98c59820f2b15860c07814f09c957491.ppt
- Количество слайдов: 29
 Effective Wireless Security – Technology and Policy CSG 256 Final Project Presentation by Dan Ziminski & Bill Davidge CSG 357 Dan Ziminski & Bill Davidge 1
Effective Wireless Security – Technology and Policy CSG 256 Final Project Presentation by Dan Ziminski & Bill Davidge CSG 357 Dan Ziminski & Bill Davidge 1
 AGENDA Some attacks to WLANs Authentication Protocols Encryption Protocols Rogue AP problem Case Studies CSG 357 Dan Ziminski & Bill Davidge 2
AGENDA Some attacks to WLANs Authentication Protocols Encryption Protocols Rogue AP problem Case Studies CSG 357 Dan Ziminski & Bill Davidge 2
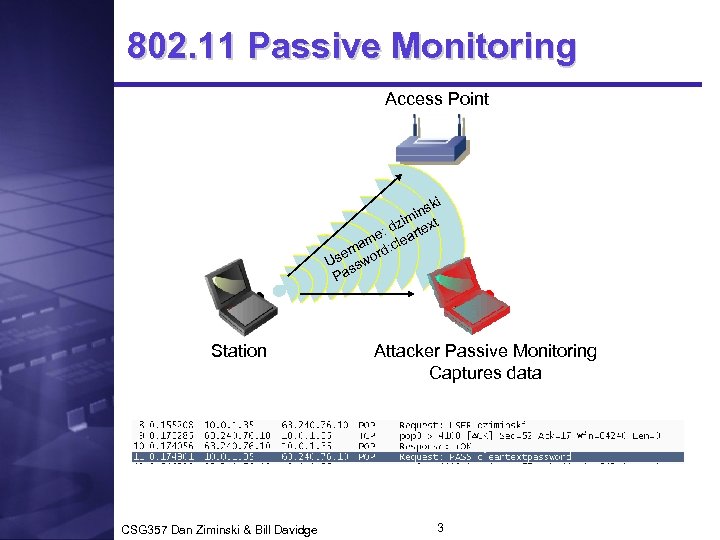 802. 11 Passive Monitoring Access Point ki ins im dz rtext e: a am d: cle rn or e Us ssw Pa Station CSG 357 Dan Ziminski & Bill Davidge Attacker Passive Monitoring Captures data 3
802. 11 Passive Monitoring Access Point ki ins im dz rtext e: a am d: cle rn or e Us ssw Pa Station CSG 357 Dan Ziminski & Bill Davidge Attacker Passive Monitoring Captures data 3
 802. 11 DOS Attack Access Point X Station Connection is broken Attacker spoofs 802. 11 Disassociate frame CSG 357 Dan Ziminski & Bill Davidge 4
802. 11 DOS Attack Access Point X Station Connection is broken Attacker spoofs 802. 11 Disassociate frame CSG 357 Dan Ziminski & Bill Davidge 4
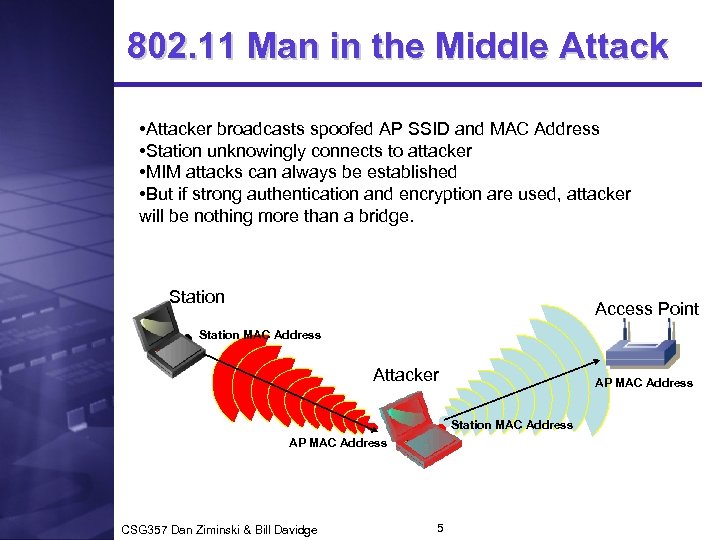 802. 11 Man in the Middle Attack • Attacker broadcasts spoofed AP SSID and MAC Address • Station unknowingly connects to attacker • MIM attacks can always be established • But if strong authentication and encryption are used, attacker will be nothing more than a bridge. Station Access Point Station MAC Address Attacker AP MAC Address Station MAC Address AP MAC Address CSG 357 Dan Ziminski & Bill Davidge 5
802. 11 Man in the Middle Attack • Attacker broadcasts spoofed AP SSID and MAC Address • Station unknowingly connects to attacker • MIM attacks can always be established • But if strong authentication and encryption are used, attacker will be nothing more than a bridge. Station Access Point Station MAC Address Attacker AP MAC Address Station MAC Address AP MAC Address CSG 357 Dan Ziminski & Bill Davidge 5
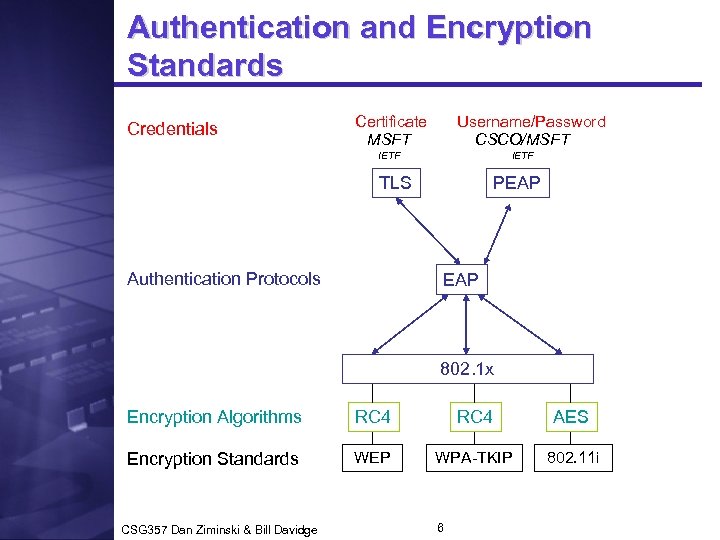 Authentication and Encryption Standards Credentials Certificate MSFT Username/Password CSCO/MSFT IETF TLS Authentication Protocols PEAP 802. 1 x Encryption Algorithms RC 4 AES Encryption Standards WEP WPA-TKIP 802. 11 i CSG 357 Dan Ziminski & Bill Davidge 6
Authentication and Encryption Standards Credentials Certificate MSFT Username/Password CSCO/MSFT IETF TLS Authentication Protocols PEAP 802. 1 x Encryption Algorithms RC 4 AES Encryption Standards WEP WPA-TKIP 802. 11 i CSG 357 Dan Ziminski & Bill Davidge 6
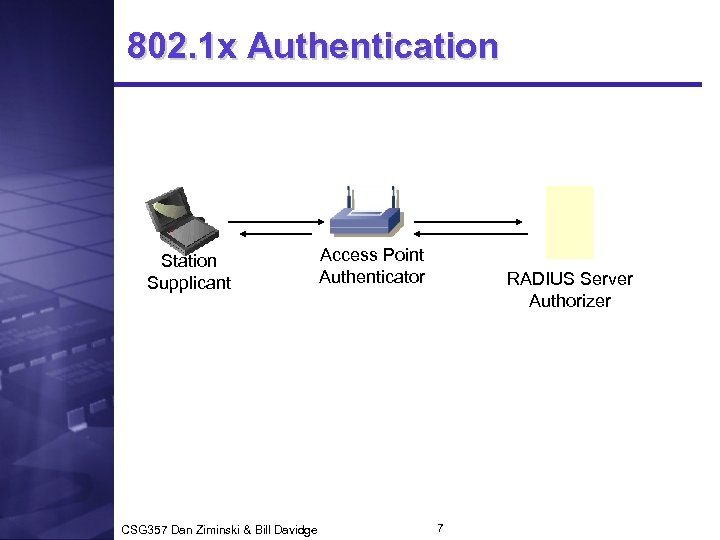 802. 1 x Authentication Station Supplicant CSG 357 Dan Ziminski & Bill Davidge Access Point Authenticator RADIUS Server Authorizer 7
802. 1 x Authentication Station Supplicant CSG 357 Dan Ziminski & Bill Davidge Access Point Authenticator RADIUS Server Authorizer 7
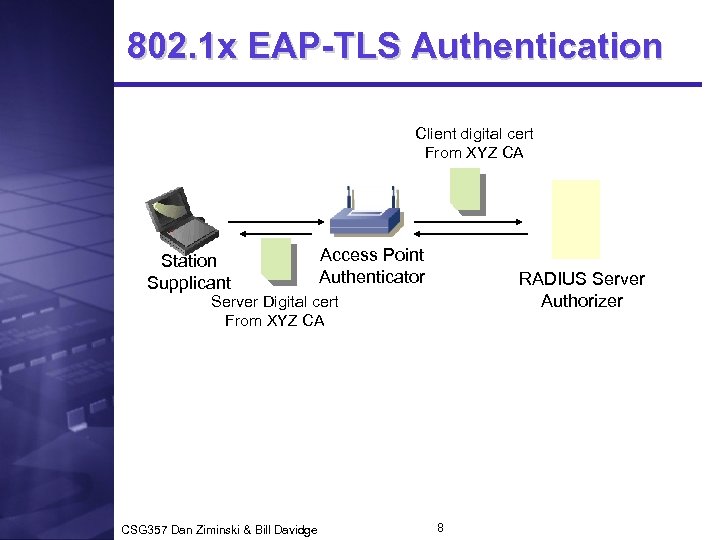 802. 1 x EAP-TLS Authentication Client digital cert From XYZ CA Station Supplicant Access Point Authenticator RADIUS Server Authorizer Server Digital cert From XYZ CA CSG 357 Dan Ziminski & Bill Davidge 8
802. 1 x EAP-TLS Authentication Client digital cert From XYZ CA Station Supplicant Access Point Authenticator RADIUS Server Authorizer Server Digital cert From XYZ CA CSG 357 Dan Ziminski & Bill Davidge 8
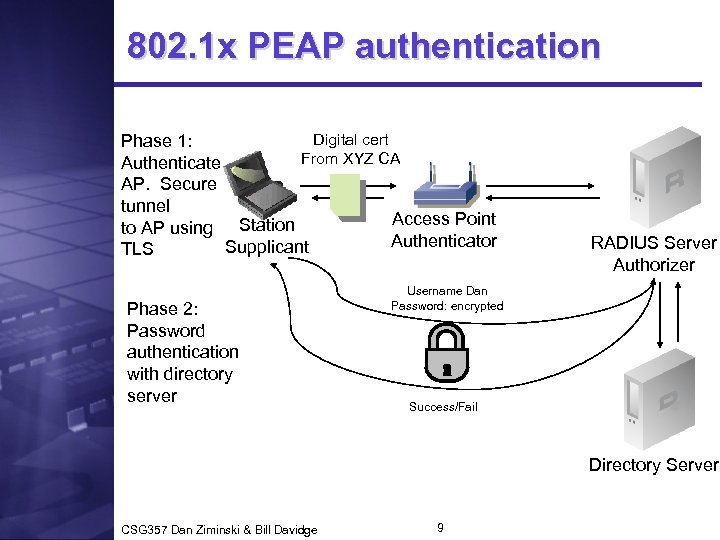 802. 1 x PEAP authentication Digital cert Phase 1: From XYZ CA Authenticate AP. Secure tunnel Access Point to AP using Station Authenticator Supplicant TLS Phase 2: Password authentication with directory server RADIUS Server Authorizer Username Dan Password: encrypted Success/Fail Directory Server CSG 357 Dan Ziminski & Bill Davidge 9
802. 1 x PEAP authentication Digital cert Phase 1: From XYZ CA Authenticate AP. Secure tunnel Access Point to AP using Station Authenticator Supplicant TLS Phase 2: Password authentication with directory server RADIUS Server Authorizer Username Dan Password: encrypted Success/Fail Directory Server CSG 357 Dan Ziminski & Bill Davidge 9
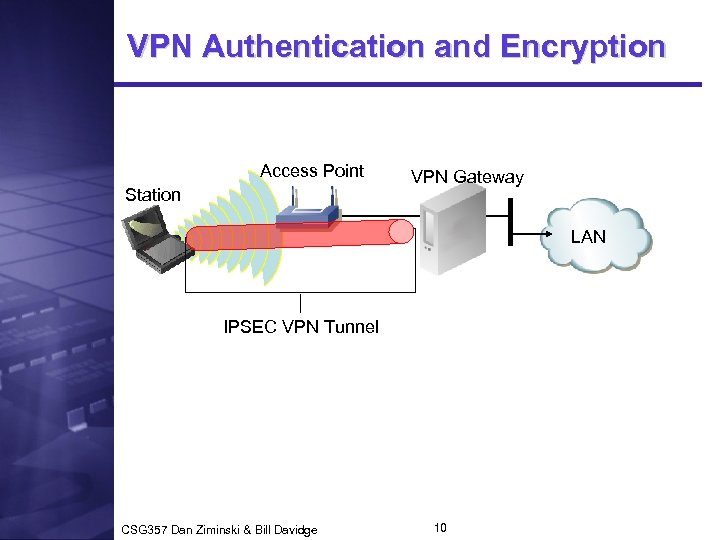 VPN Authentication and Encryption Access Point Station VPN Gateway LAN IPSEC VPN Tunnel CSG 357 Dan Ziminski & Bill Davidge 10
VPN Authentication and Encryption Access Point Station VPN Gateway LAN IPSEC VPN Tunnel CSG 357 Dan Ziminski & Bill Davidge 10
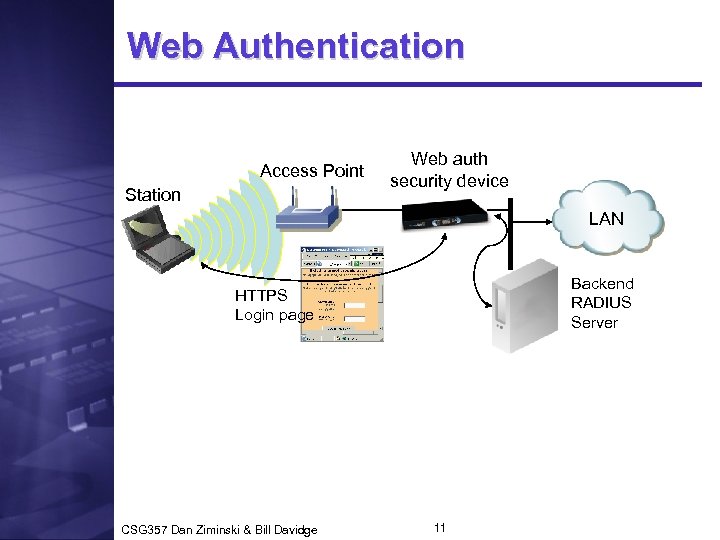 Web Authentication Access Point Station Web auth security device LAN Backend RADIUS Server HTTPS Login page CSG 357 Dan Ziminski & Bill Davidge 11
Web Authentication Access Point Station Web auth security device LAN Backend RADIUS Server HTTPS Login page CSG 357 Dan Ziminski & Bill Davidge 11
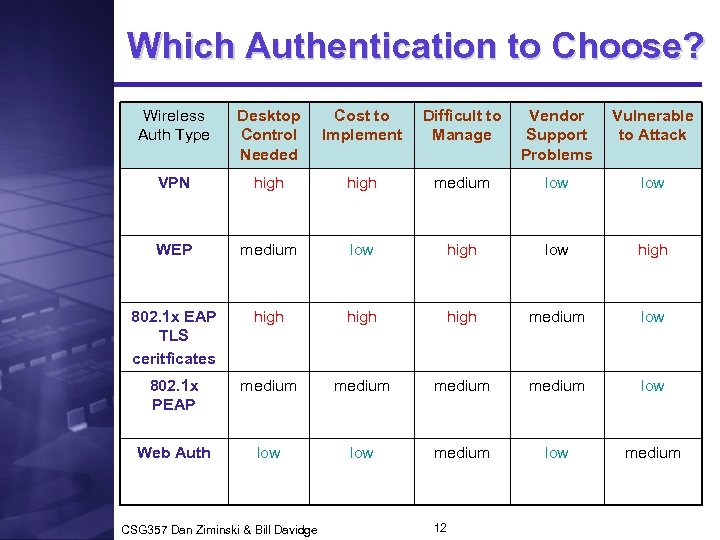 Which Authentication to Choose? Wireless Auth Type Desktop Control Needed Cost to Implement Difficult to Manage Vendor Support Problems Vulnerable to Attack VPN high medium low WEP medium low high 802. 1 x EAP TLS ceritficates high medium low 802. 1 x PEAP medium low Web Auth low medium CSG 357 Dan Ziminski & Bill Davidge 12
Which Authentication to Choose? Wireless Auth Type Desktop Control Needed Cost to Implement Difficult to Manage Vendor Support Problems Vulnerable to Attack VPN high medium low WEP medium low high 802. 1 x EAP TLS ceritficates high medium low 802. 1 x PEAP medium low Web Auth low medium CSG 357 Dan Ziminski & Bill Davidge 12
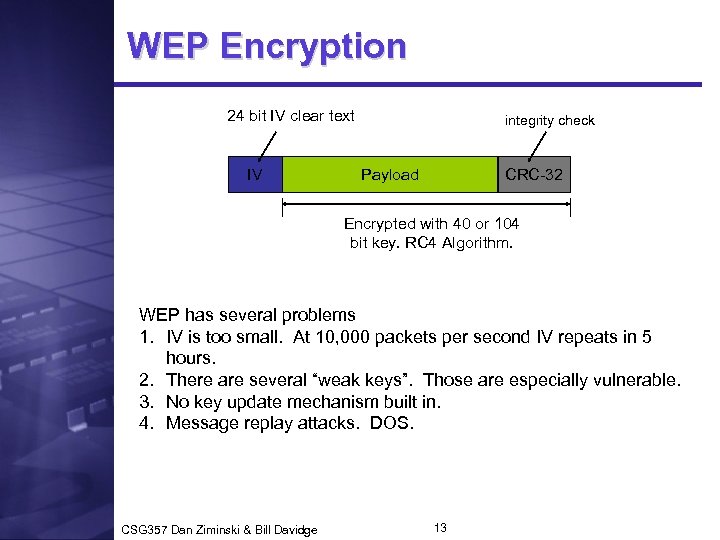 WEP Encryption 24 bit IV clear text IV integrity check Payload CRC-32 Encrypted with 40 or 104 bit key. RC 4 Algorithm. WEP has several problems 1. IV is too small. At 10, 000 packets per second IV repeats in 5 hours. 2. There are several “weak keys”. Those are especially vulnerable. 3. No key update mechanism built in. 4. Message replay attacks. DOS. CSG 357 Dan Ziminski & Bill Davidge 13
WEP Encryption 24 bit IV clear text IV integrity check Payload CRC-32 Encrypted with 40 or 104 bit key. RC 4 Algorithm. WEP has several problems 1. IV is too small. At 10, 000 packets per second IV repeats in 5 hours. 2. There are several “weak keys”. Those are especially vulnerable. 3. No key update mechanism built in. 4. Message replay attacks. DOS. CSG 357 Dan Ziminski & Bill Davidge 13
 Wi-Fi Protected Access (WPA) TKIPencryption • Wi-Fi Protected Access is an interim standard created by the Wi-Fi alliance (group of manufacturers). • WPA-TKIP fixes problems with WEP. • IV changes to 48 bits with no weak keys. 900 years to repeat an IV at 10 k packets/sec. • Use IV as a replay counter. • Message integrity. • Per-packet keying. • Supported on many wireless card and on Windows XP (after applying 2 hot fixes). • Uses 802. 1 x for key distribution. • Can also use static keys. CSG 357 Dan Ziminski & Bill Davidge 14
Wi-Fi Protected Access (WPA) TKIPencryption • Wi-Fi Protected Access is an interim standard created by the Wi-Fi alliance (group of manufacturers). • WPA-TKIP fixes problems with WEP. • IV changes to 48 bits with no weak keys. 900 years to repeat an IV at 10 k packets/sec. • Use IV as a replay counter. • Message integrity. • Per-packet keying. • Supported on many wireless card and on Windows XP (after applying 2 hot fixes). • Uses 802. 1 x for key distribution. • Can also use static keys. CSG 357 Dan Ziminski & Bill Davidge 14
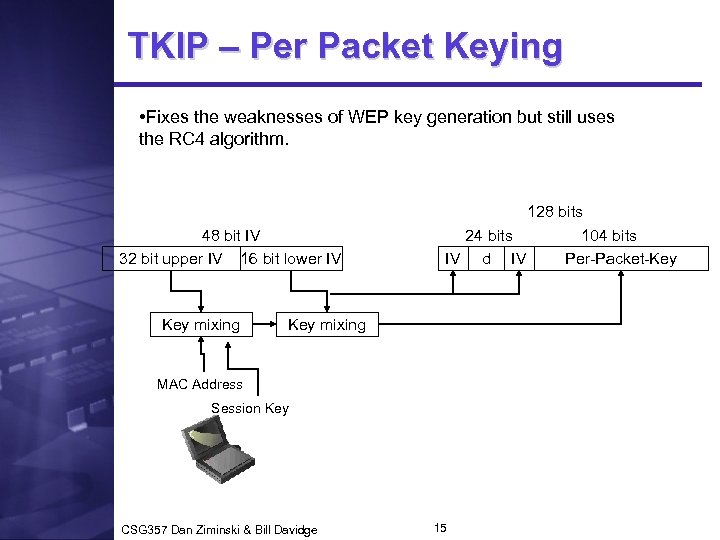 TKIP – Per Packet Keying • Fixes the weaknesses of WEP key generation but still uses the RC 4 algorithm. 48 bit IV 32 bit upper IV 16 bit lower IV Key mixing 128 bits 24 bits 104 bits IV d IV Per-Packet-Key mixing MAC Address Session Key CSG 357 Dan Ziminski & Bill Davidge 15
TKIP – Per Packet Keying • Fixes the weaknesses of WEP key generation but still uses the RC 4 algorithm. 48 bit IV 32 bit upper IV 16 bit lower IV Key mixing 128 bits 24 bits 104 bits IV d IV Per-Packet-Key mixing MAC Address Session Key CSG 357 Dan Ziminski & Bill Davidge 15
 802. 11 i AES-encryption • Ratified by the IETF in June of 04. • Uses the AES algorithm for encryption and 802. 1 x for key distribution. • Backwards compatible with TKIP to support WPA clients. • 802. 11 i not in many products yet. CSG 357 Dan Ziminski & Bill Davidge 16
802. 11 i AES-encryption • Ratified by the IETF in June of 04. • Uses the AES algorithm for encryption and 802. 1 x for key distribution. • Backwards compatible with TKIP to support WPA clients. • 802. 11 i not in many products yet. CSG 357 Dan Ziminski & Bill Davidge 16
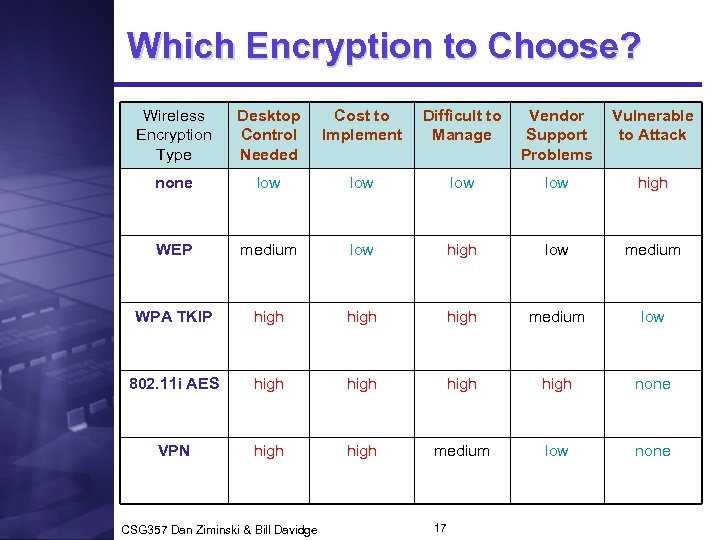 Which Encryption to Choose? Wireless Encryption Type Desktop Control Needed Cost to Implement Difficult to Manage Vendor Support Problems Vulnerable to Attack none low low high WEP medium low high low medium WPA TKIP high medium low 802. 11 i AES high none VPN high medium low none CSG 357 Dan Ziminski & Bill Davidge 17
Which Encryption to Choose? Wireless Encryption Type Desktop Control Needed Cost to Implement Difficult to Manage Vendor Support Problems Vulnerable to Attack none low low high WEP medium low high low medium WPA TKIP high medium low 802. 11 i AES high none VPN high medium low none CSG 357 Dan Ziminski & Bill Davidge 17
 Newbury Networks • 3 -hour “war driving” DNC in Boston – A total of 3, 683 unique Wi-Fi devices – An average of 1 wireless network card every 2 minutes – Nearly 3, 000 of the total Wi-Fi devices were discovered in Boston's Back Bay CSG 357 Dan Ziminski & Bill Davidge 18
Newbury Networks • 3 -hour “war driving” DNC in Boston – A total of 3, 683 unique Wi-Fi devices – An average of 1 wireless network card every 2 minutes – Nearly 3, 000 of the total Wi-Fi devices were discovered in Boston's Back Bay CSG 357 Dan Ziminski & Bill Davidge 18
 3 -hour “war driving” DNC in Boston – 65% of the wireless networks detected had no encryption – 457 unique wireless access points-the majority of which were unsecured CSG 357 Dan Ziminski & Bill Davidge 19
3 -hour “war driving” DNC in Boston – 65% of the wireless networks detected had no encryption – 457 unique wireless access points-the majority of which were unsecured CSG 357 Dan Ziminski & Bill Davidge 19
 Def. Con X Hacker Convention-2002 • 2 -hour monitoring Wireless LAN – Identified 8 sanctioned access points – 35 rogue access points, and more than – – 800 different station addresses CSG 357 Dan Ziminski & Bill Davidge 20
Def. Con X Hacker Convention-2002 • 2 -hour monitoring Wireless LAN – Identified 8 sanctioned access points – 35 rogue access points, and more than – – 800 different station addresses CSG 357 Dan Ziminski & Bill Davidge 20
 Def. Con X Hacker Convention-2002 – 200 to 300 of the station addresses were fakes – 115 peer-to-peer ad hoc networks and identified 123 stations that launched a total of 807 attacks during the two hours – 490 were wireless probes from tools such as Netstumbler and Kismet CSG 357 Dan Ziminski & Bill Davidge 21
Def. Con X Hacker Convention-2002 – 200 to 300 of the station addresses were fakes – 115 peer-to-peer ad hoc networks and identified 123 stations that launched a total of 807 attacks during the two hours – 490 were wireless probes from tools such as Netstumbler and Kismet CSG 357 Dan Ziminski & Bill Davidge 21
 Def. Con X Hacker Convention-2002 • 100 were varying forms Denial-of. Service attacks that either – jammed the airwaves with noise to shut down an access point – targeted specific stations by continually disconnecting them from an access point or – forced stations to route their traffic through other stations CSG 357 Dan Ziminski & Bill Davidge 22
Def. Con X Hacker Convention-2002 • 100 were varying forms Denial-of. Service attacks that either – jammed the airwaves with noise to shut down an access point – targeted specific stations by continually disconnecting them from an access point or – forced stations to route their traffic through other stations CSG 357 Dan Ziminski & Bill Davidge 22
 Def. Con X Hacker Convention-2002 – 27 attacks came from out-of-specification management frames where hackers launched attacks that exploited 802. 11 protocols to take over other stations and control the network • 190 were identity thefts, such as when MAC addresses and SSIDs CSG 357 Dan Ziminski & Bill Davidge 23
Def. Con X Hacker Convention-2002 – 27 attacks came from out-of-specification management frames where hackers launched attacks that exploited 802. 11 protocols to take over other stations and control the network • 190 were identity thefts, such as when MAC addresses and SSIDs CSG 357 Dan Ziminski & Bill Davidge 23
 CSG 357 Dan Ziminski & Bill Davidge 24
CSG 357 Dan Ziminski & Bill Davidge 24
 Case Studies-University • University – fosters an open, sharing environment – “…allow all, deny some…” as far as access goes. – large area – large user population – knowledgeable support group and a wide spectrum of knowledge in the user base CSG 357 Dan Ziminski & Bill Davidge 25
Case Studies-University • University – fosters an open, sharing environment – “…allow all, deny some…” as far as access goes. – large area – large user population – knowledgeable support group and a wide spectrum of knowledge in the user base CSG 357 Dan Ziminski & Bill Davidge 25
 Case Studies-Financial Institution – restricted access – limited number of authorized users – Technical staff with control of user hardware – geographically dispersed locations CSG 357 Dan Ziminski & Bill Davidge 26
Case Studies-Financial Institution – restricted access – limited number of authorized users – Technical staff with control of user hardware – geographically dispersed locations CSG 357 Dan Ziminski & Bill Davidge 26
 Case Study: Global Bank (alias) • In process of deploying enterprise WLAN. • Using 802. 1 x EAP-TLS with client web certificate for authentication. • Tested PEAP, but failed auth attempts would lock out users Active Directory account. • Had a small VPN pilot but found it didn’t scale. • Originally started testing WPA-TKIP but too many interoperability problems with card and APs. • Switched to WEP with keys rotating every 30 minutes using 802. 1 x. They feel that this is secure enough. • Monitor for rogue APs. Any rogue that is detected by 3+ APs is investigated and removed if on LAN. CSG 357 Dan Ziminski & Bill Davidge 27
Case Study: Global Bank (alias) • In process of deploying enterprise WLAN. • Using 802. 1 x EAP-TLS with client web certificate for authentication. • Tested PEAP, but failed auth attempts would lock out users Active Directory account. • Had a small VPN pilot but found it didn’t scale. • Originally started testing WPA-TKIP but too many interoperability problems with card and APs. • Switched to WEP with keys rotating every 30 minutes using 802. 1 x. They feel that this is secure enough. • Monitor for rogue APs. Any rogue that is detected by 3+ APs is investigated and removed if on LAN. CSG 357 Dan Ziminski & Bill Davidge 27
 Case Studies: home networks – small number of users – with no expectation of heavy volume – Limited technological expertise CSG 357 Dan Ziminski & Bill Davidge 28
Case Studies: home networks – small number of users – with no expectation of heavy volume – Limited technological expertise CSG 357 Dan Ziminski & Bill Davidge 28
 Q and A • You Ask • We Answer CSG 357 Dan Ziminski & Bill Davidge 29
Q and A • You Ask • We Answer CSG 357 Dan Ziminski & Bill Davidge 29


