7b61b50a0af3c9f58ee5eac7a87c3451.ppt
- Количество слайдов: 54

Efficient Group Signatures from Bilinear Pairing Author: Xiangguo Cheng, Huafei Zhu, Ying Qiu, and Xinmei Wang Presenter: 紀汶承

Outline n n n Preliminaries Definition and Security Requirements Mini Group Signature The Improved Group Signature Conclusions

Preliminaries n n Bilinear Pairing Gap Diffie-hellman Group

Bilinear Pairing n G 1 : cyclic additive group generated by P whose order is a prime q. G 2 : cyclic multiplicative group of the same order q. A bilinear pairing is a computable map e : G 1 × G 1 → G 2 with the following properties

Bilinear Pairing 1. Bilinear: and for any a, b 2. Non-degenerate: There exists such that
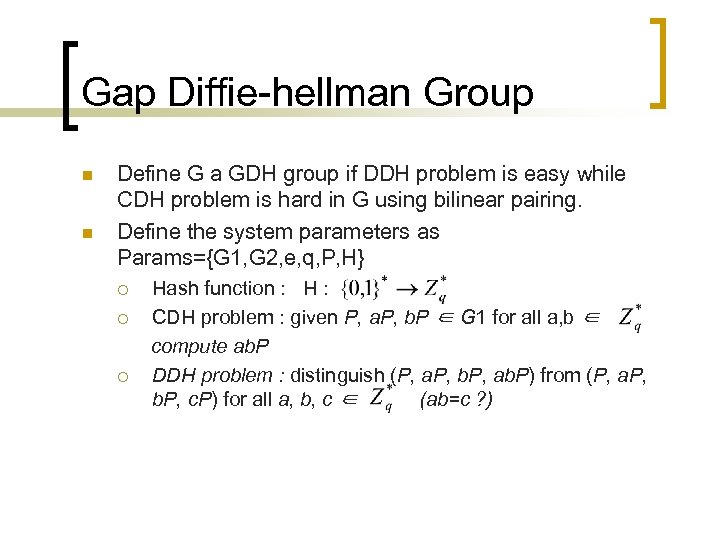
Gap Diffie-hellman Group n n Define G a GDH group if DDH problem is easy while CDH problem is hard in G using bilinear pairing. Define the system parameters as Params={G 1, G 2, e, q, P, H} ¡ ¡ ¡ Hash function : H : CDH problem : given P, a. P, b. P ∈ G 1 for all a, b ∈ compute ab. P DDH problem : distinguish (P, a. P, b. P, ab. P) from (P, a. P, b. P, c. P) for all a, b, c ∈ (ab=c ? )

Definition n A group signature scheme consists of two parties: ¡ ¡ the group manager (GM) a set of group members and comprises a family of at least five procedures described as follows.
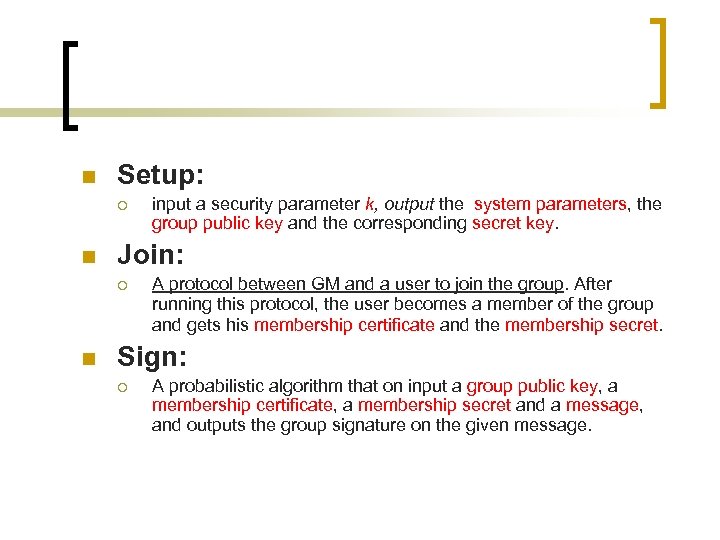
n Setup: ¡ n Join: ¡ n input a security parameter k, output the system parameters, the group public key and the corresponding secret key. A protocol between GM and a user to join the group. After running this protocol, the user becomes a member of the group and gets his membership certificate and the membership secret. Sign: ¡ A probabilistic algorithm that on input a group public key, a membership certificate, a membership secret and a message, and outputs the group signature on the given message.

n Verify: ¡ n A boolean-valued algorithm used to verify the validity of the group signature generated by the Sign. Open: ¡ An algorithm only run by GM. Given a message, a valid group signature on it, a group public key and the corresponding secret key, determine the identity of the signer

Security Requirements n 1. Correctness: ¡ n 2. Unforgeability: ¡ n None but a group member is able to produce a valid group signature on behalf of the group. 3. Anonymity: ¡ n A valid group signature generated by a group member using Sign must be accepted by Verify. Given a valid group signature of some message, it is computationally hard to determine the original signer for everyone but GM. 4. Unlinkability: ¡ Given several group signatures on the same or different messages, it is computationally infeasible to decide whether the signatures were generated by the same or by different group members.

n 5. Exculpability: ¡ n 6. Traceability: ¡ n A group signature generated by a group member cannot be successfully attributed to another. Even GM cannot produce signatures on behalf of other group members. GM is always able to open a valid group signature and identify the actual signer. 7. Coalition-resistance: ¡ Even if a coalition of some group members (even a whole set of the entire group) collaborate to generate a valid group signature on some message, can GM attribute the signature to the colluding members.

Mini Group Signature n n Scheme Security Analysis

Mini Group Signature n n n Apart from GM and a set of group members, we introduce a trusted on-line third party, called a security mediator (SEM) in our scheme. The main idea behind our scheme is that the secret key of the group is split into two parts by GM, one part is given to the user as his group membership secret key, and the other one is given to SEM. Revoke easy: GM needs only ask SEM not to provide the group member partial signatures anymore.

n SEM has the following functionality: (1)Help GM and the users to easily realize the join protocol. As a result, the users become group members. (2)Help the legal group members to produce valid group signatures. (3)Realize the immediate revocation of group membership. (4)Help GM to open some group signatures and reveal the identities of the original signers in the case of a later dispute.

The Proposed Scheme n n Setup: Given a security parameter κ, GM runs the GDH Parameters Generator to obtain the system parameters Params = {G 1, G 2, e, q, P, H}. It then randomly chooses x and computes X = x. P ∈ G 1. The private-public key pair of the group is (x, X). Join: Suppose that is a user who wants to join the group. Assume that the communication between GM and users and between SEM and GM is secure. GM randomly chooses and computes mod q. is sent to and is sent to SEM. After this protocol, becomes a group member and his group membership secret key is.
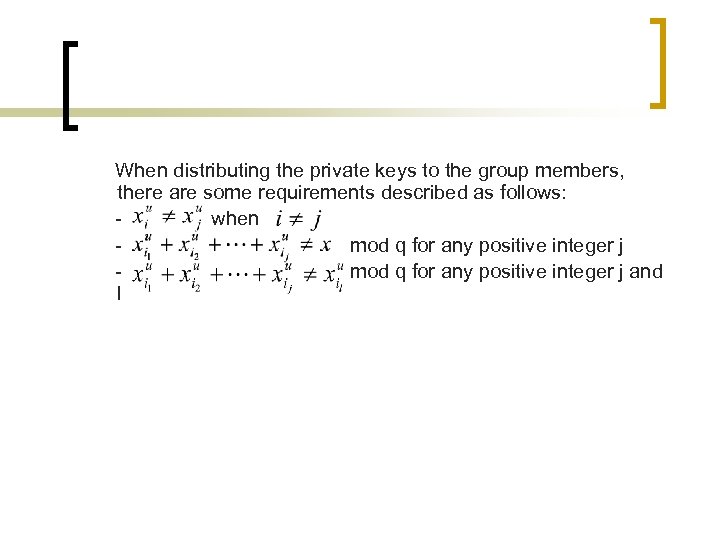
When distributing the private keys to the group members, there are some requirements described as follows: when mod q for any positive integer j and l

n Sign: To generate a group signature on some message M, the group member collaborates with SEM to do the following work: sends H(M) along with his identity to SEM - SEM first checks that the group membership of has not been revoked. It then computes , stores and send back to. computes and. He checks where holds. If so, the group signature on message M is set to be.
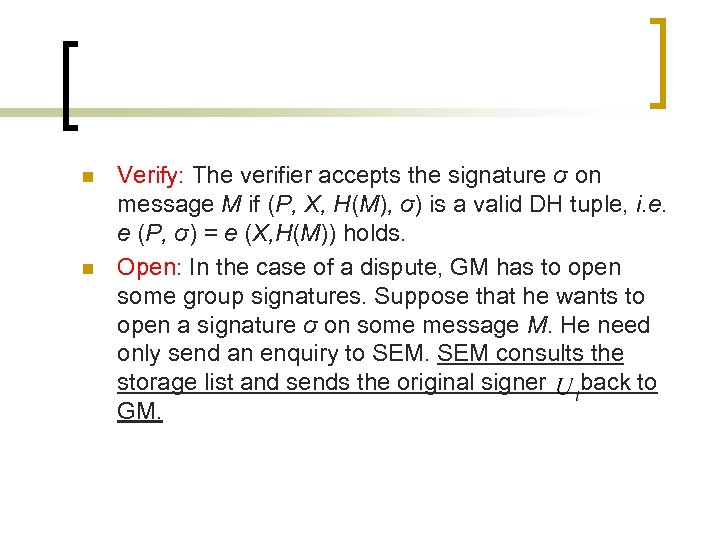
n n Verify: The verifier accepts the signature σ on message M if (P, X, H(M), σ) is a valid DH tuple, i. e. e (P, σ) = e (X, H(M)) holds. Open: In the case of a dispute, GM has to open some group signatures. Suppose that he wants to open a signature σ on some message M. He need only send an enquiry to SEM consults the storage list and sends the original signer back to GM.
Setup Input k GM
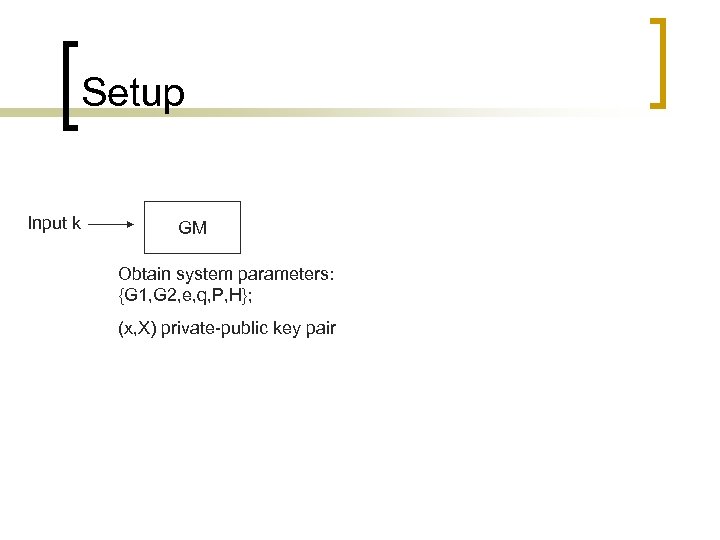
Setup Input k GM Obtain system parameters: {G 1, G 2, e, q, P, H}; (x, X) private-public key pair
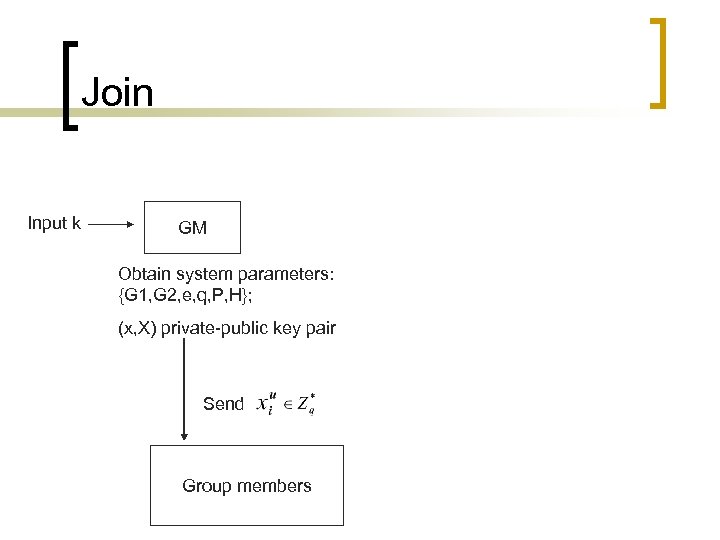
Join Input k GM Obtain system parameters: {G 1, G 2, e, q, P, H}; (x, X) private-public key pair Send Group members
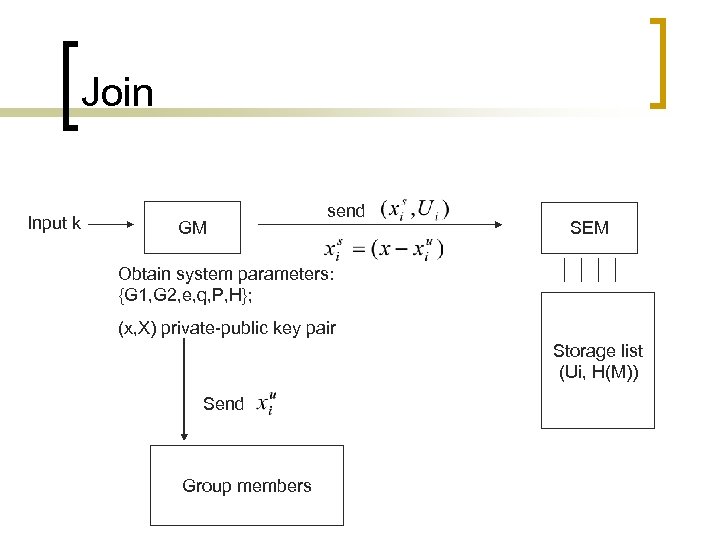
Join Input k GM send SEM Obtain system parameters: {G 1, G 2, e, q, P, H}; (x, X) private-public key pair Storage list (Ui, H(M)) Send Group members
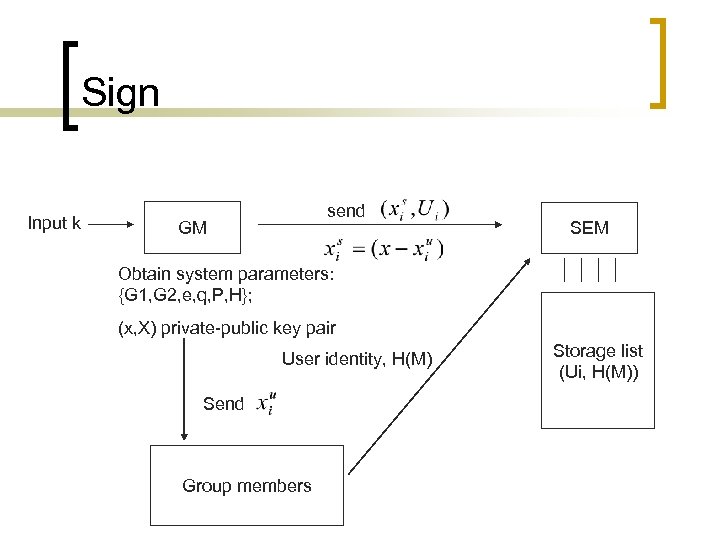
Sign Input k send GM SEM Obtain system parameters: {G 1, G 2, e, q, P, H}; (x, X) private-public key pair User identity, H(M) Send Group members Storage list (Ui, H(M))
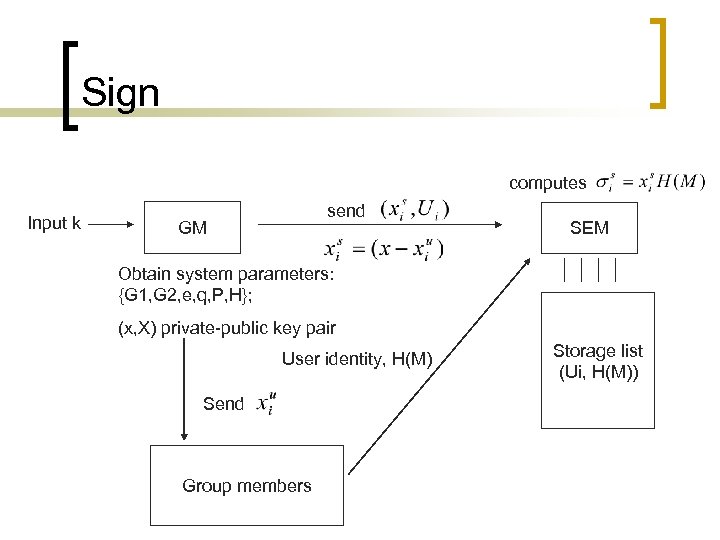
Sign computes Input k send GM SEM Obtain system parameters: {G 1, G 2, e, q, P, H}; (x, X) private-public key pair User identity, H(M) Send Group members Storage list (Ui, H(M))
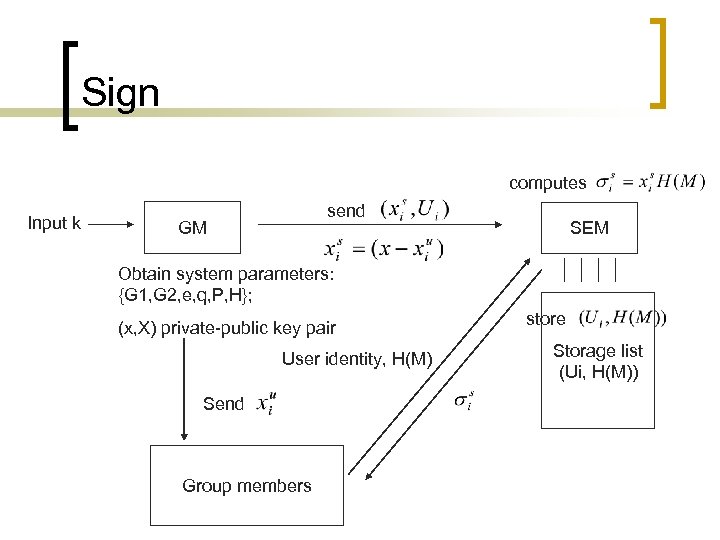
Sign computes Input k send GM SEM Obtain system parameters: {G 1, G 2, e, q, P, H}; (x, X) private-public key pair User identity, H(M) Send Group members store Storage list (Ui, H(M))
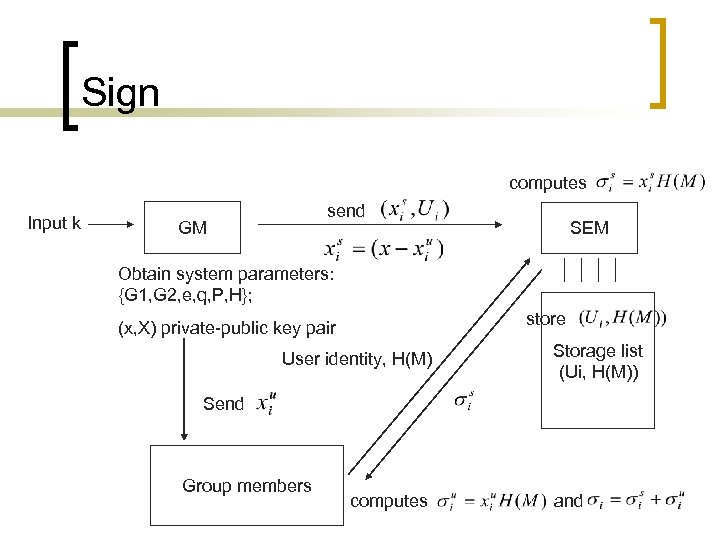
Sign computes Input k send GM SEM Obtain system parameters: {G 1, G 2, e, q, P, H}; store (x, X) private-public key pair User identity, H(M) Storage list (Ui, H(M)) Send Group members computes and
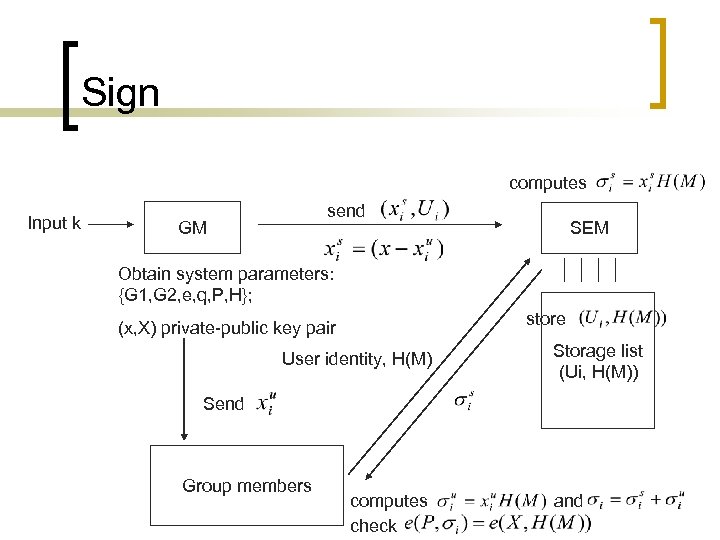
Sign computes Input k send GM SEM Obtain system parameters: {G 1, G 2, e, q, P, H}; store (x, X) private-public key pair User identity, H(M) Storage list (Ui, H(M)) Send Group members computes check and
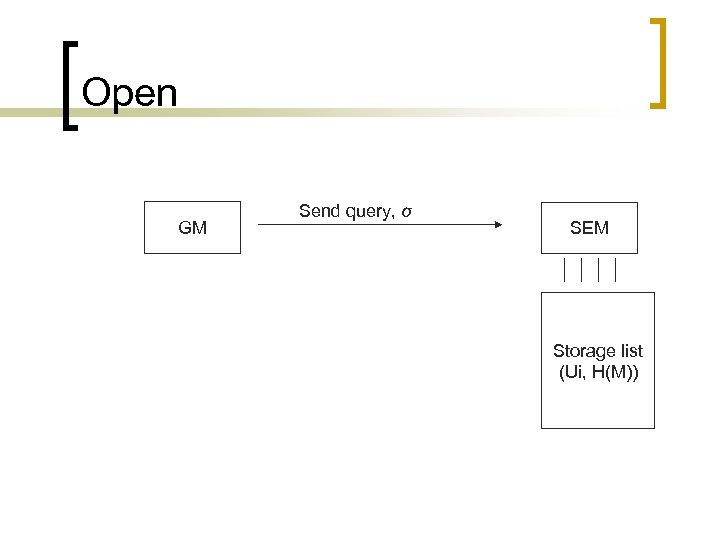
Open GM Send query, σ SEM Storage list (Ui, H(M))
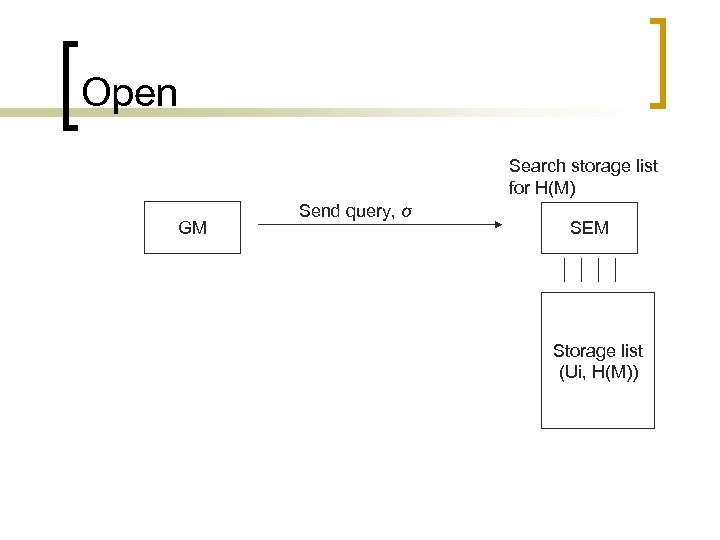
Open Search storage list for H(M) GM Send query, σ SEM Storage list (Ui, H(M))
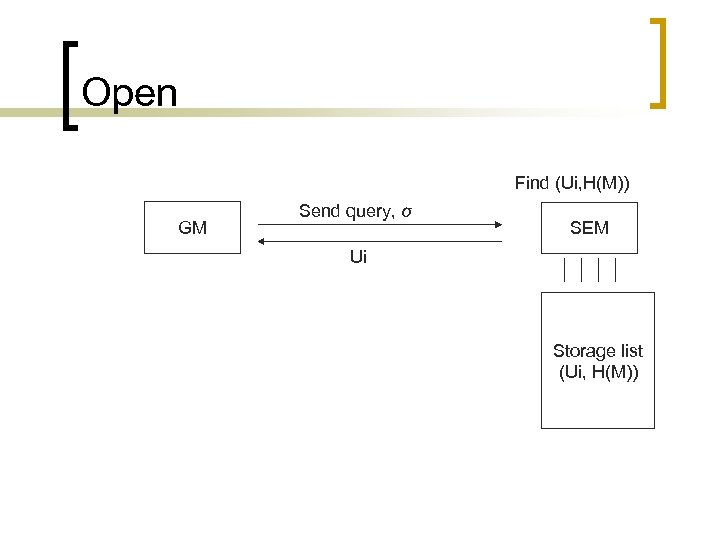
Open Find (Ui, H(M)) GM Send query, σ SEM Ui Storage list (Ui, H(M))

Security Analysis n Correctness: The group signature σ on message M given by the group member consists of two parts: the partial signature given by SEM and the partial signature given by. We note that: n since mod q. That is to say, σ is a BLS short signature of M under the group public key X. Therefore,

n Unforgeability: It is shown in BLS short signature that the underlying scheme is existential unforgeable in the random oracle model for any GDH group. (use some security game to prove that existential unforgeable on adaptive chosenmessage attacks)

n Anonymity: Given a message M, the group signature generated by the group member is: and the group signature generated by the group member is: Therefore, the group signatures on the same message generated by different group members are all the same. ※不同的group member對相同的message有相同的signature, 所以要分辨這份文件是誰簽署是困難的 In no case can one determine the original signer just from the group signature.

n Unlinkability: As discussed above, anyone (even if GM) can find nothing from the signature about the signer since the group signatures on the same message generated by different group members are all the same and a group signature consists of no information of the original signer. That is, given several group signatures, it is difficult to determine whether they were generated by the same group member or not. ※不同的group member對相同的message有相同的 signature, 所以給定一些群簽去分辨是哪個成員簽 署是困難的

n Exculpability: Note that none of the group member can generate a group signature without the help of SEM. Once a group member has signed a message, his identity along with the hash value of the message must have been stored by the trusted SEM in the storage list. Therefore, none of the group members can sign messages on behalf of other group members or attribute a signature generated by a group member to another since when ※沒有任何成員可以單獨做簽章動作而不需要靠 SEM, 所以任一成員無法取代其他成員.

n Traceability: In the case of a dispute, GM can easily open any group signature and identify the actual signer with the help of the trusted SEM. We note that all group signatures can be produced only with the help of SEM, and SEM has stored the identities of the original signers at the time it provided the partial signatures. ※因為SEM會儲存Ui的identity以及所簽署的H(M), 所 以可以很簡單的就知道這分文件是誰所簽署的

n Coalition-resistance: We note that, without the help of SEM, none of the group members can generate a valid group signature. Even if a coalition of some group members (even a whole set of the entire group) collaborate, they cannot generate a valid group signature since mod q, mod q for any positive integers j and l. ※根據定義而言, 成員間無法共謀去取代另一成員做 簽章.

Advantage of mini group signature (1) As discussed above, the group signature is in fact the BLS short signature from bilinear pairing. (2) SEM提供一個簡單且立即的方法去移除group成員, 因為沒有任 何成員做簽章時不需要靠 SEM幫忙. (3) SEM 提供一個有效的方法去join a group member. (4) The storage of the identities 提供給GM得知某個簽章是哪個成 員所簽署的.

The Improved Group Signature n There is also a drawback in mini group signature scheme: GM can generate valid group signatures on behalf of any group member since he knows the private keys of all group members. ※當GM知道群組成員的private key時, GM可以取代 其他成員做簽章動作

The Improved Group Signature n Setup: Given a security parameter κ, GM and SEM do the following work, respectively. - GM runs the GDH Parameters Generator to obtain the system parameters Params = {G 1, G 2, e, q, P, H}. - GM randomly chooses a number x and computes X=x. P. - SEM randomly chooses y and computes Y=y. P. The group public key is (X, Y ), while x and y are kept secret by GM and SEM, respectively.

n Join: Suppose that a user wants to join the group. We assume that the communication among GM, SEM and the users is secure. To realize the join of , they collaborate to do as follows: - GM randomly chooses computes mod q. is send to and is send to SEM. - After receiving , SEM randomly chooses and computes mod q. It keeps secret and send to. After this protocol, becomes a group member and his group membership secret key is.
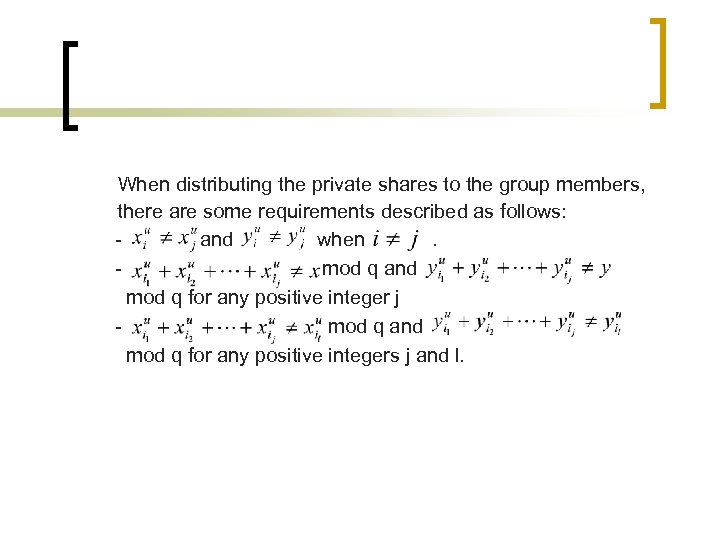
When distributing the private shares to the group members, there are some requirements described as follows: and when. mod q and mod q for any positive integer j mod q and mod q for any positive integers j and l.

n Sign: To generate a group signature on some message M, collaborates with SEM to do the following work: - sends H(M) along with his identity to SEM. - SEM first checks that ‘s membership has not been revoked. It then computes and. It stores and sends back to. - computes and. Let. He checks whether holds. If so, the group signature on message M is set to be.

n Verify: The verifier accepts the group signature σ on message M if (P, X+Y, H(M), σ) is a valid DH tuple, that is, e (P, σ) = e (X + Y, H(M)) holds. n Open: To open a group signature, GM needs only to send a enquiry to SEM can easily identifies the original signer from the storage list.
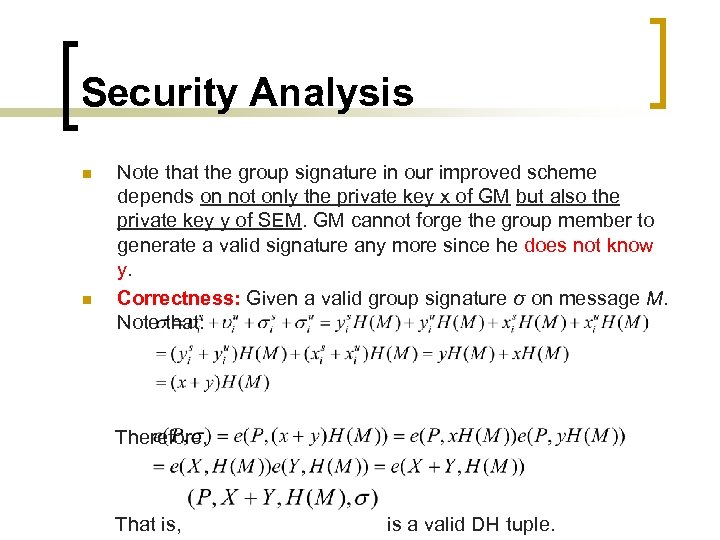
Security Analysis n n Note that the group signature in our improved scheme depends on not only the private key x of GM but also the private key y of SEM. GM cannot forge the group member to generate a valid signature any more since he does not know y. Correctness: Given a valid group signature σ on message M. Note that: Therefore, That is, is a valid DH tuple.

n Unforgeability: Suppose that there is a polynomial time adversary A for our group signature scheme, we will construct an adversary B for the underlying BLS short signature scheme by making use of A. We give a strong assumption that the adversary B has corrupted GM or GM is dishonest. The adversary is given the access to the hash and group signature signing oracles. B simulates GM and interacts with A as the following.

n n n Hash Queries: A requests the hash values on some messages of his choice, B makes the same queries on these messages to its own hash oracle and gives the responses back to A. Group Signature Queries: Proceeding adaptively, A requests the group signatures on some messages of his choice. B requests the signatures on these messages to its own group signature oracle and gives the response back to A. For the j-th query, A supplies a messages Mj , and obtains the response σj. Outputs: Eventually algorithm A halts, outputting a message M* and its group signature forgery σ*, Where M* must be a message that A have not required. If A fails to output a valid forgery, then B reports failure and terminates. Otherwise, B computes σ*1 = x. H( M* ) and σ*2 = σ* − σ*1. It is apparent that ˆσ2 is a valid BLS short signature forgery of ˆM under the public key Y.

n n If there exists an efficient algorithm A to forge our group signature scheme, then we can construct an algorithm B, with the same advantage, to forge the underlying BLS short signature scheme. However, the BLS short signature scheme is secure against existential forgery under adaptively chosen message attack in the random oracle model with the assumption that G 1 is a GDH group. Therefore, Our group signature scheme is existential unforgeable.
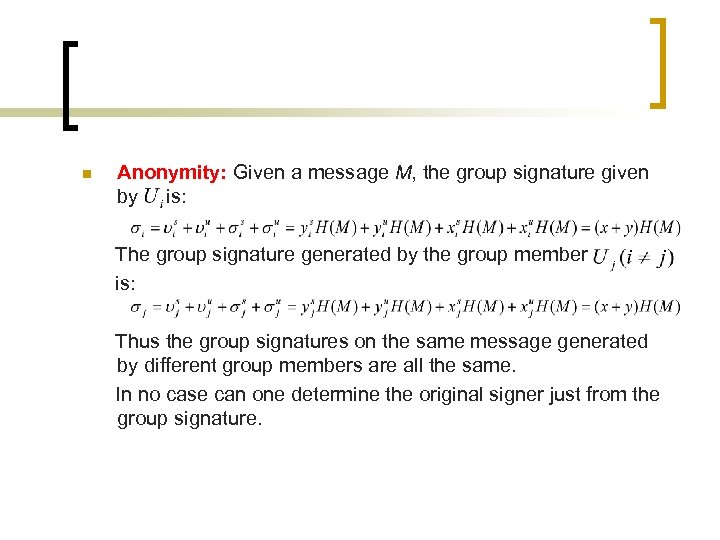
n Anonymity: Given a message M, the group signature given by is: The group signature generated by the group member is: Thus the group signatures on the same message generated by different group members are all the same. In no case can one determine the original signer just from the group signature.

n Unlinkability: As discussed above, anyone (even if GM) can find nothing from the signature about the signer since the group signatures on the same message generated by different group members are all the same and a group signature consists of no information of the original signer. That is, given several group signatures, it is difficult to determine whether they were generated by the same group member or not.

n Exculpability: Note that none of the group member can generate a group signature without the help of SEM. Once a group member has signed a message, his identity along with the hash value of the message must have been stored by the trusted SEM in the storage list. Therefore, none of the group members can sign messages on behalf of other group members or attribute a signature generated by a group member to another since and when

n Traceability: Since SEM has stored the identity of the signer at the time it provided the partial signatures, it is easy for GM to open a group signature and identify the actual signer with the help of SEM.

n Coalition-resistance:

Conclution n n We have proposed two types of group signature schemes based on the bilinear pairings The introduction of the security mediator (SEM): ¡ ¡ ¡ n the join of the group members the immediate revocation of the membership the open of the group signatures very simple and practical Note that the signatures on the same message signed by different group members are all the same. Once two different group members have signed the same message, SEM will not be able to distinguish between the two original signers. ¡ Solution: SEM does not allow different group members to sign the same message.
7b61b50a0af3c9f58ee5eac7a87c3451.ppt