fe160ddc5ea858359a034dd1e3530ae1.ppt
- Количество слайдов: 23
 Efficient Secure Aggregation in VANETs Maxim Raya, Adel Aziz, and Jean-Pierre Hubaux Laboratory for computer Communications and Applications (LCA) EPFL
Efficient Secure Aggregation in VANETs Maxim Raya, Adel Aziz, and Jean-Pierre Hubaux Laboratory for computer Communications and Applications (LCA) EPFL
 Outline § Motivation § Attacker model § Secure group formation § Secure aggregation mechanisms § Simulation results § Conclusion 2
Outline § Motivation § Attacker model § Secure group formation § Secure aggregation mechanisms § Simulation results § Conclusion 2
 Why efficient secure aggregation? § § VANET security is indispensable but expensive De facto security: limited flooding of signed messages § Since many vehicles broadcast the same event, why not try aggregation? 1. Can we make it work in VANETs? 2. And can we make it secure? § The answer is in this presentation and it is: YES 3
Why efficient secure aggregation? § § VANET security is indispensable but expensive De facto security: limited flooding of signed messages § Since many vehicles broadcast the same event, why not try aggregation? 1. Can we make it work in VANETs? 2. And can we make it secure? § The answer is in this presentation and it is: YES 3
 How to make aggregation efficient and secure? § Requirements: • Channel efficiency • Low delay • Data correctness • Non-repudiation § We propose 3 solutions: • Combined signatures • Overlapping groups • Dynamic group key creation 4
How to make aggregation efficient and secure? § Requirements: • Channel efficiency • Low delay • Data correctness • Non-repudiation § We propose 3 solutions: • Combined signatures • Overlapping groups • Dynamic group key creation 4
 Who is the attacker? § Major threat: false information dissemination § Assumption: Any group of more than 2 vehicles should contain a majority of honest nodes under normal density conditions 5
Who is the attacker? § Major threat: false information dissemination § Assumption: Any group of more than 2 vehicles should contain a majority of honest nodes under normal density conditions 5
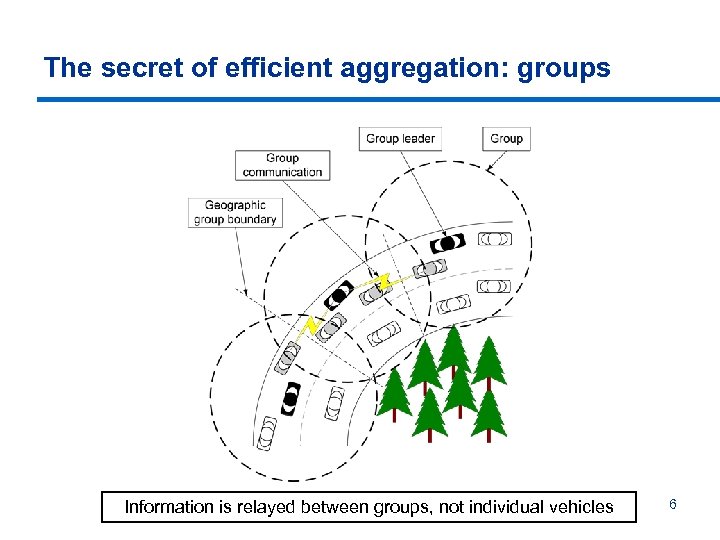 The secret of efficient aggregation: groups Information is relayed between groups, not individual vehicles 6
The secret of efficient aggregation: groups Information is relayed between groups, not individual vehicles 6
 How to make a group? § § § Preset groups: efficient but not flexible On-the-fly groups: flexible but not efficient Location-based groups: efficient and flexible • § The keyword is where and not who a vehicle’s neighbors are Group formation step-by-step: 1. 2. 3. 4. Dissect the map into small area cells, each defining a group Load map dissection function/dissected maps into vehicles Cells (groups) overlap to ensure handover One option for leader election: group leader = vehicle closest to center (with lowest ID if many), elected for a given duration 5. A vehicle checks its GPS position to determine its cell (group) 7
How to make a group? § § § Preset groups: efficient but not flexible On-the-fly groups: flexible but not efficient Location-based groups: efficient and flexible • § The keyword is where and not who a vehicle’s neighbors are Group formation step-by-step: 1. 2. 3. 4. Dissect the map into small area cells, each defining a group Load map dissection function/dissected maps into vehicles Cells (groups) overlap to ensure handover One option for leader election: group leader = vehicle closest to center (with lowest ID if many), elected for a given duration 5. A vehicle checks its GPS position to determine its cell (group) 7
 Group formation 8
Group formation 8
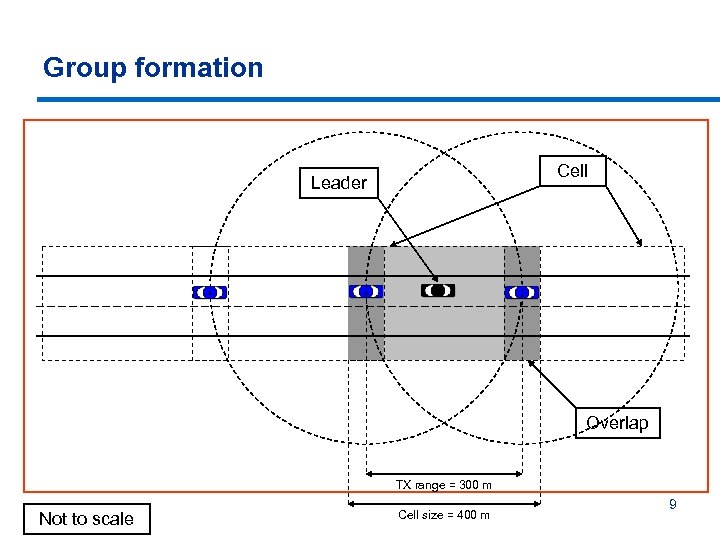 Group formation Cell Leader Overlap TX range = 300 m Not to scale Cell size = 400 m 9
Group formation Cell Leader Overlap TX range = 300 m Not to scale Cell size = 400 m 9
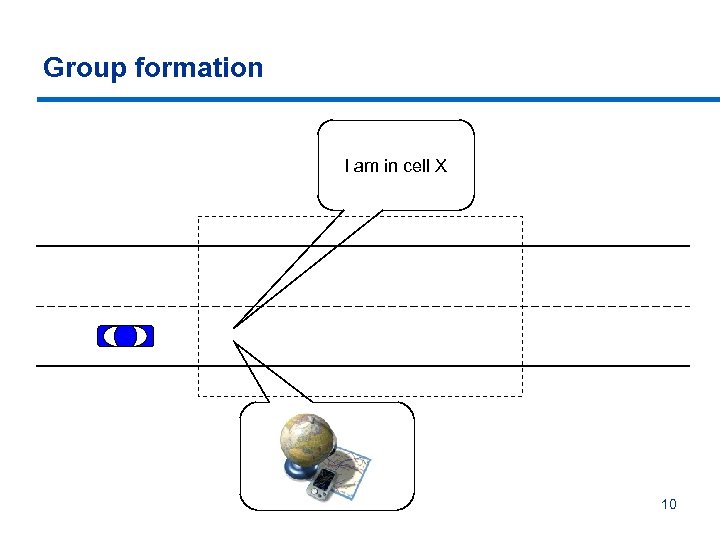 Group formation I am in cell X 10
Group formation I am in cell X 10
 SVGP (Secure VANET Group Protocol) § Goal: establishment of a symmetric group key § Secure groups protect the network from outsiders only § Concept: group leader transports group key to members § Subsequent messages include only a HMAC § On leave, nothing needs to be done § Vehicles at boundaries receive messages from 2 groups 11
SVGP (Secure VANET Group Protocol) § Goal: establishment of a symmetric group key § Secure groups protect the network from outsiders only § Concept: group leader transports group key to members § Subsequent messages include only a HMAC § On leave, nothing needs to be done § Vehicles at boundaries receive messages from 2 groups 11
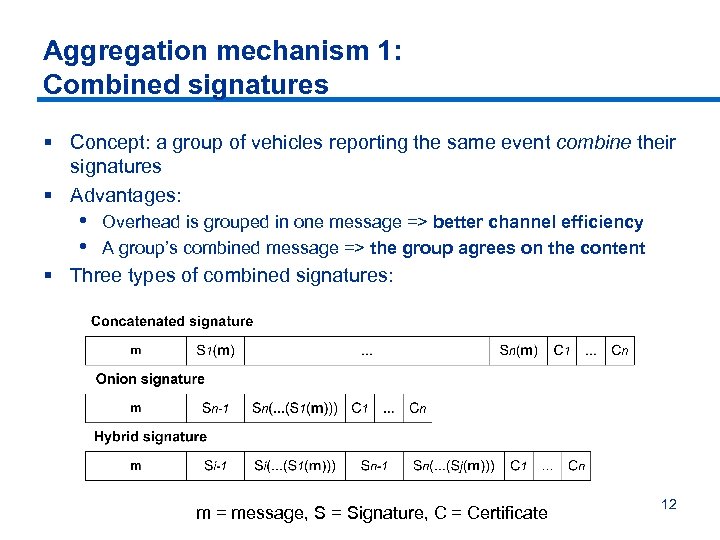 Aggregation mechanism 1: Combined signatures § Concept: a group of vehicles reporting the same event combine their signatures § Advantages: • • Overhead is grouped in one message => better channel efficiency A group’s combined message => the group agrees on the content § Three types of combined signatures: m = message, S = Signature, C = Certificate 12
Aggregation mechanism 1: Combined signatures § Concept: a group of vehicles reporting the same event combine their signatures § Advantages: • • Overhead is grouped in one message => better channel efficiency A group’s combined message => the group agrees on the content § Three types of combined signatures: m = message, S = Signature, C = Certificate 12
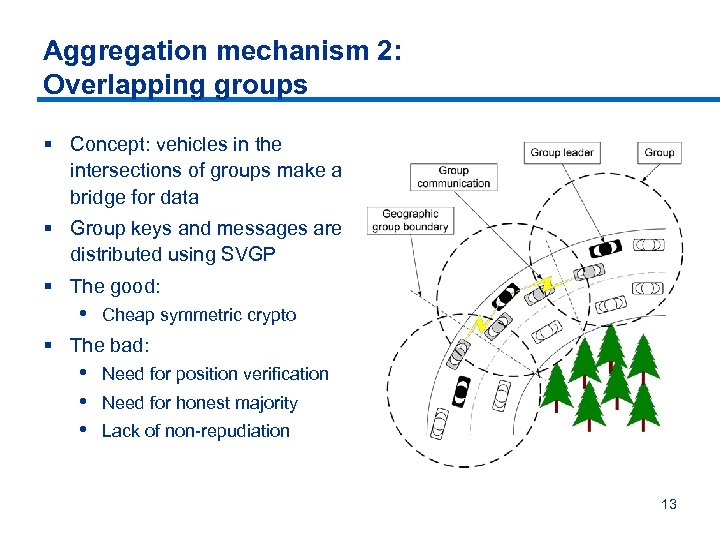 Aggregation mechanism 2: Overlapping groups § Concept: vehicles in the intersections of groups make a bridge for data § Group keys and messages are distributed using SVGP § The good: • Cheap symmetric crypto § The bad: • • • Need for position verification Need for honest majority Lack of non-repudiation 13
Aggregation mechanism 2: Overlapping groups § Concept: vehicles in the intersections of groups make a bridge for data § Group keys and messages are distributed using SVGP § The good: • Cheap symmetric crypto § The bad: • • • Need for position verification Need for honest majority Lack of non-repudiation 13
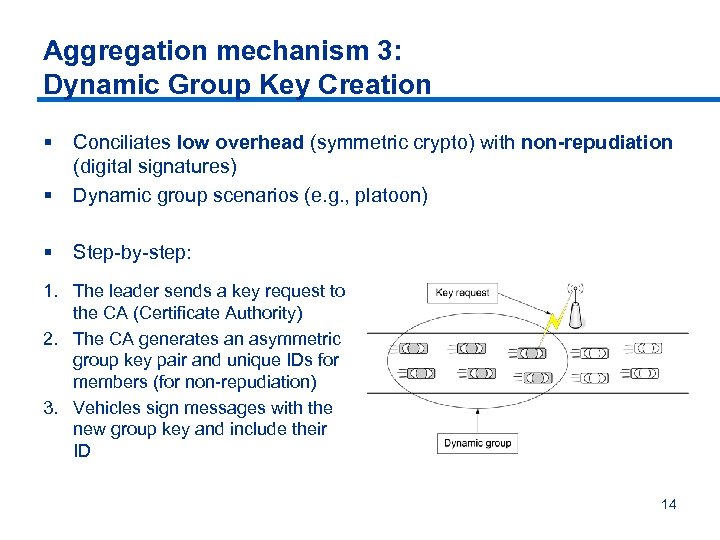 Aggregation mechanism 3: Dynamic Group Key Creation § § Conciliates low overhead (symmetric crypto) with non-repudiation (digital signatures) Dynamic group scenarios (e. g. , platoon) § Step-by-step: 1. The leader sends a key request to the CA (Certificate Authority) 2. The CA generates an asymmetric group key pair and unique IDs for members (for non-repudiation) 3. Vehicles sign messages with the new group key and include their ID 14
Aggregation mechanism 3: Dynamic Group Key Creation § § Conciliates low overhead (symmetric crypto) with non-repudiation (digital signatures) Dynamic group scenarios (e. g. , platoon) § Step-by-step: 1. The leader sends a key request to the CA (Certificate Authority) 2. The CA generates an asymmetric group key pair and unique IDs for members (for non-repudiation) 3. Vehicles sign messages with the new group key and include their ID 14
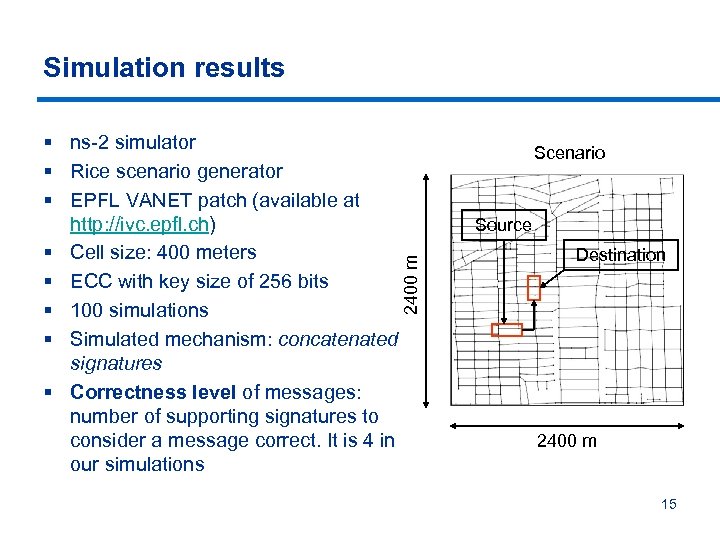 Simulation results 2400 m § ns-2 simulator § Rice scenario generator § EPFL VANET patch (available at http: //ivc. epfl. ch) § Cell size: 400 meters § ECC with key size of 256 bits § 100 simulations § Simulated mechanism: concatenated signatures § Correctness level of messages: number of supporting signatures to consider a message correct. It is 4 in our simulations Scenario Source Destination 2400 m 15
Simulation results 2400 m § ns-2 simulator § Rice scenario generator § EPFL VANET patch (available at http: //ivc. epfl. ch) § Cell size: 400 meters § ECC with key size of 256 bits § 100 simulations § Simulated mechanism: concatenated signatures § Correctness level of messages: number of supporting signatures to consider a message correct. It is 4 in our simulations Scenario Source Destination 2400 m 15
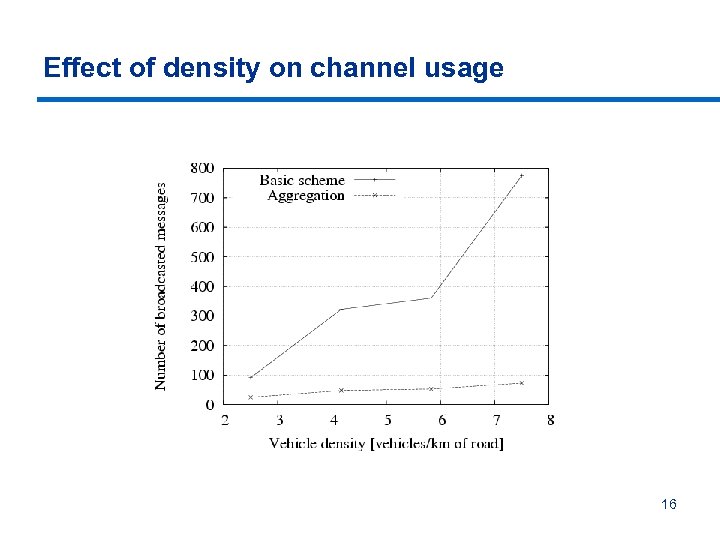 Effect of density on channel usage 16
Effect of density on channel usage 16
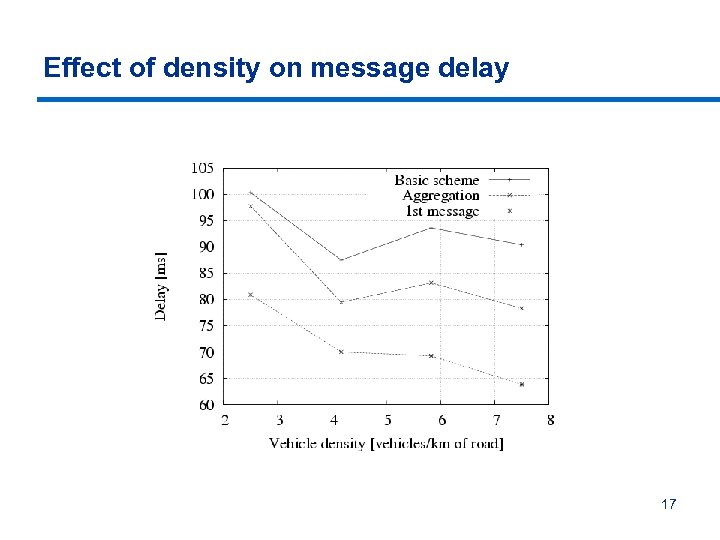 Effect of density on message delay 17
Effect of density on message delay 17
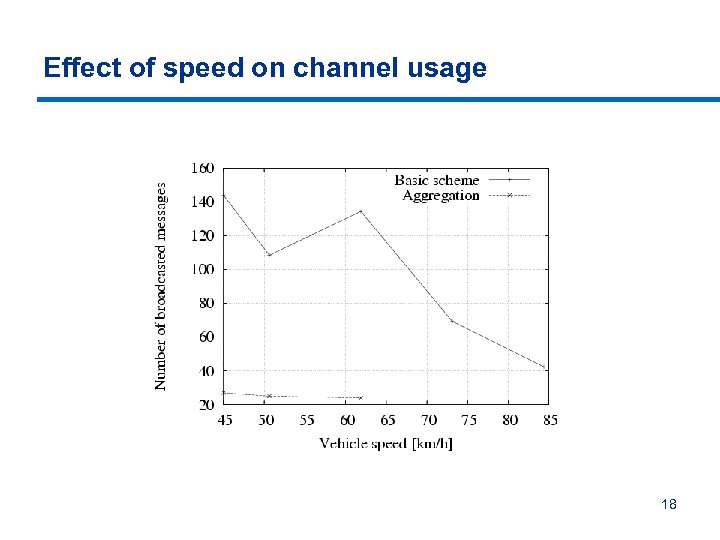 Effect of speed on channel usage 18
Effect of speed on channel usage 18
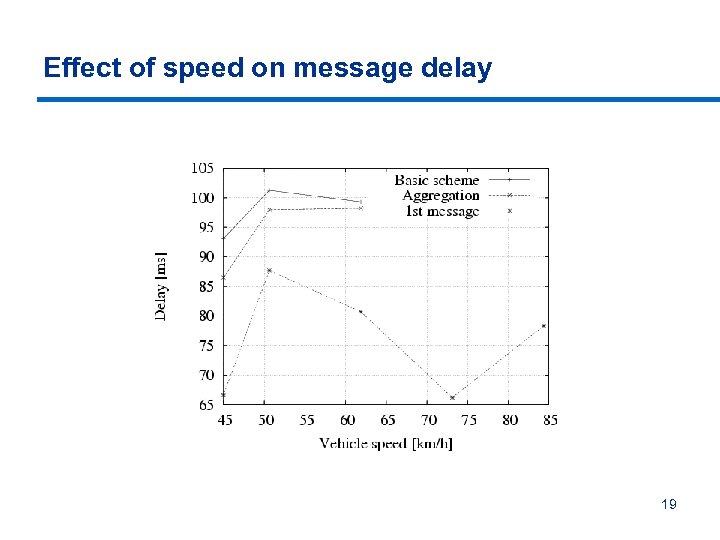 Effect of speed on message delay 19
Effect of speed on message delay 19
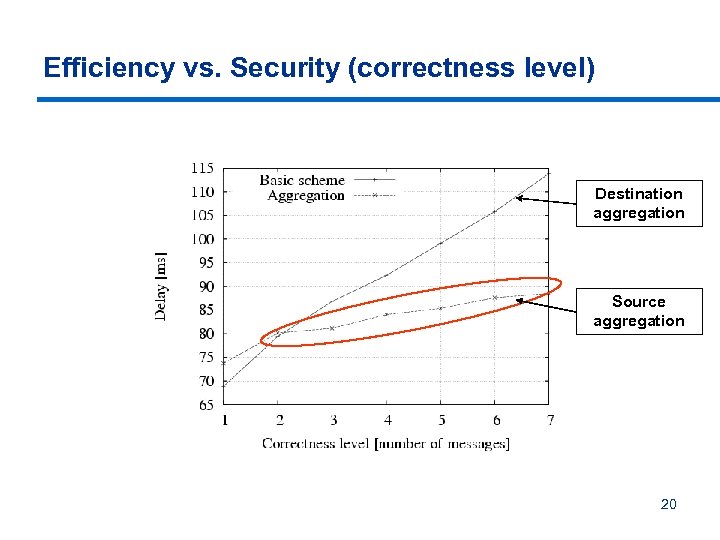 Efficiency vs. Security (correctness level) Destination aggregation Source aggregation 20
Efficiency vs. Security (correctness level) Destination aggregation Source aggregation 20
 Conclusion § Objective: the tradeoff between efficiency and security § Efficient secure aggregation is a feasible answer: • Combined signatures • Overlapping groups • Dynamic group key creation § The advantages: • Better channel usage • Lower message delivery delay • Better data correctness and hence security § Visit http: //ivc. epfl. ch and http: //www. sevecom. org 21
Conclusion § Objective: the tradeoff between efficiency and security § Efficient secure aggregation is a feasible answer: • Combined signatures • Overlapping groups • Dynamic group key creation § The advantages: • Better channel usage • Lower message delivery delay • Better data correctness and hence security § Visit http: //ivc. epfl. ch and http: //www. sevecom. org 21
 SEVECOM (SEcure VEhicular COMmunication) Objectives: Identification of threats and Specification of a security architecture 22
SEVECOM (SEcure VEhicular COMmunication) Objectives: Identification of threats and Specification of a security architecture 22
 CALL FOR PAPERS IEEE Journal on Selected Areas in Communications Vehicular Networks • Architecture of Vehicular networks • Protocol design (low-power, multi-channel, etc. ) • Vehicle-to-Vehicle • PHY, MAC, Network Layer (Routing protocols) • Vehicle-to-Roadside • Channel Modeling • Security and privacy • Cooperative aspects of vehicular communication • Cross-layer optimization techniques • Scalability and Availability issues in Vehicular networks • Mobility and traffic models • Safety and commercial applications Manuscript Submission February 1, 2007 Acceptance Notification May 15, 2007 Final Manuscript Due to Publisher July 1, 2007 Publication Date 3 rd Quarter 2007 http: //www. jsac. ucsd. edu/Calls/vehnetwkcfp. htm 23
CALL FOR PAPERS IEEE Journal on Selected Areas in Communications Vehicular Networks • Architecture of Vehicular networks • Protocol design (low-power, multi-channel, etc. ) • Vehicle-to-Vehicle • PHY, MAC, Network Layer (Routing protocols) • Vehicle-to-Roadside • Channel Modeling • Security and privacy • Cooperative aspects of vehicular communication • Cross-layer optimization techniques • Scalability and Availability issues in Vehicular networks • Mobility and traffic models • Safety and commercial applications Manuscript Submission February 1, 2007 Acceptance Notification May 15, 2007 Final Manuscript Due to Publisher July 1, 2007 Publication Date 3 rd Quarter 2007 http: //www. jsac. ucsd. edu/Calls/vehnetwkcfp. htm 23


