53effd3954e6701267d76b7cfc4036ba.ppt
- Количество слайдов: 103

Election Systems 2016 February 16, 2016 By Jim Soper http: //Counted. As. Cast. org/election-systems-2016/

Jim Soper • Co-Chair: Voting Rights Task Force (East Bay) www. meetup. com/Voting-Rights-Task-Force. East-Bay/ • Author: www. Counted. As. Cast. org & www. Counted. As. Cast. com • SF Voting Systems Task Force, 2009 -11 • 11 years, election integrity (EI) advocate • Senior software consultant (DEC) and programmer for AI & mobile devices (Sencha) • Jim. Soper 2@yahoo. com

Some Issues (not in any particular order) • Testing & Certification • Vote by mail (Vb. M) • DREs (touchscreens) & Scanners • Paper trails & paper ballots • Hand Counting (HCPB) • Auditing • Monitoring • Open Source • End-to-end systems • Internet voting (IV) • en. wikipedia. org/wiki/Electoral_fraud
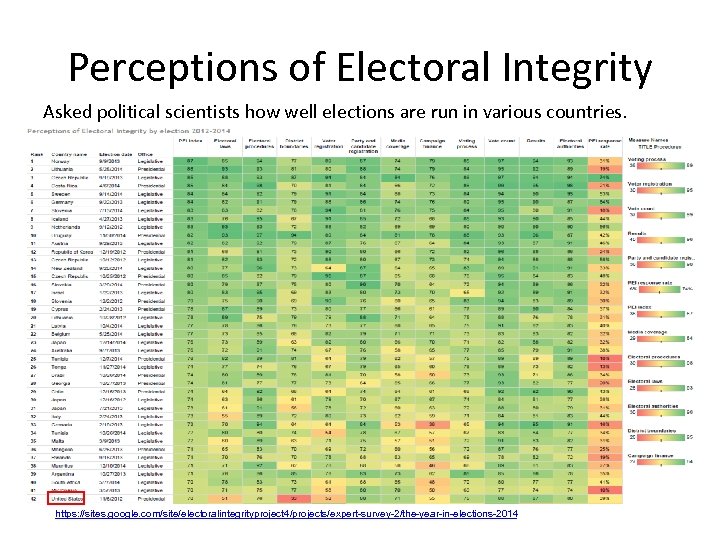
Perceptions of Electoral Integrity Asked political scientists how well elections are run in various countries. https: //sites. google. com/site/electoralintegrityproject 4/projects/expert-survey-2/the-year-in-elections-2014

Congress Can Stop the Chaos • US Constitution: Section 4. • The Times, Places and Manner of holding Elections for Senators and Representatives, shall be prescribed in each State by the Legislature thereof; but the Congress may at any time by Law make or alter such Regulations, except as to the Places of chusing Senators.

Why People Don’t Vote Government corruption Government gridlock Need multiple parties that people can vote for Need proportional representation to eliminate gerrymandering. 1 citizen, 1 vote. • Negative & dirty campaigns • Inconvenient to register • Inconvenient to vote • •
My Introduction to Election Integrity (EI) • In most states, if you are a felon, you are not allowed to vote. Sometimes even ex-felons. • BUT ….
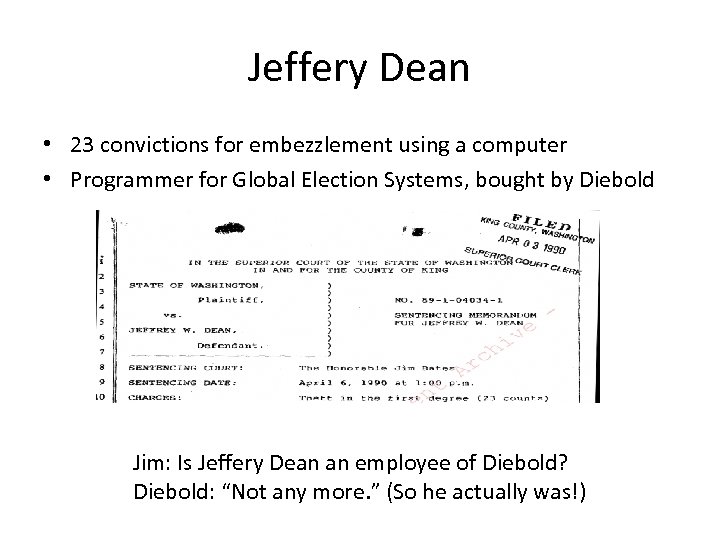
Jeffery Dean • 23 convictions for embezzlement using a computer • Programmer for Global Election Systems, bought by Diebold Jim: Is Jeffery Dean an employee of Diebold? Diebold: “Not any more. ” (So he actually was!)

John Elder • Jeffery Dean’s boss at GES/Diebold • Convicted cocaine trafficker • Elder & Dean met in prison!

Diebold et al • Diebold renamed to Premier, then bought by ES&S, and then sold to Dominion. • “I am committed to helping Ohio deliver its electoral votes to the president next year. ’’ – Wally O’Dell, CEO, Diebold, 2003 • Supersecret encryption code: 8 f 2654 hd 4 • An review of Diebold/Premier/Dominion’s history would take an hour by itself. https: //en. wikipedia. org/wiki/Premier_Election_Solutions

The Others: ES&S, Hart, Dominion • ES&S, Hart & Dominion, which bought Sequoia, and Diebold, are not much better. • READ: Black Box Voting, by Bev Harris especially chapter 8 “Company Information” http: //blackboxvoting. org/bbv_chapter-8. pdf
Videos • Archive: www. countedascast. com/resources/videos. php • Louisiana, Susan Bernacker checks the machines: www. countedascast. com/videos/louisiana-dill-25 fps-320 x 240. mov • Hacking demo by Princeton Univ. on Fox & Friends: www. countedascast. com/videos/princeton-diebold-virus-demo-fox-30 fps 320 x 240. mp 4 • MANY more on You. Tube – search for “voting machines changing votes” • Clint Curtis testifies about programming a vote rigging machine https: //www. youtube. com/watch? v=t 4 a. KOhbb. K 9 E
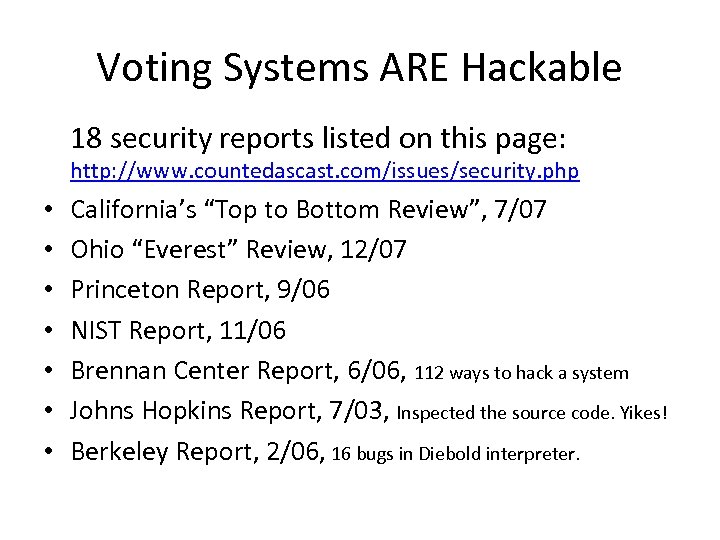
Voting Systems ARE Hackable 18 security reports listed on this page: http: //www. countedascast. com/issues/security. php • • California’s “Top to Bottom Review”, 7/07 Ohio “Everest” Review, 12/07 Princeton Report, 9/06 NIST Report, 11/06 Brennan Center Report, 6/06, 112 ways to hack a system Johns Hopkins Report, 7/03, Inspected the source code. Yikes! Berkeley Report, 2/06, 16 bugs in Diebold interpreter.
Dilbert Gets It!

Past • Counting hands • Hand counting – Corruption, vote buying in taverns (late 1800 s) – Some books • Broken Ballots: Will Your Vote Count? (Simons & Jones) • Steal This Vote: Dirty Elections and the Rotten History of Democracy in America • Deliver the Vote: A History of Election Fraud, an American Political Tradition-17422004 • Ballot Battles: The History of Disputed Elections in the United States • The Right to Vote: The Contested History of Democracy in the United States • Lever machines • Punch cards

Florida, 2000 • Yes, votes were stolen – Volusia County • The problem was not the chads, but that they lacked the time & will to recount the votes. • Move the meetings of the Electoral College to January. Federal Law from the late 1800 s. – US Code: Title 3, Chapter 1, § 7 & § 15

HAVA 2002 • Author: Robert Ney, Ohio (Diebold) – 30 month jail sentence for corruption • $4 Billion for new voting machines – They are getting old • Provided for Provisional voting • Election Assistance Commission (EAC)

Ohio 2004 • Long lines • Cuyahoga County • Kerry conceded too quickly. • Witness to a Crime, by Richard Hayes Phillips The definitive book on stealing votes in Ohio. Read about Franklin County.

Fall of 2006, A Turning Point • Princeton demos on CNN & Fox • Bowen elected

South Carolina, June 8, 2010 • South Carolina uses voting machines with no auditable paper trail. Other than absentee ballots , it’s all electronic. • Alvin Greene (see Wikipedia) – No campaign. No business cards. No money. No ads. No appearances. No staff. Somebody paid $10 K filing fee. – Wins democratic primary for US Senate: 100, 000 votes. – Defeats Vic Rawl • 8 years, South Carolina House of Representatives • 8 years, Circuit Court Judge • Charleston City Council, 2008 -? – Feb 15, 2011, Greene runs for the House: 37 votes.

South Carolina, 2016 • SC still has all-electronic voting machines. • Be wary of any primary “surprise”.

Iowa Caucuses, 2012 • Santorum won by 12 votes instead of losing to Romney by 8. Not widely reported until the spring. http: //www. kcci. com/Could-Typo-Rewrite-Caucus. History/10379876#ixzz 1 id. Uftgoh • Also: “the vote totals of eight precincts were never counted. ” (Why? ) https: //en. wikipedia. org/wiki/United_States_presidential_ele ction_in_Iowa, _2012

Iowa Caucuses 2016 • Demonstrated that we need to be able to count and recount the votes when the race is close. • It also demonstrated that running an election is very difficult.
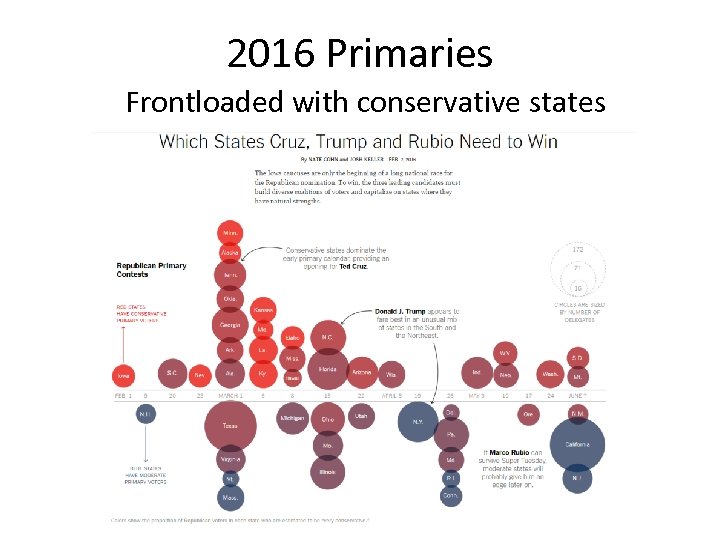
2016 Primaries Frontloaded with conservative states
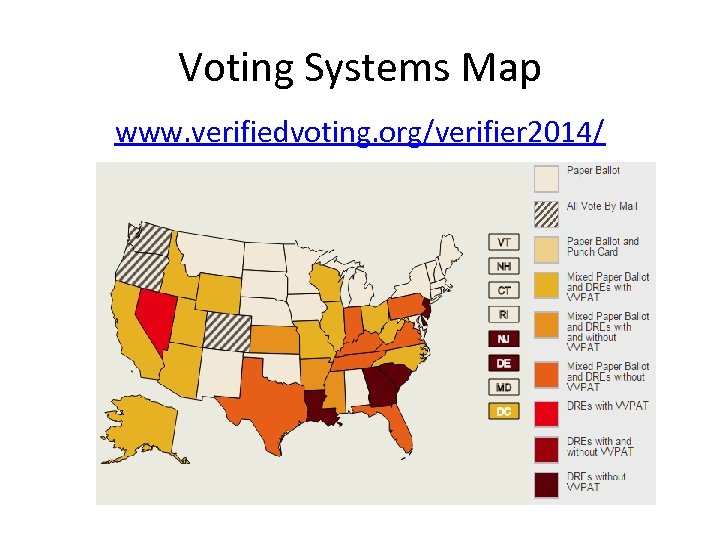
Voting Systems Map www. verifiedvoting. org/verifier 2014/
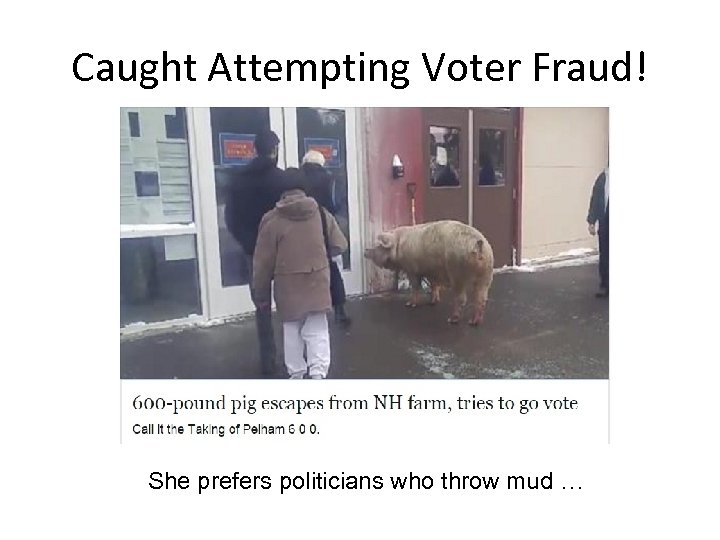
Caught Attempting Voter Fraud! She prefers politicians who throw mud …

Voter Impersonation • Texas Rep. Debbie Riddle says you should not be able to vote in place of someone else. • So does Wisc. Rep. Joel Kleefisch.
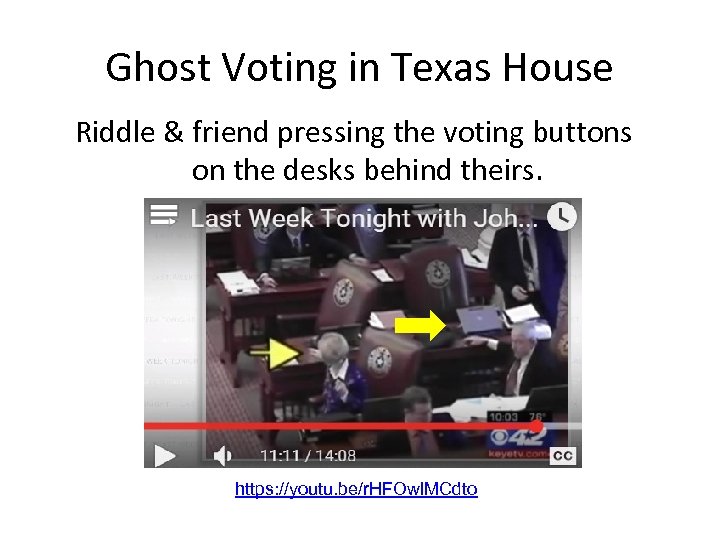
Ghost Voting in Texas House Riddle & friend pressing the voting buttons on the desks behind theirs. https: //youtu. be/r. HFOwl. MCdto
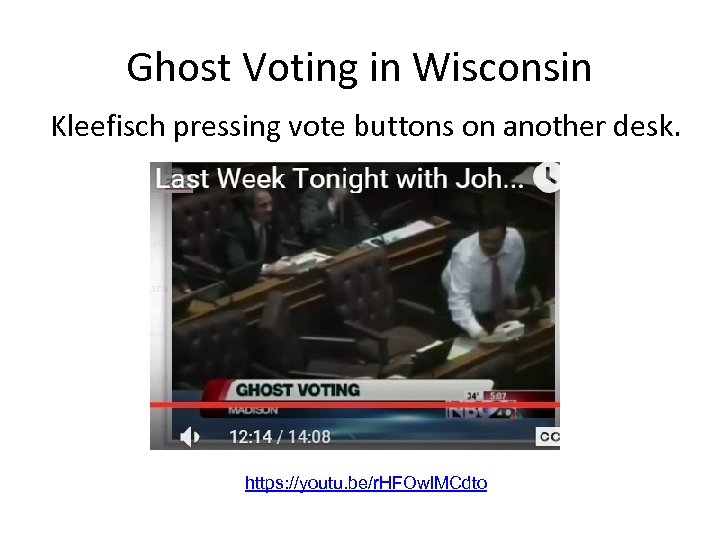
Ghost Voting in Wisconsin Kleefisch pressing vote buttons on another desk. https: //youtu. be/r. HFOwl. MCdto

Ghost Voting in California!

California 90% paper ballots LA uses Inkavote ballot ~50% vote by mail (Vb. M) Manual tally of 1% of precincts (a spot check). • AB 44 (2015), statewide recount if winning margin is less than 0. 0015% • •

National • Election Assistance Commission (EAC) • Voluntary Voting Systems Guidelines • Federal “testing” (think Volkswagen!) www. countedascast. com/issues/testing. php • SB 360 (Padilla, 2013), eliminated federal testing for California CA regulations (by Bowen) are tougher than federal • Red team (hack) testing • Better provisions for the disabled

Hand Counting • HCBP: Hand Counted Paper Ballots in the precincts. • Pro: if done right, increases confidence in the election. • Cons: – Logistics: LA would need at least 16, 000 counters for over 4, 000 precincts – Opposition counters & observers not likely to want to go into dangerous territory, be it in the deep South or city ghettos. – Additional expenses for logistics and labor. – Hand counting can also be inaccurate (it’s mind-numbing). • Iowa republican caucus, 2012, was hand counted, but still wrong. So was the 97% vote for annexation of Crimea by Russia. Not the only examples. • Canada, Germany, Ireland … count by hand, but only 1 or 2 races. • Tunisia (October, 2010) – Highly charged election. – Showed every ballot to everybody in the room in SF. – Results accepted by nearly everybody.
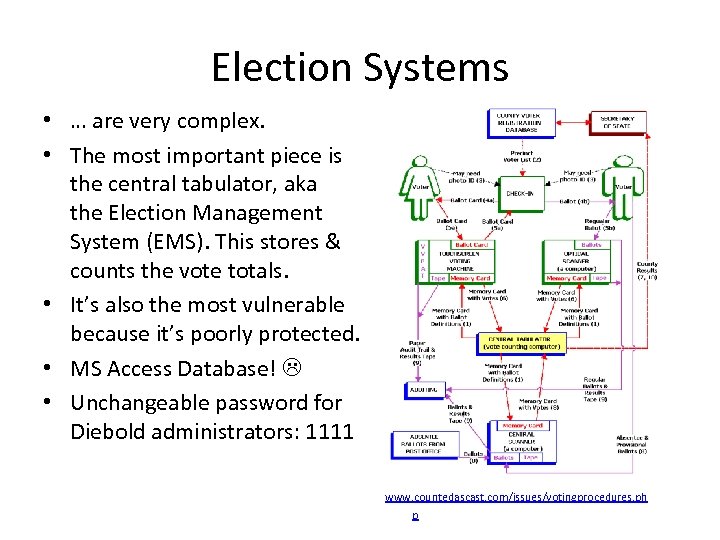
Election Systems • … are very complex. • The most important piece is the central tabulator, aka the Election Management System (EMS). This stores & counts the vote totals. • It’s also the most vulnerable because it’s poorly protected. • MS Access Database! • Unchangeable password for Diebold administrators: 1111 www. countedascast. com/issues/votingprocedures. ph p

Running An Election … • Is like running a regional airline. • Planes, vehicles, cabin crew, ground crew, baggage, supplies, demanding customers, confusing regulations, lawyers & the press … • With an army of under-paid temps … • With no practice runs … • And it MUST work on E-Day. • Contra Costa County in 2009, 700+ steps! • Thank your election officials!

SB 450 (2016, proposed) • • • Vote by mail ballots sent to every voter Vote centers open for 10 days Vote from anywhere in the county County optional Depends on statewide registration database to prevent double voting – Secretary Padilla making that happen
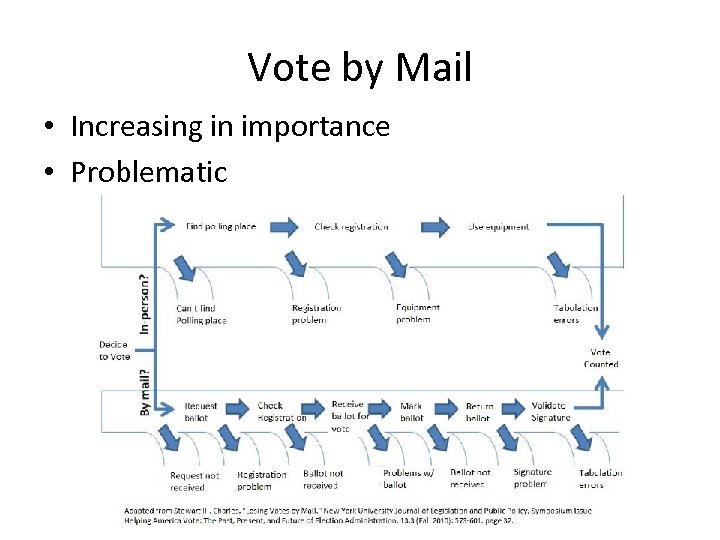
Vote by Mail • Increasing in importance • Problematic

LA’s New Voting System • • Started 2009 Roll out in LA about 2018 Not decided yet if it will be open source Of statewide and national importance www. lavote. net/vsap/about www. lavote. net/vsap/research www. lavote. net/vsap/project-overview www. cbsnews. com/news/design-firm-tackles-aging-votingmachines/
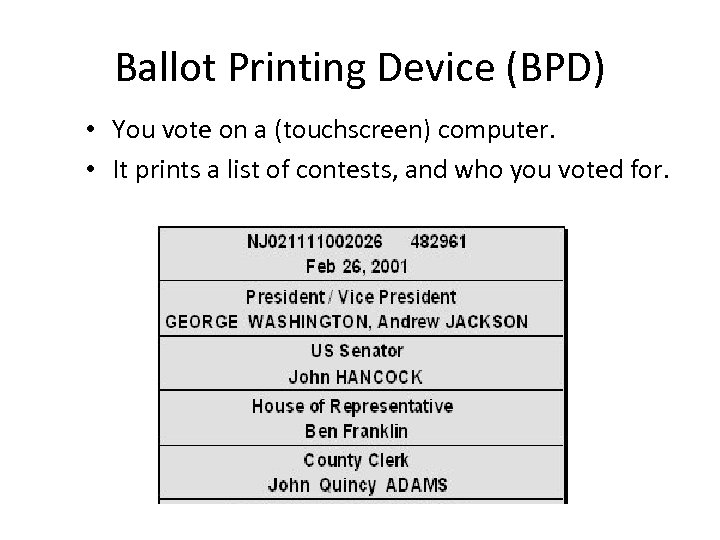
Ballot Printing Device (BPD) • You vote on a (touchscreen) computer. • It prints a list of contests, and who you voted for.

LA’s New Voting Station (2018) Ballot Printing Device (BPD) with printer and QR Code reader

QR Code Scanner The voter prepares their ballot on a mobile device at home, then shows the QR Code to the voting station, which displays the choices on the screen to the left. The voter may make any changes on the screen. They then print the ballot out for review and casting. www. lavote. net/Documents/vsap/5. 2%20 BMD%20 appearance%20 model. pdf
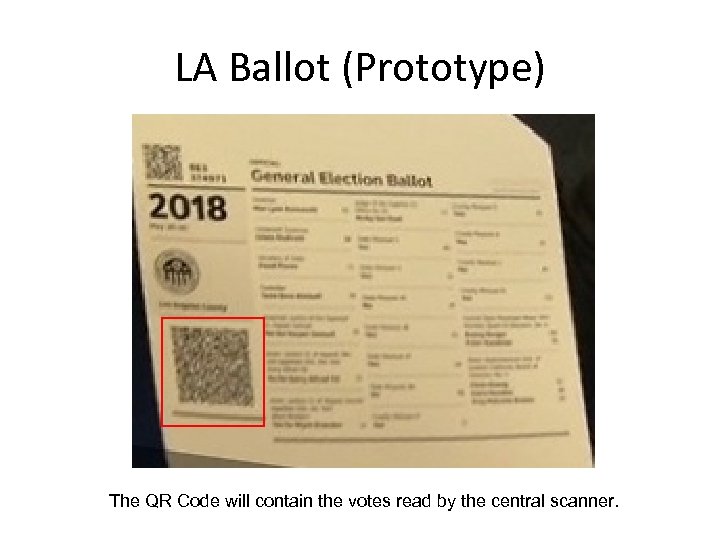
LA Ballot (Prototype) The QR Code will contain the votes read by the central scanner.
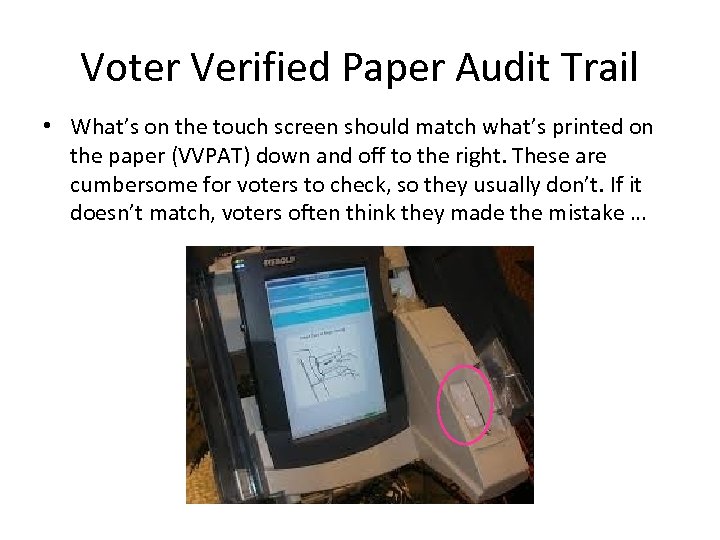
Voter Verified Paper Audit Trail • What’s on the touch screen should match what’s printed on the paper (VVPAT) down and off to the right. These are cumbersome for voters to check, so they usually don’t. If it doesn’t match, voters often think they made the mistake …

VVPATs • VVPATs are also hard to (re)count. • Use real paper ballots!

Auditing • Risk-Limiting Audits The closer the race, the more ballots you randomly check. Dr. Phillip Starks, UC Berkeley www. verifiedvoting. org/resources/post-election-audits/ • Humboldt Transparency Project Independent rescan & recount by computer of the ballots http: //democracycounts. blogspot. com/ Trachtenberg Election Verification System http: //humetp. mitchtrachtenberg. com/ • Also: Bravo, Diff. Sum, Black-box, Baysian, Bootstrap, T-pile, & Comparison http: //people. csail. mit. edu/rivest/pubs/Riv 15 y. pdf
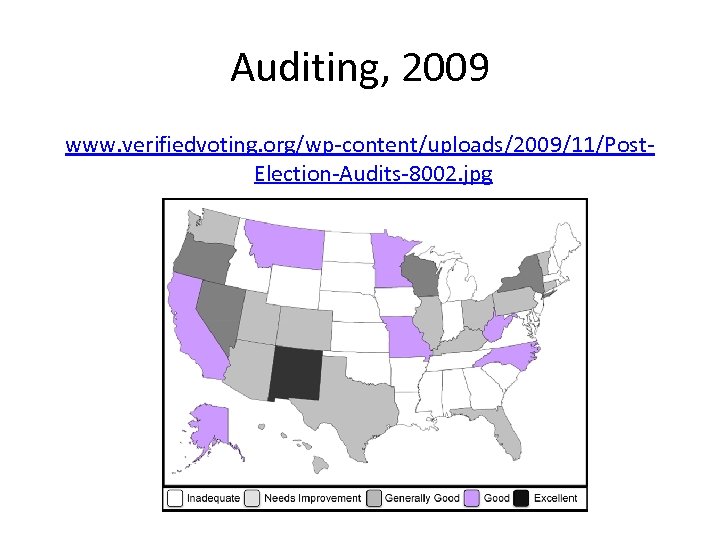
Auditing, 2009 www. verifiedvoting. org/wp-content/uploads/2009/11/Post. Election-Audits-8002. jpg

Monitoring • The central tabulator is the most important, and the most vulnerable part of the system to insider tampering. • Campaigns engage many lawyers to watch the precincts. Unfortunately, they do not have a clue what happens inside the voting machines, or at central headquarters.
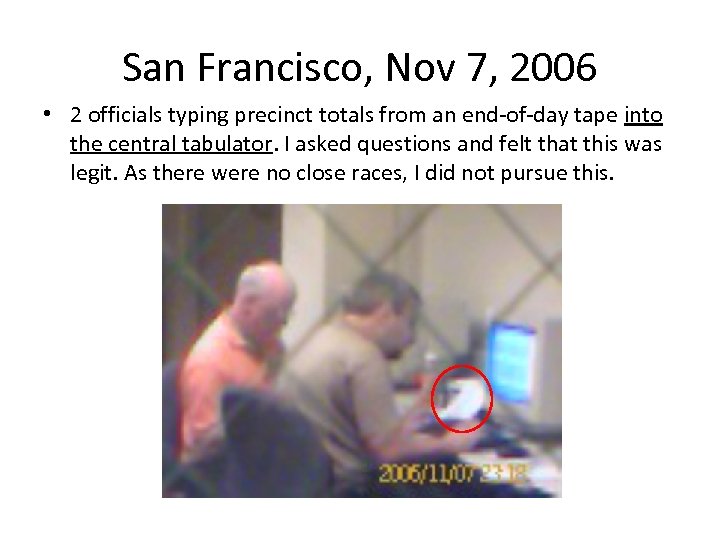
San Francisco, Nov 7, 2006 • 2 officials typing precinct totals from an end-of-day tape into the central tabulator. I asked questions and felt that this was legit. As there were no close races, I did not pursue this.

Monitoring • At county HQ, whenever there is a change in the pattern/rhythm of what they are doing, pay attention! • Candidates: do NOT concede if the race is close. • Campaigns generally do not know how to monitor an audit or recount. • Resources: www. countedascast. org/monitoring-elections/ www. countedascast. com/resources/monitoring. php

Brennan Center Report (1/16) “Election Integrity: A Pro-Voter Agenda” 1) Modernize Voter Registration To Improve Voter Rolls A priority for Secretary Padilla 2) Ensure Security and Reliability of Our Voting Machines 3) Do Not Implement Internet Voting Systems Until Security is Proven 4) Adopt Only Common-Sense Voter Identification Proposals 5) Increase Security of Mail-In Ballots 6) Protect Against Insider Wrongdoing www. brennancenter. org/publication/election-integrity-pro-voter-agenda

Open Source • The problem is that we cannot look at the closed software from Dominion, Hart or ES&S. We can’t know what it’s doing. • Disclosed source means that the anybody can read the source code. • Open source usually means that anybody can read it, change it, and/or sell it. This reduces abusive vendor control of the counties because we can then go elsewhere for support. • Disclosed/open source is not a panacea. The computer code is far too complex, and insiders can manipulate it in amazing ways. And it too can be hacked (eg: the Heartbleed bug). • We MUST be able to audit everything.
Coming Open Source Systems • Digital Foundry & Ideo (with LA) www. ideo. com • Galois, Dr. Joe Kiniry, Kiniry@Galois. com • Open Source Election Technology Foundation www. OSETFoundation. org • Prime III, Dr. Juan Gilbert, U. Florida To be used in NH primaries, 2016 www. primevotingsystem. org/ www. youtube. com/watch? v=b. M 5 DKP 4 c 4 aw • Star-Vote, Travis County (Austin) Texas traviscountyclerk. org/eclerk/Content. do? code=Elections traviscountyclerk. org/eclerk/content/images/pdf_STARVote_2015. 06. 03_RFI. pdf

Internet Voting It’s trendy Convenience Increases turnout? ? Cost savings after fully implemented & debugged? Computers are more flexible than paper (which is also part of the problem. . . ) • Would be helpful for some overseas citizens … • • •

Help Overseas Voters • The claim is that our service members overseas are having trouble getting their ballots back on time that IV would help solve that. • BUT – the studies show that almost all ballots arrive back within 7 days. The biggest problem is getting registered, maintaining the correct address, and getting the ballots overseas to them. • The solution is to use the Internet to get blank ballots to them. They can then print them out, mark them, and mail or fax the ballot back to the county. • All of which is legal in California.

Personal Issue For Me • I lived overseas for 17 years. I know the problems of voting from overseas. I know what the advantages IV would be. • But they are not worth the national security risks to our government …

Internet Voting Risks • There have been many articles and reports written about IV. • Here is one: “Internet Voting Risks” (2013) www. countedascast. org/internet-voting-risks/ • See also: Verified. Voting. org www. verifiedvoting. org/resources/internet-voting/ www. verifiedvoting. org/internet-voting-outside-the-united-states/ • A reading/video list: “Internet Voting Resources” countedascast. org/internet-voting-risks/internet-voting-reading-list/

The Wild West of the Internet • Articles about break-ins, security holes, and warnings appear almost daily. • For the most recent news, see: – the Ars Technica security page arstechnica. com/security/ – articles by Kim Zetter of WIRED magazine www. wired. com/author/kimzetter/ – And DARKReading. com

US government says IV is not secure.

E 2 E-V IV Report • End-To-End Verifiable Internet Voting (2015) countedascast. org/internet-voting-risks/endto-end-verifiable-internet-voting/ • Written by 10 election officials, computer security experts, and specialists in disability, usability, auditing, testing, and legal issues. • It included both IV optimists, and skeptics. • Thorough
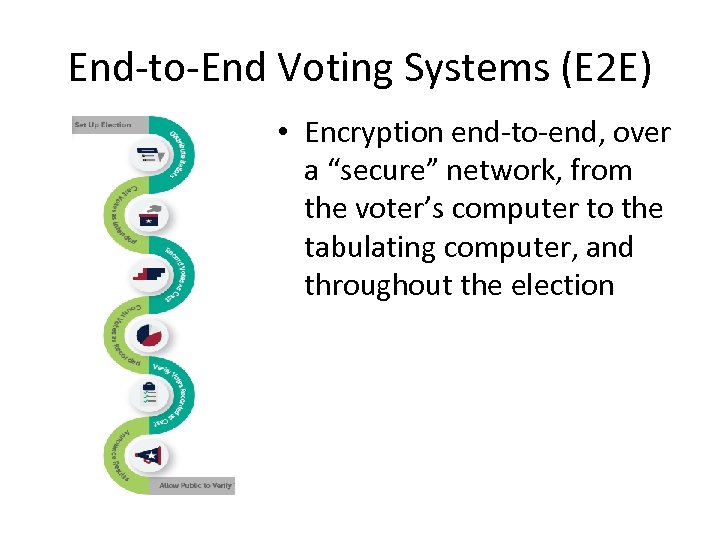
End-to-End Voting Systems (E 2 E) • Encryption end-to-end, over a “secure” network, from the voter’s computer to the tabulating computer, and throughout the election
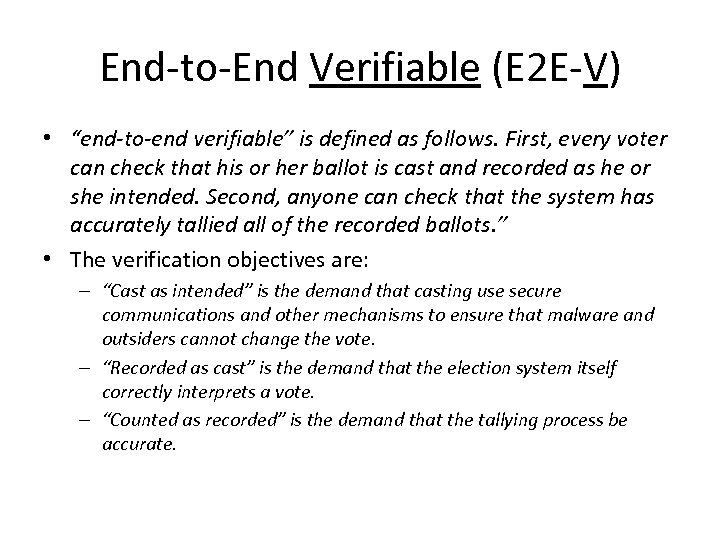
End-to-End Verifiable (E 2 E-V) • “end-to-end verifiable” is defined as follows. First, every voter can check that his or her ballot is cast and recorded as he or she intended. Second, anyone can check that the system has accurately tallied all of the recorded ballots. ” • The verification objectives are: – “Cast as intended” is the demand that casting use secure communications and other mechanisms to ensure that malware and outsiders cannot change the vote. – “Recorded as cast” is the demand that the election system itself correctly interprets a vote. – “Counted as recorded” is the demand that the tallying process be accurate.

E 2 E-VIV • Some E 2 E systems allow voter to verify online that their ballot was correctly recorded. – Not easy for the voter to do – Recorded is different from counted – Need to verify ALL the ballots, AND the totals

9. 2. 2 Research And Engineering Challenges • • Although E 2 E-V is necessary for a viable Internet voting system, use of E 2 E-V does not ensure that an Internet voting system is free from vulnerabilities. Also, the definition of an E 2 E-VIV protocol for U. S. elections is very challenging. In particular, the research community must determine how to address five key challenges: – how to handle large-scale dispute resolution; – how to authenticate voters for public elections; – how to defend an E 2 E-VIV system against denial-of-service attacks and automated attacks that aim to disrupt large numbers of votes; – how to make verifiability comprehensible and useful to the average voter; and – how to avoid voter coercion and vote selling in the context of digital observation of voting and verification. The main issues with usability are: – how to ensure usable vote privacy and vote integrity in the presence of clientside malware and – how to ensure that verification is usable and accessible to the typical set of voters.
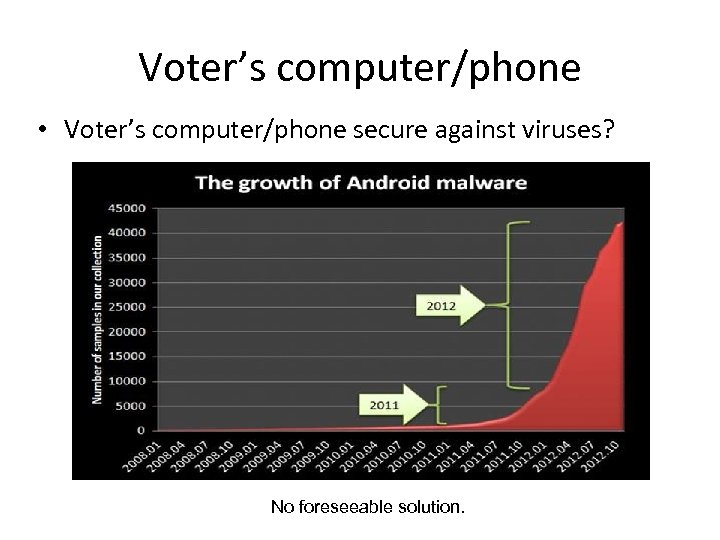
Voter’s computer/phone • Voter’s computer/phone secure against viruses? No foreseeable solution.
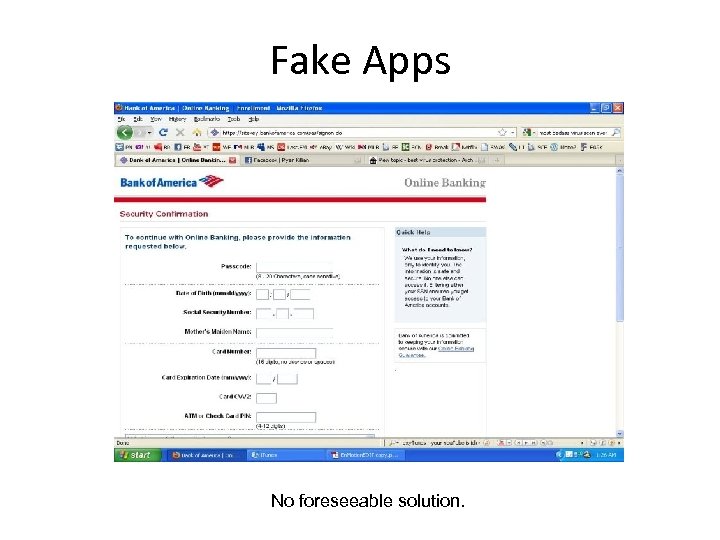
Fake Apps No foreseeable solution.
They know who you are … • “Hackers Are Sharing Reams of US Voter Data on the Dark Web” (1/18/16) http: //motherboard. vice. com/read/hackers-are-sharing-reams-of-usvoter-data-on-the-dark-web • “How to Make Your Own NSA Bulk Surveillance System” (1/27/16) www. wired. com/2016/01/how-to-make-your-own-nsa-bulk-surveillancesystem/ • So they can target the computers/phones of specific groups of voters.

Verification • Must be able to prove to the losers that they lost. • Must allow for public audit. But how do you audit a paperless system? • Must allow for large scale resolution of disputed votes. • No foreseeable solution.

Internet voting system secure from insider attacks? • Need open/disclosed source AND public auditing. • Otherwise, no foreseeable solution.
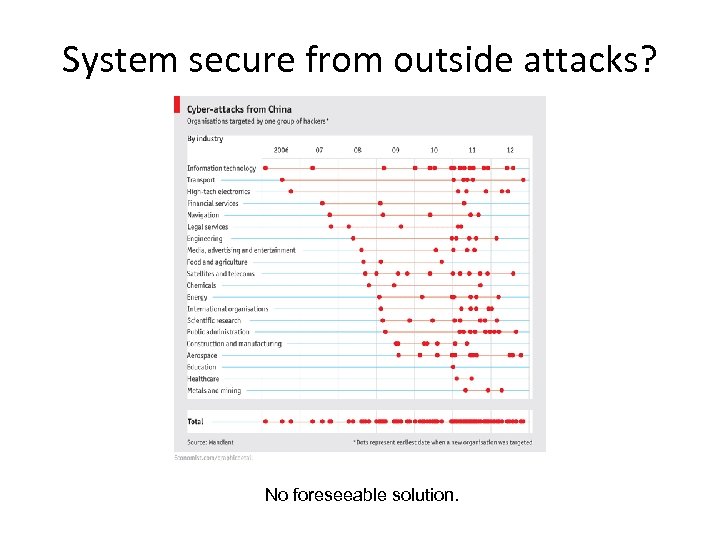
System secure from outside attacks? No foreseeable solution.

Denial of Service Attacks • The enemy sends millions of messages at the website, making it unable to respond. • No foreseeable solution.

Require public testing (Washington DC, 2010) • IV system opened to “red team” attacks. • Within 36 hours, “wolverines” from the Univ. of Michigan had complete control of everything. • System passwords, ballots, voter emails & passwords, tabulator, video cameras … everything. • Officials canceled the project. • “Hacking the D. C. Internet Voting Pilot” https: //freedom-to-tinker. com/blog/jhalderm/hacking-dc-internet-voting-pilot/
Banking Online Is Safe? • Actually online banking is not safe, it’s just insured. • Banks lose hundred of millions of dollars a year. They don’t want to tell you about it. (Talk with their security experts …) • ID & credit card theft is a huge problem. • Hacked: JP Morgan, Bank of America, Wells Fargo, C. Schwab • And no, I don’t “bank” online. It really is not safe. • At least with banking, you have a receipt for the transaction. With voting, no receipt, no tracking, no proof of what you did. • How do you refund a vote? • https: //www. verifiedvoting. org/if-i-can-shop-and-bank-online -why-cant-i-vote-online/

Internet Voting History • Pentagon – Federal Voting Assistance Program www. FVAP. gov was pushing IV very, very hard. • • • Washington DC (failed) Norway (tried and rejected) Estonia (highly contested) Germany (unconstitutional) Netherlands (rejected) …

Why No Quick Fix? • Bioscience has been trying to find a cure for the common cold for many decades. • So far, nothing, because viruses are complex, hard to see, and they keep on evolving. • Likewise with computer viruses. Only, computer viruses really are intelligently designed. They exist to attack a computer, and they can be programmed to “adapt” to their environment (re: the Stuxnet centrifuge virus).

It’s getting worse • It’s not illegal to create or sell malware. • The US spy agencies buy thousands of them. And it sometimes doesn’t tell Microsoft, Google, Apple about what it knows. . . - from Countdown to Zero Day, by Kim Zetter • You can now rent malware services on the black market for a few hundred dollars. – Harri Hursti, cybercrime expert

Stuxnet Virus • Successful attacks on unseen Iranian nuclear centrifuges buried deep underground … • … and NOT connected to the Internet! (but their programmers were) • Huge effort by US spy agencies • Astoundingly clever & very expensive • The first serious effort to “weaponize” the Internet • This was an APT – Advanced Persistent Attack • Countdown to Zero Day, by Kim Zetter //www. wired. com/2014/11/countdown-tozero-day-stuxnet/

NSA Tells Us How It’s Done • In January, the NSA's Tailored Access Unit outlined they create an Advanced Persistent Threat (APT) against high-value targets. • https: //www. yahoo. com/tech/nsa-chief-hackerexplains-keep-nsa-business-040001861. html • Hint: be more persistent than advanced; just expect them to make a tiny mistake, they will.

A Tiny Mistake • Used in the Washington DC hack • In this case, using double quotes: " or single quotes: ‘ matters. • • • “ 3. 1 Shell-injection vulnerability: … The server stores uploaded ballots in a temporary location on disk, and the DVBM application executes the gpg command to encrypt the file, using the following code: run ( "gpg”, "--trust -model always –o "#{File. expand_path ( dst. path) }" -e -r "#{@recipient }" "#{F i l e. expand_path ( src. path ) }" " ) The run method invoked by this code concatenates its first and second arguments, collapses multiple whitespace characters into single characters, and then executes the command string using Ruby’s backtick operator, which passesthe provided command to the shell. The Paperclip Rails plugin, which the application uses to handle file uploads, preserves the extension of the uploaded ballot file, and no filtering is performed on this extension, so the result of File. expand_path(src. path) is attacker controlled. Unfortunately, in the Bash shell used on the server, double quotes [instead of single quotes] do not prevent the evaluation of shell metacharacters, and so a ballot named foo. $(cmd) will result in the execution of cmd with the privileges of the web application. ” https: //jhalderm. com/pub/papers/dcvoting-fc 12. pdf

Inevitable? • “Internet voting is inevitable” • No it’s not. They want you to believe that. But it’s not. • In the 1950’s, they were telling us that “nuclear power is inevitable”. • Turns out, it’s not. For the same reason that IV is not “inevitable” • … because catastrophic meltdowns are inevitable, at least with foreseeable technology. • Even IF inevitable, IV is not ready, now, nor in the foreseeable future. • Mistakes happen constantly.

IV Meltdown • What does this look like? • Alvin Greene sweeps LA

Roy G. Saltman • Pioneer in standards for voting systems • “I fully agree that no Internet connection should be permitted. “ http: //sacredhumanism. net/letter-to-california-voter-foundation/

Richard Stallman • Pioneer in open source software • Why you can't trust internet voting. 0. You can't trust counting the votes in a computer. The people who run the server might rig the software to lie. (This applies to all use of computers to count votes. ) 1. It is not good enough if the voting client software is secure. If your machine is a zombie, the botnet will choose your vote. 2. It is not good enough if the client computer is secure. Your boss could insist you vote while he watches. Copyright (c) 2014 Richard Stallman Verbatim copying and redistribution of this entire page are permitted provided this notice is preserved. https: //stallman. org/internet-voting. html • See also: https: //stallman. org/evoting. html

IV Bills in California • • SB 908 (2011): Email voting AB 1929 (2012): Cloud-based ballot marking AB 19 (2013, Ting): IV Pilots AB 887 (2016, Ting): IV and email voting
VRTF: 4 Wins, No Losses ü All defeated by Secretaries Padilla & Bowen, the Voting Rights Task Force, and democracy advocates across California.
A Map of the Internet
What they want to do … … is take a central computer. in a county such as Los Angeles with more than 3 million votes (enough to flip California in 2012) … We don’t know who programmed it. We don’t know what the code is doing. We don’t know what the chips and motherboard (made in China) are doing. We can’t look inside, nor at the logs. We can’t test it. (There are no standards. ) It has no paper tail, so there is no way to publicly check the results. It just tells us who the winner is. And we have to accept that. No matter what it says. Because that is paperless, electronic voting. . . They want to take that mission critical, secretive, vulnerable computer …
And put it in the middle of that? (Can you say “sitting duck”? )

Slide with smartphones

LA Would Be The Top Target

Ballot Initiative #15 -0108 (2016) • “ONLINE VOTING” • Requires Secretary of State to develop or contract with a third party for an online voting system by December 31, 2017. Appropriates $45 million from the Voting Modernization Bond Act of 2002 to finance the new system. Contains security and auditing requirements. Requires testing of system in local elections. Summary of estimate by Legislative Analyst and Director of Finance of fiscal impact on state and local government: Increased costs to state and local governments to administer elections. These costs include (1) one-time costs—possibly tens of millions of dollars —to develop new information technology systems and (2) ongoing costs— possibly millions of dollars annually—to administer elections. (15 -0108. ) • Apparently not well funded. Not on the ballot, yet.

Ballot Initiatives #15 -0117 & #15 -0118 • “Election Data Security & Military Ballot Access Act” http: //www. oag. ca. gov/initiatives/active-measures • Submitted by Olson Hagel & Fishburn, LLP. A very expensive Sacramento law firm. • For 43 pages, this is about the “secure electronic submission of vote by mail ballots”. • Already, this is a dubious idea…

What They Really Want • (Page 44) Section 19205 of the Elections Code is hereby repealed. (a) No part of the voting system shall be connected to the Internet at any time. • With no qualifications. No matter what happens in the rest of the initiative, we must expose our elections to the dangers of the Internet. • Deceptively, it’s not about “vote by mail”, it’s about “vote by Internet”.

Phone Networks • Section 19205(b) of the Elections Code is hereby repealed. (b) No part of the voting system shall electronically receive or transmit election data through an exterior communication network, including the public telephone system, if the communication originates from or terminates at a polling place, satellite location, or counting center. • This enables voting by smartphone and modems.

Wireless • Section 19205(c) of the Elections Code is hereby repealed. (c) No part of the voting system shall receive or transmit wireless communications or wireless data transfers. • Wireless is a 2 -way connection into and out of a computer. If you give people all day to hack into an mission critical election system, somebody will … • From a friend, January, 2016:

Common Sense • If they have penetrated the White House, CIA, FBI, Interpol, Pentagon, NATO, State Department, Bitcoin, Google, Adobe, E-Bay, Symantec, Yahoo!, Juniper Networks, Nasdaq, Charles Schwab, Visa, Master. Card, JP Morgan, Bank of America, Wells Fargo, Northrop. Grumman, Washington DC Department of Elections, and centrifuges with no direct connection to the Internet …

How Do You Expect … • … dedicated but underfunded, understaffed, overworked county registrars with nowhere near the resources and security expertise of Google, Nasdaq, Visa, or the Pentagon … • … how do you expect them to protect our votes from multi-million dollar efforts to change the course of history - by the Chinese cyber-army, or a spy agency, or Putin’s mafia, or a very greedy bank?

Resolution (IV) • (organization) opposes any and all moves towards using the Internet for casting ballots until such time as a proposed system is proven to meet the requirements of the E 2 E-VIV report of June, 2015: https: //www. usvotefoundation. org/E 2 E-VIV • 10 page summary: http: //countedascast. org/internet-voting-risks/end-to-endverifiable-internet-voting/

E 2 E-V IV Requirements • be secure from hacking by well-funded nation states • ensure that the voter's computer/phone is protected against viruses and fake voting apps • be able to deal with large scale denial of service attacks • prevent insertion of extra ballots into the system • easily verifiable by the public • allow correction of problems when they occur • allow for large scale resolution of disputed votes • require public red-team (hack) testing

You Can Make A Difference! • Alameda County, ‘ 06, leads return to paper ballots • Elected Debra Bowen, 2006 – 2013 www. countedascast. com/california/toptobottomreview. php www. countedascast. org/thank-you-debra-bowen/ • AB 813 (Melendez/Courbat), 2013. Detailed precinct reports on the Internet. Introduced and passed by democracy advocates. • 2009, Germany rejects Internet voting. • 2005 -2015 … SF moves towards open source. • We blocked IV bills 4 times. • We will stop the IV ballot initiatives.

How? • Do your homework! Know not just what, but why. Learn the rules of government. • Teamwork. Regular meetings. Support others. • Build networks & allies, including everybody. • Develop relationships with key players. • Be strategic. Can’t do it all. Pick your fights. • Polite perseverance. • Create and take advantage of dumb luck.

Laugh! Mimi wrote: “Dear God, will this never end? ”

Answer. . . “No Mimi, it will never end. - God”

Remember … Decisions are made by those who show up. – “President” Josiah Barlett
53effd3954e6701267d76b7cfc4036ba.ppt