06af1d0e7d6ff819cbc791bfb5b4f03e.ppt
- Количество слайдов: 14

Electronic Flight Bag Security Use Case and Aircraft Security Simulator Presented by: Chris Riley, CISSP (DOT/Volpe) Photos: Corel, Photodisk; Comstock; DOT 1

Electronic Flight Bag Threat Assessment
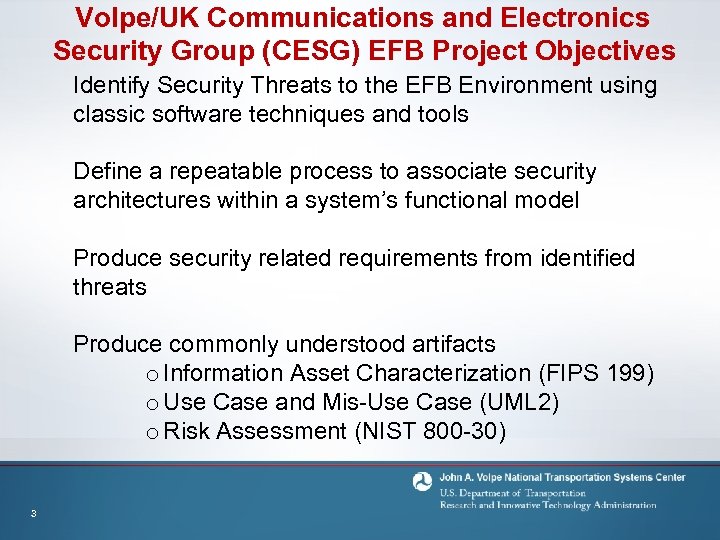
Volpe/UK Communications and Electronics Security Group (CESG) EFB Project Objectives Identify Security Threats to the EFB Environment using classic software techniques and tools Define a repeatable process to associate security architectures within a system’s functional model Produce security related requirements from identified threats Produce commonly understood artifacts o Information Asset Characterization (FIPS 199) o Use Case and Mis-Use Case (UML 2) o Risk Assessment (NIST 800 -30) 3
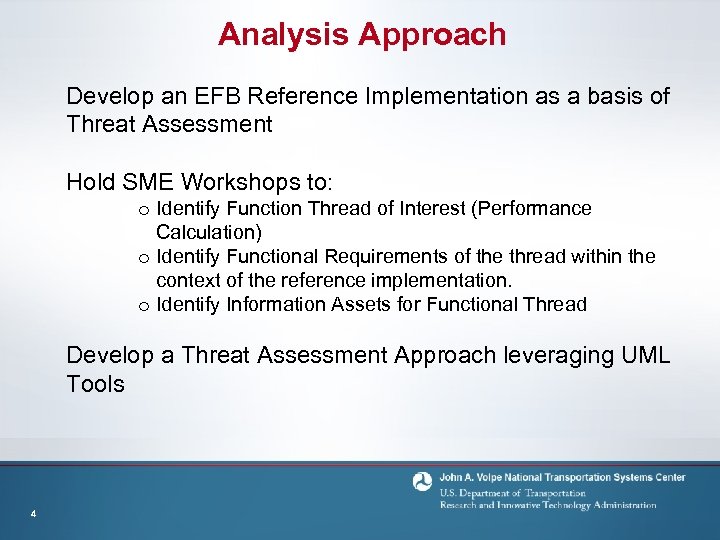
Analysis Approach Develop an EFB Reference Implementation as a basis of Threat Assessment Hold SME Workshops to: o Identify Function Thread of Interest (Performance Calculation) o Identify Functional Requirements of the thread within the context of the reference implementation. o Identify Information Assets for Functional Thread Develop a Threat Assessment Approach leveraging UML Tools 4
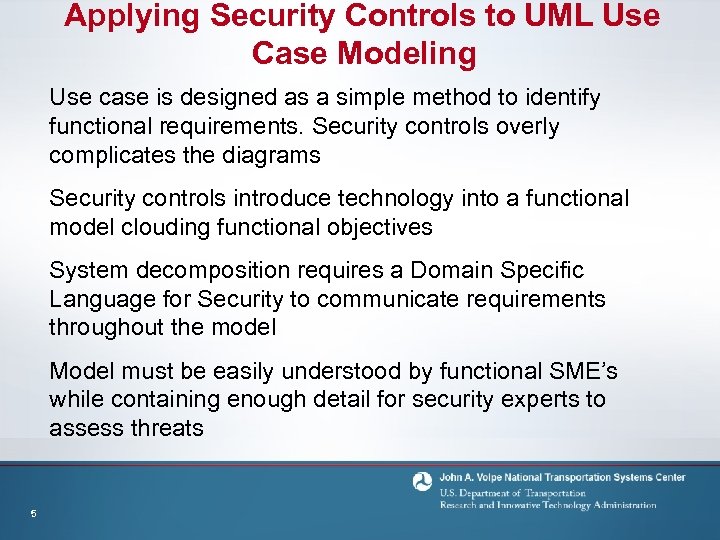
Applying Security Controls to UML Use Case Modeling Use case is designed as a simple method to identify functional requirements. Security controls overly complicates the diagrams Security controls introduce technology into a functional model clouding functional objectives System decomposition requires a Domain Specific Language for Security to communicate requirements throughout the model Model must be easily understood by functional SME’s while containing enough detail for security experts to assess threats 5
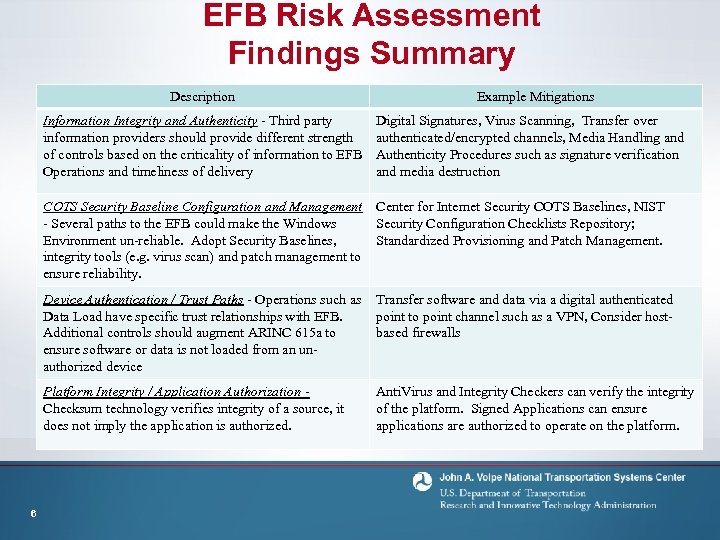
EFB Risk Assessment Findings Summary Description Information Integrity and Authenticity - Third party information providers should provide different strength of controls based on the criticality of information to EFB Operations and timeliness of delivery Example Mitigations Digital Signatures, Virus Scanning, Transfer over authenticated/encrypted channels, Media Handling and Authenticity Procedures such as signature verification and media destruction COTS Security Baseline Configuration and Management Center for Internet Security COTS Baselines, NIST - Several paths to the EFB could make the Windows Security Configuration Checklists Repository; Environment un-reliable. Adopt Security Baselines, Standardized Provisioning and Patch Management. integrity tools (e. g. virus scan) and patch management to ensure reliability. Device Authentication / Trust Paths - Operations such as Data Load have specific trust relationships with EFB. Additional controls should augment ARINC 615 a to ensure software or data is not loaded from an unauthorized device Platform Integrity / Application Authorization Checksum technology verifies integrity of a source, it does not imply the application is authorized. 6 Transfer software and data via a digital authenticated point to point channel such as a VPN, Consider hostbased firewalls Anti. Virus and Integrity Checkers can verify the integrity of the platform. Signed Applications can ensure applications are authorized to operate on the platform.

Airborne Network Security Simulator (ANSS)

Phase 2: Airborne Network Security Simulator (ANSS) Goals • Identify potential information security threats in synthetic environment by simulating next generation aircraft communications systems. • Share knowledge, tools and methodologies with academia and other interested stakeholders to extend research value. • Act as coordinating authority for cyber security risk mitigation within the international aerospace & aviation community. • Recommend appropriate technical & procedural standards for security risks to aid in the development of regulatory guidelines and policies. • Influence industry bodies on cyber security best practice with respect to specifications, procedures, and recommendations used by the industry. 8
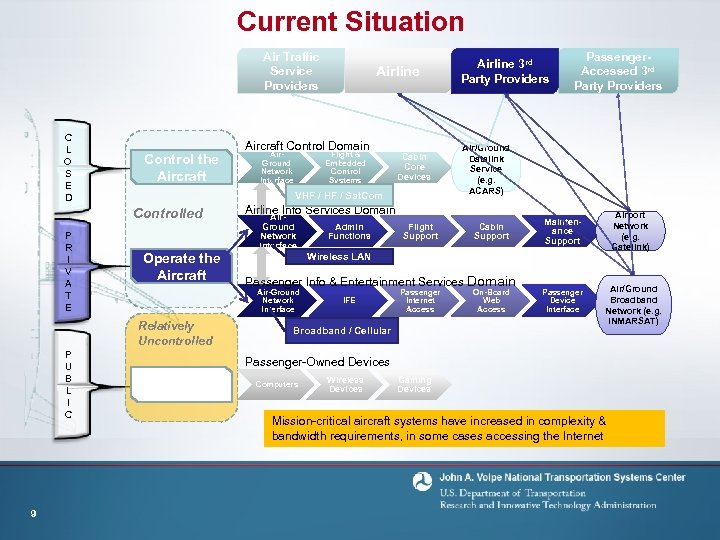
Current Situation Air Traffic Service Providers C L O S E D Control the Aircraft Operate the Aircraft 9 Air. Ground Network Interface Flight & Embedded Control Systems Airline Info Services Domain Air. Ground Network Interface Cabin Core Devices Admin Functions Flight Support Passenger. Accessed 3 rd Party Providers Air/Ground Datalink Service (e. g. ACARS) Cabin Support Airport Network (e. g. Gatelink) Maintenance Support Wireless LAN Passenger Info & Entertainment Services Domain Air-Ground Network Interface Relatively Uncontrolled P U B L I C Aircraft Control Domain VHF / Sat. Com Controlled P R I V A T E Airline 3 rd Party Providers IFE Passenger Internet Access Broadband / Cellular On-Board Web Access Passenger Device Interface Air/Ground Broadband Network (e. g. INMARSAT) Passenger-Owned Devices Passenger Use Computers Wireless Devices Gaming Devices Mission-critical aircraft systems have increased in complexity & bandwidth requirements, in some cases accessing the Internet
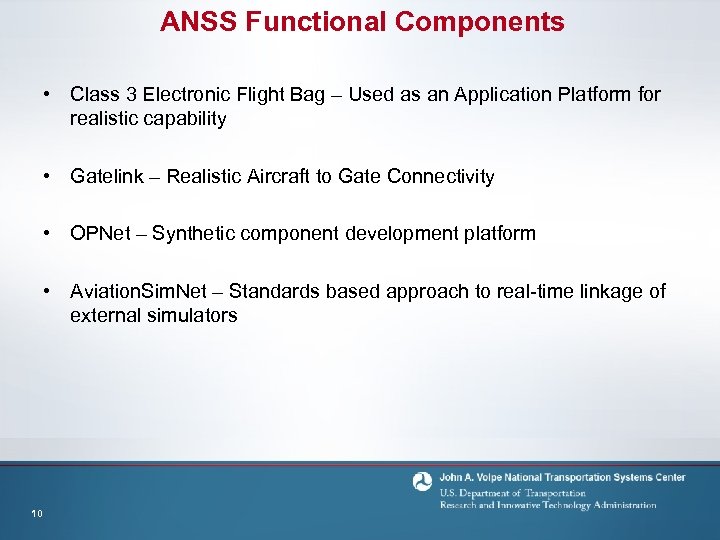
ANSS Functional Components • Class 3 Electronic Flight Bag – Used as an Application Platform for realistic capability • Gatelink – Realistic Aircraft to Gate Connectivity • OPNet – Synthetic component development platform • Aviation. Sim. Net – Standards based approach to real-time linkage of external simulators 10
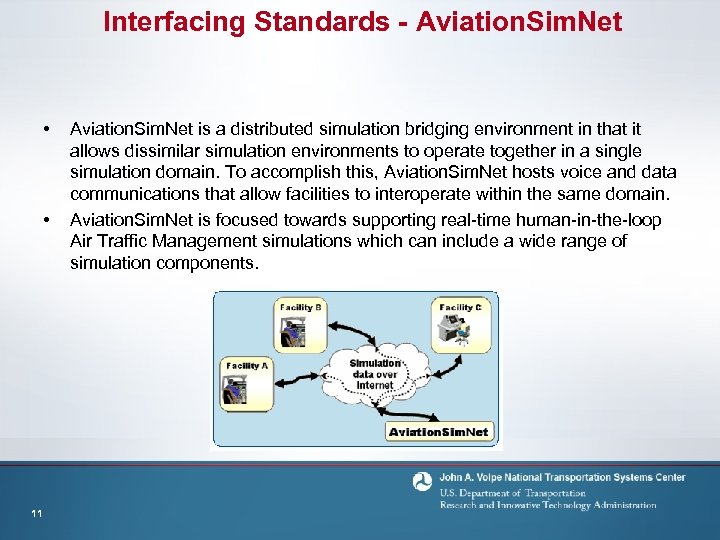
Interfacing Standards - Aviation. Sim. Net • • 11 Aviation. Sim. Net is a distributed simulation bridging environment in that it allows dissimilar simulation environments to operate together in a single simulation domain. To accomplish this, Aviation. Sim. Net hosts voice and data communications that allow facilities to interoperate within the same domain. Aviation. Sim. Net is focused towards supporting real-time human-in-the-loop Air Traffic Management simulations which can include a wide range of simulation components.
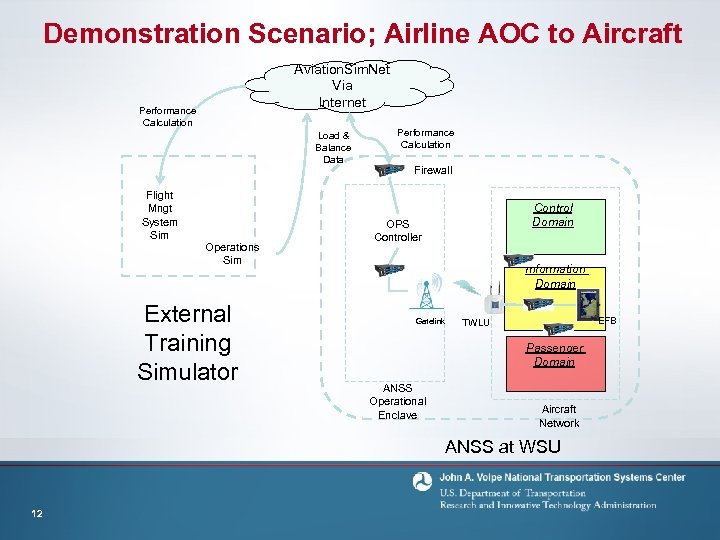
Demonstration Scenario; Airline AOC to Aircraft Aviation. Sim. Net Via Internet Performance Calculation Load & Balance Data Flight Mngt System Sim Operations Sim External Training Simulator Performance Calculation Firewall Control Domain OPS Controller Information Domain Gatelink EFB TWLU Passenger Domain ANSS Operational Enclave Aircraft Network ANSS at WSU 12
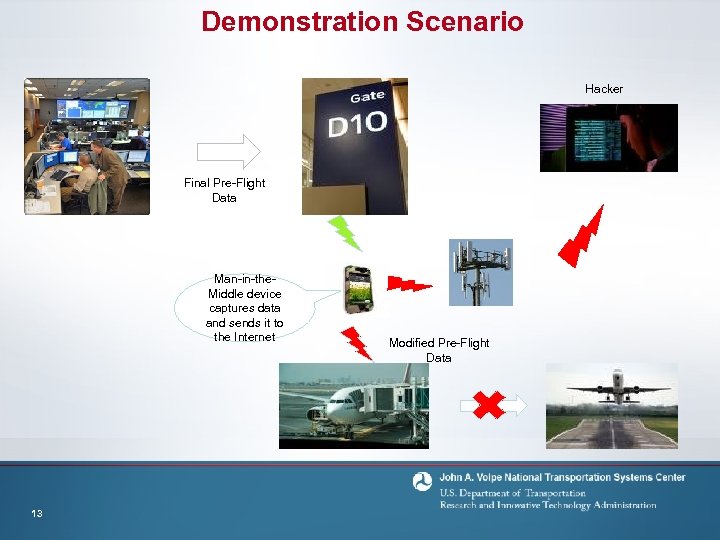
Demonstration Scenario Hacker Final Pre-Flight Data Man-in-the. Middle device captures data and sends it to the Internet 13 Modified Pre-Flight Data

Contact Information • • 14 Kevin Harnett, Volpe Center Cyber Security Program Manger – Email: kevin. harnett@dot. gov – Email: Phone: 617 -699 -7086 Chris Riley, Volpe Center Cyber Security Researcher – Email: riley@info-tools. com – Email: Phone: 508 -672 -6032
06af1d0e7d6ff819cbc791bfb5b4f03e.ppt