861001cc5df72cba4d61e5c1fd11da32.ppt
- Количество слайдов: 20
 Electronic Content Management (in a De-Perimeterised Environment) Presentation at ISACA/IIA Wellington Prof. Clark Thomborson 27 th July 2007
Electronic Content Management (in a De-Perimeterised Environment) Presentation at ISACA/IIA Wellington Prof. Clark Thomborson 27 th July 2007
 Questions to be Addressed 1. What is Enterprise Content Management? n n 2. 3. How does it differ from Digital Rights Management? What do we want from an ECM system? What are the technical constraints on ECM? What features can we expect to find in next-generation ECM systems?
Questions to be Addressed 1. What is Enterprise Content Management? n n 2. 3. How does it differ from Digital Rights Management? What do we want from an ECM system? What are the technical constraints on ECM? What features can we expect to find in next-generation ECM systems?
 Digital Rights Management (DRM) systems were “hot properties” in the dot-com era. n n n n Stefik ’ 012 (filed 1994) discloses a “system for controlling the distribution and use of digital works having a fee reporting mechanism”. References include R. Weber, “Digital Rights Management Technology”, October 1995. Assignee: Xerox. Johnson ’ 876 (filed 1996) discloses an “electronic rights management and authorization system”. Assignee: Copyright Clearance Centre, Inc. Kahn ’ 646 (filed 1997) discloses a “digital object management system”. Assignee: CNRI of Reston VA. Ginter, . . . , Weber ’ 683 (filed 1998) discloses a “secure content delivery method”. Assignee: Inter. Trust. 2001: Inter. Trust sued Microsoft over DRM, . Net, trusted computing. 2004: Microsoft licensed Inter. Trust’s patents for $440 million. DRM systems allow authors to create and enforce licenses on the use of their digital works.
Digital Rights Management (DRM) systems were “hot properties” in the dot-com era. n n n n Stefik ’ 012 (filed 1994) discloses a “system for controlling the distribution and use of digital works having a fee reporting mechanism”. References include R. Weber, “Digital Rights Management Technology”, October 1995. Assignee: Xerox. Johnson ’ 876 (filed 1996) discloses an “electronic rights management and authorization system”. Assignee: Copyright Clearance Centre, Inc. Kahn ’ 646 (filed 1997) discloses a “digital object management system”. Assignee: CNRI of Reston VA. Ginter, . . . , Weber ’ 683 (filed 1998) discloses a “secure content delivery method”. Assignee: Inter. Trust. 2001: Inter. Trust sued Microsoft over DRM, . Net, trusted computing. 2004: Microsoft licensed Inter. Trust’s patents for $440 million. DRM systems allow authors to create and enforce licenses on the use of their digital works.
 DRM for Corporations? n n DRM systems could be used to control access to company-confidential documents. Inter. Trust and Media. Snap spent hundreds of millions of dollars developing and marketing unsuccessful DRM systems. n n Inter. Trust’s “Doc. Box” plugin is still available in Adobe Acrobat. Why were these systems unsuccessful? n n How much would your company pay (in cash per year, and in reduced employee productivity) to improve your confidentiality controls, and to manage other people’s copyright licenses? Wouldn’t you prefer a system which improves, rather than impedes, communication and collaboration?
DRM for Corporations? n n DRM systems could be used to control access to company-confidential documents. Inter. Trust and Media. Snap spent hundreds of millions of dollars developing and marketing unsuccessful DRM systems. n n Inter. Trust’s “Doc. Box” plugin is still available in Adobe Acrobat. Why were these systems unsuccessful? n n How much would your company pay (in cash per year, and in reduced employee productivity) to improve your confidentiality controls, and to manage other people’s copyright licenses? Wouldn’t you prefer a system which improves, rather than impedes, communication and collaboration?
 Enterprise Content Management DRM systems control access to documents, by defining licenses for created content. n n Goal: Enforce corporate policies on confidentiality and authorship, without unduly impeding profit-making activities. Enterprise Content Management systems facilitate the distribution of documents. n n Goal: Improve communication and cooperation, without unduly running the risk of violating corporate policies on confidentiality and authorship. The only difference is in the emphasis. n n n DRM is security-first, and ECM is feature-first. This difference is very important in marketing, but it is not a sharp technical distinction. DRM will restrict access “when in doubt”, but ECM will allow access “when in doubt”. DRM enforces a “need-to-know” policy, whereas ECM enforces a “reason-to-exclude” policy. Which is the bigger market? Can’t one system do both?
Enterprise Content Management DRM systems control access to documents, by defining licenses for created content. n n Goal: Enforce corporate policies on confidentiality and authorship, without unduly impeding profit-making activities. Enterprise Content Management systems facilitate the distribution of documents. n n Goal: Improve communication and cooperation, without unduly running the risk of violating corporate policies on confidentiality and authorship. The only difference is in the emphasis. n n n DRM is security-first, and ECM is feature-first. This difference is very important in marketing, but it is not a sharp technical distinction. DRM will restrict access “when in doubt”, but ECM will allow access “when in doubt”. DRM enforces a “need-to-know” policy, whereas ECM enforces a “reason-to-exclude” policy. Which is the bigger market? Can’t one system do both?
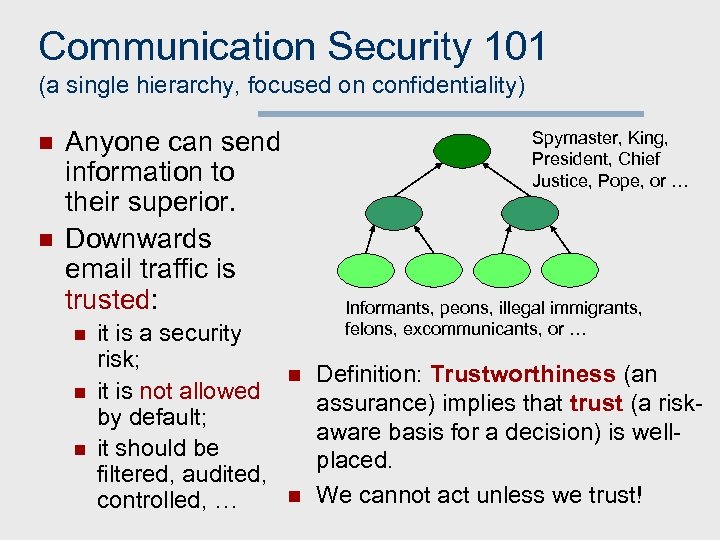 Communication Security 101 (a single hierarchy, focused on confidentiality) n n Anyone can send information to their superior. Downwards email traffic is trusted: n n n it is a security risk; it is not allowed by default; it should be filtered, audited, controlled, … Spymaster, King, President, Chief Justice, Pope, or … Informants, peons, illegal immigrants, felons, excommunicants, or … n n Definition: Trustworthiness (an assurance) implies that trust (a riskaware basis for a decision) is wellplaced. We cannot act unless we trust!
Communication Security 101 (a single hierarchy, focused on confidentiality) n n Anyone can send information to their superior. Downwards email traffic is trusted: n n n it is a security risk; it is not allowed by default; it should be filtered, audited, controlled, … Spymaster, King, President, Chief Justice, Pope, or … Informants, peons, illegal immigrants, felons, excommunicants, or … n n Definition: Trustworthiness (an assurance) implies that trust (a riskaware basis for a decision) is wellplaced. We cannot act unless we trust!
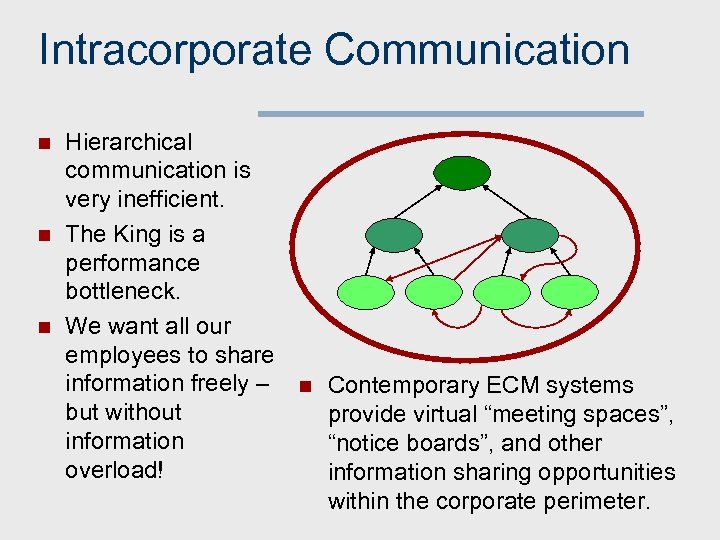 Intracorporate Communication n Hierarchical communication is very inefficient. The King is a performance bottleneck. We want all our employees to share information freely – but without information overload! n Contemporary ECM systems provide virtual “meeting spaces”, “notice boards”, and other information sharing opportunities within the corporate perimeter.
Intracorporate Communication n Hierarchical communication is very inefficient. The King is a performance bottleneck. We want all our employees to share information freely – but without information overload! n Contemporary ECM systems provide virtual “meeting spaces”, “notice boards”, and other information sharing opportunities within the corporate perimeter.
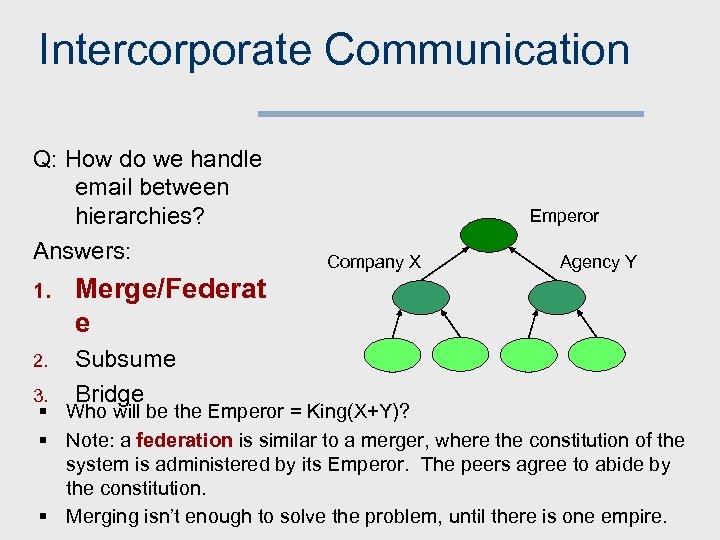 Intercorporate Communication Q: How do we handle email between hierarchies? Answers: 1. Subsume Bridge Company X Agency Y Merge/Federat e 2. Emperor 3. § Who will be the Emperor = King(X+Y)? § Note: a federation is similar to a merger, where the constitution of the system is administered by its Emperor. The peers agree to abide by the constitution. § Merging isn’t enough to solve the problem, until there is one empire.
Intercorporate Communication Q: How do we handle email between hierarchies? Answers: 1. Subsume Bridge Company X Agency Y Merge/Federat e 2. Emperor 3. § Who will be the Emperor = King(X+Y)? § Note: a federation is similar to a merger, where the constitution of the system is administered by its Emperor. The peers agree to abide by the constitution. § Merging isn’t enough to solve the problem, until there is one empire.
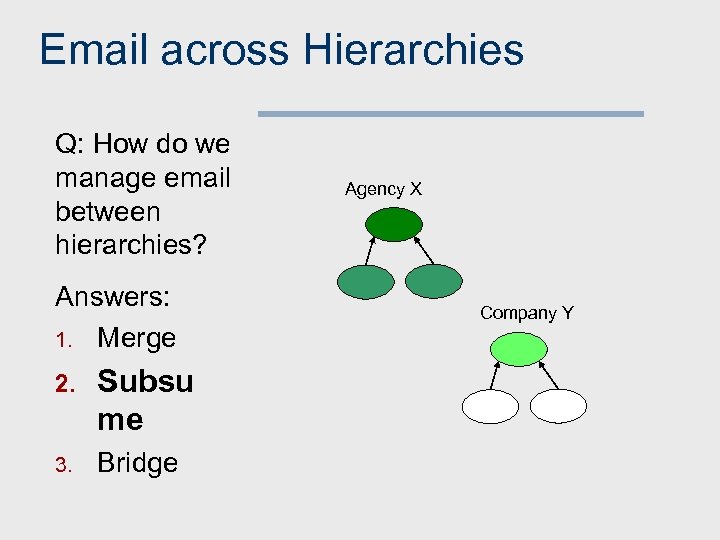 Email across Hierarchies Q: How do we manage email between hierarchies? Answers: 1. Merge 2. Subsu me 3. Bridge Agency X Company Y
Email across Hierarchies Q: How do we manage email between hierarchies? Answers: 1. Merge 2. Subsu me 3. Bridge Agency X Company Y
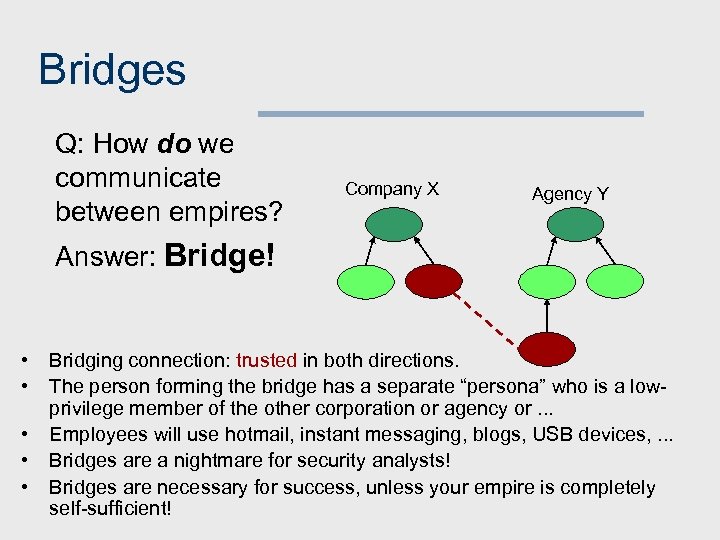 Bridges Q: How do we communicate between empires? Company X Agency Y Answer: Bridge! • • • Bridging connection: trusted in both directions. The person forming the bridge has a separate “persona” who is a lowprivilege member of the other corporation or agency or. . . Employees will use hotmail, instant messaging, blogs, USB devices, . . . Bridges are a nightmare for security analysts! Bridges are necessary for success, unless your empire is completely self-sufficient!
Bridges Q: How do we communicate between empires? Company X Agency Y Answer: Bridge! • • • Bridging connection: trusted in both directions. The person forming the bridge has a separate “persona” who is a lowprivilege member of the other corporation or agency or. . . Employees will use hotmail, instant messaging, blogs, USB devices, . . . Bridges are a nightmare for security analysts! Bridges are necessary for success, unless your empire is completely self-sufficient!
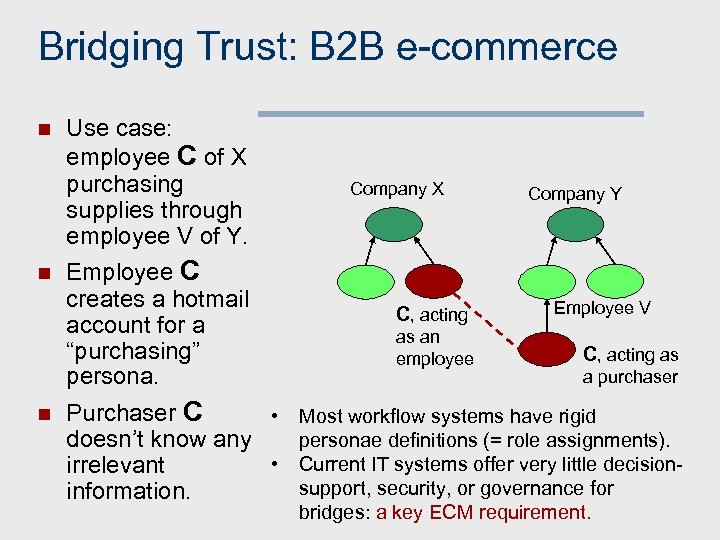 Bridging Trust: B 2 B e-commerce n n n Use case: employee C of X purchasing supplies through employee V of Y. Employee C creates a hotmail account for a “purchasing” persona. Company X C, acting as an employee Company Y Employee V C, acting as a purchaser Purchaser C • Most workflow systems have rigid doesn’t know any personae definitions (= role assignments). • Current IT systems offer very little decisionirrelevant support, security, or governance for information. bridges: a key ECM requirement.
Bridging Trust: B 2 B e-commerce n n n Use case: employee C of X purchasing supplies through employee V of Y. Employee C creates a hotmail account for a “purchasing” persona. Company X C, acting as an employee Company Y Employee V C, acting as a purchaser Purchaser C • Most workflow systems have rigid doesn’t know any personae definitions (= role assignments). • Current IT systems offer very little decisionirrelevant support, security, or governance for information. bridges: a key ECM requirement.
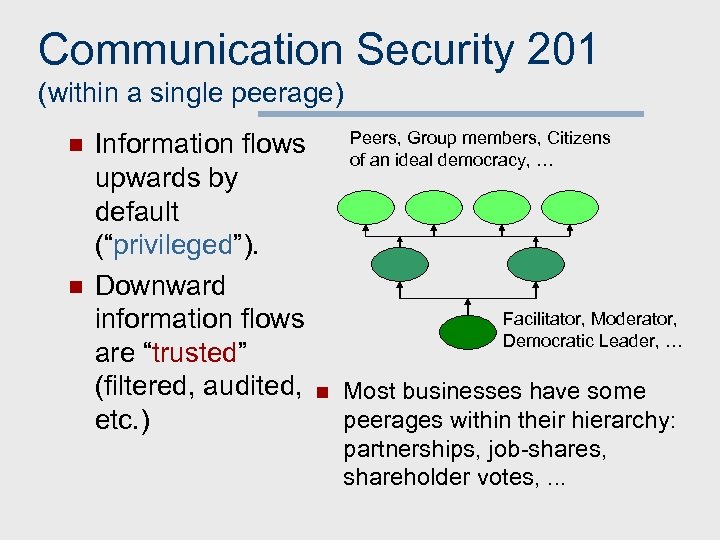 Communication Security 201 (within a single peerage) n n Information flows upwards by default (“privileged”). Downward information flows are “trusted” (filtered, audited, etc. ) Peers, Group members, Citizens of an ideal democracy, … Facilitator, Moderator, Democratic Leader, … n Most businesses have some peerages within their hierarchy: partnerships, job-shares, shareholder votes, . . .
Communication Security 201 (within a single peerage) n n Information flows upwards by default (“privileged”). Downward information flows are “trusted” (filtered, audited, etc. ) Peers, Group members, Citizens of an ideal democracy, … Facilitator, Moderator, Democratic Leader, … n Most businesses have some peerages within their hierarchy: partnerships, job-shares, shareholder votes, . . .
 What should an ECM system do? n ECMs should build (and advertise) bridges to 1. 2. 3. n n Current-generation ECM systems handle #1 and some of #2. Bridges are extremely important for performance, but they create security risks. • • • n facilitate intra-enterprise communication, facilitate intra-federation communication, and facilitate inter-federation communication. Every bridge to an external organisation should be subject to managerial oversight. The “rules of the bridge” must be defined before a bridge can be used safely. (Should a contract be signed? What are your requirements for IT security on the other end of the bridge? ) Employees need guidance and technical support, when forming and using external bridges. How important are bridges of types #2 and #3, to your organisation? • What are your corporate policies on these bridges, and how do you enforce them?
What should an ECM system do? n ECMs should build (and advertise) bridges to 1. 2. 3. n n Current-generation ECM systems handle #1 and some of #2. Bridges are extremely important for performance, but they create security risks. • • • n facilitate intra-enterprise communication, facilitate intra-federation communication, and facilitate inter-federation communication. Every bridge to an external organisation should be subject to managerial oversight. The “rules of the bridge” must be defined before a bridge can be used safely. (Should a contract be signed? What are your requirements for IT security on the other end of the bridge? ) Employees need guidance and technical support, when forming and using external bridges. How important are bridges of types #2 and #3, to your organisation? • What are your corporate policies on these bridges, and how do you enforce them?
 2. Technical Constraints n We haven’t yet agreed on our “public key infrastructure”. • • n Leading creators of “identity certificates”: Verisign, PGP/Thawte. Confederations or empires of “identity managers”: Microsoft’s Passport/Live ID, Liberty Alliance, . . . We can’t build a secure bridge unless we can securely identify a persona (organisational role) “on the other side”. • • I want to form a contract with an authorised purchasing agent for NZ Telecom, and not with someone who makes a false claim to this identity. Is your corporation willing to create and maintain digital certificates for all its authorised agents? Would you want to restrict access to this information?
2. Technical Constraints n We haven’t yet agreed on our “public key infrastructure”. • • n Leading creators of “identity certificates”: Verisign, PGP/Thawte. Confederations or empires of “identity managers”: Microsoft’s Passport/Live ID, Liberty Alliance, . . . We can’t build a secure bridge unless we can securely identify a persona (organisational role) “on the other side”. • • I want to form a contract with an authorised purchasing agent for NZ Telecom, and not with someone who makes a false claim to this identity. Is your corporation willing to create and maintain digital certificates for all its authorised agents? Would you want to restrict access to this information?
 Endpoint Compliance n We haven’t yet agreed on security standards for trusted endpoints. • • n Copy of SAS 70 certification (in the US)? Assured compliance (by whom? ) with (which? ) ISO 17799, 27000 series standards? Assured (by whom? ) compliance with (what? ) site-specific, jurisdiction-specific, industry-specific, culture-specific, standards and understandings regarding physical security, employment practices, system security, network security, . . . ? “TPM inside”? (If a Trusted Platform Module reports that its platform was booted with a known BIOS and known hardware configuration, does this address any of our security concerns? ) We can’t build a secure bridge without secure foundations!
Endpoint Compliance n We haven’t yet agreed on security standards for trusted endpoints. • • n Copy of SAS 70 certification (in the US)? Assured compliance (by whom? ) with (which? ) ISO 17799, 27000 series standards? Assured (by whom? ) compliance with (what? ) site-specific, jurisdiction-specific, industry-specific, culture-specific, standards and understandings regarding physical security, employment practices, system security, network security, . . . ? “TPM inside”? (If a Trusted Platform Module reports that its platform was booted with a known BIOS and known hardware configuration, does this address any of our security concerns? ) We can’t build a secure bridge without secure foundations!
 A Small Matter of Programming n Hundreds of millions of dollars have been spent on unsuccessful DRM/ECM systems for the corporate (C 2 C) market. n n n Building a secure ECM with type-2 (intra-federation) bridges is over-ambitious, except for well-structured communications among well-defined groups. n n A few DRM systems for the consumer market (= B 2 C distribution of media content) have been successful. B 2 C DRM systems don’t stop all “piracy”, but they do control it – for a while. In 2002, Wal-Mart required all its suppliers to use EDIINT AS 2 for their (structured) data exchanges. Building a secure ECM for general-purpose type-3 (inter-federation) bridges will be a monumental task.
A Small Matter of Programming n Hundreds of millions of dollars have been spent on unsuccessful DRM/ECM systems for the corporate (C 2 C) market. n n n Building a secure ECM with type-2 (intra-federation) bridges is over-ambitious, except for well-structured communications among well-defined groups. n n A few DRM systems for the consumer market (= B 2 C distribution of media content) have been successful. B 2 C DRM systems don’t stop all “piracy”, but they do control it – for a while. In 2002, Wal-Mart required all its suppliers to use EDIINT AS 2 for their (structured) data exchanges. Building a secure ECM for general-purpose type-3 (inter-federation) bridges will be a monumental task.
 Technology Isn’t Enough n n We’ll need international agreements: standards and assurances. We’ll need legal support in all participating jurisdictions, to deter and respond to personalidentity frauds, machine-identity frauds, assurance frauds, etc. We’ll need investigative support in all participating jurisdictions, to deter and detect frauds. A modest proposal: TPMs (in “trusted computers”) really should be licensed to owners, and owners should have responsibilities. • Automobiles, aircraft, gun owner/operators are licensed in most jurisdictions. • SIMcards are registered to owners in some jurisdictions. • What are the privileges and responsibilities of computer ownership?
Technology Isn’t Enough n n We’ll need international agreements: standards and assurances. We’ll need legal support in all participating jurisdictions, to deter and respond to personalidentity frauds, machine-identity frauds, assurance frauds, etc. We’ll need investigative support in all participating jurisdictions, to deter and detect frauds. A modest proposal: TPMs (in “trusted computers”) really should be licensed to owners, and owners should have responsibilities. • Automobiles, aircraft, gun owner/operators are licensed in most jurisdictions. • SIMcards are registered to owners in some jurisdictions. • What are the privileges and responsibilities of computer ownership?
 Feasible and Desirable ECM n Our identity management, persona (role) management, reputation management, trust management, and end-point assurance procedures are non-standard and don’t interoperate. • Our ECM systems will be limited by these shortcomings. n We can’t expect strong control on confidentiality. • Computers aren’t sufficient to enforce confidentiality constraints. • If someone can read a document, they can take a picture of it – this is the “analog hole” in all DRM systems. • If we allow people outside our zone of legal/physical control to read our documents, they can copy them without our knowledge. n n We can expect good control on document integrity and authorship identification, if our authors and readers are willing (and are trained) to work with digital certificates. We can expect more efficient and effective distribution of our corporate documents, if we web-publish them instead of squirrelling them away on our workstations and shared fileservers.
Feasible and Desirable ECM n Our identity management, persona (role) management, reputation management, trust management, and end-point assurance procedures are non-standard and don’t interoperate. • Our ECM systems will be limited by these shortcomings. n We can’t expect strong control on confidentiality. • Computers aren’t sufficient to enforce confidentiality constraints. • If someone can read a document, they can take a picture of it – this is the “analog hole” in all DRM systems. • If we allow people outside our zone of legal/physical control to read our documents, they can copy them without our knowledge. n n We can expect good control on document integrity and authorship identification, if our authors and readers are willing (and are trained) to work with digital certificates. We can expect more efficient and effective distribution of our corporate documents, if we web-publish them instead of squirrelling them away on our workstations and shared fileservers.
 Browser-Based ECMs n It’s not hard to imagine a browser-based ECM architecture • Google. Apps with security governance; Share. Point with open-standard interfaces; Lotus Connections with type-2 and type-3 bridges; . . . • Use HTTPS rather than HTTP; unencrypted or encrypted with keys held by corporation (so that it can be filtered); two-way authentication. n A licensed TPM owner could generate adequately-secure digital certificates for their end-users. • TPM owners should be de-licensed if their computers don’t pass a periodic “warrant of fitness”. • Certificates issued by a corporate TPM could (except when anonymity is required) be signed with company authority. • This would greatly simplify ECM design: existing webservices could be converted into type-3 ECM bridges. n A corporate workstation could keep track of all certificates it has accepted (= bridges it has built), for managerial oversight and security auditing. • Would you ever want to take an inventory of these bridges? • Would your employees think it’s an invasion of privacy? • What do you want from an ECM system?
Browser-Based ECMs n It’s not hard to imagine a browser-based ECM architecture • Google. Apps with security governance; Share. Point with open-standard interfaces; Lotus Connections with type-2 and type-3 bridges; . . . • Use HTTPS rather than HTTP; unencrypted or encrypted with keys held by corporation (so that it can be filtered); two-way authentication. n A licensed TPM owner could generate adequately-secure digital certificates for their end-users. • TPM owners should be de-licensed if their computers don’t pass a periodic “warrant of fitness”. • Certificates issued by a corporate TPM could (except when anonymity is required) be signed with company authority. • This would greatly simplify ECM design: existing webservices could be converted into type-3 ECM bridges. n A corporate workstation could keep track of all certificates it has accepted (= bridges it has built), for managerial oversight and security auditing. • Would you ever want to take an inventory of these bridges? • Would your employees think it’s an invasion of privacy? • What do you want from an ECM system?
 Acknowledgement n This research was supported by your tax payments, via New Zealand’s Foundation for Research Science and Technology. Thank you!
Acknowledgement n This research was supported by your tax payments, via New Zealand’s Foundation for Research Science and Technology. Thank you!


