73ea58933504e1da651f16ef17bc6421.ppt
- Количество слайдов: 51
 ELC 200 Day 22 ELECTRONIC COMMERCE From Vision to Fulfillment Third Edition Elias M. Awad © 2007 Prentice-Hall, Inc 6 -1
ELC 200 Day 22 ELECTRONIC COMMERCE From Vision to Fulfillment Third Edition Elias M. Awad © 2007 Prentice-Hall, Inc 6 -1
 Agenda • Assignment 8 Due • Assignment 9 Posted (optional) – Due April 28 • Quiz 4 on April 24 – Chapters 12 -16 – 25 M/C questions – Extra Credit on next quiz • First example of paper money (world) • First example of paper money in USA • First Digital Cash Company and its founder • Framework presentation on April 28 – E-mail your Power. Point to tonyg@maine. edu 30 min before class • Framework paper due on May 1 – Upload in Blackboard by 2 PM – No class • Finish discussion on Encryption • Discussion on Getting the Money © 2007 Prentice-Hall, Inc 6 -2
Agenda • Assignment 8 Due • Assignment 9 Posted (optional) – Due April 28 • Quiz 4 on April 24 – Chapters 12 -16 – 25 M/C questions – Extra Credit on next quiz • First example of paper money (world) • First example of paper money in USA • First Digital Cash Company and its founder • Framework presentation on April 28 – E-mail your Power. Point to tonyg@maine. edu 30 min before class • Framework paper due on May 1 – Upload in Blackboard by 2 PM – No class • Finish discussion on Encryption • Discussion on Getting the Money © 2007 Prentice-Hall, Inc 6 -2
 Encryption: A Matter of Trust ELECTRONIC COMMERCE From Vision to Fulfillment Third Edition Elias M. Awad
Encryption: A Matter of Trust ELECTRONIC COMMERCE From Vision to Fulfillment Third Edition Elias M. Awad
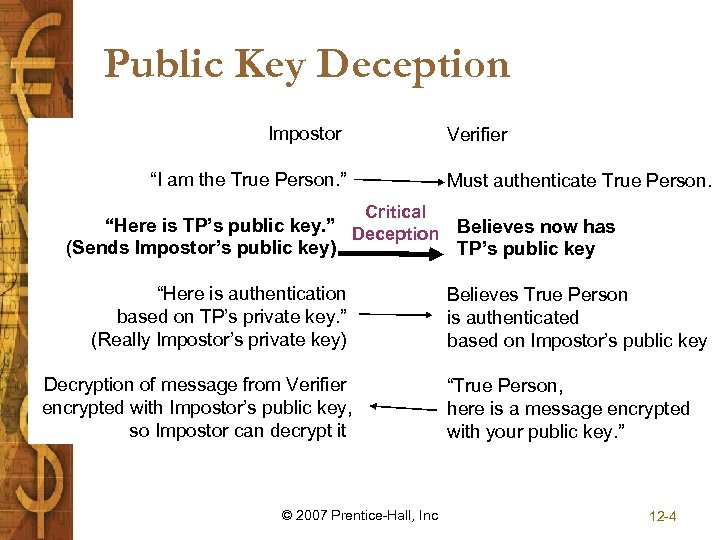 Public Key Deception Impostor Verifier “I am the True Person. ” Must authenticate True Person. Critical “Here is TP’s public key. ” Deception Believes now has (Sends Impostor’s public key) TP’s public key “Here is authentication based on TP’s private key. ” (Really Impostor’s private key) Decryption of message from Verifier encrypted with Impostor’s public key, so Impostor can decrypt it © 2007 Prentice-Hall, Inc Believes True Person is authenticated based on Impostor’s public key “True Person, here is a message encrypted with your public key. ” 12 -4
Public Key Deception Impostor Verifier “I am the True Person. ” Must authenticate True Person. Critical “Here is TP’s public key. ” Deception Believes now has (Sends Impostor’s public key) TP’s public key “Here is authentication based on TP’s private key. ” (Really Impostor’s private key) Decryption of message from Verifier encrypted with Impostor’s public key, so Impostor can decrypt it © 2007 Prentice-Hall, Inc Believes True Person is authenticated based on Impostor’s public key “True Person, here is a message encrypted with your public key. ” 12 -4
 Digital Certificates • Digital certificates are electronic documents that give the true party’s name and public key • Applicants claiming to be the true party have their authentication methods tested by this public key • If they are not the true party, they cannot use the true party’s private key and so will not be authenticated • Digital certificates follow the X. 509 Standard © 2007 Prentice-Hall, Inc 12 -5
Digital Certificates • Digital certificates are electronic documents that give the true party’s name and public key • Applicants claiming to be the true party have their authentication methods tested by this public key • If they are not the true party, they cannot use the true party’s private key and so will not be authenticated • Digital certificates follow the X. 509 Standard © 2007 Prentice-Hall, Inc 12 -5
 Digital Certificates • Digital certificates are the heart of secure online transactions • A digital certificate is a software program that can be installed in a browser • Your digital certificate identifies you to Web sites equipped to check it automatically • Digital certificate is an electronic document issued by a certificate authority to establish a merchant’s identity • Certificate authority (CA) is a trusted entity that issues and revokes public-key certificates and manages key-pairs © 2007 Prentice-Hall, Inc 12 -6
Digital Certificates • Digital certificates are the heart of secure online transactions • A digital certificate is a software program that can be installed in a browser • Your digital certificate identifies you to Web sites equipped to check it automatically • Digital certificate is an electronic document issued by a certificate authority to establish a merchant’s identity • Certificate authority (CA) is a trusted entity that issues and revokes public-key certificates and manages key-pairs © 2007 Prentice-Hall, Inc 12 -6
 Third-Party Services • Certificate authority verifies certificates intended for use by other distinct legal entities • Certificate policy is a set of rules that identifies how, when, and for what reasons certificates are used within the assigned organization • Directory service is a repository that distributes certificates as requested by message originators © 2007 Prentice-Hall, Inc 12 -7
Third-Party Services • Certificate authority verifies certificates intended for use by other distinct legal entities • Certificate policy is a set of rules that identifies how, when, and for what reasons certificates are used within the assigned organization • Directory service is a repository that distributes certificates as requested by message originators © 2007 Prentice-Hall, Inc 12 -7
 Four Classes of Digital Certificates • Class 1 certificates contain minimum checks on the user’s background • Class 2 certificates check for information like real name, Social Security number, and the date of birth • Class 3 certificates are the strongest type • Class 4 certificates are the most thorough © 2007 Prentice-Hall, Inc 12 -8
Four Classes of Digital Certificates • Class 1 certificates contain minimum checks on the user’s background • Class 2 certificates check for information like real name, Social Security number, and the date of birth • Class 3 certificates are the strongest type • Class 4 certificates are the most thorough © 2007 Prentice-Hall, Inc 12 -8
 Authentication and Trust • Digital Signature is a special signature for signing electronic correspondence, produced by encrypting the message digest with the sender’s private key • Authentication is verifying that a message or document, in fact, comes from the claimed sender • Hash function is a formula that converts a message of a given length into a string of digits called a message digest • Cryptographic hash functions are generally used to construct the message digest © 2007 Prentice-Hall, Inc 12 -9
Authentication and Trust • Digital Signature is a special signature for signing electronic correspondence, produced by encrypting the message digest with the sender’s private key • Authentication is verifying that a message or document, in fact, comes from the claimed sender • Hash function is a formula that converts a message of a given length into a string of digits called a message digest • Cryptographic hash functions are generally used to construct the message digest © 2007 Prentice-Hall, Inc 12 -9
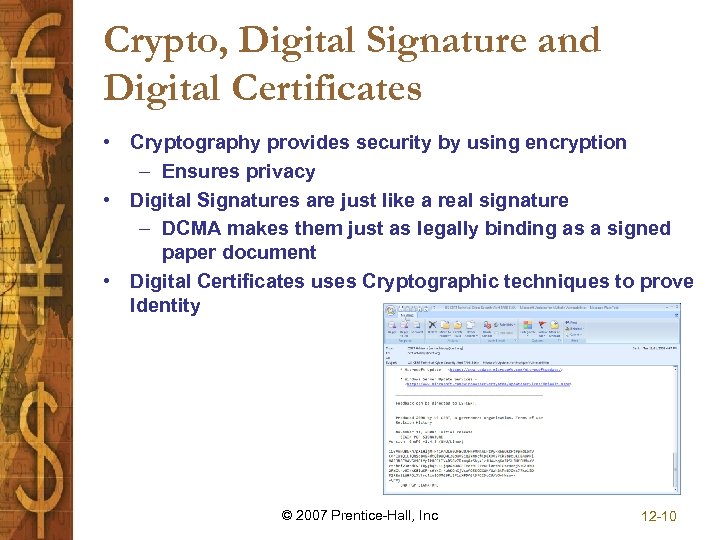 Crypto, Digital Signature and Digital Certificates • Cryptography provides security by using encryption – Ensures privacy • Digital Signatures are just like a real signature – DCMA makes them just as legally binding as a signed paper document • Digital Certificates uses Cryptographic techniques to prove Identity © 2007 Prentice-Hall, Inc 12 -10
Crypto, Digital Signature and Digital Certificates • Cryptography provides security by using encryption – Ensures privacy • Digital Signatures are just like a real signature – DCMA makes them just as legally binding as a signed paper document • Digital Certificates uses Cryptographic techniques to prove Identity © 2007 Prentice-Hall, Inc 12 -10
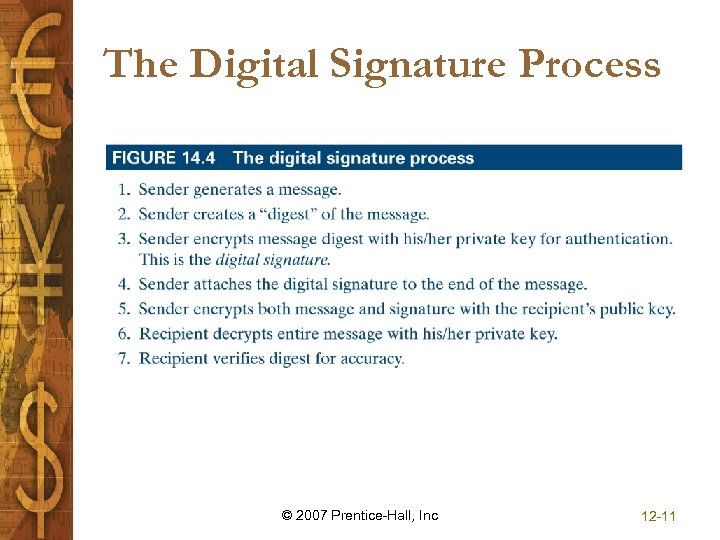 The Digital Signature Process © 2007 Prentice-Hall, Inc 12 -11
The Digital Signature Process © 2007 Prentice-Hall, Inc 12 -11
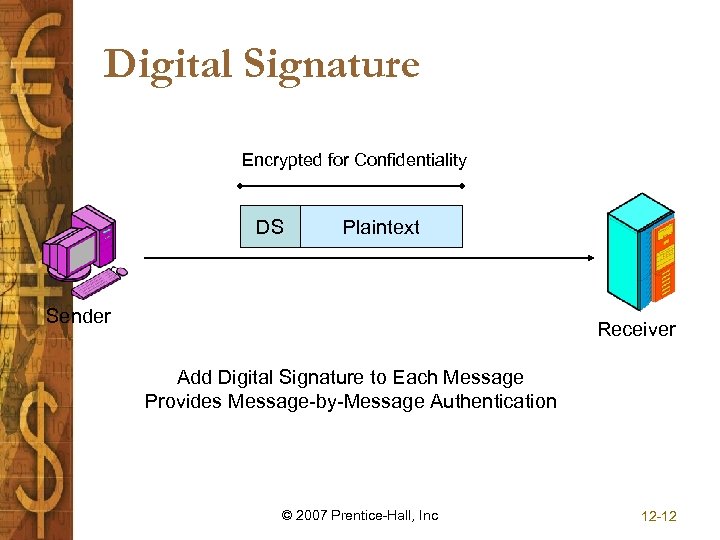 Digital Signature Encrypted for Confidentiality DS Plaintext Sender Receiver Add Digital Signature to Each Message Provides Message-by-Message Authentication © 2007 Prentice-Hall, Inc 12 -12
Digital Signature Encrypted for Confidentiality DS Plaintext Sender Receiver Add Digital Signature to Each Message Provides Message-by-Message Authentication © 2007 Prentice-Hall, Inc 12 -12
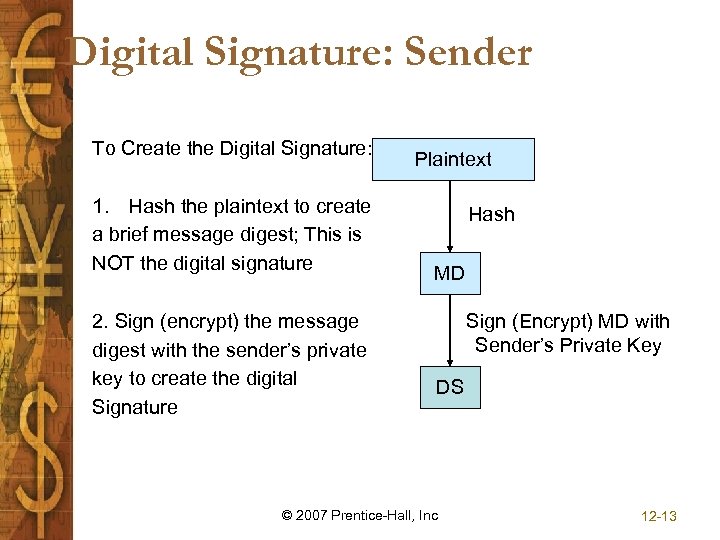 Digital Signature: Sender To Create the Digital Signature: 1. Hash the plaintext to create a brief message digest; This is NOT the digital signature 2. Sign (encrypt) the message digest with the sender’s private key to create the digital Signature Plaintext Hash MD Sign (Encrypt) MD with Sender’s Private Key DS © 2007 Prentice-Hall, Inc 12 -13
Digital Signature: Sender To Create the Digital Signature: 1. Hash the plaintext to create a brief message digest; This is NOT the digital signature 2. Sign (encrypt) the message digest with the sender’s private key to create the digital Signature Plaintext Hash MD Sign (Encrypt) MD with Sender’s Private Key DS © 2007 Prentice-Hall, Inc 12 -13
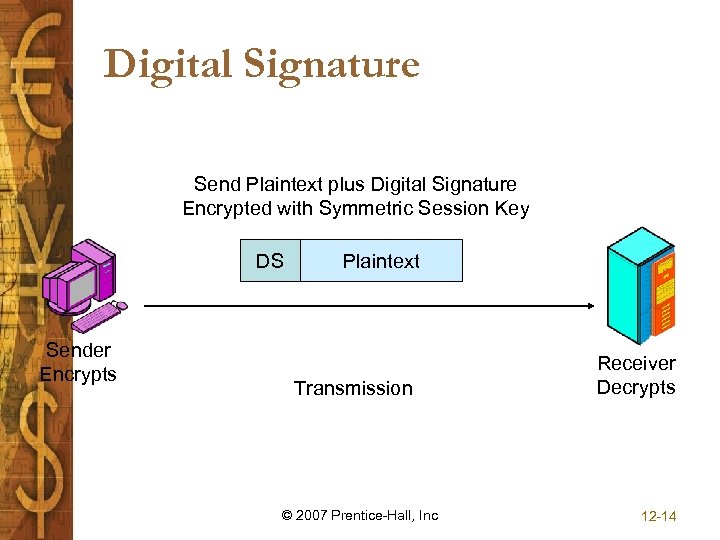 Digital Signature Send Plaintext plus Digital Signature Encrypted with Symmetric Session Key DS Sender Encrypts Plaintext Transmission © 2007 Prentice-Hall, Inc Receiver Decrypts 12 -14
Digital Signature Send Plaintext plus Digital Signature Encrypted with Symmetric Session Key DS Sender Encrypts Plaintext Transmission © 2007 Prentice-Hall, Inc Receiver Decrypts 12 -14
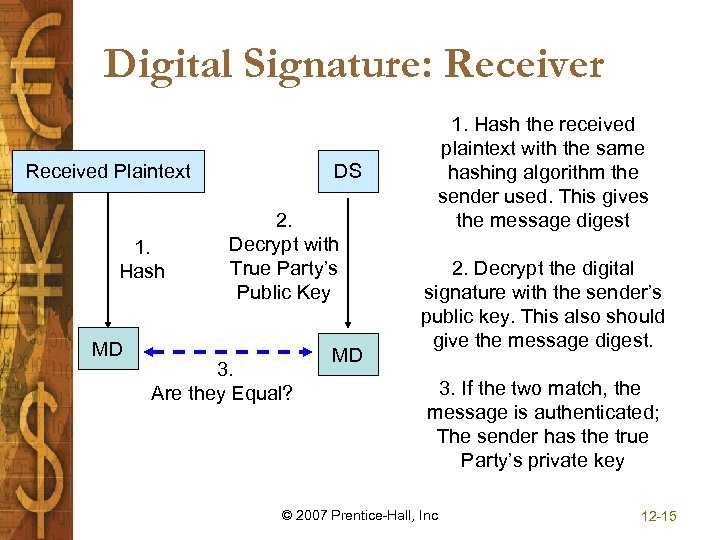 Digital Signature: Receiver Received Plaintext 1. Hash MD DS 2. Decrypt with True Party’s Public Key 3. Are they Equal? MD 1. Hash the received plaintext with the same hashing algorithm the sender used. This gives the message digest 2. Decrypt the digital signature with the sender’s public key. This also should give the message digest. 3. If the two match, the message is authenticated; The sender has the true Party’s private key © 2007 Prentice-Hall, Inc 12 -15
Digital Signature: Receiver Received Plaintext 1. Hash MD DS 2. Decrypt with True Party’s Public Key 3. Are they Equal? MD 1. Hash the received plaintext with the same hashing algorithm the sender used. This gives the message digest 2. Decrypt the digital signature with the sender’s public key. This also should give the message digest. 3. If the two match, the message is authenticated; The sender has the true Party’s private key © 2007 Prentice-Hall, Inc 12 -15
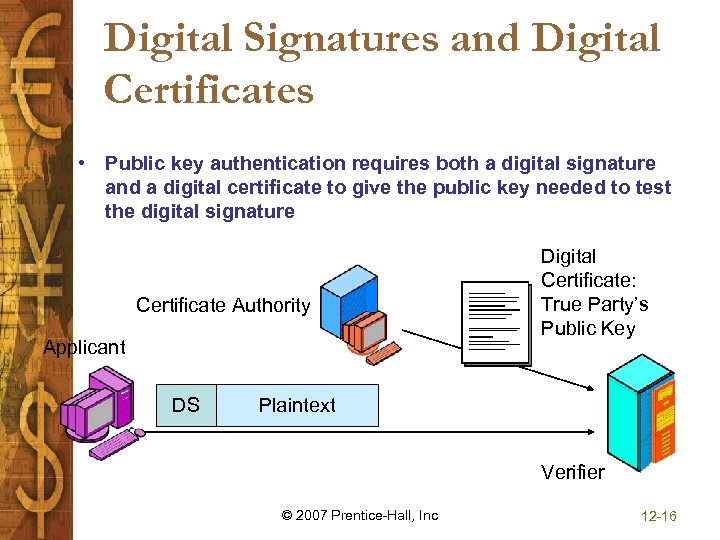 Digital Signatures and Digital Certificates • Public key authentication requires both a digital signature and a digital certificate to give the public key needed to test the digital signature Certificate Authority Applicant DS Digital Certificate: True Party’s Public Key Plaintext Verifier © 2007 Prentice-Hall, Inc 12 -16
Digital Signatures and Digital Certificates • Public key authentication requires both a digital signature and a digital certificate to give the public key needed to test the digital signature Certificate Authority Applicant DS Digital Certificate: True Party’s Public Key Plaintext Verifier © 2007 Prentice-Hall, Inc 12 -16
 Managing Cryptographic Keys • Key management is the process of making keys known to the systems that need them and making sure keys are protected against disclosure or substitution • Key Life Cycle – Key generation and registration – Key distribution – Key backup and recovery • Key escrow: location where keys held in trust by a third party reside – http: //pgp. mit. edu/ • Notary service: company that provides encryptionoriented services including key escrow, key recovery, time stamping, trusted intermediary, and archiving – Key revocation and destruction © 2007 Prentice-Hall, Inc 12 -17
Managing Cryptographic Keys • Key management is the process of making keys known to the systems that need them and making sure keys are protected against disclosure or substitution • Key Life Cycle – Key generation and registration – Key distribution – Key backup and recovery • Key escrow: location where keys held in trust by a third party reside – http: //pgp. mit. edu/ • Notary service: company that provides encryptionoriented services including key escrow, key recovery, time stamping, trusted intermediary, and archiving – Key revocation and destruction © 2007 Prentice-Hall, Inc 12 -17
 Internet Security Protocols • Two key protocols for secure World Wide Web transactions are: – Secure Socket Layer (SSL) is a protocol for secure Web transactions, secures data packets at the network layer – Secure HTTP (S-HTTP) is a protocol that secures Web transactions and nothing else • Secure Electronic Transaction (SET) is a protocol used for handling funds transfers from credit card issuers to a merchant’s bank account – A digital certificate customers can request from their issuing bank by filling out a form on the bank’s Web site – A digital wallet is an online shopping device that seals personal information in a free plug-in that can be invoked when making a purchase © 2007 Prentice-Hall, Inc 12 -18
Internet Security Protocols • Two key protocols for secure World Wide Web transactions are: – Secure Socket Layer (SSL) is a protocol for secure Web transactions, secures data packets at the network layer – Secure HTTP (S-HTTP) is a protocol that secures Web transactions and nothing else • Secure Electronic Transaction (SET) is a protocol used for handling funds transfers from credit card issuers to a merchant’s bank account – A digital certificate customers can request from their issuing bank by filling out a form on the bank’s Web site – A digital wallet is an online shopping device that seals personal information in a free plug-in that can be invoked when making a purchase © 2007 Prentice-Hall, Inc 12 -18
 Secure E-mail • Pretty Good Privacy (PGP) is a protocol that encrypts the data with a one-time algorithm and then encrypts the key to the algorithm using public-key cryptography – http: //www. pgp. com/ – http: //www. gnupg. org/ • S/MIME (Multipurpose Internet Mail Extension) is a powerful protocol that provides security for different data types and attachments to e-mails • Message Security Protocol (MSP) is a protocol that secures e-mail attachments across multiple platforms © 2007 Prentice-Hall, Inc 12 -19
Secure E-mail • Pretty Good Privacy (PGP) is a protocol that encrypts the data with a one-time algorithm and then encrypts the key to the algorithm using public-key cryptography – http: //www. pgp. com/ – http: //www. gnupg. org/ • S/MIME (Multipurpose Internet Mail Extension) is a powerful protocol that provides security for different data types and attachments to e-mails • Message Security Protocol (MSP) is a protocol that secures e-mail attachments across multiple platforms © 2007 Prentice-Hall, Inc 12 -19
 Implications for E-Commerce • Developing high-powered and reliable encryption methods is a top priority for many organizations • Most encryption systems have prevention as the sole means of defense • Merchants face a number of choices when considering encryption methods • A major concern is the cost associated with different encryption methods • Government regulations present considerable problems for businesses © 2007 Prentice-Hall, Inc 12 -20
Implications for E-Commerce • Developing high-powered and reliable encryption methods is a top priority for many organizations • Most encryption systems have prevention as the sole means of defense • Merchants face a number of choices when considering encryption methods • A major concern is the cost associated with different encryption methods • Government regulations present considerable problems for businesses © 2007 Prentice-Hall, Inc 12 -20
 Chapter Summary • Encryption addresses message transmission security requirements • Encryption satisfies requirements for authentication, integrity, and nonrepudiation • There are two classes of key-based algorithms – Secret key – Public key • Cryptanalysis is the science of deciphering encrypted messages without knowing the right key © 2007 Prentice-Hall, Inc 12 -21
Chapter Summary • Encryption addresses message transmission security requirements • Encryption satisfies requirements for authentication, integrity, and nonrepudiation • There are two classes of key-based algorithms – Secret key – Public key • Cryptanalysis is the science of deciphering encrypted messages without knowing the right key © 2007 Prentice-Hall, Inc 12 -21
 Chapter Summary (Cont’d ) • One way to implement public-key authentication is to send a digital signature with each message • A digital certificate is an electronic document issued by a certificate authority (CA) to establish a merchant’s identity by verifying its name and public key • Security measures installed to minimize vulnerability to the exchange of information includes – SSL – SHTTP – SET – S/MIME © 2007 Prentice-Hall, Inc 12 -22
Chapter Summary (Cont’d ) • One way to implement public-key authentication is to send a digital signature with each message • A digital certificate is an electronic document issued by a certificate authority (CA) to establish a merchant’s identity by verifying its name and public key • Security measures installed to minimize vulnerability to the exchange of information includes – SSL – SHTTP – SET – S/MIME © 2007 Prentice-Hall, Inc 12 -22
 Getting the Money ELECTRONIC COMMERCE From Vision to Fulfillment Third Edition Elias M. Awad
Getting the Money ELECTRONIC COMMERCE From Vision to Fulfillment Third Edition Elias M. Awad
 The focus of this chapter is on several learning objectives • Real-world and electronic cash and their unique features and uses • The key requirements for Internet-based payments • The many ways people pay to purchase goods and services on the Internet • Business-to-business methods of payment • Paying for goods and services via the mobile phone • Issues and implications behind electronic money transactions and payments
The focus of this chapter is on several learning objectives • Real-world and electronic cash and their unique features and uses • The key requirements for Internet-based payments • The many ways people pay to purchase goods and services on the Internet • Business-to-business methods of payment • Paying for goods and services via the mobile phone • Issues and implications behind electronic money transactions and payments
 BRIEF HISTORY OF MONEY • Barter • Medium of Exchange – Tokens – Notational Money – Credit System
BRIEF HISTORY OF MONEY • Barter • Medium of Exchange – Tokens – Notational Money – Credit System
 Real-World Cash • Money – Medium of exchange to simplify transactions – Standard of value – Store of value to facilitate the concept of saving • Cash continues to be the most widely used form of payment – Convenience – Wide acceptance – Anonymity – No cost of use – No audit trail
Real-World Cash • Money – Medium of exchange to simplify transactions – Standard of value – Store of value to facilitate the concept of saving • Cash continues to be the most widely used form of payment – Convenience – Wide acceptance – Anonymity – No cost of use – No audit trail
 Electronic Money (E-Money) • E-money is an electronic medium for making payments – – Credit cards Smart cards Debit cards Electronic funds transfer • Identified e-money (digital cash) is a notational money system that generates an audit trail and can be traced • Anonymous e-money is a notational money system that cannot be traced • Types of e-money – – Identified and online (+I+L) Identified and off-line (+I-L) Anonymous and online (-I+L) Anonymous and off-line (-I-L)
Electronic Money (E-Money) • E-money is an electronic medium for making payments – – Credit cards Smart cards Debit cards Electronic funds transfer • Identified e-money (digital cash) is a notational money system that generates an audit trail and can be traced • Anonymous e-money is a notational money system that cannot be traced • Types of e-money – – Identified and online (+I+L) Identified and off-line (+I-L) Anonymous and online (-I+L) Anonymous and off-line (-I-L)
 US Cash • Largest US bill is $100 • $1, 000 weighs 20 pounds and is 643 cubic inches (8”X 6”X 13”) and would fit in a large briefcase • One ton of $100 dollars bill is 10 billion dollars • The US Federal Deficit is $11, 200, 320, 070, 871. 32 – http: //www. brillig. com/debt_clock/ – This is equal to 22 Million pounds of $100 dollar bills – It would require 2700 tractor trailers to hold all the cash it would require to pay off the federal debt (36 miles of trucks parked bumper to bumper!)
US Cash • Largest US bill is $100 • $1, 000 weighs 20 pounds and is 643 cubic inches (8”X 6”X 13”) and would fit in a large briefcase • One ton of $100 dollars bill is 10 billion dollars • The US Federal Deficit is $11, 200, 320, 070, 871. 32 – http: //www. brillig. com/debt_clock/ – This is equal to 22 Million pounds of $100 dollar bills – It would require 2700 tractor trailers to hold all the cash it would require to pay off the federal debt (36 miles of trucks parked bumper to bumper!)
 Properties Of Money • Online/offline represents risk – Online is on the spot validated transaction – An offline transactions is validated later • Identified and Online (+I+L) – Credit cards and debit cards • Identified and Offline (+I-L) – Checks, Money orders • Anonymous and Online (-I+L) – Cash payments • Anonymous and Offline (-I-L) – ATM deposit – Electronic cash (but not real cash)
Properties Of Money • Online/offline represents risk – Online is on the spot validated transaction – An offline transactions is validated later • Identified and Online (+I+L) – Credit cards and debit cards • Identified and Offline (+I-L) – Checks, Money orders • Anonymous and Online (-I+L) – Cash payments • Anonymous and Offline (-I-L) – ATM deposit – Electronic cash (but not real cash)
 ACID TEST • Atomicity – All or nothing • Consistency – All agree • Isolation – Doesn’t effect other transactions • Durability – Can go back to previous state (i. e. reversible)
ACID TEST • Atomicity – All or nothing • Consistency – All agree • Isolation – Doesn’t effect other transactions • Durability – Can go back to previous state (i. e. reversible)
 ICES TEST • Interoperability – Ability to move between system • Conservation – Temporal consistency and durability • Economy – Cost of use • Scalability – Multiple users
ICES TEST • Interoperability – Ability to move between system • Conservation – Temporal consistency and durability • Economy – Cost of use • Scalability – Multiple users
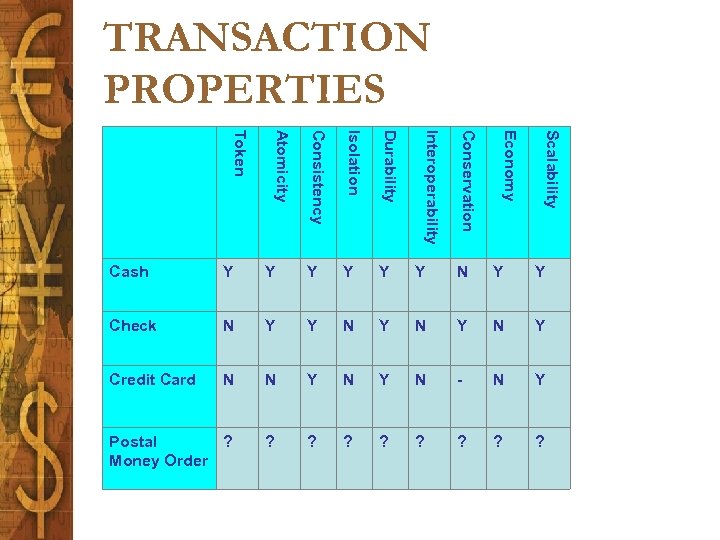 TRANSACTION PROPERTIES Scalability Economy Durability Conservation Isolation Interoperability Consistency Atomicity Token Cash Y Y Y N Y Y Check N Y Y N Y N Y Credit Card N N Y N - N Y Postal ? Money Order ? ?
TRANSACTION PROPERTIES Scalability Economy Durability Conservation Isolation Interoperability Consistency Atomicity Token Cash Y Y Y N Y Y Check N Y Y N Y N Y Credit Card N N Y N - N Y Postal ? Money Order ? ?
 Requirements for Internet-based Payments • Electronic payments are financial transactions made without the use of paper documents such as cash or checks • Internet-based Payment Systems Models – Electronic currency is the network equivalent of cash – Credit and debit cards are the electronic equivalent of checks • Properties important to an electronic payment system: – – Acceptability Ease of integration Customer base Ease of use and ease of access
Requirements for Internet-based Payments • Electronic payments are financial transactions made without the use of paper documents such as cash or checks • Internet-based Payment Systems Models – Electronic currency is the network equivalent of cash – Credit and debit cards are the electronic equivalent of checks • Properties important to an electronic payment system: – – Acceptability Ease of integration Customer base Ease of use and ease of access
 ELECTRONIC TRANSACTION SYSTEMS • Cyber. Cash – http: //www. cybercash. com/ – Bought by Verisign, then by Pay. Pal • Netbill – http: //www. netbill. com/ – No longer active • First Virtual – No longer in internet payment systems • Paypal – www. paypal. com
ELECTRONIC TRANSACTION SYSTEMS • Cyber. Cash – http: //www. cybercash. com/ – Bought by Verisign, then by Pay. Pal • Netbill – http: //www. netbill. com/ – No longer active • First Virtual – No longer in internet payment systems • Paypal – www. paypal. com
 Active payment systems (2008) • • • http: //www. paysimple. com/ http: //www. mypaynet. com http: //checkout. google. com/sell? promo=sha 2 http: //www. authorize. net/ http: //www. worldpay. com/ https: //www. paypal. com/ http: //www. westernunion. com https: //www. ikobo. com/ https: //www. xoom. com/
Active payment systems (2008) • • • http: //www. paysimple. com/ http: //www. mypaynet. com http: //checkout. google. com/sell? promo=sha 2 http: //www. authorize. net/ http: //www. worldpay. com/ https: //www. paypal. com/ http: //www. westernunion. com https: //www. ikobo. com/ https: //www. xoom. com/
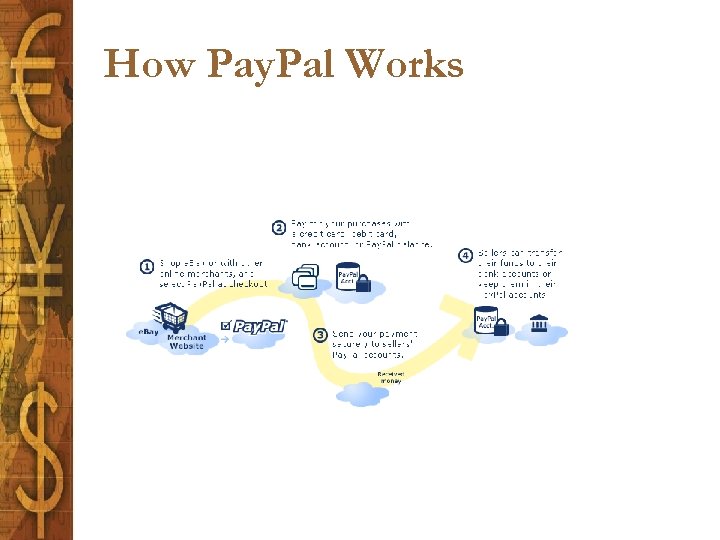 How Pay. Pal Works
How Pay. Pal Works
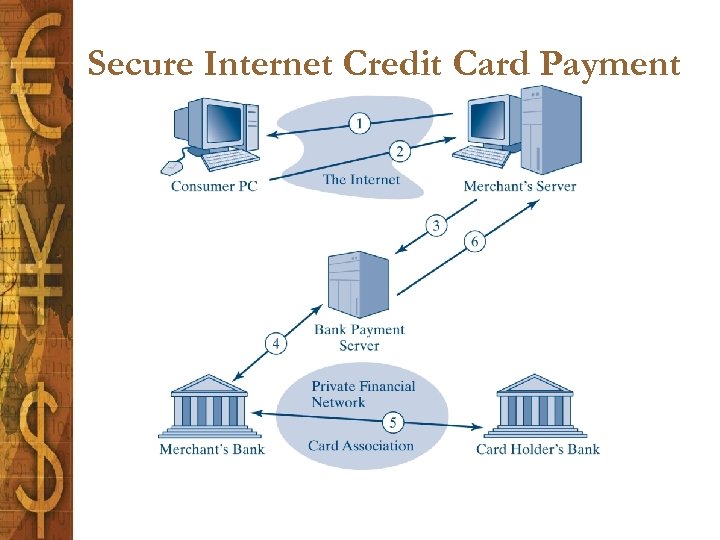 Secure Internet Credit Card Payment
Secure Internet Credit Card Payment
 How Would You Like to Pay? • Types of electronic payment media – Trusted third-party type – Notational fund transfer-related type – Digital cash or electronic money
How Would You Like to Pay? • Types of electronic payment media – Trusted third-party type – Notational fund transfer-related type – Digital cash or electronic money
 Paying with Credit Cards • A merchant must accept credit cards • You must first open a merchant account with your bank • Charges the merchant pays for online transactions are equivalent to the charges for phoning in the transaction • The Web merchant needs some form of secure and encrypted line, usually (SSL) • The merchant needs a shopping cart program that allows users to collect their purchases
Paying with Credit Cards • A merchant must accept credit cards • You must first open a merchant account with your bank • Charges the merchant pays for online transactions are equivalent to the charges for phoning in the transaction • The Web merchant needs some form of secure and encrypted line, usually (SSL) • The merchant needs a shopping cart program that allows users to collect their purchases
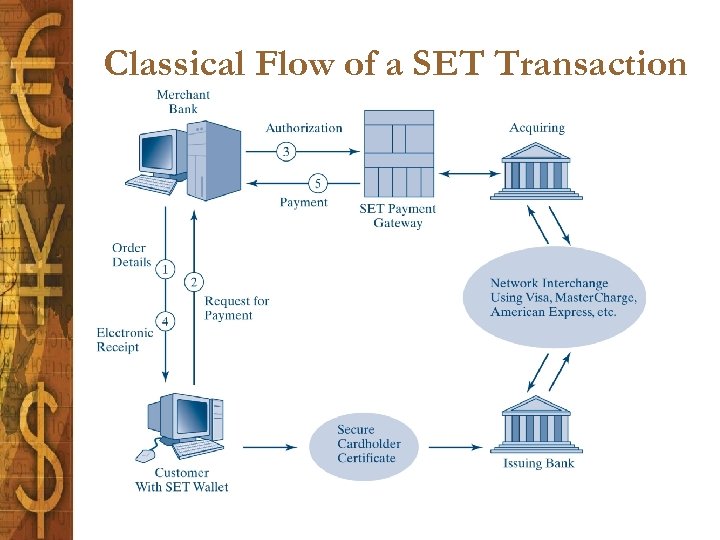 Classical Flow of a SET Transaction
Classical Flow of a SET Transaction
 Debit Cards • Look exactly like credits cards, except they directly tap your checking account every time you make a purchase or a withdrawal • Using a debit card frees you from having to carry cash or a checkbook • Debit cards are more readily accepted by merchants than are checks • It is generally easier to get a debit card than a credit card • Use of PIN creates identified & online transaction – Hard to dispute!
Debit Cards • Look exactly like credits cards, except they directly tap your checking account every time you make a purchase or a withdrawal • Using a debit card frees you from having to carry cash or a checkbook • Debit cards are more readily accepted by merchants than are checks • It is generally easier to get a debit card than a credit card • Use of PIN creates identified & online transaction – Hard to dispute!
 Debit Cards (Cont’d ) • Returned debit card purchases are treated just like returns for items purchased by cash or check • The debit card is a quick pay now process • Using a debit card may mean less protection for items that are never delivered, for defective items, or for items that were mis-represented • Cardholders might overspend their limit before anyone finds out
Debit Cards (Cont’d ) • Returned debit card purchases are treated just like returns for items purchased by cash or check • The debit card is a quick pay now process • Using a debit card may mean less protection for items that are never delivered, for defective items, or for items that were mis-represented • Cardholders might overspend their limit before anyone finds out
 Smart Cards • Uses for Smart Cards – Provides users with the ability to make a purchase – Holds cash, ID information, and a key to a house or an office – Three categories of applications • Authenticate an individual’s claim of personal identification • Authorization for things like drug prescription fulfillment and voting purposes • Transaction processing – Provides encryption and decryption of messages to ensure security, integrity, and confidentiality – Acts as a carrier of value
Smart Cards • Uses for Smart Cards – Provides users with the ability to make a purchase – Holds cash, ID information, and a key to a house or an office – Three categories of applications • Authenticate an individual’s claim of personal identification • Authorization for things like drug prescription fulfillment and voting purposes • Transaction processing – Provides encryption and decryption of messages to ensure security, integrity, and confidentiality – Acts as a carrier of value
 Smart Card Applications • Government • Identification • Health care • Loyalty • Telecommunications • Transportation • Financial
Smart Card Applications • Government • Identification • Health care • Loyalty • Telecommunications • Transportation • Financial
 Digi. Cash, E-Cash and E-Wallet • Digital cash leaves no audit trail • From a regulatory point of view, digital cash is not any different from any other kind of electronic financial payment medium • Pay. Pal. combines e-mail and the credit card network to send real cash • E-wallet is an electronic payment system that operates like a carrier of e-cash and information in the same way a real-world wallet functions • Amazon. com’s 1 -Click system, http: //www. Amazon. com
Digi. Cash, E-Cash and E-Wallet • Digital cash leaves no audit trail • From a regulatory point of view, digital cash is not any different from any other kind of electronic financial payment medium • Pay. Pal. combines e-mail and the credit card network to send real cash • E-wallet is an electronic payment system that operates like a carrier of e-cash and information in the same way a real-world wallet functions • Amazon. com’s 1 -Click system, http: //www. Amazon. com
 Electronic Funds Transfer and Automated Clearinghouse • Electronic fund transfer (EFT) is a computer-based system that facilitates the transfer of money or the processing of financial transactions between two financial institutions • Automated Clearinghouse (ACH) is where bank transactions, involving more than one institution, are routed to debit and credit the correct accounts
Electronic Funds Transfer and Automated Clearinghouse • Electronic fund transfer (EFT) is a computer-based system that facilitates the transfer of money or the processing of financial transactions between two financial institutions • Automated Clearinghouse (ACH) is where bank transactions, involving more than one institution, are routed to debit and credit the correct accounts
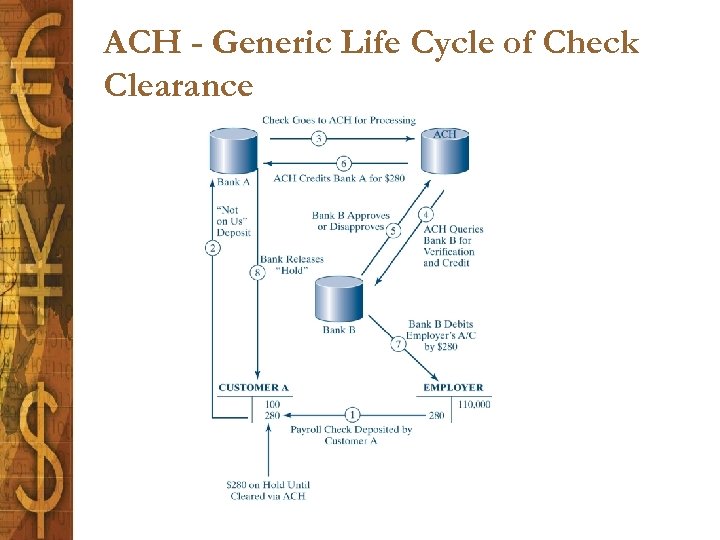 ACH - Generic Life Cycle of Check Clearance
ACH - Generic Life Cycle of Check Clearance
 Check Numbers http: //en. wikipedia. org/wiki/Demand_draft http: //www. qchex. com/
Check Numbers http: //en. wikipedia. org/wiki/Demand_draft http: //www. qchex. com/
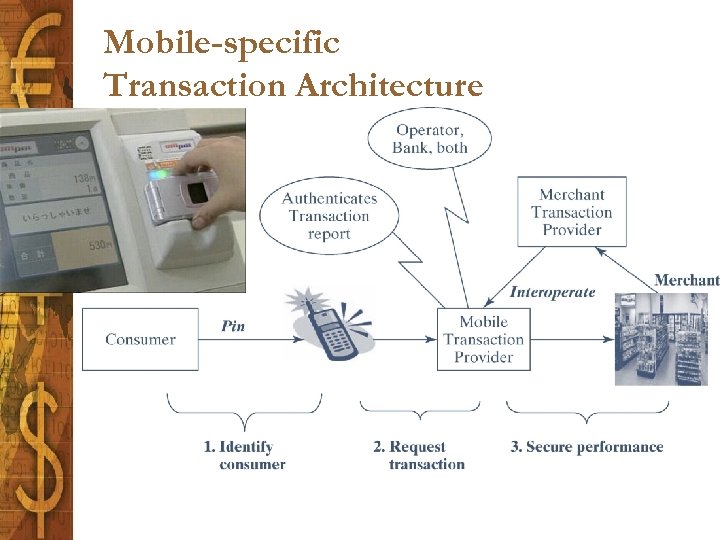 Mobile-specific Transaction Architecture
Mobile-specific Transaction Architecture
 General Guide to E-Payment • Use a secure Web browser • Read the Web site’s privacy policy carefully • Determine the merchant’s refund policies in advance of the final purchase • Investigate the trustworthiness of the merchant before you initiate a purchase • Keep a record of all online transactions and check e-mail and other contacts regularly • Review your credit card statements line-by-line to ensure authenticity
General Guide to E-Payment • Use a secure Web browser • Read the Web site’s privacy policy carefully • Determine the merchant’s refund policies in advance of the final purchase • Investigate the trustworthiness of the merchant before you initiate a purchase • Keep a record of all online transactions and check e-mail and other contacts regularly • Review your credit card statements line-by-line to ensure authenticity
 Issues Regarding Electronic Payment Methods and Methodologies • Consumer needs • Corporate processes • Corporate strategy • Regulation of competition • Economic and social processes
Issues Regarding Electronic Payment Methods and Methodologies • Consumer needs • Corporate processes • Corporate strategy • Regulation of competition • Economic and social processes


