27658234ae1da6795c5d4e3d3238a568.ppt
- Количество слайдов: 53
 ELC 200 Day 21 Prentice Hall, 2003 1
ELC 200 Day 21 Prentice Hall, 2003 1
 Agenda Questions from last Class? Assignment 5 Due April 17 3 more assignments left Operations & Finance & ? ? ? EBiz plan and presentations Due may 8 @ 8 AM More to come Two more Quizzes April 20 & May 4 Today's’ discussion is on Law, Ethics, and Cyber Crime Prentice Hall, 2003 2
Agenda Questions from last Class? Assignment 5 Due April 17 3 more assignments left Operations & Finance & ? ? ? EBiz plan and presentations Due may 8 @ 8 AM More to come Two more Quizzes April 20 & May 4 Today's’ discussion is on Law, Ethics, and Cyber Crime Prentice Hall, 2003 2
 Chapter 9 Law, Ethics, and Cyber Crime Prentice Hall, 2003 3
Chapter 9 Law, Ethics, and Cyber Crime Prentice Hall, 2003 3
 Learning Objectives Describe the difference between legal and ethical issues Understand the difficulties of protecting privacy in EC Discuss issues of intellectual property rights in EC Understand the conflict between free speech and censorship on the Internet Prentice Hall, 2003 4
Learning Objectives Describe the difference between legal and ethical issues Understand the difficulties of protecting privacy in EC Discuss issues of intellectual property rights in EC Understand the conflict between free speech and censorship on the Internet Prentice Hall, 2003 4
 Learning Objectives (cont. ) Document the rapid rise in computer and network security attacks Understand the factors contributing to the rise of EC security breaches Describe the key security issues facing EC sites Discuss some of the major types of cyber attacks against EC sites Describe some of the technologies used to secure EC sites Prentice Hall, 2003 5
Learning Objectives (cont. ) Document the rapid rise in computer and network security attacks Understand the factors contributing to the rise of EC security breaches Describe the key security issues facing EC sites Discuss some of the major types of cyber attacks against EC sites Describe some of the technologies used to secure EC sites Prentice Hall, 2003 5
 Additional Resources Center for Democracy & Technology Electronic Privacy Information Center Electronic Frontier Foundation Bruce Schiener FTC & Privacy Lawrence Lessig Prentice Hall, 2003 6
Additional Resources Center for Democracy & Technology Electronic Privacy Information Center Electronic Frontier Foundation Bruce Schiener FTC & Privacy Lawrence Lessig Prentice Hall, 2003 6
 MP 3, Napster, and Intellectual Property Rights The Problem MP 3. com enabled users to listen to music from any computer with an Internet connection without paying royalties Napster supported the free distribution of music and other digitized content among millions utilizing peer-to-peer (P 2 P) technology These services could not be ignored because they could result in the destruction of millions of jobs and revenue Prentice Hall, 2003 7
MP 3, Napster, and Intellectual Property Rights The Problem MP 3. com enabled users to listen to music from any computer with an Internet connection without paying royalties Napster supported the free distribution of music and other digitized content among millions utilizing peer-to-peer (P 2 P) technology These services could not be ignored because they could result in the destruction of millions of jobs and revenue Prentice Hall, 2003 7
 MP 3, Napster, and Intellectual Property Rights (cont. ) The Solution Emusic. com filed a copyright infringement lawsuit against MP 3. com Copyright laws and copyright cases have been in existence for years but: Were not written for digital content Financial gain loophole was not closed Prentice Hall, 2003 8
MP 3, Napster, and Intellectual Property Rights (cont. ) The Solution Emusic. com filed a copyright infringement lawsuit against MP 3. com Copyright laws and copyright cases have been in existence for years but: Were not written for digital content Financial gain loophole was not closed Prentice Hall, 2003 8
 MP 3, Napster, and Intellectual Property Rights (cont. ) The Results All commerce involves a number of legal, ethical, and regulatory issues EC adds a number of questions about what constitutes illegal behavior versus unethical, intrusive, or undesirable behavior Prentice Hall, 2003 9
MP 3, Napster, and Intellectual Property Rights (cont. ) The Results All commerce involves a number of legal, ethical, and regulatory issues EC adds a number of questions about what constitutes illegal behavior versus unethical, intrusive, or undesirable behavior Prentice Hall, 2003 9
 Legal Issues vs. Ethical Issues Ethics—the branch of philosophy that deals with what is considered to be right and wrong Businesspeople engaging in e-commerce need guidelines as to what behaviors are reasonable under any given set of circumstances What is unethical in one culture may be perfectly acceptable in another Prentice Hall, 2003 10
Legal Issues vs. Ethical Issues Ethics—the branch of philosophy that deals with what is considered to be right and wrong Businesspeople engaging in e-commerce need guidelines as to what behaviors are reasonable under any given set of circumstances What is unethical in one culture may be perfectly acceptable in another Prentice Hall, 2003 10
 Privacy—the right to be left alone and the right to be free of unreasonable personal intrusions Two rules have been followed fairly closely in court decisions: 1. The right of privacy is not absolute. Privacy must be balanced against the needs of society 2. The public ’s right to know is superior to the individual’s right of privacy Prentice Hall, 2003 11
Privacy—the right to be left alone and the right to be free of unreasonable personal intrusions Two rules have been followed fairly closely in court decisions: 1. The right of privacy is not absolute. Privacy must be balanced against the needs of society 2. The public ’s right to know is superior to the individual’s right of privacy Prentice Hall, 2003 11
 Privacy Advocates Take On Double. Click is one of the leading providers of online advertising Double. Click uses cookies to personalize ads based on consumers’ interests In January 1999, Double. Click bought catalog marketer Abacus Direct and announced plans to merge Abacus’s off-line database with their online data Prentice Hall, 2003 12
Privacy Advocates Take On Double. Click is one of the leading providers of online advertising Double. Click uses cookies to personalize ads based on consumers’ interests In January 1999, Double. Click bought catalog marketer Abacus Direct and announced plans to merge Abacus’s off-line database with their online data Prentice Hall, 2003 12
 Privacy Advocates Take On Double. Click (cont. ) Several class action lawsuits were brought against Double. Click, claiming that the company was “tracking Internet users and obtaining personal and financial information with-out the individual’s knowledge In violation of the state’s Consumer Protection Act and asked it to stop placing cookies on consumers’ computers without their permission In January 2001, the FTC ruled that Double. Click had not violated FTC policies http: //www. infoworld. com/articles/hn/xml/01/01/22 /010122 hndoubleclick. html? p=br&s=1 Prentice Hall, 2003 13
Privacy Advocates Take On Double. Click (cont. ) Several class action lawsuits were brought against Double. Click, claiming that the company was “tracking Internet users and obtaining personal and financial information with-out the individual’s knowledge In violation of the state’s Consumer Protection Act and asked it to stop placing cookies on consumers’ computers without their permission In January 2001, the FTC ruled that Double. Click had not violated FTC policies http: //www. infoworld. com/articles/hn/xml/01/01/22 /010122 hndoubleclick. html? p=br&s=1 Prentice Hall, 2003 13
 Privacy Advocates Take On Double. Click (cont. ) Double. Click agreed to enhance its privacy measures and to pay legal fees and costs up to $18 million Key provision of the settlement requires Double. Click to “obtain permission from consumers before combining any personally identifiable data with Web surfing history” Prentice Hall, 2003 14
Privacy Advocates Take On Double. Click (cont. ) Double. Click agreed to enhance its privacy measures and to pay legal fees and costs up to $18 million Key provision of the settlement requires Double. Click to “obtain permission from consumers before combining any personally identifiable data with Web surfing history” Prentice Hall, 2003 14
 Web-Site Self-Registration questionnaires 50% disclose personal information on a Web site for the chance to win a sweepstakes Uses of the private information collected: For planning the business May be sold to a third party Must not be used in an inappropriate manner Prentice Hall, 2003 15
Web-Site Self-Registration questionnaires 50% disclose personal information on a Web site for the chance to win a sweepstakes Uses of the private information collected: For planning the business May be sold to a third party Must not be used in an inappropriate manner Prentice Hall, 2003 15
 Cookies Cookie—a small piece of data that is passed back and forth between a Web site and an end user’s browser as the user navigates the site; enables sites to keep track of users’ activities without asking for identification Cookies can be used to invade an individual ’s privacy Personal information collected via cookies has the potential to be used in illegal and unethical ways Prentice Hall, 2003 16
Cookies Cookie—a small piece of data that is passed back and forth between a Web site and an end user’s browser as the user navigates the site; enables sites to keep track of users’ activities without asking for identification Cookies can be used to invade an individual ’s privacy Personal information collected via cookies has the potential to be used in illegal and unethical ways Prentice Hall, 2003 16
 Cookies (cont. ) Solutions to unwanted cookies Users can delete cookie files stored in their computer Use of anti-cookie software Passport—a Microsoft component that lets consumers permanently enter a profile of information along with a password and use this information and password repeatedly to access services at multiple sites Prentice Hall, 2003 17
Cookies (cont. ) Solutions to unwanted cookies Users can delete cookie files stored in their computer Use of anti-cookie software Passport—a Microsoft component that lets consumers permanently enter a profile of information along with a password and use this information and password repeatedly to access services at multiple sites Prentice Hall, 2003 17
 Protection of Privacy Notice/awareness Choice/consent Access/participation Integrity/security Enforcement/redress Supported in the U. S. by the Federal Internet Privacy Protection Act Supported in the European Union by EU Data Protection Directive Prentice Hall, 2003 18
Protection of Privacy Notice/awareness Choice/consent Access/participation Integrity/security Enforcement/redress Supported in the U. S. by the Federal Internet Privacy Protection Act Supported in the European Union by EU Data Protection Directive Prentice Hall, 2003 18
 Intellectual Property Rights Intellectual property (IP)—creations of the mind, such as inventions, literary and artistic works, and symbols, names, images, and designs used in commerce © ® Prentice Hall, 2003 19
Intellectual Property Rights Intellectual property (IP)—creations of the mind, such as inventions, literary and artistic works, and symbols, names, images, and designs used in commerce © ® Prentice Hall, 2003 19
 Intellectual Property Rights (cont. ) Copyright—an exclusive grant from the government that allows the owner to reproduce a work, in whole or in part, and to distribute, perform, or display it to the public in any form or manner, including the Internet Digital watermarks—unique identifiers imbedded in digital content that make it possible to identify pirated works http: //www. digimarc. com/ Prentice Hall, 2003 20
Intellectual Property Rights (cont. ) Copyright—an exclusive grant from the government that allows the owner to reproduce a work, in whole or in part, and to distribute, perform, or display it to the public in any form or manner, including the Internet Digital watermarks—unique identifiers imbedded in digital content that make it possible to identify pirated works http: //www. digimarc. com/ Prentice Hall, 2003 20
 Intellectual Property Rights (cont. ) Trademarks—a symbol used by businesses to identify their goods and services; government registration of the trademark confers exclusive legal right to its use Gives exclusive rights to: Use trademark on goods and services registered to that sign Take legal action to prevent anyone from using trademark without consent Patent—a document that grants the holder exclusive rights on an invention for a fixed number of years United States Patent and Trademark Office Prentice Hall, 2003 21
Intellectual Property Rights (cont. ) Trademarks—a symbol used by businesses to identify their goods and services; government registration of the trademark confers exclusive legal right to its use Gives exclusive rights to: Use trademark on goods and services registered to that sign Take legal action to prevent anyone from using trademark without consent Patent—a document that grants the holder exclusive rights on an invention for a fixed number of years United States Patent and Trademark Office Prentice Hall, 2003 21
 Free Speech and Censorship on the Internet The issue of censorship is one of the most important to Web surfers “Most citizens are implacably opposed to censorship in any form — except censorship of whatever they personally happen to find offensive. ” Citizen action groups desiring to protect every ounce of their freedom to speak Children ’s Online Protection Act (COPA) http: //www. copacommission. org/ Governments protective of their role in society Prentice Hall, 2003 22
Free Speech and Censorship on the Internet The issue of censorship is one of the most important to Web surfers “Most citizens are implacably opposed to censorship in any form — except censorship of whatever they personally happen to find offensive. ” Citizen action groups desiring to protect every ounce of their freedom to speak Children ’s Online Protection Act (COPA) http: //www. copacommission. org/ Governments protective of their role in society Prentice Hall, 2003 22
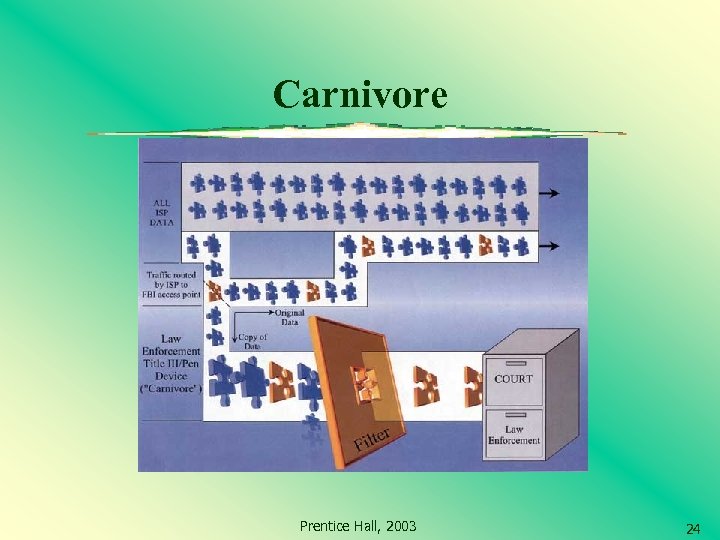
 Government Invasions of Privacy? Internet Wire Taps FBI has the ability to tap into your Internet Traffic FBI has Dragon. Ware which contains three parts: Carnivore - A Windows NT/2000 -based system that captures the information Packeteer - No official information released, but presumably an application for reassembling packets into cohesive messages or Web pages Coolminer - No official information released, but presumably an application for extrapolating and analyzing data found in the messages FBI’s Carnivore http: //www. epic. org/privacy/carnivore/foia_documents. html More on Carnivore http: //computer. howstuffworks. com/carnivore. htm Prentice Hall, 2003 23
Government Invasions of Privacy? Internet Wire Taps FBI has the ability to tap into your Internet Traffic FBI has Dragon. Ware which contains three parts: Carnivore - A Windows NT/2000 -based system that captures the information Packeteer - No official information released, but presumably an application for reassembling packets into cohesive messages or Web pages Coolminer - No official information released, but presumably an application for extrapolating and analyzing data found in the messages FBI’s Carnivore http: //www. epic. org/privacy/carnivore/foia_documents. html More on Carnivore http: //computer. howstuffworks. com/carnivore. htm Prentice Hall, 2003 23
 Carnivore Prentice Hall, 2003 24
Carnivore Prentice Hall, 2003 24
 Controlling Spamming—the practice of indiscriminately broadcasting messages over the Internet (e. g. , junk mail) Spam comprised 25 to 50% of all e-mail Slows the internet in general; sometimes Shuts ISPs down completely Electronic Mailbox Protection Act ISPs are required to offer spam-blocking software Recipients of spam have the right to request termination of future spam from the same sender and to bring civil action if necessary http: //spam. abuse. net/ Prentice Hall, 2003 25
Controlling Spamming—the practice of indiscriminately broadcasting messages over the Internet (e. g. , junk mail) Spam comprised 25 to 50% of all e-mail Slows the internet in general; sometimes Shuts ISPs down completely Electronic Mailbox Protection Act ISPs are required to offer spam-blocking software Recipients of spam have the right to request termination of future spam from the same sender and to bring civil action if necessary http: //spam. abuse. net/ Prentice Hall, 2003 25
 Cyber Crime Fraud Intentional deceit or trickery, often with the aim of financial gain – Trademark infringement is often fraud (fake Gucci, Rolex etc) Cyber attack An electronic attack, either criminal trespass over the Internet (cyber intrusion) or unauthorized access that results in damaged files, programs, or hardware (cyber vandalism) Prentice Hall, 2003 26
Cyber Crime Fraud Intentional deceit or trickery, often with the aim of financial gain – Trademark infringement is often fraud (fake Gucci, Rolex etc) Cyber attack An electronic attack, either criminal trespass over the Internet (cyber intrusion) or unauthorized access that results in damaged files, programs, or hardware (cyber vandalism) Prentice Hall, 2003 26
 The Players: Hackers, Crackers, and Other Attackers Hackers Original hackers created the Unix operating system and helped build the Internet, Usenet, and World Wide Web; and, used their skills to test the strength and integrity of computer systems Over time, the term hacker came to be applied to rogue programmers who illegally break into computers and networks Hacker underground http: //www. defcon. org/ http: //www. blackhat. com/ http: //www. 2600. com/ Prentice Hall, 2003 27
The Players: Hackers, Crackers, and Other Attackers Hackers Original hackers created the Unix operating system and helped build the Internet, Usenet, and World Wide Web; and, used their skills to test the strength and integrity of computer systems Over time, the term hacker came to be applied to rogue programmers who illegally break into computers and networks Hacker underground http: //www. defcon. org/ http: //www. blackhat. com/ http: //www. 2600. com/ Prentice Hall, 2003 27
 The Players: Hackers, Crackers, and Other Attackers (cont. ) Crackers People who engage in unlawful or damaging hacking short for “criminal hackers” Other attackers “Script kiddies” are ego-driven, unskilled crackers who use information and software (scripts) that they download from the Internet to inflict damage on targeted sites Scorned by both the Law enforcement and Hackers communities Prentice Hall, 2003 28
The Players: Hackers, Crackers, and Other Attackers (cont. ) Crackers People who engage in unlawful or damaging hacking short for “criminal hackers” Other attackers “Script kiddies” are ego-driven, unskilled crackers who use information and software (scripts) that they download from the Internet to inflict damage on targeted sites Scorned by both the Law enforcement and Hackers communities Prentice Hall, 2003 28
![Script Kiddies script kiddies: pl. n. 1. [very common] The lowest form of cracker; Script Kiddies script kiddies: pl. n. 1. [very common] The lowest form of cracker;](https://present5.com/presentation/27658234ae1da6795c5d4e3d3238a568/image-29.jpg) Script Kiddies script kiddies: pl. n. 1. [very common] The lowest form of cracker; script kiddies do mischief with scripts and rootkits written by others, often without understanding the exploit they are using. Used of people with limited technical expertise using easy-to-operate, pre-configured, and/or automated tools to conduct disruptive activities against networked systems. Since most of these tools are fairly well-known by the security community, the adverse impact of such actions is usually minimal. 2. People who cannot program, but who create tacky HTML pages by copying Java. Script routines from other tacky HTML pages. More generally, a script kiddie writes (or more likely cuts and pastes) code without either having or desiring to have a mental model of what the code does; someone who thinks of code as magical incantations and asks only “what do I need to type to make this happen? ” Source: http: //www. catb. org/jargon/html/S/scriptkiddies. html More info: http: //www. tamingthebeast. net/articles/scriptkiddies. htm Prentice Hall, 2003 29
Script Kiddies script kiddies: pl. n. 1. [very common] The lowest form of cracker; script kiddies do mischief with scripts and rootkits written by others, often without understanding the exploit they are using. Used of people with limited technical expertise using easy-to-operate, pre-configured, and/or automated tools to conduct disruptive activities against networked systems. Since most of these tools are fairly well-known by the security community, the adverse impact of such actions is usually minimal. 2. People who cannot program, but who create tacky HTML pages by copying Java. Script routines from other tacky HTML pages. More generally, a script kiddie writes (or more likely cuts and pastes) code without either having or desiring to have a mental model of what the code does; someone who thinks of code as magical incantations and asks only “what do I need to type to make this happen? ” Source: http: //www. catb. org/jargon/html/S/scriptkiddies. html More info: http: //www. tamingthebeast. net/articles/scriptkiddies. htm Prentice Hall, 2003 29
 Internet Security Cyber attacks are on the rise Internet connections are increasingly a point of attack The variety of attacks is on the rise Why now? Because that’s where the money and information is! Prentice Hall, 2003 30
Internet Security Cyber attacks are on the rise Internet connections are increasingly a point of attack The variety of attacks is on the rise Why now? Because that’s where the money and information is! Prentice Hall, 2003 30
 Internet Security (cont. ) Factors have contributed to the rise in cyber attacks: Security and ease of use are antithetical to one another Security takes a back seat to market pressures Security of an EC site depends on the security of the Internet as a whole Security vulnerabilities are mushrooming Security is compromised by common applications Prentice Hall, 2003 31
Internet Security (cont. ) Factors have contributed to the rise in cyber attacks: Security and ease of use are antithetical to one another Security takes a back seat to market pressures Security of an EC site depends on the security of the Internet as a whole Security vulnerabilities are mushrooming Security is compromised by common applications Prentice Hall, 2003 31
 Basic Security Issues From the user ’s perspective: How can the user be sure that the Web server is owned and operated by a legitimate company? How does the user know that the Web page and form do not contain some malicious or dangerous code or content? How does the user know that the Web server will not distribute the information the user provides to some other party? Prentice Hall, 2003 32
Basic Security Issues From the user ’s perspective: How can the user be sure that the Web server is owned and operated by a legitimate company? How does the user know that the Web page and form do not contain some malicious or dangerous code or content? How does the user know that the Web server will not distribute the information the user provides to some other party? Prentice Hall, 2003 32
 Basic Security Issues (cont. ) From the company ’s perspective: How does the company know the user will not attempt to break into the Web server or alter the pages and content at the site? How does the company know that the user will not try to disrupt the server so that it is not available to others? Prentice Hall, 2003 33
Basic Security Issues (cont. ) From the company ’s perspective: How does the company know the user will not attempt to break into the Web server or alter the pages and content at the site? How does the company know that the user will not try to disrupt the server so that it is not available to others? Prentice Hall, 2003 33
 Basic Security Issues (cont. ) From both parties ’perspectives: How do they know that the network connection is free from eavesdropping by a third party “listening in ”on the line? How do they know that the information sent back and forth between the server and the user ’s browser has not been altered? Prentice Hall, 2003 34
Basic Security Issues (cont. ) From both parties ’perspectives: How do they know that the network connection is free from eavesdropping by a third party “listening in ”on the line? How do they know that the information sent back and forth between the server and the user ’s browser has not been altered? Prentice Hall, 2003 34
 Basic Security Issues (cont. ) Authorization The process that ensures that a person has the right to access certain resources Authentication The process by which one entity verifies that another entity is who they claim to be by checking credentials of some sort Prentice Hall, 2003 35
Basic Security Issues (cont. ) Authorization The process that ensures that a person has the right to access certain resources Authentication The process by which one entity verifies that another entity is who they claim to be by checking credentials of some sort Prentice Hall, 2003 35
 Basic Security Issues (cont. ) Auditing The process of collecting information about attempts to access particular resources, use particular privileges, or perform other security actions Confidentiality (privacy) Integrity As applied to data, the ability to protect data from being altered or destroyed in an unauthorized or accidental manner Prentice Hall, 2003 36
Basic Security Issues (cont. ) Auditing The process of collecting information about attempts to access particular resources, use particular privileges, or perform other security actions Confidentiality (privacy) Integrity As applied to data, the ability to protect data from being altered or destroyed in an unauthorized or accidental manner Prentice Hall, 2003 36
 Basic Security Issues (cont. ) Integrity As applied to data, the ability to protect data from being altered or destroyed in an unauthorized or accidental manner Availability Nonrepudiation The ability to limit parties from refuting that a legitimate transaction took place, usually by means of a signature Prentice Hall, 2003 37
Basic Security Issues (cont. ) Integrity As applied to data, the ability to protect data from being altered or destroyed in an unauthorized or accidental manner Availability Nonrepudiation The ability to limit parties from refuting that a legitimate transaction took place, usually by means of a signature Prentice Hall, 2003 37
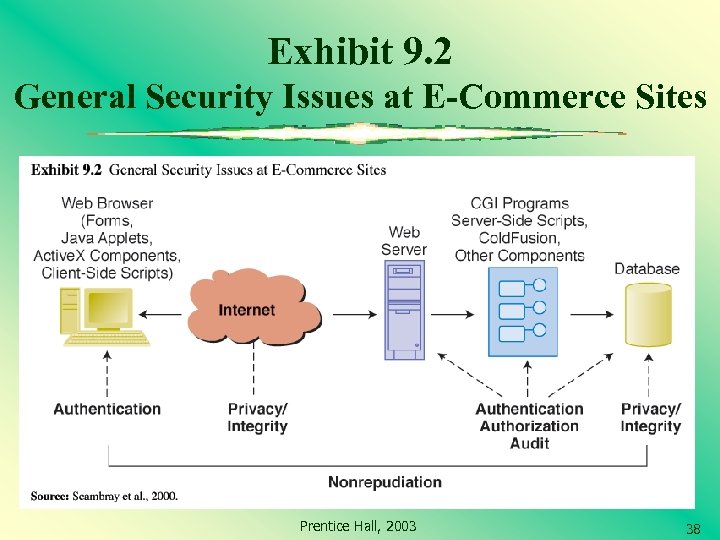 Exhibit 9. 2 General Security Issues at E-Commerce Sites Prentice Hall, 2003 38
Exhibit 9. 2 General Security Issues at E-Commerce Sites Prentice Hall, 2003 38
 Types of Cyber Attacks Technical attack An attack perpetrated using software and systems knowledge or expertise Nontechnical attack An attack in which a perpetrator uses chicanery or other form of persuasion to trick people into revealing sensitive information or performing actions that compromise the security of a network Social Engineering Prentice Hall, 2003 39
Types of Cyber Attacks Technical attack An attack perpetrated using software and systems knowledge or expertise Nontechnical attack An attack in which a perpetrator uses chicanery or other form of persuasion to trick people into revealing sensitive information or performing actions that compromise the security of a network Social Engineering Prentice Hall, 2003 39
 Types of Cyber Attacks (cont. ) Common vulnerabilities and exposures (CVEs) Publicly known computer security risks or problems; these are collected, enumerated, and shared by a board of security-related organizations (cve. mitre. org) http: //www. cert. org/ Denial-of-service (Do. S) attack An attack on a Web site in which an attacker uses specialized software to send a flood of data packets to the target computer with the aim of overloading its resources Prentice Hall, 2003 40
Types of Cyber Attacks (cont. ) Common vulnerabilities and exposures (CVEs) Publicly known computer security risks or problems; these are collected, enumerated, and shared by a board of security-related organizations (cve. mitre. org) http: //www. cert. org/ Denial-of-service (Do. S) attack An attack on a Web site in which an attacker uses specialized software to send a flood of data packets to the target computer with the aim of overloading its resources Prentice Hall, 2003 40
 Types of Cyber Attacks (cont. ) Distributed denial of service (DDo. S) attack A denial-of-service attack in which the attacker gains illegal administrative access to as many computers on the Internet as possible and uses these multiple computers to send a flood of data packets to the target computer Malware A generic term for malicious software Prentice Hall, 2003 41
Types of Cyber Attacks (cont. ) Distributed denial of service (DDo. S) attack A denial-of-service attack in which the attacker gains illegal administrative access to as many computers on the Internet as possible and uses these multiple computers to send a flood of data packets to the target computer Malware A generic term for malicious software Prentice Hall, 2003 41
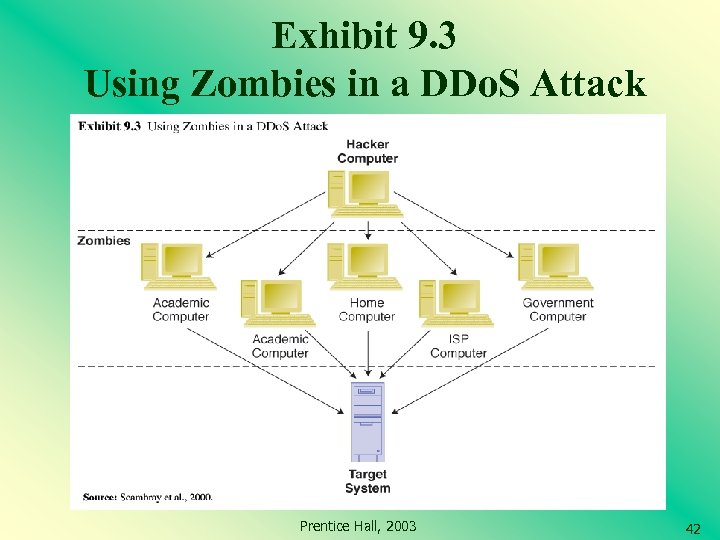 Exhibit 9. 3 Using Zombies in a DDo. S Attack Prentice Hall, 2003 42
Exhibit 9. 3 Using Zombies in a DDo. S Attack Prentice Hall, 2003 42
 Types of Cyber Attacks (cont. ) Virus A piece of software code that inserts itself into a host, including the operating systems, to propagate; it cannot run independently but requires that its host program be run to activate it Worm A software program that runs independently, consuming the resources of its host from within in order to maintain itself and propagating a complete working version of itself onto another machine Prentice Hall, 2003 43
Types of Cyber Attacks (cont. ) Virus A piece of software code that inserts itself into a host, including the operating systems, to propagate; it cannot run independently but requires that its host program be run to activate it Worm A software program that runs independently, consuming the resources of its host from within in order to maintain itself and propagating a complete working version of itself onto another machine Prentice Hall, 2003 43
 Types of Cyber Attacks (cont. ) Trojan horse A program that appears to have a useful function but that contains a hidden function that presents a security risk Two of the better-known Trojan horses “Back Orifice ”and “Net. Bus” Self-contained and self-installing utilities that can be used to remotely control and monitor the victim ’s computer over a network (execute commands, list files, upload and download files on the victim’s computer) Prentice Hall, 2003 44
Types of Cyber Attacks (cont. ) Trojan horse A program that appears to have a useful function but that contains a hidden function that presents a security risk Two of the better-known Trojan horses “Back Orifice ”and “Net. Bus” Self-contained and self-installing utilities that can be used to remotely control and monitor the victim ’s computer over a network (execute commands, list files, upload and download files on the victim’s computer) Prentice Hall, 2003 44
 Trojan Horse Attack on Bugtraq List Bug. Traq—a full disclosure moderated mailing list for the detailed discussion and announcement of computer security vulnerabilities: What they are How to exploit them How to fix them Prentice Hall, 2003 45
Trojan Horse Attack on Bugtraq List Bug. Traq—a full disclosure moderated mailing list for the detailed discussion and announcement of computer security vulnerabilities: What they are How to exploit them How to fix them Prentice Hall, 2003 45
 Trojan Horse Attack on Bugtraq List (cont. ) Security. Focus. com experts have been fooled Sent the code containing a Trojan horse to its 37, 000 Bug. Trac subscribers Network Associates server found itself under attack The way the list is moderated did not change Prentice Hall, 2003 46
Trojan Horse Attack on Bugtraq List (cont. ) Security. Focus. com experts have been fooled Sent the code containing a Trojan horse to its 37, 000 Bug. Trac subscribers Network Associates server found itself under attack The way the list is moderated did not change Prentice Hall, 2003 46
 Security Technologies Internet and EC security is a thriving business Firewalls and Access Control One major impediments to EC is the concern about the security of internal networks Sidestep the issue by letting third parties host their Web sites Primary means of access control is password Prentice Hall, 2003 47
Security Technologies Internet and EC security is a thriving business Firewalls and Access Control One major impediments to EC is the concern about the security of internal networks Sidestep the issue by letting third parties host their Web sites Primary means of access control is password Prentice Hall, 2003 47
 Security Technologies (cont. ) Firewall A network node consisting of both hardware and software that isolates a private network from a public network Intrusion detection system (IDS) A special category of software that can monitor activity across a network or on a host computer, watch for suspicious activity, and take automated action based on what it sees Prentice Hall, 2003 48
Security Technologies (cont. ) Firewall A network node consisting of both hardware and software that isolates a private network from a public network Intrusion detection system (IDS) A special category of software that can monitor activity across a network or on a host computer, watch for suspicious activity, and take automated action based on what it sees Prentice Hall, 2003 48
 Security Technologies (cont. ) Security risk management A systematic process for determining the likelihood of various security attacks and for identifying the actions needed to prevent or mitigate those attacks Assessment Planning Implementation Monitoring Prentice Hall, 2003 49
Security Technologies (cont. ) Security risk management A systematic process for determining the likelihood of various security attacks and for identifying the actions needed to prevent or mitigate those attacks Assessment Planning Implementation Monitoring Prentice Hall, 2003 49
 Managerial Issues How can the global nature of EC impact business operations? What sorts of legal and ethical issues should be of major concern to an EC enterprise? What are the business consequences of poor security? Prentice Hall, 2003 50
Managerial Issues How can the global nature of EC impact business operations? What sorts of legal and ethical issues should be of major concern to an EC enterprise? What are the business consequences of poor security? Prentice Hall, 2003 50
 Managerial Issues (cont. ) Are we safe if there are few visitors to our EC site? Is technology the key to EC security? Where are the security threats likely to come from? Prentice Hall, 2003 51
Managerial Issues (cont. ) Are we safe if there are few visitors to our EC site? Is technology the key to EC security? Where are the security threats likely to come from? Prentice Hall, 2003 51
 Summary Describe the differences between legal and ethical issues in EC Understand the difficulties of protecting privacy in EC Discuss the issues of intellectual property rights in EC. proven to be particularly Understand the conflict between free speech and censorship on the Internet Prentice Hall, 2003 52
Summary Describe the differences between legal and ethical issues in EC Understand the difficulties of protecting privacy in EC Discuss the issues of intellectual property rights in EC. proven to be particularly Understand the conflict between free speech and censorship on the Internet Prentice Hall, 2003 52
 Summary (cont. ) Document the rapid rise in computer and network security attacks Understand the factors contributing to the rise of EC security breaches Describe the key security issues facing EC sites Discuss some of the major types of cyber attacks against EC sites Describe some of the technologies used to secure EC sites Prentice Hall, 2003 53
Summary (cont. ) Document the rapid rise in computer and network security attacks Understand the factors contributing to the rise of EC security breaches Describe the key security issues facing EC sites Discuss some of the major types of cyber attacks against EC sites Describe some of the technologies used to secure EC sites Prentice Hall, 2003 53


