5261d2b1990bafc13a95d472bfeb2969.ppt
- Количество слайдов: 37
 Electronic Discovery & Compliance: Meeting the Challenges “Avoiding a Trial by Fire…. ” Timothy Wells Information Governance Specialist EMC Corporation wells_tim@emc. com © Copyright 2009 EMC Corporation. All rights reserved. 1
Electronic Discovery & Compliance: Meeting the Challenges “Avoiding a Trial by Fire…. ” Timothy Wells Information Governance Specialist EMC Corporation wells_tim@emc. com © Copyright 2009 EMC Corporation. All rights reserved. 1
 Agenda Who Are We and How Did We Get Here? – A Brief Background of e-Data, Compliance, the FRCP and e. Discovery What's Next and Why Should I Care? – 2010 Drivers and Landscape – Costs and Risks of e-Information What's An Enterprise To Do? – Information Management (Email, Archives, Records, etc. ) – e. Discovery Process and Infrastructure How Can We Justify Our Spend? – The Road To ROI What's Our Next Step? – Conclusions and Next Steps How About Some Free Advice? – Q&A © Copyright 2009 EMC Corporation. All rights reserved. 2
Agenda Who Are We and How Did We Get Here? – A Brief Background of e-Data, Compliance, the FRCP and e. Discovery What's Next and Why Should I Care? – 2010 Drivers and Landscape – Costs and Risks of e-Information What's An Enterprise To Do? – Information Management (Email, Archives, Records, etc. ) – e. Discovery Process and Infrastructure How Can We Justify Our Spend? – The Road To ROI What's Our Next Step? – Conclusions and Next Steps How About Some Free Advice? – Q&A © Copyright 2009 EMC Corporation. All rights reserved. 2
 EMC e. Discovery & Compliance Team An Expert, Diverse Team of 90+ Professionals – Industry-leader Kazeon & Source. One Family – Focused on e. Discovery § Industry best, dedicated sales team § Dedicated Legal / SME Team § Product management and support Leading-Edge Activities – – The Sedona Conference Electronic Discovery Reference Model (EDRM) ARMA Webcasts, Podcasts, Articles, Speaking engagements CT TX NY CA CO GA MA © Copyright 2009 EMC Corporation. All rights reserved. 3
EMC e. Discovery & Compliance Team An Expert, Diverse Team of 90+ Professionals – Industry-leader Kazeon & Source. One Family – Focused on e. Discovery § Industry best, dedicated sales team § Dedicated Legal / SME Team § Product management and support Leading-Edge Activities – – The Sedona Conference Electronic Discovery Reference Model (EDRM) ARMA Webcasts, Podcasts, Articles, Speaking engagements CT TX NY CA CO GA MA © Copyright 2009 EMC Corporation. All rights reserved. 3
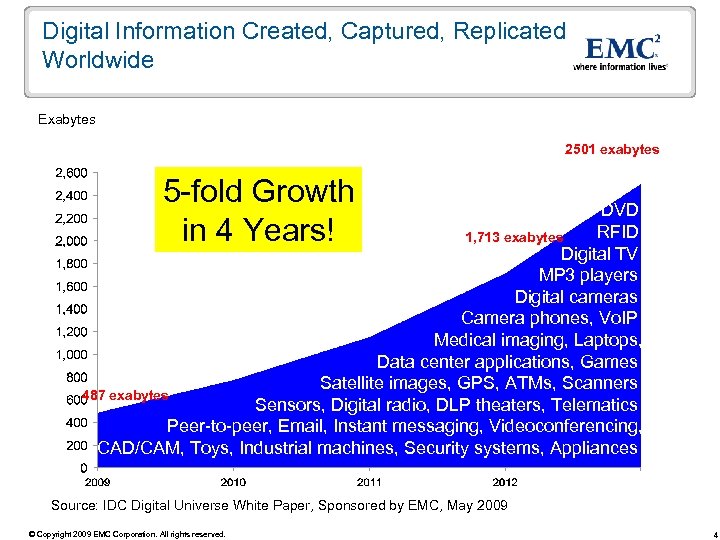 Digital Information Created, Captured, Replicated Worldwide Exabytes 2501 exabytes 5 -fold Growth in 4 Years! DVD RFID 1, 713 exabytes Digital TV MP 3 players Digital cameras Camera phones, Vo. IP Medical imaging, Laptops, Data center applications, Games Satellite images, GPS, ATMs, Scanners 487 exabytes Sensors, Digital radio, DLP theaters, Telematics Peer-to-peer, Email, Instant messaging, Videoconferencing, CAD/CAM, Toys, Industrial machines, Security systems, Appliances Source: IDC Digital Universe White Paper, Sponsored by EMC, May 2009 © Copyright 2009 EMC Corporation. All rights reserved. 4
Digital Information Created, Captured, Replicated Worldwide Exabytes 2501 exabytes 5 -fold Growth in 4 Years! DVD RFID 1, 713 exabytes Digital TV MP 3 players Digital cameras Camera phones, Vo. IP Medical imaging, Laptops, Data center applications, Games Satellite images, GPS, ATMs, Scanners 487 exabytes Sensors, Digital radio, DLP theaters, Telematics Peer-to-peer, Email, Instant messaging, Videoconferencing, CAD/CAM, Toys, Industrial machines, Security systems, Appliances Source: IDC Digital Universe White Paper, Sponsored by EMC, May 2009 © Copyright 2009 EMC Corporation. All rights reserved. 4
 Perfect Storm Drives the Need for Efficiency Information explosion – 70% of information is created by individuals but enterprises are responsible for the security, privacy, reliability, and compliance of 85% – Your “digital shadow” is larger than the digital information you actively create about yourself More lawsuits and regulation – – – Widespread belief that deregulation was a failure Food and drug safety Climate change, and environmental concerns and sustainability efforts Financial meltdown Workplace/unions No New Budget – Do more with less Enterprise Information Management – How do you get started? © Copyright 2009 EMC Corporation. All rights reserved. 5
Perfect Storm Drives the Need for Efficiency Information explosion – 70% of information is created by individuals but enterprises are responsible for the security, privacy, reliability, and compliance of 85% – Your “digital shadow” is larger than the digital information you actively create about yourself More lawsuits and regulation – – – Widespread belief that deregulation was a failure Food and drug safety Climate change, and environmental concerns and sustainability efforts Financial meltdown Workplace/unions No New Budget – Do more with less Enterprise Information Management – How do you get started? © Copyright 2009 EMC Corporation. All rights reserved. 5
 Years After FRCP Amendments… State of Readiness: Unprepared 57% of law firms: Clients are not ready to find and produce information relevant to litigation 39% of In-house: Company is not prepared for e-discovery Errors Generate Sanctions and Headlines Scenario 1: Lawyers for a company produced a small batch of relevant e-mails about 10 hours before trial. U. S. District Court Judge Marilyn Hall Patel declares “Heads will have to roll. ” According to reports, the punished company had reviewed terabytes of information for this case. Scenario 2: Company hit with an $8. 5 million penalty for mistakes with its own discovery of e-mail relevant to a patent lawsuit. As federal courts emphasize the responsibility of parties to conduct thorough discovery searches, more such mishaps are likely. “Companies Not Ready For E-Discovery”, http: //www. informationweek. com/blog/main/archives/2008/09/ companies_not_r. html, posted 9/23/08 (Andrew Conry-Murray, Information Week). Survey from Oce Business Services. © Copyright 2009 EMC Corporation. All rights reserved. 6
Years After FRCP Amendments… State of Readiness: Unprepared 57% of law firms: Clients are not ready to find and produce information relevant to litigation 39% of In-house: Company is not prepared for e-discovery Errors Generate Sanctions and Headlines Scenario 1: Lawyers for a company produced a small batch of relevant e-mails about 10 hours before trial. U. S. District Court Judge Marilyn Hall Patel declares “Heads will have to roll. ” According to reports, the punished company had reviewed terabytes of information for this case. Scenario 2: Company hit with an $8. 5 million penalty for mistakes with its own discovery of e-mail relevant to a patent lawsuit. As federal courts emphasize the responsibility of parties to conduct thorough discovery searches, more such mishaps are likely. “Companies Not Ready For E-Discovery”, http: //www. informationweek. com/blog/main/archives/2008/09/ companies_not_r. html, posted 9/23/08 (Andrew Conry-Murray, Information Week). Survey from Oce Business Services. © Copyright 2009 EMC Corporation. All rights reserved. 6
 Pension Committee Case Guidance from the Bench Pension Committee provides guidance related to litigation holds, preservation and search methods, and appropriate behavior by organizations charged with delivering relevant data as part of a civil litigation matter. Some insight from Judge Scheindlin: Courts cannot expect perfection. They do expect that litigants and counsel take necessary steps to ensure that relevant records are preserved when litigation is reasonably anticipated. One requirement noted by the judge is written hold notifications be issued to and acknowledged by all potential custodians. Failure to preserve evidence, electronic or paper, resulting in the loss or destruction of relevant information is "surely negligent" and depending on the circumstances, may be "grossly negligent" or "willful. " Preservation of backup tapes can be required if they are the sole source of relevant information related to the matter. © Copyright 2009 EMC Corporation. All rights reserved. 7
Pension Committee Case Guidance from the Bench Pension Committee provides guidance related to litigation holds, preservation and search methods, and appropriate behavior by organizations charged with delivering relevant data as part of a civil litigation matter. Some insight from Judge Scheindlin: Courts cannot expect perfection. They do expect that litigants and counsel take necessary steps to ensure that relevant records are preserved when litigation is reasonably anticipated. One requirement noted by the judge is written hold notifications be issued to and acknowledged by all potential custodians. Failure to preserve evidence, electronic or paper, resulting in the loss or destruction of relevant information is "surely negligent" and depending on the circumstances, may be "grossly negligent" or "willful. " Preservation of backup tapes can be required if they are the sole source of relevant information related to the matter. © Copyright 2009 EMC Corporation. All rights reserved. 7
 What is e. Discovery? Electronic discovery (e. Discovery) is the process in which electronically stored information (“ESI”) is searched, collected, preserved, analyzed, and reviewed for legal and regulatory proceedings. Litigation Investigation Audit Current and reasonably anticipated state and federal litigation State and federal regulators, IRS, OSHA, SEC, NASD, FINRA, HIPAA, Data Privacy & Protection Internal and external audits of books and records, Defense Contractor Audit, Govt Contract Audits, etc. © Copyright 2009 EMC Corporation. All rights reserved. 8 Public Disclosure Federal, State and Local - Freedom of Information Act, Open/Public Records Acts 8
What is e. Discovery? Electronic discovery (e. Discovery) is the process in which electronically stored information (“ESI”) is searched, collected, preserved, analyzed, and reviewed for legal and regulatory proceedings. Litigation Investigation Audit Current and reasonably anticipated state and federal litigation State and federal regulators, IRS, OSHA, SEC, NASD, FINRA, HIPAA, Data Privacy & Protection Internal and external audits of books and records, Defense Contractor Audit, Govt Contract Audits, etc. © Copyright 2009 EMC Corporation. All rights reserved. 8 Public Disclosure Federal, State and Local - Freedom of Information Act, Open/Public Records Acts 8
 Agenda Who Are You and How Did We Get Here? – A Brief History What's Next and Why Should I Care? – 2010 Drivers and Landscape – Costs and Risks of e-Information What's An Enterprise To Do? – Recommendations and Initiatives – e. Discovery Process and Infrastructure How Do We Justify That? – The Road To ROI What's Our Next Step? – Conclusions and Next Steps How About Some Free Advice? – Q&A © Copyright 2009 EMC Corporation. All rights reserved. 9
Agenda Who Are You and How Did We Get Here? – A Brief History What's Next and Why Should I Care? – 2010 Drivers and Landscape – Costs and Risks of e-Information What's An Enterprise To Do? – Recommendations and Initiatives – e. Discovery Process and Infrastructure How Do We Justify That? – The Road To ROI What's Our Next Step? – Conclusions and Next Steps How About Some Free Advice? – Q&A © Copyright 2009 EMC Corporation. All rights reserved. 9
 2009 Outlook Hint: It hasn’t changed much for 2010…. Forrester: “As one outcome of the current macro-economic environment… expect more litigation and regulation in 2009. ” Regulatory investigations – Fallout from the financial crisis = enhanced regulation Employee Litigation – Layoffs generate lawsuits and investigations Shareholder derivative actions – Reporting, drop in stock, financial crisis Aggressive IP Practices – Seeking additional revenue sources CFO Oversight – Weaker economy results in pressure on expenses - including legal Sources: Forrester: “Trends 2009: e. Discovery”, Brian Hill, 1/15/2009 “As companies increase layoffs, lawsuits are likely to follow”, Carol Williams, Los Angeles Times, 12/28/08 © Copyright 2009 EMC Corporation. All rights reserved. 10
2009 Outlook Hint: It hasn’t changed much for 2010…. Forrester: “As one outcome of the current macro-economic environment… expect more litigation and regulation in 2009. ” Regulatory investigations – Fallout from the financial crisis = enhanced regulation Employee Litigation – Layoffs generate lawsuits and investigations Shareholder derivative actions – Reporting, drop in stock, financial crisis Aggressive IP Practices – Seeking additional revenue sources CFO Oversight – Weaker economy results in pressure on expenses - including legal Sources: Forrester: “Trends 2009: e. Discovery”, Brian Hill, 1/15/2009 “As companies increase layoffs, lawsuits are likely to follow”, Carol Williams, Los Angeles Times, 12/28/08 © Copyright 2009 EMC Corporation. All rights reserved. 10
 The Costs of e. Discovery $1. 5 M 89% Average Cost Per Incident Of Companies Face Litigation 10 x Increased Costs To Outsource $34 M $18 M+ Average Annual Legal Costs Cost to Review 1 TB of Info © Copyright 2009 EMC Corporation. All rights reserved. 11
The Costs of e. Discovery $1. 5 M 89% Average Cost Per Incident Of Companies Face Litigation 10 x Increased Costs To Outsource $34 M $18 M+ Average Annual Legal Costs Cost to Review 1 TB of Info © Copyright 2009 EMC Corporation. All rights reserved. 11
 E-mail Is Most Requested Content in Legal Proceedings and Regulatory Investigations… But Not the Only Electronic Information requested To the best of your knowledge, which of the following record types has your organization been asked to produce in a legal proceeding or regulatory inquiry? 80% E-mail and attachments 60% General office productivity 49% Database records 41% Invoices and other customer records 36% Financial statements 29% Phone call recordings and other Laptops 25% Digital images Desktops 21% Instant messages Video files E-mail residing on: File servers 16% E-mail servers Other 5% 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% Source: ESG Research Report: 2007 E-mail Archiving Survey, November 2007; based on 107 respondents © Copyright 2009 EMC Corporation. All rights reserved. 12
E-mail Is Most Requested Content in Legal Proceedings and Regulatory Investigations… But Not the Only Electronic Information requested To the best of your knowledge, which of the following record types has your organization been asked to produce in a legal proceeding or regulatory inquiry? 80% E-mail and attachments 60% General office productivity 49% Database records 41% Invoices and other customer records 36% Financial statements 29% Phone call recordings and other Laptops 25% Digital images Desktops 21% Instant messages Video files E-mail residing on: File servers 16% E-mail servers Other 5% 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% Source: ESG Research Report: 2007 E-mail Archiving Survey, November 2007; based on 107 respondents © Copyright 2009 EMC Corporation. All rights reserved. 12
 Web 2. 0 On the Horizon Blogs: 48% for industry, 33% in government Wikis: 44% industry; 38% in government. Facebook: 44% industry; 28% government You. Tube: 26% of government responders; 25% of industry Virtual World / Second Life (typically used for recruitment or web conferences): 13% of industry responders and 10% of government responders. IDC, Survey Shows Glimmers of Hope for Government Web 2. 0, Adelaide O'Brien, August 26, 2009 © Copyright 2009 EMC Corporation. All rights reserved. 13
Web 2. 0 On the Horizon Blogs: 48% for industry, 33% in government Wikis: 44% industry; 38% in government. Facebook: 44% industry; 28% government You. Tube: 26% of government responders; 25% of industry Virtual World / Second Life (typically used for recruitment or web conferences): 13% of industry responders and 10% of government responders. IDC, Survey Shows Glimmers of Hope for Government Web 2. 0, Adelaide O'Brien, August 26, 2009 © Copyright 2009 EMC Corporation. All rights reserved. 13
 Agenda Who Are You and How Did We Get Here? – A Brief History What's Next and Why Should I Care? – 2009 Drivers and Landscape – Costs and Risks of e-Information What's An Enterprise To Do? – Recommendations and Initiatives – e. Discovery Process and Infrastructure How Do We Justify That? – The Road To ROI What's Our Next Step? – Conclusions and Next Steps How About Some Free Advice? – Q&A © Copyright 2009 EMC Corporation. All rights reserved. 14
Agenda Who Are You and How Did We Get Here? – A Brief History What's Next and Why Should I Care? – 2009 Drivers and Landscape – Costs and Risks of e-Information What's An Enterprise To Do? – Recommendations and Initiatives – e. Discovery Process and Infrastructure How Do We Justify That? – The Road To ROI What's Our Next Step? – Conclusions and Next Steps How About Some Free Advice? – Q&A © Copyright 2009 EMC Corporation. All rights reserved. 14
 Establish Boundaries Around Information Management… Use the appropriate process for cost & risk management Unmanaged Unstructured Content Email Systems Managed Unstructured Content Management Network File Shares Unstructured Content Desktops & Laptops Collaboration Common Services Custom Classify/Archive e. Discovery Enterprise Content Subject to Compliance Control Policy Enforcement Page-Oriented Legacy Disposition Data Systems Physical Records Structured Content Email Archive Manage In-place Fixed Content © Copyright 2009 EMC Corporation. All rights reserved. Database Content Line-oriented Data Structured Content 15
Establish Boundaries Around Information Management… Use the appropriate process for cost & risk management Unmanaged Unstructured Content Email Systems Managed Unstructured Content Management Network File Shares Unstructured Content Desktops & Laptops Collaboration Common Services Custom Classify/Archive e. Discovery Enterprise Content Subject to Compliance Control Policy Enforcement Page-Oriented Legacy Disposition Data Systems Physical Records Structured Content Email Archive Manage In-place Fixed Content © Copyright 2009 EMC Corporation. All rights reserved. Database Content Line-oriented Data Structured Content 15
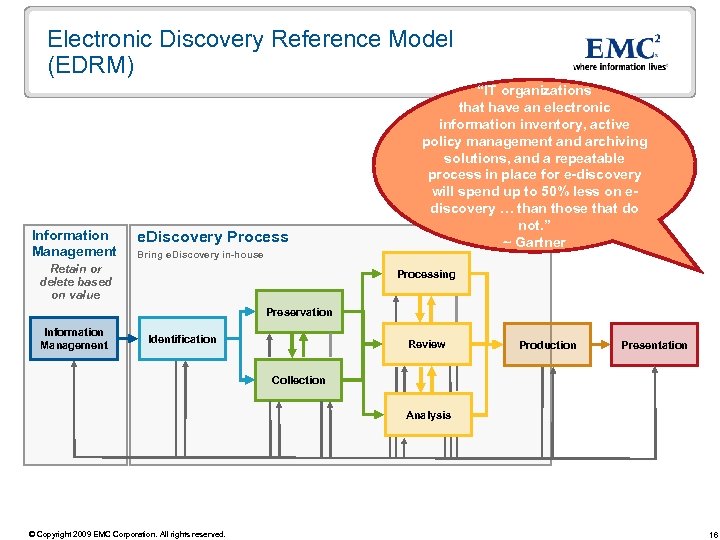 Electronic Discovery Reference Model (EDRM) Information Management e. Discovery Process Bring e. Discovery in-house Retain or delete based on value “IT organizations that have an electronic information inventory, active policy management and archiving solutions, and a repeatable process in place for e-discovery will spend up to 50% less on ediscovery … than those that do not. ” ~ Gartner Processing Preservation Information Management Identification Review Production Presentation Collection Analysis © Copyright 2009 EMC Corporation. All rights reserved. 16
Electronic Discovery Reference Model (EDRM) Information Management e. Discovery Process Bring e. Discovery in-house Retain or delete based on value “IT organizations that have an electronic information inventory, active policy management and archiving solutions, and a repeatable process in place for e-discovery will spend up to 50% less on ediscovery … than those that do not. ” ~ Gartner Processing Preservation Information Management Identification Review Production Presentation Collection Analysis © Copyright 2009 EMC Corporation. All rights reserved. 16
 Segment Data by Business Value Business records Compliance Archive (e. g. , automated message capture of strategic departments/users) Official business record Long-term retention Business important e-mails/docs Compliance or Native Archive (e. g. , automated message capture of strategic departments/users or as part of a Discovery Manager search) Native Archive Large-volume e-mails / docs (e. g. , routine business e-mail archived as part of good information governance and regulatory compliance) © Copyright 2009 EMC Corporation. All rights reserved. Referential Modest retention Required for discovery Non-record Compliance-driven Enforced deletion 17
Segment Data by Business Value Business records Compliance Archive (e. g. , automated message capture of strategic departments/users) Official business record Long-term retention Business important e-mails/docs Compliance or Native Archive (e. g. , automated message capture of strategic departments/users or as part of a Discovery Manager search) Native Archive Large-volume e-mails / docs (e. g. , routine business e-mail archived as part of good information governance and regulatory compliance) © Copyright 2009 EMC Corporation. All rights reserved. Referential Modest retention Required for discovery Non-record Compliance-driven Enforced deletion 17
 Potential ESI Enterprise Email Server(s) Legacy data Local Email stores (pst, etc. ) User desktops Relational databases CDs, DVDs – CRM – Accounting / Financial Data PDAs / Wireless phones Fileshares Flash drives Content Management Home offices Instant Messaging Legacy / stray tapes Video and voice captures Decommissioned servers Backup / DR tapes Computer graveyard Wikis & Blogs Stray drives Archives © Copyright 2009 EMC Corporation. All rights reserved. 18
Potential ESI Enterprise Email Server(s) Legacy data Local Email stores (pst, etc. ) User desktops Relational databases CDs, DVDs – CRM – Accounting / Financial Data PDAs / Wireless phones Fileshares Flash drives Content Management Home offices Instant Messaging Legacy / stray tapes Video and voice captures Decommissioned servers Backup / DR tapes Computer graveyard Wikis & Blogs Stray drives Archives © Copyright 2009 EMC Corporation. All rights reserved. 18
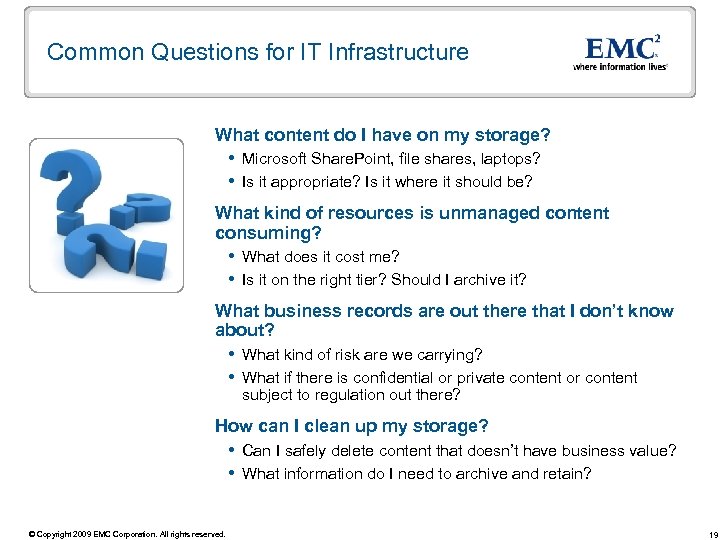 Common Questions for IT Infrastructure What content do I have on my storage? Microsoft Share. Point, file shares, laptops? Is it appropriate? Is it where it should be? What kind of resources is unmanaged content consuming? What does it cost me? Is it on the right tier? Should I archive it? What business records are out there that I don’t know about? What kind of risk are we carrying? What if there is confidential or private content or content subject to regulation out there? How can I clean up my storage? Can I safely delete content that doesn’t have business value? What information do I need to archive and retain? © Copyright 2009 EMC Corporation. All rights reserved. 19
Common Questions for IT Infrastructure What content do I have on my storage? Microsoft Share. Point, file shares, laptops? Is it appropriate? Is it where it should be? What kind of resources is unmanaged content consuming? What does it cost me? Is it on the right tier? Should I archive it? What business records are out there that I don’t know about? What kind of risk are we carrying? What if there is confidential or private content or content subject to regulation out there? How can I clean up my storage? Can I safely delete content that doesn’t have business value? What information do I need to archive and retain? © Copyright 2009 EMC Corporation. All rights reserved. 19
 File Remediation / Classification Action Non Record Delete Referential Record Short Retention Record Move to RM System Attributes Lunch, Gym, emails, MP 3 s, etc Mkt. Power. Point, Meeting Notices, etc. Contracts, Invoices, PII, etc Infrastructure © Copyright 2009 EMC Corporation. All rights reserved. 20
File Remediation / Classification Action Non Record Delete Referential Record Short Retention Record Move to RM System Attributes Lunch, Gym, emails, MP 3 s, etc Mkt. Power. Point, Meeting Notices, etc. Contracts, Invoices, PII, etc Infrastructure © Copyright 2009 EMC Corporation. All rights reserved. 20
 Intelligent Information Governance with EMC Source. One File Intelligence Enables educated decision-making and policy creation Laptops and desktops Copy/move to archive storage EMC Celerra, Data Domain, Centera File systems E-mail servers Documentum Copy/move to enable records Identify content to migrate to Documentum Microsoft Share. Point Third-party archives © Copyright 2009 EMC Corporation. All rights reserved. Copy/move to cloud storage The cloud 21
Intelligent Information Governance with EMC Source. One File Intelligence Enables educated decision-making and policy creation Laptops and desktops Copy/move to archive storage EMC Celerra, Data Domain, Centera File systems E-mail servers Documentum Copy/move to enable records Identify content to migrate to Documentum Microsoft Share. Point Third-party archives © Copyright 2009 EMC Corporation. All rights reserved. Copy/move to cloud storage The cloud 21
 Source. One File Intelligence: How It Works Catalog Analyze Classify Search Act Report Crawl data sources Classify files based on metadata, keyword content, and pattern matching Build index Age, owner, location, file type, etc. – Metadata basic – Metadata with document type – Metadata with hash – Deep crawl full text – Deep crawl with classification Business value, security risk, intellectual property, PII, PCI Analyze data with search and report tools – Semantic search with Boolean, proximity, stemming, phrase support – More than 30 pre-built reports out of the box – Custom reports as needed © Copyright 2009 EMC Corporation. All rights reserved. Robust action set – Move, copy, delete, retain, export, tag Policy-based actions – One-time – Scheduled – Recurring 22
Source. One File Intelligence: How It Works Catalog Analyze Classify Search Act Report Crawl data sources Classify files based on metadata, keyword content, and pattern matching Build index Age, owner, location, file type, etc. – Metadata basic – Metadata with document type – Metadata with hash – Deep crawl full text – Deep crawl with classification Business value, security risk, intellectual property, PII, PCI Analyze data with search and report tools – Semantic search with Boolean, proximity, stemming, phrase support – More than 30 pre-built reports out of the box – Custom reports as needed © Copyright 2009 EMC Corporation. All rights reserved. Robust action set – Move, copy, delete, retain, export, tag Policy-based actions – One-time – Scheduled – Recurring 22
 Rich Data Classification Classify files by attributes – High business value § Files created or modified in the last 30 days § Files owned by company executives – Medium business value § Files not accessed in the last 90 days and not modified in the last 180 days §. PST files – Low business value § Files not accessed in the last 180 days § MP 3/MP 4, JPEG, MOV files Classify selected files based on file content and metadata – Files with “Confidential” content § e. g. , source code files, patents, product manuals, contracts, etc. – Files containing non-public information § e. g. , Social Security numbers, credit card numbers etc. Classify files based on IT or business input – Administrator tags – Line-of-business tags – User tags © Copyright 2009 EMC Corporation. All rights reserved. 23
Rich Data Classification Classify files by attributes – High business value § Files created or modified in the last 30 days § Files owned by company executives – Medium business value § Files not accessed in the last 90 days and not modified in the last 180 days §. PST files – Low business value § Files not accessed in the last 180 days § MP 3/MP 4, JPEG, MOV files Classify selected files based on file content and metadata – Files with “Confidential” content § e. g. , source code files, patents, product manuals, contracts, etc. – Files containing non-public information § e. g. , Social Security numbers, credit card numbers etc. Classify files based on IT or business input – Administrator tags – Line-of-business tags – User tags © Copyright 2009 EMC Corporation. All rights reserved. 23
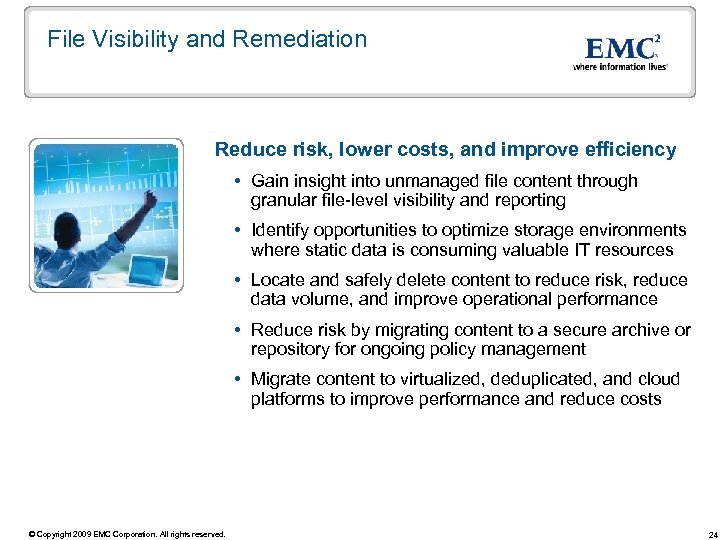 File Visibility and Remediation Reduce risk, lower costs, and improve efficiency Gain insight into unmanaged file content through granular file-level visibility and reporting Identify opportunities to optimize storage environments where static data is consuming valuable IT resources Locate and safely delete content to reduce risk, reduce data volume, and improve operational performance Reduce risk by migrating content to a secure archive or repository for ongoing policy management Migrate content to virtualized, deduplicated, and cloud platforms to improve performance and reduce costs © Copyright 2009 EMC Corporation. All rights reserved. 24
File Visibility and Remediation Reduce risk, lower costs, and improve efficiency Gain insight into unmanaged file content through granular file-level visibility and reporting Identify opportunities to optimize storage environments where static data is consuming valuable IT resources Locate and safely delete content to reduce risk, reduce data volume, and improve operational performance Reduce risk by migrating content to a secure archive or repository for ongoing policy management Migrate content to virtualized, deduplicated, and cloud platforms to improve performance and reduce costs © Copyright 2009 EMC Corporation. All rights reserved. 24
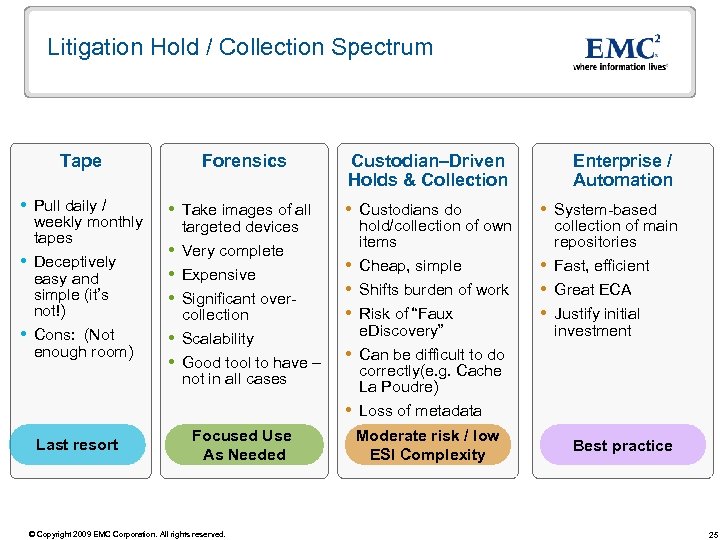 Litigation Hold / Collection Spectrum Tape Forensics Custodian–Driven Holds & Collection Enterprise / Automation Pull daily / weekly monthly tapes Deceptively easy and simple (it’s not!) Cons: (Not enough room) Take images of all targeted devices Very complete Expensive Significant overcollection Scalability Good tool to have – not in all cases Custodians do hold/collection of own items Cheap, simple Shifts burden of work Risk of “Faux e. Discovery” Can be difficult to do correctly(e. g. Cache La Poudre) Loss of metadata System-based collection of main repositories Fast, efficient Great ECA Justify initial investment Focused Use As Needed Moderate risk / low ESI Complexity Last resort © Copyright 2009 EMC Corporation. All rights reserved. Best practice 25
Litigation Hold / Collection Spectrum Tape Forensics Custodian–Driven Holds & Collection Enterprise / Automation Pull daily / weekly monthly tapes Deceptively easy and simple (it’s not!) Cons: (Not enough room) Take images of all targeted devices Very complete Expensive Significant overcollection Scalability Good tool to have – not in all cases Custodians do hold/collection of own items Cheap, simple Shifts burden of work Risk of “Faux e. Discovery” Can be difficult to do correctly(e. g. Cache La Poudre) Loss of metadata System-based collection of main repositories Fast, efficient Great ECA Justify initial investment Focused Use As Needed Moderate risk / low ESI Complexity Last resort © Copyright 2009 EMC Corporation. All rights reserved. Best practice 25
 EMC e. Discovery - Data Flow Desktops Fileshares Exchange Server EMC Documentum Microsoft Share. Point Step 1 Knowledge workers create electronically stored information (ESI) on data sources as usual; this solution requires no changes to data creation processes and no agents to be deployed on data sources © Copyright 2009 EMC Corporation. All rights reserved. Step 2 The solution indexes (harvests) the ESI on the data sources to gather intelligence about the stored data Step 3 Investigative users search the indexes to determine what ESI is relevant Step 4 Relevant ESI is secured and placed on legal hold on immutable storage Step 5 Investigator culls through held data and generates production sets for use in legal review by outside counsel or hosted review vendor 26
EMC e. Discovery - Data Flow Desktops Fileshares Exchange Server EMC Documentum Microsoft Share. Point Step 1 Knowledge workers create electronically stored information (ESI) on data sources as usual; this solution requires no changes to data creation processes and no agents to be deployed on data sources © Copyright 2009 EMC Corporation. All rights reserved. Step 2 The solution indexes (harvests) the ESI on the data sources to gather intelligence about the stored data Step 3 Investigative users search the indexes to determine what ESI is relevant Step 4 Relevant ESI is secured and placed on legal hold on immutable storage Step 5 Investigator culls through held data and generates production sets for use in legal review by outside counsel or hosted review vendor 26
 EMC Source. One e. Discovery Kazeon Case Management Preservation and Collection Analysis and Review © Copyright 2009 EMC Corporation. All rights reserved. • Legal Hold reporting dashboard • Legal Hold workflow management • Segregate data and cases by role • Built-in and custom reports • Agent-based & agent-less collection • Full and incremental collections • Laptop / Desktop Collection • Single-step targeted collection • Multiple target repositories • Distributed and collaborative review • Email analytics and threading • Concept search and analysis • Interactive tagging and review • Highly scalable for multiple case support 27
EMC Source. One e. Discovery Kazeon Case Management Preservation and Collection Analysis and Review © Copyright 2009 EMC Corporation. All rights reserved. • Legal Hold reporting dashboard • Legal Hold workflow management • Segregate data and cases by role • Built-in and custom reports • Agent-based & agent-less collection • Full and incremental collections • Laptop / Desktop Collection • Single-step targeted collection • Multiple target repositories • Distributed and collaborative review • Email analytics and threading • Concept search and analysis • Interactive tagging and review • Highly scalable for multiple case support 27
 Enterprise Information Governance Solution S 1 Supervisor MS Exchange 2003 / 2007 / 2010 Lotus Notes / Domino Messaging Servers Regulatory Compliance Review Sampled Messages S 1 e. Discovery – Kazeon Source. One Archive Email & IM MS Share. Point File Archiving Other Content Repositories Currently two step collection and unified matter management for: File. Net, Content Manager, Group. Wise and other sources Includes Connectors for: File Shares Home Drives (laptops & desktops) Exchange & Notes / PSTs & NSFs Documentum Share. Point S 1 Email Archive In-place Legal Hold Desktops, Remote Offices, and Laptops © Copyright 2009 EMC Corporation. All rights reserved. File Shares Avamar Backups Snapshots Document Repositories Share. Point Documentum Target Legal Hold Collect Legal Store Preservation Server Legal Hold / Legal Store or Preservation Store – Celerra, Centera, Data Domain & others 28
Enterprise Information Governance Solution S 1 Supervisor MS Exchange 2003 / 2007 / 2010 Lotus Notes / Domino Messaging Servers Regulatory Compliance Review Sampled Messages S 1 e. Discovery – Kazeon Source. One Archive Email & IM MS Share. Point File Archiving Other Content Repositories Currently two step collection and unified matter management for: File. Net, Content Manager, Group. Wise and other sources Includes Connectors for: File Shares Home Drives (laptops & desktops) Exchange & Notes / PSTs & NSFs Documentum Share. Point S 1 Email Archive In-place Legal Hold Desktops, Remote Offices, and Laptops © Copyright 2009 EMC Corporation. All rights reserved. File Shares Avamar Backups Snapshots Document Repositories Share. Point Documentum Target Legal Hold Collect Legal Store Preservation Server Legal Hold / Legal Store or Preservation Store – Celerra, Centera, Data Domain & others 28
 Agenda Who Are You and How Did We Get Here? – A Brief History What's Next and Why Should I Care? – 2009 Drivers and Landscape – Costs and Risks of e-Information What's An Enterprise To Do? – Recommendations and Initiatives – e. Discovery Process and Infrastructure How Do We Justify Purchases in 2010? – The Road To ROI What's Our Next Step? – Conclusions and Next Steps How About Some Free Advice? – Q&A © Copyright 2009 EMC Corporation. All rights reserved. 29
Agenda Who Are You and How Did We Get Here? – A Brief History What's Next and Why Should I Care? – 2009 Drivers and Landscape – Costs and Risks of e-Information What's An Enterprise To Do? – Recommendations and Initiatives – e. Discovery Process and Infrastructure How Do We Justify Purchases in 2010? – The Road To ROI What's Our Next Step? – Conclusions and Next Steps How About Some Free Advice? – Q&A © Copyright 2009 EMC Corporation. All rights reserved. 29
 Challenges In 2010 IT Budgets are flat or declining *, but e. Discovery is not discretionary and the money is already being spent IT • • FTEs spending time on restores of historic data based on vague requests by Legal No ability to delete because of a lack of insight into data, and unrealistic policies from Legal Massive over-collection (“screw drivers and wheel barrels”), leads to huge legal review and processing costs by outsourcers (1 gig = 50, 000 files for review) Risk of sanctions for deleting the wrong thing leads to over-preservation (“save everything”) *“Global purchases of IT goods and services … will equal $1. 66 trillion in 2009, declining by 3% after an 8% rise in 2008. ” Global IT Market Outlook: 2009, Forrester Research, 1/12/2009 © Copyright 2009 EMC Corporation. All rights reserved. 30
Challenges In 2010 IT Budgets are flat or declining *, but e. Discovery is not discretionary and the money is already being spent IT • • FTEs spending time on restores of historic data based on vague requests by Legal No ability to delete because of a lack of insight into data, and unrealistic policies from Legal Massive over-collection (“screw drivers and wheel barrels”), leads to huge legal review and processing costs by outsourcers (1 gig = 50, 000 files for review) Risk of sanctions for deleting the wrong thing leads to over-preservation (“save everything”) *“Global purchases of IT goods and services … will equal $1. 66 trillion in 2009, declining by 3% after an 8% rise in 2008. ” Global IT Market Outlook: 2009, Forrester Research, 1/12/2009 © Copyright 2009 EMC Corporation. All rights reserved. 30
 e. Discovery and RIM ROI “Organizations unprepared for e-discovery in 2009 will be at a disadvantage … open to potential sanctions from an increasingly technically literate U. S. judiciary. As defendants, organizations need to respond quickly and effectively. . . As plaintiffs, organizations must have their ESI house in order and be prepared for reciprocal discovery requests…” Gartner, “Reduce the Cost and Risk of E-Discovery in 2009”, D. Logan & J. Bace, 1/9/09 ROI Factors “Between 10% and 90% of what [clients] have does not need to be retained for any reason. ” © Copyright 2009 EMC Corporation. All rights reserved. Budget roughly $500, 000 on IT support for cases involving 10 or more custodians and/or more than three different systems One terabyte of data can result in $18. 75 M in legal review costs Unprepared companies will spend 1/3 more on e-discovery than those with content archiving solutions. 31
e. Discovery and RIM ROI “Organizations unprepared for e-discovery in 2009 will be at a disadvantage … open to potential sanctions from an increasingly technically literate U. S. judiciary. As defendants, organizations need to respond quickly and effectively. . . As plaintiffs, organizations must have their ESI house in order and be prepared for reciprocal discovery requests…” Gartner, “Reduce the Cost and Risk of E-Discovery in 2009”, D. Logan & J. Bace, 1/9/09 ROI Factors “Between 10% and 90% of what [clients] have does not need to be retained for any reason. ” © Copyright 2009 EMC Corporation. All rights reserved. Budget roughly $500, 000 on IT support for cases involving 10 or more custodians and/or more than three different systems One terabyte of data can result in $18. 75 M in legal review costs Unprepared companies will spend 1/3 more on e-discovery than those with content archiving solutions. 31
 The Cost of e. Discovery Notice Collection Hold Inspect/Review Produce © Copyright 2009 EMC Corporation. All rights reserved. Percentage of discovery costs when proceedings or investigations involve the discovery of ESI: * 28% Costs associated with document collection from inaccessible locations 20% Cost of holding massive volumes Unanticipated legal risk Spoliation risk 35% Cost directly related to number of documents to review 17% Cost of delivering ESI to various recipients on various media (e. g. , CD, DVD, or paper) * Source: Enterprise Strategy Group, 2007 32
The Cost of e. Discovery Notice Collection Hold Inspect/Review Produce © Copyright 2009 EMC Corporation. All rights reserved. Percentage of discovery costs when proceedings or investigations involve the discovery of ESI: * 28% Costs associated with document collection from inaccessible locations 20% Cost of holding massive volumes Unanticipated legal risk Spoliation risk 35% Cost directly related to number of documents to review 17% Cost of delivering ESI to various recipients on various media (e. g. , CD, DVD, or paper) * Source: Enterprise Strategy Group, 2007 32
![Straightforward ROI “T]he payback period for an e-discovery investment is very short, on the Straightforward ROI “T]he payback period for an e-discovery investment is very short, on the](https://present5.com/presentation/5261d2b1990bafc13a95d472bfeb2969/image-33.jpg) Straightforward ROI “T]he payback period for an e-discovery investment is very short, on the order of three to six months after implementation takes place. ” [1] “Market. Scope for E-Discovery Software Product Vendors”, Gartner, Inc. , 12/17/08. © Copyright 2009 EMC Corporation. All rights reserved. 33
Straightforward ROI “T]he payback period for an e-discovery investment is very short, on the order of three to six months after implementation takes place. ” [1] “Market. Scope for E-Discovery Software Product Vendors”, Gartner, Inc. , 12/17/08. © Copyright 2009 EMC Corporation. All rights reserved. 33
 Agenda Who Are You and How Did We Get Here? – A Brief History What's Next and Why Should I Care? – 2009 Drivers and Landscape – Costs and Risks of e-Information What's An Enterprise To Do? – Recommendations and Initiatives – e. Discovery Process and Infrastructure How Do We Justify That? – The Road To ROI What's Our Next Step? – Conclusions and Next Steps How About Some Free Advice? – Q&A © Copyright 2009 EMC Corporation. All rights reserved. 34
Agenda Who Are You and How Did We Get Here? – A Brief History What's Next and Why Should I Care? – 2009 Drivers and Landscape – Costs and Risks of e-Information What's An Enterprise To Do? – Recommendations and Initiatives – e. Discovery Process and Infrastructure How Do We Justify That? – The Road To ROI What's Our Next Step? – Conclusions and Next Steps How About Some Free Advice? – Q&A © Copyright 2009 EMC Corporation. All rights reserved. 34
 Next Steps Get Cross-Functional – IT Meet Legal; Legal Meet IT Assemble Your Case – Collect data, anecdotes, research Top-Down – Focus initial work on high impact areas Let EMC Help – We know your information – Our team can facilitate next steps Knowledge Is Power – – EMC e. Discovery and Compliance (www. emc. com/ediscovery) Bringing e. Discovery In-House (For Dummies): (www. emc. com/ediscovery 4 dummies) The Sedona Conference (www. sedonaconference. net) EDRM (www. edrm. net) © Copyright 2009 EMC Corporation. All rights reserved. 35
Next Steps Get Cross-Functional – IT Meet Legal; Legal Meet IT Assemble Your Case – Collect data, anecdotes, research Top-Down – Focus initial work on high impact areas Let EMC Help – We know your information – Our team can facilitate next steps Knowledge Is Power – – EMC e. Discovery and Compliance (www. emc. com/ediscovery) Bringing e. Discovery In-House (For Dummies): (www. emc. com/ediscovery 4 dummies) The Sedona Conference (www. sedonaconference. net) EDRM (www. edrm. net) © Copyright 2009 EMC Corporation. All rights reserved. 35
 Agenda Who Are You and How Did We Get Here? – A Brief History What's Next and Why Should I Care? – 2009 Drivers and Landscape – Costs and Risks of e-Information What's An Enterprise To Do? – Recommendations and Initiatives – e. Discovery Process and Infrastructure How Do We Justify That? – The Road To ROI What's Our Next Step? – Conclusions and Next Steps How About Some Free Advice? – Q&A © Copyright 2009 EMC Corporation. All rights reserved. 36
Agenda Who Are You and How Did We Get Here? – A Brief History What's Next and Why Should I Care? – 2009 Drivers and Landscape – Costs and Risks of e-Information What's An Enterprise To Do? – Recommendations and Initiatives – e. Discovery Process and Infrastructure How Do We Justify That? – The Road To ROI What's Our Next Step? – Conclusions and Next Steps How About Some Free Advice? – Q&A © Copyright 2009 EMC Corporation. All rights reserved. 36
 © Copyright 2009 EMC Corporation. All rights reserved. 37
© Copyright 2009 EMC Corporation. All rights reserved. 37


