7e57e39ca9f8fb8f344a823528553d54.ppt
- Количество слайдов: 25
 ELC 200 Day 22 ELECTRONIC COMMERCE From Vision to Fulfillment Third Edition Elias M. Awad © 2007 Prentice-Hall, Inc 12 -1
ELC 200 Day 22 ELECTRONIC COMMERCE From Vision to Fulfillment Third Edition Elias M. Awad © 2007 Prentice-Hall, Inc 12 -1
 Agenda • Assignment 8 posted – Due Dec 1 • ECommerce Initiative Frameworks – Guidelines – Due Dec 19 @ 10 AM – 25 days away • Today we will begin discussion on Encryption: A Matter of Trust © 2007 Prentice-Hall, Inc 6 -2
Agenda • Assignment 8 posted – Due Dec 1 • ECommerce Initiative Frameworks – Guidelines – Due Dec 19 @ 10 AM – 25 days away • Today we will begin discussion on Encryption: A Matter of Trust © 2007 Prentice-Hall, Inc 6 -2
 Schedule for rest of semester • Today – Chap 14 • Dec 1 – No class – Assignment 8 due • Dec 4 – Chap 15 – Assignment 9 posted • Dec 8 – Chap 15 • Dec 11 – Quiz 4 – Assignment 9 due • Friday, Dec 19 @ 10 AM – Presentation of e. Commerce Initiative – 5 -10 min per students © 2007 Prentice-Hall, Inc 6 -3
Schedule for rest of semester • Today – Chap 14 • Dec 1 – No class – Assignment 8 due • Dec 4 – Chap 15 – Assignment 9 posted • Dec 8 – Chap 15 • Dec 11 – Quiz 4 – Assignment 9 due • Friday, Dec 19 @ 10 AM – Presentation of e. Commerce Initiative – 5 -10 min per students © 2007 Prentice-Hall, Inc 6 -3
 Assignment 8 Security for Your e. Business 1. Identify and quantify in monetary terms the critical assets in your company that may be at risk form the dangers listed in Chapter 13. (you should identify at a bare minimum 5 assets) 2. For each of the critical assets at risk, what steps could you take to protect your company from the risks? 3. For of the steps and possible solutions you identify in question 2, find out how much it would cost to implement the steps or solution. 4. Is the cost of fixing the problems make sense in relation to potential monetary loss of not fixing the security problem? 5. Could you purchase anti-hacker insurance for your company? If so, from where and how much would it cost? © 2007 Prentice-Hall, Inc 12 -4
Assignment 8 Security for Your e. Business 1. Identify and quantify in monetary terms the critical assets in your company that may be at risk form the dangers listed in Chapter 13. (you should identify at a bare minimum 5 assets) 2. For each of the critical assets at risk, what steps could you take to protect your company from the risks? 3. For of the steps and possible solutions you identify in question 2, find out how much it would cost to implement the steps or solution. 4. Is the cost of fixing the problems make sense in relation to potential monetary loss of not fixing the security problem? 5. Could you purchase anti-hacker insurance for your company? If so, from where and how much would it cost? © 2007 Prentice-Hall, Inc 12 -4
 Encryption: A Matter of Trust ELECTRONIC COMMERCE From Vision to Fulfillment Third Edition Elias M. Awad © 2007 Prentice-Hall, Inc 12 -5
Encryption: A Matter of Trust ELECTRONIC COMMERCE From Vision to Fulfillment Third Edition Elias M. Awad © 2007 Prentice-Hall, Inc 12 -5
 Major Attacks on Cryptosystems • Chosen-plaintext attack • Known-plaintext attack • Ciphertext-only attack • Third-party attack – Man in the middle © 2007 Prentice-Hall, Inc 12 -6
Major Attacks on Cryptosystems • Chosen-plaintext attack • Known-plaintext attack • Ciphertext-only attack • Third-party attack – Man in the middle © 2007 Prentice-Hall, Inc 12 -6
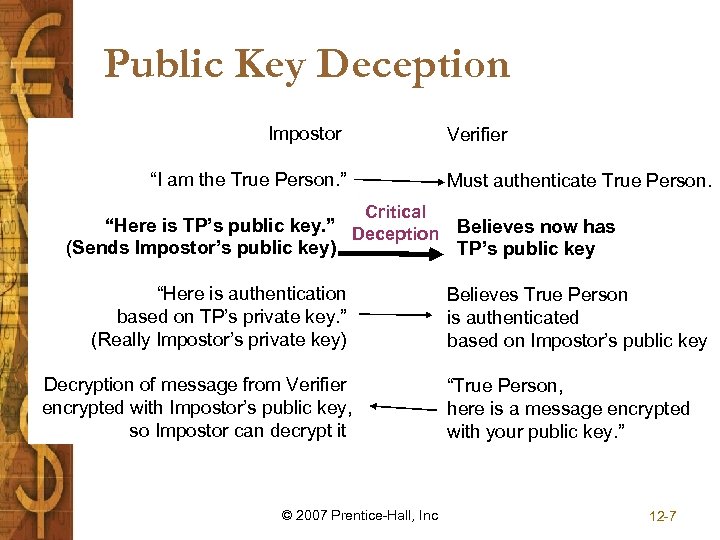 Public Key Deception Impostor Verifier “I am the True Person. ” Must authenticate True Person. Critical “Here is TP’s public key. ” Deception Believes now has (Sends Impostor’s public key) TP’s public key “Here is authentication based on TP’s private key. ” (Really Impostor’s private key) Decryption of message from Verifier encrypted with Impostor’s public key, so Impostor can decrypt it © 2007 Prentice-Hall, Inc Believes True Person is authenticated based on Impostor’s public key “True Person, here is a message encrypted with your public key. ” 12 -7
Public Key Deception Impostor Verifier “I am the True Person. ” Must authenticate True Person. Critical “Here is TP’s public key. ” Deception Believes now has (Sends Impostor’s public key) TP’s public key “Here is authentication based on TP’s private key. ” (Really Impostor’s private key) Decryption of message from Verifier encrypted with Impostor’s public key, so Impostor can decrypt it © 2007 Prentice-Hall, Inc Believes True Person is authenticated based on Impostor’s public key “True Person, here is a message encrypted with your public key. ” 12 -7
 Digital Certificates • Digital certificates are electronic documents that give the true party’s name and public key • Applicants claiming to be the true party have their authentication methods tested by this public key • If they are not the true party, they cannot use the true party’s private key and so will not be authenticated • Digital certificates follow the X. 509 Standard © 2007 Prentice-Hall, Inc 12 -8
Digital Certificates • Digital certificates are electronic documents that give the true party’s name and public key • Applicants claiming to be the true party have their authentication methods tested by this public key • If they are not the true party, they cannot use the true party’s private key and so will not be authenticated • Digital certificates follow the X. 509 Standard © 2007 Prentice-Hall, Inc 12 -8
 Digital Certificates • Digital certificates are the heart of secure online transactions • A digital certificate is a software program that can be installed in a browser • Your digital certificate identifies you to Web sites equipped to check it automatically • Digital certificate is an electronic document issued by a certificate authority to establish a merchant’s identity • Certificate authority (CA) is a trusted entity that issues and revokes public-key certificates and manages key-pairs © 2007 Prentice-Hall, Inc 12 -9
Digital Certificates • Digital certificates are the heart of secure online transactions • A digital certificate is a software program that can be installed in a browser • Your digital certificate identifies you to Web sites equipped to check it automatically • Digital certificate is an electronic document issued by a certificate authority to establish a merchant’s identity • Certificate authority (CA) is a trusted entity that issues and revokes public-key certificates and manages key-pairs © 2007 Prentice-Hall, Inc 12 -9
 Third-Party Services • Certificate authority verifies certificates intended for use by other distinct legal entities • Certificate policy is a set of rules that identifies how, when, and for what reasons certificates are used within the assigned organization • Directory service is a repository that distributes certificates as requested by message originators © 2007 Prentice-Hall, Inc 12 -10
Third-Party Services • Certificate authority verifies certificates intended for use by other distinct legal entities • Certificate policy is a set of rules that identifies how, when, and for what reasons certificates are used within the assigned organization • Directory service is a repository that distributes certificates as requested by message originators © 2007 Prentice-Hall, Inc 12 -10
 Four Classes of Digital Certificates • Class 1 certificates contain minimum checks on the user’s background • Class 2 certificates check for information like real name, Social Security number, and the date of birth • Class 3 certificates are the strongest type • Class 4 certificates are the most thorough © 2007 Prentice-Hall, Inc 12 -11
Four Classes of Digital Certificates • Class 1 certificates contain minimum checks on the user’s background • Class 2 certificates check for information like real name, Social Security number, and the date of birth • Class 3 certificates are the strongest type • Class 4 certificates are the most thorough © 2007 Prentice-Hall, Inc 12 -11
 Authentication and Trust • Digital Signature is a special signature for signing electronic correspondence, produced by encrypting the message digest with the sender’s private key • Authentication is verifying that a message or document, in fact, comes from the claimed sender • Hash function is a formula that converts a message of a given length into a string of digits called a message digest • Cryptographic hash functions are generally used to construct the message digest © 2007 Prentice-Hall, Inc 12 -12
Authentication and Trust • Digital Signature is a special signature for signing electronic correspondence, produced by encrypting the message digest with the sender’s private key • Authentication is verifying that a message or document, in fact, comes from the claimed sender • Hash function is a formula that converts a message of a given length into a string of digits called a message digest • Cryptographic hash functions are generally used to construct the message digest © 2007 Prentice-Hall, Inc 12 -12
 Crypto, Digital Signature and Digital Certificates • Cryptography provides security by using encryption – Ensures privacy • Digital Signatures are just like a real signature – DCMA makes them just as legally binding as a signed paper document • Digital Certificates uses Cryptographic techniques to prove Identity © 2007 Prentice-Hall, Inc 12 -13
Crypto, Digital Signature and Digital Certificates • Cryptography provides security by using encryption – Ensures privacy • Digital Signatures are just like a real signature – DCMA makes them just as legally binding as a signed paper document • Digital Certificates uses Cryptographic techniques to prove Identity © 2007 Prentice-Hall, Inc 12 -13
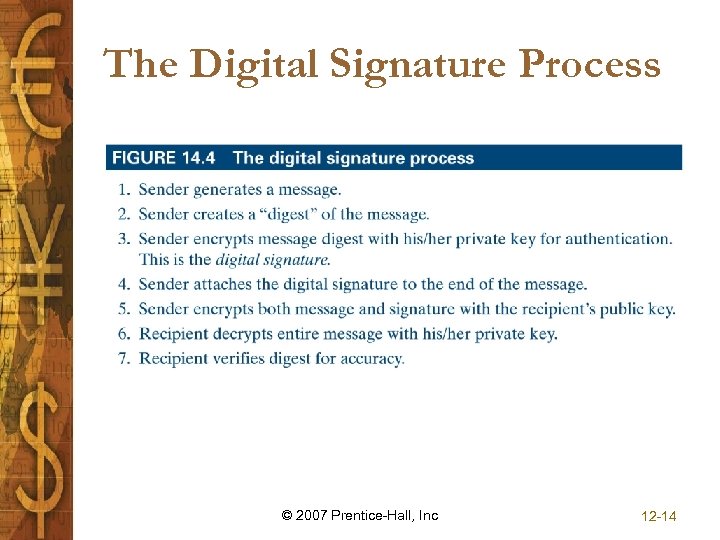 The Digital Signature Process © 2007 Prentice-Hall, Inc 12 -14
The Digital Signature Process © 2007 Prentice-Hall, Inc 12 -14
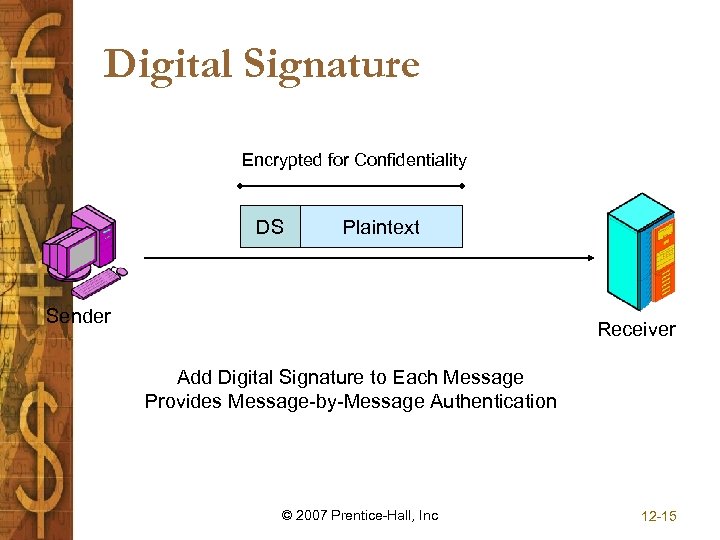 Digital Signature Encrypted for Confidentiality DS Plaintext Sender Receiver Add Digital Signature to Each Message Provides Message-by-Message Authentication © 2007 Prentice-Hall, Inc 12 -15
Digital Signature Encrypted for Confidentiality DS Plaintext Sender Receiver Add Digital Signature to Each Message Provides Message-by-Message Authentication © 2007 Prentice-Hall, Inc 12 -15
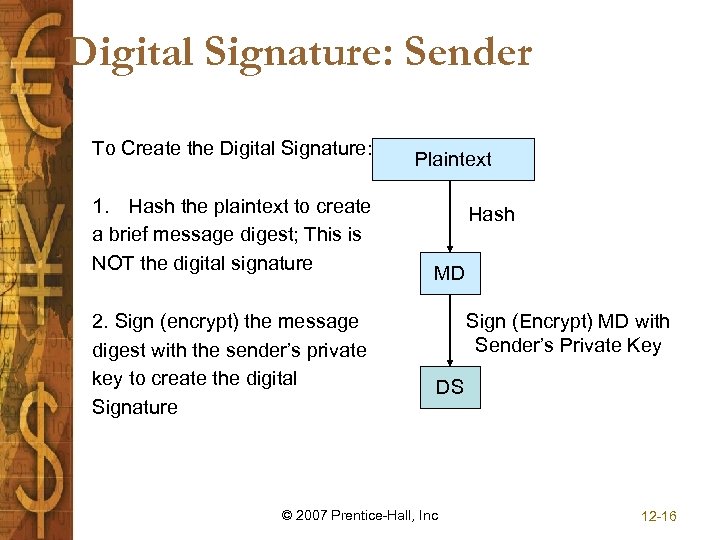 Digital Signature: Sender To Create the Digital Signature: 1. Hash the plaintext to create a brief message digest; This is NOT the digital signature 2. Sign (encrypt) the message digest with the sender’s private key to create the digital Signature Plaintext Hash MD Sign (Encrypt) MD with Sender’s Private Key DS © 2007 Prentice-Hall, Inc 12 -16
Digital Signature: Sender To Create the Digital Signature: 1. Hash the plaintext to create a brief message digest; This is NOT the digital signature 2. Sign (encrypt) the message digest with the sender’s private key to create the digital Signature Plaintext Hash MD Sign (Encrypt) MD with Sender’s Private Key DS © 2007 Prentice-Hall, Inc 12 -16
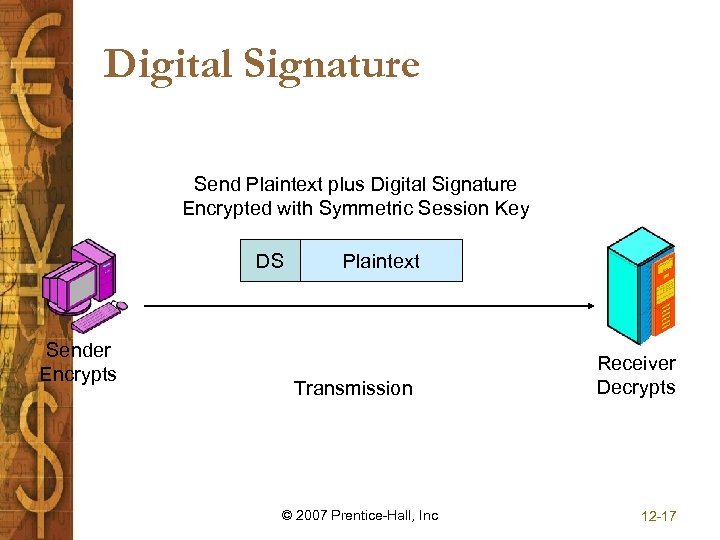 Digital Signature Send Plaintext plus Digital Signature Encrypted with Symmetric Session Key DS Sender Encrypts Plaintext Transmission © 2007 Prentice-Hall, Inc Receiver Decrypts 12 -17
Digital Signature Send Plaintext plus Digital Signature Encrypted with Symmetric Session Key DS Sender Encrypts Plaintext Transmission © 2007 Prentice-Hall, Inc Receiver Decrypts 12 -17
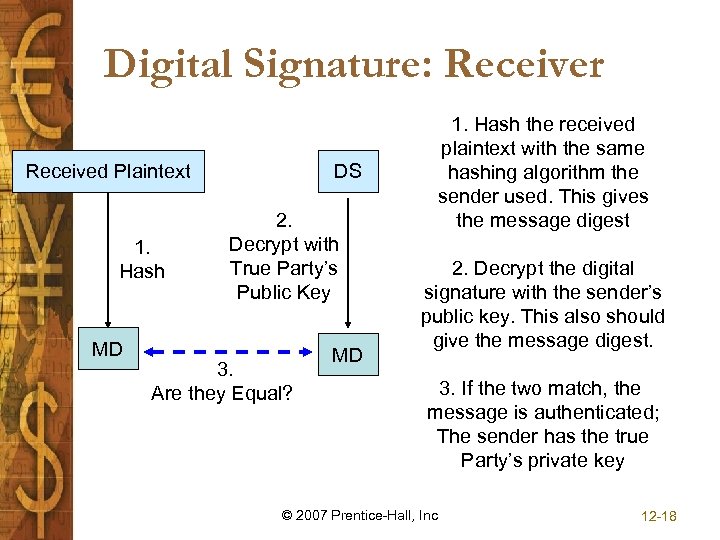 Digital Signature: Receiver Received Plaintext 1. Hash MD DS 2. Decrypt with True Party’s Public Key 3. Are they Equal? MD 1. Hash the received plaintext with the same hashing algorithm the sender used. This gives the message digest 2. Decrypt the digital signature with the sender’s public key. This also should give the message digest. 3. If the two match, the message is authenticated; The sender has the true Party’s private key © 2007 Prentice-Hall, Inc 12 -18
Digital Signature: Receiver Received Plaintext 1. Hash MD DS 2. Decrypt with True Party’s Public Key 3. Are they Equal? MD 1. Hash the received plaintext with the same hashing algorithm the sender used. This gives the message digest 2. Decrypt the digital signature with the sender’s public key. This also should give the message digest. 3. If the two match, the message is authenticated; The sender has the true Party’s private key © 2007 Prentice-Hall, Inc 12 -18
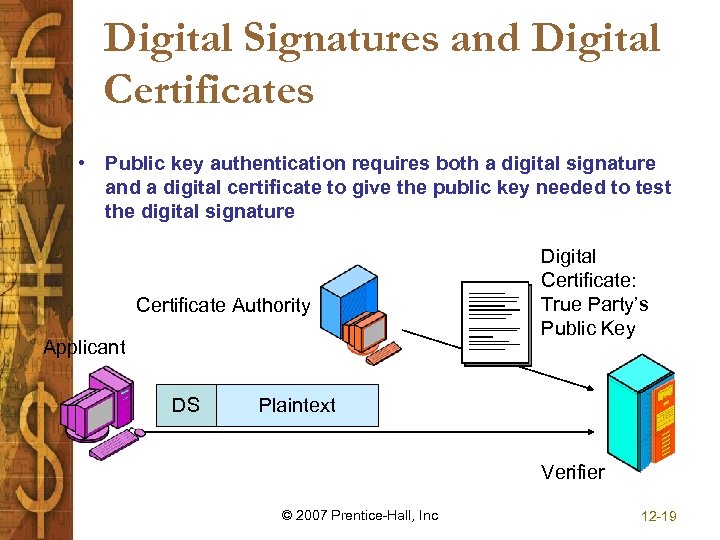 Digital Signatures and Digital Certificates • Public key authentication requires both a digital signature and a digital certificate to give the public key needed to test the digital signature Certificate Authority Applicant DS Digital Certificate: True Party’s Public Key Plaintext Verifier © 2007 Prentice-Hall, Inc 12 -19
Digital Signatures and Digital Certificates • Public key authentication requires both a digital signature and a digital certificate to give the public key needed to test the digital signature Certificate Authority Applicant DS Digital Certificate: True Party’s Public Key Plaintext Verifier © 2007 Prentice-Hall, Inc 12 -19
 Managing Cryptographic Keys • Key management is the process of making keys known to the systems that need them and making sure keys are protected against disclosure or substitution • Key Life Cycle – Key generation and registration – Key distribution – Key backup and recovery • Key escrow: location where keys held in trust by a third party reside – http: //pgp. mit. edu/ • Notary service: company that provides encryptionoriented services including key escrow, key recovery, time stamping, trusted intermediary, and archiving – Key revocation and destruction © 2007 Prentice-Hall, Inc 12 -20
Managing Cryptographic Keys • Key management is the process of making keys known to the systems that need them and making sure keys are protected against disclosure or substitution • Key Life Cycle – Key generation and registration – Key distribution – Key backup and recovery • Key escrow: location where keys held in trust by a third party reside – http: //pgp. mit. edu/ • Notary service: company that provides encryptionoriented services including key escrow, key recovery, time stamping, trusted intermediary, and archiving – Key revocation and destruction © 2007 Prentice-Hall, Inc 12 -20
 Internet Security Protocols • Two key protocols for secure World Wide Web transactions are: – Secure Socket Layer (SSL) is a protocol for secure Web transactions, secures data packets at the network layer – Secure HTTP (S-HTTP) is a protocol that secures Web transactions and nothing else • Secure Electronic Transaction (SET) is a protocol used for handling funds transfers from credit card issuers to a merchant’s bank account – A digital certificate customers can request from their issuing bank by filling out a form on the bank’s Web site – A digital wallet is an online shopping device that seals personal information in a free plug-in that can be invoked when making a purchase © 2007 Prentice-Hall, Inc 12 -21
Internet Security Protocols • Two key protocols for secure World Wide Web transactions are: – Secure Socket Layer (SSL) is a protocol for secure Web transactions, secures data packets at the network layer – Secure HTTP (S-HTTP) is a protocol that secures Web transactions and nothing else • Secure Electronic Transaction (SET) is a protocol used for handling funds transfers from credit card issuers to a merchant’s bank account – A digital certificate customers can request from their issuing bank by filling out a form on the bank’s Web site – A digital wallet is an online shopping device that seals personal information in a free plug-in that can be invoked when making a purchase © 2007 Prentice-Hall, Inc 12 -21
 Secure E-mail • Pretty Good Privacy (PGP) is a protocol that encrypts the data with a one-time algorithm and then encrypts the key to the algorithm using public-key cryptography – http: //www. pgp. com/ – http: //www. gnupg. org/ • S/MIME (Multipurpose Internet Mail Extension) is a powerful protocol that provides security for different data types and attachments to e-mails • Message Security Protocol (MSP) is a protocol that secures e-mail attachments across multiple platforms © 2007 Prentice-Hall, Inc 12 -22
Secure E-mail • Pretty Good Privacy (PGP) is a protocol that encrypts the data with a one-time algorithm and then encrypts the key to the algorithm using public-key cryptography – http: //www. pgp. com/ – http: //www. gnupg. org/ • S/MIME (Multipurpose Internet Mail Extension) is a powerful protocol that provides security for different data types and attachments to e-mails • Message Security Protocol (MSP) is a protocol that secures e-mail attachments across multiple platforms © 2007 Prentice-Hall, Inc 12 -22
 Implications for E-Commerce • Developing high-powered and reliable encryption methods is a top priority for many organizations • Most encryption systems have prevention as the sole means of defense • Merchants face a number of choices when considering encryption methods • A major concern is the cost associated with different encryption methods • Government regulations present considerable problems for businesses © 2007 Prentice-Hall, Inc 12 -23
Implications for E-Commerce • Developing high-powered and reliable encryption methods is a top priority for many organizations • Most encryption systems have prevention as the sole means of defense • Merchants face a number of choices when considering encryption methods • A major concern is the cost associated with different encryption methods • Government regulations present considerable problems for businesses © 2007 Prentice-Hall, Inc 12 -23
 Chapter Summary • Encryption addresses message transmission security requirements • Encryption satisfies requirements for authentication, integrity, and nonrepudiation • There are two classes of key-based algorithms – Secret key – Public key • Cryptanalysis is the science of deciphering encrypted messages without knowing the right key © 2007 Prentice-Hall, Inc 12 -24
Chapter Summary • Encryption addresses message transmission security requirements • Encryption satisfies requirements for authentication, integrity, and nonrepudiation • There are two classes of key-based algorithms – Secret key – Public key • Cryptanalysis is the science of deciphering encrypted messages without knowing the right key © 2007 Prentice-Hall, Inc 12 -24
 Chapter Summary (Cont’d ) • One way to implement public-key authentication is to send a digital signature with each message • A digital certificate is an electronic document issued by a certificate authority (CA) to establish a merchant’s identity by verifying its name and public key • Security measures installed to minimize vulnerability to the exchange of information includes – SSL – SHTTP – SET – S/MIME © 2007 Prentice-Hall, Inc 12 -25
Chapter Summary (Cont’d ) • One way to implement public-key authentication is to send a digital signature with each message • A digital certificate is an electronic document issued by a certificate authority (CA) to establish a merchant’s identity by verifying its name and public key • Security measures installed to minimize vulnerability to the exchange of information includes – SSL – SHTTP – SET – S/MIME © 2007 Prentice-Hall, Inc 12 -25


