open standards controlled by international bodies. Computing Science, University of Aberdeen 41
Domain Names l Who controls internet names? » Which company is business. com? l Internet Corporation for Assigned Names and Numbers, ICANN, http: //www. icann. org/ » Decides on top-level domain names, such as. com » International body, not-for-profit, public-benefit, self -appointed? » IANA, part of ICANN ``The Internet Assigned Numbers Authority (IANA) is responsible for the global coordination of the DNS Root, IP addressing, and other Internet protocol resources’’ Computing Science, University of Aberdeen 42

Domain names l Verisign (company) controls. com » Under contract from US government. » Why should US govt control? l Nominet controls. uk » Private not-for-profit company l Country domain names often controlled by national telecomms » http: //www. iana. org/domains/root/db/ Computing Science, University of Aberdeen 43
Domain names l l l Security problems DNS Cache Poisoning: corrupt data fed into Domain Name System – directs traffic to wrong address. Border Gateway Protocol: handles core routing decisions. » Hijacking – corrupt routing tables of BGP: sends traffic to wrong address. l l Security extensions proposed. DNS root name servers (logical clusters). Many in the US. Until recently only 13. Now 200+. » Have been under DDo. S attack. Computing Science, University of Aberdeen 44
Domain Name Control Domain Name System (1983 ish) l Historical artefact. l » E. g. , US has top-level control because we use ARPANet names l Under review? Computing Science, University of Aberdeen 45

Who controls Internet? Hardware: decentralized, anarchic l Software: increasingly open-source l Protocols: increasingly international standards bodies l Domain names: mixture l Computing Science, University of Aberdeen 46

Who should control net? l No one (anarchy)? » Governments control within their country? » No one controls net as a whole? Self-appointed committees (e. g. , W 3 C)? l UN body? l Computing Science, University of Aberdeen 47

UN Internet Agency? l Should an international body be set up to exercise global control over the Internet? » Control standards, domain names? » Provide open-source software? » Under UN control? – 2005 working group, set up by sec. -gen. Annan l Good idea or bad idea? Computing Science, University of Aberdeen 48

In the news … l http: //www. guardian. co. uk/technology/2 012/oct/17/who-rules-internet Computing Science, University of Aberdeen 49
4eadb28f09a3cfc08f7ab43d05036386.ppt