 Efficient User Authentication and Key Management for Peer-to. Peer Live Streaming Systems Authors: X. Liu, Y. Hao, C. Lin, and C. Du Source: Tsinghua Science and Technology, vol. 14, no. 2, pp. 234 -241, 2009 Speaker: Shu-Fen Chiou (邱淑芬) 1
Efficient User Authentication and Key Management for Peer-to. Peer Live Streaming Systems Authors: X. Liu, Y. Hao, C. Lin, and C. Du Source: Tsinghua Science and Technology, vol. 14, no. 2, pp. 234 -241, 2009 Speaker: Shu-Fen Chiou (邱淑芬) 1
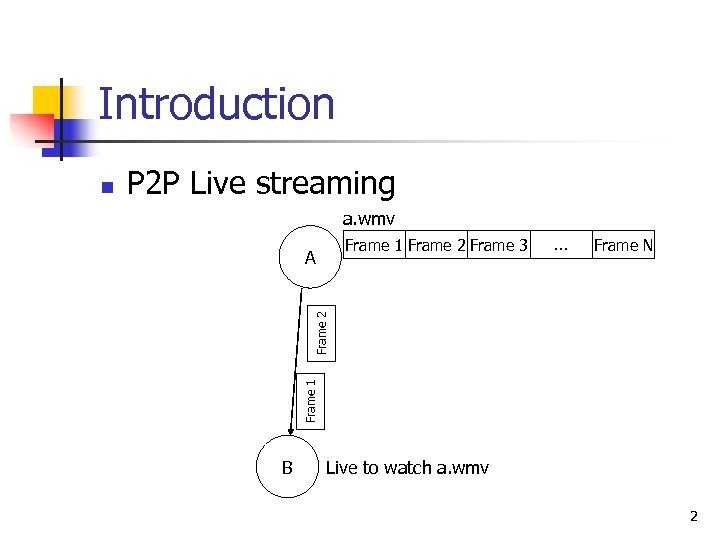 Introduction P 2 P Live streaming a. wmv Frame 1 Frame 2 Frame 3 … Frame N Frame 2 A Frame 1 n B Live to watch a. wmv 2
Introduction P 2 P Live streaming a. wmv Frame 1 Frame 2 Frame 3 … Frame N Frame 2 A Frame 1 n B Live to watch a. wmv 2
 Challenges in streaming systems n n n High bit rates End-to-end delay Packet losses Network congestion Service guarantees Security 3
Challenges in streaming systems n n n High bit rates End-to-end delay Packet losses Network congestion Service guarantees Security 3
 Motivation n For P 2 P live media streaming, authors proposed a secure scheme using user authentication and key managements. 4
Motivation n For P 2 P live media streaming, authors proposed a secure scheme using user authentication and key managements. 4
 Requirements n n Confidentiality Data integrity Scalability Efficient 5
Requirements n n Confidentiality Data integrity Scalability Efficient 5
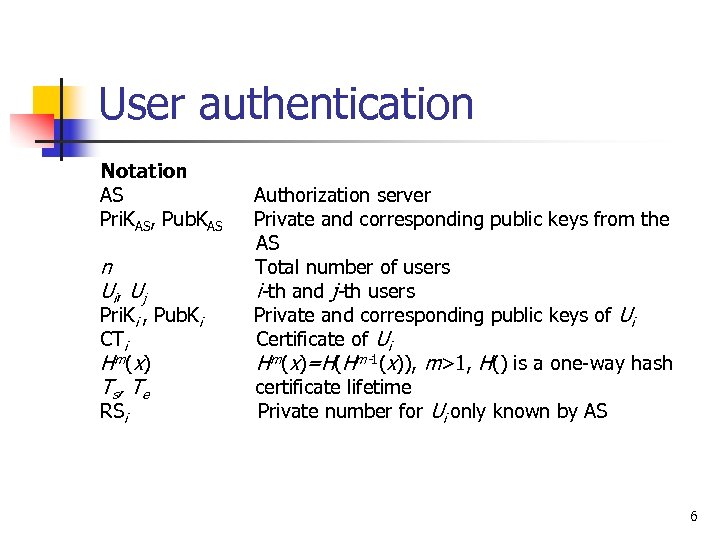 User authentication Notation AS Pri. KAS, Pub. KAS n Ui, Uj Pri. Ki , Pub. Ki CTi H m ( x) Ts, Te RSi Authorization server Private and corresponding public keys from the AS Total number of users i-th and j-th users Private and corresponding public keys of Ui Certificate of Ui Hm(x)=H(Hm-1(x)), m>1, H() is a one-way hash certificate lifetime Private number for Ui only known by AS 6
User authentication Notation AS Pri. KAS, Pub. KAS n Ui, Uj Pri. Ki , Pub. Ki CTi H m ( x) Ts, Te RSi Authorization server Private and corresponding public keys from the AS Total number of users i-th and j-th users Private and corresponding public keys of Ui Certificate of Ui Hm(x)=H(Hm-1(x)), m>1, H() is a one-way hash certificate lifetime Private number for Ui only known by AS 6
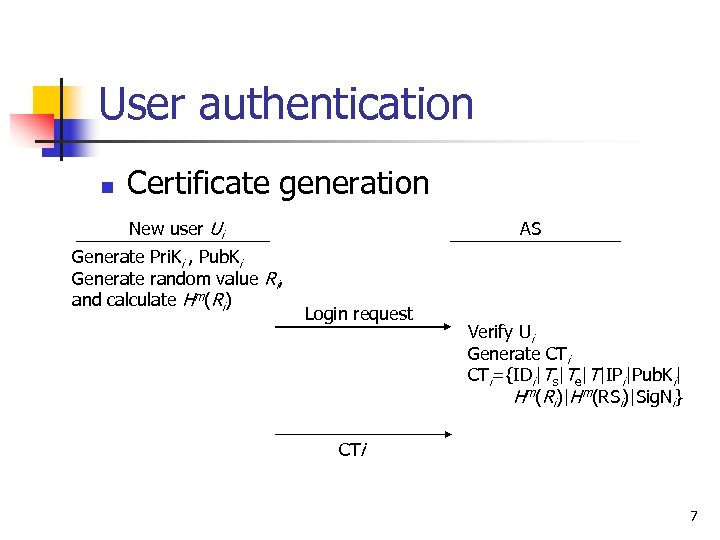 User authentication n Certificate generation New user Ui Generate Pri. Ki , Pub. Ki Generate random value Ri, and calculate Hm(Ri) AS Login request Verify Ui Generate CTi={IDi|Ts|Te|T|IPi|Pub. Ki| Hm(Ri)|Hm(RSi)|Sig. Ni} CTi 7
User authentication n Certificate generation New user Ui Generate Pri. Ki , Pub. Ki Generate random value Ri, and calculate Hm(Ri) AS Login request Verify Ui Generate CTi={IDi|Ts|Te|T|IPi|Pub. Ki| Hm(Ri)|Hm(RSi)|Sig. Ni} CTi 7
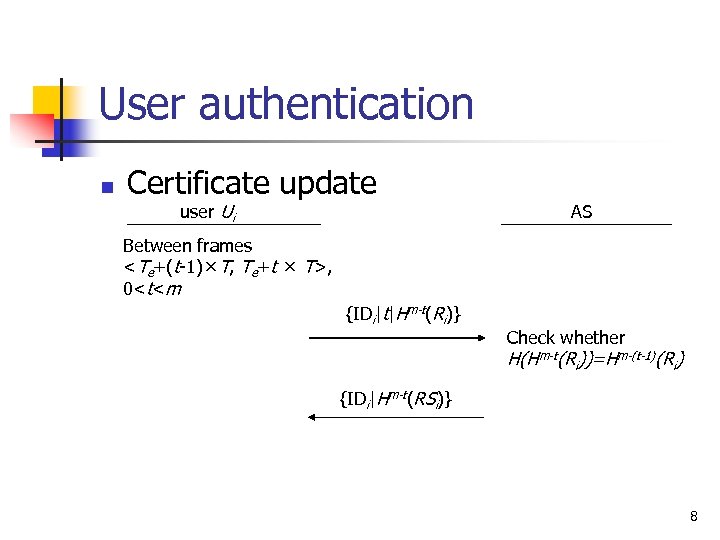 User authentication n Certificate update user Ui AS Between frames , 0
User authentication n Certificate update user Ui AS Between frames , 0
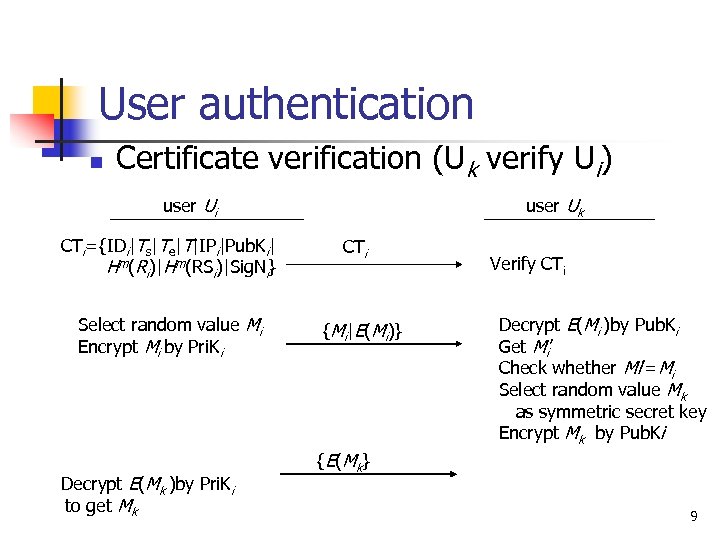 User authentication n Certificate verification (Uk verify Ui) user Ui CTi={IDi|Ts|Te|T|IPi|Pub. Ki| Hm(Ri)|Hm(RSi)|Sig. Ni} Select random value Mi Encrypt Mi by Pri. Ki Decrypt E(Mk )by Pri. Ki to get Mk user Uk CTi {Mi|E(Mi)} Verify CTi Decrypt E(Mi )by Pub. Ki Get Mi’ Check whether Mi’=Mi Select random value Mk as symmetric secret key Encrypt Mk by Pub. Ki {E(Mk} 9
User authentication n Certificate verification (Uk verify Ui) user Ui CTi={IDi|Ts|Te|T|IPi|Pub. Ki| Hm(Ri)|Hm(RSi)|Sig. Ni} Select random value Mi Encrypt Mi by Pri. Ki Decrypt E(Mk )by Pri. Ki to get Mk user Uk CTi {Mi|E(Mi)} Verify CTi Decrypt E(Mi )by Pub. Ki Get Mi’ Check whether Mi’=Mi Select random value Mk as symmetric secret key Encrypt Mk by Pub. Ki {E(Mk} 9
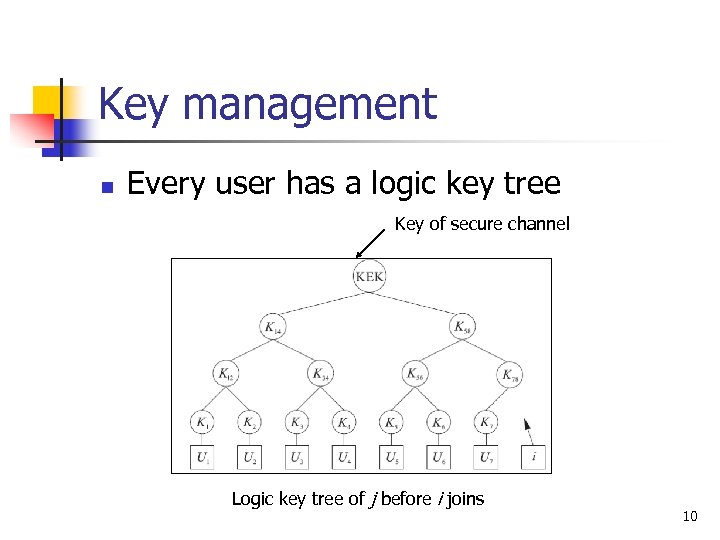 Key management n Every user has a logic key tree Key of secure channel Logic key tree of j before i joins 10
Key management n Every user has a logic key tree Key of secure channel Logic key tree of j before i joins 10
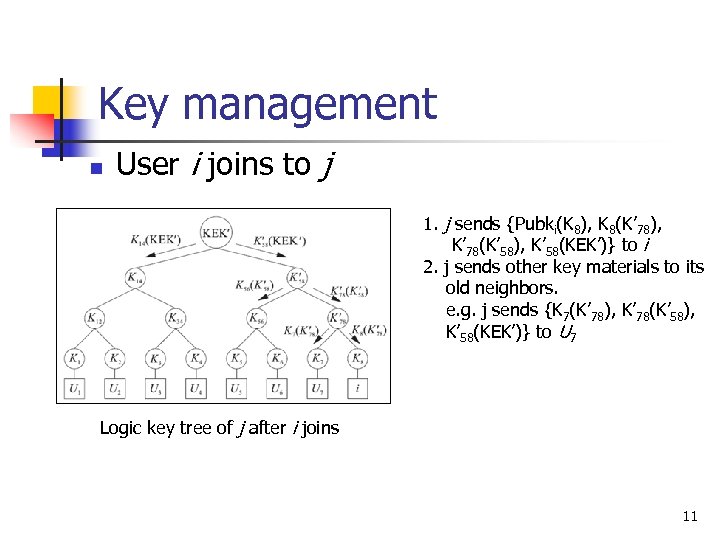 Key management n User i joins to j 1. j sends {Pubki(K 8), K 8(K’ 78), K’ 78(K’ 58), K’ 58(KEK’)} to i 2. j sends other key materials to its old neighbors. e. g. j sends {K 7(K’ 78), K’ 78(K’ 58), K’ 58(KEK’)} to U 7 Logic key tree of j after i joins 11
Key management n User i joins to j 1. j sends {Pubki(K 8), K 8(K’ 78), K’ 78(K’ 58), K’ 58(KEK’)} to i 2. j sends other key materials to its old neighbors. e. g. j sends {K 7(K’ 78), K’ 78(K’ 58), K’ 58(KEK’)} to U 7 Logic key tree of j after i joins 11
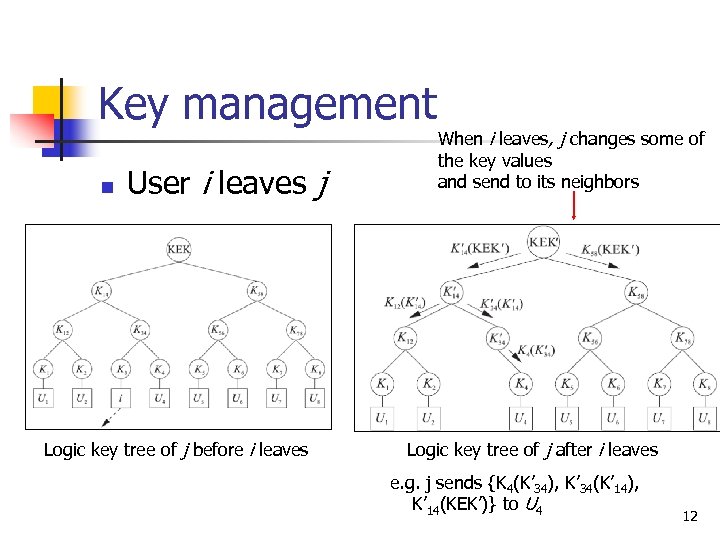 Key management n User i leaves j Logic key tree of j before i leaves When i leaves, j changes some of the key values and send to its neighbors Logic key tree of j after i leaves e. g. j sends {K 4(K’ 34), K’ 34(K’ 14), K’ 14(KEK’)} to U 4 12
Key management n User i leaves j Logic key tree of j before i leaves When i leaves, j changes some of the key values and send to its neighbors Logic key tree of j after i leaves e. g. j sends {K 4(K’ 34), K’ 34(K’ 14), K’ 14(KEK’)} to U 4 12
 此篇paper之優缺點 n 優點: n n 延伸authentication及key management應用 在P 2 P live streaming protocol 缺點: n Certificate verification無相互驗證 13
此篇paper之優缺點 n 優點: n n 延伸authentication及key management應用 在P 2 P live streaming protocol 缺點: n Certificate verification無相互驗證 13
 可能研究方向 n n Certificate verification相互驗證 加入付費機制 14
可能研究方向 n n Certificate verification相互驗證 加入付費機制 14